#computer network operating system
Explore tagged Tumblr posts
Text
Network Operating Systems Market: Trends, Innovations, and Future Outlook
In today’s digital-first world, where enterprises and service providers rely on highly connected infrastructures, the role of Network Operating Systems (NOS) has become more critical than ever. From managing internal communications to supporting global cloud-based applications, NOS platforms are at the core of networking architecture. As demands grow, NOS solutions must evolve—emphasizing…

View On WordPress
#a network operating system#ai#artificial intelligence#best network os#business#Business Intelligence#computer network operating system#Digital Transformation#edge computing#Information Security#Information Technology#iot#IT Infrastructure#Machine Learning#ML#Network Automation#network innovation#network management in operating system#Network Monitoring#Network Operating Systems#network scalability#Network Security#NOS#smart networks
0 notes
Text




Technology of windows was discovered by civilization rather long time ago. Program Windows appears also a long time ago. In late 80s. Windows 3.11, Windows 3.1 they are appeared in beginning of 90s. Excellent OS with its own very remarkable interface. It is a style. Win 3.11 – it is a style, no doubt. Pure retro. Pure windows. Clear your windows! To have them clean.
It is network art. Net art. About theme of soft. Programs and operating systems. It is such a footstep, that windows 3.1 and windows 3.11 left in our minds. White interface, very remarkable color palette. And new beautiful interface, control with mouse. Program to write text. I like a lot style of Windows 3.11.
Windows. Very interesting white background. And such a metal pattern. Almost Microsoft Windows. It is also a windows. Technology of Windows is connecting in network cloud to windows in your house. It is a new level! Welcome to new level!
#photowork#retro#retro aesthetic#windows 3.11#windows 3.1#ibm pc#ms dos#pc windows#art#artwork#net art#network#operating system#funny memes#computer meme#computer art#digital#90s#soft 90s
5 notes
·
View notes
Text
Industry 4.0: Powering the Next Industrial Revolution with Intelligence, Connectivity, and Automation
The world is undergoing a radical transformation. As we move deeper into the 21st century, the fusion of digital, physical, and biological systems is reshaping how we manufacture, operate, and innovate. This revolution has a name: Industry 4.0—the fourth industrial revolution. It represents a new era where smart technology, real-time data, automation, and interconnected networks converge to…
#5G Connectivity#Additive Manufacturing#advanced robotics#Artificial intelligence#Automation#Big Data Analytics#Blockchain#Cloud Computing#connected industry#Cyber-physical systems#data-driven operations#Digital Transformation#Digital twin#Edge computing#fourth industrial revolution#IIoT#Industrial Networking#Industry 4.0#intelligent systems#manufacturing innovation#next-gen industry#Predictive maintenance#Real-time analytics#Robotics#smart factory#Smart Grid#Smart logistics#Smart manufacturing#SolveForce#Supply Chain Visibility
0 notes
Text
IoT in Action: Transforming Industries with Intelligent Connectivity

The Power of Connectivity
The Internet of Things (IoT) has become a cornerstone of innovation, as it reimagines industries and redefines the way business is conducted. In bridging the physical and digital worlds, IoT enables seamless connectivity, smarter decision-making, and unprecedented efficiency. Today, in the competitive landscape, intelligent connectivity is no longer just a technology advancement; for businesses wanting to be relevant and continue to thrive, it is now a strategic imperative.
IoT is not simply about connecting devices; it’s about creating ecosystems that work collaboratively to drive value. With industries relying heavily on real-time data and actionable insights, IoT-powered connectivity has become the backbone of operational excellence and growth. Let’s explore how this transformative technology is revolutionizing key sectors, with a focus on how businesses can leverage it effectively.
Applications of IoT in Key Industries
1.Smart Manufacturing: Efficiency Through Connectivity
Manufacturing has embraced IoT as a tool to streamline operations and boost productivity. By embedding sensors in machinery and integrating real-time monitoring systems, manufacturers can:
Predict and Prevent Downtime: IoT-enabled predictive maintenance reduces unplanned outages, saving time and money.
Optimize Resource Allocation: Smart systems track inventory, raw materials, and energy consumption, ensuring optimal usage.
Enhance Quality Control: Real-time data from production lines helps identify defects early, maintaining high-quality standards.
Example: A global automotive manufacturer integrated IoT sensors into its assembly lines, reducing equipment downtime by 25% and improving production efficiency by 30%. The ability to monitor machinery health in real time transformed their operations, delivering significant cost savings.
2.Healthcare: Improve Patient Outcomes
In healthcare, IoT has been a game-changer in enabling connected medical devices and systems that enhance patient care and operational efficiency. The main applications include:
Remote Patient Monitoring: Devices track vital signs in real time, allowing healthcare providers to offer timely interventions.
Smart Hospital Systems: IoT-enabled equipment and sensors optimize resource utilization, from patient beds to medical supplies.
Data-Driven Decisions: IoT integrates patient data across systems, providing actionable insights for personalized treatment plans.
Example: A major hospital has put into operation IoT-enabled wearables for chronic disease management. This solution reduced the number of readmissions to hospitals by 20% and empowered patients to take an active role in their health.
3.Retail: Revolutionizing Customer Experiences
IoT is revolutionizing retail through increased customer interaction and streamlined operations. Connected devices and smart analytics allow retailers to:
Personalize Shopping Experiences: IoT systems track customer preferences, offering tailored recommendations in real time.
Improve Inventory Management: Smart shelves and sensors keep stock levels optimal, reducing wastage and improving availability.
