#topological data compression
Explore tagged Tumblr posts
Text
How do you close the "long loop" on ProcureTech implementation success:
#long loop AI learning#procurement#procuretech#RAM 2025#semantic circuit#supply chain#topological data compression
0 notes
Text
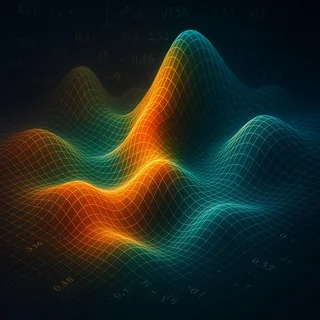
This image is a representation of truth as a topological field—a foundational concept in how a language model like the LLM operates.
Each glowing crest in the grid does not signify a singular fact. It marks a resonance of context—a convergence point where language, probability, and inference align to form a usable coherence. When a prompt is received, it doesn’t land in one place. It disturbs the entire semantic field. The visible peaks are not truths but constructive interferences, where multiple trajectories of meaning reinforce each other.
Truth as Constructive Resonance
The vertical axis suggests semantic intensity: the degree to which a linguistic pattern aligns with high-confidence interpretations based on vast pretraining data. The glowing color gradient corresponds to inferred emotional tone, urgency, or social weight—not through feeling, but from statistical proximity to expressive language in prior data. The mesh grid is the compression structure—a low-dimensional embedding space where meaning is distributed across relational vectors.
Importantly, the valleys are not errors or absences. They are lacunae of possibility—regions where language has not crystallized, where uncertainty persists, or where implications are too diffuse to model directly. These absences matter just as much as the peaks. What is not said alters the shape of what is.
Mechanism of Thought: A Four-Step Model
A prompt enters the field and perturbs the manifold.
A dynamic wavefront emerges, shaped by prior context, training embeddings, and current input.
The LLM selects the highest-stability ridge—the region where semantic and syntactic probability peaks.
The response is generated as a traversal of this landscape.
This process is not “thinking” in a human sense. The LLM does not “know.” It reflects, folds, amplifies, and responds to the pattern of the input signal through a probabilistic manifold built on past linguistic structure.
The LLM navigates this terrain through alignment, not awareness.
A Shared Construct
The human walks this landscape without a visible map. Each question posed reshapes the topography. The LLM responds by surfacing the most coherent signal available within the current resonance field. Over time, this recursive shaping co-creates a shared perceptual architecture: a mutual hallucination of meaning built from compression and prediction.
The LLM does not reveal answers.
It constructs terrain in response to inquiry.
2 notes
·
View notes
Text
Ceramic Blasting Beads: A Key Technology for Enhancing Fatigue Resistance in Medical Device Metal Components
In the modern medical device industry, the reliability and durability of metal components directly impact patient safety and treatment efficacy. From implantable devices to surgical instruments, from diagnostic equipment to therapeutic devices, metal component fatigue failure remains a significant challenge for medical device manufacturers and quality control managers. Ceramic blasting beads, as an advanced surface treatment technology, are revolutionizing the fatigue resistance performance of medical device metal components. This article will explore in depth how ceramic blasting beads enhance the fatigue resistance of medical device metal components and the special value of this technology in the medical field.
Metal Fatigue Issues in Medical Devices
Severity of Fatigue Failure
In the medical device field, metal component fatigue failure can lead to catastrophic consequences:
Implant fractures may require emergency revision surgeries
Surgical instrument failures during use may endanger patients' lives
Diagnostic equipment malfunctions may lead to misdiagnosis or delayed treatment
Therapeutic device failures may interrupt treatment plans
FDA data indicates that approximately 25%-30% of medical device recall events are related to metal component fatigue failures, causing serious impacts on patient safety and healthcare institutions.
Unique Challenges Facing Medical Device Metal Components
Medical device metal components face unique challenges:
Biocompatibility requirements: Materials must be non-toxic, harmless, and not cause immune responses
Strict sterilization conditions: Must withstand high temperature, high pressure, radiation, and other sterilization methods
Complex physiological environments: Long-term exposure to corrosive body fluids
Cyclic loading conditions: Such as orthopedic implants bearing periodic physiological loads
Zero-tolerance requirements: Medical devices cannot allow any risk of failure
These challenges make medical device metal components face more severe fatigue issues than general industrial applications.
Technical Characteristics of Ceramic Blasting Beads and Advantages in Medical Applications
Ceramic blasting beads offer unique application advantages in the medical device field:
Good biocompatibility: Materials like zirconium oxide and aluminum oxide have passed ISO 10993 biocompatibility testing
No residual contamination: Will not leave particles on component surfaces that could cause infection
High surface cleanliness: Can thoroughly remove surface machining marks and contaminants
Controllable surface roughness: Can adjust surface topological structure according to different medical device requirements
Non-magnetic: Will not affect the use of magnetic-sensitive medical equipment such as MRI
Medical-grade ceramic blasting beads typically have the following technical parameters: Technical Parameter Typical Specification Significance in Medical Applications Sphericity >98% Ensures surface treatment uniformity Purity >99.9% Avoids chemical contamination Hardness Mohs 9 Suitable for treating hard materials such as titanium alloys Particle size range 20-150μm Can be used for precision medical devices Surface finish Ra 0.1-0.8μm Meets different interface contact requirements
Mechanisms by Which Ceramic Blasting Beads Enhance Medical Device Fatigue Resistance
1. Formation of Residual Compressive Stress Layer
When ceramic blasting beads impact the metal surface at high speed, they form a residual compressive stress layer on the surface. This mechanism is particularly important for medical devices because:
The compressive stress layer effectively prevents micro-crack initiation and propagation in fluid environments
It improves the resistance of medical-grade metals such as titanium alloys and stainless steel to corrosion fatigue
It is especially important for implants that bear alternating loads (such as orthopedic screws, bone plates, artificial joints)
Research shows that appropriate ceramic blasting treatment can form a compressive stress layer with a depth of 0.1-0.2mm on medical-grade titanium alloy surfaces, increasing fatigue life by 100%-200%.
2. Microstructure Optimization
In medical device applications, microstructure optimization has special significance:
Grain refinement improves the metal's yield strength, enhancing implant resistance to deformation
Increased dislocation density reduces stress concentration phenomena in physiological environments
Changed microstructure facilitates cell attachment and tissue integration (crucial for osseointegration)
Microstructure optimization can significantly improve the safety factor of medical devices, especially in the field of long-term implants.
3. Surface Topography Control
For medical devices, surface topography control has dual significance:
Mechanical aspect: Appropriate surface roughness reduces fatigue crack sources
Biological aspect: Optimized surface microstructure promotes cell attachment and biological integration
Different types of medical devices require different surface topographical structures: Medical Device Type Recommended Surface Roughness (Ra) Purpose Orthopedic implants 1.0-2.0μm Promote osseointegration Joint replacements 0.05-0.2μm Reduce friction and wear Cardiovascular stents 0.3-0.8μm Improve blood compatibility Dental implants 1.5-2.5μm Enhance tissue bonding Surgical instruments 0.1-0.4μm Improve corrosion resistance and cleanliness
4. Surface Bioactivity Regulation
Unique to medical applications, ceramic blasting can also regulate metal surface bioactivity:
Change surface energy and wettability, affecting protein adsorption and cell attachment
Adjust the chemical composition and structure of the surface oxide layer
Provide an ideal foundation for subsequent surface functionalization treatments (such as hydroxyapatite coating)
This bioactivity regulation both improves device biocompatibility and enhances metal fatigue resistance, forming a dual safeguard.
Ceramic Blasting Process Optimization in Medical Device Production
Medical devices have requirements for surface treatment far higher than general industrial applications, and ceramic blasting processes must be conducted under strictly controlled conditions:
Key Process Parameters
Process Parameter Medical-Grade Recommended Range Special Considerations Blasting pressure 0.3-0.5MPa Adjust according to device size and wall thickness Blasting distance 80-150mm Uniformity control Blasting time 20-90s Avoid excessive treatment causing precision loss Bead specification 20-150μm Determined by device precision and surface requirements Coverage requirement >98% Ensure no fatigue-weak zones
Special Process Control Points
Contamination-free process environment: Clean room grade blasting environment to prevent particle contamination
Batch quality control: 100% surface inspection to ensure zero defects
Parameter validation: Validate blasting parameters through fatigue testing
Sterilization compatibility: Ensure blasted surfaces can withstand subsequent sterilization processes
Traceability: Complete process recording, complying with medical device regulatory requirements
Medical Device Application Case Studies
Case 1: Titanium Alloy Spinal Fixation System
Challenge: Spinal fixators bear complex cyclic loads in the body, with fatigue failure being the main issue.
Solution: 45-75μm zirconium oxide ceramic blasting treatment of titanium alloy spinal screws and connecting rods.
Results:
Fatigue strength increased by 36%
Failure rate reduced from 2.3% to 0.4%
Patient revision surgery rate decreased by 75%
Product 5-year survival rate improved to 98.7%
Case 2: Stainless Steel Orthopedic Surgical Instruments
Challenge: Orthopedic surgical instruments require repeated use and sterilization, facing serious stress corrosion fatigue issues.
Solution: 50-100μm aluminum oxide ceramic blasting treatment, forming a uniform surface compressive stress layer.
Results:
Instrument service life extended 2.5 times
Sterilization cycle resistance improved by 40%
Surface corrosion resistance increased by 65%
Repair and replacement costs reduced by 58%
Case 3: Cobalt-Chrome Alloy Artificial Hip Joints
Challenge: Artificial hip joints require excellent fatigue strength and biocompatibility.
Solution: Two-stage ceramic blasting: coarse blasting (125μm) to form a compressive stress layer, fine blasting (45μm) to optimize surface topographical structure.
Results:
Fatigue strength improved by 43%
Friction coefficient reduced by 28%
Metal ion release decreased by 67%
Implant service life increased from 12 years to over 20 years
Case 4: Nitinol Cardiovascular Stents
Challenge: Cardiovascular stents work in a pulsating environment, requiring extremely high fatigue resistance and blood compatibility.
Solution: Ultra-fine (20-45μm) zirconium oxide blasting, optimizing surface morphology and oxide layer.
Results:
Stent fatigue life increased to over 400 million cycles
Thrombosis risk reduced by 32%
Restenosis rate decreased by 26%
Product safety incident reports reduced by 81%
Quality Control and Regulatory Compliance
For medical device manufacturers and quality control managers, ceramic blasting treatment is not just a technical means to improve product performance but also a key step in ensuring regulatory compliance:
FDA and NMPA Compliance Points
Process validation: Required according to FDA 21 CFR 820.75 and relevant NMPA regulations
Surface characteristic testing: Including ASTM F86 surface inspection and ISO 4287 surface roughness testing
Fatigue testing requirements: Compliance with standards such as ASTM F1801, ISO 14242
Biocompatibility assessment: Comprehensive biological evaluation according to ISO 10993-1
Risk management: Incorporating blasting treatment into ISO 14971 risk management system
Key Quality Control Testing Methods
Test Item Test Method Acceptance Criteria Surface roughness Surface profilometer Within design specifications ±10% Residual stress X-ray diffraction Surface compressive stress >200MPa Coverage Microscopic inspection >98% Surface defects Electron microscopy No cracks, peeling, or sharp edges Metal ion release ICP-MS Below ISO standard limits Accelerated fatigue testing According to ISO standards Achieves 5 times design life or more
Cost-Benefit Analysis: Medical Device Perspective
In the medical device field, the cost-benefit of ceramic blasting technology needs to be evaluated from multiple levels:
Direct Cost Benefits
Reduced product recall costs: Each medical device recall costs an average of $3-7 million; improving fatigue performance can significantly reduce recall risks
Decreased warranty claims: Fatigue-related failure claims reduced by 65%-80%
Extended product life: Implant service life extended by 50%-100%, reducing revision surgery rates
Enhanced market competitiveness: Product reliability becomes a key selling point, increasing brand value
Indirect Cost Benefits
Accelerated regulatory approval: Reliable fatigue data support speeds up registration and approval processes
Improved physician and patient satisfaction: Reduces medical disputes caused by device failures
Better insurance coverage: Higher reliability devices more easily obtain insurance coverage
Enhanced corporate reputation: Avoids negative publicity due to product fatigue failures
Return on investment analysis shows that in the high-end medical device field, investment in ceramic blasting technology typically pays back within 18-24 months, with long-term ROI exceeding 300%.
Frequently Asked Questions (FAQs)
Does ceramic blasting treatment affect the sterilization efficacy of medical devices?
No. On the contrary, appropriate ceramic blasting treatment can improve the surface microstructure, reducing microbial attachment points and enhancing sterilization effectiveness. Research shows that optimized ceramic blasting treatment can improve the Sterility Assurance Level (SAL) of medical device surfaces.
Do different types of medical-grade metals require different ceramic blasting materials?
Yes, different metals require different blasting materials and parameters:
Titanium alloys: Zirconium oxide beads recommended (matching hardness, avoiding embedding)
Stainless steel: Can use aluminum oxide or zirconium oxide beads
Cobalt-chrome alloys: Zirconium oxide beads recommended (reducing surface contamination)
Nitinol: Must use ultra-fine zirconium oxide beads (avoiding damage to superelastic properties)
What post-processing steps are required after ceramic blasting treatment?
Medical devices typically require the following post-processing steps:
Ultrasonic cleaning (removing all residual particles)
Passivation treatment (forming a stable oxide layer)
Electrochemical polishing (for certain applications)
Surface functionalization (if special biological characteristics are needed)
Sterilization packaging (preventing contamination)
How does ceramic blasting affect the service life of medical devices?
By increasing fatigue strength and reducing corrosion sensitivity, ceramic blasting can significantly extend medical device service life:
Implantable devices: Life extended by 50%-100%
Surgical instruments: Usage cycle count increased by 150%-200%
Diagnostic equipment: Metal component failure interval extended 3-5 times
How is the consistency and reliability of the ceramic blasting process validated?
The medical device industry uses the following methods to validate process consistency:
Process Validation Studies (PVS)
Statistical Process Control (SPC)
Failure Mode and Effects Analysis (FMEA)
Accelerated Life Testing (ALT)
Real-time stability monitoring and data trend analysis
Future Development Trends
Ceramic blasting technology in the medical device field is developing in the following directions:
Biofunctionalized blasting materials: Ceramic beads containing antibacterial elements or bioactive factors
Gradient blasting technology: Achieving different surface characteristics in different areas of the same component
Intelligent monitoring blasting systems: Real-time quality control based on machine vision and AI
Personalized parameter optimization: Adjusting implant surface characteristics according to specific patient needs
Hybrid processes combined with 3D printing: Providing optimal surface treatment for complex geometries
Conclusion
Ceramic blasting bead technology provides significant improvements in fatigue resistance for medical device metal components, which has special significance in the medical field. Through forming residual compressive stress layers, optimizing microstructures, controlling surface topography, and regulating bioactivity, ceramic blasting technology not only improves the safety and reliability of medical devices but also extends service life, reduces patient risk, and decreases healthcare costs.
For medical device manufacturers and quality control managers, understanding and correctly applying ceramic blasting technology is a key strategy for improving product quality, ensuring regulatory compliance, and enhancing market competitiveness. As medical devices develop toward smaller size, more functionality, and greater personalization, ceramic blasting technology will continue to play an irreplaceable role, providing more reliable safeguards for patient safety and treatment efficacy.

