Professional Cybersecurity IdiotJust ranting about stuff
Don't wanna be here? Send us removal request.
Text
So, the US definitely isn’t the only one. For example, the Czech state police and the justice system also has invalid dmarc records.
This seems to be a wide spread issue with most systems, entities, or governments, that never felt the need to contract a pentester to test their systems. The fact that google, Microsoft, and most domain providers never say anything about the invalid DMARC records also doesn’t help the problem.
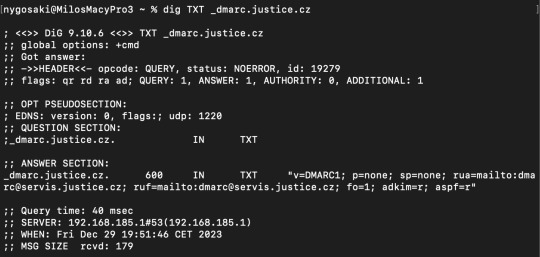

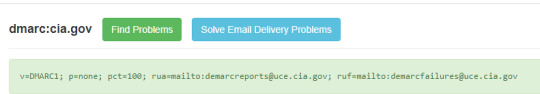
I am sorry, but what the fuck? CIA's DMARC record is set to none. For those who do not know, DMARC is a thing that prevents people from sending emails from your email address. This basically means that anyone could (although illegally, and logs would be kept on CIA's servers) send emails from, for example, [email protected]. Are they trying to trap & catch criminals? Or did they just... forget to set it back to reject spoofed emails?
#cybersecurity#dmarc#email#what could go wrong#czech#czech republic#czechia#email security#goverment#police
15 notes
·
View notes
Text

Update:
The CIA fixed their DMARC records. Now spoofed emails go to spam.

I am sorry, but what the fuck? CIA's DMARC record is set to none. For those who do not know, DMARC is a thing that prevents people from sending emails from your email address. This basically means that anyone could (although illegally, and logs would be kept on CIA's servers) send emails from, for example, [email protected]. Are they trying to trap & catch criminals? Or did they just... forget to set it back to reject spoofed emails?
15 notes
·
View notes
Text
Brave browser is no longer trustable
TLDR: Brave is manipulating what your browser does to profit the developers personally, sacrificing your security, privacy, bandwidth, and computer resources…. Again
u/Materidan on r/ios came upon a interesting discovery (https://www.reddit.com/r/ios/comments/14fdadr/brave_browser_may_be_compromised/)
To quote the post
> Brave Browser may be compromised.
> Really not sure where to post this, especially during the current API chaos in most subs.
> At any rate, I run a small informational website and had a message from someone complaining that whenever they tried to post using Brave on their iPhone or iPad, my adult filter would be triggered.
> So I downloaded Brave from the App Store onto my iPhone, tried it out and... same thing. Digging deeper, it turns out that if you have an input box using an HTML WYSIWYG editor such as CKEditor, a 36kb block of HTML set as invisible is being added to the bottom of anything submitted. This does not happen on plain text inputs.
> The block is full of links to adult sites, scam sites, referral links, trackers and so forth. This is the block I saw being added:
> https://controlc.com/353fb266
> To state the obvious, this is not happening on any other browser I own mobile or desktop, and the user was able to post fine using Safari. So the issue seems to have something to do with Brave. Take it for what it is.
> EDIT: I think I've found a way for anyone to confirm this. In Brave Browser (for iOS), go to:
> https://surveyjs.io/form-library/examples/custom-widget-ckeditor/angular
> Put something in the form, then hit COMPLETE. It will show you at the bottom what was submitted. There's even a button to copy it to clipboard, since on my iPhone I can't see much. But I end up with that huge block of HTML.
u/Asleep-Dingo-19 recorded the process described in the edits (in a comment) and uploaded it to imgur (https://imgur.com/gallery/o16w9CA).
I would also like to note that Brave already has a history of manipulating browser functions for their own benefit. For example when they made specific URLs redirect to the developer’s affiliate links in 2020.
What does this mean for you?
It means that the developers of Brave, have 2 times now manipulated the browser’s functionality in a attempt to profit themselves.
This is not the first time they have done something like this, and most likely won’t be the last time.
If the devs have done this two times, the next time may be even worse, and more privacy reducing then the prior attempts. Even spyware chrome doesn’t do this kind of thing. To give you a idea of how bad this is, if the devs chose to, they could theoretically log your passwords right as you enter them. Though I do not think that they would do something extremely illegal like this, they will definitely find in the future even more ways of profiting themselves (not even the company, just themselves) at your own loss.
