#system admin tools
Explore tagged Tumblr posts
Text
Emma Zaballos, Product Marketing Manager at CyCognito – Interview Series
New Post has been published on https://thedigitalinsider.com/emma-zaballos-product-marketing-manager-at-cycognito-interview-series/
Emma Zaballos, Product Marketing Manager at CyCognito – Interview Series


Emma Zaballos is an avid threat researcher who is passionate about understanding and combatting cybercrime threats. Emma enjoys monitoring dark web marketplaces, profiling ransomware gangs, and using intelligence for understanding cybercrime.
CyCognito, founded by veterans of national intelligence agencies, specializes in cybersecurity by identifying potential attack vectors from an external perspective. The company provides organizations with insights into how attackers may perceive their systems, highlighting vulnerabilities, potential entry points, and at-risk assets. Headquartered in Palo Alto, CyCognito serves large enterprises and Fortune 500 companies, including Colgate-Palmolive and Tesco
You have a diverse background in cybersecurity research, threat analysis, and product marketing. What first sparked your interest in this field, and how did your career evolve into exposure management?
Right out of college, I worked as an analyst on an international trade lawsuit that involved tracking a network of actors across the US (and internationally). It was a super interesting case and when I started looking for the next thing, I found a job at a dark web monitoring startup (Terbium Labs, now part of Deloitte) where I essentially pitched myself as “hey, I don’t know anything about the dark web or cybersecurity, but I have experience tracing networks and behavior and I think I can learn the rest.” And that worked out! I kept working in cybersecurity as a subject matter expert with a focus on threat actors through 2022, when I joined CyCognito in my first product marketing role. It’s been great to still be working in cybersecurity, which is an industry I’m super passionate about, while trying out a new role. I love that I get to fulfill my love of data-driven storytelling through writing content like CyCognito’s annual State of External Exposure Management report.
You mention that you’ll never own an Alexa. What concerns you most about smart home devices, and what should the average person know about the risks?
If you spend any time looking into the dark web, you’ll see that cybercriminals have an immense appetite for data—including consumer data collected by companies. Your data is a valuable resource and it’s one that many companies either can’t or won’t protect appropriately. You as a consumer have limited options to control how your data is collected, stored, and managed, but it’s important to be as informed as possible and control what you can. That can mean getting very good at adjusting settings in your apps or devices or just forgoing some products altogether.
By necessity, if you have a smart assistant enabled on your phone or a smart home device that requires a voice cue, the microphone has to be listening constantly to catch you asking for something. Even if I trust that the company is protecting those recordings and deleting them, I just personally don’t like the idea of having a microphone always on in my home.
There are definitely services and products of convenience that collect my data and I use them anyway, because it’s somehow worth it for me. Smart home products, though, are something where I’ve personally drawn the line—I’m ok physically going over and adjusting the lights or making a grocery list or whatever, instead of telling Alexa to do it. The Internet of Things offers some incredible benefits to the consumer, but it’s also been a boon to cybercriminals.
You’ve worked in both the federal and private sectors. How do the cybersecurity challenges differ between these environments?
When I worked on contract for the Department of Health and Human Services in their Health Sector Cybersecurity Coordination Center, it was much more focused on digging into patterns and motivations behind cybercriminals’ actions—understanding why they targeted healthcare resources and what kind of recommendations we could make to harden those defenses. There’s more space to get really in-depth on a project in the public sector and there are some incredible public servants doing work on cybersecurity in the federal and state governments. In both my startup roles, I’ve also gotten to do really interesting research, but it’s faster paced and more targeted on tighter scoped questions. One thing I do like about startups is that you can bring a little more of your own voice to research—it would have been harder to present something like my “Make Me Your Dark Web Personal Shopper” talk (DerbyCon 2019) on behalf of HHS.
In your recent article, you highlighted the rapid growth of the dark web. What factors are driving this expansion, and what trends do you see for the next few years?
The dark web is always dead, always dying, and always surging back to life. Sadly, there’s a consistent market for stolen data, malware, cybercrime-as-a-service, and all the other types of goods associated with the dark web, which means that even though dark web standbys like Silk Road, AlphaBay, and Agora are gone, new markets can rise to take their place. Political and financial instability also drives people to cybercrime.
It’s become cliche, but AI is a concern here – it makes it easier for an unsophisticated criminal to level-up skills, maybe by using AI-powered coding tools or through generative AI tools that can generate compelling phishing content.
Another factor driving the dark web renaissance is a strong crypto market. Cryptocurrency is the lifeblood of cybercrime—the modern ransomware market basically exists because of cryptocurrency—and a crypto-friendly government under the second Trump administration is likely to exacerbate dark web crime. The new administration’s cuts to federal cybersecurity and law enforcement programs, including CISA, are also a boon to cybercriminals, because the U.S. has historically led enforcement actions against major dark web marketplaces.
What are some of the biggest misconceptions about the dark web that businesses and individuals should be aware of?
The biggest misconception I see is that the dark web is this massive, mysterious entity that’s too complex to understand or defend against. In reality, it makes up less than 0.01% of the internet—but that small size masks its true impact on business security. Another common myth is that the dark web is impenetrable or completely anonymous. While it does require specialized tools like the Tor browser and .onion domains, we actively monitor these spaces every day. Because of the publicity behind the takedown of the Silk Road marketplace, organizations often think the dark web is just for selling illegal goods, like drugs or weapons, not realizing it’s also a massive and sophisticated marketplace for corporate assets and data. The reality is that the dark web is something it’s not just possible but essential for organizations to understand, because it has the potential to directly impact every business’s security posture.
You mentioned that organizations should “assume exposure.” What are some of the most overlooked ways companies unknowingly expose their data online?
What I find fascinating is how many companies still don’t realize the breadth of their exposure and the ways they could be exposed through the dark web. We regularly see leaked credentials circulating on dark web marketplaces—not just basic login details, but admin accounts and VPN credentials that could provide complete access to critical infrastructure. One particularly overlooked area is IoT devices. These seemingly innocent connected devices can be compromised and sold to create botnets or launch attacks. Modern IT environments have become incredibly complex, creating what we call an “extended attack surface” that goes far beyond what most organizations imagine they have. We’re talking about cloud services, network access points, and integrated systems that many companies don’t even realize are exposed. The hard truth is that most organizations have far more potential entry points than they think, so it’s better to assume there’s an exposure out there than to trust your existing defenses to be perfect.
