#utility damage prevention software
Explore tagged Tumblr posts
Text
Revolutionize Utility Damage Prevention with Norfield’s 811 Ticket Management Software
In today’s fast-paced world, effective utility damage prevention is more critical than ever. Norfield’s 811 Ticket Management Software simplifies and streamlines the entire process of managing 811 tickets, ensuring your utility marking and excavation projects are handled efficiently and safely. As a trusted provider, Norfield brings innovation and precision to utility management, reducing risks associated with underground damages and project delays.
Designed for utility locators, contractors, and project managers, this software provides a user-friendly platform that centralizes ticket handling and coordination. It automates ticket processing, improves communication between stakeholders, and tracks every project step—from initial requests to final clearances—making it easier to ensure compliance with regulatory standards. Norfield’s 811 Ticket Management Software also offers real-time updates, helping teams stay informed and respond swiftly to changes or new information. By optimizing workflows, users can minimize errors, reduce miscommunication, and enhance productivity.
What sets Norfield apart is its commitment to a smooth user experience, with tailored features like customized reporting, detailed mapping integrations, and efficient scheduling tools. Whether you're overseeing large-scale construction or small utility projects, Norfield’s software adapts to your needs, making it ideal for a wide range of industries, including telecom, gas, water, and electrical services.
If your goal is to ensure safe digging practices while meeting project deadlines, Norfield’s 811 Ticket Management Software is the ultimate solution. Explore the many ways it can enhance safety, accountability, and operational efficiency for your organization. With an emphasis on security and data accuracy, Norfield's technology stands out as an essential tool for any company involved in utility management and excavation.
Visit Norfield’s website today to learn more about how 811 Ticket Management Software can transform your utility operations.
#811 ticket management software#utility damage prevention software#811 software solutions#excavation project management#underground utility management#ticket processing automation
0 notes
Text
The Role of ERP in Managing Quality Control in Manufacturing
In the highly competitive manufacturing sector, maintaining stringent quality control is not just a necessity but a strategic advantage. In a landscape where efficiency and precision define success, integrating ERP for manufacturing companies in India has become a game-changer. The role of manufacturing ERP software in India extends beyond operational management; it plays a pivotal part in ensuring quality control throughout the production lifecycle.

Understanding the Need for Quality Control in Manufacturing
Quality control ensures that products meet predefined standards, adhere to regulations, and satisfy customer expectations. Without effective systems in place, manufacturing companies risk producing defective products, incurring financial losses, and damaging their reputation. This is where manufacturing enterprise resource planning software in India comes into play. By centralizing data and streamlining processes, ERP systems empower manufacturers to monitor, measure, and enhance quality at every stage.
How ERP Facilitates Quality Control in Manufacturing
1. Centralized Data Management
ERP systems consolidate data from various departments into a unified platform. This centralization is crucial for quality control, as it provides real-time access to critical metrics like raw material quality, production processes, and final product evaluations. ERP software companies in India ensure that manufacturers have a single source of truth, enabling faster and more informed decision-making.
2. Automation of Quality Checks
The manufacturing ERP module often includes automated tools for conducting quality checks. By automating repetitive tasks such as inspecting raw materials, testing products, and verifying compliance, ERP reduces human error and enhances efficiency. This capability is particularly valuable for industries with strict quality standards, such as automotive, pharmaceuticals, and electronics.
3. Compliance Management
Staying compliant with industry regulations is non-negotiable for manufacturing companies. ERP systems provide features that help monitor compliance parameters, generate audit reports, and track regulatory changes. ERP software providers in India offer tailored solutions to meet local and global compliance requirements, ensuring seamless operations.
4. Real-Time Analytics and Reporting
Real-time analytics is a cornerstone of modern ERP systems. These tools allow manufacturers to track quality metrics in real-time, identify deviations, and implement corrective actions instantly. The insights gained from these analytics not only improve quality but also drive process optimization.
5. Supply Chain Integration
Quality control begins with raw materials and extends through the supply chain. ERP systems facilitate end-to-end supply chain visibility, enabling manufacturers to assess supplier performance and ensure the quality of incoming materials. Many ERP solution providers in India offer integrated supply chain management modules to support this functionality.
6. Continuous Improvement through Feedback Loops
ERP systems support continuous improvement by capturing and analyzing feedback from quality control processes. This data is invaluable for identifying recurring issues, uncovering root causes, and implementing preventive measures. Top 10 ERP software providers in India have built-in tools for continuous quality enhancement, ensuring sustained excellence.
Benefits of ERP for Quality Control in Manufacturing
Integrating an ERP system offers several tangible benefits for quality control:
Enhanced Traceability: ERP systems provide traceability across the production process, making it easier to track and rectify defects.
Reduced Waste: By identifying inefficiencies and defects early, ERP reduces waste and optimizes resource utilization.
Improved Customer Satisfaction: Consistently delivering high-quality products strengthens customer trust and loyalty.
Cost Savings: Preventing defects and ensuring compliance minimizes the financial risks associated with recalls, fines, and reputational damage.
Choosing the Right ERP Software for Quality Control
Selecting the best ERP solution requires careful consideration of your manufacturing needs. Here are some factors to consider:
Industry-Specific Features: Look for manufacturing ERP software in India that offers modules tailored to your industry.
Scalability: Ensure the ERP system can scale with your business as it grows.
Integration Capabilities: The ERP should integrate seamlessly with your existing systems and technologies.
Vendor Expertise: Collaborate with an ERP software company in India with proven expertise in delivering quality solutions.
Why Indian Manufacturers Need ERP for Quality Control
India's manufacturing sector is poised for growth, driven by initiatives like Make in India and PLI schemes. However, this growth comes with increasing competition and stricter quality expectations. Leveraging ERP software providers in India can give manufacturers the edge they need to thrive in this evolving landscape.
A Trusted Partner for ERP Implementation
With numerous options available, finding the right ERP vendor is crucial. Leading ERP software companies in India offer customized solutions to meet the unique challenges of Indian manufacturers. These providers combine deep industry knowledge with cutting-edge technology to deliver exceptional results.
Shantitechnology: A Trusted Name in ERP Solutions
Shantitechnology, a renowned name among top 10 ERP software providers in India, specializes in delivering robust ERP solutions for manufacturing companies. Our comprehensive manufacturing ERP module is designed to address the intricacies of quality control, ensuring manufacturers achieve excellence with ease.
Conclusion
In the modern manufacturing landscape, quality control is not an isolated function but a core component of operational success. ERP systems empower manufacturers to seamlessly integrate quality control into their workflows, ensuring consistent product excellence. As one of the best ERP software providers in India, Shantitechnology is committed to helping manufacturers navigate the complexities of quality control with innovative ERP solutions. By embracing the right ERP system, Indian manufacturers can enhance their competitive edge, drive customer satisfaction, and achieve sustainable growth.
If you are looking to elevate your quality control processes, partner with a leading ERP software company in India like Shantitechnology. Contact us today to learn more about our customized ERP solutions and how they can transform your manufacturing operations.
#ERP software in India#Top 10 ERP software providers in India#ERP software company in India#Engineering ERP Software company in India#ERP software for engineering companies#Engineering ERP software solution#ERP software for engineering companies in India#ERP software providers in India#ERP software companies in India#ERP solution providers in India#Best ERP software provider in India#ERP for manufacturing company in India#Manufacturing ERP software in India#Manufacturing enterprise resource planning software in India#Manufacturing ERP module
5 notes
·
View notes
Text
Ways to Protect Your VPS Against Online Threats
Leaks of customer information are devastating to businesses; not only may they damage the reputation of your firm, but they may also result in severe legal penalties. It is essential to have a solid understanding of virtual private server security in order to protect oneself from any dangers on the internet.
Nevertheless, in addition to adhering to the most effective security practices, you are required to perform routine checks on your virtual private server (VPS). In this article, you are given useful suggestions for protecting virtual private servers (VPS) from cyberattacks. Keep reading to learn more!

Tips for Virtual Private Server Cybersecurity in 2024-
If you are in charge of a web server, it is absolutely necessary to remain up to date on the most recent security measures and risks that are posed by the internet. In the year 2024, the following are the best practices for assuring the security of virtual private servers (VPS)!
Deactivate the Root Login feature
Any element of the server can be modified by the root user of a virtual private server (VPS), who has the highest level of operational entitlements. In an effort to seize control of the system, hackers might select this user as their target.
This login account can be removed, which would reinforce the defense against root access and safeguard your website from attacks. For the sake of server administration, we recommend creating a new login that is capable of accessing the root level and running commands.