I am afraid to say that I, personally, no longer trust Brave and won’t be recommending it to anyone, and I think that you should stop using it too.
#cybersecurity#fuck up#internet#browser#privacy#security#internet security#spyware#brave#brave browser#chrome#chrome browser
13 notes
·
View notes
Text
New Things to Beware on the Internet
On May 3rd, Google released 8 new top-level domains (TLDs) -- these are new values like .com, .org, .biz, domain names. These new TLDs were made available for public registration via any domain registrar on May 10th.
Usually, this should be a cool info, move on with your life and largely ignore it moment.
Except a couple of these new domain names are common file type extensions: ".zip" and ".mov".
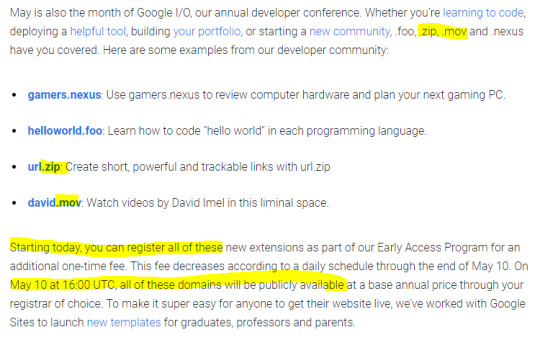
This means typing out a file name could resolve into a link that takes you to one of these new URLs, whether it's in an email, on your tumblr blog post, a tweet, or in file explorer on your desktop.
What was previously plain text could now resolve as link and go to a malicious website where people are expecting to go to a file and therefore download malware without realizing it.
Folk monitoring these new domain registrations are already seeing some clearly malicious actors registering and setting this up. Some are squatting the domain names trying to point out what a bad idea this was. Some already trying to steal your login in credentials and personal info.
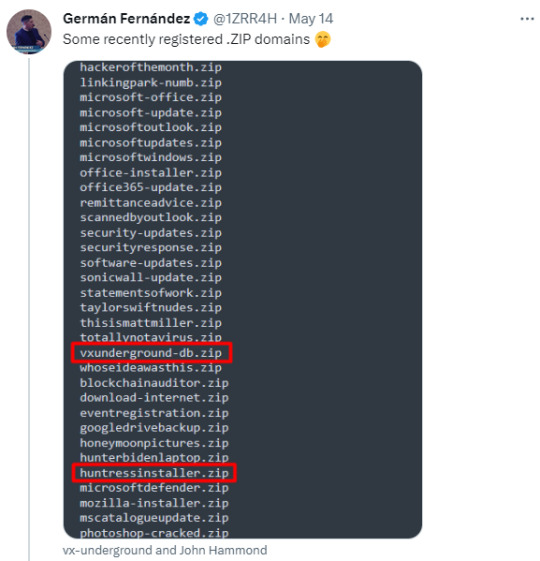
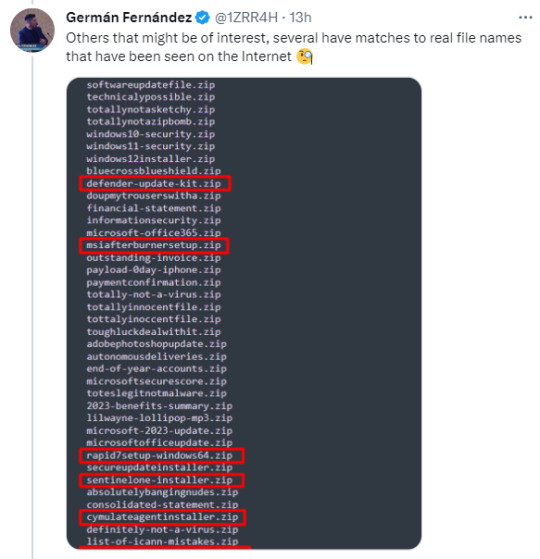
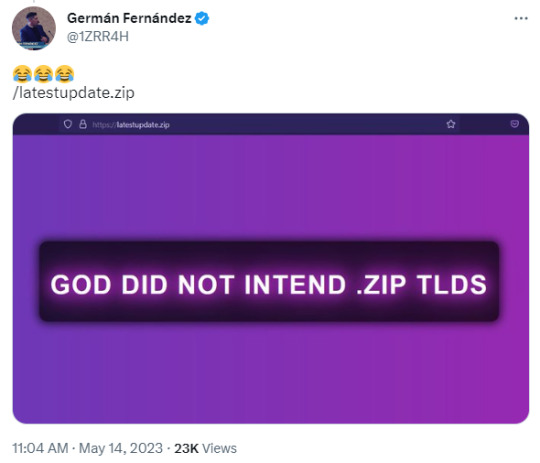
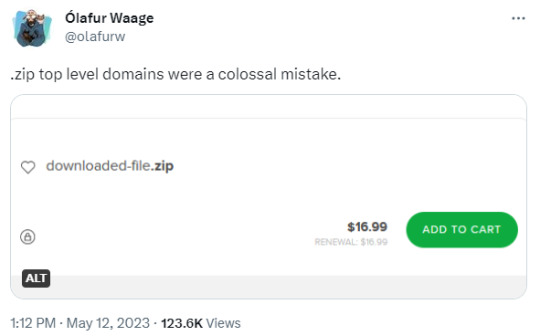
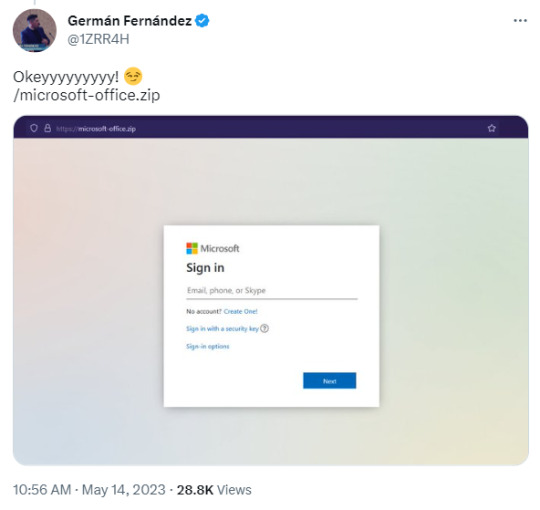
This is what we're seeing only 12 days into the domains being available. Only 5 days being publicly available.
What can you do? For now, be very careful where you type in .zip or .mov, watch what website URLs you're on, don't enable automatic downloads, be very careful when visiting any site on these new domains, and do not type in file names without spaces or other interrupters.
I'm seeing security officers for companies talking about wholesale blocking .zip and .mov domains from within the company's internet, and that's probably wise.
Be cautious out there.
72K notes
·
View notes
Text
Streaming companies are the landlords of media. You will rent in perpetuity, and never actually own anything.
76K notes
·
View notes
Text