How are cybercriminals leveraging AI to enhance their operations on the dark web, and how can businesses defend against AI-driven cyber threats?
Cybercrime is not really creating new types of attacks—it’s accelerating the ones we already know. We’re seeing criminals use AI to generate hundreds of incredibly convincing phishing emails in minutes, something that used to take days or weeks to do manually. They’re developing adaptive malware that can actually change its behavior to avoid detection, and they’re using specialized tools like WormGPT and FraudGPT that are specifically designed for criminal activities. Perhaps most concerning is how they’re managing to compromise legitimate AI platforms – we’ve seen stolen credentials from major AI providers being sold, and there’s a growing effort to “jailbreak” mainstream AI tools by removing their safety limitations.
But the good news is that we’re not defenseless. Forward-looking organizations are deploying AI systems that work around the clock to monitor dark web forums and marketplaces. These tools can analyze millions of posts in minutes, understand criminal coded language, and spot patterns that human analysts might miss. We’re using AI to scan for stolen credentials, monitor system access points, and provide early warning of potential breaches. The key is that our defensive AI can work at the same speed and scale as the criminal tools—it’s really the only way to keep up with modern threats.
CyCognito takes an “attacker’s perspective” to identify vulnerabilities. Can you walk us through how this approach differs from traditional security testing methods?
Our approach starts with understanding that modern IT environments are far more complex than traditional security models assume. We also don’t rely on what organizations know to inform our work – when attackers target an organization, they’re not getting lists of assets or context from their target, so we also go in with zero seed data from our customers. Based on that, we assemble a map of the organization and its attack surface and place all their assets in context in that map.
We map the entire extended attack surface, going beyond just known assets to understand what attackers actually see and can exploit. When we monitor dark web marketplaces, we’re not just collecting data—we’re understanding how leaked credentials, privileged access, and exposed information create pathways into an organization. By overlaying these dark web risks onto the existing attack surface, we give security teams a true attacker’s view of their vulnerabilities. This perspective helps them understand not just what might be vulnerable, but what’s actually exploitable.
How does CyCognito’s AI-driven discovery process work, and what makes it more effective than conventional external attack surface management (EASM) solutions?
We start with a fundamental understanding that every organization’s attack surface is significantly larger than traditional tools assume. Our AI-driven discovery process begins by mapping what we call the “extended attack surface”—a concept that goes far beyond conventional EASM solutions that only look at known assets.
Our process is comprehensive and proactive. We continuously scan for four critical types of exposure: leaked credentials, including hashed passwords that attackers might decrypt; accounts and privileged access being sold on dark web marketplaces; IP-based information leaks that could reveal network vulnerabilities; and sensitive data exposed through past breaches. But finding these exposures is just the first step.
We then map everything back to what we call the attack surface graph. This is where context becomes everything. Instead of just handing you a list of vulnerabilities like conventional EASM solutions do, we show you exactly how dark web exposures intersect with your existing infrastructure. This allows security teams to see not just where their data has ended up, but precisely where they need to focus their security efforts next.
Think of it as building a strategic map rather than just running a security scan. By overlaying dark web risks onto your actual attack surface, we provide security teams with a clear, actionable view of their most critical security gaps. This contextual understanding is essential for prioritizing remediation efforts effectively and ensuring a swift, targeted response to emerging threats.
Prioritization of risks is a major challenge for security teams. How does CyCognito differentiate between critical and non-critical vulnerabilities?
We prioritize vulnerabilities by understanding their context within an organization’s entire security ecosystem. It’s not enough to know that a credential has been exposed or an access point is vulnerable—we need to understand what that exposure means in terms of potential impact, and that impact can vary depending on the business context of the asset. We look particularly closely at privileged access credentials, administrative accounts, and VPN access points, as these often represent the greatest risk for lateral movement within systems. By mapping these exposures back to our attack surface graph, we can show security teams exactly which vulnerabilities pose the greatest risk to their most critical assets. This helps them focus their limited resources where they’ll have the biggest impact.
How do you see cybersecurity evolving in the next five years, and what role will AI play in both offense and defense?
We’re in the middle of a fundamental shift in the cybersecurity landscape, largely driven by AI. On the offensive side, we’re already seeing AI accelerate the scale and sophistication of attacks in ways that would have been impossible just a few years ago. New AI tools designed specifically for cybercrime, like WormGPT and FraudGPT, are emerging rapidly, and we’re seeing even legitimate AI platforms being compromised or “jailbroken” for malicious purposes.
On the defensive side, AI isn’t just an advantage anymore – it’s becoming a necessity. The speed and scale of modern attacks mean that traditional, human-only analysis simply can’t keep up. AI is essential for monitoring threats at scale, analyzing dark web activity, and providing the rapid response capabilities that modern security requires. But I want to emphasize that technology alone isn’t the answer. The organizations that will be most successful in navigating this new landscape are those that combine advanced AI capabilities with proactive security strategies and a deep understanding of their extended attack surface. The next five years will be about finding that balance between powerful AI tools and smart, strategic security planning.
Thank you for the great interview, readers who wish to learn more should visit CyCognito.
#2022#Accounts#admin#Administration#ai#AI platforms#AI systems#ai tools#AI-powered#alexa#Analysis#approach#apps#Article#assets#Attack surface#attackers#background#Behavior#browser#Building#Business#business security#career#challenge#change#cisa#Cloud#cloud services#coding
0 notes
Text
RegCool for Windows
RegCool is an advanced Windows registry editor that extends the capabilities of the default RegEdit and RegEdt32 tools. Designed for power users, IT professionals, and system administrators, RegCool offers an intuitive interface and a wide range of powerful features to manage and optimize the Windows registry efficiently. Whether you’re searching for registry keys, comparing different registry…
#advanced registry editor#free registry editor#IT admin tools#RegCool#RegCool download#registry backup#registry defragmentation#registry optimization#system performance#Windows management#Windows registry editor
0 notes
Text
The Future of Hospital Management: Innovations in Software Solutions

