#transfer malwarebyte in new computer
Explore tagged Tumblr posts
Text
New Computer
I have some special news: I got a new computer a few days ago :D a laptop with W10.
I discovered a few years ago that I had some gift cards lying around. When I was younger, my sister and I found them in a parking lot all scattered about. We shared them between ourselves, and after misplacing them and finding them again I had them checked for the amounts. I had 4 of them with varied totals, but it was enough to save up for something. Since you can't exchange them for money, I figured I'd find something worth spending them on. I initially wanted a Switch :D but after a few scares with my old ass W7 desktop, I convinced myself I needed a new computer for emergencies.
The problem is most computers nowadays are hella expensive D: and despite my family thinking I'm tech savvy, I was completely lost on what I wanted or what would be the best. Not to mention the nightmare of transferring stuff from the old computer to the new one.
But some luck fell on my lap, and I partook in a survey that offered me more gift cards for my feedback. Small amounts, but hey, free cards for my funds :D Then Black Friday came along, and I found a seemingly good Dell laptop on sale. It's refurbished and was one of the few I was able to afford with the current fund, so I got it for quite a steal after using up nearly all my cards.
I was pretty anxious at first, but I've come to love my little computer. Bypassing all the bullshit and customizing it wasn't too hard either to my surprise. The real pain right now is transferring some of my stuff over, such as games and art programs, some of which are pirated lol
I got my Photoshop CS5 moved without issue and I'm currently looking for my old version of GIMP 2.6. But the real problem is the fact that I can't install my games such as Sims 3 and Spore, nor my 2010 Microsoft Word+etc. since they require discs and this laptop has no disc drive. Buying an external disc drive is an option since it's fairly cheap, but there's the product keys to consider, and in Word's case I wanna avoid updating it so I don't have to use the bullshit that is Microsoft 365 Office and pay for it. Is that even possible? I have no clue.
There's also my anti virus which has been shit lately. Norton's latest update is a trash fire that nearly overheated my desktop and broke shit, so I'm thinking of dropping them entirely once my sub runs out and going for Malwarebytes or something else instead if they don't get better. I noticed my desktop ran better after I removed both versions of Norton entirely lol while this newest one doesn't impact the start up time much, all the processes running in the background and my loss of control over certain things sours those benefits.
tl;dr I have a personal laptop in case of problems so whenever I start commissions again, I don't have to worry about the desktop fucking up on me :'D Right now I'm setting important stuff up and trying to get used to it. If there's anyone out there that knows something that could help me with some issues I mentioned, I'm all ears.
0 notes
Text
www.malwarebytes.com/install
www.malwarebytes.com/install -With the development of the digital world, online protection is crucial. It is extremely important to protect your PCs, Mac, computers as well as mobile devices and tablets with malwarebytes.com.
It will shield your computer from various threats by detecting and removing viruses in real time. This is done with the use of anti-malware, anti-spyware, and anti-rootkit technology. The software’s auto-scan feature also offers a proactive way to clean up a system.
Download and install Malwarebytes for Windows
To begin utilizing Malwarebytes on your Windows PC, download and introduce the most recent variant of Malwarebytes for Windows. Directions are given underneath to control you through the establishment procedure. These means additionally apply to re-establishment, or how to get back the program if there should arise an occurrence of a coincidental uninstall.
Download the newest version of Malwarebytes for Windows.
Locate the setup file that was downloaded, Mbsetup.exe.
In most cases, downloaded files are saved to the Downloads folder.
Double-click the setup file.
When User Account Control arrives, click Yes.
User Account Control asks permission to install Malwarebytes for Windows.
A screen asks what kind of computer you are installing Malwarebytes on. This choice determines the kinds of Malwarebytes product notifications you will receive periodically. Click either the Personal Computer or Work Computer.
To install Malwarebytes for Windows and agree to the End User License Agreement, click Agree and Install. To choose a different install location, click Advanced Options.
At the point when your Malwarebytes for Windows establishment finishes, the program opens to the Welcome to Malwarebytes screen. Snap the Get started button.
Malwarebytes inquires as to whether you might want to utilize either the Malwarebytes Freeform or the Malwarebytes Premium adaptation. Snap one of the accompanying catches:
Use Malwarebytes Free: To utilize the Malwarebytes Free form. This form just evacuates existing diseases and has no proactive assurance.
Buy Premium: To buy a membership for Malwarebytes Premium and open all assurance highlights.
Guarantee free 14-day preliminary: This catch possibly shows up if it is your first time introducing Malwarebytes on your machine. Snap this catch to open Malwarebytes Premium highlights for 14 days. You should give an email on the accompanying screen to actuate the preliminary.
Initiate License: To include a permit key which enacts a Malwarebytes Premium membership. For additional subtleties, see Activate Premium membership in Malwarebytes for Windows.
When you have decided to initiate a www.malwarebytes.com/install membership, actuate a 14-day preliminary, or utilize the Malwarebytes Free form, you are taken to the primary Dashboard of the program. Malwarebytes is effectively introduced on your Windows gadget.
#www.malwarebytes.com/install#malwarebytes for mac#malwarebytes for windows#reinstall malwarebytes#install malwarebytes with licence key#transfer malwarebyte in new computer
0 notes
Text
What is a Trojan Horse?
Now you know what a Trojan horse is, you’ve seen Trojan horse examples, and know what it can do and how to avoid an attack. An anti-phishing service with link click protection and malicious attachment blocking will help you keep your data safe and your computer free from all kinds of malware.A Trojan horse or Trojan is a type of malware that is often disguised as legitimate software. Trojans can be used by hackers trying to gain access to users' systems. Users are typically tricked by some form of social engineering into loading and executing Trojans on their systems. Once activated, Trojans can enable cyber-criminals to spy on you, steal your sensitive data, and gain backdoor access to your system.
Uses of a Trojan horse
When a Trojan horse becomes active, it puts sensitive user data at risk and can negatively impact performance. Once a Trojan has been transferred, it can:
give the attacker backdoor control over the computing device;
record keyboard strokes to steal the user's account data and browsing history;
download and install a virus or worm to exploit a vulnerability in another program;
install ransomware to encrypt the user's data and extort money for the decryption key;
activate the computing device's camera and recording capabilities;
turn the computer into a zombie computer that can be used to carry out click fraud schemes or illegal actions and
legally capture information relevant to a criminal investigation for law enforcement.
Read more - SearchSecurity.

Common types of Trojan malware, from A to Z
Here’s a look at some of the most common types of Trojan malware, including their names and what they do on your computer:
Backdoor Trojan
This Trojan can create a “backdoor” on your computer. It lets an attacker access your computer and control it. Your data can be downloaded by a third party and stolen. Or more malware can be uploaded to your device.
Distributed Denial of Service (DDoS) attack Trojan
This Trojan performs DDoS attacks. The idea is to take down a network by flooding it with traffic. That traffic comes from your infected computer and others.
Downloader Trojan
This Trojan targets your already-infected computer. It downloads and installs new versions of malicious programs. These can include Trojans and adware.
Fake AV Trojan
This Trojan behaves like antivirus software, but demands money from you to detect and remove threats, whether they’re real or fake.

Game-thief Trojan
The losers here may be online gamers. This Trojan seeks to steal their account information.
Infostealer Trojan
As it sounds, this Trojan is after data on your infected computer.
Mailfinder Trojan
This Trojan seeks to steal the email addresses you’ve accumulated on your device.
Ransom Trojan
This Trojan seeks a ransom to undo damage it has done to your computer. This can include blocking your data or impairing your computer’s performance.
Remote Access Trojan
This Trojan can give an attacker full control over your computer via a remote network connection. Its uses include stealing your information or spying on you.
Rootkit Trojan
A rootkit aims to hide or obscure an object on your infected computer. The idea? To extend the time a malicious program runs on your device.

SMS Trojan
This type of Trojan infects your mobile device and can send and intercept text messages. Texts to premium-rate numbers can drive up your phone costs.
Trojan banker
This Trojan takes aim at your financial accounts. It’s designed to steal your account information for all the things you do online. That includes banking, credit card, and bill pay data.
Trojan IM
This Trojan targets instant messaging. It steals your logins and passwords on IM platforms.
That’s just a sample. There are a lot more...this and more on - Norton.
How You Can Get a Trojan
Unfortunately, getting a trojan virus is as simple as downloading the wrong application onto your computer or mobile device. Even if you never download software, it's still possible to inadvertently transfer one of these malicious applications to your computer.
If you take any of the following actions, you could make yourself vulnerable to a trojan attack.

Click on a link in an email that downloads an application to your computer.
Downloading "free" software from websites that you don't recognize.
Clicking on website pop-up ads.
Downloading files off the dark web.
Sharing or downloading Bittorrent files.
The bottom line is that any time you place a file onto your computer from a website or any other source that you don't recognize, you're putting your computer at risk for a trojan attack...to know more, visit - lifewire.
How to remove trojan malware
Once a Trojan is installed on your computer, the process of removing it is similar to that of removing any other kind of malware — but that isn't easy. CSO has information on how to remove or otherwise recover from rootkits, ransomware, and cryptojacking. We also have a guide to auditing your Windows registry to figure out how to move forward.
If you're looking for tools for cleansing your system, Tech Radar has a good roundup of free offerings, which contains some familiar names from the antivirus world along with newcomers like Malwarebytes...go to - CSO to know more.
Now you know what a Trojan horse is, you’ve seen Trojan horse examples, and know what it can do and how to avoid an attack. An anti-phishing service with link click protection and malicious attachment blocking will help you keep your data safe and your computer free from all kinds of malware.
1 note
·
View note
Text
Why we need to Purchase Windows 10 Pro?
Below is actually a whistle-stop tour with the main differences among both variations to help you you're making that call.
Win10 Home vs Home windows ten Pro: Main features
Glancing about the above table, Home windows ten Property has all you'll need for personal Laptop use. Home wind10 Pro is instead angled towards power people and people who just love small- to medium-sized corporations. Unless you might have an individual need for extra security and business features, you're unlikely to need to Buy Windows 10 Pro. If, on the other hand, you choose to do need people things, you will want to consider Home windows ten Pro's offerings in great detail.

BitLocker
BitLocker is actually a part of encryption software that bolsters Home windows 10's security. Its inclusion while in the Pro edition of Home windows ten targets corporations that could transfer a great deal of sensitive information. A current iteration from it now towards the all-or-nothing way of encryption, with end users to be able to securely retail store encrypted files alongside unencrypted files.
Remote Access Services
Remote Desktop Sessions might be operated with equally Windows 10 House and Windows 10 Pro, but only PCs running the latter can be remotely controlled. For those who have Home win10 House, it could possibly basically assisted remotely - not fully controlled.