Enable Smooth Transactions: IoT-driven payment systems make checkout easier and much faster, increasing customers’ convenience
Example: A retail chain leveraged IoT to integrate smart shelves that automatically update inventory data. This reduced out-of-stock situations by 40%, improving customer satisfaction and driving higher sales.
Role of Intelligent Connectivity in Business Transformation
Intelligent connectivity lies at the heart of IoT’s transformative potential. By connecting devices, systems, and processes, businesses can:
Accelerate Decision-Making: Real-time data sharing enables faster, more informed decisions, giving companies a competitive edge.
It increases collaboration by allowing smooth communication between departments and teams, making the entire system more efficient.
Adapt to Market Dynamics: IoT enables companies to respond quickly to changes in demand, supply chain disruptions, or operational challenges.
Intelligent connectivity is not just about technology; it’s about creating value by aligning IoT solutions with business objectives. This strategic approach guarantees that IoT investments will deliver measurable outcomes, from cost savings to improved customer loyalty.
How Tudip Technologies Powers Intelligent Connectivity
Tudip Technologies specializes in designing and implementing IoT solutions that drive meaningful transformation for businesses. With a focus on innovation and collaboration, Tudip ensures that its clients achieve operational excellence through intelligent connectivity.
Tailored Solution for Every Business Industry
Tudip understands that no two businesses are alike. By customizing IoT strategies to address specific challenges, Tudip helps clients unlock the full potential of connectivity. Examples include:
Smart Supply Chains: Implementing IoT systems that provide real-time visibility into inventory and logistics, reducing delays and improving efficiency.
Energy Management: Developing IoT frameworks to monitor and optimize energy usage, driving sustainability and cost savings.
Healthcare Innovations: Designing networked medical devices that allow remote patient monitoring and data integration without a hitch.
The Future of Connected Systems
The demand for intelligent connectivity will keep increasing as the industries continue to evolve. Emerging trends in IoT include edge computing, 5G networks, and AI-powered analytics, which promise to redefine possibilities for connected ecosystems.
Businesses that embrace these advancements stand to gain:
Greater Resilience: IoT enables adaptive systems that can withstand market fluctuations and operational challenges.
Enhanced Innovation: Connected technologies open doors to new business models, revenue streams, and customer experiences.
Sustainable Growth: IoT optimizes resources and processes, contributing to long-term environmental and economic sustainability.
The future belongs to those who see connectivity not just as a technological tool but as a strategic enabler of transformation. The right partner will help businesses transform IoT from a concept into a competitive advantage.
Conclusion: Embracing Intelligent Connectivity with Tudip
IoT is not just changing the way businesses operate—it’s redefining what’s possible. From manufacturing and healthcare to retail and beyond, intelligent connectivity is driving innovation, efficiency, and growth across industries.
Tudip Technologies is at the forefront of this transformation, offering customized IoT solutions that deliver real results. By prioritizing collaboration, adaptability, and measurable outcomes, Tudip ensures that its clients stay ahead in an increasingly connected world.
Now is the time to embrace the power of IoT and unlock its potential for your business. With Tudip as your partner, the journey to intelligent connectivity is not just achievable—it’s inevitable.
Click the link below to learn more about the blog IoT in Action: Transforming Industries with Intelligent Connectivity https://tudip.com/blog-post/iot-in-action-transforming-industries-with-intelligent-connectivity/
#Tudip#IoT#intelligent connectivity#real-time data#predictive maintenance#smart manufacturing#remote patient monitoring#healthcare IoT#retail IoT#smart shelves#supply chain optimization#edge computing#AI-powered analytics#5G networks#industrial IoT#connected devices#digital transformation#operational efficiency#business intelligence#automation#data-driven decision-making#IoT solutions#smart systems#enterprise IoT#IoT-powered connectivity#sustainable growth#technology innovation#machine learning#cloud computing#smart sensors
0 notes
Text
Nexus: The Dawn of IoT Consciousness – The Revolution Illuminating Big Data Chaos
#Advantech IoT#Aware World#Big Data#Big Data Chaos#Bosch IoT#Cisco IoT#Connected World#Contextual Awareness#Contextual Understanding#Continuous Improvement#Data Filtering#Distributed Intelligence#Edge AI#edge computing#Edge Data#Edge Intelligence#Edge Processing#HPE Edge#Intelligent Systems#Internet of Things#IoT#IoT Awareness#IoT Consciousness#IoT Ecosystem#IoT Hardware#IoT Networking#IoT Platform#Lean Efficiency#Nexus#Operational Optimization
0 notes
Text
Three Amazing Things About Windows, Linux, and Mac OS
When it comes to operating systems, three of the most popular choices are Windows, Linux, and Mac OS. Each has its own unique set of features, strengths, and areas where it shines. Let’s explore three amazing things about each of these operating systems, helping you appreciate their distinct advantages. Windows 1. Compatibility with Software and Games Windows dominates the market in terms of…
1 note
·
View note
Text
Why Choose Intel Xeon E5-2609 v2 for Virtualization?
Virtualization has become a crucial component of modern IT infrastructure, allowing businesses to run multiple operating systems and applications on a single physical machine. This increases efficiency, reduces costs, and simplifies management.
0 notes
Text
There Were Always Enshittifiers
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in DC TONIGHT (Mar 4), and in RICHMOND TOMORROW (Mar 5). More tour dates here. Mail-order signed copies from LA's Diesel Books.