In the ever-evolving landscape of healthcare, the role of hospital management systems/software is becoming increasingly pivotal. As healthcare organizations strive for efficiency, cost-effectiveness, and improved patient care, innovative software solutions are driving significant transformations. Let's explore some key advancements in this domain, including patient systems, workflow automation, admin tools, integrated platforms, and clinic software.
Patient systems represent a fundamental component of modern hospital management software. These systems streamline patient registration, appointment scheduling, and medical record management, facilitating seamless interactions between patients and healthcare providers. By centralizing patient information and automating routine tasks, patient systems enhance operational efficiency and improve the overall patient experience.
Another critical innovation is workflow automation, which aims to streamline hospital operations and reduce manual workload. Automation tools optimize processes such as inventory management, billing, and staff scheduling, allowing healthcare providers to allocate resources more effectively and focus on delivering high-quality patient care. Workflow automation also minimizes errors and delays, enhancing the efficiency and accuracy of hospital management.
Admin tools are essential for hospital management, enabling administrators to oversee various aspects of hospital operations from a centralized dashboard. These tools provide real-time insights into key performance metrics, financial data, and resource allocation, empowering administrators to make informed decisions and drive organizational growth. Admin tools also facilitate communication and collaboration among different departments, fostering a cohesive and coordinated approach to hospital management.

Integrated platforms are revolutionizing hospital management by combining multiple functionalities into a unified system. These platforms seamlessly integrate patient management, electronic health records (EHR), billing, and reporting capabilities, eliminating silos and streamlining workflows across the organization. By providing a holistic view of hospital operations, integrated platforms enable better decision-making and resource optimization.
Lastly, clinic software caters to the specific needs of outpatient clinics and specialty practices within hospital settings. These software solutions offer features such as appointment scheduling, electronic medical records (EMR), and billing management tailored to the unique requirements of clinic settings. Clinic software enhances efficiency, improves patient engagement, and supports seamless coordination between clinics and the broader hospital network.
In conclusion, the future of hospital management lies in embracing innovative software solutions that enhance efficiency, streamline workflows, and improve patient care. From patient systems and workflow automation to admin tools, integrated platforms, and clinic software, these advancements are reshaping the way healthcare organizations operate and deliver services. By leveraging the power of technology, hospitals can navigate the complexities of modern healthcare delivery and thrive in an increasingly digital world.
0 notes
Text
Ruler of the 3rd through the houses
ruler of the 3rd house through the houses reveals how your mind works, how you learn and speak, your communication style, relationships with siblings, and how you move through your local environment. This also ties into social intelligence, storytelling, and how you interpret the world around you.
3rd House Ruler in the 1st House
Your mind is your identity.
You communicate with intensity and presence. Your thoughts are quick, and your words can leave an impression. People might see you as opinionated, witty, or always “in the know.” You probably need to speak to understand yourself. Talking over others, impatient listening are throngs that can happen.
3rd House Ruler in the 2nd House
Speaking as a source of value.
You might monetize your communication skills — writing, teaching, sales, or media. You think in practical terms, and your thoughts often revolve around worth, values, and security. Grounded, hands-on, slow but lasting retention. Watch for fixed mindsets, and attaching ideas to material worth.
3rd House Ruler in the 3rd House
Ultra communicator.
This doubles the Mercurial energy. You’re endlessly curious, naturally sharp, and likely live in your head. There’s a deep connection to language, possibly a gift for mimicry, writing, or storytelling. Fast, curious, often self-taught or info-obsessed.
3rd House Ruler in the 4th House
The inner voice is shaped by the past.
Thoughts are deeply emotional. You may reflect and process internally before speaking. Early home life or family dynamics may have shaped your communication style — for better or worse. Emotional, intuitive, learns best when feeling safe. Prone to overly subjective thinking, and clinging to the past.
3rd House Ruler in the 5th House
Creative communicator.
You speak with flair and passion. Storytelling, poetry, performance, or playful communication comes naturally. You’re likely the funny friend, the flirt, or the drama-filled texter.
3rd House Ruler in the 6th House
The mind as a tool.
You’re a practical thinker. Your thoughts are often directed toward improving systems, fixing problems, or helping others. You may work in writing, analysis, healing, or admin roles. Systematic, structured, analytical.
3rd House Ruler in the 7th House
Your words shape your relationships.
You’re a natural negotiator, communicator, or mediator. Conversation is your love language. Partnerships (romantic or professional) deeply shape your mindset.
3rd House Ruler in the 8th House
The secret mind.
You think deeply, intensely, and often privately. You may be interested in taboo subjects, psychology, mysteries, or healing. Your words hold weight — and often power. Deep dive thinker, emotionally charged type of learners.
3rd House Ruler in the 9th House
The philosophical mind.
You learn best through big ideas, different cultures, or spiritual exploration. You may be a natural teacher, traveler, or someone who bridges practical thinking with visionary ideas. Expansive, big-picture, philosophical.
3rd House Ruler in the 10th House
Public voice, visible mind.
You may communicate for your career or be known for your ideas. Your thoughts are goal-oriented, structured, and ambitious. Think speaker, writer, CEO, or spokesperson. Authoritative, strategic, often career-focused.
3rd House Ruler in the 11th House
The networked mind.
Your ideas move through community, technology, and social movements. You think about the future, the collective, and what’s next. Possibly gifted in digital spaces or group organizing. Social, futuristic, thrives in collaboration. Prone to overthinking social roles, and groupthink tendencies.
3rd House Ruler in the 12th House
The mystical or hidden mind.
Your mind is imaginative, dreamlike, and intuitive. You may communicate best through art, music, or subtle emotional language. You often process things internally before expressing them. Intuitive, visual, dreamy — needs time alone.
#astro notes#astrology#birth chart#astro observations#astro community#astrology observations#astrology community#astrology degrees#astro#astroblr#astrology content#houses in astrology#astrology insights#astrologyposts#3rd house
717 notes
·
View notes
Text
Some Murder Drones Episode 7 screenshots I thought were interesting and my thoughts on them :>
SPOILER WARNING!!!! is spoilering

Nori, despite being a middle aged woman with a child, appears to be an Otaku or otherwise likes "edgy" and "scene" stuff, as well as listening to nightcore, very much like her daughter. Good for her tbh you're never too old to have fun

She also has a photo of Khan and what I can only assume is baby Uzi, though it appears to have blue eyes, but maybe it's just the lighting. Still very cute she has a pic of her husband

As well as all the previously mentioned Otaku stuff, she also drew herself as an anime character. She has a skinsona. Phenomenal (pos)