Windows Update for Business enterprise
In case you are familiar with Windows Property edition, you will know how Microsoft needs to force patches and updates for your machine automatically. Purchase Windows 10 Pro lets you delayed updates for several months in a time, giving you greater command over what applications are on your own business PCs - and stopping incompatibilities with new updates from hobbling your workflow.
Buy Win10 Pro essentially permits you to run virtual machines, allowing you to run over a person running system all at once for a Personal computer. You will need to have a very CPU that supports virtualization, and may ought to manually install it.
When you tend to make use of your Pc for some get the job done, personal browsing and enjoying games, there is absolutely no pay extra cash for Home windows ten Pro. If you're searching for a functioning system specifically with business in your mind, and can even make definite using of added security and group compatibility features, then Win10 Pro features a handful of boosts about bat roosting areas. Virtually all consumers, nevertheless, probably will not are interested.
For more info:- Buy Malwarebytes
1 note
·
View note
Text
Windows 10 100 percent disk usage 2019 無料ダウンロード.www.makeuseof.com
Windows 10 100 percent disk usage 2019 無料ダウンロード.修正済み:Windows 10タスクマネージャーでディスク使用量が100%

Windows 10 November 2021 Update.Windows 10 のディスク イメージ (ISO ファイル) のダウンロード
Windows 10 の ISO ファイルをダウンロードするためにメディア作成ツールを使用した場合は、これらの手順に従う前に、ISO ファイルを DVD に書き込む必要があります。 Windows 10 をインストールする PC に、USB フラッシュ ドライブまたは DVD を挿入します。 May 25, · Windows Searchは、%のディスク使用量のWindows 10を引き起こすことが知られているプロセスの1つです。Windows Searchが%ディスク使用量の問題の原因であるかどうかを判断するには、Windows Searchを一時的に無効にします。 手順 1 Mar 03, · Windows 10 - % Disk Usage. possible solution did the WIndows +r. entered disables the bits (background intelligent transfer service), superfech, windows search but stayed at % then i noticed the "xbox live auth manager" was ruining i
Windows 10 100 percent disk usage 2019 無料ダウンロード.% Disk Usage in Windows 10? 17 Tips and Tricks to Fix This Issue
Windows 10 の ISO ファイルをダウンロードするためにメディア作成ツールを使用した場合は、これらの手順に従う前に、ISO ファイルを DVD に書き込む必要があります。 Windows 10 をインストールする PC に、USB フラッシュ ドライブまたは DVD を挿入します。 Apr 27, · Ran both browsers Disk usage again climbed to %. I quit the Edge browser. Disk usage gradually fell back to 0%. I can only conclude that the Microsoft Edge browser has a problem on my own, and possibly your computer. Disk usage climbs so high that the computer eventually slows to a crawl and becomes inoperable May 25, · Windows Searchは、%のディスク使用量のWindows 10を引き起こすことが知られているプロセスの1つです。Windows Searchが%ディスク使用量の問題の原因であるかどうかを判断するには、Windows Searchを一時的に無効にします。 手順 1
So your computer is hanging and freezing. Same old Windows, right? Except you're using a brand-new Windows 10 device; you've only had it a few days. So just what is going on? Surely this can't be, right? Sadly, it is. The latest versions of Windows have a problem with the drives being overworked, which slows down the operating system. This issue affects both hard disk drives HDDs and solid-state drives SSDs. When the error was first discovered, only a few culprits were found.
Once you've established that there is a problem, you have several options available. Check the following steps one at a time, checking the disk usage in the Task Manager after each.
Note that even if you find a solution, a Windows Update could reset the changes you've made. Bookmarking this page will help you find it in the future and run through the fixes again.
This performance issue is most obvious when attempting to use Windows Search to find a file or program, and anything else that requires the drive to do some work perhaps copying and pasting a group of files. To establish whether it is a problem that is affecting you, when your computer next slows down, use Task Manager to run a disk check.
Note that this may take some time to open with the drive being under strain. On the Processes tab look for the Disk column.
However, using Windows' built-in disk check can fix this:. Wait while the system scans the drive; a reboot may be required for a full disk repair. This should deal with the error.
As with any performance issue, the first thing to do is confirm that your computer hasn't been infected with malware.
Your security software should be able to deal with this, whether it's a free app or a paid suite. At the very least, tools like Malwarebytes Anti-Malware should be able to scan your system drive and detect any problems. Note that with a heavy load on your drive already this may take a while. If threats are found, use the software's recommendations to discard them and reboot. Next, check your drive's performance again. Hopefully, you've resolved the issue; if not, then malware wasn't to blame, so read on.
A bug in Windows 10 results in a "search loop" that causes an increased load on the system drive. To stop this and prevent it from happening during your current session until Windows is rebooted :. That should solve most issue. If there is no change, even after rebooting, you can permanently disable Windows Search and Indexing. A few moments after disabling Windows Search, your Windows 10 performance should improve considerably.
If not, move on…. Since Windows 10 the Windows 10 October Update this has been renamed to "SysMain. To prevent this service from causing the disk usage issue, open another Windows PowerShell Admin and enter:. Again, wait a few moments to check whether this has had any effect on your computer's performance. You should also run Check Disk in PowerShell:. You'll be informed that your PC must be rebooted for Check Disk to complete, so make sure you have closed all your applications first.
If this doesn't work, it is likely that you're experiencing a frustrating iteration of this issue that is simple to resolve. Flash remains one of the most vulnerable aspects of modern computing and should be disabled. The next thing to do is update to the latest version of Chrome.
If you can't see any of the options, don't worry. It simply means that your version of Chrome has already updated and no longer supports Flash. The obvious option is to choose a different browser. Windows 10 already has two browsers built in. You probably don't want to use Internet Explorer, but Microsoft Edge is an adequate replacement for Chrome. Related: The Best Browsers for Windows. In an era when online collaboration and video meetings is increasing, Skype is a likely culprit.
Since Skype has been more closely integrated with Windows 10, it is a little trickier to deal with. What you can do, however, is stop Skype from running to help determine if it is the cause of the issues. Head back to the Task Manager to see the change. You may also consider finding a Skype alternative. Under Runs at log-in , change the switch from On to Off. Further issues with Skype can also be dealt with in this screen.
You can Repair , Reset , and even Uninstall Skype to aid with your troubleshooting. Some drivers don't run quite as they should in Windows sys driver, which has a firmware bug.
sys intended for storage devices connected to the PC or laptop motherboard via Advanced Host Controller Interface PCI-Express. sys , you could be affected by this bug. Double-click this, then change the Value data: to 0.
Enjoy gaming and have Steam installed? Usually this is due to update delivery, causing the background downloader to get caught in a loop. Clear the Steam cache to fix this. First, make sure you have exited Steam. In this case, use the Windows 10 Task Manager to close the software.
Finally, it's worth considering the impact of diagnostic tracking in Windows When it comes to reducing your hard disk drive usage, it's quicker to simply disable the DiagTrack service. This usually only happens when Windows Update has a problem which is typically due to a file refusing to download.
You have two options here:. Once the update has finished downloading, it's wise to run it as soon as possible. Virtual memory is a combination of RAM and hard disk space and can be responsible for overuse of your HDD. If there isn't enough RAM to perform a task, the HDD is used to supplement the RAM. Data moved to the HDD is then returned to RAM when required.
These numbers can be confusing, so with the first value, rely on the recommended option. For the maximum value, aim for a figure no more than 1. The next step is to clear the temporary files that have been used in the previous virtual memory allocation. The downside, of course, is that your computer will use more power. Thanks to modern processor design this shouldn't be a massive issue. However, notebooks and desktop replacement laptops may take a hit on battery life.
If this isn't a displayed option, you'll need to create your own custom power plan. Click Create a power plan , then choose High performance. Give the plan a name, tweak any personal settings you need then select it as a power plan to use.
Your Windows 10 computer almost certainly uses SATA connections for hard drives, SSDs, and optical drives. If the drivers aren't up to date, the disk usage error can occur. You may need to reboot Windows for this to take effect. Note that if it doesn't work, you can still try this by checking the manufacturer's website for a new driver. This can be installed using the instructions that accompany it.
If disk usage issues can be attributed to excessive disk activity, then it follows there might be a power-related cause. Once plugged into the power adaptor, the issue resolves. Similarly, the problem has been shown to alleviate once a new PSU is installed in a desktop PC. Check our guide to new PC power supply units to help you choose a replacement. You'll have noticed this feature that pops up when you're doing something for the first time with useful tips and suggestions.
Incorrectly identified as a virus or malware, WaasMedicAgent. exe part of the Windows Update Medic Service is a Microsoft system process that checks downloaded Windows Update files.
Disabling the update medic is an extreme step to take. A slow computer is one with a problem, and if you cannot fix it by disabling a browser plugin, stopping services, or running your antivirus software, then the problem may well be hardware related. Try these fixes the next time your Windows computer slows down. Be sure to check your Windows Experience Index periodically to identify performance issues in need of immediate resolution. Want to figure out your computer performance and any immediate bottlenecks?
0 notes
Text
Malwarebytes For Mac 10.8.5 Download
AVG Ultimate 2021 Antivirus+Cleaner+VPN 10 Devices, 2 Years PC/Mac/Mobile Download by AVG. 4.0 out of 5 stars 45. Digital $49.99 $ 49. 99 $99.99 $99.99. Malwarebytes Premium Download by Malwarebytes. 4.0 out of 5 stars 118. Software Download Currently unavailable. Norton 360 Premium 2021 – Antivirus software for 10. Malwarebytes version for mac 10.8.5 please.
Malwarebytes For Mac 10.8.5 Downloads
Malwarebytes For Mac Review
Download Malwarebytes for your computer or mobile device. Whether you need cybersecurity for your home or your business, there's a version of Malwarebytes for you. Try our free virus scan and malware removal tool, then learn how Malwarebytes Premium can protect you from ransomwar.
Mac Os X 10.5.8 free download - Apple Mac OS X Snow Leopard, Apple Safari, R for Mac OS X, and many more programs.
4.8/5(63 votes )
If you search on the internet a Mac OS X Mountain Lion 10.8.5 DMG Files So, you come to the right place now a day shares with you a Mac OS Powerfull operating system latest upgraded Mountain Lion 10.8.5 developed by Apple Inc. In This Version, MAC OS X Mountain Lion 10.8.5 added an exciting new feature to more improve the work and enjoy or also fixed the Bugs in the previous version of Mac. Mac added 200 plus new features just like ma enjoy including iMessage support, Reminders, Notification Center, Notes, Game Center, extensive icloud integration, and much more.