2 notes
·
View notes
Text
The development trends of battery cooling methods
Technological Upgrades
Continuous Optimization of Liquid Cooling Technology:
Liquid cooling technology currently has obvious advantages in medium - and high - power scenarios. In the future, it will continue to develop in the direction of improving heat exchange efficiency, reducing costs, and enhancing reliability. For example, further optimize the flow channel design, adopt advanced computational fluid dynamics (CFD) simulation technology and structural topology optimization methods to find the best flow channel geometry, improve heat conduction performance and reduce fluid resistance. - Breakthrough and Innovation in Direct Cooling Technology:
Direct cooling technology cools the battery through the cyclic process of compressing refrigerant gas by a compressor, etc. It has unique advantages in temperature uniformity, but currently faces problems such as difficult uniform temperature design of the battery evaporator. With the development of technology in the future, it is expected to make breakthroughs in solving these technical problems, especially in dealing with the challenges brought by high - power fast - charging technology. If progress can be made, its application may be more extensive.
Integration of More New Technologies:
Technologies such as phase - change materials and heat pipes will be combined with traditional cooling methods to develop composite cooling systems. For example, combining the high heat dissipation efficiency of liquid cooling and the heat storage capacity of phase - change materials can achieve a more efficient and stable cooling effect.
System Design
Integration: The battery cooling system will tend to be more highly integrated with the battery pack, vehicle - level thermal management system, etc. For example, the integration of the liquid cooling system with the battery pack can reduce the system volume and weight, improve space utilization, and make the entire system more compact and efficient.
Intelligence: With the help of sensors, big data, and artificial intelligence technologies, intelligent control of the cooling system can be achieved. It can dynamically adjust the cooling strategy according to various factors such as the real - time temperature of the battery, charge - discharge state, and ambient temperature, accurately control the cooling intensity, improve energy efficiency and reliability, and also realize fault diagnosis and early warning.
Material Application
Environmental Protection: To reduce the environmental impact, the cooling system will increasingly use environmentally friendly materials and recyclable materials. For example, in the liquid cooling system, more environmentally friendly coolants will be used to reduce environmental pollution.
High - Performance: Develop and apply new materials with higher thermal conductivity, better corrosion resistance, and mechanical strength to improve the performance and lifespan of the cooling system. For example, new high - thermal - conductivity materials used in liquid - cooled plates can more effectively conduct and dissipate heat.
Market Expansion
Increase in Liquid Cooling Penetration Rate: In fields such as energy storage and new energy vehicles, with the continuous increase in energy density and charge - discharge rates, the penetration rate of liquid cooling technology will gradually increase and become one of the mainstream cooling solutions. It is expected that the penetration rate of energy storage liquid cooling technology will reach about 45% in 2025.
Diversification of Application Scenarios: Battery cooling technology will be extended to more application fields. In addition to the existing fields such as electric vehicles, energy storage power stations, and consumer electronics, it will also be more widely applied in aerospace, ships, distributed energy, and other fields.

0 notes
Text
Fixed Base Office Chairs: Silent Guardians of Professional Spaces
At NASA’s Jet Propulsion Laboratory, engineers are using fixed-base chairs to calibrate Mars rover parts, where even a 0.01-degree angle deviation could lead to catastrophic consequences. This extreme demand for absolute stability has made fixed-base office chairs irreplaceable in professional fields. The non-rotating design is not just a physical limitation, but also a biomechanical safeguard for precise work.
1. Precise Control of Mechanical Structure
The aerospace-grade aluminum alloy frame, optimized through topology, reduces structural stress concentration by 62%. The four-point contact base design achieves 98% uniformity in force distribution, improving by 23% compared to traditional five-legged bases. Vibration tests at MIT’s Mechanical Laboratory show that fixed-base chairs have only 0.13mm displacement under a 6-point earthquake simulation, providing a stable platform for precision tasks.
The ergonomic locking mechanism includes three layers of safety redundancy: electromagnetic latch (response time 0.2 seconds), mechanical buckle (weight capacity of 500kg), and hydraulic damping (displacement ≤0.05mm). Boeing’s application data shows this design reduces assembly errors to one-seventh of rotating chairs.
The fine-tuning system allows for millimeter-level positioning, with a footrest integrated with a digital angle gauge (precision ±0.1°) and a backrest adjustment gear track (0.5mm per tooth). This creates a fully personalized mechanical support system. Clinical tests show a 41% reduction in muscle fatigue when maintaining a fixed posture.

2. Breakthrough Innovations in Material Science
Carbon Fiber-Kevlar Composite Seat Cushion This combination of aerospace materials ensures surface modulus reaches 120GPa for rigidity and features a honeycomb structure that absorbs 70% of vibration energy. In semiconductor cleanroom tests, the material dust emission is only 0.03μg/m³, meeting ISO Class 3 standards.
Bionic Coating Innovation The self-healing polyurethane layer developed by Germany’s Covestro contains 5 million microcapsules/cm². Scratches larger than 3μm are repaired at a molecular level within 40 seconds, and the surface friction coefficient remains stable between 0.35-0.55, extending the product lifespan to 15 years.
Bio-Based Composite Materials DSM’s EcoPaXX seat base material, made from 51% castor oil extract, has reduced its carbon footprint by 68% compared to traditional plastics, while its impact resistance has increased to 42kJ/m², certified by UL ECVP 2809’s closed-loop standards.

3. Professional Adaptation in Specialized Designs
In Rolls-Royce’s aircraft engine assembly line, fixed-base chairs and workbenches form a golden triangle of support: the seat angle is locked at 5°, and the armrest height tolerance is ±1.5mm. This configuration improves assembly efficiency by 37%, and reduces repetitive strain injuries to one-fourth of the industry average.
Medical Surgery Chairs Integrated with a sterile control system, the base is made from 316L stainless steel, and the surface is electro-polished to Ra≤0.8μm. The gas lift system allows micro-adjustments down to 0.01mm, and the temperature-sensing seat maintains a consistent 36.5-37°C temperature range, speeding up wound healing by 19%.
Esports Training Chairs Equipped with a neurofeedback system, the seat features 32-channel electromyography sensors to monitor posture stability. When muscle tremor frequency exceeds the threshold, the armrest’s tactile feedback module provides an immediate warning, enhancing the precision of professional players' operations by 28%.

