Don't wanna be here? Send us removal request.
Text
Hurdles to Becoming a Good Developer
Source code is confusing. There can be thousands of functions in many different directories. The codebase can get messy fast. It is thus important to develop a well-designed piece of software. Planning the software out is one of the most important things a developer can do. It allows only what is needed to be written and saves time. Once the scope is known the developer can look to shorten his code by omitting unnecessary lines. That said he needs to be crafty to do so. The smaller the codebase the better.
Writing more than needed is one of the main flaws in beginner software developers. A software developer does not need to do work out of scope. It can create problems down the road. A developer only needs to write code that is being used and is needed. All other code should be deleted. This shortens the code base and makes it easier to read and understand.
When developing code comments are an important aspect. They help explain code, making it easier for other developers to understand and edit. That said too much of anything can be bad. Comments do not stray from this rule. Comments take up lines and can turn a five-line function into 10 or more. The comment may even be longer than the function. It is thus important only to comment what is necessary.
Good code is short and concise. A reader may not understand the logic inside a function but should be able to tell what the function does. A proper function name should do the job. For example, take a function that is mathematically heavy. A comment could be used to let the reader know what is being done. A comment could also be used at every step explaining it. This creates havoc on the codebase. The reader is spending more time reading the comments then the actual code. A simple refactor by creating a function with a creative name that explains the function in two to three words can convey all the information needed. If one still does not understand the function, due to the smart naming, the reader can due a quick web search about the function and understand the steps. Variables should follow similar rules. The name should represent what it is storing. Software development is about being smart and concise, no need to write more then needed.
The concept of only writing what is need can be applied to design as well. Too often a hungry go getter developer will try to write and do more than what is needed. A simple task will be turned into a complicated one. Usually this makes code generic. The functions written may help and be needed in the future but now are not. Making these extra functions takes time. Not only is time being used on useless functions but also on testing. A project that may take two to three person months may now take a person year. It is important to know what is needed and the future of the project, so over designing does not occur.
A good developer plans. The developer knows what is coming and the scope of the project. He is concise and only writes what is needed. He is lazy in time but makes up for it with his brain. He is crafty and smartly writes only what is needed. His code makes sense and is quick to read, with proper naming. The key to good software design is to be short a sweet. A task that seems easy but is very daunting.
0 notes
Text
Choosing a H/FOSS
H/FOSS (Humanitarian Free Open Source Software), like many things, come in many shapes and sizes. Four main types are single vendor, developer communities, user communities, and competence centers. Each type works to produce free software to solve specific problems. As they each are structed differently the H/FOSS groups have different methodology and structure on how the software is maintained and created. Single vendors are single leader developing companies, while competence centers are lead by a board of directors and already have a predetermined chain of command. User communities, as the name suggests are lead by software users where developing communities are lead by individual developers. As a project progresses and grows it may mutate and become a different type of project. For example, as a single vendor project grows it may need to change into a developer community as the number of pull requests becomes too great on the lead developer. This is the case with many H/FOSS communities that have a good culture.
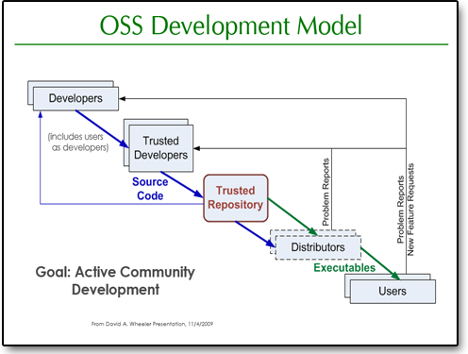
A good culture attracts passionate members that improve the project. Once a new member contributes, they become a rightfully named contributor. These contributions can be small as fixing documentation or finding a bug to as large as refactoring the whole code base or adding a brand-new feature. Every contribution is helpful as it helps expand the project.
Every contribution or issue according to GitHub has its challenges. Within the Development Model it is important to have good communication and documentation to work through challenges. As many F/HOSS projects are used by fortune 500 companies there needs to be a structure to the project. Projects should have a README file that contains all useful information. This includes code of conduct, code format, communication channels, installation instructions, mission statement, project goals, and anything else that a user or developer may need. A well-documented project makes contributing easier as everything is in order.