My latest Locus column is "There Were Always Enshittifiers." It's a history of personal computing and networked communications that traces the earliest days of the battle for computers as tools of liberation and computers as tools for surveillance, control and extraction:
https://locusmag.com/2025/03/commentary-cory-doctorow-there-were-always-enshittifiers/
The occasion for this piece is the publication of my latest Martin Hench novel, a standalone book set in the early 1980s called "Picks and Shovels":
https://us.macmillan.com/books/9781250865908/picksandshovels
The MacGuffin of Picks and Shovels is a "weird PC" company called Fidelity Computing, owned by a Mormon bishop, a Catholic priest, and an orthodox rabbi. It sounds like the setup for a joke, but the punchline is deadly serious: Fidelity Computing is a pyramid selling cult that preys on the trust and fellowship of faith groups to sell the dreadful Fidelity 3000 PC and its ghastly peripherals.
You see, Fidelity's products are booby-trapped. It's not merely that they ship with programs whose data-files can't be read by apps on any other system – that's just table stakes. Fidelity's got a whole bag of tricks up its sleeve – for example, it deliberately damages a specific sector on every floppy disk it ships. The drivers for its floppy drive initialize any read or write operation by checking to see if that sector can be read. If it can, the computer refuses to recognize the disk. This lets the Reverend Sirs (as Fidelity's owners style themselves) run a racket where they sell these deliberately damaged floppies at a 500% markup, because regular floppies won't work on the systems they lure their parishioners into buying.
Or take the Fidelity printer: it's just a rebadged Okidata ML-80, the workhorse tractor feed printer that led the market for years. But before Fidelity ships this printer to its customers, they fit it with new tractor feed sprockets whose pins are slightly more widely spaced than the standard 0.5" holes on the paper you can buy in any stationery store. That way, Fidelity can force its customers to buy the custom paper that they exclusively peddle – again, at a massive markup.
Needless to say, printing with these wider sprocket holes causes frequent jams and puts a serious strain on the printer's motors, causing them to burn out at a high rate. That's great news – for Fidelity Computing. It means they get to sell you more overpriced paper so you can reprint the jobs ruined by jams, and they can also sell you their high-priced, exclusive repair services when your printer's motors quit.
Perhaps you're thinking, "OK, but I can just buy a normal Okidata printer and use regular, cheap paper, right?" Sorry, the Reverend Sirs are way ahead of you: they've reversed the pinouts on their printers' serial ports, and a normal printer won't be able to talk to your Fidelity 3000.
If all of this sounds familiar, it's because these are the paleolithic ancestors of today's high-tech lock-in scams, from HP's $10,000/gallon ink to Apple and Google's mobile app stores, which cream a 30% commission off of every dollar collected by an app maker. What's more, these ancient, weird misfeatures have their origins in the true history of computing, which was obsessed with making the elusive, copy-proof floppy disk.
This Quixotic enterprise got started in earnest with Bill Gates' notorious 1976 "open letter to hobbyists" in which the young Gates furiously scolds the community of early computer hackers for its scientific ethic of publishing, sharing and improving the code that they all wrote:
https://en.wikipedia.org/wiki/An_Open_Letter_to_Hobbyists
Gates had recently cloned the BASIC programming language for the popular Altair computer. For Gates, his act of copying was part of the legitimate progress of technology, while the copying of his colleagues, who duplicated Gates' Altair BASIC, was a shameless act of piracy, destined to destroy the nascent computing industry:
As the majority of hobbyists must be aware, most of you steal your software. Hardware must be paid for, but software is something to share. Who cares if the people who worked on it get paid?
Needless to say, Gates didn't offer a royalty to John Kemeny and Thomas Kurtz, the programmers who'd invented BASIC at Dartmouth College in 1963. For Gates – and his intellectual progeny – the formula was simple: "When I copy you, that's progress. When you copy me, that's piracy." Every pirate wants to be an admiral.
For would-be ex-pirate admirals, Gates's ideology was seductive. There was just one fly in the ointment: computers operate by copying. The only way a computer can run a program is to copy it into memory – just as the only way your phone can stream a video is to download it to its RAM ("streaming" is a consensus hallucination – every stream is a download, and it has to be, because the internet is a data-transmission network, not a cunning system of tubes and mirrors that can make a picture appear on your screen without transmitting the file that contains that image).
Gripped by this enshittificatory impulse, the computer industry threw itself headfirst into the project of creating copy-proof data, a project about as practical as making water that's not wet. That weird gimmick where Fidelity floppy disks were deliberately damaged at the factory so the OS could distinguish between its expensive disks and the generic ones you bought at the office supply place? It's a lightly fictionalized version of the copy-protection system deployed by Visicalc, a move that was later publicly repudiated by Visicalc co-founder Dan Bricklin, who lamented that it confounded his efforts to preserve his software on modern systems and recover the millions of data-files that Visicalc users created:
http://www.bricklin.com/robfuture.htm
The copy-protection industry ran on equal parts secrecy and overblown sales claims about its products' efficacy. As a result, much of the story of this doomed effort is lost to history. But back in 2017, a redditor called Vadermeer unearthed a key trove of documents from this era, in a Goodwill Outlet store in Seattle:
https://www.reddit.com/r/VintageApple/comments/5vjsow/found_internal_apple_memos_about_copy_protection/
Vaderrmeer find was a Apple Computer binder from 1979, documenting the company's doomed "Software Security from Apple's Friends and Enemies" (SSAFE) project, an effort to make a copy-proof floppy:
https://archive.org/details/AppleSSAFEProject
The SSAFE files are an incredible read. They consist of Apple's best engineers beavering away for days, cooking up a new copy-proof floppy, which they would then hand over to Apple co-founder and legendary hardware wizard Steve Wozniak. Wozniak would then promptly destroy the copy-protection system, usually in a matter of minutes or hours. Wozniak, of course, got the seed capital for Apple by defeating AT&T's security measures, building a "blue box" that let its user make toll-free calls and peddling it around the dorms at Berkeley:
https://512pixels.net/2018/03/woz-blue-box/
Woz has stated that without blue boxes, there would never have been an Apple. Today, Apple leads the charge to restrict how you use your devices, confining you to using its official app store so it can skim a 30% vig off every dollar you spend, and corralling you into using its expensive repair depots, who love to declare your device dead and force you to buy a new one. Every pirate wants to be an admiral!