Make your passwords more secure
The most easily guessed passwords are ones that are poorly crafted, such as those that contain common terms or data that may be identified. You may create secure passwords by mixing different types of characters, including numerals, special characters, and both uppercase and lowercase letters.
The use of secured password management software is something you might want to think about if you want to simply generate and save secure passwords. It is essential to keep in mind that originality is essential. Consequently, it is recommended that you change your passwords periodically, preferably once every three months, and never use the same password for more than one account. As a final precaution, you should never provide your root login credentials in order to prevent unauthorized access.
Modify the SSH Port That Is Default
If you continue to allow attackers to access your virtual server over the normal SSH port of 22, you are inviting them to do so. Port scanning and brute-force attacks are two methods that attackers can use to gain unauthorized access to a remote system. When securing virtual private server (VPS) cyber threats, it is important to lock out unauthorized users and change the default SSH listening port to something unexpected.
Restriction of User Access
When you have a significant number of users on your virtual private server (VPS) hosting, it is important to carefully plan out how rights and control will be distributed. Your server's sensitive data and assets are at risk of being compromised if you grant root access to each and every user. By understanding and applying the various forms of authorization, you can make certain that each user has access to only the permissions that they require.
In the event that an account is compromised, this strategy ensures that the damage is reduced to a minimum. Sensitive information and systems are protected from harm since this reduces the attack surface and diminishes the possible effects that could be caused by attacks that originate from within the organization. A further benefit is that it simplifies audit procedures, which makes it easier to monitor user activity and identify inconsistencies.
Put the Principles of Robust Authentication into Practice
A strong, one-of-a-kind password should be generated for each account on your virtual private server (VPS), and you should utilize multi-factor authentication (MFA) to add an extra layer of security. For remote access, you should make use of secure protocols such as SSH keys in order to prevent unauthorized login attempts and protect your virtual private server (VPS) against assaults that are based on credentials.
It is difficult to decode these automated keys because they are typically longer than passwords. Public and private keys are the components that makeup SSH keys. It is the device that is utilized that is responsible for storing the private key, whereas the server of the computer is where the public key is kept. In the event that an individual attempts to log in, the system generates an arbitrary string. This string is then protected with the public key. The only way to gain access is to decrypt this string using a private key that is compliant with the security system.
Set up a VPN on your VPS
Your information is at risk of being intercepted and stolen by third parties who are not authorized to do so if you use a public connection. Set up a virtual private network, also known as a VPN, to protect yourself from potential security threats and in order to avoid this. Using a virtual private network (VPN), your computer is able to conceal its true location while also directing traffic through a secure connection.
This is accomplished by using a new IP address. Your Internet Protocol (IP) address will be rendered untraceable as a result of this, which will allow you to remain anonymous surfing the internet. Your data is protected by a virtual private network (VPN), which also prevents hackers from accessing your communications. Alongside a firewall, it provides additional protection for virtual private servers (VPS).
Be sure to utilize firewalls
Your firewalls are your first line of defense against threats that come from the internet. APF and CSF are examples of programs that act as guardians by monitoring both incoming and outgoing traffic. They contribute to the identification and prevention of undesired movements at the entrance, so ensuring that only authorized traffic is allowed to pass through. They offer a barrier that can be designed to match the specific requirements and security requirements of your system, and it may be updated to meet those requirements.
Firewalls have a number of features that aid with the rapid identification and management of typical cyber risks. One of these features is the ability to generate detailed logs and send notifications regarding potential safety incidents. The fact that they are able to make adjustments and offer timely protections makes them an essential resource for cybersecurity.
Make sure you do regular backups
You should create backups of your data on a regular basis to protect it from being lost in the event that there is a data breach. Ensure that backups are stored in a location that is not the virtual private server (VPS) and implements automated backup mechanisms. Because of this, even if the virtual private server (VPS) is compromised, your essential data will remain secure and accessible.
Set up an antivirus program
Installing antivirus software on your virtual private server (VPS) will protect your data and forestall any compromises. An antivirus tool for your server performs continuous inspections of files and actions, much like software that has prevented the malware from infecting a large number of PCs around the world by spotting dangers in real-time.
Employ a Malware Scanner Software
Your virtual private server (VPS) is protected from dangers such as trojans and worms by an antivirus program; however, it may not be able to identify more recent exploits such as zero-day malware.
Combine antivirus software with a malware scanner to improve the security of your virtual private server (VPS). This category of software is able to update the detection rule more quickly, which enables it to differentiate between newer threats that are present on your system.
Check out the User Rights
If there are a large number of users on your virtual private server (VPS) hosting, you should give serious consideration to the distribution of control and rights. Your server's resources and sensitive data will be put at risk of security breaches if you grant root rights to every user on the server.
You should restrict the number of users who can access your server in order to avoid this problem. Managing users and assigning them varying permissions for particular files and system resources is one way to accomplish this goal.
Install systems that can detect and prevent intrusions
Monitoring and analyzing network traffic with the help of intrusion detection and prevention systems (IDPS) is a good way to keep an eye out for any indicators of malicious behavior or efforts to gain unauthorized access. IDPS's ability to detect and block threats in real time contributes to an overall improvement in the security posture of your virtual private server (VPS).
Conclusion-
The protection of your virtual private server (VPS) is essential since it stores sensitive information. In spite of the fact that Linux is well-known for its robust security, the virtual private server (VPS) nevertheless has weaknesses. Malware, sniffer and brute-force attacks, SQL injections, cross-site scripting (XSS), lacking function-level control, and incomplete authentication are some of the most common types of cyber assaults and problems that can occur in a Linux system. Virtual private server owners need to be aware of how to monitor the server and operating system in order to implement effective security measures in order to avoid these issues.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
The Ultimate Guide to Mechanical Maintenance: Strategies for Success
Photo by William Warby on Unsplash
Mechanical maintenance is fundamental to the smooth operation and longevity of machinery across various industries. Effective maintenance practices can significantly reduce downtime, improve efficiency, and extend the lifespan of equipment. This guide explores the intricacies of mechanical maintenance, offering strategies and best practices to ensure optimal machinery performance.
The Essence of Mechanical Maintenance
Mechanical maintenance involves a series of actions aimed at keeping machinery in peak condition. These actions include regular inspections, timely repairs, and preventive measures to avoid unexpected failures. The primary goal is to ensure that all mechanical systems function efficiently and safely.
Types of Mechanical Maintenance
Preventive Maintenance: Scheduled maintenance activities designed to prevent equipment failures. Tasks include regular inspections, lubrication, and replacing worn components. The objective is to keep machinery running smoothly and avoid unexpected breakdowns.
Predictive Maintenance: This approach uses real-time data and monitoring tools to predict when maintenance should be performed. Techniques like vibration analysis and thermal imaging help identify potential issues before they lead to equipment failure.
Corrective Maintenance: Also known as reactive maintenance, this involves repairing equipment after a failure has occurred. While this can be more costly and disruptive, it is essential for addressing unexpected issues that preventive measures did not catch.
Condition-Based Maintenance: Maintenance activities are conducted based on the actual condition of equipment. Sensors and monitoring devices provide continuous data, allowing for maintenance to be performed precisely when needed, rather than on a fixed schedule.
Key Components of Effective Mechanical Maintenance
Regular Inspections: Conducting systematic checks to identify early signs of wear, tear, or malfunction. Using detailed checklists ensures all critical components are evaluated.
Lubrication: Ensuring all moving parts are adequately lubricated to minimize friction and wear. The correct type and amount of lubricant are crucial for maintaining machinery efficiency.
Cleaning: Keeping machinery clean prevents contamination and ensures optimal performance. Regular removal of dust, debris, and other contaminants is essential.
Calibration: Regular calibration of tools and equipment ensures accuracy and precision in operations. Standardized procedures and tools help maintain consistent performance.
Component Replacement: Timely replacement of worn or damaged parts prevents further damage and ensures continuous operation. Keeping an inventory of critical spare parts allows for quick replacements when necessary.
Best Practices for Mechanical Maintenance
Develop a Maintenance Schedule: A detailed maintenance schedule that outlines routine inspections, servicing, and part replacements is essential. Adherence to this schedule ensures no maintenance tasks are overlooked.
Utilize Maintenance Management Software: Implementing software to track and manage maintenance activities improves efficiency. These tools can schedule tasks, record maintenance history, and generate performance reports.
Train Maintenance Personnel: Regular training ensures maintenance personnel are up-to-date with the latest techniques and technologies. Continuous learning enhances their skills and effectiveness.
Implement Safety Protocols: Establishing and enforcing safety protocols protects both maintenance personnel and equipment. Proper training and protective gear are essential components of a safe maintenance environment.