An organized project allows for users to report bugs. The developers can quickly find and fix the bugs. This is in accordance to the model above. The users report bugs for the developers to fix and post to the repository. However, this does not always go smoothly. Passion in a F/HOSS project is important, however can be deadly as well. Depending on the project and the structure of the community behind it, a singular passionate person can be fatal. Although HFOSS communities tend to be welcoming communities some have leadership problems. For example, let’s look at a single vendor community. A user has a suggestion to improve the project. This suggestion however will revamp the application and undermine all the hard work the leader has done. The leader thus does not allow the pull requests to merge into the project. He has become a dictator, pushing contributors away from the project, hindering its growth.
When looking to contribute to a F/HOSS project, it is important to find the right group. A wrong group can hinder your growth as a developer. Take the time to review all the documentation and look through the communication channels. Choosing a F/HOSS community is like choosing a job. If unorganized or has a bad culture, a job quickly becomes toxic and a negative work environment. The same goes with F/HOSS projects.
0 notes
Text
Initial Blog part 2
OK we are back at It. However this is the first semester of the the senior seminar (491 not 492) at Dickinson College. So once again this blog is made to be reflective as we have class discussions about legal, ethical, and social problems that involve technology.
Plans After College:
My plans after this semester is to get a job in cyber security. I have a few contacts to people in DC. I hope they work out.
0 notes
Text
Reflective Blog Post
My 492 senior seminar is coming to a close. It had been an interesting ride. I am sad I have to get off. Overall this course has been very insightful. I have learned how to work as a developer expanding on my civic skills along with technical skills. The most challenging part was learning the technical skills needed for to make the contributions.
Some technical aspects that I have learned revolves around frameworks. Two frameworks that I had to learn was Vaadin and Springboot. These were very interesting as I have never worked with them before. These were some of the first frameworks that I have worked with. It is interesting to see how much easier they make things. That said some are not easy to learn.
This course has definitely helped increase my ability to reach out for help over the internet. I am very good at reaching out and learning in person, however reaching out over the internet is new for me. As the project manager is from the England there is no way we can meet in person. It has been an eye opening experience reaching out for help.
In regards to the blogs and the readings they have helped broaden my knowledge of how technology is effecting the world. Technology feels as it has been around for ever when really it is still in its infancy. Being able to talk about the new technologies has been very insightful and a good learning experience.
This class has been one of my favorite at Dickinson. I have learned more than I have in another class while at the same time I feel like I have learned nothing. The class I showed me what I want to do for the rest of my life. I am glad this is part of the school curriculum.
Big Shoot Out to my professor. Thank you for all the help this semester.
0 notes
Text
Quantum Computing

Quantum computing is a new type of computing that harnesses the phenomena of quantum mechanics. Quantum mechanics follow a different set of rules that we see in our day to day life. For example, we do not experience quantum entanglement. A cut on my brothers arm does not effect me in anyway. If it did we would be quantumly entangled. With quantum entanglement, this is not the case. It would be impossible to describe my state without describing my brothers. We are essentially linked no matter where we are in the universe. These machines take advantage of quantum mechanic laws to be able to compute problems that supper computers cannot do reasonably.
If we look at Grover's Search algorithm it is able to find an item in a list in sqrt(N) time. A normal computer would take on average N/2 or at most N time. This is impressive. To put it in perspective, to find a single item in a list of 1 trillion items, it would take a classical computer about a week. A Quantum computer can do this in a second. That speed causes some trouble for the modern day computers.
Currently quantum computing is limited. Due to the expense of these computers there are only a few of them. Like modern day computers they too will become main stream as they decrease in size and price. However until that happens they produce a risk. Do to the speed they are able to compute at, they are able to break popular hashing algorithms. We have solutions for this however it can be costly. All encrypted data would need to be re encrypted. This can be costly in time and expense. Sadly this is only a short term solution as well. If quantum computers get powerful enough they will be able to solve these stronger hashing algorithms as well.
All I got say is change is coming. Grab some popcorn.