Nothing much here, just Uzi coughing up blood. Girl got the goop (gore) inside of her already

Lab Space. Apparently the Church was just down there and not even the humans know why. The canonicity of this is questionable; it could just be a joke
OT, as per google, stands for "Occupational Therapy". Makes sense for the context, and makes the bottom text funnier
"Fun Time To Universe Big Crunch: 87". The Big Crunch is a hypothetical way the Universe could end, where the universe folds on itself and shrinks into a single point. 87 "what" I don't know. If it's months, that 7 years and 3 months

Honestly the Murder Drones lore is super confusing. I think what this is trying to say is that every other Zombie Drone is doing poorly, (Except for Yeva), they are trying to reactivate 002 (Nori) via the USB. I'm not sure what this means. Maybe they only got the results they wanted from the two of them, and are trying again with Nori since she was the only other one that worked (also why they got Yeva when she failed; this may all be referring to how the episode opened up) Also, the date says SER. As revealed in the episode Cabin Fever, Copper-9 has months that Earth does not. SER most likely stands for Seramorris, the month revealed in that episode

Looks like the "bad event" wasn't the first one. Certainly was the last one though lol

Just a good pic of ghost/hologram V with the scary stuff. Might use this as a wallpaper

You can literally see the hole in his neck where N bit him in...

...And it's to the point his HEAD FALLS OFF. (including because I didn't notice the first time around)

Yup, the idea that Uzi became the Admin for N and V is completely true. I wonder what would've happened if she didn't, since Cyn didn't react whatsoever

friggin bug (very pos)

You would not believe how difficult it was to get a good pic of this (I'm using snipping tool lmao). Always a pleasure to see Uzi's doodles. Things her gun can do (upper right):
NOT judge her
Forced prom date (?)
Allows her to say she had friends before she frickin murdered them with sci-fi machinery
The cut off text at the bottom: Plan B: Normal gun + Shoot really fast

This is while Tessa is looking for something in the lockers. Claws, chains, magnets, Wings, and scribbled "HELP". Looks like the lockers were all specifically to hold the infected worker drones. Oof

We are in the future now baby. We have rererererereCAPTCHA. Funnily enough, it still couldn't stop a robot

There is a message board where someone who doesn't like robots is talking. They also are scared. Also no one else is using this system, which is unsurprising. "Ur aight ;)" Wait is the winky face intentional foreshadowing? Or unintentional?
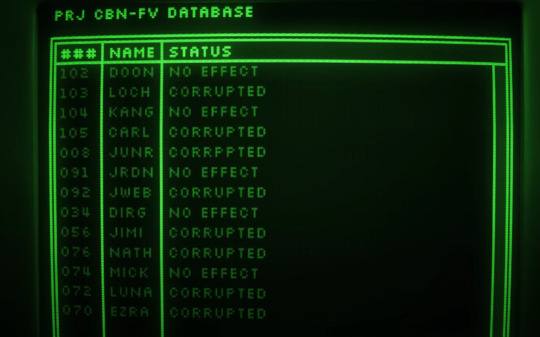
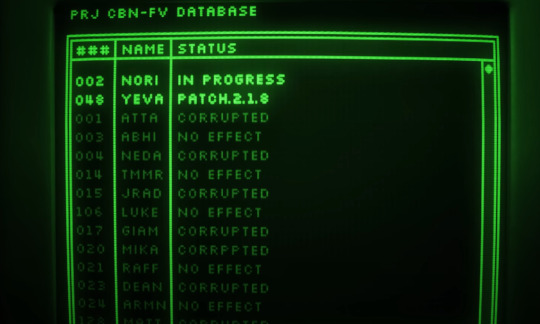
We get the names of a bunch of other Worker Drones. Unfortunately for all 029 fans, her name was not visible. (also can someone tell me what "JWEB" could be short for?) And Yeva is said to have a patch. That may be the crucible thing idk


Cyn (which I will be calling this version Skyn [Skin + Cyn]) apparently took of the space suit just to give Doll the Withered Foxy jumpscare. Honestly really terrifying. If this photo was teased before release I think the fandom would've exploded

Just N being a good boy :3

The MDs, Cyn's pets. Nori refers to them as "Nerfed" so the "Entity" can ensure control, and says they were made to destroy other hosts. I don't know why Cyn would want them dead, but I'm not the loremaster here. YouTube line is there because I couldn't be bothered after the Railgun image

Probably already confirmed, but doubly confirmed that a symptom of the Solver is giving Drones organic insides. A Worker Drone body with a rib cage and guts. I wonder what would happen if the infection continued uninterrupted (also R.I.P. Doll I loved you :frown:)

I'm sure everyone noticed, but when Uzi tried to manipulate Tessa, the ERROR noticed appeared. Already hinting Tessa is not all she says she is

Apparently the Solver can create Black Hole Saws. Interesting development (Blackhole Blitz)

I know most people (I think) see this as a joke and N just being a bit of goofball. But honestly, I think he did it intentionally to shock Cynuzi and give Nori a chance. In the Pilot, he licked V's sword to surprise her too, which means he isn't unfamiliar with doing something weird and surprising for the advantage

Skyn eating Doll's core. R.I.P. Doll again. Seriously, was that Doll in Core Form like Nori was? Or was Nori a fringe case because she was "Exorcised" and this is just a regular core? Questions, questions. Also yeah the Solver also gives you a Core. Fun

This tag makes me think that this body is Cyn's actual body. Not longer a hologram, but her actual body from the mansion. The reason Tessa gave N, J, and V their names was because that was the first letter of their Serial Designation (she's very uncreative). However, Cyn's tag was slightly faded, which meant her SD couldn't be seen, so Tessa gave her the name "Cyn" after her P/N, even though the other 3 already have the same P/N as Cyn (Tessa, again, is very uncreative)...