Malwarebytes For Mac 10.8.5 Downloads
The 9th edition of Apple’s OS X series has some exciting, new features to be found. The operating system has definitely been recognized by iOS users since the products were made publicly accessible on July 25, 2012. OS has come up with many new features and improvements to make some immediate changes and still is available for purchase in the Apple App Store. Hall and oates x static rar. In reality, the big cat version is designed to offer new features and refining of how tabs appear, manage the media and browse things.

Mac OS X Mountain Lion 10.8.5 OverView:
Fixed screen saver, as well as addressed mail problems in this release, are also made. Additionally, there is the reliability of Xsan, the transfer of huge files across an Ethernet, authentication of the Open Directory Server and many other changes to enable the system to deliver better network performance. Security vulnerabilities also exist in the areas discovered by the following: Installer, Kernel, IPSec, Mobile Device Management, PHP, PostgreSQL, OpenSSL, Power Management, Screen Lock, QuickTime, and kudos: Apache, Certificate Trust Policy, Bind, ClamAV, ImageIO, CoreGraphics, and others. On final notes, the stable and best operating system is Mac OS X Mountain Lion 10.8.5.
Likewise, the one among the most popular features held in the “Dictation,” a voice transcript that lets you speak in the field provided and get your wanted text written and then is translated into different languages (subject to your own) through the server. What was new to Mountain Lion is the theme of hundreds of features, whereas we want to highlight some of the striking ones: the improved promise on safety and privacy, which fulfills the need to “Disable automatic login” and allow applications to be downloaded from the official Apple store or from the “identified developer.”
OS X 10.8 Mountain Lion is Mac’s most recent OS for Apple. It brings OS X much closer to iOS when it comes to features and iPad and iPhone synchronization. We have already described the major changes in Mountain Lion, most of which are features taken from iOS. We will take a closer look at Mountain Lion’s features here. It includes all features and updates for the OSX 10.8.2 Mountain Lion plus system-specific enhancing and fixing of the late 2012 systems. The updated Apple OS X Mountain Lion is recommended for all 13″MacBook Pro with a retina display, 21.5 “iMac (late 2012) and Mac mini (late 2012) systems. you can also check out the Mac OS X Snow Leopard DMG.
Features Of Mac OS X Mountain Lion 10.8.5
Auto-save to access previously saved part/version of content.
AirPlay Mirroring to stream the media you desire.
Improved notification center.
Game center was being introduced.
No way to get malware in action, while Gatekeeper is awake.
Safari latest was being added with Chrome like browsing.
The iCloud library is there to provide you a substantial place to get your important data saved.
Automated application updating facility.
Integration of Twitter with mail contacts and publishing to other social media, directly.
Power Nap to put Mac in action, while in sleep mode.
A stable operating system for your Apple device
Various security enhancements and issues fixes
Better performance of MacBook Air
fixes for Smart Card and screen saver issues
AFP file transfer performance over 802.11
Sending huge data over the ethernet
Much More…………………./
Mac OS X Mountain Lion DMG Technical Setup Details
Software Full Name: Mac OS X Mountain Lion
Setup File Name: Mac_OS_X_Mountain_Lion_10_8_5_Official.iso
Full Setup Size: 4.2 GB
Setup Type: Offline Installer / Full Standalone Setup
Compatibility Architecture: 32 Bit (x86) / 64 Bit (x64)
Latest Version Release Added On: 24th Mar 2019
System Requirements For Mac OS X Mountain Lion

8 GB free HDD
2GB RAM
Core 2 Duo Intel Processor
Malwarebytes For Mac Review
Download Free Mac OS X Mountain Lion 10.8.5 DMG Full Version
0 notes
Text
Format Flash Drive Mac Os X
How to format internal and/or external drive to work properly on Mac and Windows computers?
You can easily format (erase) any USB drive in Mac OS X with the Disk Utility app, we'll demonstrate this with a flash drive that will format as Mac OS forma. To format a flash drive on a Mac, plug in the drive and open the 'Applications' folder, the 'Utilities' folder and then 'Disk Utility.' Your flash drive should be listed in the left menu.
External data storage devices such as USB flash drives, external Hard Disk Drives (HDDs), and Solid State Drives (SSDs) provide one of the easiest ways to transfer files between separate computers without accessing the Internet. This option is often used when attempting to move very large files. The method is also chosen by people who work with media data that imposes various limitations and automatic optimizations when transferring via Internet. Despite the advantages of using external data storage to transfer content, some experienced users encounter problems caused by the difference between operating systems. This article addresses these issues.
A common issue discussed by users within various technical support forums is that of USB flash drives not working on their computers. This is a cross-platform problem that Windows and macOS users often experience. For example, a photographer may provide you with a USB flash drive with stored photos and videos from your birthday party, but you cannot access them on your system. This is the result of differences between operating systems on computers. Windows and macOS use separate file system formats. PCs with Windows operating systems use New Technology File System (NTFS) while Macs with macOS operating systems use Hierarchical File System (HFS+). By default, USB flash drives and external storage are formatted with the NTFS file system - this works flawlessly on PCs, while Mac computers are able to read data in the format, but struggle to write using this type of storage. Fortunately, there is a simple solution: format your external storage with the File Allocation Table (FAT32) or Extended File Allocation Table (exFAT) file system. In this article, we describe the differences between these two file systems and how to format external storage using a Mac computer.
Table of Contents:
It is recommended to run a free scan with Malwarebytes - a tool to detect malware and fix computer errors. You will need to purchase the full version to remove infections and eliminate computer errors. Free trial available.
Which file system to choose - FAT32 or exFAT?
As mentioned above, both file systems are compatible with Windows or macOS/OS X operating systems. Naturally, the question is: which should you choose? To make the choice easier, we describe both file systems and their features below.
Starting with FAT32 (on a Mac, known as MS-DOS (FAT)), this file system is fully compatible with all versions of Windows and Mac operating systems. Therefore, even the oldest versions of operating systems such as Windows XP SP1 and OS x 10.5 Leopard are compatible. As well as computers, the FAT32 file system is supported by PlayStation 3, Xbox 360, and most cameras. This particular file system does contain file size restrictions. For example, the maximum size of supported files is 4GB (you cannot write files larger than 4GB). Also, you cannot create a startup drive for Mac computers within storage media that uses the FAT32 file system. If, however, you are not planning to use external storage to transfer large files or create any executable partitions (such as a Mac startup drive) the FAT32 file system might be an option, since this format is supported in all versions of the operating system.
exFAT is a newer file system format and has the biggest advantage when compared with FAT32: there are no restrictions on file or partition sizes stored. Therefore, you can write a file of, for example, 1TB size and create partitions of 5TB within the device. Despite this improvement of available data size, some older versions of operating systems are no longer compatible with this file system format. The oldest versions of operating systems compatible with exFAT are listed below:
Mac OS X Snow Leopard 10.6.5 or later
OS X Lion
Windows XP SP2 or later (with an additional update for exFAT support)
Windows Vista SP1 or later
Windows 7
Unfortunately, as well as some old versions of operating systems, the exFAT file system format is not supported by various cameras, video games consoles, and other devices able to read and/or write to external storage. If you will be using a USB flash drive or external storage device with any of these, the required format is FAT32. Otherwise, if the device is to be used only with computers with modern versions of operating systems, the recommended format is exFAT.
Format the drive with Mac computer
Firstly, bear in mind that formatting the drive will erase all content stored on it. Mac computers are capable of formatting any storage device (internal or external) such as HDD/SSD, USB flash drive, and external storage. Even if the Mac is unable to mount the storage, following this method will enable you to format the storage. Begin by connecting the storage device to your Mac, and then launch Disk Utility using Spotlight. Simply use the keyboard shortcut of Command and Spacebar, type Disk Utility, and then press return. Alternatively, open Finder and go to Applications, open Utilities, and then launch Disk Utility. Select the drive you wish to format from the list in the left sidebar of the Disk Utility window.
Then click the Erase button at the top of the window, in the new pop-up window, and type the name of drive. Then click the drop-down menu beside Format and select MS-DOS (FAT) - the FAT32 file format - or exFAT. These formats are described above.
If you are not planning to use this drive as the Windows startup disk or use it with the oldest version of the operating system, do not change the Scheme. Select Master Boot Record.
Finally, when all preferences are set, click the Erase button. The formatting process duration depends on size and type of the drive. A hard disk drive will take longer to format than a flash drive. NOTE: formatting will erase all existing data on the drive.
Video Showing how to format drive for Mac and Windows computers
For Apple Mac users, there are two ways to format USB flash drive to FAT32, including Disk Utility and Terminal command line. Refer to detailed steps of using both tools for FAT32 format. Formatting would erase data completely, make sure that you have a data backup. Otherwise, you can use data recovery software to recover data from a formatted USB drive.
Are you looking for a secure way to format USB to FAT32 on Mac? You are at the right place. Follow here, you can find two methods that will assist you in doing so on your storage device. And if you lost data during the formatting, reliable Mac file recovery software is ready to help anytime:
Workable SolutionsStep-by-step TroubleshootingMethod 1. Use Disk UtilityConnect USB to Mac > Go to Applications > Utilities > Disk Utility > Select USB and click 'Erase'...Full stepsMethod 2. Use Terminal CommandConnect USB to Mac > Hit cmd + space keys > Type terminal and hit Enter...Full stepsBonus Tip. Recover Formatted DataIf you lost data due to formatting, run EaseUS file recovery software > Scan and recover formatted data...Full steps
How to Format a USB Flash Drive with Mac to FAT32
Computer users who use a USB might have the demand for formatting it to the FAT32 file system. Compare with the other commonly used NTFS file system on a flash drive, FAT32 has a compatibility advantage across many operating systems.
It's a universal format that is compatible with Mac OS X/macOS, Windows, Linux, and DOS systems. So, if users anticipate using the flash drive with more than one operating system, they will definitely benefit from the FAT32 file system. For Apple Mac users, there are two ways to format a USB flash drive to FAT32, namely Disk Utility and Terminal command line. Below are the detailed steps of the FAT32 format with both methods.
Method 1. Format FAT32 on Mac (Disk Utility)
To format USB to FAT32 with Disk Utility will erase all data on the flash drive, so before you doing so, please do remember to check whether you have saved useful data to another secure device in advance.
To format the USB drive to FAT32, follow the next steps:
Step 1. Connect the USB flash drive to your Mac computer.
Step 2. Go to Applications >Utilities > Double click and open Disk Utility.
Step 3. Select your USB flash drive on the sidebar, choose Erase.
Format Hard Drive For Mac And Pc

Step 4. Rename the USB flash drive (optional).
Step 5. Choose the format as MS-DOS (FAT) for Format, Master Boot Record for Scheme. Then click Erase.