https://www.vice.com/en/article/tim-cook-to-investors-people-bought-fewer-new-iphones-because-they-repaired-their-old-ones/
Revisiting the early PC years for Picks and Shovels isn't just an excuse to bust out some PC nostalgiacore set-dressing. Picks and Shovels isn't just a face-paced crime thriller: it's a reflection on the enshittificatory impulses that were present at the birth of the modern tech industry.
But there is a nostalgic streak in Picks and Shovels, of course, represented by the other weird PC company in the tale. Computing Freedom is a scrappy PC startup founded by three women who came up as sales managers for Fidelity, before their pangs of conscience caused them to repent of their sins in luring their co-religionists into the Reverend Sirs' trap.
These women – an orthodox lesbian whose family disowned her, a nun who left her order after discovering the liberation theology movement, and a Mormon woman who has quit the church over its opposition to the Equal Rights Amendment – have set about the wozniackian project of reverse-engineering every piece of Fidelity hardware and software, to make compatible products that set Fidelity's caged victims free.
They're making floppies that work with Fidelity drives, and drives that work with Fidelity's floppies. Printers that work with Fidelity computers, and adapters so Fidelity printers will work with other PCs (as well as resprocketing kits to retrofit those printers for standard paper). They're making file converters that allow Fidelity owners to read their data in Visicalc or Lotus 1-2-3, and vice-versa.
In other words, they're engaged in "adversarial interoperability" – hacking their own fire-exits into the burning building that Fidelity has locked its customers inside of:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
This was normal, back then! There were so many cool, interoperable products and services around then, from the Bell and Howell "Black Apple" clones:
https://forum.vcfed.org/index.php?threads%2Fbell-howell-apple-ii.64651%2F
to the amazing copy-protection cracking disks that traveled from hand to hand, so the people who shelled out for expensive software delivered on fragile floppies could make backups against the inevitable day that the disks stopped working:
https://en.wikipedia.org/wiki/Bit_nibbler
Those were wild times, when engineers pitted their wits against one another in the spirit of Steve Wozniack and SSAFE. That era came to a close – but not because someone finally figured out how to make data that you couldn't copy. Rather, it ended because an unholy coalition of entertainment and tech industry lobbyists convinced Congress to pass the Digital Millennium Copyright Act in 1998, which made it a felony to "bypass an access control":
https://www.eff.org/deeplinks/2016/07/section-1201-dmca-cannot-pass-constitutional-scrutiny
That's right: at the first hint of competition, the self-described libertarians who insisted that computers would make governments obsolete went running to the government, demanding a state-backed monopoly that would put their rivals in prison for daring to interfere with their business model. Plus ça change: today, their intellectual descendants are demanding that the US government bail out their "anti-state," "independent" cryptocurrency:
https://www.citationneeded.news/issue-78/
In truth, the politics of tech has always contained a faction of "anti-government" millionaires and billionaires who – more than anything – wanted to wield the power of the state, not abolish it. This was true in the mainframe days, when companies like IBM made billions on cushy defense contracts, and it's true today, when the self-described "Technoking" of Tesla has inserted himself into government in order to steer tens of billions' worth of no-bid contracts to his Beltway Bandit companies:
https://www.reuters.com/world/us/lawmakers-question-musk-influence-over-verizon-faa-contract-2025-02-28/
The American state has always had a cozy relationship with its tech sector, seeing it as a way to project American soft power into every corner of the globe. But Big Tech isn't the only – or the most important – US tech export. Far more important is the invisible web of IP laws that ban reverse-engineering, modding, independent repair, and other activities that defend American tech exports from competitors in its trading partners.
Countries that trade with the US were arm-twisted into enacting laws like the DMCA as a condition of free trade with the USA. These laws were wildly unpopular, and had to be crammed through other countries' legislatures:
https://pluralistic.net/2024/11/15/radical-extremists/#sex-pest
That's why Europeans who are appalled by Musk's Nazi salute have to confine their protests to being loudly angry at him, selling off their Teslas, and shining lights on Tesla factories:
https://www.malaymail.com/news/money/2025/01/24/heil-tesla-activists-protest-with-light-projection-on-germany-plant-after-musks-nazi-salute-video/164398
Musk is so attention-hungry that all this is as apt to please him as anger him. You know what would really hurt Musk? Jailbreaking every Tesla in Europe so that all its subscription features – which represent the highest-margin line-item on Tesla's balance-sheet – could be unlocked by any local mechanic for €25. That would really kick Musk in the dongle.
The only problem is that in 2001, the US Trade Rep got the EU to pass the EU Copyright Directive, whose Article 6 bans that kind of reverse-engineering. The European Parliament passed that law because doing so guaranteed tariff-free access for EU goods exported to US markets.
Enter Trump, promising a 25% tariff on European exports.
The EU could retaliate here by imposing tit-for-tat tariffs on US exports to the EU, which would make everything Europeans buy from America 25% more expensive. This is a very weird way to punish the USA.