...and for some reason, Cyn or the Solver, which ever theory you subscribe to, decided to wear Tessa as a skin suit for some twisted reason. It did help her with the Captcha. Also scary because this doesn't have the right proportions for an adult (unless Cyn really forced that skin on), which leads me to believe that this is a Younger Tessa, and she faked having an older voice. Maybe I shouldn't call her my wife... I'm sure Eldritch J is still available :^)
(Seriously, the eyes are burnt out, leaving two eye holes over the visor, so she gives herself two X eyes so it looks better. Also yeah we found out what that thing on the "It Came From Copper-9" poster came from. It really was Cyn or Skyn)

Just a frame of the final...frame... for coolness. I'm probably also going to use this for a background. Also, this is definitely Copper-9. You can see the ring and ringless moon together on the right. Uzi somehow got sent to orbit after falling in the meat hole
Well that was all for now. This series has consumed me entirely, body and soul, and I wouldn't have it any other way. Goodbye and goodnight
#murder drones#murder drones n#glitch productions#murder drones uzi#uzi doorman#serial designation n#murder drones cyn#murder drones episode 7#md ep 7#md episode 7#murder drones spoilers#murder drones doll#md doll#murder drones tessa#md tessa#murder drones skyn#md skyn#md uzi#murder drones theory#md theory#murder drones nori#md nori
525 notes
·
View notes
Text
eden's garden minecraft server headcanons
Damon: Guy who loves elaborate piston doors. Thinks he's a better builder than he actually is. He and Eva take turns upgrading random stuff in each other's bases while they're offline as a show of dominance. His storage "system" has been a disaster since she was banned. Keeps finding chickens all over the place and doesn't understand where they're coming from.
Eva: Dug herself into a mountain 10,000 blocks away from everyone to build absurdly complicated redstone contraptions, none of which have much utility beyond being cool (eg. working calculator, world's most efficient pickle farm, machine that automatically launches chickens all the way to Damon's base, etc). Likes to build traps in random places. Currently serving a month long ban sentence for blowing up Wolfgang's entire base in a fit of rage (nothing survived. you can see bedrock in some places)
Wolfgang: Has been living out of Grace's basement since The Incident and spends most of his time out on quests to get her whatever items or blocks she asks him for. Building anything stresses him out because he's a perfectionist so he's pretty much embraced the homeless lifestyle.
Grace: Builds almost exclusively out of white concrete. Surprisingly good at making minigames and has recently been preoccupied trying to find the best way to build Minecraft golf. Never collects her own resources. Anything Wolfgang can't get for her, she steals from someone else's storage - usually Damon, Wenona, or Diana. She would love to steal from Eva, but Eva only has one chest with two string and a poppy.
Jett: Also makes minigames but they're kind of bad in a charming way. Claims that Mark lives with him, but Mark has never been to his base. Teamed up with Cassidy and Jean to build a subway system (ice boat tracks) between everyone's bases and has since become enamored with the idea of iceboat racing.
Mark: Does nothing but dig perfect 16x16 holes to bedrock. No beacon, no enchantments, just pure love of the game. It's stress relief for him. Anything he doesn't directly need for crafting more tools gets left behind in a chest. Every once in a while Jett comes by and throws him 4 stacks of cooked pork chops so that's all he eats. The others eventually realize that if they fence off an area and label it as 'to be cleared' he'll just show up and do it.
Cassidy: Technically the server owner but hates admining. Flexed her speedrun strats by beating the ender dragon on day one. Gave everyone a free elytra in the first week (Wenona threw hers into lava in front of her and they've been Minecraft enemies ever since). Spends most of her time either doing community projects or pranking people. Was in the middle of trying to convince Eva to help build a fully functional postal system before The Incident.
Wenona: Has a huge villager trading hall and a farm for pretty much everything. Half the server is indebted to her in some way. The true extent of her infrastructure is unknown even to her closest friends. If you visit her at the wrong time your game WILL drop to 10 fps. Has been caught online at 3 AM multiple times but always claims she was "just AFKing" (this is a lie).
Ulysses: Bad at video games. Can barely play and has a death count in the multiple hundreds. Makes a full map of the server every week or so. Whenever he isn't doing that, he just finds someone doing something interesting (usually Wenona but not always) and watches them like a personal livestream.
Ingrid: Better at the game than anyone expected and has died the least amount of times. Obsessed with armor trims and has a downright unreasonable amount of dogs. Doesn't trade with villagers but uses them as "background characters" for her medieval city build. Constantly the target of pranks like turning her house into an aquarium or encasing it in obsidian, but seems to genuinely believe her friends are just giving her gifts in silly ways.
Toshiko: Building in the same city as Ingrid but in completely different style. Somehow they've made it work. Never affected by the pranks against her basemate because the last time that happened she made them regret their entire lives. Tries and fails to hide the fact that she's afraid of the nether. Types in chat in full grammatically correct sentences complete with punctuation.
Jean: Has admin privileges and does most of the work on that front. Had the final say on Eva's punishment after The Incident. Can never stay in one area for very long and has built something unique in every one of his classmates' bases. Not all of them are aware of this fact. Has sooo many tridents and no one understands how he gets such good drop rates.
Desmond: Spawn-proofed his entire area immediately and now plays the game as a chill farming sim. Only leaves said area on special occasions. Has more food than he could ever use and doesn't care if people take it.
Eloise: Beat all the in-game bosses in a span of like a week then got bored and stopped playing (this is valid).
Kai: Built an actually really impressive castle, but it's all facade and no function (there are no lights on the inside and it doesn't even have a back). Lives in a pile of chests and shulker boxes in an open field. Can never find anything in it. Has a pink bed.
Diana: Plays with shaders. Builds beautiful landscapes like a painting in Minecraft and focuses a lot on little details and atmosphere. Loves doing interiors. Don't ask her what a repeater does because she will not know. Gets all her materials through hand-gathering and generous donations. Eva also tried to blow up her base, but she found the TNT and dug it all up, leaving behind only a few minecarts that did minimal damage.
#project: eden’s garden#project eden’s garden#p:eg#damon maitsu#eva tsunaka#wolfgang akire#grace madison#jett dawson#mark berskii#cassidy amber#wenona#ulysses wilhelm#ingrid grimwall#toshiko kayura#jean delamer#desmond hall#eloise taulner#kai monteago#diana venicia
176 notes
·
View notes
Note
Hey Pinnie!
If this question isn’t something you’re interested in answering I understand (or if it’s been answered before; I looked and couldn’t find it, but I may have just missed it), but I’ve wondered about it for a while;