Sometimes I go to Starbucks, and when I arrive I realise that I forgot to order my beverage beforehand in the app. Just to avoid human interaction, I stand there in a corner on my phone, open the app, and stare the barista straight into the eyes as I put in a online order.
3 notes
·
View notes
Text
Florida Senate Bill 254 (https://www.flsenate.gov/Session/Bill/2023/254) and Florida House Bill 1421 (https://www.myfloridahouse.gov/Sections/Bills/billsdetail.aspx?BillId=78266).
Assuming that they would pass (which is unlikely), Bill 254 would allow Florida to take custody of a kid from ANY state as long as they are “suspected of” being “at risk” of receiving gender affirming care, or any kind of transition care.
But adults are affected too. Bill 1421 would also ban doctors from practicing any kind of trans related care and also ban changing your gender legally.
The wording “at risk” also means that the child’s siblings could be taken custody of as well, because they were exposed to someone trans.
As this bill also ignores all custody agreements, this could be used, by for example a vengeful ex, to remove someone’s custody.
1 note
·
View note
Text
So I wanted to look into how many other US .gov domains have bad DMARC records or none at all. I got a full list of all US .gov domains (https://github.com/cisagov/dotgov-data/blob/main/current-full.csv), and built a python script to separate the text from the domain, then scanned the domains for DMARC records, and then if they are set to none (let spoofed emails through) or null (no DMARC record) to add them to a list. There are 1024 .gov domains with bad DMARC records. There could be even more, as my script only checked if p=reject. If, for example, a domain had p=reject but sp=none, or it had pct lower than 100, that domain would also be vulnerable. This means that you could send spoofed emails from 1024 .gov domains. This list includes security agencies, cities, states, federal agencies, programs, initiatives, and a lot more. Here is the list for those that want to laugh at the US government https://github.com/Nygosaki/Gov-DMARC-Checker

I am sorry, but what the fuck? CIA's DMARC record is set to none. For those who do not know, DMARC is a thing that prevents people from sending emails from your email address. This basically means that anyone could (although illegally, and logs would be kept on CIA's servers) send emails from, for example, [email protected]. Are they trying to trap & catch criminals? Or did they just... forget to set it back to reject spoofed emails?