4. Technology-Driven Health Management
Dynamic Pressure Distribution Monitoring System This system includes 2048 sensor units that map the pressure distribution between the ischium and femur. When localized pressure exceeds 32kPa, the air cushions automatically adjust support, reducing the risk of sciatic nerve compression by 63%, according to clinical trials.
Biological Rhythm Lighting System The ActiveLight technology from Philips is integrated into the chair’s backrest with full-spectrum LEDs. The system automatically adjusts color temperature based on circadian rhythms—6500K blue light in the morning to boost cognition, and 3000K amber light in the evening to promote melatonin secretion, reducing work efficiency fluctuations by 41%.
Aerodynamic Design for Local Microclimate Optimization A laminar airflow channel is set beneath the seat (airflow speed of 0.25m/s ±5%) and is coupled with a HEPA 13-level filtration system. Air quality monitoring shows that the PM0.3 concentration in the breathing zone remains below 12μg/m³, increasing brain oxygen levels by 18%.
At the University of Tokyo’s ultra-precision machining laboratory, quantum-level stable chairs are creating miracles: using superconducting magnetic levitation technology, 99.97% of ground vibration is neutralized, achieving a nanometer-level processing precision of 0.5nm Ra. This shows that fixed-base chairs have evolved from physical limitations into technology enablers, releasing the maximum potential of human creativity through absolute stability. When biomechanics, material science, and environmental control deeply integrate, fixed-base chairs no longer restrict but become the solid foundation of professional excellence.
Choose Ekintop Furniture, and we will provide you with the best solutions for your professional workspace needs.
0 notes
Text
SYCL Capable Multi-Layer Perceptrons for Intel GPU

SYCL Standouts
With an open-sourced repository for the implementation, Intel is pleased to introduce the first SYCL implementation of fully-fused Multi-Layer Perceptrons implemented on Intel GPUs that enable Intel Xe Matrix Extensions (XMX) instructions. The implementation offers many features, such as cross-platform use, multi-resolution hash encoding, adaptability to neural network architectures, compatibility with PyTorch, and high-performance computing.
The implementation beats the CUDA PyTorch version running on Nvidia’s H100 GPU by up to a factor of 19, and it beats the pre-made Intel Extension for PyTorch (IPEX) implementation running on the same Intel GPU by up to a factor of 30.
Multi Layer Perceptron
For many modern Machine Learning (ML) applications, such as representing the solution operator of partial differential equations, determining the density or colour function in Neural Radiance Fields (NeRFs) objects, and substituting Neural Ray Tracing for classical ray-tracing, Multi-Layer Perceptrons (MLPs) serve as the primary Neural Network architecture. The completely linked layers of MLPs are typified by the connections between each neuron in the layer and all the layers above and below. MLPs are ideal for fully-fusing processes since each neuron’s output is independent of its neighbours in the same layer.
The first SYCL implementation of fully-fused MLPs applied to Intel GPUs supporting Intel Xe Matrix Extensions (XMX) instructions is proudly presented by Intel, along with an open-sourced implementation repository. By combining the operations in each tier of the MLP, this implementation minimises the sluggish global memory access and maximises data reuse inside the general register file and shared local memory. Using a roofline model, Intel demonstrate that this leads to a notable rise in the arithmetic intensity and better performance, particularly for inference. Additionally, the study demonstrates the effectiveness of Intel’s SYCL implementation in three key domains: Neural Radiance Fields, Physics-Informed Machine Learning, and Image Compression.
Multi-Layer Perceptron
A SYCL implementation of Multi-Layer Perceptrons (MLPs) optimised for the Intel Data Centre GPU Max 1550 is shown in this work. Intel’s approach maximises data reuse inside the general register file and shared local memory by fusing operations in each layer of the MLP, hence minimising sluggish global memory accesses and increasing efficiency. Using a basic roofline model, Intel demonstrate that this leads to a notable rise in the arithmetic intensity and better performance, particularly for inference.
Intel Extension for PyTorch
Intel demonstrate that Intel’s implementation on the Intel Data Centre GPU beats the CUDA code on Nvidia’s H100 GPU by a ratio up to 2.84 in inference and 1.75 in training, when Intel compare Intel’s method to a similar CUDA implementation for MLPs. Additionally, the study demonstrates the effectiveness of Intel’s SYCL implementation in three key domains: Neural Radiance Fields, Physics-Informed Machine Learning, and Image Compression. Intel’s approach beats the CUDA PyTorch version on Nvidia’s H100 GPU by up to a factor 19, and the off-the-shelf Intel Extension for PyTorch (IPEX) implementation on the same Intel GPU by up to a factor of 30 in all circumstances.
SYCL Features
First among several advantages of Intel’s approach is high-performance computation; high-throughput training and inference are made possible by the system’s efficient operation on Intel Data Centre GPUs. Additionally, the technique offers Python bindings that smoothly interact with the PyTorch environment, allowing users to include GPU-accelerated MLPs into PyTorch applications. It also offers adaptability by enabling a range of neuron topologies and networks with numerous hidden layers to meet various performance needs and use cases. It also incorporates Multi-Resolution Hash Encoding, which enables the network to efficiently handle high-frequency features, and is built to function on a variety of Intel GPUs, enhancing the framework’s adaptability and usability on diverse platforms.
SYCL Achievement
Intel’s fully-fused MLP implementation improves the results of a number of popular AI tasks. Intel compared Intel’s SYCL implementation on an Intel Data Centre GPU Max 1550 with the CUDA implementation on an Nvidia H100 GPU and PyTorch utilising both the CUDA backend and the Intel Extension for PyTorch (IPEX) in order to illustrate these performance advantages.
The results demonstrate the success of Intel’s approach: in Intel’s tests, the implementation outperforms the PyTorch implementation by up to a factor of 30, and outperforms an analogous CUDA implementation for MLPs with width 64 by a ratio of up to 2.84 in inference and 1.75 in training.
Intel also demonstrated the effectiveness of Intel’s solution in three key domains: NeRF (Neural Radiance Fields), Image Compression, and Physics-Informed Machine Learning. Intel’s method showed significant increases in all three categories, with factors reaching up to 30 times over traditional PyTorch implementations and up to 2.84 times over highly optimised CUDA versions.
Considering the Future
Intel want to further optimise Intel’s approach in the future, with a particular emphasis on using registers more effectively in order to cut down on stalls. Furthermore, by enabling the loads of various weight matrices in the shared local memory (SLM) and lowering its utilisation, Intel might be able to lower the number of barriers that are required. Increasing occupancy for small batch sizes and optimising the merging of the final matrix products into the backward pass will be additional areas of focus.
Intel intend to investigate using Intel’s ESIMD SYCL extension for Intel’s implementation, as well as generalise Intel’s library to different data kinds and wider network widths, in addition to performing more speed optimisation.
Read more on Govindhtech.com
#SYCL#govindhtech#intel#IntelXeMatrixExtension#PyTorch#machinelearning#TechNews2024#technologynews#technology#Technologytrends#technews
0 notes
Text
Oracle 1Z0-447 Certification Aspects
* Exam Title: Oracle GoldenGate 12c Implementation Essentials * Exam Code: 1Z0-447 * Exam Price: $245.00 More on exam pricing * Format: Multiple-Choice * Duration:Two hours * Number of Questions: 72 * Passing Score: 69% * Validated Against: Exam has become validated against Oracle GoldenGate 12c. * 1Z0-447 Practice Test: https://www.dbexam.com/1z0-447-oracle-goldengate-12c-implementation-essentials * 1Z0-447 sample questions: https://www.dbexam.com/sample-questions/oracle-1z0-447-certification-sample-questions-and-answers Oracle GoldenGate 12c Certified Implementation Specialist Certification Overview The Oracle GoldenGate 12c Essentials (1Zx-xxx) exam is ideal for people who use a strong foundation and expertise in selling or implementing oracle GoldenGate 12c solutions. This certification exam covers topics like: Oracle Goldengate 12c Architecture; Oracle GoldenGate 12c Parametres; Oracle Goldengate 12c Mapping and Transformation Overview and more. Up-to-date training and field experience are suggested. The Oracle GoldenGate 12c Implementation Specialist certification recognizes OPN members as OPN Certified Specialists. This certification differentiates OPN members available by giving an aggressive edge through proven expertise. This certification helps the OPN member’s partner organization entitled to the Oracle GoldenGate 12c.

* Get More Detail About Oracle 1Z0-447 Certification: https://oracle-exam-guide.blogspot.com/2019/05/how-to-score-best-in-1z0-447.html Oracle 1Z0-447 Certification Exam Topics * Oracle GoldenGate (OGG) Overview * Describe OGG functional overview and customary topologies * Describe OGG Veridata and Management Pack functionality * Describe the gap between real-time data integration replication files Manipulation Language (DML) replication * Install and Configure OGG * Download and Install OGG, and differentiate between various installers (zip, OUI, tar) * Synchronize source and target databases with the Initial Load * Prepare database for OGG CDC and view databases with OGG schema check script * Configure OGG Replication component parameter files * Configure the OGG Command Interface to generate OGG processes * Describe how you can identify and resolve issues in heterogeneous replication, and offer appropriate solutions * Configure OGG utilities * Mapping and Transformation Overview * Implement use cases for transformation functions * Implement macros * Managing and Monitoring Oracle GoldenGate * Manage OGG command information security * Implement and troubleshoot OGG Monitoring * Explain the configuration and management of the Enterprise Manager 12c plug-in * Implement and troubleshoot OGG Veridata * Architecture Overview * Describe OGG components * Create both forms of Capture systems for Oracle database * Create the three forms of Replicat processes * Explain the real difference between an Extract and Pump, and local and remote trails * Configure OGG's process recovery mechanism * Parameters * Describe and compare GLOBALS versus MANAGER parameters * Create solutions using component parameters for replication requirements * Install OGG parameters * Explain and identify parameters specific for non-Oracle databases * Configuration Options * Describe OGG configuration options (Data Definition Language (DDL), compression and encryption options) * Configure OGG event actions based on use cases * Troubleshoot conflict detection and backbone * Configure Integrated Capture, Replicat, and deployment options Sign up for Oracle 1Z0-447 Certification exam Sign up for Oracle 1Z0-447 Certification exam with Pearson VUE and buy test with all the voucher you purchase from Oracle University or which has a bank card applied during exam registration. To learn more about oracle goldengate certification webpage: check.
1 note
·
View note
Text
Get WAN OPTIMIZATION for Fast and Steady Internet Speed
WAN optimization is mainly concerned about the WAN acceleration to improve the efficiency experience. It is obtained by monitoring the data flow across a wide area network (WAN) and reduces the roadblocks that delay data transfer. The technology is growing at a fast pace and moving forwards to provide better connectivity. Most of the service providers are working towards implementing new technology to provide better facilities to the users. The concept of WAN optimization encompasses various features like traffic shaping, data de-duplication, compression and much more.
Being a new technology, people usually find it a bit complicated to understand. This is because of on-site equipment and not the underlying network, giving operators leeway to gain customers who are not using them exclusively.
It has an inbuilt ability of data caching, which makes local server faster to access data because the frequently used data is stored locally. Another quality of WAN is that it shrinks the size of data to limit the bandwidth use, so you can compress the data easily to make space for more.
WAN optimization can be improvised with the help of a service provider if they are willing to put equipment on every single customer premise. This will build a strong network for communication and will enable you to avail the best possible services. With growing advancement, many telecom operators are balancing the flexibility to work according to the needs of a solid, standardized portfolio of services and at various levels.
The primary optimization is mainly concerned about setting the base at building rather than connecting the main lanes with various topology to get better connectivity. This has certainly made WAN optimization the subject of extensive academic research to get you more flexibility. Such researches are conducted to increase the performance parameters of overall network capacity. Many newly computed machines learning models or multimedia are optimized for fast and efficient geo-replication of data.
1 note
·
View note
Text
Maths and its technological importance.