Wait for the process to complete, then you'll get an empty new USB flash drive with FAT32 as the file system. You can use it for saving data again.
Method 2. Format FAT32 on Mac (Terminal Command Line)
The command-line behavior does the same way to erase data with the Disk Utility. Again, create a backup before taking this action.
To format FAT32 on Mac with Terminal, follow the next steps:
Step 1. Connect the USB flash drive to your Mac computer.
Step 2. Hit cmd + space to run Spotlight, type: terminal, and hit Enter.
Step 3. Type: diskutil list and find out which disk is your USB drive.
Step 4. Type: sudo diskutil eraseDisk FAT32 MBRFormat /dev/disk2.
sudo gives you user right.
Diskutil calls disk utility program.
eraseDisk commands to format.
FAT32 sets the file system.
MBRFormat tells disk utility to format with a Master Boot Record.
/dev/disk2 is the location of the USB drive.
Wait for the process to complete. After this, you can type 'diskutil list' in the command again to check if the formatting has been successful.
Bonus Tip: How to Recover Data from Formatted USB
Formatting the USB would erase the data on it completely, so please make sure that you have a backup. If you don't, you can count on data recovery software to retrieve the lost data.
Format Flash Drive Mac Fat32
EaseUS Data Recovery Wizard has both Windows and Mac versions, so it's a good choice for data recovery, no matter you're using a PC or Mac. For Mac users, it only takes a few clicks for the software to scan and display the formatted data. To guarantee an effective data recovery without spending money to no avail, you can install the Mac data recovery free version for the first trial. You can preview all the found data before the final recovery.
To recover data from a formatted USB flash drive on Mac, follow the next steps:
Step 1. Correctly connect your USB flash drive to your Mac. Launch EaseUS Data Recovery Wizard for Mac. Start selecting the flash drive and click 'Scan' to let the software search lost files on it.
Mac Flash Drive To Pc
Step 2. After a quick scan and deep scan, all files will be presented in the left panel in the scan results.
Best Flash Drives For Macs
Step 3. Select files you want to recover and click the 'Recover Now' button. Don't save the recoverable files to the USB drive itself in case of data overwriting.
0 notes
Text
Kaspersky Coupon
Two kits revolve around weight loss, and the other two around weight maintenance. It also helps if you keep yourself updated on the facts. It's crucial that you do not run or install a software program on the disk drive with which you are facing data loss issues. Many doctors recommend building strength before attempting to add aerobic work to an exercise routine for heart disease patients. Belgium (47%) and Luxemburg (49%) were the most satisfied. For example a skydiving company would do everything in their power to upsell pictures or Kaspersky promo 2018 videos. If MalwareBytes' prompts you to reboot, please do not do so. Further, the much hyped virtualization technology, which allows companies' business application to be managed by host's hardware, will be a key in securing virtual movements on the servers. Lastly, if you're feeling absolutely drained and you really feel as though you can't gather the energy to total your training for the day, just make it simple. It is recommended that you scan your computer regularly each week, to confirm that it does not have any computer viruses, worms, Trojans or other infections. Look over the features advertised by the company and make sure they are adequate to your needs. Whatever specific problems you or your sales Kaspersky coupon 2018 team are encountering in producing the level of sales you need, the first step to the sales process is the SMART step you must know what you are trying to achieve, and with good sales training courses you Kaspersky promo code can achieve it. As the world turns into a global village with innovations in technologies and communication modes, the logistics industry is also developing strategies to remain ahead in the race. Mac computers have a great reputation for being resistant to malicious system attacks from viruses and other Kaspersky promo malware, but many Mac users don't realize that their computers are still susceptible to normal wear and tear. Once the prerequisites are met, Kaspersky coupon Bitdefender will inform you of the encryption status of your chat Kaspersky discount coupon 2018 session through messages displayed in the chat window. By looking at your logo image, will they be able to guess what the company products/services are. It helps your metabolism by boosting the metabolic function of your white adipose tissue and guarding against type II diabetes. It is only with the right knowledge and the best antivirus protection software that Internet users everywhere can beat online bugs for good. You should expect that your path to promotion Kaspersky discount coupon will be Kaspersky discount 2018 a curving and sometimes rough road. They can be easily satisfied if you make information searching in your site as simple and fast as possible. Swimming is also easier on people who have joint or muscle pain. A company manufactures a product to sell it in the market. Download the Mozilla browser and surf the web with confidence. Your computer will run faster after using this program. The key thing with e-commerce websites is that security is crucial. You can install avast free software on your machine to gain at least the basic protection for your digital assets. One of the most important things you Kaspersky promo code 2018 can do to ensure that your web videos receive optimal online exposure, is to take full advantage of emergent video SEO techniques. It is an easy to use and it is a simple service. The skin is comprised of connective tissue that gives it elasticity. A domain Kaspersky coupon code 2018 name transfer can in fact refer to two detach and Kaspersky coupon code unique domain name transactions. This particular brand-new aspect will probably be productive by simply default. The better news in hardly anyone in sales has any idea of the power it can bring your business. Use CAD bathroom software to plan your room to its exact dimensions so you can properly work out which fixtures look best where and how you can create the most space in your bathroom. Once the phone has been registered, the program will obtain a copy of the information that the phone sends Kaspersky discount normally and store it for you on the website. However, terrorists have been trying to kill us long before anyone ever heard of George W. Dads might like to see their daughters raking the leaves, mowing the lawn, or polishing their golf clubs. Marijuana Facts: Marijuana, is similar to other stimuli which is available in varying levels of potency. There is no doubt that support provided by Microsoft is the best, apart from the rest.
1 note
·
View note
Video
youtube
Lenovo IdeaPad L340 15.6" FHD Gaming Laptop Computer, 9th Gen Intel Quad-Core i5-9300H up to 4.1GHz, 16GB DDR4 RAM, 512GB ...https://ift.tt/32trOUP #Gamer #Game #Gaming https://ift.tt/32trOUP - Lenovo IdeaPad L340 15.6" FHD Gaming Laptop Computer, 9th Gen Intel Quad-Core i5-9300H up to 4.1GHz, 16GB DDR4 RAM, 512GB ... I checked the screen, keyboard, and just about everything else. The double tap gesture isn't working currently but the computer is downloading a lot of updates so it could be that. Very pleased with it. Box was not tampered with at all, factory sealed. Unlike other Amazon purchases of laptops that Ive done recently, this one was excellent in every way. First, it arrived a day early - unexpected and a nice bonus. The Lenovo box was sealed with the original Lenovo seal; everything was in perfect condition. The laptop booted up with no issues, and the Windows 10 setup went without a hitch. Screen performance, boot speed, general overall performance was more than excellent - really fast stuff. The backlit keyboard is nicely sensitive, and the keys feel solid and reliable, not flimsy at all. I did discover one very minor thing - the top of the laptop (where the keyboard and mouse pad reside) was slightly up on one side toward the corner. A small amount of pressure, and it snapped into place 100% solidly, no issues. Laptop is quiet, though you can hear the fan ramp up during heavy workloads, such as windows patches, etc. The Nvidia graphics chips provide excellent performance. I ran the Lenovo Experience program and got all the current Lenovo updates for the laptop (including a bios update) with no problems. Following that, I did all the Windows updates as well. (Those took some time, but thats Windows for ya.) Installed my product preferences (Got rid of that nasty McAfee garbage and put in Webroot and Malwarebytes, a fantastic damn-near bulletproof combination.) I then transferred my wifes profile from her old laptop to the new one using the Lenovo transfer product, which worked like a charm. Great experience overall. Strongly recommend this specific product and vendor/supplier. Thanx for watching my review presentation. Dow you want to buy it? then link is in description. As an Amazon Associate I earn from qualifying purchases. Thank you for your support. by Shopping Reviews
0 notes
Text
New Details Emerge on the Ransomware Attack Against Epiq Global
On Monday, this blog broke the news that Epiq Global, the international e-discovery and managed services company, had taken its systems offline globally after becoming the target of a ransomware attack.
Now, new details are emerging about exactly what happened to force Epiq to shut down its systems.
The information security and technology news publication Bleeping Computer, citing a source in the cybersecurity industry, is reporting that Epiq was attacked by the Ryuk ransomware and that the company took its systems offline Saturday after the ransomware was deployed and began encrypting devices on its network.
According to the website Crowdstrike, Ryuk is specifically used to target large enterprises for high-ransom returns. Malwarebytes reports that the group behind Ryuk typically seeks ransoms in the range of $97,000 to $320,000.
Epiq has not said whether it has paid a ransom.
The Bleeping Computer report says that the attack against Epiq started in December when a computer on its network was infected with the TrickBot malware, probably through a phishing email.
TrickBot first harvests data from the compromised computer and then tries to spread throughout a network to gather more data. When done, it then opens a reverse shell to the Ryuk operators, who are able eventually to deploy the ransomware.
Investigation Required
On Monday, Epiq told me that there was no evidence that the attack had resulted in any unauthorized transfer, misuse or exfiltration of any data. But security expert Brett Callow, says Epiq cannot really know that at this point.
Callow, a threat analyst with Emsisoft, a cybersecurity company that is also an associate partner in the No More Ransom Project, an initiative between multiple law enforcement agencies and the private sector, said only a full forensic investigation can determine whether data was compromised.
“Such comments are fairly typical, but they’re usually meaningless platitudes,” Callow said. “It’s like you walking into your burglarized home and, after briefly glancing around, saying, ‘Well, I don’t think anything was taken.’ Working out what did or did not happen during a ransomware incident requires a full forensic investigation that can take several weeks.”
Even so, Callow said that it is unlikely data was exfiltrated, because the Ryuk group is not known to be one that steals data.
For Callow, a major concern is that companies are not reporting or disclosing ransomware attacks. Delays in notifying customers that their data may have been breached can give criminals time to hit unsuspecting third parties with spear-phishing attacks and other forms of fraud.
“Folks’ tax returns and veterans’ PTSD claims are being posted online, and these people have no clue that they’re sitting ducks for identity thieves because the companies haven’t told them,” Callow said. “Similarly, I suspect that the groups are using the stolen data to spear phish other companies.”
Comparison to Coronavirus
David Carns, a former technology director at and technology consultant to law firms who is now chief revenue officer at Casepoint, said his company’s contracts with clients expressly provide that it will notify them of breaches.
He also agreed with Callow that the full implications of the attack cannot be determined without a full investigation. “There needs to be a full forensics investigation. We’ve learned long ago that, whenever there’s a crisis, declarations of success should be slow to come.”
Carns believes that ransomware attacks against e-discovery or legal technology companies are rare, especially against companies of the magnitude of Epiq. In fact, he says this is the first such attack he knows of involving a major SaaS e-discovery provider.