0 notes
Text
Facial Recognition
Facial Recognition is a new popular form of security. Its easy you look and its already unlocked. Supper convenient. Especially for phones. However is it secure? Apple claims they measure around 30,000 points of data to unlock your phone. This is used then to adapt your face as ones face is always changing. That is like a 30,000 character long password. Sounds secure right. WRONG!
There have been countless results of masks being able to trick an iPhone into unlocking. This is why I am sad to say facial Recognition is not secure. I would not want to protect my bank account with my face. Details are not fully worked out yet.
That said I still use my face to unlock my bank account while using my phone. This is different. Like ATMs today a physical device is needed. In this case the phone. ATMs use a card is which is linked to a password or pin. To unlock an ATM both are needed.
Using facial recognition everywhere is not secure. As mentioned above a mask can unlock an iPhone and thus possibly ann ATM. It is all the same thing. Facial Recognition is great for ease however I would not trust it as a full security measure.
0 notes
Text
Data Privacy
Recently there has been a debate about who has ownership of the data collected from the internet. Is it the company's or the users. Both have the right of claim. In this post I will discuss both sides.
To start we need to set the scene. Let's imagine a new Facebook user. To sign up one must enter an email and a password. After the account is created a the user follows some pages, adds friends, and is the average Facebook user.
In the process of signing up Facebook already has some of your personal data. As you start using Facebook more metadata is collected. This is where the gray area is. Who has possession.
Facebook would argue that in order to provide the best services they collect this data. Upon signing up for Facebook one accepts the metadata collection.
The User would argue saying that he was just using facebooks normal services and didn't need Facebook to collect the times that he logged on each day or search history. Gives him no benefit. It is also his actions that created the metadata. Thus it belongs to him.
Both have a right of claim.
The problem with Facebook collecting the data is what happens if they get hacked or want to sell the data. It's an asset to them. It can also be detrimental to the user. One can use services such as Facebook and other social media platforms to profile a person. It can cause harm in a number of ways.
It is important to protect data that is collected as one never knows what will happen in the future.
0 notes
Text
Cant Escape
I don't know if any of you have heard of the IoT (Internet of Things), but it surrounds our life. To give a simple definition it is the internet and anything that connects to it. Your phone, dishwasher, laptop, security system, smart watch, xbox, basically anything with a transmitter is a part of it.

With IoT data is collected every time you use the device. Depending on company and device the data may or may not be shared with third parties. These third parties then use our data for their own purposes, usually targeted ads. When we talk about data privacy its hard to deny that there is privacy. A company may not share the data collected but it can always be subpoenaed by a judge.
Some of the scariest data collections are from the smart assistants that are always listening. Alexa one of the big three smart assistants is the worst at protecting your data. In order to improve Alexa, Amazon listens to your audio recordings. According to Matt Ferrell a YouTuber, Amazon does not hide any personal data and employees get bank account data and personal names. Apple and Google have slightly better policies where google uses an automated system and apple transcribes the data collected and neither unlike Amazon show or give person data to their employees. His video can be found here.
Depending on ones job, one may be required to have a IoT device. A job today is a lifeline. Its giving back to society. We no longer grow our own food and gather our own water. We pay for it all by working. The world economy has changed from the hunter and gather days. There are more specialized positions now then back then. These specialized jobs require specialized technology. To deny a job that requires a phone today is ludicrous. Even if we don't need a phone for a job we still have to punch in on a computer, a IoT device. There is no escape. No way to unplug yourself.
So what happens when we want to "unplug" ourselves from the IoT? I know I would get massive FoMo and begin to have some mental health problems. To be completely unplugged would turn my life upside down. I would not be able to get to my job ,as I need a car. I couldn't communicate with my friends as few actually have my address to send me letters. I would miss out on almost everything as I would have no idea what's going on around me. Essentially I would excommunicate myself from the world. Self-destruction. The only good thing that I could see come from it is my fitness. With no one to communicate with and do things with, I would probably start pushing more iron.

The world has become reliant on computers. With all techonolical advances, there is good and bad. It is hard to know what line to walk. Every advancement is picking out a hat filled with good and bad consequences. There is no way of knowing what the results are.