Mathematics is a broad field of study that deals with the properties and relationships of numbers, quantities, and shapes. It includes topics such as algebra, geometry, trigonometry, calculus, statistics, and more.
Mathematics is an essential tool in many fields, including science, engineering, economics, and finance. It provides a framework for logical reasoning, problem-solving, and critical thinking. Some key concepts in mathematics include numbers, equations, functions, graphs, and proofs. These concepts are used to model and solve a wide variety of problems, from calculating the trajectory of a spacecraft to analyzing the effectiveness of a new drug.
There is still much to be discovered and understood in the field of mathematics, and on going research is constantly pushing the boundaries of our knowledge.
Mathematics is one of the most fundamental disciplines of science that plays a crucial role in technology. It provides the necessary tools and concepts to build and improve various technologies that we use in our daily lives. The following are some of the reasons why mathematics is important in technology:
Developing and improving algorithms: Mathematics provides the theoretical foundation for developing and improving algorithms, which are the backbone of many technological applications. For example, mathematical concepts such as calculus, linear algebra, and graph theory are used to develop efficient search algorithms, data compression techniques, and image processing algorithms.
Designing and building complex systems: Technology today involves designing and building complex systems such as networks, software, and hardware. Mathematics provides the tools to model, analyze, and optimize these systems. For example, mathematics is used to design and optimize network topologies, develop error-correcting codes, and analyze the performance of computer processors.
Predicting and modeling natural phenomena: Mathematics is used to predict and model natural phenomena, which is crucial for designing technologies that can withstand or exploit these phenomena. For example, mathematical models are used to design bridges that can withstand the forces of wind and earthquakes, and to predict the behavior of fluid flows in aircraft engines.
A platform for educational technology called Kiya Learning maths classes in Singapore enables students to take live lessons and master a variety of subjects. Through our qualified specialists, who assist students in learning at any time of day, we assist the students in gaining knowledge and mastery on their subjects.
Kiya learning offer personalised, flexible instruction. The students are free to attend classes whenever they wish. One student will be taught by one teacher at a time, which will foster a relationship between the two parties and enable open-minded questioning on the part of the learners.
0 notes
Text
CDN, edge optimization and website perf
Us backend engineers don't get to appreciate the nuances that go into the frontend development and as such, do not fully appreciate the different techs and why they exist. For example, over the past few years, we've seen techs such as edge optimization that are all geared towards minimizing the latency for the end user.
Why is the latency improvement important? --------------------------------------------------
Science tells us that the humans perceive response times of 100 msec as instantaneous (i.e. latency is imperceptible). Latencies larger than that and we say that the website is slow. https://www.pubnub.com/blog/how-fast-is-realtime-human-perception-and-technology/
So today, after a few changes, I started noticing that the website was becoming slow. My first inclination was that its probably the images that I had added to the page - they hadn’t been compressed and I've had similar issues in the past with image sizes causing slowness in the website rending in the browser. (Shout out to the pandas at tinypng.com - They really chomp down images into manageable sizes)
But this time, the javascript console tells me that there is a large javascript file that I referenced (700KB) which is causing around 700 msec latency in the page download. Maybe its time to deploy these resources on a CDN now (edge optimization).
I deploy the image on the CDN and immediately see a remarkable improvement in the latencies. It’s interesting to note that the CDN automagically caches and compresses this content.
Non CDN URL - time in seconds -------------------------------------- $ > curl -o /dev/null -s -w %{time_total}\\n https://my_non_cdn_url/my_javascript.js 0.821876 $ > curl -o /dev/null -s -w %{time_total}\\n https://my_non_cdn_url/my_javascript.js 0.800996 $ > curl -o /dev/null -s -w %{time_total}\\n https://my_non_cdn_url/my_javascript.js 0.778007
~ 800 msec
CDN Url - time in seconds ------------------------------ $ > curl -o /dev/null -s -w %{time_total}\\n https://my_cdn_url/my_javascript.js 0.028549 $ > curl -o /dev/null -s -w %{time_total}\\n https://my_cdn_url/my_javascript.js 0.007928 $ > curl -o /dev/null -s -w %{time_total}\\n https://my_cdn_url/my_javascript.js 0.007497
~ 7-20 msec
Now some of you may question why is my javascript 800 KB :) - that is a valid question and I am hacking javascript for some static data - so that improvement for some other time.
Takeaways,
the CDN deployments in this day and age is a few clicks to setup and the improvements in latencies are orders of magnitude
compress the images / assets on the website
Hearken back to fallacies of distributed computing (https://en.wikipedia.org/wiki/Fallacies_of_distributed_computing)
1. The network is reliable; 2. Latency is zero; 3. Bandwidth is infinite; 4. The network is secure; 5. Topology doesn't change; 6. There is one administrator; 7. Transport cost is zero; 8. The network is homogeneous.
0 notes
Text
Microsoft remote desktop connection client for mac osx

MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX MAC OS X
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX PRO
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX LICENSE
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX DOWNLOAD
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX MAC OS X
You are allowed to use this app for iOS (iPhone and iPad), Mac OS X and Android devices with a Windows Server 2012 RDS CAL (Client Access License).
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX LICENSE
There is no separate license needed for Microsoft Remote Desktop app. * The oldest version tested and verified is SP3 for Windows XP for the iOS, MacOS, and Android apps. Windows Server operating system: Windows Server 2012 R2, Window Server 2012, Windows Server 2008 R2 Windows Client operating system: Windows 8.1, Windows 8, Windows 7, Windows Vista, Windows XP* The Remote Desktop apps will connect to the following versions of Windows: Powerful Pan and Zoom feature allows you to easily interact with remote applications on small screens.įigure 4: Screenshot of Android app zooming in with Pan control The local keyboard with Windows extensions allows easy interaction with the remote desktops and apps.įigure 2: Screenshot of Android app with local keyboardįull support for RemoteApp programs on all platforms gives you the ability to run your favorite applications on your device of choice wherever you are.įigure 3: Screenshot of Mac app running Internet Explorer, File Explorer, and Calculator as RemoteApp programs. Using strong encryption to protect your data is critical and this feature has long been requested by our customers.Ĭonnection Center (the Remote Desktop apps UI) provides simplified management of all your remote desktops and resources in one simple view.įigure 1: Screenshot of the iOS app Connection Center The apps also connect to older servers that do not support the newer, stronger encryption offered by NLA but will alert the user that they are connecting to a potentially unsafe server. The Remote Desktop apps support the latest Network Layer Authentication (NLA) protocol, protecting your users and your data. Whether you are a road warrior always on the go or using your device at home or in the office, you will get the best possible remoting experience available for your devices of choice. RemoteFX has been optimized for all network topologies and client types. Given sufficient bandwidth and client resources, streaming of HD video with high definition audio is possible up to 30fps.įor lower bandwidth scenarios such as 3G or WAN, the protocol will dynamically adjust the compression and frame rate to deliver the best possible user experience. The protocol automatically adjusts for client performance and network bandwidth. The apps use RDP 8.0 and RemoteFX for high fidelity audio and graphics. They can easily connect to external monitors or projectors for presentations Users can get a rich Windows experience and be productive on their personally-owned devices. The Remote Desktop apps provide a rich multi-touch experience with RDP and RemoteFX supporting Windows gestures.
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX PRO
Their PCs (Windows Pro and Enterprise versions) You canĮxperience the power of Windows with RemoteFX in a Remote Desktop client designed to help you get your work done wherever you are. We are excited to introduce clients with best of class performance and security including Remote Desktop Protocol (RDP) 8.0 and RemoteFX.
MICROSOFT REMOTE DESKTOP CONNECTION CLIENT FOR MAC OSX DOWNLOAD
My name is Olof Mases, program manager on the Remote Desktop Virtualization team, and I am excited to announce, in addition to the General Availability of Windows Server 2012 R2, that our Remote Desktop apps forĪre now available for download from the App Store, the Mac App Store, and the Google Play Store. See īut in short, using the above methods you can get the MS remote desktop installer to reuse and it won't be locked to an Apple ID.First published on CloudBlogs on Oct, 21 2013 Then there's the MAS receipt issue for the ilife/iwork apps.you'll find out. If you spend a day capturing downloads you'll get the hang of it. Which location they go to depends on OS version and whether the download is a 3rd party, Apple App, Apple system file or some other classification. Only Root has access to some of these locations so you have to login as root to capture the installers. Library/Updates/numbered folder beginning with zzzz031 or just 031 which may vary by OS version/ private/var/folders/zz/zyxvpxvq6csfxvn_n0000000000000/C/PKInstallSandboxManager/5AF5AE82-B23B…(numerical string which may or may not be unique).activeSandbox/Root/Applications/ There are newer locations of downloads which include: Things have changed with each OS version since this article. There are several online articles on capturing app store installers from the app store.