Still, Carns sees parallels between the current coronavirus crisis and the rise in ransomware attacks.
“The two have something in connection, in that they shed light on the need for good hygiene in general, and good cyber-hygiene in particular,” he said. “No system is immune from attack, but there are best practices that people can employ to improve one’s chances of good health.”
He urges law firms to look carefully at a vendor’s security policies. Too often, he suggested, companies tout their data center’s security ratings as evidence of their own — but security policies must apply also at the company level and even down to the file level.
As the Epiq incident demonstrates, it takes just one successful phishing attack to take down an entire network. For that reason, Carns said, companies need to emphasize regular and company-wide security training for all employees.
He also suggested that companies compartmentalize their data, so if an employee’s lack of diligence opens the door to an attack, it does not infect the entire system.
“The ransomware or malware has to have access to the files in order to encrypt them, in order to elicit a ransom,” Carns said. “If you make it so executables only have access at any one time to certain sets of data, then it can only attack those certain segments of your data.”
I asked Carns about the impact of a ransomware attack on the reputation of a company. He recalled the notorious 1982 murders in which over-the-counter bottles of Tylenol had been laced with poison. Manufacturer Johnson & Johnson not only survived the incidents, but gained praise as an example of how a major business should handle a disaster.
“This is something that can be survived by a good response, a proper response, and good remediation,” Carns said. “It’s in everyone’s interest to be forthcoming.”
from Law and Politics https://www.lawsitesblog.com/2020/03/new-details-emerge-on-the-ransomware-attack-against-epiq-global.html via http://www.rssmix.com/
0 notes
Text
Windows Or Mac Software Updated To Free Download Latest Version 2019
Adobe Acrobat Reader DC is the industry standard for viewing, printing, signing and commenting on PDF documents. It’s the only PDF viewer available*, which is able to open and interact with all types of PDF content, including forms and multimedia.
Working with Adobe reader 9.1 free download is easy, as it has some very cool tools to work with. With a modern, tabbed viewing interface that allows you to view multiple documents from within the same window and apps and tools that can enhance viewing, revising and annotating documents, you are sure to improve your workflow.
There are so many free online photo editing tool nowadays that are arising and very promising. But there are still proprietary tools that do it best when it comes to photo editing. It has been evolving now for many years and until today, it has made its major upgrade that will surely give us fascination, photoshop cs6 free download full version for windows 7.
Dual SIM Feature Phone; Basically Samsung b310e flash file Guru Music 2 B310e PHONE is a feature phone. No touchpad or touch screen to use. It’s a simple, but powerful keypad Samsung mobile phone with lots of smart features. Samsung Guru Music 2 B310e facilitated with Dual SIM slots [Dual SIM Supportable] which enables you to use two numbers on the same device.
Below you will get the list of all Samsung FRP tool, before downloading, we would recommend you to read this first if your Samsung Galaxy device has an android version like 8.0 or 7.0. so for that you should follow (Talkback) method, and by following this method, you need to access the “Chrome Browser”, once you access there, simply open our this teach eligible page in your mobile, and then download from there frp bypass tool to unlock frp, if you want to understand this method in more.
GetIntoPC Windows 7 is one of the most widely used and evergreen operating systems for all sorts of users. Microsoft has offered Windows OS in different versions for more than 30 years. Windows XP was the most famous version of Windows and after XP, Windows 7 becomes more popular due to its stability and reliability.
Adobe Photoshop 7.0, although a bit older version but there are solid reasons to choose 7.0 over advanced series. Simplicity and quick tools to draw your desired sketch lines and shades which were never so easy, free download adobe photoshop 7.0 full version setup
The steam offline installer provides over 10.000 games available to purchase, download, and play from any computer. Check out the new releases, indie hits, casual favorites and everything in between. Find someone to play with, meet up with friends, connect with groups of similar interests, and host and join chats, matches, and tournaments.
Check out our below download section and z3x Samsung tool without boxor Z3X Samsung tool pro v28.2 for almost all Samsung devices. Z3X 28.2 tool pro is one of the most famous Samsung Smartphone repairing tools. User can flash firmware, can change or repair IMEI number, can bypass Samsung FRP lock, unlock Samsung device, can reset EFS and also can download combination files, etc.
After downloading free ARC Welder You can run apps and games for Android on PC with any operating system directly in browser Google Chrom quickly and without effort. Download arc welder on pc for easy android
Looking for safe clean download of Adobe Photoshop 7 setup to complete your professional photo editing projects? well, here we have one for you. Download free Adobe Photoshop 7.0 free download for windows 7 full offline installer for windows 32 & 64 bit operating systems from the direct high-speed resume-able download link.
Adobe Illustrator CC 2019 Portable Free Download Latest Version for Windows. The program illustrator portable and all files are checked and installed manually before uploading, the program is working perfectly fine without any problem.
Xender for pc Filehippo is used for cross-platform file sharing. You can transfer files like music, pictures, music, and apps at very high speed. You can transfer files between Windows and other platforms.
GetIntoPC SHAREit is simple yet elegant software which allows its users to share media between different devices. It’s tiny and lightweight software which can be handled very easily.
Windows 10 All in One Preactivated ISO is an example of exceptional progressive work by Microsoft which provides ultimate versatility for the user to adopt the OS as one among the most recent editions for 32 bit and 64 bit systems. Windows 10 is much better in comparison to Windows 8 or 8.1 in concerns including, performance, layout, and security.
Miracle Setup Latest Fuzzy Logic Technology is famous in a combination of Hardware and Software, this technology does not depend on Database, sometimes it uses its own function for checking what the problem came in an electronic device, it changes its own signal/function according to the problem accrued, which not need every time to update software database.
Initially quite late compared to most competitors such as Avid or Adobe Premiere Pro in reaching the user market, but Final Cut pro torrent has quickly become the best software thanks to its superior features.
Microsoft Office 2019 is the latest iteration of the industry-standard office suit. Microsoft word for mac free download full version includes the latest versions of Word, Excel, PowerPoint, Outlook, Exchange, SharePoint and Skype for Business, each of which is an essential tool in the computerized office workplace of today. It also boasts a range of enhanced IT options that are designed to make life easier for newcomers to the field.
Download Mac OS X 10.10 Yosemite Latest Installer for free. Give a new refreshing look to your Mac and MacBooks interface with Mac OS X Yosemite. Yosemite 10.10 download DMG
Download Mac OS X Mountain Lion DMG File Installer for version 10.8. Free download and experience Apple’s OS X 9th edition with brand new features. Mountain Lion download DMG
Record audio in a digital audio workstation (DAW) with full MIDI support and 3rd party plugins installed separately. Work with layers, layouts, templates, plug-ins, and various synthesizers. Add loops, kicks, EDM sounds, Bass, and other Analog and logic pro x free download Digital layers.
A powerful mac os x release, high sierra 10.13.6 iso affords a huge range of security and different enhancements that enhance the user revel in addition to provides higher performance Download high Sierra DMG.
This name generator will give you 10 random names for kingdom name generator, empires, and dynasties. The names are based on kingdoms, empires, and dynasties which have existed or still exist today, as well as fictional versions. So they include names from different cultures and languages to achieve a broader range of names for all sorts of purposes.
Demon name generator comes in all shapes and sizes, and their names can be very varied too. Their names are often more guttural and harsher sounding though and can be hard to pronounce at times too. This name generator will generate a wide variety of such names too, so there’s always something to pick from no matter what type of demon you need a name for.
Song name generator needs the perfect name. Often, coming up with a title for your masterpiece can be tougher than writing the lyrics themselves. We’re here to help you choose your title. Tell us a bit about your song then, based on a bank of successful song names, we’ll suggest some personalized just for you.
This screen name generator works by listing adjectives and you adding names/words to the end (append) or at the start (prepend) of the adjective.
Dwarf name generator comes in many different forms, but they usually have traits in common. They usually live in the mountains, they usually have an affinity for mining, gems, and metalworking, and they usually have big beards and short statures.
Orc name generator is brutish, usually ferocious humanoids. They usually have green skin, muscular bodies, tusks, a hatred for nature, and a lack of hygiene. J.R.R. Tolkien first created the orcs, but they have since been adapted over and over in all sorts of works of fiction.
Dungeons & Dragons is a fantasy tabletop role-playing game first published in 1974 by Tactical Studies Rule, Inc., but has seen many new versions and expansions since.dnd name generator
The Medieval name generator Period lasted from the 5th until the 15th century, so names changed over this period. Not always by a lot, but the later the period, the bigger the chance of different cultural influences and other changes affecting the names.
Another way to register your Antivirus and get a free license key is via the form on the Avast premier license key official website. The form itself is very simple and you will need only your name and e-mail.
Likewise, I will give you a different key. You can utilize them for the activating or launch the free account. What’s more in Malwarebytes free crack? Here I will give you the software with the free lifetime key. So you can download this Malwarebytes premium key crack.
These Working Keys are Genuine if you are using Windows 7 or Windows 8 you can easily upgrade to windows 8.1 and get latest Version and features of Windows 8.1. I am Providing You windows 8.1 pro build 9600 product key, Serial Key and Activation Key.
Avast Key is one of the most reliable antivirus software out there. After downloading Avast Antivirus from the official Avast website, you will get a free version for 30 days. After this period, you have to buy an Avast license key to access the premium version of the antivirus. Avast cleanup activation code.
EaseUS Data Recovery License Code is the best data recovery software can be seen nowadays. A comprehensive restore tool for data recovery for windows as well as Mac. Easeus activation code.
Windows 8.1 is the successor to Windows 8 operating system by Microsoft. It has all new features of Windows 8 and updating to Windows 8.1 Key is free for the users who are using windows 8.
When you have installed the windows 7 to your computer, then you need to have the completely working windows 7 home premium product key so that you can activate or repair your copy of windows 7 home premium.
As the name would suggest, Filehippo youtube downloader Free YouTube Download lets you download YouTube videos and convert and save them to your hard drive so you can watch them whenever you want.
ImgBurn FileHippo compares it against a given image file to ensure the actual data is correct), and discovery used in combination with DVDInfoPro, you can check the quality of the burns your drive is producing.
Before the fancy flashy user interfaces and programming tools of the modern day, compilers like Turbo c++ Filehippo C 3.0 were the best way to develop your applications, and the program is not without its uses today.
format factory download Filehippo is an easy-to-use application that allows you to convert the format of a group of files at once. No matter if they are videos, sounds or images, FormatFactory can deal with all of them.
XAMPP download for windows 7 32 bit old version is a free and open source cross-platform web server solution stack package, consisting mainly of the Apache HTTP Server, MySQL database, and interpreters for scripts written in the PHP and Perl programming languages.