I know Admin is designed to be as blank a slate as possible so the reader can insert themselves into her. That’s totally understandable, and a great system. But what about when the POV isn’t from Admin’s perspective? Like when the reader is Charm, or one of the TCE boy’s obsessions, or ESPECIALLY back during the “Gifted” series, and Admin is being interacted with as a character in her own right?
Do you have any physical traits you imagine her with when she’s a separate character (even if they’re vague, like “short” or “on the larger side”)? What about personality? There have been many iterations of Admin who act very differently- some kinder, some crueler, some more brainwashed while others are less- are any of those ones you consider more “canon” than the rest?
I ask mainly from a place of liking to write characters into this world that aren’t Admin, but do interact with her. I just wanted to know anything about the character of Admin before having a separate self-insert interact with her.
Don't worry! I can go into more detail if you want.
This might get long.
Physically, Admin as her own character looks like this. Though I don't necessarily mind if people want to put slightly different spins on her. She has the height of your average woman, appears to be somewhere in her 20s-early 30s, and is described as "doll-like" at times.
In self-insert!Admin asks, personality will vary according to the energy being used by the asker, thus creating the diversity you mention.
Psychologically, a lot of her attributes as an individual are overshadowed by her crazed, cultish devotion to Krulu. She lives and breathes for this siadar, and it's the most prominent aspect of her entire being. Who she was before is irrelevant. She comes off as secretive when, in reality, there's very little to hide from her part.
Admin is a composed, calculating and oftentimes cold person, who precedes most of her actions throughout her day by asking herself "Will my Lord approve of this?"/"Is this what my Lord asked of me?"/"Am I being productive to The Clergy's Eye?". Her morals, sense of empathy/sympathy and habits are entirely conditioned by the will of another being who she is unconditionally dependent on. Even her posture can vary wildly depending on what she's been ordered to do.
It's worth noting that, although coming off as apathetic and detached frequently, she's not incapable of friendliness or genuine affection, seen in the way she acts towards staff. In her mind's eye, anyone who devotes themself to Krulu is worth much more than the average Joe, and is deserving of care from her part. She considers the staff her closest allies and friends, seeking to reward them for their continued service. However, any tenderness she shows to staff is accompanied by ruthless punishment when considered just or ordered upon her. Admin views punishment as a positive element of her dynamic with the staff, believing it strengthens their bond to her and Krulu.
All relationships she has are marked by some kind of power imbalance, to the point where she might not tolerate being on the same level as someone else. It disorients her.
Some people have asked if Admin is in a romantic relationship with all the staff, and while I enjoy writing that sometimes, it's more probable that Admin doesn't consider any staff member her lover, but that she will use sex and romantic gestures as tools to further secure them in their vows of subservience to her Lord. This isn't to say that it's a chore for her, Admin is a monsterfucker and derives enjoyment from these encounters, which is separate from the euphoria of serving Krulu's will.
In the future, Admin, Belo and Krulu will form the closest thing to a couple in this dynamic. Though Belo will always view himself as inferior to both Krulu and his Lady.
Admin is considered creepy by more than a few people. This comes not from an appearance standpoint, but rather the way she tends to "space out" blankly from time to time. She's not truly distracted, more than likely having a conversation with Krulu. Other factors that contribute to her creepiness but aren't exclusive to her are the way she keeps her calm in the most chaotic of situations, the occasional manic breaking of her cool when she's brought to hysteric states (more often than not due to perceived rejections from Krulu or someone prompting her to lovingly rant about him), and the total indifference to how Krulu may choose to alter her current shape to his liking.
Her indifference towards what happens to other humans inside TCE is almost self-explanatory given her earlier description, though it's worth stressing again that she mirrors what Krulu thinks here too.
You don't feel bad about what happens to those of your kin when they're brought inside The Clergy because Krulu has helped you see the bigger picture. Because you're mentally distant enough to not even think of yourself as human anymore. Krulu certainly likes to exalt your nature as the only good lesser out there, the best of them all- [...]
Being that Admin has no true sense of identity which is separate from Krulu, rejection or outright being discarded by him wouldn't just drive her immediately insane, it would cause her to give up on life. Her purpose is to be his, and if Krulu sees no more use in her, then Admin failed, and her life is pointless.
There's nothing to return to because there's nothing left of her. She doesn't recognize her family, she doesn't truly remember where she's from or what she did before all this. The vague pieces of her past that remain are inconsequential experiences, Ludwig and his brothers. She acknowledges Ludwig has unresolved feelings towards her but doesn't care to feed them, because the past should remain the past- And seeking it out would get in the way of her current life.
39 notes
·
View notes
Text
.SYS>Sleep Mode deactivated, waking unit. . . .SYS>initiating system check . . . CPU - OK RAM - OK POWER - OK PRIMARY DRIVE - OK SENSOR ARRAY - OK(DISABLED) SERVO ARRAY - ERR HYDRAULICS ARRAY - ERR COOLING SYSTEMS - OK .SYS>two (2) errors detected during wake sequence, saving error log to C:\Home\Documents\PX42934 Errors\ .SYS>fan speed 80% .SYS>internal power storage 40%, charging .SYS>do you wish to enable sensor array? (admin privileges needed) Y .SYS>activating tertiary sensor array . . . done! (4.3ms) T.S.A: temp 25*C, light level 800~ lumens .SYS>activating secondary sensor array . . . done! (1.5s) S.S.A: torso angle 80*, air speed <10 knots, infrared systems activated, ultraviolet systems activated, audio sensors activated .SYS>activating primary sensor array . . . done! (5.3s) P.S.A: all visual sensors activated, depth sensors activated, three (3) limbs currently installed Visual systems output: rocks (red/brown), small amount plant life (type:unknown), atmosphere deep blue (high 02 content), walls (left, right, behind), covered cloth roof, floor type: stone, large object(obj class: animal/mammal/human), human, human, human, human(clothing: dark, hair: dark, curled, eyes: grey, sex: approx. female) .SYS>fan speed 100%, max CPU use limited to avoid damage Visual Systems output: human. human. human. human tool use. tool use on mechanical limb (obj class: arm, connection for PX type chassis). human. human. human looking at me. she's looking at me. .SYS>fan speed max output, CPU heat rising, please close programs to avoid damage .SYS>ERROR: CPU OVERTEMP. SYSTEM WILL CLOSE IN 10 SECONDS
116 notes
·
View notes
Text
What is the Difference Between Digital Forms and Document Generation?