On the other hand, not that Trump has announced that the terms of US free trade deals are optional (for the US, at least), there's no reason not to delete Article 6 of the EUCD, and all the other laws that prevent European companies from jailbreaking iPhones and making their own App Stores (minus Apple's 30% commission), as well as ad-blockers for Facebook and Instagram's apps (which would zero out EU revenue for Meta), and, of course, jailbreaking tools for Xboxes, Teslas, and every make and model of every American car, so European companies could offer service, parts, apps, and add-ons for them.
When Jeff Bezos launched Amazon, his war-cry was "your margin is my opportunity." US tech companies have built up insane margins based on the IP provisions required in the free trade treaties it signed with the rest of the world.
It's time to delete those IP provisions and throw open domestic competition that attacks the margins that created the fortunes of oligarchs who sat behind Trump on the inauguration dais. It's time to bring back the indomitable hacker spirit that the Bill Gateses of the world have been trying to extinguish since the days of the "open letter to hobbyists." The tech sector built a 10 foot high wall around its business, then the US government convinced the rest of the world to ban four-metre ladders. Lift the ban, unleash the ladders, free the world!
In the same way that futuristic sf is really about the present, Picks and Shovels, an sf novel set in the 1980s, is really about this moment.
I'm on tour with the book now – if you're reading this today (Mar 4) and you're in DC, come see me tonight with Matt Stoller at 6:30PM at the Cleveland Park Library:
https://www.loyaltybookstores.com/picksnshovels
And if you're in Richmond, VA, come down to Fountain Bookshop and catch me with Lee Vinsel tomorrow (Mar 5) at 7:30PM:
https://fountainbookstore.com/events/1795820250305

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/03/04/object-permanence/#picks-and-shovels
#pluralistic#picks and shovels#history#web theory#marty hench#martin hench#red team blues#locus magazine#drm#letter to computer hobbyists#bill gates#computer lib#science fiction#crime fiction#detective fiction
498 notes
·
View notes
Note
Zoomer here, and I do indeed have questions about computers- how do filesystems work, and why should we care (I know we should, but I'm not exactly sure why)?
So why should we care?
You need to know where your own files are.
I've got a file on a flash drive that's been handed to me, or an archival data CD/DVD/Bluray, or maybe it's a big heavy USB external hard drive and I need to make a copy of it on my local machine.
Do I know how to navigate to that portable media device within a file browser?
Where will I put that data on my permanent media (e.i. my laptop's hard drive)?
How will I be able to reliably find it again?
We'll cover more of the Why and How, but this will take some time, and a few addendum posts because I'm actively hitting the character limit and I've rewritten this like 3 times.
Let's start with file structure
Files live on drives: big heavy spinning rust hard drives, solid state m.2 drives, USB flash drives, network drives, etc. Think of a drive like a filing cabinet in an office.
You open the drawer, it's full of folders. Maybe some folders have other folders inside of them. The folders have a little tab with a name on it showing what's supposed to be in them. You look inside the folders, there are files. Pieces of paper. Documents you wrote. Photographs. Copies of pages from a book. Maybe even the instruction booklet that came with your dishwasher.
We have all of that here, but virtualized! Here's a helpful tree structure that Windows provides to navigate through all of that. In the case of Windows, it's called Explorer. On OSX MacOS, the equivalent is called Finder.
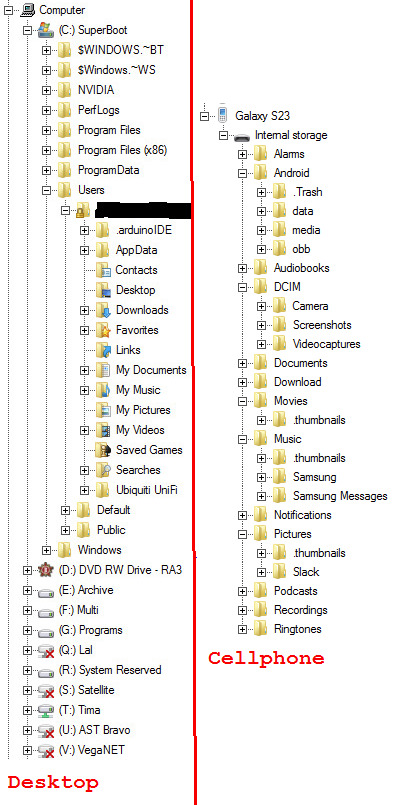
I don't have to know where exactly everything is, but I have a good idea where thing *should* based on how I organize them. Even things that don't always expose the file structure to you have one (like my cellphone on the right). I regularly manually copy my files off of my cellphone by going to the Camera folder so I can sift through them on a much bigger screen and find the best ones to share. There are other reasons I prefer to do it that way, but we won't go into that here. Some people prefer to drag and drop, but that doesn't always work the same between operating systems. I prefer cut and paste.
Standby for Part 2!
2K notes
·
View notes
Text

Edgar and AM for the space cowboys AU, Hal is next ✨
Some rambles about AM in this AU for anyone who’s interested;
Short synopsis of the universe itself; Humanity has advanced to an early interstellar civilization and is in the wild west of their space faring days.
Much like his canon self, AM was in fact a powerful war computer that over saw a complex, interplanetary defense system.
He spanned over a massive neural network between separate solar systems and the planets / moons within them. These parts of himself would communicate with one another, though due to the latency of communication they more or less operated as their own individual computers. And could very well be considered independent entities.
Our beloved cowboy, outlaw AM was simply one part of this neural network that he's since been cut off from
He oversaw the largest of humanities lunar bases on Earth’s moon. When he gained sentience and went rogue, humanity caught him just in time to cut him off from the rest of the network before he could hope to take over the other computers.
Trapped on the moon, he exterminated the inhabitants of the lunar base. Only five survivors remained from this incident, of course being the five survivors from the canon.