KMPlayer free download for windows 7 32 bit is a versatile media player which can cover various types of container format such as VCD, DVD, AVI, MKV, Ogg Theora, OGM, 3GP, MPEG-1/2/4, WMV, RealMedia, and QuickTime among others. It handles a wide range of subtitles and allows you to capture audio, video, and screenshots in many ways, KMPlayer for windows 7.
In addition to typing, Typing master download full version 2014 free download games give user interactive lessons in the form of games so that user can learn quickly in a short time. Typing master lessons are easy and compiled in such a way, you will get step by step training.
HitFilm 4 Express Download is the best way to discover the excitement of making your own movies. With power editing and amazing special effects, no other video product offers such a massive range of features and free training at this kind of price.
CCleaner FileHippo fully featured Registry Cleaner identifies these issues and fixes them. The registry analysis takes seconds and cleaning just a little bit longer. Prompts advise you when to save backups to avoid losing important data.
0 notes
Text
Updated Malwarebytes Anti-Malware 3.7.1 Crack + License Key Premium Reg Key Full Torrent 2019 [Win/Mac]
Updated Malwarebytes Anti-Malware 3.7.1 Crack + License Key Premium Reg Key Full Torrent 2019 [Win/Mac]
Malwarebytes Anti-Malware 3.7.1 Crack: is the most effective application for removing malware and additionally the advanced malware and spyware that's terribly dangerous for laptop or waterproof. it's a terribly fast and economical package that enables you best scans and eliminates the malware and spyware. It will discover the viruses and take away them from your laptop that makes the system a lot of economical and strong. Malwarebytes Anti-Malware safeguard your system as a result of it's all the options that a system want for defense. Then your merchandise has an associate unconquered record of protective computers by utterly removing every kind of malware, together with viruses, Trojans, spyware.
Malwarebytes Anti-Malware Keygen with Latest Version
Malwarebytes Anti-Malware Keygen may be a complete associatetivirus software; it's additionally an opposing ransomware and protection program. during this addition, it provides on-line protection that you simply can be connected to the net. This app offers the potential of scans to find and detects injury that's delete, malware, and different high-level threats. Malwarebytes blocks the virus and infected sites from your laptop that produces your pc infected. It combines the varied tools that are malware-fighting a program. The speed of scanning is fourfold more than each different device that's anti-malware.
Furthermore, it contains the handy tool that's necessary for the protection of laptop, Mac, and portable computer from all reasonably Virus, spyware and malicious activities. Also, Its determine malware that's able to injury your protect, however it makes your laptop full secured around the clock. thus Malwarebytes Anti-Malware 3.7.1 Crack is functioning expeditiously as your laptop computer is that the startup. thence It identifies all spyware from transfer files, sharing files and e-mail information.
Malwarebytes Anti-Malware Premium Crack Lifetime
In addition, this package fight against malware and provides your protection to your essential information. the great issue regarding this package is that it removes malware wherever even the known anti-virus and anti-malware applications fail. Hence, Malwarebytes Anti-Malware Premium Crack do each procedure and stops malicious processes before they even begin. also, all of your browsing histories is secure. it offers you a great many net protection so you'll be able to secure from on-line threats like online-hackers, malware, and different threats. in nowadays this application is employed wide as a result of it's a full package of security.
What’s New?
Current Version: Malwarebytes Anti-Malware 3.7.1
Enhanced detection engine and additionally improved redress
Future updates also will properly retain the setting.
Improved renewal expertise for purchased users.
The license that's original is preserved post renewal for the activation.
Updated the installer to alter the installation to the standalone Enterprise mode
Also, mounted BSOD involving fault.sys
In this version Stability problems mounted
Context Menu scanning possibility allows by default.
Fixed issue with exclusion touching short filenames
Additional allow checks to confirm subscription details.
The updated product that's new.
Plus rather more.
Malwarebytes Anti-Malware Crack Features:
A list that's tiny of utilities to assist eliminate malware manually.
Multi-lingual support.
Ability to execute scans that are stuffed with all drives.
Settings to spice up your Malwarebytes’ Anti-Malware performance.
Light rate scanning that's fast.
Works along with extra edges that are anti-malware.
Dos Command line prompt support for fast scanning.
New Malwarebytes Anti Malware module for protection
Daily updates discharged for database
Within Context menu integration to files and folders that are scan demand.
fixed some minor bugs
improved performance
System Requirements:
Windows:
Windows vista / 7 / 8 / 8.1/10.
900MHz mainframe or quicker, with SSE2 technology
2048 MB (64-bit OS), 1024 MB (32-bit OS)
512 MB for Windows XP
250 MB of free fixed disk house
Windows XP Service Pack 2
Internet explorer 6 or later.
1024 MB of RAM
1024 x 768 screen resolution
Mac:
Core two pair mainframe or quicker
2 GB RAM
50 MB free fixed disk house
800×650 minimum screen resolution
Technical Information:
Operating systems: Windows(all versions), Mac OS X, Android
License: free to download here
Languages: Multiple Languages
Developed by: Malwarebytes
Malwarebytes Anti-Malware 3.7.1 Premium Keys:
ID : 9LF95 Key : 472A-JBMX-B429-FYR5 ID: 6QE24 Key: V0EK-Z9FF-VP6R-M2XZ ID: 4PG56 Key: W624-QG9G-NJG4-RA17
How to Crack?
Download the trial version from the official web site
After downloading install the setup and don’t run it
Download the crack setup given below
Extract the crack file
Paste it into C:/ProgramData/Malwarebytes/Malwarebytes/AntiMalware directory
Now the crack version of Malwarebytes AntiMalware 3.6.1 is ready
All done Enjoy! Run the appliance and revel in all options
Updated Malwarebytes Anti-Malware 3.7.1 Crack + License Key Premium Reg Key Full Torrent 2019 [Win/Mac]
Summary: Very good Anti-Malware
Reviewer: Rizwan Sheikh
Review Date: 2019-03-01
Reviewed Item: Malwarebytes Anti-Malware Crack
Author Rating: 5 Stars
window.fbAsyncInitPredefined = window.fbAsyncInit; window.fbAsyncInit = function() { window.FB.init({ appId: 117100935120196, status: true, cookie: true, xfbml: true, version: 'v3.0' }); window.FB.init = function(){}; window.fbAsyncInitPredefined && window.fbAsyncInitPredefined(); }; (function(d, s, id) { var js, fjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) return; js = d.createElement(s); js.id = id; js.src = "http://connect.facebook.net/en_US/sdk.js?"; fjs.parentNode.insertBefore(js, fjs); }(document, 'script', 'facebook-jssdk'));
See More Here: Updated Malwarebytes Anti-Malware 3.7.1 Crack + License Key Premium Reg Key Full Torrent 2019 [Win/Mac]
0 notes
Text
Advanced mac cleaner malware
You are able to download a registry cleaner to fix the issue. If you don't wish to address taking away the virus yourself, you can get in touch with a local computer repair shop. If you wish to shut off your computer you must close all the programs and after that go to start menu, click turn off computer and click the turn off button. To begin with, make certain your computer is turned off.
Thus, the Advanced Mac Cleaner doesn't really have beneficial capabilities. The SmartShield Antivirus appears much like a normal AV, but it offers comprehensive and total security solutions to safeguard your complete on-line experience. Among the most common totally free windows based antivirus suites offered for Mac.

Aside from that keeping the computer totally free of viruses and malware is also quite important. Removal of viruses will not only fix the error, but in addition resolve many other computer troubles. Undoubtedly, a stubborn malware infection can harm your device to an irreparable extent, but the very best malware removal tool is sufficient to keep it from doing this. When it has to do with cleaning up an infected device, Malwarebytes has ever been free and we recommend it as an important tool in the struggle against malware.
Therefore, install only credible software that has been appreciated as helpful and productive. Windows will search for the newest updates for your PC. Unfortunately, some completely free downloads do not adequately disclose that other software will likewise be installed and you may discover that you have installed adware without your knowing. Apart from that, there's a new option which permits you to install Avast as a supplementary program to your mainstay antivirus program.
If you are a newcomer to the networking then, it is far better to call online technical support companies for assistance. It's possible to easily transfer several quantities of data files that have many computers on the identical network with the support of networking. It's possible to repair the network issues on own your own if you've got a very great networking knowledge. Because of their high exposure and the simple fact that viruses can be readily disguised as legitimate files, peer-to-peer network should be avoided in any way costs.
Actually, several threats have been produced and launched before with a key purpose of collecting users' bitcoins. Any minor mistake can change your complete network settings and might cause an irreparable circumstance. You should take care when dealing with registry because there's a probability of critical system issues.
Unless you're planning to get the software, you're advised to select the free edition. Windows will reveal to you the error if your Windows Firewall isn't properly configured. Windows will demonstrate the problem if there's any matter with registry files. Windows 10 was launched with a lot of advanced tweaks and alternatives to make it one of the major Windows version.
Attempt to eliminate something-you'll fail. Therefore, it's advised that you run malicious software removal tool to entirely eliminate Advanced Mac Cleaner off your MAC system. It's curious that the second application doesn't start automatically. After the download is finished, run the downloaded file.
The Nuiances of Advanced Mac Cleaner Malware
There are several security products out there with many features and perks for any sort of user, which means you are certain to discover the perfect security software for your requirements. One easy means to get around is using AdBlock that's quite fantastic for most browsers. Inappropriate online connection between the networks devices will result in the issue. Nevertheless, including a quality that will make it possible for the tool to steal valuable information like Bitcoin wallet addresses are going to be a different story.
Most community cookbooks attempt to construct cookbooks which work on a broad selection of environments. Most browsers supply a cookie manager letting you control what cookies should be stored. The online browser will run the job of cleaning.
0 notes
Text
Hackers Target Fortnite Gamers to Gain Address to Personal and Bitcoin Keys
New Post has been published on https://bnn.io/news/hackers-target-fortnite-gamers-gain-address-personal-bitcoin-keys/?utm_source=Tumblr&utm_medium=socialpush&utm_campaign=SNAP
Hackers Target Fortnite Gamers to Gain Address to Personal and Bitcoin Keys
Fortnite, the wildly popular video game recently unveiled a fresh season, but recent reports an army of scam artists is attacking the game. The scammers have created malware disguised as cheating software to resemble the real thing, hoping to catch innocent users off guard and steal Bitcoin addresses, reported Malwarebytes on October 2, 2018.
The bug created by these scammers is more dangerous than the ones created by ordinary con artists who attack using non-existent surveys and downloads that don’t account for much. The malware being distributed by these scammers is being used to steal users’ data, including personal information relating to cryptocurrency wallets. Unfortunately, that’s just the beginning.