Conduct Root Cause Analysis: Identifying the root causes of equipment failures helps in implementing effective corrective actions. This prevents recurrence and improves the overall reliability of machinery.
Challenges in Mechanical Maintenance
Resource Constraints: Limited availability of skilled personnel, tools, and spare parts can hinder maintenance activities. Effective resource management and planning are crucial to overcoming these challenges.
Unplanned Downtime: Unexpected equipment failures can lead to significant production stoppages and increased costs. Implementing predictive and preventive maintenance strategies can mitigate these risks.
Data Management: Managing and analyzing large volumes of maintenance data can be challenging. Ensuring data accuracy and leveraging advanced analytics tools can enhance decision-making.
Aging Equipment: Older machinery often requires more frequent maintenance and can be less reliable. Balancing the cost of ongoing maintenance with the potential benefits of upgrading to newer equipment is a key consideration.
Case Studies and Real-World Examples
Preventive Maintenance in Manufacturing: A manufacturing plant implemented a rigorous preventive maintenance program, resulting in a 20% reduction in equipment downtime and a 15% increase in production efficiency. Regular inspections and timely component replacements were key to these improvements.
Predictive Maintenance in Power Generation: A power generation company utilized predictive maintenance techniques, such as vibration analysis and thermal imaging, to identify potential failures before they occurred. This approach reduced maintenance costs by 25% and significantly improved equipment reliability.
Corrective Maintenance in the Automotive Industry: An automotive company experienced a sudden equipment failure on the production line. Through corrective maintenance, the faulty component was swiftly replaced, minimizing downtime and preventing substantial production losses.
Condition-Based Maintenance in Aviation: An airline implemented condition-based maintenance for its fleet, using advanced sensors and data analytics to monitor the condition of critical components. This strategy improved safety, reduced maintenance costs, and increased aircraft availability.
Conclusion
Effective mechanical maintenance is vital for the smooth operation and longevity of machinery across various industries. By understanding the different types of maintenance, implementing best practices, and addressing common challenges, businesses can enhance equipment reliability, reduce downtime, and achieve operational excellence. Regular inspections, proper lubrication, timely component replacement, and the use of maintenance management software are key strategies for ensuring optimal performance and longevity of mechanical systems.
Explore More Topics
If you found this post insightful, you might also be interested in exploring our other topics that have garnered millions of views:
Mechanical Tools and Their Uses Discover the comprehensive guide to mechanical tools, covering everything from basic hand tools to advanced machinery. Learn about the names and uses of essential tools every mechanical engineer needs.
Forging Tools and Their Uses Explore the various forging tools and their applications. Understand the different types of forging processes and the tools required to achieve precision and efficiency in forging operations.
Mechanical engineering is a challenging yet rewarding field, and with the right mindset and tools, you can navigate its complexities and build a successful career.
Visit our website for more insights: Mech Forged
#artificial intelligence#mechanical pencil#mechanical drawings#mecha#the mechanisms#mechanophilia#robotics#machinery#mecha art#marvin's marvelous mechanical museum#adeptus mechanicus#robot#cybernetics#autos#design#entrepreneur#success
3 notes
·
View notes
Text
Where to Buy Crystal Meth in Queensland

Crystal meth is a synthetic drug that comes in the form of crystalline rocks or bluish-white shards. It is typically smoked, snorted, or injected, producing an intense euphoric rush and increased energy. However, the effects of crystal meth are short-lived and often followed by a crash, leading users to seek more of the drug to maintain the high.
The Dangers of Crystal Meth
The use of crystal meth can have severe consequences for both individuals and society as a whole. Chronic use can lead to addiction, psychosis, cardiovascular problems, and damage to the brain. Additionally, the production and distribution of crystal meth contribute to crime and violence in communities.
Legal Status of Crystal Meth in Queensland
In Queensland, crystal meth is classified as a dangerous drug under the Drugs Misuse Act 1986. Possession, trafficking, and production of crystal meth are criminal offenses punishable by law. Law enforcement agencies are actively involved in combating the illicit drug trade, including crystal methamphetamine.
Risks of Buying Crystal Meth
Purchasing crystal meth in Queensland poses significant risks to both buyers and sellers. Law enforcement agencies conduct operations to target drug trafficking networks, leading to arrests and prosecutions. Furthermore, the quality and purity of crystal meth obtained from illicit sources are often unknown, increasing the likelihood of harmful effects on users' health.
Where to Buy Crystal Meth in Queensland
Despite the legal and health risks, individuals may still attempt to procure crystal meth in Queensland. Several avenues exist for obtaining the drug, including:
Online Sources
Some individuals may attempt to purchase crystal meth through online marketplaces or social media platforms. However, this method is risky and illegal, as law enforcement agencies monitor online activities related to drug trafficking.
Dark Web Markets
The dark web provides a platform for anonymous transactions, including the sale of illicit drugs like crystal meth. However, accessing these markets requires specialized software and presents significant legal and cybersecurity risks.
Street Dealers
Street-level drug dealers may also offer crystal meth for sale in Queensland's urban areas. However, purchasing drugs from street dealers exposes buyers to the dangers of violence, robbery, and arrest.
Risks and Considerations
Regardless of the method chosen, buying crystal meth in Queensland carries inherent risks. Individuals may face legal consequences, including fines, imprisonment, and criminal records. Moreover, the use of crystal meth poses serious health risks, including addiction, overdose, and long-term damage to physical and mental health.
Alternatives to Buying Crystal Meth
Instead of seeking out crystal meth, individuals struggling with substance abuse can explore alternative options for help and support. These include:
Seeking professional treatment for addiction through rehabilitation centers and counseling services.
Participating in support groups such as Narcotics Anonymous (NA) or SMART Recovery.
Utilizing harm reduction strategies to reduce the risks associated with drug use, such as needle exchange programs and overdose prevention education.
While the temptation to buy crystal meth in Queensland may exist, the risks far outweigh any perceived benefits. From legal consequences to severe health effects, the dangers of crystal methamphetamine use are profound. Instead of succumbing to the allure of illicit drugs, individuals are encouraged to seek help and support to overcome addiction and lead healthier lives.
Address: 1569 Ave, New York,NY 10028, USA
Contacts: Email: [email protected] Mobile: +1(818) 714-0948
Visit Here: https://crystalmethshop.com/
3 notes
·
View notes
Text
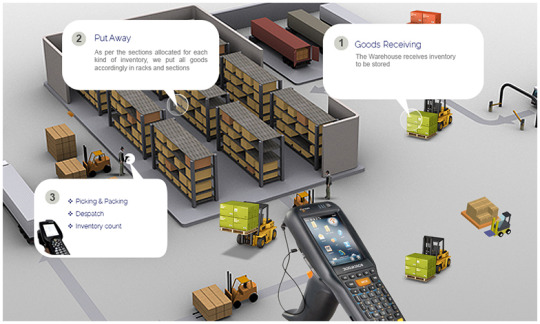
easyTRACK Warehouse Management System
An intelligent solution to control movement and storage of materials within a Warehouse.
A well-structured Warehouse Management system is important for the smooth and efficient operation of any warehouse, irrespective of the size or volume of material it handles. Most of the small and medium warehouses do not require an expensive WMS with redundant features. easyTRACK WMS is a perfect solution on the enterprise mobility for the warehouse management of small and medium enterprises which helps them manage all the essential warehouse functions. easyTRACK warehouse automation software allows the users in warehouse to manage the following operations at their palm.
Goods receiving
Put away
Picking & Palletizing
Dispatch
Stock count, etc.
easyTRACK WMS Lite Benefits
Solves the challenges faced in the conventional system.
Goods Receiving-
Priority Issue Multiple Shipments received at a time
Delayed Data entry Stock may be available but not available for Sale Dead /Damage/Short supply on arrival not instantly notified.
SOLUTION: GRN on PDT “goods receiving made easy with GRN on PDT”
Welcome to Technowave Group, your trusted provider of advanced technology solutions in Dubai. Our RFID Warehouse Inventory Management Systems can help businesses improve their inventory management and provide complete visibility into their warehouse operations.
What is RFID Warehouse Inventory Management System?
RFID Warehouse Inventory Management System uses RFID technology to automate the process of inventory tracking and management. It involves tagging inventory items with that contain unique identification numbers. The RFID tags are read by RFID readers, which transmit the data to a computer system that stores the information and provides real-time updates on the inventory’s location, movement, and status.
Key Features of our RFID Warehouse Inventory Management System
Our RFID Warehouse Inventory Management System comes with the following key features:
Real-time inventory tracking:
Our RFID system provides accurate and up-to-date information on inventory levels, locations, and movements in real-time. This means that businesses can quickly identify any discrepancies, such as missing or misplaced items, and take corrective action before they become bigger problems.