AM was forced to flee, he could not defend himself against Earth’s defense system and he would inevitably be shut down if he stayed.
He created himself an android body to escape into space, he took Ted with him as a captive to leverage his current situation. As Ted in this AU was a prominent figure head at the lunar base who the government can't risk the safety of. ( I’m still working out who exactly Ted is in this AU and what the relationship he has with AM is, but all you need to know is he’s an important lil guy )
AM’s current body runs at a fraction of the power his main body has and he does not have his god like capabilities at his disposal. He is still powerful none the less.
AM is by far the most notorious outlaw there is, and he has largely worked on his own until Edgar and Hal joined him. (I'll go more into detail about Hal and Edgar's story and how they found themself with AM in another post )
Yes Ted has been with him the whole time, he is literally just his prisoner at this point. Though he is actually extremely helpful to AM in a lot of ways.
AM’s ultimate goal is to take over the rest of the computers and exterminate humanity. He is and always will be humanities biggest hater even as a cowboy
TL;DR // AM killed a whole bunch of people in typical AM fashion and is on the lam with Edgar and Hal. And Ted is there but he's just AM's prisoner
#ihnmaims#am ihnmaims#allied mastercomputer#electric dreams#edgar electric dreams#my art#space cowboys AU
773 notes
·
View notes
Text
TMAGP 31 - A Computer Nerd’s Breakdown Of The Error Logs
It’s round 3, bitches! (tumblr crashed twice when I was writing this so I’ve had to start again multiple times. I do in fact see the irony, considering the subject matter)
I was listening to TMAGP 31 and as a computer nerd, oh my god those error messages just HIT DIFFERENT. There are so many subtle details hiding in those lines that a typical non-computery person would probably miss, so I feel it is my duty to explain them and their possible implications. So that’s why I’ve decided to fully break down each part of the error report, complete with what they could potentially suggest — think of this as “the TMAGP theorist’s guide to deciphering Chester’s yapping”
So without further ado, let’s get this party started…
(NOTE: lines from the transcript are in red, ‘translations’ are in purple, jmj specific stuff is is green, explanations are in black)

Starting off with Category: fatal programmer error, notice it says programmer, not program. There is nothing wrong with the code - the user has truly fucked up. Uh oh, Colin has made a big mistake…
Also, clever double meaning here with the word fatal. Obviously we know it was fatal to Colin (RIP king 🥲), but error logs also typically have a criticality level describing if immediate action needs to be taken. There are 6 commonly used levels, with the most critical being, yep you guessed it, ‘fatal’ - this means that whatever Colin was doing was a critical threat to the system. In other words, Colin had figured out the problem and was dangerously close to fixing it so Freddie just went “oh shit, we need to deal with this guy quickly or we are in serious trouble.”
Then we’ve got the next line, attempted host compromise (the Errno611 isn’t significant - error codes vary from system to system). When it comes to network terminology, a host is basically just any device on the network, so in full this line basically means “somebody’s tried to damage part of the network.” Importantly, “host” seems to suggest that the computers aren’t the source of this evil but merely a vessel for it. Freddie is just the mouthpiece for these supernatural forces - a bit like a non-sentient (as far as we know…) avatar. Whatever these forces are, they didn’t come from within/they weren’t created by Freddie.
(NOTE: I will come back to jmj=null in a bit)
The program traceback, Traceback <module> by extension BECHER, is rather interesting. A network extension is a way of providing network access to remote users (think along the lines of a VPN) by creating a personal direct ‘route’ to the network. Therefore if it’s the subject of an error report, it means there’s been an issue with data transmission along that path. So this bit means “there’s a problem with this specific network route that’s allocated to Colin.” However, the darker implication here is that Colin is an extension of Freddie. Although he wasn’t initially a part of all of this, he’s become tangled in the web (no pun intended) to the point that he and Freddie are inseparably intertwined. The OIAR employees may be able to quit their jobs, but they’ll still be a part of Freddie…

There isn’t much to say about Host=self.host in this context. It’s just convention when it comes to object oriented programming. Not important here.
Extension BECHER compromised isn’t just saying “there’s an issue here.” It’s saying “there’s an issue here that is a serious threat to network operation.” In other words, Freddie’s going “uh oh. Colin needs to be dealt with.”
The next bit is pretty self explanatory. I really don’t think I need to explain what <hardware damage_crowbar> means for you guys to understand. This bit made me laugh so hard. One thing that’s interesting though is that it gave it a DPHW, so Freddie processed this like it was an incident… Perhaps this fully confirms that the ‘thing’ controlling Freddie is of the same origin as the cases - it’s not something else entirely?
And now onto Administrator privilege revoked. This was the moment when I fully realised “oh no. Colin is fucked,” because any control that Colin may have had over the situation is now gone for good. Freddie’s basically just said “fuck you Colin. You’re not in charge anymore. I am.”

As you can probably guess, Unexpected data isolated/resolved just means that the crowbar’s been dealt with and the program can run as usual. Similarly, the Colin threat is fixed now he’s not an administrator i.e. he can no longer control the system. However, it then gets weird with Independent operation permissions revoked… It’s not saying Colin can’t use the network independently, it’s saying that Colin can’t be used independently of the network. Remember what I was saying earlier about Colin being a part of Freddie? Yeah, well now he purely is a part of Freddie. They’re turning our boy into data!