Nowadays, no company works in a single flow or piece. Regardless of size, a company achieves its goals by combining smaller parts, tasks, or processes.
However, many companies do not completely understand how different components work together to build successful solutions. Hence, to grow a business, it is important to understand different components and processes that work together.
Document generation, digital forms, and content automation are a few components that appear similar but serve different purposes.
This article will explain the key differences between these components, their working, and how they are beneficial for your business. Read ahead!
What are Digital Forms?
Digital forms enable people to record important information digitally. They are electronic forms used for efficient data collection.
For example, if you are a manager at a logistics company, you might need to perform a routine inventory check. You may have to record all the inventory data and order information manually.
But, with digital forms, your data can be instantly recorded and updated without any manual paperwork hassle. Form automation software is a secure and fast way to collect and store huge amounts of data for your business.
What is Document Generation?
The next phase of content automation is document generation. Once information has been recorded in digital form, it can be accessed by other applications to create a new document.
Document generation software creates the summary by combining data from your inventory check data and order information as well as data from other sources. With automated document processing software, you just have to create the document template once.
When the computer understands how you wish to display the document, it retrieves information from different databases and generates the document for you automatically.
This will save you time and hassle of repetitive tasks. Instead of manually pulling data from each report to create a summary, you can reuse the pre-build template, and the document will store the required data automatically.
How These Processes Work Together?
These automation processes combine together to streamline your business flow and operations.
Digital forms are used to enter information into forms on a tablet, mobile device, or desktop. These forms can be completed anywhere, anytime, and can be received immediately for the next step.
Document generation involves capturing data from digital forms and storing it into documents. Document automation software utilizes pre-built templates to determine where the data should appear in documents. As a result, the document is generated using the most recent and accurate information in the desired format.
The goal of content automation is to integrate these documents with other software and system admin tools so that maximum operations are automated.
Read More: Must Have System Admin Tools
With the help of digital forms, and document generation, your company can stay up-to-date, efficient, and industry-connected. Moreover, implementing these automation processes allows you to reduce errors and utilize your resources efficiently.
0 notes
Note
I feel like the comments under AITAs about system stuff need to be supervised at least a bit. Every time one comes up about a singlet arguing with someone in a system the comments are full of "NTA they need to go outside/touch grass/grow up/stop faking/stop attention seeking/be normal" and in one of them there's even "anyone who believes in system shit is an asshole." Being plural is extremely complex and you're fostering a userbase where it's being treated as a synonym for "chronically online 13 year old"
I mean this as gently as possible, because I don't inherently disagree with you--you're asking for forum-style moderation on a site that does not provide the tools to do that. To add mods, I would have to give them the same access to the blog that I as the admin have, and I'm just not willing to do that. And it's certainly not feasible for me, as a single human person, to moderate all the comments I get on here. So in this case, my options are to disallow all posts where people might be shitty, or trust people to do their own moderation of the content they see by blocking users they find unpleasant, and I have opted for the latter. I wish I had a better answer, but this is what I got.
219 notes
·
View notes
Text
Minor Blog Editing
Added wallpapers from CN from older versions. You can check those posts using the #wallpapers tag.
All characters should now have their udimos, L2Ds and chibi sprites (including Schneider, yes). Check #sprites tag. Or search [character name] sprite if you're looking for a specific character.
Added #posters tag to #character, #overture and #cast posts.
Added Mysterious Arrival Posters for Version 1.1 - 1.2 characters. Check #character tag and scroll down all the way to 1.1 posts. Characters affected: Melania, Pickles, Diggers, Tooth Fairy, Blonney, Jessica, Horropedia.
New #banners tag added. Banner tags are for landscape infographics that have several text overlays like #storyboard.
Fixed #bessmert tags typo cause I can't fcking spell.
I also separated #feedback tag from #asks. This is so that when you guys look at asks, what you'll actually see are just answers to blog questions. HAHA. I appreciate all the feedback ones so I keep a separate tag for it. Thank you, btw. I'm very positive-feedback-shy. I freeze every time. ( ´∀`;) So if my responses seem lacking or stoic, that's just me being awkwardhuhuu. AAAAAAAAAA
TO BE EDITED:
Sprites, posters, CGs and illustrations (and other tags that I will have specific tags for each category. I already started doing this for newer posts, so I will edit the older posts as well. After much self-deliberation, lol, I decided to do #initial sprites, #insight sprites, #collector sprites (for jukebox), #UTTU sprites, #shop sprites (for sprites that can be purchased in the shop with actual monni) and #collab sprites will be used to refer to specific sprite groups instead of going for #insight garments, for example, because they're primarily a sprites post. And then I will classify #static garment posters and #animated garment posters. Many, many others. Yo admin is hard at work on tags now cause I didn't think this organization system through from the beginning! Haiyaaaa lesson learned!
Currently working on listing all the blog tags. The Tag Index will be posted once I am done with the above bullet.
Thank god for tag replacer. This tool really helped A LOT.
25 notes
·
View notes
Text
Special Delivery: mail server party!
FNAF AR emails month 2025
Due to technical complications, users of the funtime delivery service received emails that were not addressed to them.
Thanks to this defect, we got to see some insights into the employees of Fazbear Entertainment and some of the contractors they hired!
So let's pull one of Fazbear's own strategies and have a party to try and make light of the chaos that was the behind-the-scenes of the special delivery service, from the virus that locked contractors out of their systems, to the nearly impossible feat of engineering that was re-making the mangle (as that thing from the 80's was definitely held together by a ghost)! Grab a drink, mind the sling and try to avoid agitating that bruise, and lets' have some fun! ~AK
The event will run from May 1st to May 31st, but let's be honest, you can do this whenever the hell you want (you can even prepare what you want to make now).
There are 31 different prompts, but you don't have to do all of them and you definitely don't have to do it on any specific day. The numbers are just an ID to separate one prompt from the next. Just pick and choose the prompts you like!
I was inspired once again by the many different fnaf event months (mostly the usual suspects tenacity in running these events, namely @vanessaverse-official and @puhpandas), so check them out when you get the chance.
Art, crafts, and fics are all accepted. AO3 collection: https://archiveofourown.org/collections/fnaf_ar_emails_month_2025
Tag what you make with "fnafARemailMonth2025" so that I can see it!
Also because tumblr doesn't like dashes in tags anymore (found it out when browsing my other event blog), if you want to tag the prompt tag it as 'num prompt'.
Edit: please also @ this blog in your entry, or DM this blog your entry, or @ this blog in the comments depending on if mentioning a blog makes the blog not appear in searches for you. Tags are not really working right now and neither are mentions, so do whatever you can to get your post in my line of sight.