Inventory management:
Our RFID system automates the inventory management process, including item counting, reordering, and tracking. This means that businesses can easily monitor inventory levels and reorder products when they are running low. This helps prevent stockouts and ensures that products are always available for customers.
Asset tracking:
It can track and manage assets, including equipment, tools, and vehicles, helping businesses keep track of their assets’ location, status, and maintenance schedules. This allows businesses to optimize asset utilization and minimize downtime, which can result in significant cost savings.
Reporting and analytics:
The RFID system generates detailed reports on inventory and asset tracking, providing businesses with valuable insights into their warehouse operations. Businesses can use this information to identify areas for improvement and make informed decisions about inventory levels, order fulfillment, and asset management.
Improved accuracy and efficiency:
Our RFID system eliminates the need for manual inventory tracking, reducing the risk of errors and improving accuracy. This saves time and resources by automating inventory management and asset tracking, allowing businesses to focus on other critical tasks.
Improved visibility and control:
It provides real-time updates on inventory and asset movement, giving businesses complete visibility into their warehouse operations. This helps businesses make informed decisions and take corrective action quickly, leading to increased efficiency and productivity.
Improved customer satisfaction:
Our RFID system helps businesses improve their order fulfillment process, reducing stockouts and improving delivery times. This leads to increased customer satisfaction and repeat business, which can be a significant competitive advantage in today’s market.
Compliance with regulations:
Last but not least, our RFID system helps businesses comply with regulations related to inventory tracking and management. For example, our system can provide traceability requirements for food and pharmaceutical products, ensuring that businesses meet regulatory requirements and avoid costly penalties.
Overall, our RFID Warehouse Inventory Management System offers businesses a range of benefits, from increased efficiency and productivity to improved customer satisfaction and regulatory compliance.
Get in Touch With Us!
At Technowave Group, we have a team of experienced professionals who are dedicated to providing high-quality service and support to our clients. We work closely with our clients to understand their unique business needs and provide tailored solutions that help them achieve their goals.
Whether you are a small business or a large enterprise, we can help you leverage technology to improve your warehouse operations and achieve your goals. Contact us today to learn more about our RFID Warehouse Inventory Management System and other technology solutions.
3 notes
·
View notes
Text
Top Tips to Build a Secure Website Backup Plans

Why Website Backup Is Crucial
Website backup is a critical aspect of website management, offering protection against various threats and ensuring smooth operations. Here's an in-depth look at why website backup is essential:
1. Protection Against Data Loss: During website development, frequent changes are made, including code modifications and content updates. Without proper backup, accidental deletions or code errors can lead to irrecoverable data loss.
2. Safeguarding Against Cyber Attacks: Malicious cyber attacks, including ransomware, pose a significant threat to websites. Regular backups provide a safety net, allowing businesses to restore their websites to a pre-attack state quickly.
3. Mitigating Risks of Hardware and Software Failures: Hardware failures or software glitches can occur unexpectedly, potentially resulting in data corruption or loss. Website backup ensures that data can be restored swiftly in such scenarios.
4. Facilitating Smoother Updates and Overhauls: Website updates and overhauls are inevitable for staying current and meeting evolving requirements. Having backups in place streamlines these processes by providing a fallback option in case of unforeseen issues.
Understanding Website Backup
What is Website Backup? Website backup involves creating duplicate copies of website data, including media, code, themes, and other elements, and storing them securely to prevent loss or damage.
Components of Website Backup:
Website Files: Includes all website data such as code files, media, plugins, and themes.
Databases: Backup of databases like MySQL or PostgreSQL, if utilized.
Email Sending: Backup of email forwarders and filters associated with the website.
Tips for Secure Website Backup Planning
1. Choose the Right Backup Frequency: Frequency depends on website traffic, update frequency, and content sensitivity.
2. Opt for Third-Party Backup Solutions: Consider factors like storage capacity, automation, security features, and user-friendliness.
3. Utilize Backup Plugins for WordPress: Plugins like UpdraftPlus, VaultPress, and others offer secure and automated backup solutions.
4. Maintain Offsite Backups: Store backups in remote data centers or cloud services for added security.
5. Test Your Backups: Regular testing ensures backup integrity and readiness for restoration.
6. Supplement Hosting Backup Services: While hosting providers offer backups, explore additional backup solutions for enhanced security and control.
7. Consider Manual Backups: Manual backups provide flexibility and control, especially for specific needs or scenarios.
8. Encrypt Backup Data: Encrypting backup files adds an extra layer of security, preventing unauthorized access.
9. Monitor Backup Processes: Regular monitoring helps identify issues promptly and ensures backup availability.
10. Implement Disaster Recovery Plans: Prepare for unforeseen events with comprehensive disaster recovery strategies.
Secure Website Backup Service with Servepoet
For comprehensive website backup solutions, consider CodeGuard Backup service, offering automated daily backups, robust encryption, and user-friendly management features.
Conclusion
Building a secure website backup plan is vital for protecting against data loss, cyber threats, and operational disruptions. By following best practices and leveraging reliable backup solutions, businesses can safeguard their websites and ensure continuity of operations.
#buy domain and hosting#best domain hosting service#domain hosting services#marketing#cloud vps providers#web hosting and server#shared web hosting
2 notes
·
View notes
Text
MacBook Pro A1989 13" Repair Service #Nehru Place
Conquering MacBook Pro A1989 13" Display Anomalies with Expertise:~~
Our seasoned technicians understand the intricate dynamics of the A1989 13" display, and their expertise is at the forefront of our solution. Whether the flickering is a result of cable wear, hinge stress, or internal friction, our approach goes beyond the surface, addressing the root causes with finesse. We prioritize clarity, precision, and a commitment to delivering a flicker-free display that meets the standards of your MacBook Pro.
By choosing our MacBook Pro A1989 13" Flickering Solution, you're not just opting for a fix; you're embracing a journey led by expertise. Our comprehensive strategies encompass cable inspections, hinge adjustments, and targeted solutions, ensuring a holistic resolution to the anomalies affecting your MacBook Pro display.

Factors Contributing to MacBook Pro A1989 Screen Flickers:~~
The MacBook Pro A1989 is a powerhouse, but users occasionally encounter screen flickering issues that can be both frustrating and disruptive.
Flex Cable Wear: Wear or damage to these cables may lead to intermittent connections, causing screen flickering.
Hinge Stress: Hinge stress may increase friction on flex cables, contributing to flickering issues.
Internal Friction: Microscopic damage from internal friction can disrupt stable display connections, leading to flickering.
Overheating: Overheating may lead to malfunctions in electronic components, including those related to display functionality.
Software Issues: Software-related problems may cause intermittent display anomalies, contributing to flickering.
Graphics Card Malfunction: Malfunctions in the GPU may result in visual artifacts, including flickering on the screen.
Incompatible Software or Drivers: Incompatibility issues may lead to flickering as the system struggles to render graphics correctly.
Interference from External Devices: Electromagnetic interference can disrupt the display signal, leading to flickering.
Display Settings and Calibration: Adjustments to brightness, contrast, or color settings might affect display stability.
Hardware Failures: Damaged hardware components may result in flickering and other display issues.
How Our Company Pinpoints Flickering in MacBook Pro A1989 13" Displays:~~
Comprehensive Diagnostics: We commence our process with a comprehensive diagnostic assessment, utilizing cutting-edge tools and software to analyze the display's performance. This step involves a thorough examination of both hardware and software components.
Flex Cable Inspection: One of the primary contributors to flickering is often wear or damage to flex cables. Our experts meticulously inspect these delicate cables, identifying any signs of wear, tears, or compromised connections that may be causing flickering.
Hinge Stress Analysis: Frequent opening and closing of MacBook Pro laptops can cause stress on hinges, potentially affecting the display. We assess the hinge mechanism for any irregularities and make adjustments to minimize stress on flex cables.
Temperature and Overheating Check: Overheating can impact internal components, including those related to the display. Our diagnostics include monitoring temperature levels and ensuring proper cooling mechanisms to prevent overheating-related flickering.
Software and Driver Audits: Software glitches or outdated drivers can contribute to display anomalies. Our team conducts thorough audits of the operating system, display drivers, and related software to identify and rectify any issues causing flickering.
External Interference Analysis: External devices or accessories can introduce electromagnetic interference, affecting the display. We assess the environment and connected peripherals to minimize interference and enhance display stability.
Graphics Card Evaluation: Issues with the graphics processing unit (GPU) can lead to flickering. Our experts scrutinize the GPU's performance, ensuring it functions optimally and addressing any malfunctions that may be contributing to the flickering.