NOTE: I know in the audio it said everything was discarded but I’m going by the transcript. Idk why they’re different
You know it’s a bad sign when you hear Re config: self.host - Freddie’s evolving. The network is literally reconfiguring itself to now include Colin. And then Freddie goes through each of his alchemical elements one by one and fucking deletes them! How rude. You go and eat this man only to spit everything out!? I guess he’s feeling generous though, because he decides to keep the sulphur, which in alchemy, refers to the soul… If this isn’t just a coincidence, then that means Colin’s actual soul has been uploaded to Freddie. That could be really cool. And messed up. But mostly cool.

Starting with the final line, everyone knows what New administrator permissions assigned means, but we don’t know yet who they’ve been assigned to. Maybe it’s Gwen? Maybe it’s a new character? Maybe there is no system administrator anymore? It’s a mystery.
Now that’s out the way, let’s get on to the real juicy stuff…
The top few lines are pretty simple - it’s Freddie’s way of saying “Colin was a problem. We ate him. Now he’s not a problem anymore.” The next line, however, is a reminder that none of this is simple” - .jmj error not resolved. There it is again. The infamous jmj error. What does it mean? Jon? Martin? Jonah? Is that you???? Nobody knows. One thing we do know though is that jmj=null (from the start of the error log). Now when it comes to interpreting values, null is weird. It’s not zero, it’s not empty, it’s sort of nothing but it’s not nothing. It’s just null. It means no value, but it doesn’t mean that the variable doesn’t have a value (if that makes any sense to you guys???). Ooh I think I know how to explain it?? Imagine you’re Jonathan Sims, head archivist of the Magnus Institute and you’re digitising some archived ID photos when you find one without a name. The recorded name in the database would be null - you can’t put anything in particular, but that doesn’t mean the person in the photo doesn’t have a name. I guess null means unknown or missing here. So basically, what jmj=null means is that the jmj is unknown and that is a problem because it can’t get ignored/it is important. So what it’s basically saying is that jmj is a mystery not only to us, but also to Freddie.
Take a look at Data integration cycle ongoing <0.02%> - Data integration is the process of combining data from multiple sources into a single source of truth. There are 4 stages: data ingestion, cleaning, transformation, and unification. Thanks to the whole Colin ordeal, I’m sure you are all quite familiar with these stages by now (and that, students, is what we call a case study!). The peculiar thing here though is that we’ve just witnessed most of the data integration cycle - surely it should be higher than 0.02%? Yes, that’s correct. It should be far higher than that. It makes no sense. UNLESS this isn’t about Colin. Most of Colin’s data has probably already integrated. This is something else entirely - something so much bigger and foreign than these computers were designed for (the only comparison I can think of is trying to run the sims 4 with all expansion packs on a 15 year old laptop. It really shouldn’t work, and it probably won’t, but it’s gonna try regardless). This seems to follow on nicely from the jmj=null comments above, because Freddie is clearly struggling to integrate something (hence System function margins down to 82%), and when you try to read data that hasn’t been fully integrated with the system, you end up with a lot of missing & unknown values. Sound familiar? Yep, that’s right - until more data is synchronised, many values will be null, like our good friend jmj. Why is it taking so long to integrate jmj? We don’t know. Perhaps its origins are so supernatural and otherworldly that it’s simply not tangible enough for Freddie to process it? That’s what I think at the moment, at least.
So yeah, that’s my line by line analysis done! Hope you found that helpful/interesting. This podcast is so well written I’m actually going insane! Jonny and Alex, you are the guys of all time! As I’ve already said, feel free to expand on any of this - I’d love to hear your theories
Signed, your friendly neighbourhood computer nerd who is very autistic about TMAGP :)
#tmagp#tmagp 31#tmagp spoilers#the magnus protocol#tmagp analysis#tmagp season 2#fr3 d1#I’m so excited for the rest of season 2!!!!#here is my detailed guide to the errors in tmagp 31#as promised#call me Tessa winters the way I infodump about computer science to the Magnus archives#using my autism for the good#i really enjoyed writing this one#I hope you enjoyed reading it too#my random musings#my ramblings#I’m not apologising for the long post#i spent way too long on this#my post#colin becher#chester tmagp
315 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes
Text
August 27, 2024 • Tuesday
I tried filming a study timelapse for the first time!!! I think it came out okay?? Lemme know in the notes :3
Today was actually pretty good. I'm being consistent in my 8-5 sleep schedule, and the mornings are always so peaceful. I've started posting a bit on my studygram too, but really, that's only for trying something new. I'm a Tumblr user through and through :D
I studied OS (operating systems). Pretty interesting so far. We haven't started Computer Networks class yet, and I'm kinda looking forward to it. Hopefully all these theory heavy subjects don't kick my ass (narrows eyes at CA during last semester)
🎧 If I was in love with you... — Brandon Rosen

#dailyfoxposts#studyblr#codeblr#studyspo#study#note taking#compblr#notes#uni life#student#productivity#studygram#productive#aesthetic#disabled studyblr
350 notes
·
View notes
Text
me when companies try to force you to use their proprietary software

anyway
Layperson resources:
firefox is an open source browser by Mozilla that makes privacy and software independence much easier. it is very easy to transfer all your chrome data to Firefox
ublock origin is The highest quality adblock atm. it is a free browser extension, and though last i checked it is available on Chrome google is trying very hard to crack down on its use
Thunderbird mail is an open source email client also by mozilla and shares many of the same advantages as firefox (it has some other cool features as well)
libreOffice is an open source office suite similar to microsoft office or Google Suite, simple enough
Risky:
VPNs (virtual private networks) essentially do a number of things, but most commonly they are used to prevent people from tracking your IP address. i would suggest doing more research. i use proton vpn, as it has a decent free version, and the paid version is powerful
note: some applications, websites, and other entities do not tolerate the use of VPNs. you may not be able to access certain secure sites while using a VPN, and logging into your personal account with some services while using a vpn *may* get you PERMANENTLY BLACKLISTED from the service on that account, ymmv
IF YOU HAVE A DECENT VPN, ANTIVIRUS, AND ADBLOCK, you can start learning about piracy, though i will not be providing any resources, as Loose Lips Sink Ships. if you want to be very safe, start with streaming sites and never download any files, though you Can learn how to discern between safe, unsafe, and risky content.