0 notes
Text
Surveillance VS Data Collection and the Ugly Truth
Today 2.5 quintillion bytes of data is being collected daily by the 3.7 billion humans that are using the internet. This data doesn't even include the data the government receives from the Patriot Act and the "fiber-optic splitters" installed after 9/11. Luckily most of the data collected is deleted. Storing that amount of data daily would be virtually impossible. Still the amount of data saved is important to national security. It has protected and put many criminals in jail.
The definition of Surveillance is "a close observation, especially of a suspected spy or criminal", according to the Oxford dictionary. With the Patriot Act the government is allowed to look into the conversations and data collected from third parties. This allows a closer observation of a person. One can be able to find out somebodies friends, location, activities, basically the persons virtual self. Scary! There is a debate if the data collection is considered surveillance as its purpose at first, was not. Since the definition of surveillance does not include anything about purpose looking at the data collected is surveillance. It allows one to understand a person better.
The ugly truth about data collection is that we can't escape it. AT&T a major networking company with more then 100 million U.S. customers, has recoded billions of communication records through its domestic surveillance equipment. It has shared this data with the NSA according to a PBS article. A service which is a necessity today sharing your activity that you assumed was private is nerve-racking. AT&T is not the only company doing this as well. There is no escaping. Life today forces us to have a digital self. Most jobs force us to leave a Digital trace of ourselves even if it is a simple punch in and out. We must go against society to protect ourselves from surveillance, meaning no use of the Internet of Things (IOT). I am not ready to give up my use of the IOT however I do not like being always surveyed. Its a big problem today.
1 note
·
View note
Photo

Biometric Data was created in order to make accessing systems easier or in some cases more secure. It uses an algorithm to make a unique identifier for the user based on a physical adaptation. A technological feat. No longer do we have to memorize a password and type it in, a task both time-consuming and irritating if it is forgotten. This feat is so impressive that it can differentiate identical twins with the number of data points collected.
With all data collection, unexpected events can happen. Knowledge is power after all. This is the reason why we collect figure-prints of criminals and certain people. Biometrics have helped us solve numerous crimes and prevent others. However with the advancement and usage of technologies such as Face ID from apple and the increase of biometric technology in everyday items, we need to think about the consequences.
When Face ID came out hackers raced to break it. Many did. One Vietnamese security firm made a mask of the iPhone’s owner’s face which could unlock the phone every time. An article on this acomplishment can be found here. This event should not alarm the average iPhone user. A detailed scan of the the owners face was needed and apple securely stores and processes everything in their enclave chip. However high profile targets, and users that store their biometric data on the cloud may be at risk. This mask could potentially be created from data collected from photographs. Storing biometric data on the cloud also increases the chances for an attack on server. Physical adaptations unlike a passwords can not be changed. Once a hacker receives your data there is very little that can be done and may be able to get unrestricted access to a device.
If a hacker was able to accumulate a lot of Biometric data on a person a deep fake could be made. Depending on the person and position in the world disastrous events can occur. A single false message from and sent to the right person can change the world. Data must be protected.
With more and more data being collected security measures must be put in place. Technology is putting power at our fingertips. It is important to know where and how your data is being stored and used. Always use two step verification even if only your face can open your phone.
0 notes
Text
Autonomous Vehicles Bring in a New Age.
Autonomous Vehicles (AVs) are just around the corner. In fact they are already here but not for the average consumer. Zoox an autonomous vehicle company founded in 2014 has been releasing videos of their AVs driving around San Fransisco. Their latest video in their Autonomous Driving playlist on YouTube was only two months ago (Link to the playlist). Quoting Elon Musk, “There are no fundamental challenges remaining. There are many small problems. And then there’s the challenge of solving all those small problems and putting the whole system together.” By this he means acceptance of self driving cars by people and governments of the system. An article in The Conversation journal summaries in five reasons what the small problems are (Article can be found here). However, there is only two points in the article: improvement of sensors, which can always be improved, and getting people to accept the algorithms, the harder of the two.