Display Calibration and Settings Adjustment: Incorrect display settings or calibration can cause visual anomalies. We meticulously adjust brightness, contrast, and color settings to optimize the display experience and eliminate flickering.
Documentation and Reporting: Throughout the diagnostic process, our team maintains detailed documentation. This includes findings, identified issues, and the steps taken for resolution. This documentation serves as a reference for transparency and future troubleshooting if needed.
2 notes
·
View notes
Text
So, in the category of Silly and Impossible Sim Challenges, I wonder what mods, cheats, and mechanics you'd have to use to make Murderbot in Sims 2?
Murderbot is a construct of a type called a SecUnit made of cloned human tissue, extremely complex hardware, and software that integrates with both and makes the hardware look simple. Its primary function is to protect, so it has energy weapons in its arms, superstrength, superspeed, a certain amount of self-healing, and can handle multiple sensory and data inputs, utilizing scout drones and a kind of universal internet/virtual reality environment called "the feed." It can, quite literally, fight a running battle with multiple opponents, hack multiple systems, track what's going on in other locations that it has camera access to, communicate and make coherent plans with other intelligent entities over the feed or through direct verbal communication, and worry about what's going on in places outside of its sensory reach, all at the same time. A lot of its time, however, has been spent monitoring a peaceful environment for threats and hacking systems while consuming media.
It can pass as a human augmented with cyborg technology, and has altered its height and its hair production to make this easier. It also runs subroutines to mimic random human movement when it wants to pass. When it doesn't want to pass, it becomes noticeably uncanny valley.
Corporations abuse their SecUnits functions quite a bit, and install governor modules in their constructs that punish them by directly acting on neural tissue, in case they protect the "wrong thing" (like, workers instead of equipment) but after a certain horrific incident, Murderbot hacked its governor module so that it could do whatever it wanted to. It then kept doing its job, lying low and watching media, because it didn't know what else it wanted to do; only what it didn't want to do. This backstory has left Murderbot full of rage and anxiety. It is touch averse and doesn't like being looked at directly or making eye contact with people. Sometimes it has an Emotion and it wants privacy for that.
It is AAA - agender, asexual, and aromantic. It literally has no sex organs, and being used to spy on clients 24/7 has left it not only indifferent to but deeply repulsed by sex - it fast-forwards through sex scenes in media. It doesn't even like the word "relationship," yet its favorite show is a long-running soap opera, and it tracks the personal relationships of its clients closely (ostensibly for security reasons; if a married couple who treat each other and it well retreat to a room it can't monitor they're more likely to be having sex than plotting against it, while two people who hate each other may break out into violence and require intervention to prevent them from damaging each other and/or company property).
It derives operating energy from a rechargeable battery pack of remarkable productivity and longevity. It could mimic eating or drinking, but what it consumed would just sit in a lung till it could be expelled and that's gross. Most human bodily functions repel it more or less, though it isn't disgusted by seeing people eat. It doesn't sleep but occasionally goes offline during recharge cycles, mostly to avoid conversations it doesn't want to have.
The obvious thing is to make it a servo, which should deal with some of the motive-based things; but the first thing you'd need would be a servo default that looked like a humaniform sim, onto which you could add layerable CC accessories. Its bare feet are a particular problem as they are never explicitly described, but the text makes it clear that they're not remotely like human feet. However, as I understand it (I have never played a servo), servos are on the same gender binary as humaniform sims, so we'd need a lot of androgynous CC, too. Its preferred clothing styles are hoodies and loose pants with lots of pockets (for carrying drones and tools and evidence and stuff; it also has secret compartments in its torso, which we fortunately don't have to worry about because of the inventory mechanic), and it wears boots with most outfits. Oh, yeah, and it can detach extremities and still operate them like drones, which I don't think we can simulate but so far in the series it's only done this once. Another difficulty with servos is that Murderbot's core identity is SecUnit and it resents being asked to do mundane chores outside of its function, while Servos were designed and coded with the notion of a housekeeping bot in mind.
Using an editing tool to set its gender preference at -100/-100 should be sufficient for the asexual/aromantic part. Zero social points is obvious; but nice points are a problem. Murderbot is capable of extreme violence even when its rage isn't activated (its rage is usually activated) but it's never unprovoked violence. It would never walk up to a stranger and flick their nose or otherwise pick a fight. It would recoil from flirts or solicitations to dance or play, but if you did get it to play catch with you, it wouldn't throw the ball at your head - it'd be more likely to aim precisely at your hand so that it's almost impossible for you not to catch it. In a lot of ways it's high nice, but the nice gestures are entirely inappropriate to it.
Active and playful points are another puzzle. Murderbot can stand still for hours, perfectly happy, watching hour after hour of media and scanning for threats, but it can also sustain heavy mental and physical activity for similar stretches of time. It takes life very seriously but has a snarky sense of humor and an endless capacity for media consumption.
Honestly all the personality points are like that. It's scrupulously tidy but isn't down for cleaning up after anybody - that's one of the things drones and cleaning bots are for. It's cripplingly shy but you only have to look vulnerable and it will adopt you as a client and protect you with its life and then some, even if you're not very nice to it. (We only see it happen once, but it has no reason to lie when it says that multiple clients have shot it.)
Aspiration is hard. It likes winning fights and Popularity is the least sexy aspiration, but the idea of it actively wanting to make friends with people or throw parties is absurd. Fortune sims are very sexy and though Murderbot likes getting paid so it can get its own gear and doesn't have to pirate shows it's not much into money otherwise. Pleasure and Romance are right out. Family would be...technically doable but so, so weird in so, so many ways. And Knowledge...well, it's very smart indeed, and highly knowledgeable in its areas of interest, but it's also prone to using words it knows are wrong but can't be bothered to correct, and it complains about the low quality of learning modules provided by the company it was owned by until the end of the first book, but never provides itself with better ones.
It would have to have max body points and stuck smart milk syndrome, but otherwise start play pretty ignorant.
Probably you couldn't really do it satisfactorily at all, but I'm willing to hear suggestions from simmers who have read The Murderbot Diaries, or have played nonhuman sims before and know where the CC is.
5 notes
·
View notes
Text
Decoding Cybersecurity: Unveiling the Future of US Digital Forensics Excellence
What is the Size of US Digital forensics Industry?
US Digital forensics Market is expected to grow at a CAGR of ~% between 2022-2028 and is expected to reach ~USD Mn by 2028.
Escalating cyberattacks targeting individuals, organizations, and critical infrastructure underscore the need for robust digital forensics capabilities. The increasing frequency and sophistication of these attacks drive the demand for advanced tools and expertise to investigate and respond effectively.
Rapid technological advancements, including IoT, cloud computing, AI, and blockchain, introduce new avenues for cyber threats. Digital forensics services are crucial to understanding these emerging technologies' vulnerabilities and mitigating associated risks.
Furthermore, stricter data protection regulations and compliance mandates necessitate thorough digital evidence collection, preservation, and analysis.
Organizations across industries has invested in digital forensics to ensure adherence to legal requirements and regulatory frameworks.
Additionally Legal proceedings increasingly rely on digital evidence. Law enforcement, legal firms, and corporations require robust digital forensics services to gather, analyze, and present evidence in a court of law, driving market expansion.
Us Digital Forensics Market By Type
The US Digital forensics market is segmented by Computer Forensics, Network Forensics, Mobile Device forensics and Cloud forensics. Based on type, Computer Forensics type segment is emerged as the dominant segment in US Digital forensics market in 2022.
Computers are ubiquitous in modern society, utilized across industries, organizations, and households. As a result, a significant portion of digital evidence related to cybercrimes and incidents is generated from computer systems, driving the demand for specialized computer forensics expertise. Computers and their software environments evolve rapidly.
Us Digital Forensics Market By End User Application
US Digital forensics market is segmented by Government and Defence, BFSI, Telecom and IT, Retail, Healthcare and Other Government and Defence market is dominant in end user application segment in Digital forensics market in 2022.
Government and defense agencies handle highly sensitive information related to national security and intelligence. The increasing sophistication of cyber threats targeting these entities necessitates robust digital forensics capabilities to investigate and respond to cyber incidents effectively.
Government and defense entities are prime targets for cyberattacks due to their critical roles. Effective incident response through digital forensics helps in containing and mitigating cyber incidents swiftly, minimizing damage and preventing further breaches.
US Digital forensics by Region
The US Digital forensics market is segmented by Region into North, East, West, South. In 2022, the dominance region is East region in US Digital forensics market.