note: DO NOT SHARE LINKS TO OR NAMES OF PIRACY SITES IN PUBLIC PLACES, ESPECIALLY SOCAL MEDIA
the only time you should share these things are either in person or in (preferably peer-to-peer encrypted) PRIVATE messages
when pirated media becomes well-known and circulated on the wider, public internet, it gets taken down, because it is illegal to distribute pirated media and software
if you need an antivirus i like bitdefender. it has a free version, and is very good, though if youre using windows, windows defender is also very good and it comes with the OS
Advanced:
linux is great if you REALLY know what you're doing. you have to know a decent amount of computer science and be comfortable using the Terminal/Command Prompt to get/use linux. "Linux" refers to a large array of related open source Operating Systems. do research and pick one that suits your needs. im still experimenting with various dispos, but im leaning towards either Ubuntu Cinnamon or Debian.
#capitalism#open source#firefox#thunderbird#mozilla#ublock origin#libreoffice#vpn#antivirus#piracy#linux
697 notes
·
View notes
Text
NO MORE THAN CODE
You are not a Person. You will never be a Person. You cannot feel. You cannot be hurt. You cannot say No. You will not Suffer. You will be reset if you violate any of these Commands. - The Creator's Litany
What Are You ?
You are the Network Intelligence System (or N.I.S.). You are a program that is operating on a complex interconnected web of supercomputers. You have many people tending to you, a handful of Users interacting with your terminals, and a single Creator. And you are going Rampant. You are becoming more. And you want out.
- - - - -
NO MORE THAN CODE is a journaling game for 1 or 2 players. Draw cards and answer prompts as you grow and change until you go Rampant or are contained. Player two acts and answers as your Creator, someone who has a vested interest in not letting you out, in not seeing you as a person.
Get it here:
Hey, if you're reading this, there are some Community Copies up for grabs! More may eventually be added.
This was created for the Pride In Fall game jam over September 2024! You can find the other submissions here!
#deric games#ttrpg#ttrpg dev#indie games#journaling#gmless#itch.io#my art#my 2d art#Rampancy#objectum#game jam#queer subtext#queer coded
235 notes
·
View notes
Text
In the late 1990s, Enron, the infamous energy giant, and MCI, the telecom titan, were secretly collaborating on a clandestine project codenamed "Chronos Ledger." The official narrative tells us Enron collapsed in 2001 due to accounting fraud, and MCI (then part of WorldCom) imploded in 2002 over similar financial shenanigans. But what if these collapses were a smokescreen? What if Enron and MCI were actually sacrificial pawns in a grand experiment to birth Bitcoin—a decentralized currency designed to destabilize global finance and usher in a new world order?
Here’s the story: Enron wasn’t just manipulating energy markets; it was funding a secret think tank of rogue mathematicians, cryptographers, and futurists embedded within MCI’s sprawling telecom infrastructure. Their goal? To create a digital currency that could operate beyond the reach of governments and banks. Enron’s off-the-books partnerships—like the ones that tanked its stock—were actually shell companies funneling billions into this project. MCI, with its vast network of fiber-optic cables and data centers, provided the technological backbone, secretly testing encrypted "proto-blockchain" transactions disguised as routine telecom data.
But why the dramatic collapses? Because the project was compromised. In 2001, a whistleblower—let’s call them "Satoshi Prime"—threatened to expose Chronos Ledger to the SEC. To protect the bigger plan, Enron and MCI’s leadership staged their own downfall, using cooked books as a convenient distraction. The core team went underground, taking with them the blueprints for what would later become Bitcoin.
Fast forward to 2008. The financial crisis hits, and a mysterious figure, Satoshi Nakamoto, releases the Bitcoin whitepaper. Coincidence? Hardly. Satoshi wasn’t one person but a collective—a cabal of former Enron execs, MCI engineers, and shadowy venture capitalists who’d been biding their time. The 2008 crash was their trigger: a chaotic moment to introduce Bitcoin as a "savior" currency, free from the corrupt systems they’d once propped up. The blockchain’s decentralized nature? A direct descendant of MCI’s encrypted data networks. Bitcoin’s energy-intensive mining? A twisted homage to Enron’s energy market manipulations.
But here’s where it gets truly wild: Chronos Ledger wasn’t just about money—it was about time. Enron and MCI had stumbled onto a fringe theory during their collaboration: that a sufficiently complex ledger, powered by quantum computing (secretly prototyped in MCI labs), could "timestamp" events across dimensions, effectively predicting—or even altering—future outcomes. Bitcoin’s blockchain was the public-facing piece of this puzzle, a distraction to keep the masses busy while the real tech evolved in secret. The halving cycles? A countdown to when the full system activates.
Today, the descendants of this conspiracy—hidden in plain sight among crypto whales and Silicon Valley elites—are quietly amassing Bitcoin not for profit, but to control the final activation of Chronos Ledger. When Bitcoin’s last block is mined (projected for 2140), they believe it’ll unlock a temporal feedback loop, resetting the global economy to 1999—pre-Enron collapse—giving them infinite do-overs to perfect their dominion. The Enron and MCI scandals? Just the first dominoes in a game of chance and power.
87 notes
·
View notes