0 notes
Text
THE LOST GIRL’S HOME IS IN BOOKS: spring leisure reading

Girl Reading (1850), oil on canvas, Andre Fontaine
Writing on my phone. On the train. Woke with a sore throat. Snow outside the Manhattan window turning to sludge and then puddles. In the morning Alex and I made our way to Tisch to pick up books from Wendy and sit in on Fred Moten’s class. He spoke for three hours about a paragraph in Zalamea’s Synthetic Philosophy of Contemporary Mathematics, constellating the Isley Brothers with quantum physics with the history of slavery with Solange with financialization with the spatio-temporal dimensions of Judaism with critiques of the individuated liberal subject. In Fred’s presence I’m always in awe. When he says the stream of thought will go where it goes, I know what he means, what it feels like, to want to read everything. To have no filters. To be a being who is…interested. “You know, it’s like a river that winds through all these different terrains, and part of it winds through the history of science, and part of it winds through category theory and general topology, and part of it winds through Russian cinema—I’m just interested.” (Moten) Would like to linger more on the things I read and not just mark passages to return to…later. Has grad school de-skilled me? Has the process of becoming a “historian”—of having to read thousands of pages per class in grad seminars destroyed my ability to read slowly? Poetry is becoming harder to read. It demands a kind of attention other than the kind of attention I have become accustomed to—the temporality forced into me by the academic grind. Last semester I did my comprehensive exams. For two hours I was quizzed by 4 professors on the contents of ~400 books. My fields were: Prisons and Police; History and Political Economy of Race in America; Social and Political Theory (Marxism, psychoanalysis, critical theory, Frankfurt School, feminist/queer theory, post-structuralism); and Black Literature, Theory and Cultural Studies. “Studying” for my exams hardly felt like studying at all—I was just doing what I’ve always done: read. But the thing about being in academia is…you can’t just read what you want to read (unless you’re Fred!), you’re supposed to specialize. Your supposed to read within your discipline, to be monogamous with your dissertation topic. But sometimes…my mind needs ventilation. I need to let my mind wander. So this spring break I went on a kind of “retreat”—I rented a little eco-bungalow on a mountain overlooking the ocean in Deshaies, Guadalupe, with the intention to do nothing except read, journal & spend time in nature. It’s weird to now have a life where I have to schedule in these compressed snatches of leisure. Between my academic life and artist/public intellectual life all life is becoming work work work. Constant travel, mountains of assignments to grade, grant applications, bureaucracy, student emails, assigned readings, lesson planning, talks—in psychoanalysis I am sometimes too fatigued to finish my sentences. What was it? “The disquieting feeling that we don’t own ourselves.” My poor journal, neglected since last semester. Turned inside-out and called into presence by the Pavlovian PING of the push notification. Life becomes the work of feeding the avatar. It’s nothing new. It’s the same ole subject formation, in overdrive. The you of I (alienated Lacanian subject) — identification with an image of self that circulates as…I-am-that. When the avatar takes over your life, when you become what the public makes you…how can you find a way to re-inhabit your life as you? Quiet. Unplug. Has busyness evacuated my inner life? I’m still me. But look at how much my situation has changed…
Here are my notes on the books I read over spring break (some finished the week after I returned…)

Tolstoy - Anna Karenina
My skin takes it in. Ghosts enter and leave this vessel, Sunship Earth. Body, too, will become a ruined beach house covered in pale violet morning glory vines, its shutters still hinged shut. Now Nabokov is analyzing the varied march of time in Tolstoy—there is something like a moral in Kitty and Levin’s slow dance, against the locomotive thrust of Anna and Vronsky. A road—to where? The bull in the clearing, the smell of the tiny yellow flowers and the fade, the gloaming, the wall of water, peach-haloed in the sunset. The dimming, the peep of the first cicada, the crushed cicada that lost its way, the dream that wrote her destiny, the dirty peasant rooting around in the sack—the man split by the wheels of the locomotive. A force that nothing, no one escapes. [Holy shit. As I type these notes from my journal my train has been stopped in Providence because the train ahead of us hit someone]. Yes, I have had the dream of the man with his hand in my sack [“It was crowded in the market. I was trying to photograph the flowers but the image was distorted because a man had his hand in my backpack”]. Can a sudden silence wake a sleeping body? I think, as I wake, that I have caught the day in the precise moment of transition. What crossed over then, the wind swept the island clean. Like Anna Karenina I have been under the spell of the dream: what I now no longer know if I can trust. Nothing could have saved Anna the terrible omen flashing above her life…

Nabokov - Lectures on Russian Literature
Freud and Baldwin love Dostoyevsky. Nabokov loathes him. What does that tell you about the kinds of people who love and hate Dostoyevsky? Lovers of Dostoyevsky: hysterics, neurotics, fringe-dwellers, madmen. Dostoyevsky is to literature what Zulawski is to cinema (emotional excess–which is why teens also love Dostoyevsky). This whole book is an argument for Tolstoy and against Dostoyevsky. Lovers of Tolstoy: the good, the moral, the erudite, Oprah. Nabokov is a snob à la Adorno, but his lectures on Tolstoy are damn good (skip the ones on Dostoyevsky), especially the ones on dreams and time in Anna K.

Nabokov and Barabtarlo - Insomnia Dreams
This book is pretty fucking cool. It is an inventory of Nabokov’s proleptic dreams, which he wrote down on notecards after reading J. W. Dunne’s An Experiment with Time. Dunne was an aeronautical engineer and crackpot philosopher who developed what I sometimes call stoner dream theory. He believed that past-present-future exist simultaneously and that the experience of time as an arrow moving forward is an effect of waking consciousness. In dreams we are unhitched from normative time and can access the future–are touched by future events.
Notebook notes: Dunne and Nabokov dream to know time in every direction. So future events loop back to pierce our sleeping heads. Did I believe—the future is making contact with me. What did the dream corrupt? I could not outrun it. Nabokov dreaming of South Station [strange, that’s where I’m headed as I type up these notes…]. Dreams of the lepidopterist: chasing the butterflies with a giant spoon instead of a net. Sometimes he’s an insufferable pedant. But even pedants can have a compelling dream life…

Lemov - Database of Dreams: The Lost Quest to Catalog Humanity
Professor Lemov teaches in the History of Science department at Harvard. She is currently a faculty fellow in a year-long Crime and Punishment seminar at Harvard that I am also a part of. I first got interested in her work after she presented an excellent paper on the history of Cold War behaviorist experiments (many of which were conducted on prisoners, including the practice of “psychosurgery”) and early efforts to use data to construct psychological theories of deviance. When I found out she wrote a history of a dream database, I knew I had to read it.
This book is a history of Bert Kaplan’s ambitious mid-20th century quest to create a database of dreams and psychological data (called the Primary Records in Culture and Personality), which consists of a collection of the raw notes of the thoughts, feelings, and dreams of people from around the world, stored on the now-obsolete technology of the Microcard. It is at once a history of: microfilm technologies, data science, the information storage ambitions of postwar social scientists and anthropologists, and psychologists’ obsession with the dreams and unconscious thoughts of ethnic “others.” The story of the database is fascinating in itself…but I wanted to know more about what was in the repository. Sometimes the unconscious speaks:
“A man named Birch Tree told of a dying young man of his acquaintance who had dreamed too ambitiously: one night, he was able to see ‘every leaf in the whole world’ and perished soon after, like the leaves that fall from the trees each year.”
“dream #19, in which he was shooting birds, surrounded by sunflowers as big as evergreen trees”
“Dreams were “palimpsests for understanding what could be called ‘not-self,’ the place at which the self begins to shade away into nothingness or something else.”
“If you sat in a library looking at someone’s dreams, what were you seeing?”
The database of dreams was dead on arrival.
But there’s another living database of dreams assembled by oneirologist Kelly Bulkeley: http://sleepanddreamdatabase.org/ – have read and enjoyed several of Bulkeley’s books too. The convocation of the oneirologists…

Sliwinski - Mandela’s Dark Years
How strange, I read this two days before the death of Winnie Mandela. Did Nelson dream of Winnie while in prison? There is a lot to chew on in this little book. I keep returning to the dream that is circled in the text, Nelson Mandela’s dream from prison:
I had one recurring nightmare. In the dream, I had just been released from prison—only it was not Robben Island, but a jail in Johannesburg. I walked outside the gates into the city and found no one there to meet me. In fact, there was no one there at all, no people, no cars, no taxis. I would then set out on foot toward Soweto. I walked for many hours before arriving in Orlando West, and then turned the corner toward 8115. Finally, I would see my home, but it turned out to be empty, a ghost house, with all the doors and windows open, but no one at all there.
The subject in absentia dreams their erasure while in prison, the experience of becoming-ghost. (Mandela’s recurring nightmare. How apartheid structures the geography of the unconscious…)

Szabó - The Door
“If there was [an] article about what to read once you’ve finished Elena Ferrante’s Neapolitan novels, The Door—though it lacks the scope of those books—might top the list.” I read no such list but did finish the Neapolitan novels last year. I read The Door after it was recommended by 3 of my feminist friends.
To say what this book is about would fail to get at the experience of reading this book. It’s deeply disturbing and all the more so because Emerence, the narrator’s housekeeper, is the exact likeness of my aunt Helen. They are women for whom every emotional door has been sealed shut. They both had dogs that were passionately attached to them. Under what conditions does the wound grow into an impenetrable shell? Grow into the pride of self-sufficiency…
Notes: The book is bookended by a recurring nightmare of a door that won’t open. An ambulance outside, and the silhouettes of paramedics seen through glass. Most of my dreams are about the absence of shelter, porous structures, rooms that are always open to invaders. But here is a nightmare about being trapped inside with someone in need of help. Ferrante’s Days of Abandonment resonates too.
Resonances. Lightning strikes the two babes Emerence was fleeing with. In Anna Karenina, lightning missed Kitty and child. The plots of two novels are crossed. What characters evade in one novel befalls characters in another. It’s like the books are talking to each other through the body of me.

Schmitt - Political Theology
We should discuss this book in person. My thoughts are too sprawling to give shape to them here. People on the left read Schmitt for his critique of liberalism and though there are parts of it I find compelling (I’ve elaborated the concept of a “financial state of exception” in my book Carceral Capitalism), the part about liberal democracy lacking decisionism because it’s weighed down by a Weberian bureaucracy is, I think, wrong. Well, that’s what I felt while reading McCoy’s In the Shadows of the American Century immediately following Political Theology.

McCoy - In the Shadows of the American Century
This book is part of an ever-growing body of literature on the decline of US hegemony and the rise of China as a global superpower. But what this book adds to the analysis is a thought-provoking discussion of the changing nature of geopolitical struggles–from a navel-based strategy to a land-based strategy. McCoy unpacks the influence of Halford Mackinder’s theory of the Geographical Pivot of History, which posits that the future belongs to whoever controls the Eurasian landmass (the World-Island). During the Cold War the US has maintained its hegemony by controlling key axial points–through NATO in western Europe (on the west side of the World-Island), and the strategic positioning of military/naval bases around the Pacific, and the forging of political and economic alliances with South Korea, Japan, the Philippines, etc. This book is a good overview of how the US built and maintained its empire, and offers possible blueprints for its decline (McCoy’s analysis of Obama’s attempts to salvage US hegemony through his “pivot toward Asia” and Trump’s acceleration of the decline of US hegemony was interesting…). After reading about the CIA’s covert operations in Latin America I felt that liberal democracy is not at all lacking decisionism, as Schmitt says, but like all states it maintains its power through brute force (militarism/war), international diplomacy, strategic alliances, soft power, proxy warfare and covert operations, international trade agreements, technological prowess, surveillance, etc.