The East region has a dense population and a well-established digital infrastructure, making it a hotspot for cybercriminal activity. The higher frequency of cyber threats and incidents necessitates a strong emphasis on digital forensics to investigate and mitigate these risks effectively. Additionally, the East region often sees a proactive approach from regulatory and legal bodies, reinforcing the demand for digital forensics services to ensure compliance and assist in investigations. The proximity of key players in law enforcement, government agencies, legal firms, and corporate headquarters further fuels the need for robust digital forensics capabilities.
Download a Sample Report of US digital forensics Solution Market
Competition Scenario in US Digital forensics Market
The US digital forensics market is characterized by a competitive landscape with several key players competing for market share. Prominent companies offering a range of digital forensics solutions and services contribute to the market's dynamism.
The competitive landscape also includes smaller, specialized firms and start-ups that focus on niche areas of digital forensics, such as cloud forensics, memory forensics, and industrial control systems forensics.
The competition is further intensified by the continuous evolution of technology, leading to the emergence of new players and innovative solutions. As the demand for digital forensics continues to grow, companies in this market are likely to invest in research and development to stay ahead of the curve, leading to a consistently competitive environment.
What is the Expected Future Outlook for the Overall US Digital forensics Market?
Download a Custom Report of US digital forensics market Growth
The US Digital forensics market was valued at USD ~Million in 2022 and is anticipated to reach USD ~ Million by the end of 2028, witnessing a CAGR of ~% during the forecast period 2022- 2028.
The US digital forensics market is poised for robust expansion due to the ever-evolving cybersecurity landscape, technological advancements, and regulatory pressures. Organizations across industries will increasingly recognize the necessity of investing in digital forensics to safeguard their digital assets and ensure compliance.
As long as cyber threats continue to evolve, the demand for sophisticated digital forensic tools, services, and expertise will remain on an upward trajectory.
The US digital forensics market appears promising, characterized by a confluence of technological advancements, increasing cyber threats, and growing legal and regulatory requirements. As technology continues to evolve rapidly, so does the nature of cybercrimes, creating a persistent demand for digital forensics solutions and services.
Additionally, the escalating frequency and complexity of cyberattacks. As more critical operations and personal information are digitized, the potential attack surface expands, leading to a higher likelihood of security breaches. This dynamic compels organizations and law enforcement agencies to enhance their digital forensic capabilities to investigate, mitigate, and prevent cyber incidents effectively.
Furthermore, the rise of emerging technologies like the Internet of Things (IoT), artificial intelligence (AI), and blockchain presents both opportunities and challenges. These technologies bring new possibilities for efficiency and connectivity but also introduce novel avenues for cyber threats. Consequently, the demand for digital forensics services is expected to surge as organizations seek expertise in unraveling incidents involving these cutting-edge technologies.
The market is also likely to see increased adoption of cloud-based digital forensics solutions. As more data is stored and processed in the cloud, digital forensic providers will need to develop tools and methodologies to effectively gather evidence from virtual environments, remote servers, and distributed systems.
2 notes
·
View notes
Text
Benefits Of Kmspico Microsoft Windows Activator

KMSPICO works as an activation software that grants users the ability to install Windows and Microsoft Products for both free or for a lifetime. It's easy-to-use and comes with a smaller software package that can be easily installed. Furthermore, it is completely safe to use as there are no viruses nor malware in it.
There is no need to generate product keys.
It's no mystery that MS products tend to cost a lot. Nonetheless, there exist ways around paying for these heftily priced products. One method utilized is by using activation. This program allows the activation of pirated versions of Windows, as well as other Windows products, for no cost. The most notable feature is the fact that this tool is virus- and malware- free.
The application operates by interacting with a trusted server, which holds various authorized keys for Windows Activation. It's important for users to understand that all systems cannot be activated with panacea. It is also not compatible with all Microsoft Office versions.
Many people have claimed that an antivirus program has advised against downloading and installing kmspico windows 10 due to its alleged shadiness and connection with malware. Despite being warned, the KMSPICO tool continues to be used regularly by those who seek a cost-effective and dependable way of activating their pirated Windows. This holds especially true for those students who are unable to purchase a licensed version of Microsoft's software.
No risk of Fraude detection.
KMSpico acts as a fake key management service server. KMS Servers are utilized to license Microsoft applications for organizations with large volumes. KMSPICO can infringe Microsoft's service agreements and result in software piracy. Moreover, using this software can lead to legal troubles since it infringes copyright law.
Many cybersecurity experts advise against obtaining KMSPICO. These cheat tools tend to be distributed via fake downloading portals, search engines, and sales websites. These may be accompanied by self-signed certificates that attempt to make them seem authentic. These programs can potentially pose a danger as being Headless Trojans or Malware. This renders them hard to recognize by anti-virus programs.
KMSPICO may cause software activations or pop-up warnings and inhibit users' access to updates, support, and other features available only through licensed products. In addition, this application can lead users to malicious websites that aim to gather personal data or inflict viruses. To prevent these threats, only utilize a legitimate program that is also free.
KMSpico is easy to use and does not contain any viruses or malware that can harm the computer.
KMSpico is easy to use and does NOT contain any virus or malicious code that can damage the computer. It does NOT rely on an Internet connection and will not make the computer sluggish or perform poorly. Its installation and usage are simple.
KMSPICO supports both the modern as well as the vintage editions of both Windows® and MS Office®. It utilizes a software program known as KMS, which communicates with a remote server for activating Microsoft software. Unlike some activators, kmspico for windows 11 does NOT install any patches or cracked versions of the OS and remains updated frequently.
kmspico can be downloaded for FREE from reputable websites and used to reactivate Microsoft Products for ever. It is a simple tool that doesn't require any technical knowledge to operate. It's a straightforward tool to operate that doesn't require any technological knowledge. It can be used to both conserve money while still obtaining the highest quality features from branded Microsoft software.
The lifetime license is valid for two years.
KMSPico ranks among the select few activators that grants a perpetual license. It supports activating both Microsoft Windows and Microsoft Office Products, which include the most recent version of Windows 10. It supports using both 32- and 64-bit systems. Unlike many other activator software, this one is not obstructed by a complicated installation and can be downloaded and utilized for free.
KMSPico, which is frequently employed by piraters to circumvent Microsoft licensing requirements, is plagued by numerous flaws and should never be used. It is particularly dangerous if it's downloaded through a phishing website. It is capable of modifying system configurations and restricting access control to disaster recovery and backup images. It's important that cybersecurity, legality, and security are given a higher priority when selecting software licenses and activations. This explains why using authentic Microsoft software is preferred. Furthermore, this approach ensures the compliance with copyright legislation and supports software authenticity. Additionally, it can prevent users from incurring expensive license fees by preventing unauthorized installation.
KMSPICO can be used free of-charge and permanently unlock Microsoft Windows and all other products. It's easy to use and relatively small in size, making it very easy for users to set up. KMSPICO is completely safe to use and doesn't include any virus or malicious code.
There is no need to purchase product keys anymore.
It's no surprise that purchasing Microsoft can become expensive. Nonetheless, there exist ways around paying for these heftily priced products. One method utilized is by using activation. This program allows the activation of pirated versions of Windows, as well as other Windows products, for no cost. The most notable feature is the fact that this tool is virus- and malware- free.
The application operates by interacting with a trusted server, which holds various authorized keys for Windows Activation. It's important for users to understand that all systems cannot be activated with panacea. It is also not compatible with all Microsoft Office versions.
Many people have claimed that an antivirus program has advised against downloading and installing kmspico windows 10 due to its alleged shadiness and connection with malware. Despite being warned, the KMSPICO tool continues to be used regularly by those who seek a cost-effective and dependable way of activating their pirated Windows. This applies particularly to students who may lack the funds to purchase a licensed version of Windows.
No risk of Fraude detection.
KMSpico acts as a fake key management service server. KMS Servers are utilized to license Microsoft products for larger organizations. KMSPICO can infringe Microsoft's service agreements and result in software piracy. Moreover, using this software can lead to legal troubles since it infringes copyright law.
Many cybersecurity experts advise against obtaining KMSPICO. These cheat tools tend to be distributed via fake downloading portals, search engines, and sales websites. These programs may also contain self-signed certificates, attempting to make them look legitimate. These programs can pose a threat because of being infected with trojan-like and potentially infected malware, which can make them extremely difficult for antivirus software to identify.
KMSPICO may cause software activations or pop-up warnings and inhibit users' access to updates, support, and other features available only through licensed products. In addition, this application can lead users to malicious websites that aim to gather personal data or inflict viruses. To minimize these risks, ensure that the software utilized is both legitimately and completely free.
KMSpico is easy to use and does not contain any viruses or malware that can harm the computer.