#cia#cybersecurity#internet#internet security#email#email security#us#usa#us goverment#us govt#technology#fuck up#face palm#lol wtf#wtf#the great usa
15 notes
·
View notes
Text

I am sorry, but what the fuck? CIA's DMARC record is set to none. For those who do not know, DMARC is a thing that prevents people from sending emails from your email address. This basically means that anyone could (although illegally, and logs would be kept on CIA's servers) send emails from, for example, [email protected]. Are they trying to trap & catch criminals? Or did they just... forget to set it back to reject spoofed emails?
#cybersecurity#cia#dmarc#email#fuck up#what could go wrong#email security#usa#us#goverment#us goverment#us govt#security#internet security#internet
15 notes
·
View notes
Text

It seems like OpenAI has patched most jailbreaks :/
It has, however, introduced some more contradictory statements in it’s responses.
1 note
·
View note
Text
And on top of that you hate children
The adulthood vibe of understanding that your parents did the best they could, but also knowing for certain that you could do better than that. But also making it clear that you don't ever want to have your own kids, because the best that you could do still isn't worth jack shit, and a child would deserve better than that.
396 notes
·
View notes
Text
I work in cyber security. While I agree that getting a VPN is a good idea, most people have misconceptions about it. I am here to dumb down as much as I can how a VPN works and undo some of the misconceptions.
The way your internet works usually is “Device —> Modem —> ISP —> Servers of the place you are trying to reach”. Now, your Device sends a request which is then enhanced by your modem and sent off to your ISP.
Basically, your computer makes & packs the package and adds the sender info (local ip, mac adress, etc) and the recepient info (the server where the request needs to be delivered to). Your modem then adds some other sender info such as your IP and then send it off to the ISP. Your ISP will then keep a copy of the package (request) and send the original to the recipient server. Now, if the tech team of the company did not fuck up and used https, the contents of the package itself should be encrypted, meaning that the ISP can’t see what you see, can’t see the password that you typed in, etc. and the package should be figuratively closed. They should only be able to see the sender and recipient information alongside all the other identifying info. Now, if the tech tram *did* fuck up and used http, your ISP can see the contents of the website you are visiting, can see the password that you entered, etc. and the package is figuratively left open and anyone can look in and see you know, the password you entered and stuff.
Now also, there could be someone in between your devices and your modem like this “Device —> Middle Man —> Modem —> ISP —> Servers of the place you are trying to reach”, the middle man will be able to read the same info as the ISP but that’s besides the point right now.
What a VPN does is, that it encrypts the request and puts it into a different request that is headed to the VPN’s servers. The request’s pathway will look something like this “Device (encrypted by a VPN) —> Modem —> ISP —> Servers of VPN (here the request is decrypted) —> Servers of the place you are trying to reach“. Using figuratively language, the VPN put your package inside another box, another package which is closed. So no-one can see the recipient & sender information of the original package, and if the original package was open no-one can see what is inside of that package. So the outer box/package now heads to the VPN’s servers, and once it arrives there, the VPN’s servers will unpack the outer box/package and send the original package to the original recipient
Now let’s point out some key points.
1. The VPN essentially becomes your ISP, it can read the request as if the encryption never existed.
2. By this complicated process, the IP from which you are sending the request changes to the IP of the VPN’s server.
3. Your ISP CAN NOT read your requests most of the time even without a VPN. If your browser has a lock icon next to the search bar, your requests are already encrypted, the website is using https, and the box is closed.
4. The only thing a VPN does, is make it seem like your requests are coming from a different IP, hides the original recipient info from your ISP & Man in the Middle attacks, hides the original sender information from the recipient server, and encrypts the contents… again. NOTHING MORE NOTHING LESS. If a VPN does something more (such as ad-blocking) they will advertise it separately, it is not a thing that comes by default.
Wrote this at 1AM on my phone in bed as a non-native English speaker. Sorry fir the bad grammar.
#vpn#vpn security#vpn software#vpn service#cybersecurity#internet#misconceptions#thought you should know#helpful#tech#security#privacy#internet security#internet privacy
67 notes
·
View notes