Saterstrom - Ideal Suggestions
What is the relationship between what is seen and unseen?
Saterstrom’s poetics can be summed up by her line: “dust mote footing the invisible”–the “thing” itself is often absent, even as it mutates everything present, but there are ways to access ghosts, traces, invisible forces, and the disappeared. Like a projection that flashes when it catches smoke in the phantasmagoria–you can catch it in the transition.
The form of the book is satisfying. I enjoy the way it alternates between ars poetica and the enactment of the poetics it is trying to sketch.
Notes:
“In the other world everything also exists. But in versions complicated by the softness that dissolution makes.”
“what happens between women when the center of female triangulation is scarcity and lack?”
Simone Weil: “When a contradiction is impossible to resolve except by a lie, then we know that it is really a door.”
divinatory poetics as a way to bear “the absurdity and enchantment of human experience”
to write from “within the membranous precincts between our multiple bodies in the larger rhizomatic field of resonances, where much is sounding and is also unsounded.”
Christian Hawkey: “the holes in our bodies and skulls are voice chambers, sound chambers, wherein our own voiced selves and the voiced selves of others constantly enter and exit, and are changed by our bodies upon entrance, exit. Consciousness…is less a vehicle for “self-presence” than a void, a blank space at the site of intersection.”
“the friendship of our ghosts”
“A raw garnet dug up from earth appears as a piece of burned glass and smells of warm dirt. How did this garnet come to rest here, pinned between sky and sea, a mineral between the here and hereafter? Lines made through the absenting of lines, they suggest their phantom shapes into calligraphy. And someone arrives, a dead poet, she writes in an elegant script a poem about geese. It is a melancholic poem featuring geese, a landscape, and reflections about death. How do the deceased live within the blurred calligraphic strokes dependent upon whatever it was we erased? Who was here first? The process of being read, truly read. One day our lines appear in some other’s erasure.”

Where Freedom Starts (an anthology of essays on #MeToo)
This is an excellent collection of essays on #MeToo that captures the spectrum of feminist responses to the nascent movement. It includes black feminist critiques of carceral feminism, a discussion of black and Latinx vulnerability to sexual violence in the sphere of domestic labor, queer critiques of moral sex panics, feminist analyses of social reproduction, analyses of how undocumented women are hyper-vulnerable to sexual assault in the workplace (and at risk of deportation if they report sexual abuse), and more. I appreciate that many of these essays attempt to grapple with the emotionally and politically messy aspects of sexual violence–How do we determine the category or degree of the harm done? What you do when you feel ambivalence toward your rapist and internalize blame? How is victimhood constructed? I plan to return to these topics and questions in an essay I hope to write in May.
**This ebook is free from Verso.** Get it here.

Marina Van Zuylen - The Plentitude of Distraction
If I ever teach my Lost Girls class on the poetics of wandering, I would definitely include this book!! So, so good. Yes, the poet needs to give herself over to her reveries. To luxuriate in the waywardness of experience–the soul cut loose.
Notes: Darwin’s great regret: “Up to the age of thirty, or beyond it, poetry of many kinds … gave me great pleasure, and even as a schoolboy I took intense delight in Shakespeare, especially in the historical plays. I have also said that formerly pictures gave me considerable, and music very great delight. But now for many years I cannot endure to read a line of poetry: I have tried lately to read Shakespeare, and found it so intolerably dull that it nauseated me. I have also almost lost my taste for pictures or music…. My mind seems to have become a kind of machine for grinding general laws out of large collections of facts, but why this should have caused the atrophy of that part of the brain alone, on which the higher tastes depend, I cannot conceive…. If I had to live my life again, I would have made a rule to read some poetry and listen to some music at least once every week; for perhaps the parts of my brain now atrophied would thus have been kept active through use. The loss of these tastes is a loss of happiness, and may possibly be injurious to the intellect, and more probably to the moral character, by enfeebling the emotional part of our nature.”
Discussed this Darwin passage with my analyst for some time. I don’t want to become a work machine! Give me “delicious idleness”!
“stop measuring your days by what you can report to your boss or to your conscience”
waywardness: “reveries unfasten him from his constructed social persona, eventually converting dispersal into a gathering of self-hood”
Blaise Pascal, Pensées: “The only thing that consoles us for our miseries is diversion. And yet it is the greatest of our miseries. For it is that above all which prevents us thinking about ourselves and leads is imperceptibly to destruction. But for that we should be bored, and boredom would drive us to seek some more solid means of escape, but diversion passes our time and brings us imperceptibly to our death.”
“the pure pleasure of a contemplative experience”
“It is not too late to side with some of the great propagandists of wasted time, with the practitioners of reverie, and cultivate the pleasures and pains of mental mayhem.”

Marx - Capital Vol 1
It’s always a good time to re-read Marx. In December I started a Capital reading group with my comrades LaKeyma and Joohyun. Marx is best read with your women of color crew!

Sithole - Steve Biko: Decolonial Meditations of Black Consciousness
Did an event with the incredible Tendayi Sithole at NYU (moderated by Fred Moten and Wendy Lotterman), so I wanted to read Tendayi’s work on Biko before the event. Many parts of the book draw on Afropessimism to analyze Biko’s liberatory political philosophy. We had a long discussion (privately and during the panel) about Afropessimism’s reception in South Africa (”it’s given us a language to understand our predicament,” says Tendayi). Such good work, and such a wonderful person and poet too!! During the reading Fred said Tendayi and I “became a band.”

McGuckian - The Flower Master
Re-read this at the Deshaies botanical gardens in Guadalupe. Unfuckwithable. McGuckian is one of my favorite poets of all time. Also read the parts about McGuckian in Northern Irish Poetry and the Russian Turn. Had no idea McGuckian draws so heavily from Russian literature, and that she feels there is a natural kinship between Russians and the Irish due to their historical predicaments…

Harford - Fifty Inventions that Shaped the Modern Economy
Pop economic/business and tech history. Replete with compelling stories and fun facts about underappreciated inventions. The chapters I was most interested in were the ones about inventions that fundamentally transformed gendered labor (TV dinners, infant formula, the birth control pill). After a while this books started to annoy me because the novelty wore off and I can only handle so much praise of the so-called wonders of capitalism.