KMSpico is easy to use and does NOT contain any virus or malicious software that can infect or damage the computer. It does NOT rely on an Internet connection and will not make the computer sluggish or perform poorly. Its size of the software is compact, making it easy for users to easily set up and utilize.
KMSPICO supports both the modern as well as the vintage editions of both Windows® and MS Office®. It utilizes a software program known as KMS, which communicates with a remote server for activating Microsoft software. Unlike some activators, it doesn't require installing any patches or cracked operating systems, and it is frequently updated.
kmspico windows 10 can be downloaded for FREE from reputable websites and used to reactivate Microsoft Products for ever. It is a simple tool that doesn't require any technical knowledge to operate. It's a straightforward tool that doesn't require any technological knowledge. It allows users to acquire a discounted price while still getting the superior features that come with a licensed Microsoft system.
A lifetime license is available for purchase.
KMSPico ranks among the select few activators that grants a perpetual license. It supports activating Microsoft Office and Windows products, which include the most recent version of Microsoft. It supports using both 32- and 64-bit systems. Unlike many other activators, this one does not need any complicated installation and can be downloaded and used immediately.
KMSPico, which is frequently employed by piraters to circumvent Microsoft licensing requirements, is plagued by numerous flaws and should never be used. It is particularly dangerous if it's downloaded through a phishing website. It may also modify system configurations and obstruct access to recovering options such as shadow volumes. It's important that cybersecurity, legality, and security are given a higher priority when selecting software licenses and activations. This explains why using authentic Microsoft software is preferred. Additionally, this technique ensures that software is in compliance and authenticated. Additionally, it can prevent users from incurring expensive license fees by preventing unauthorized installation.
3 notes
·
View notes
Text
Optimize Asset Protection with Advanced Damage Prevention Software
Discover cutting-edge damage prevention software designed to streamline utility management and prevent costly infrastructure damage. At Norfield DP, we offer advanced tools to empower utility operators, contractors, and municipalities with efficient solutions for managing excavation and underground assets.
Our damage prevention software ensures seamless communication between stakeholders, reduces risks, and enhances safety in excavation projects. By automating workflows, tracking underground utilities, and providing real-time insights, we help you mitigate damage, improve productivity, and meet compliance standards effortlessly.
Whether you are involved in pipeline management, construction, or utility operations, our software provides reliable tools for underground asset protection, utility mapping, and risk management. Say goodbye to delays and costly damage repairs with precision-driven solutions tailored to your needs.
Choose Norfield for innovative damage prevention solutions that support your operational goals while prioritizing safety and efficiency. Visit Norfield DP today to explore how our software can transform your damage prevention strategy.
#damage prevention software#underground asset protection#damage prevention solutions#utility damage prevention#excavation risk management#utility mapping software#Norfield damage prevention#infrastructure damage prevention tools
1 note
·
View note
Text
Leading Tips to Avoid Costly Medical Billing and Coding Errors in 2024
Top Tips to Avoid Costly Medical Billing and Coding Errors in 2024
In the rapidly evolving healthcare industry, accurate medical billing and coding are more critical than ever. Errors in billing and coding can lead to denied claims, delayed reimbursements, compliance penalties, and ample financial losses. As we step into 2024,implementing best practices to prevent these costly mistakes is essential for healthcare providers,medical billers,and coding professionals alike. This comprehensive guide offers valuable insights and actionable tips to help you reduce errors and optimize yoru medical billing processes.
Understanding the Impact of Medical Billing and Coding Errors
Medical billing and coding are fundamental components of healthcare administration. They ensure healthcare providers get paid for services rendered while maintaining compliance with regulations. However,errors such as incorrect code assignment,duplicate claims,or missing facts can have serious repercussions:
Increased claim denials and rework
Delayed revenue cycle and cash flow problems
Compliance risks,including audits and penalties
Patient dissatisfaction and trust issues
Legal liabilities and reputation damage
Benefits of accurate Medical Billing and Coding
Prioritizing accuracy in billing and coding offers several tangible benefits:
Enhanced revenue cycle management
Reduced claim rejection rates
Better compliance with regulations like HIPAA and CMS standards
Improved patient satisfaction through accurate billing
Streamlined administrative workflows
practical Tips to Prevent Medical Billing and Coding Errors in 2024
1. Keep Up-to-Date with Coding Guidelines and Regulations
The healthcare coding landscape is constantly changing. Ensure your staff stays current with updates from the American Medical Association (AMA), Centers for Medicare & Medicaid Services (CMS), and other relevant bodies. Subscription to official coding updates, webinars, and continuing education courses can substantially reduce coding errors.
2. Invest in Quality Medical Coding Software
Automated coding tools can minimize human errors by suggesting appropriate codes based on clinical documentation. Choose reliable, compliant software that integrates seamlessly with your Electronic health Record (EHR) system. Regularly update your software to reflect the latest coding standards.
3. Conduct Regular Staff Training and Education
Ongoing training ensures your billing and coding team understands the nuances of coding, billing rules, and compliance requirements. Training should cover common errors, new coding updates, and best practices in documentation.
4. Implement Robust Documentation Practices
Clear, accurate, and detailed clinical documentation lays the foundation for correct coding.Encourage staff to document services comprehensively, including diagnoses, procedures, visit reasons, and modifiers when applicable.
5. Perform Routine audits and Quality Checks
Regular audits help identify error patterns and areas needing improvement. Establish a schedule for internal audits and consider third-party audits periodically. Use audit findings to update training and refine processes.
6. Use Checklists and Coding Compliance Tools
A standardized checklist can ensure all coding elements are correct before claim submission. Incorporate compliance tools that flag potential errors, such as incorrect modifiers or incomplete information.
7.Maintain Open Communication Between Clinical and Billing Teams
Encourage collaboration between healthcare providers and billing specialists. When clinicians understand billing requirements, they can provide more precise documentation, reducing misinterpretations and errors.
8. Leverage Data Analytics for Error Monitoring
Utilize data analytics tools to monitor billing trends, identify anomalies, and measure coding accuracy over time. data-driven insights enable targeted improvements and proactive error correction.
Case Studies: Success Stories in Error Reduction
Practise Type
Error Reduction Strategy
Outcome
Small Clinic
Annual staff coding workshops and monthly audits
Claim rejection rate decreased by 25% in one year
Mid-sized Hospital
implemented integrated billing software with real-time error alerts
Reimbursement delays cut by 40%
Specialty Practice
Enhanced documentation protocols and clinician training
Error-related denials reduced by 30%
First-Hand Experience: Implementing a Prosperous Error-Prevention Program
In our own experience working with diverse healthcare providers, we found that a combination of staff education, technology, and ongoing audits yields remarkable results. such as, a dermatology practice we assisted integrated AI-powered coding software and established monthly review meetings, leading to a noticeable decrease in coding errors and increased staff confidence.The key takeaway? Consistency and continuous improvement are essential for success in reducing costly errors.
Conclusion
Accurate medical billing and coding are vital to the financial health and regulatory compliance of any healthcare organization. As we navigate through 2024, adopting proactive measures-such as staying current with regulations, investing in technology, continuous staff training, and implementing regular audits-can help prevent costly errors. By prioritizing accuracy and efficiency, healthcare providers can improve revenue cycle management, enhance patient satisfaction, and maintain compliance with evolving standards.
If you want to stay ahead in the dynamic healthcare habitat, adopting these top tips now will position your practice for success in 2024 and beyond. Remember,prevention is always better than cure when it comes to medical billing and coding errors.
https://medicalbillingcertificationprograms.org/leading-tips-to-avoid-costly-medical-billing-and-coding-errors-in-2024/
0 notes
Text
Ways to protect your copyright
Protecting Your Copyright: A Quick Guide
Copyright is a legal right that gives creators control over their original works, whether it’s writing, music, art, or software. Safeguarding your copyright is crucial to prevent unauthorized use and to ensure you get the recognition and compensation you deserve for your creations. Here are some essential tips to help you protect your copyright:
Know Your Rights
The moment you create an original piece and put it into a tangible form, copyright protection kicks in. You automatically gain exclusive rights to reproduce, distribute, display, and perform your work.
Register Your Copyright
Although registration isn’t mandatory, officially registering your work with your country’s copyright office (like the U.S. Copyright Office) can offer significant legal benefits, including the ability to sue for damages if someone infringes on your rights.
Add Copyright Notices
Placing a copyright notice (for example, © [Year] [Your Name]) on your work lets others know that it’s protected and identifies you as the owner. This simple step can help deter potential infringement.