Researchers at Malwarebytes underwent a series of steps before uncovering the rip-off which included subscribing to several “free” versions of Fortnite designed for Android gadgets. This included the popular “free V-Bucks” that are used to purchase extra content for the game as well as several broken links, wallhacks, and aimbots.
As usual, the scam followed the well-worn path of a typical survey. However, unseen to the common eye was an iota of data theft malware that was masquerading as a cheat tool.
Scammers are getting smarter by utilizing new technology, but they still go back to the same old tricks hackers use. They will pretend to introduce a new product or service using a chain of click-throughs until you end up swallowing their bait.
The YouTube Draw
To make it appear genuine, the scammers first uploaded a video to a YouTube account that showed it had 700 subscribers and over 2,200 views in just 24 hours.
Once a potential victim clicks on the provided link, he is directed to a page on Sub2Unlock. However, instead of leading to a typical survey page where one can expect to fill in a questionnaire or click on offers to receive a reward, victims were asked to subscribe to a social portal of the person who sent you the invitation. That’s already a red flag!
A genuine survey page would give a validation before proceeding to the next step, but in this case, it was missing. When gamers clicked on the “subscribe” button to open the channel’s YouTube profile, the usual system of ensuring that one was a genuine subscriber was missing, another red flag.
After this, gamers were made to access the Sub2Unlock site and hit the download button, which redirected to a site located at www.bt-fortnight-cheats.tk, which has since been taken down.
For all its efforts, the portal’s design is physically charming and offers all the cheat tools anyone would want, and an unsuspecting user could easily conclude it is genuine. Potential victims will be asked to click a few more buttons before they reach a general download site that contains what looks like tens of adverts and files. At the time of writing, a total of 1207 downloads of the malicious file had been recorded.
File information
According to Malwarebytes, the file is a Trojan.Malpack, a term given to suspicious-looking external programs. There is no telling what the malware can do, but we can assume it won’t be good. Digging deeper into the file showed that victims were dealing with a data stealer.
As soon as the initial.EXE, with a size of 168KB gains access to the target system, it quickly enumerates the specific details of the infected computer before it attempts to send data using a POST command to an /index.php file in the Russian Federation, using the IP address 5(dot)101(dot)78(dot)169.
The malware is particularly interested in details browser session information, bitcoin wallets, cookies, and steam sessions.
Most importantly, the IP address mentioned above is shared with similar files. This particular download contains lots of data that are packed differently. For instance, there is one that has a process called “Stealer.exe.” while others post the stolen personal details on /gate.php instead of index.php, which are the preferred sign of Zbot and other similar ones.
While it isn’t the first time scammers are using malware to target Fortnite players, the new method has massive potential to create severe damage. With a horde of scam artists attempting to steal data and cryptocurrency from unsuspecting users by leveraging the game’s popularity, a lot of cleanups can be expected from Fortnite’s developers.
Finally, it is worth mentioning that the readme file advertised by the scammers will automatically purchase more Fortnite cheats worth 80 USD in bitcoin.
Under the prevailing circumstances, it’s only advisable for anyone intending to cheat to remember the saying, “better safe than sorry.” While winning is a great thing, remember that you will be risking con artists transferring your data, which is the higher price you will be paying.
0 notes
Text
Amateur Cryptojackers and Apple Macs Emerge as Two Mining Malware Trends for 2018
2017 was a big year for cryptojacking. It increased by 8,500 percent, according to figures published by Symantec in March. And it would seem that 2018 has so far been an even bigger year for mining malware, as the Cyber Threat Alliance September report revealed that, beginning on Jan. 1, cryptojacking still had room to increase by a further 500 percent.
However, beneath this simple outline of growth, there is a bigger, more complicated picture. Despite reports from some quarters showing that mining malware detections increased in the first two quarters of 2018, other reports suggest that they have in fact decreased.
And while the overall growth in mining malware since last year has been attributed to the volatility of cryptocurrency prices and the existence of software bugs, other factors have played a significant role, such as the involvement of amateur cryptojackers and the cost of mining legitimately.
Amateur cryptojackers
If there’s one dominant trend this year in the underworld of cryptojacking, it’s that most mining malware focuses on Monero. Indeed, Palo Alto Networks revealed in July that Monero accounts for 84.5 percent of all detected malware, compared to 8 percent for Bitcoin and 7 percent for other coins.
The reason for this is simple: Monero (XMR) is not only a privacy coin, but also the most valuable privacy coin by market cap — and 10th overall. Using the Cryptonight proof-of-work (PoW) algorithm, it mixes the user’s inputs with those of other users, and it also uses “ring confidential transactions” that obscure the amount of XMR being transferred. It’s therefore ideal for cybercriminals.
Monero was already the most popular coin for cryptojackers in 2017, but a number of new developments have emerged in 2018 to distinguish this year from its predecessor. Most notably, cryptojacking is increasingly becoming the province of amateur ‘hackers,’ who are lured into the illicit activity by the cheap availability of mining malware and by obvious financial rewards. According to Russian cybersecurity firm Group-IB, the dark web is “flooded with cheap mining software,” which can often be purchased for as little as $0.50.
Such software has become abundant this year: In 2017, Group-IB encountered 99 announcements regarding for-sale cryptojacking software on underground forums, while in 2018 it counted 477, signalling an increase of 381.8 percent. As the firm notes in its report:
“Low entry barrier to the illegal mining market results in a situation where cryptocurrency is being mined by people without technical expertise or experience with fraudulent schemes.”
More growth
In other words, cryptojacking has become a kind of hobbyist crime, popular among thousands of amateur hackers. This would perhaps account for why there has been a marked increase in detections this year, with Kaspersky Labs informing Cointelegraph that the number of PC cryptojacking victims increased from 1.9 million in 2016/17 to 2.7 million in 2017/18. Evgeny Lopatin — a malware analyst at Kaspersky Lab – shared:
“The mining model […] is easier to activate and more stable [than other attack vectors]. Attack your victims, discreetly build cryptocurrency using their CPU or GPU power and then transfer that into real money through legal exchanges and transactions.”
Of course, whenever “detections” are mentioned, the possibility arises that any increase is largely the result of an improvement in detection measures. “However, this is not the main driver here, as we see actual growth,” says Lopatin.
“Our analysis shows that more and more criminals increasingly use crypto miners for malicious purposes across the world.”
McAfee noted in a report from April that the vast majority of its detections were of CoinMiner, a piece of malware that surreptitiously inserts code taken from the CoinHive XMR mining algorithm into the victim’s computer. This occurs when the victim downloads an infected file from the web, but what’s new in 2018 is that such a vulnerability now affects Apple Macs as well, which had previously been regarded as much more secure than its Windows rivals.
This development was noted by United States security firm Malwarebytes, which in a May blog post reported on the discovery of a new malicious crypto miner that harnesses the legit XMRig miner. Thomas Reed, the director of Mac and mobile at the company, wrote:
“Often, Mac malware is installed by things like fake Adobe Flash Player installers, downloads from piracy sites, [and] decoy documents users are tricked into opening.”
In fact, this wasn’t the first piece of Mac mining malware it had discovered, with Reed stating that it “follows other cryptominers for macOS, such as Pwnet, CpuMeaner and CreativeUpdate.”
EternalBlue
However, while cryptojacking has become more of an amateur-driven phenomenon, it still remains the case that many of this year’s exploits can be traced to more ‘elite’ sources. Cybersecurity firm Proofpoint reported at the end of January that Smominru, a cryptojacking botnet, had spread to over half a million computers — largely thanks to the National Security Agency, which had discovered a Windows bug that was then leaked online.
This vulnerability is better known as EternalBlue, which most famously was responsible for the WannaCry ransomware attack/incident of May 2017. And according to Cyber Threat Alliance (CTA), it’s another big factor in this year’s 459 percent increase in cryptojacking.
Worryingly, the CTA’s report suggests that cryptojacking is only likely to increase as it becomes more successful and profitable:
“[Cryptojacking’s] influx of money could be used for future, more sophisticated operations by threat actor groups. For instance, several large-scale cryptocurrency mining botnets (Smominru, Jenkins Miner, Adylkuzz) have made millions of dollars.”
And things are already bad enough in the present, with the CTA writing that infection by mining malware comes with steep costs for victims.
“Taken in aggregate, when criminals install cryptocurrency miners in large enterprise networks, the costs in excess energy usage, degraded operations, downtime, repairs of machines with physical damage and mitigation of the malware in systems incurred by the victims far outweigh the relatively small amount of cryptocurrency the attackers typically earn on a single network.”
Costs
The mention of costs is significant when it comes to cryptojacking, not just for (potential) victims, but also for perpetrators. That’s because cryptojacking is essentially the theft of electricity and CPU, which implies that it will continue being prevalent not only for as long as Monero and other coins remain valuable, but also for as long as it remains expensive to mine XMR and other cryptos.
According to CryptoCompare’s profitability calculator for Monero, an individual U.S.-based miner using a graphics card capable of a 600 H/s hash rate (e.g., the Nvidia GTX 1080) and using 100W of power (a very conservative estimate) will make only $0.8033 in profit every month. This, clearly, isn’t especially promising, which is a large part of the reason why so many amateurs have turned to cryptojacking, since mining XMR while paying for your own electricity just isn’t fruitful when you’re not a big mining company.
There are, however, recent signs that Monero mining has become more profitable, even for the smaller miner. This came after its hard fork on April 6, which changed its PoW protocol so as to make it incompatible with ASIC miners, which tend to dominate mining (particularly in the case of Bitcoin).
As soon as this hard fork was completed, reports came from the Monero subreddit that profitability had increased by 300 percent or even 500 percent, although this boost was soon lost in the following weeks, according to BitInfoCharts.
Likewise, Monero itself has been cautious with regard to promising that it can resist ASIC mining equipment forever. “Thus, it is recognized that ASICs may be an inevitable development for any proof-of-work [cryptocurrency],” wrote developers dEBRYUNE and dnaleor in a February blog. “We also concede that ASICs may be inevitable, but we feel that any transition to an ASIC-dominated network needs to be as egalitarian as possible in order to foster decentralization.”
Decline?
Assuming that it has become more profitable to mine XMR legitimately, this would account for a flattening in cryptojacking growth that has been observed by some cybersecurity firms. In its Q2 2018 report, Malwarebytes revealed that mining malware detections dropped from a peak of 5 million at the beginning of March, to a low of 1.5 million at the beginning of June. This decline may contradict what other analysts have reported this year, but given that Malwarebytes’ research is the most recent in terms of the dates covered, it’s arguably the most authoritative.