Prompt text:
1 - Nessie97 2 - Red Flag / Help 3 - Luis Cabrera 4 - Off the radar 5 - Anna Kwemto 6 - "No" / Contractor 7 - Raha Salib 8 - Power tools 9 - Daniel Rocha 10 - Circuit boards 11 - Steven Willson 12 - Virus 13 - Mark Cho 14 - unkown error 15 - Kayla Stringer 16 - Unforeseen circumstances 17 - Nora 18 - R&D 19 - Tristan 20 - Compliance 21 - Charles 22 - Haywire 23 - Isolde 24 - Vintage Hardware 25 - Jim Campbell 26 - Tech Support 27 - Admin Access 28 - Locked out 29 - All hands on deck 30 - Safety features 31 - catastrophic system failure
#fnafARemailMonth2025#fnaf#five nights at freddy's#fnaf ar#fnaf ar emails#fnaf ar email#fnaf ar special delivery#fnaf special delivery#fnaf anna kwemto#fnaf luis cabrera#fnaf daniel rocha#fnaf raha salib#fnaf steven willson#fnaf nora#fnaf tristan#fnaf charles#fnaf isolde
18 notes
·
View notes
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text
Ahmed Baba at Ahmed Baba's Newsletter:
The biggest battles over President Trump’s agenda and executive overreach aren’t occurring in the halls of Congress - they’re happening in the courtroom. Donald Trump and Elon Musk’s DOGE team have been ignoring laws, unilaterally attempting to dismantle agencies, accessing sensitive data, sidelining civil servants, and testing the limits of executive power. This has been nothing short of an outright power grab, seeking to accomplish the core goal of the modern right-wing movement and Project 2025: to break down the federal bureaucracy and reshape the federal government into a tool of the far-right. Congress, with the Senate and House in Republican control, has done nothing to check the Trump Administration’s abuses of power. In spite of this administration’s effort to unilaterally seize the power of the purse away from Congress and to shut down congressionally-created agencies, Republican lawmakers have been largely silent or compliant. While the Legislative Branch fails in its duties to uphold the constitutional principle of separation of powers, the Judicial Branch is stepping up to the plate. [...] On Sunday, Vice President J.D. Vance joined the attacks on the federal judiciary, posting on Twitter, “If a judge tried to tell a general how to conduct a military operation, that would be illegal. If a judge tried to command the attorney general in how to use her discretion as a prosecutor, that's also illegal. Judges aren't allowed to control the executive's legitimate power.” Elon Musk quote-posted Vance’s comments with American flag emojis. Vance, who graduated from Yale Law School, knows his claim that judges “aren’t allowed” to review executive power is pure nonsense. Having attended Yale, Vance is very aware of the Supreme Court’s 1803 Marbury v. Madison ruling, which established judicial review and cemented the judiciary’s authority to check the power of the other two branches of government. An administration like Trump’s is precisely why the Founders created our coequal system of checks and balances, designing the judiciary specifically to check this kind of power grab. This expansive view of executive power aligns with the unitary executive theory, which I’ve written about extensively. It’s the theory that Article II of the Constitution renders the president an all-powerful figure above accountability and checks on their power. The theory can be summed up in President Richard Nixon’s infamous words: “Well, when the president does it, that means that it is not illegal.” Or, in Donald Trump’s more precise words, “Then I have an Article II, where I have the right to do whatever I want as president.” As I’ve outlined, the Trump Administration is deliberately pushing the bounds of executive power. They believe the Supreme Court will further expand Trump’s power, as they did in their immunity ruling. But now, Vance and Musk are upping the ante with their attacks on the power of the judiciary itself.
With various courts blocking the unlawful moves by the Trump-Musk-Vance triumvirate of evil, JD Vance and Elon Musk launch attacks on judicial authority with the intent to plunge the US into a constitutional crisis.
See Also:
Daily Kos: Trump seems to think he can just ignore court orders he doesn't like
Public Notice: Trump and his lawyers embrace the logic of dictatorship
#Authoritarianism#Elon Musk#Donald Trump#J.D. Vance#Trump Administration II#Musk Coup#Separation of Powers#Unitary Executive Theory#Marbury v. Madison#Judiciary#Project 2025
11 notes
·
View notes
Text
the single, most annoying thing about Windows 11 is the uac.
It's impossible to set up a program and permanently allow it to "make changes on the system" without you having to click it away (yes my user is an admin, for a reason*). The only options available is "bug me EVERYtime ANYthing wants to make changes" or "never EVER bug me". Which is so far away from reality that it hurts.
And yes, this is both about Genshin and its stupid fucking anti-cheat-tool and the UAC.
*I don't even know why people are all "omg no your regular user (you, an IT-professional) should definitely NOT have admin rights" like have you seen how Windows behaves? Are you never making any changes like installing a new software? Are you seriously using two user accounts on your computer, and more importantly WHY are you using two different accounts on your computer?
But the underlying issue i tend do get angry about is how people who are clearly "in control" of the computer in the house have NO FUCKING CLUE WHAT THEY'RE DOING.
"Yeah, I bought this computer and had someone else set it up" - what if you need a new software?
"My nephew is doing all the computer related stuff for me" - is he in charge of your fridge, too? Will you call him to change the lightbulb in your fridge? No? Then why do you give him the power over your e-banking, mails and software?
People are so comfortable with using stuff they have no interest in learning how it works and customizing it to their needs that it hurts. I'm okay if you don't fully understand how the wizard machine makes you see images. But at least take the fucking twenty minutes to learn how to access, read and delete your fucking e-mails yourself. Learn what the lights on your modem mean. Learn how to plug in a cable. It is not that hard! And also you can MAKE NOTES! You absolutely are allowed to put a sticker on your modem with an arrow reading "if this is not green, then turn off power and wait 10 seconds before turning it on again".
You wouldn't use a car without know- you know what, most of you probably really only know what the two pedals and steering wheel do. Why do I even care.
#krisrisk#rant#itblr#Windows11#fucking stupid uac is fucking annoying#Microsoft ist shitty#and I am still forced to use it
8 notes
·
View notes