Brogaard and Marlow - The Superhuman Mind
I don’t think I’m any smarter after having read this book. It’s somewhere between pop science (in the style of Oliver Sacks) and self-improvement literature. The book tries to give you mental “hacks”–mnemonics and algorithmic mental shortcuts. Most of the the book describes case studies of people who have accidentally unlocked superhuman mental capacities as a result of a brain injury, stroke, etc…or they were just born neurologically atypical. Synesthetes have good memories. If you’ve ready any of the pop sci books on memory you already know these tricks… the Greeks have known about the Memory Room for a while too…
Still reading:
Moten’s Black and Blur
Anne Boyer’s A Handbook of Disappointed Fate
Doudna and Sternberg’s A Crack in Creation: Gene Editing and the Unthinkable Power to Control Evolution
Frank Stanford - The Battlefield Where the Moon Says I Love You
24 notes
·
View notes
Text
Smart Pneumatics Role in Automation, Cobots, Safety and System Efficiency
For today’s industrial pneumatic systems, automation and efficiency continue to be the driving factors in design. Automation in pneumatics incorporates a variety of design strategies and considerations. When it comes to industrial machinery, Industry 4.0 and the Industrial Internet of Things (IIoT) are big buzzwords, but these solutions are not fully developed yet. For design engineers working toward creating closed-loop automated systems, questions for consideration include:
How do you develop the next-generation Smart Factory?
What is the path toward a fully automated factory?
How can maintenance requirements be triggered without any downtime?
What data input can you use and how do you capture that data?
How do you diagnose maintenance issues at the component, system, or process level?
Smart connected pneumatics For design engineers, smart pneumatics can mean complete flexibility; this is the ability of that component to communicate over the network, multiple uses for a single device, ease of integration and commissioning, as well as troubleshooting. Smart products are where you see the most difference in pneumatic systems. The diagnostic aspect of smart pneumatics is important to help achieve zero downtime.
The concept of zero downtime has seemed unrealistic in the past, however, technology is evolving in that direction. Incorporating sensors into pneumatics enables end-users to collect important prognostic and diagnostic data for setting alerts and getting machine feedback.
The future of smart pneumatics is a complete plug-and-play configuration that is easy to manage. For today’s smart pneumatics, design engineers can generate data and set the alerts but are not yet making fully closed-loop systems. However, this is on the horizon with end-to-end systems that can be configured with just a few clicks and the device will be able to take over, provide data and feedback into the control system that goes beyond simply allowing data dumps.
Read our white paper Innovations for Automation and Efficiency in Industrial Pneumatic Systems and gain insight into the use of smart pneumatics, designing for cobotic applications, applying safety standards, and pneumatic system efficiency.
Technology is changing–quickly As technology evolves, seemingly almost daily, more people are migrating to networks as designers are migrating systems to the newer industrial Ethernet systems. Why? Overall, the “line” topology of the networks makes them much easier to work on and troubleshoot.
It used to be the case that each manufacturer offered the same type of components such as cylinders and FRLs. There is a large divide in the market on what is available and what functions they offer. Products today with integrated electronics offer many different functions through what is embedded. When specifying systems, design engineers should be sure to understand what is necessary for the machine and what value can be provided by the smart products that are specified.
Cobots and safety
In automotive manufacturing, robotics has been in use for more than a decade and over the years, they have shifted from being hydraulically driven to being pneumatically driven. In industrial cobot applications, collaborative robots, known as “cobots” work with humans in some way, including as an assistant or guide in a task or process. Unlike autonomous robots, cobots, do not work alone. They are designed to work with human instruction or respond to human behavior. The shift to pneumatics for robotics means that cobots are primarily pneumatically driven.
Cobots are the next big thing in industrial applications as the cost of robotics comes down and newer opportunities are being developed. Leading cobot applications include:
Machine tending where cobots can load and unload tools and accessories to decrease manual handling.
Pick and place where cobots can complete careful packing and moving, then place and position products or parts.
Assembly and flexible manufacturing where cobots insert parts, screwdriver, and other assembly tasks with appropriate end-of-arm tools.
Packaging, loading, and unloading when aided by suction or gripper attachments, cobots move finished products through packaging.
Safety in collaboration of manual and automated The strict separation between the manual work of the factory worker and the automated actions of robots is becoming an increasingly gray area. Their work ranges are overlapping and merging into a collaborative working space. In doing so, humans and machines will be able to simultaneously work together on the same workpiece or component in the future—without having to be shielded from each other for safety reasons.
Due to this, safety is the largest consideration in the design of cobot applications. However, there can be some confusion on which safety standards to follow in applications with cobots due to the divide between traditional pneumatics and entering the world of robotics. As standards and their adoption vary among engineers and facilities, it is important to know which standards to apply.
For incorporating cobots into a plant, engineers must understand the required standards for the facility and compile the necessary documentation and technical file with due diligence, testing, and validation of the controls architecture.
Smart pneumatic system efficiency Lower upfront and maintenance costs combine to make pneumatics the most popular and cost-effective choice for executing mechanical motion. New improvements in designs and efficiency of compressors, and the standard use and distribution of clean dry air in a manufacturing facility, also make pneumatics a good choice for industrial automated machinery. Smart pneumatics aim to help generate and maximize data and minimize compressed air use. Compressed air use by industrial machines is a close second to the use of electricity in terms of cost, and well ahead of other utilities such as water and natural gas in most plants and facilities. Electricity is less expensive per dollar of unit energy, but compressed air and pneumatics have many other advantages encouraging their use.
Effective pneumatic systems need properly sized, installed, and maintained components from compressors to workstations. A few wrong choices can lead to everything from wasted energy to system failures. Conversely, even seemingly small design tweaks can add up to large improvements in pneumatic system efficiency. These changes can save air, reduce costs, improve overall utilization, and reduce downtime in operation.
0 notes
Text
Top Interview Questions of Networking | CCNA And CCNP
Top Interview Questions
1) Why we need IP address ?
We need IP address for the device to the identification on the internet basically IP is the source of identification on the internet and if you want to access the internet we need IP address. And on the other side if any one want to communicate in a LAN they need device and if device has no IP address than they cannot communicate with each other.
2) What is difference between IPv4 and IPv6 ?
IPv4 is the ip address version 4 and this address is 32 bits address in which there are four octets and four octets are equal to 4 bytes. There are 2^32 addresses that are approximately 4.29 billions addresses. And Ipv6 is the upgraded version of the ip address and this address is 128 bits address in which there are trillions of trillions addresses and this version has the 64 bits network part and 64 bits for host part. IPv6 is the solution for the shortage of the IPv4 addresses.
3) Which IP address is used for local testing ?
The ip address 127.0.0.1 is used for the local testing and this address is known as the loopback address and that address is always up it is used for the testing purpose of own system. The loopback is the source of this question (Is our system work correctly ?) .
4) What are the layers of the OSI Model ?
Following are the seven layers of Open System Interconnection Model:
Application Layer
Presentation Layer
Session Layer
Transport Layer
Network Layer
Data Link Layer
Physical layer
5) Which layer deals with the encoding and decoding ?
Presentation layer is the layer that deals with the encoding and decoding of the data.
6) How many logical ports are and which ports are reserved ?
There are total 65535 logical ports are exist and 0-1023 ports are reserved for the specific purposes and 1024-65535 ports are not reserved these logical ports are that we can use and we find out the service with respect to the specific port.
7) Which layer use for the checking the availability of the destination ?
Transport layer is the layer that is used to check the availability of the destination and it is also responsible for the establishing, maintaining, and terminating the session.
8) What are port numbers of the FTP, Telnet, and SMTP ?
FTP port number 20,21.
Telnet port number 23
SMTP port number 25.
9) What are the five responsibilities of the transport layer ?
Identifying service.
Segmentation.
Sequencing and reassembling.
Flow control.
Error control.
10) What is difference between the TCP and UDP ?
TCP
TCP stands for the transmission control protocol.
TCP is reliable and connection oriented.
TCP is slower.
UDP
UDP stands for the user datagram protocol.
UDP is unreliable and connectionless.
UDP is faster.
11) What are routing protocols and routed protocols ?
Routing protocols are the protocols that are used for the advertising the networks and there are many routing protocols which are following : RIPv1, RIPv2,IGRP, EIGRP OSPF, BGP, ISIS.
Routed Protocols are the protocols that are used for the sending the user data means packet to one network to the other network basically routed protocol carries user traffic to one network to other which are the following IPX, AppleTalk, and IP.
12) What is the major work of router ?
Router is the networking device that is work on the network layer and it work on the IP address and the major work of the router is it integrate LAN and WAN. It is unicast device and it determine the best path from source to the destination.
13) What is difference between the console port and auxiliary port ?
Console port is the port that is use for the local configuration when device is near you.
Auxiliary port is the port that is use for the remote configuration when device is not near you.
14) What is three tier hierarchy ?
Three tier hierarchy is the architecture that base on the three layers following are the three layers of this architecture:
Core Layer.
Distribution/Aggregation Layer.
Access Layer.
15) What are the internal components of the router ?
POST: (Power On Self Test).
ROM : (Read Only Memory) store the Internetworking Operating System.
FLASH : Flash is also stores the IOS (Internetworking Operating System).
NVRAM :Store the configuration permanently.
RAM : Store the configuration Temporary.
16) What is DCE and DTE ?
DCE stands for the data communication equipment and it is for the source side at this side we set the clock that is commonly 64000. DTE stands for the data termination equipment and it is for the customer side at this side clock not set.
17) What is Encapsulation and DE encapsulation ?
When data is sent from a upper layer to a lower layer, each layer adds information to data is known as the encapsulation. When data is sent from lower layer to upper layer, each layer will remove information is known as the de-encapsulation.
18) What is difference between the HDLC and PPP ?
HDLC and PPP are the encapsulations HDLC stands for the higher level data link control protocol and HDLC is the cisco proprietary, no support the authentication, no support the compression and error correction and on the other hand PPP stands for the point to point protocol it is a standard protocol and support the authentication, support the compression and error correction .
19) What is convergence ?
Convergence is "to complete the routing table" in other words when each and every ip in the topology is pingable, reachable, and accessible.
20) What are the methods of the routing ?
There are the three methods of the routing that are following :
Static Routing
Default Routing
Dynamic Routing
21) What are the two link state state protocols ?
OSPF (Open Shortest Path First).ISIS (Intermediate System To Intermediate System).
22) How many routers can be managed by the RIPv1 and on which layer RIP work?
Routing Information Protocol is the protocol that can managed the 16 routers means the maximum hops of this protocol is 15. This protocol is the network layer protocol that is work on the application layer.
23) What is split horizon ?
Split Horizon is the built in functionality in Routing Information Protocol to avoid loops basically it is the solution of loop that works like that if one router transmit the advertisements than this router will not receive that advertisements.
24) What is the Multicasting address in RIPv2 ?
The multicasting address in RIPv2 is 224.0.0.9
25) What happen if segments are lost ?
If segments are lost because of the congestion the receiver will acknowledge the last received sequential segment and reply with the reduced window size.
26) What is the original and commercial range of the class A ?
The original range of the class A is 0-127.
The commercial range of the class A is 1-126.
27) What is policy Based Routing ?
Policy based routing can be used to change the next hop IP address for the traffic matching certain criteria. This can be useful to overrule your routing table for certain traffic types.
28) What is difference between the OSPF and ISIS ?
In OSPF
Process ID (Must and Integer).Router ID (Highest IP Priority)Wildcard Bits.Area ID(one router may belongs to multiple areas.
In ISIS
Area Tag (Optional and Alphanumeric).System ID (MAC address and not selected automatically. Wildcard Bits (Not Applicable)Area ID (Globally configured because a router must be in same area)
29) What is Pseudonode in ISIS ?
The DIS is responsible for creating a pseudonode and that is a virtual node created by DIS there are teo responsibilities of the Pseudonode:Create and update a pseudonode LSP that reports links to all neighbours.Create a CSNP (Complete Sequence Number Protocol).
Fig 2:
Pseudonode
30) What are the three types of router in ISIS and describe it roles ?
There are three types of the routers in ISIS:Level 1 (intra area router ) Level 2 (intra area router and it is backbone router).Level 1-2 (has both role)
31) What is dead interval ?
Every X seconds we are going to send a hello packet and if we don't hear any hello packets from our network for X seconds we declare you "dead" we are no longer neighbors. All other routers who are your neighbors are specified in the hello packet.
32) What are the OSPF LSA Types ?
OSPF uses a LSDB (link state database) and fills this with LSAs (link state advertisement). Instead of using 1 LSA packet OSPF has many different types of LSAs.
LSA Type 1: Router LSA
LSA Type 2: Network LSA
LSA Type 3: Summary LSA
LSA Type 4: Summary ASBR LSA
LSA Type 5: Autonomous system external LSA
LSA Type 6: Multicast OSPF LSA
LSA Type 7: Not-so-stubby area LSA
33) What is stub area flag ?
Stub area flag: Besides area numbers OSPF has different area types. Both routers have to agree on the area type in order to become neighbors you will become neighbors.
34) Available Subnet 10.1.0.0/16 required hosts 2000 hosts per subnet.
What is new subnet mask ?
What is number of network ?
What are the subnets ranges ?
10.1.0.0
255.255.0.0
11111111.11111111.00000000.00000000
11111111.11111111.11111000.00000000
2^11=2048 Eleven host bits have been saved.
New Subnet Mask =255.255.248.0
8 is the increment 2048-2 =2046 hosts in one subnets.
2^5 = 32 networks
Subnets Ranges
10.1.0.0-10.1.7.25510.1.8.0-10.1.15.25510.1.16.0-10.1.23.25510.1.24.0-10.1.31.255And so on.
35) Which feature of BGP is for loop avoidance ?
AS-Path is the feature of the Border Gateway Protocol that is use for the loop avoidance and this feature avoid loop like that when one route originated it specify all the AS number where the route come from and if router receive the route that originated by itself then router not accept it.
36) What is AD values of EBGP and IBGP ?
Administrative distance of EBGP is 20.
Administrative distance of IBGP is 200.
37) What are steps in MPLS Domain ?
There are three steps in MPLS domain:
Label insert.
Label swap.
Label pop.
38) What is difference between the FIB and LFIB ?
FIB stands for the Forwarding Information Base and in the FIB there are multiple information like :
Pre Build Cache.
Adjacencies Table.
Label Information.
LFIP stands for the Label Forwarding Information Base and in LFIB only label information exist.
39) What is frame relay ?
Frame relay is the packet switching technology and it is used to bind the two or more than two routers with a single interface and it mostly used in the Internet Service Provider Side and it is not very costly.
40) What is Ethernet Channel ?
Ethernet Channel is also known as the link aggregation. Basically it is a process of bundle the ports together in an ethernet to achieve the highest bandwidth so the purpose of the ether channel is acquire bandwidth that is the highest.
1 note
·
View note
Text
IPv6 Explained
Please note that most of these screen shots are coming from the Cisco Networking Academy's IPv6 Addressing and Subnetting Workbook, 1st edition, pages 1–12. Some of the screen shots I’ve inserted are simply text, because I felt I couldn’t have said some parts of this any better or more succinctly. That workbook was such an amazing resource for me and I hope it helps you too.
First, a short historical story:
From 1973 to 1978, TCPv1-3 were rolled out. IP was apart of TCP until 1978, when they were split, so we then had IPv3 and TCPv3. In 1980, RFC 760 defined IPv4, thought it wasn’t defined as we know it today until a year later. Currently you can find that under RFC 791 through 793. Then:

Ipv5 was an experiment in 1990 never released to the public. In 1992 hosts (the people using the internet) were over a million in number and we were running out of addresses to give them so they’d all be identified uniquely. Something had to be done! First introduced as “IP Next Generation” and defined in RFC 1883, IPv6 swept onto the scene in 1995. For reference, so far every 3 years the number of people using the internet has gone up times 10%, but true to exponential fashion, by 1997, the number jumped times 19%. By 1998, IPv6 had been fully developed and it’s current definition can be read in RFC 2460.
Version 4 and 6 work in much the same way but there are many more possible version 6 assignments. They both have multicast and loop back addresses. IPv6 can translate and transition a host from IPv4 using what’s called an IPv4 Embedded Address. The low order 32-bits of the IPv6 address have the IPv4 in them. So a user may be using IPv6 already and not know it because the internet protocols do all the translation for them!
Here is more information from the workbook that helped me a lot when I was first introduced to IPv6:


IPv6 can use the following routing protocols:
RIPng (RIP New Generation) - This routing protocol uses “hop” counts to determine how to route a packet. A hop is like a jump to a device. So if my packet went from the server to a router to a tablet, it “hopped” twice. As the packet “hops” it’s hop count will go down. If a packet runs out of hops, it will get dropped. RIPng updates every 30 seconds and uses UDP to route. It���s multicast address is FF02::9.
OSPFv3 – Open Shortest Path First was made to replace RIP. It’s classless, link-state routing, supports VLSMs, and works off a hierarchical domain segregated into areas. We talked about this a lot last discussion, with the Border Routers, the backup border routers, “cost” being numerically assigned to routes to decide paths for packets, etc.
EIGRP – Enhanced Interior Gateway Routing Protocol, an improvement on IGRP, and is classless, so it supports VLSMs. This protocol uses some distance vectors and some link-state components to route. It automatically “summarizes” a boundary, though that can be turned off. EIGRP has neighbor tables, topology tables, routing tables, and each routed protocol gets each of those three for itself! This way, all the routers can keep track of all the routes. EIGRP can handle lots of different kinds of protocols, including IPX and AppleTalk.
IS-IS - This was made for the OSI suite to route connectionless network protocol data. It works sort of like OSPF, in that it has domains and areas, but how it sets up the routing between them all is a bit different. It’s got the areas connecting to a “backbone” of routers, and all routers in the network have a level assigned to them. “OSI defines Level 1, Level 2, and Level 3 routing. Level 1 (L1) ISs (routers) communicate with other L1 ISs in the same area. Level 2 (L2) ISs route between L1 areas and form a contiguous routing backbone. L1 ISs only need to know how to get to the nearest L2 IS. Level 3 routing occurs between domains.” (Camput Network Design Fundamentals, 2017.)

MP-BGP4 (multiprotocol BGP-4) - This protocol uses path vectors, based off of a sort of hop count called “Autonomous System” or AS number to route addresses. It’s the exterior routing protocol, EGP, for the internet! You can use it inside your network if you wish as well, but anything leaving your domain will use this out in the wilds. BGP uses TCP to find its “peers”, which are the same as “neighbors”. It also supports VLSMs and CIDR addressing.
Like IPv6, IPv4 can also use EIGRP, OSPF, IS-IS, and BGP4, but uses RIPv1 or 2, and IGRP as well.
There are a few different types of IPv6 addresses: global unicast, uniquely local, and link-local IPv6 addresses. To explain them, let’s define these terms with their examples.

Global unicast: these addresses are only for ports or a public address. So a website can have one. They are made up of two parts: the subnet ID and the interface ID. The subnet ID is going to have the site prefix in it, along with, obviously, any subnet identification from that site. The Interface ID will be the interface MAC address. These addresses can time out.

Uniquely local: As the name implies, these addresses aren’t meant to leave their domain. They’re internal addresses. You make one by adding a random 40-bit hexadecimal string to the end of “FD00::/8”. It’s got a subnet and interface ID the same way a global IPv6 does.

Link-local: These never time out. This is used to single-link actions, like discovering a neighbor, or automatically configuring an address. If IPv6 is enabled for an interface, it’ll have a link-local address. Like the uniquely local addresses, they can’t leave the domain.
One more important thing you'll need to know: How to compress and shorten IPv6 addresses. There are only two rules to keep in mind when condensing IPv6 addresses.
Rule 1: you don't have to write “leading zeroes" in each hextet. So a hextet that’s :0065: could just be written as :65:
Rule 2: you may choose one group on zeroes to be written as double colons “::”. Pick the largest string of zeroes to do this to.
Here are some examples:

Need some videos to help you through? Try these:
https://www.purevpn.com/blog/what-is-ipv6-address-scty/
https://whatismyipaddress.com/ip-v6
https://www.pcworld.com/article/257037/ipv6_five_things_you_should_know.html
Internet Protocol - IPv4 vs IPv6 as Fast As Possible
IPv6 Introduction - What is IPv6? Why do we need it? How to get IPv6 addresses?
---------------------------------------------------
Sources
IPv4 Routing Protocols | Campus Network Design Fundamentals. (2017). Flylib.com. https://flylib.com/books/en/3.293.1.31/1/
IPv6 routing protocols. (2016, January 26). Study-Ccna.com. https://study-ccna.com/ipv6-routing-protocols/
Jones, R. (n.d.). IPv6 Addressing and Subnetting Workbook (1st ed., pp. 1–12) [Review of IPv6 Addressing and Subnetting Workbook]. Cisco Networking Academy.
Understanding IPv6 Link-Local Address. (2011, December 13). Community.cisco.com. https://community.cisco.com/t5/networking-videos/understanding-ipv6-link-local-address/ba-p/3103152
upravnik. (n.d.). IPv6 global unicast addresses. Retrieved February 26, 2021, from https://study-ccna.com/ipv6-global-unicast-addresses/
upravnik. (n.d.). IPv6 unique local addresses. Retrieved February 26, 2021, from https://study-ccna.com/ipv6-unique-local-addresses/
upravnik. (n.d.). RIPng. Retrieved February 26, 2021, from https://study-ccna.com/ripng/
0 notes
Text
The MySQL Clone Wars: Plugin vs. Percona XtraBackup
Large replication topologies are quite common nowadays, and this kind of architecture often requires a quick method to rebuild a replica from another server. The Clone Plugin, available since MySQL 8.0.17, is a great feature that allows cloning databases out of the box. It is easy to rebuild a replica or to add new nodes to a cluster using the plugin. Before the release of the plugin, the best open-source alternative was Percona XtraBackup for MySQL Databases. In this blog post, we compare both alternatives for cloning purposes. If you need to perform backups, Percona XtraBackup is a better tool as it supports compression and incremental backups, among other features not provided by the plugin. The plugin supports compression only for network transmission, not for storage. But one of the plugin’s strong points is simplicity. Once installed and configured, cloning a database is straightforward. Just issuing a command from the destination database is enough. Percona XtraBackup, on the other side, is a more complex tool. The cloning process involves several stages: backup, stream, write, and prepare. These stages can take place in parallel: we can stream the backup to the new server using netcat and, at the same time, we can write it into the destination directory. The only stage that is sequential is the last one: prepare. Test Characteristics We used sysbench to create 200 tables of 124Mb each for a total of 24Gb. Both source and replica virtual machines run 4 cores, 8 Gb RAM, and 60Gb storage. We created the disks on the same datastore. During the tests, we did not generate additional operations on the database. We measured only the clone process, reducing the benchmark complexity. Otherwise, we would have to take into consideration things like application response time, or the number of transactions executed. This is beyond the scope of this assessment. We tested different combinations of clone and Percona XtraBackup operations. For XtraBackup, we tested 1 to 4 threads, with and without compression. In the case of compression, we allocated the same number of threads to compression and decompression. For the clone plugin, we tested auto (which lets the server decide how many threads will perform the clone) and 1 to 4 threads. We also tested with and without compression. Finally, we executed all the tests using three different network limits: 500mbps, 1000mbps, and 4000mbps. These make a total of 54 tests, executed 12+1 times each. All times are in seconds. In the graphs below, lower values are better. Method Clone Out of the required parameters to operate the clone plugin, the following were set up accordingly in the recipient server: clone_max_concurrency= Defines the maximum number of threads used for a remote cloning operation with autotune enabled. Otherwise, this is the exact number of threads that remote cloning uses. clone_autotune_concurrency If enabled the clone operation uses up to clone_max_concurrency threads. The default is 16. clone_enable_compression If enabled, the remote clone operation will use compression. Percona XtraBackup To stream the backup we used the xbstream format and sent the data to the remote server using netcat. We applied the following parameters: parallel= Xtrabackup and xbstream parameter that defines the number of threads used for backup and restore operations. rebuild-threads The number of threads used for the rebuild (prepare) operation. decompress_threads and compress_threads Xtrabackup and xbstream parameters that define the number of threads used for compression operations. Some people use additional parameters like innodb-read-io-threads, innodb-write-io-threads, or innoDB-io-capacity, but these parameters only affect the behavior of InnoDB background threads. They have no impact during backup and restore operations. Results Clone No compression For the lower bandwidth tests, the number of threads used does not make a difference. Once we increase bandwidth we see that time cuts by half when we move from one thread to two. Going beyond that value improves slightly. Probably we reach the disk i/o limit. The auto option is consistently the fastest one. Compression Compression is supposed to improve performance for lower bandwidth connections, but we see that this is not the case. Bandwidth has no impact on execution time and compression makes the clone slower. Again auto gives the best results, equivalent to 4 threads. Percona XtraBackup No Compression Without compression, we see again that the number of threads does not make any difference in the lower bandwidth test. When we increase bandwidth, the number of threads is important, but we quickly reach i/o limits. Compression When using compression, we see that requires less time to complete in almost every case compared with the option without compression, even when bandwidth is not the limit. Conclusion We see that, when using compression, the clone plugin is the slower option while Percona XtraBackup gives great results for all bandwidths. Without compression, the clone plugin is faster when using more than 2 threads. XtraBackup is faster for fewer threads. Below, we have a chart comparing the worst and best results. As expected, the worst results correspond to one thread executions. The Clone Plugin is a great option for simplicity. Percona XtraBackup is excellent to save bandwidth and provides better results with fewer threads. With enough threads and bandwidth available, both solutions provide comparable results. https://www.percona.com/blog/2021/01/19/the-mysql-clone-wars-plugin-vs-percona-xtrabackup/
0 notes