Getting into an AV, similar to how when we are getting into a taxi, we are giving up control and putting our trust into someone or an algorithm in this case. These algorithms make choices and like all choices there are repercussions. Cause and Effect. As there is no way in predicting and programing in an optimal solution to every possible situation, some choices need to be made in order to allow the algorithm to work. For example, One finds themselves on a highway boxed in by a bus filled with children on the left, a truck to the right, a motorcycle tailgating behind, and a car in front that has slammed on its breaks for some reason. In this situation no mater what the AV does somebody dies. The problem is deciding who.
Each society values life differently. Thus making this an impossible question to answer. Overall most people agree it is ok to sacrifice a person for the greater good as explained by Jean-François Bonnefon in his article The Social Dilemma of Autonomous Vehicles. However the lines can get blurry when asked to define the greater good. The more technology advances the more variables we have. This is usually a good thing. More variables mean more relationships leading to more solutions. However when there is no good solution how do you decided who's get hurt. Eventually technology will allow us to know a persons value to society and an AV will be able to deiced who to kill based on that instead of just the number of objects and their sizes to hit. We are on the verge of a new age of discrimination. Are we all truly equal? Why not let a machine decided.
0 notes
Text
Information Ethics
Today we live in a brand new world. An Information World! Never before have we have had so much power at our finger tips. After all knowledge is power. Today we collect data on everything. There is even important data in this simple blog post. After awhile patterns start to form and we are able to see things. For a simple example where I will be every Tuesday around four (or at least I hope that this will become true). If my plan to write my blog post for my senior seminar everyday after class Tumblr can look at the time stamp for my posts in their databases and predict I am at my computer or on my phone writing a post. With more data such as an IP address they will be able to further predict my exact location. The point being is that everything we do is recorded and with the right algorithm that can sort through all our metadata some unpredicted outcomes can occur. This is why information ethics is important.
Ethics are based on social contracts. Depending on the society one lives in different ethical frameworks exits: Kantianism, Act Utilitarianism and Rule Utilitarianism. These frameworks can be respectfully summed up into three categories: morality, aftermath, and a predetermined ruling. Depending on the ethic framework determines if the action is right or wrong.
An issue that the world is facing today that we did not have to face in previous years is with how information is distributed. Today most algorithms are based on search statistics. The more something is viewed the more it is shown. This boils down to simple statistics which seems innocent at first. However after a while patterns start to form. Not all are good either. One example is discrimination. It becomes harder and harder to make it big. There are no longer local celebrities. We only see the same names over and over again. To make it worse only the people in their circle can make it big. The world is becoming about who you know versus what you know because of Information Ethics.
We have to ask ourselves and figure out who's job it is to monitor and control our information. The government, big tech companies, individuals? We also can't go back to the old days either. We have become too dependent on technology. In order to move forward we must figure what is ethical.
What is the correct way to use and view information on the internet? Only time will tell.
0 notes
Text
Linux Tutorial
As this is my Senior seminar, and its supposed to be a capstone of my Computer Science Degree, there is going to be review. Most of the activity today was to make sure we are up to date and know the basic linux commands. Most of them I knew. It was good to review and catch up on them. My only issue was that I did not learn them earlier. That means that I wish they were taught in my Data Structures class. I learned most of these commands on my own when I got an internship or took courses at other universities. Teaching in the Data Structures class the student will already have the basics down and this will help them excel in the future. Not too early but not too late. Many times, before I learned these, I got stuck and had to teach myself these commands. Ultimately, good review but shouldn't have to review. In my opinion it should be second nature at this point.
0 notes
Text
Plans After College
My plans after college are to find a job in development, or technology consulting and move out of the Albany area. Currently I am taking a LOA (leave of absence) from school due to Covid-19. If I due well on this winter break course I will be graduating in the fall of 2021. If I dont then spring 2021. Curently I am working on howning my develeper skills learning JS and React, in order to make some of my own apps. After my internship and my comunications with the Jahnel group I realized that I need to put in work outside of the school just as I do with Squash in order to become a good developer. There are tasks that College can not teach you and must be learned on your own.
0 notes
Text
readme.txt
This blog is being created for this course and will be used to post reflective writing on reading and discussion topics related to free and open source software (FOSS), software engineering and contemporary social and ethical issues in technology.
1 note
·
View note