It’s not clear whether this decline is the result of an increase in profitability for legit Monero miners, of business and individuals wising up to the threat of cryptojacking, or of a general decline in the value of cryptocurrencies. Regardless, Malwarebytes predict that “Cryptocurrency miners will be going out of style” as a cybersecurity threat. “Of course, we are still going to see plenty of miners being distributed and detected,” its report concludes. “However, it looks like we are at the tail end of the ‘craze.'”
window.fbAsyncInit = function() { FB.init({ appId : '1922752334671725', xfbml : true, version : 'v2.9' }); FB.AppEvents.logPageView(); };
(function(d, s, id){ var js, fjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) {return;} js = d.createElement(s); js.id = id; js.src = "http://connect.facebook.net/en_US/sdk.js"; fjs.parentNode.insertBefore(js, fjs); }(document, 'script', 'facebook-jssdk'));
!function(f,b,e,v,n,t,s) {if(f.fbq)return;n=f.fbq=function(){n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments)}; if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version='2.0'; n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0]; s.parentNode.insertBefore(t,s)}(window,document,'script', 'https://connect.facebook.net/en_US/fbevents.js'); fbq('init', '1922752334671725'); fbq('track', 'PageView'); This news post is collected from Cointelegraph
Recommended Read
Editors' Picks
BinBot Pro – Safest & Highly Recommended Binary Options Auto Trading Robot
Do you live in a country like USA or Canada where using automated trading systems is a problem? If you do then now we ...
User rating:
9.5
Demo & Pro Version Get It Now Hurry!
Read full review
Most Popular 2
Bit Bubble Tech – Learn How To Profit Big When Bitcoin Bubble Bursts?
If you have not already heard of the Bit Bubble Tech App, you undoubtedly wish to read this Bit Bubble Tech Review. We ...
User rating:
9.3
Free For 90 Days Get It Now
Read full review
The post Amateur Cryptojackers and Apple Macs Emerge as Two Mining Malware Trends for 2018 appeared first on Review: Legit or Scam?.
Read more from → https://legit-scam.review/amateur-cryptojackers-and-apple-macs-emerge-as-two-mining-malware-trends-for-2018-3
0 notes
Photo

New Post has been published here http://www.cryptoquicknews.com/amateur-cryptojackers-and-apple-macs-emerge-as-two-mining-malware-trends-for-2018/
Amateur Cryptojackers and Apple Macs Emerge as Two Mining Malware Trends for 2018

This post was originally published here
2017 was a big year for cryptojacking. It increased by 8,500 percent, according to figures published by Symantec in March. And it would seem that 2018 has so far been an even bigger year for mining malware, as the Cyber Threat Alliance September report revealed that, beginning on Jan. 1, cryptojacking still had room to increase by a further 500 percent.
However, beneath this simple outline of growth, there is a bigger, more complicated picture. Despite reports from some quarters showing that mining malware detections increased in the first two quarters of 2018, other reports suggest that they have in fact decreased.
And while the overall growth in mining malware since last year has been attributed to the volatility of cryptocurrency prices and the existence of software bugs, other factors have played a significant role, such as the involvement of amateur cryptojackers and the cost of mining legitimately.
Amateur cryptojackers
If there’s one dominant trend this year in the underworld of cryptojacking, it’s that most mining malware focuses on Monero. Indeed, Palo Alto Networks revealed in July that Monero accounts for 84.5 percent of all detected malware, compared to 8 percent for Bitcoin and 7 percent for other coins.

The reason for this is simple: Monero (XMR) is not only a privacy coin, but also the most valuable privacy coin by market cap — and 10th overall. Using the Cryptonight proof-of-work (PoW) algorithm, it mixes the user’s inputs with those of other users, and it also uses “ring confidential transactions” that obscure the amount of XMR being transferred. It’s therefore ideal for cybercriminals.
Monero was already the most popular coin for cryptojackers in 2017, but a number of new developments have emerged in 2018 to distinguish this year from its predecessor. Most notably, cryptojacking is increasingly becoming the province of amateur ‘hackers,’ who are lured into the illicit activity by the cheap availability of mining malware and by obvious financial rewards. According to Russian cybersecurity firm Group-IB, the dark web is “flooded with cheap mining software,” which can often be purchased for as little as $0.50.
Such software has become abundant this year: In 2017, Group-IB encountered 99 announcements regarding for-sale cryptojacking software on underground forums, while in 2018 it counted 477, signalling an increase of 381.8 percent. As the firm notes in its report:
“Low entry barrier to the illegal mining market results in a situation where cryptocurrency is being mined by people without technical expertise or experience with fraudulent schemes.”
More growth
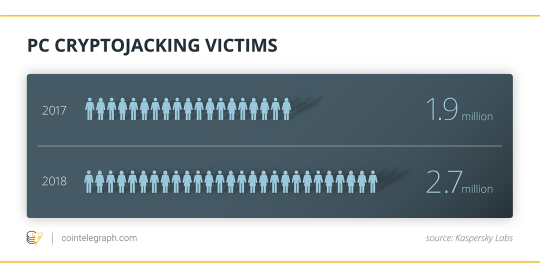
In other words, cryptojacking has become a kind of hobbyist crime, popular among thousands of amateur hackers. This would perhaps account for why there has been a marked increase in detections this year, with Kaspersky Labs informing Cointelegraph that the number of PC cryptojacking victims increased from 1.9 million in 2016/17 to 2.7 million in 2017/18. Evgeny Lopatin — a malware analyst at Kaspersky Lab – shared:
“The mining model […] is easier to activate and more stable [than other attack vectors]. Attack your victims, discreetly build cryptocurrency using their CPU or GPU power and then transfer that into real money through legal exchanges and transactions.”
Of course, whenever “detections” are mentioned, the possibility arises that any increase is largely the result of an improvement in detection measures. “However, this is not the main driver here, as we see actual growth,” says Lopatin.
“Our analysis shows that more and more criminals increasingly use crypto miners for malicious purposes across the world.”
McAfee noted in a report from April that the vast majority of its detections were of CoinMiner, a piece of malware that surreptitiously inserts code taken from the CoinHive XMR mining algorithm into the victim’s computer. This occurs when the victim downloads an infected file from the web, but what’s new in 2018 is that such a vulnerability now affects Apple Macs as well, which had previously been regarded as much more secure than its Windows rivals.
This development was noted by United States security firm Malwarebytes, which in a May blog post reported on the discovery of a new malicious crypto miner that harnesses the legit XMRig miner. Thomas Reed, the director of Mac and mobile at the company, wrote:
“Often, Mac malware is installed by things like fake Adobe Flash Player installers, downloads from piracy sites, [and] decoy documents users are tricked into opening.”
In fact, this wasn’t the first piece of Mac mining malware it had discovered, with Reed stating that it “follows other cryptominers for macOS, such as Pwnet, CpuMeaner and CreativeUpdate.”
EternalBlue
However, while cryptojacking has become more of an amateur-driven phenomenon, it still remains the case that many of this year’s exploits can be traced to more ‘elite’ sources. Cybersecurity firm Proofpoint reported at the end of January that Smominru, a cryptojacking botnet, had spread to over half a million computers — largely thanks to the National Security Agency, which had discovered a Windows bug that was then leaked online.
This vulnerability is better known as EternalBlue, which most famously was responsible for the WannaCry ransomware attack/incident of May 2017. And according to Cyber Threat Alliance (CTA), it’s another big factor in this year’s 459 percent increase in cryptojacking.
Worryingly, the CTA’s report suggests that cryptojacking is only likely to increase as it becomes more successful and profitable:
“[Cryptojacking’s] influx of money could be used for future, more sophisticated operations by threat actor groups. For instance, several large-scale cryptocurrency mining botnets (Smominru, Jenkins Miner, Adylkuzz) have made millions of dollars.”
And things are already bad enough in the present, with the CTA writing that infection by mining malware comes with steep costs for victims.
“Taken in aggregate, when criminals install cryptocurrency miners in large enterprise networks, the costs in excess energy usage, degraded operations, downtime, repairs of machines with physical damage and mitigation of the malware in systems incurred by the victims far outweigh the relatively small amount of cryptocurrency the attackers typically earn on a single network.”
Costs
The mention of costs is significant when it comes to cryptojacking, not just for (potential) victims, but also for perpetrators. That’s because cryptojacking is essentially the theft of electricity and CPU, which implies that it will continue being prevalent not only for as long as Monero and other coins remain valuable, but also for as long as it remains expensive to mine XMR and other cryptos.
According to CryptoCompare’s profitability calculator for Monero, an individual U.S.-based miner using a graphics card capable of a 600 H/s hash rate (e.g., the Nvidia GTX 1080) and using 100W of power (a very conservative estimate) will make only $0.8033 in profit every month. This, clearly, isn’t especially promising, which is a large part of the reason why so many amateurs have turned to cryptojacking, since mining XMR while paying for your own electricity just isn’t fruitful when you’re not a big mining company.
There are, however, recent signs that Monero mining has become more profitable, even for the smaller miner. This came after its hard fork on April 6, which changed its PoW protocol so as to make it incompatible with ASIC miners, which tend to dominate mining (particularly in the case of Bitcoin).
As soon as this hard fork was completed, reports came from the Monero subreddit that profitability had increased by 300 percent or even 500 percent, although this boost was soon lost in the following weeks, according to BitInfoCharts.

Likewise, Monero itself has been cautious with regard to promising that it can resist ASIC mining equipment forever. “Thus, it is recognized that ASICs may be an inevitable development for any proof-of-work [cryptocurrency],” wrote developers dEBRYUNE and dnaleor in a February blog. “We also concede that ASICs may be inevitable, but we feel that any transition to an ASIC-dominated network needs to be as egalitarian as possible in order to foster decentralization.”
Decline?
Assuming that it has become more profitable to mine XMR legitimately, this would account for a flattening in cryptojacking growth that has been observed by some cybersecurity firms. In its Q2 2018 report, Malwarebytes revealed that mining malware detections dropped from a peak of 5 million at the beginning of March, to a low of 1.5 million at the beginning of June. This decline may contradict what other analysts have reported this year, but given that Malwarebytes’ research is the most recent in terms of the dates covered, it’s arguably the most authoritative.
It’s not clear whether this decline is the result of an increase in profitability for legit Monero miners, of business and individuals wising up to the threat of cryptojacking, or of a general decline in the value of cryptocurrencies. Regardless, Malwarebytes predict that “Cryptocurrency miners will be going out of style” as a cybersecurity threat. “Of course, we are still going to see plenty of miners being distributed and detected,” its report concludes. “However, it looks like we are at the tail end of the ‘craze.'”
View the website
New Post has been published here http://www.cryptoquicknews.com/amateur-cryptojackers-and-apple-macs-emerge-as-two-mining-malware-trends-for-2018/
0 notes