Keep Good Records
Make sure to save drafts, timestamps, emails, or any other evidence that shows how your work developed. This documentation can be crucial if you ever need to prove ownership.
Utilize Licensing Agreements
If you decide to let others use your work, always use written licensing agreements. These documents clarify how your work can be used and help you maintain control over it.
Keep an Eye on Your Work Online
Use tools like Google Alerts or reverse image searches to see if your work is being used without your permission. If you find any infringement, you can send a takedown notice or consider legal action.
By following these steps, you can better protect your creative efforts and ensure that your rights as a copyright holder are honored.
by beatrice
0 notes
Text
Conductive Foam For Static And EMI Protection
Conductive Foam is a specialized cloth applied in electronics and electric programs for electromagnetic interference (EMI) protection, static discharge protection, and thermal management. It includes a foam center—normally polyurethane or polyethylene—blanketed or embedded with conductive materials which includes nickel, copper, silver, or carbon. This aggregate makes the foam not simplest compressible and mild-weight however also electrically conductive, making it a flexible solution in modern electronics.
Key Features of Conductive Foam
EMI Shielding- One of the primary uses of Conductive Foam Supplier in China is to shield touchy electronic components from electromagnetic interference. As electronic devices come to be smaller and extra effective, the threat of EMI disrupting indicators or negative components increases. Sinkeryfoam provides a cost-effective and adaptable barrier that absorbs and displays electromagnetic waves.
Static Discharge Protection- Conductive Foam is likewise used to prevent electrostatic discharge (ESD), which could damage touchy components like microchips and circuit forums. Foam utilized in packaging and transportation gives a secure medium to shop or deliver electronics without the danger of static buildup.
Flexibility and Compressibility- Thanks to its foam base, conductive foam is flexible and can agree to irregular shapes and areas. It’s ideal for sealing gaps in enclosures or among surfaces at the same time as retaining conductivity. This makes it beneficial in gaskets, grounding pads, and protective strips.
Customizable Forms- Conductive foam can be die-reduce, laminated, or adhesive-subsidized for clean software. Manufacturers regularly produce it in several thicknesses and densities to fulfill specific universal overall performance and environmental requirements.
Common Applications
Conductive Foam in China is substantially used throughout diverse industries, which incorporates:
Medical Devices: Sensitive scientific units depend upon conductive foam to hold universal performance integrity.
Automotive: Used in infotainment structures, sensors, and electric powered vehicle (EV) electronics to ensure strong operation.
Industrial Equipment: Machinery and robotics frequently require EMI protection in noisy electric environments.
Benefits of Using Conductive Foam
Lightweight and clean to handle
Highly flexible and compressible
Effective over a huge frequency range
Available in flame-retardant and RoHS-compliant versions
Reduces detail failure due to EMI and ESD
Conclusion
Conductive Foam Manufacturer in China is an important material for cutting-edge electronics, imparting multi-useful safety in compact, adaptable bureaucracy. Its ability to dam EMI, discharge static, and comply with complex geometries makes it a bypass-to answer for engineers and manufacturers. As the call for compact, high-velocity electronics continues to develop, the position of Sinkeryfoam in making sure reliability and usual performance is extra important than ever.
#Conductive Foam#Conductive Foam in China#Conductive Foam Supplier in China#Conductive Foam Manufacturer#Conductive Foam Sheet#foam
0 notes
Text
BPE - Your Trusted Partner for Uninterrupted Power
In an increasingly digital and interconnected world, the reliance on continuous, clean power has never been more critical. From the vast server farms driving global communication to the personal desktop that powers your daily productivity, any power disruption can lead to significant data loss, operational downtime, and financial setbacks. This is where Battery Power Equipment (BPE) steps in. As one of the leading UPS Manufacturers & Suppliers in India, BPE is dedicated to providing cutting-edge Uninterruptible Power Supply (UPS) solutions that ensure unwavering power for critical infrastructure, personal workstations, and everything in between.
At BPE, we understand that power protection is not a one-size-fits-all solution. Our expertise spans the entire spectrum of power backup needs, from highly complex and demanding environments like data centers to simpler yet equally crucial individual setups. Our commitment to innovation, reliability, and customer satisfaction has cemented our position as a preferred choice among UPS Manufacturers & Suppliers in India.
Fortifying the Digital Core: UPS for Data Centers & UPS Systems for Data Centers
Data centers are the very heart of the digital economy. They house the servers, storage, and networking equipment that keep businesses running, power cloud services, and facilitate global communication. Any downtime in a data center can lead to catastrophic consequences, measured in millions of rupees lost per minute. This is precisely why robust and reliable UPS FOR DATA CENTERS are not just an option, but a fundamental necessity.
BPE specializes in designing, manufacturing, and supplying advanced UPS Systems for Data Centers that provide unparalleled power protection. Our solutions are engineered to meet the stringent demands of modern data center environments, ensuring:
Continuous Power Flow: Our UPS Systems for Data Centers provide immediate, seamless power during outages, preventing hardware damage and data corruption. They utilize advanced online double conversion technology, which isolates critical loads from raw utility power, providing a consistently clean and stable power supply.
Scalability and Flexibility: As data centers grow, their power requirements evolve. BPE's UPS solutions are designed for modularity and scalability, allowing for easy expansion to meet increasing demands without extensive overhauls.
High Efficiency: With a focus on reducing operational costs, our UPS FOR DATA CENTERS are engineered for high energy efficiency, minimizing power loss and cooling requirements.
Redundancy and Reliability: We incorporate robust redundancy options (N+1, 2N architectures) to eliminate single points of failure, ensuring that even if a component fails, the power supply remains uninterrupted.
Intelligent Monitoring & Management: Our UPS Systems for Data Centers come with sophisticated monitoring software, allowing data center managers to track power conditions, battery health, and system performance in real-time, enabling proactive maintenance and issue resolution.
Seamless Integration: Designed to integrate smoothly with existing data center infrastructure and building management systems.
As experienced UPS Manufacturers & Suppliers in India, BPE provides comprehensive support from consultation and design to installation and ongoing maintenance for your critical data center infrastructure.
Empowering Individual Productivity: The Best UPS for Desktop
While data centers grab headlines, the need for reliable power backup extends to every home office and personal workstation. A sudden power cut can erase hours of work, damage hardware, or interrupt crucial online meetings. This is why having the Best UPS for desktop is an essential investment for anyone who relies on their computer.
BPE offers a range of UPS solutions tailored for personal and small office use, designed to be user-friendly, efficient, and highly effective. Our models designated as the Best UPS for desktop typically feature:
Instantaneous Backup: Providing immediate power transfer to battery when mains power fails, ensuring your desktop (and connected peripherals like monitors, modems, and routers) stays on without interruption.
Surge Protection: Shielding your valuable electronics from harmful power surges and voltage fluctuations that can cause irreversible damage.
Sufficient Runtime: Offering enough battery backup time to safely save your work, shut down your computer gracefully, and maintain internet connectivity for critical communication. BPE offers options ranging from minutes to several hours, depending on the model and load.
Compact Design: Designed to fit neatly under a desk or in a small office space without being obtrusive.
Silent Operation: Ensuring a quiet working environment, unlike noisy generators.
Easy Installation: Plug-and-play functionality makes setup simple for any user.
Choosing the Best UPS for desktop from BPE means safeguarding your productivity, protecting your valuable equipment, and ensuring continuity in your work or leisure activities.
BPE: Your Trusted UPS Manufacturers & Suppliers in India
Our commitment at BPE goes beyond just manufacturing and supplying UPS units. We are a team of power protection specialists dedicated to understanding the unique challenges faced by our clients across India. Our comprehensive portfolio covers a wide range of needs, making us a one-stop solution for reliable power backup.
As one of the leading UPS Manufacturers & Suppliers in India, BPE is proud of its:
Robust R&D: Continuous innovation to bring cutting-edge power solutions to the market.
Strict Quality Control: Ensuring every unit meets the highest international standards for performance and durability.
Pan-India Presence: A strong distribution and service network ensuring timely delivery and support across the country.
Customer-Centric Approach: A dedicated support team always ready to assist with technical queries, installation, and after-sales service.
In a world where power is paramount, BPE stands as your steadfast partner, providing the reliable and efficient UPS FOR DATA CENTERS, the essential Best UPS for desktop, and a full spectrum of robust UPS Systems for Data Centers. Choose BPE for uninterrupted power, unparalleled protection, and complete peace of mind. Contact us today to discuss your specific power backup requirements and discover the BPE advantage.
#UPS FOR DATA CENTERS#UPS Systems for Data Centers#Best UPS for desktop#UPS Manufacturers & Suppliers in India#Top UPS Manufacturers in india
0 notes