Don't wanna be here? Send us removal request.
Text
Server Saturday: Delivering Content at Lightning Speed - Understanding Content Delivery Networks (CDN)
Welcome to Server Saturday, where we dive into the world of content delivery networks (CDNs)! Today, get ready for an entertaining and informative journey through the magical realm of CDNs. We’ll explore how CDNs deliver content at lightning speed, ensuring a delightful user experience. With the help of funny analogies and cheerful emojis, we’ll make even the most novice readers understand the…

View On WordPress
#analogies#caching#CDNs#content delivery networks#emojis#enhanced security#global reach#scalability#super speedy couriers#website performance
0 notes
Text
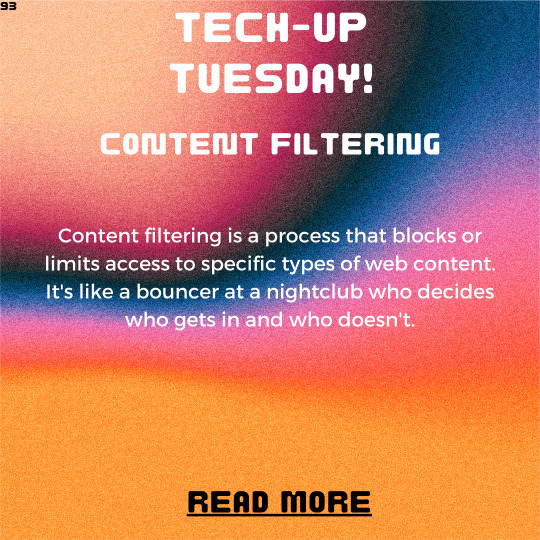
Tech-Up Tuesday: Content Filtering - Protecting Your Network from Malicious Content
Welcome to another exciting edition of Tech-Up Tuesday! Today, we’re diving deep into the world of content filtering and how it can protect your network from those pesky malicious elements. Get ready for a hilarious and informative journey, complete with analogies and emojis, to help even the most novice readers understand the importance of content filtering. Let’s get started! 😄 Introduction:…
View On WordPress
#analogies#benefits#content filtering#emojis#filtering types#malicious content#network protection#network security
0 notes
Text
Mesh it Up Monday: Web Hosting - Finding Your Place on the World Wide Web
Welcome to another Mesh it Up Monday, where we dive deep into the fascinating world of web hosting! Today, we’ll take you on a fun-filled journey through the intricacies of finding your place on the World Wide Web. So, sit back, relax, and get ready to embark on this exciting adventure! 😄 Introduction to Web Hosting: The Cyberspace Real Estate Imagine the internet as a bustling city with…

View On WordPress
#analogies#beginners#choose the right provider#emojis#factors to consider#finding the perfect place#hosting options#web hosting#World Wide Web
0 notes
Text
Subnet Sunday: Domain Name System (DNS) - The Address Book of the Internet
Welcome to Subnet Sunday, where we unravel the mysteries of the Domain Name System (DNS) in a fun and entertaining way. In this blog post, we’ll explore how DNS functions as the address book of the internet, connecting websites to their corresponding IP addresses. Using relatable analogies, humorous anecdotes, and a sprinkle of emojis, we’ll make DNS easy to understand for even the most novice…

View On WordPress
#address book of the internet#DNS#DNS caching#DNS detectives#DNS resolution#DNS security#DNS servers#Domain Name System#IP addresses#website names
0 notes
Text
Server Saturday: Managing Your Server - Tips and Best Practices for Keeping Your Server Running Smoothly
Welcome to Server Saturday, where we embark on a humorous journey to explore the world of server management. In this blog post, we’ll equip you with practical tips and best practices to ensure your server runs smoothly, even if you’re a novice in the realm of server administration. We’ll use funny analogies, relatable emojis, and a touch of humor to make server management an enjoyable adventure.…

View On WordPress
#backups#best practices#performance optimization#scalability#security measures#server administration#server maintenance#server management#software updates#tips
0 notes
Text
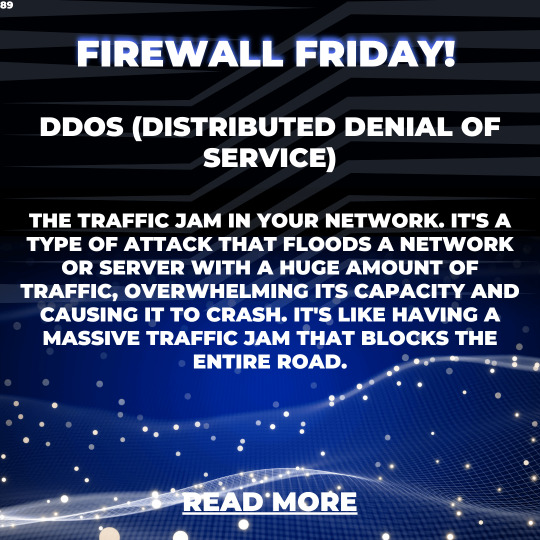
Firewall Friday: Defending Against DDoS Attacks - How to Keep Your Network Safe
Welcome to Firewall Friday, where we dive into the world of DDoS attacks and equip you with the knowledge to safeguard your network against these digital bullies. But don’t worry, we won’t let these troublemakers ruin our Friday vibes. Instead, we’ll tackle the topic with a humorous tone, using analogies and emojis to make it easy for even the most novice readers to understand. So, put on your…
View On WordPress
#anomaly detection#cloud-based defenses#cybersecurity#DDoS attacks#firewall#intrusion prevention systems#load balancing#network security#rate limiting#traffic analysis
0 notes
Text
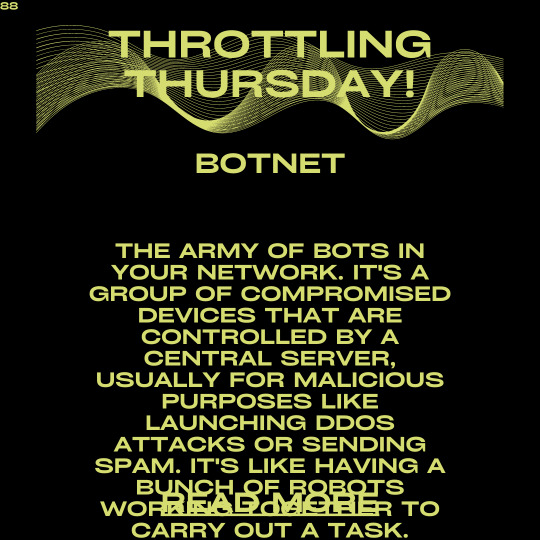
Throttling Thursday: Botnet - The Menace Lurking in Your Network
Welcome to Throttling Thursday, where we unveil the hidden world of botnets and equip you with the knowledge to combat these digital troublemakers. But don’t worry, we won’t let these mischievous bots ruin our day. Instead, we’ll tackle the topic with a humorous tone, using analogies and emojis to make it easy for even the most novice readers to understand. So, fasten your seatbelts, put on your…
View On WordPress
#anti-malware software#behavior-based detection#botnet#collaboration against botnets#combat botnets#digital menace#firewall#network security#recognizing botnet signs#traffic analysis#vulnerability patches
0 notes
Text
Webinar Wednesday: Combatting Spam - Effective Strategies for Blocking Unwanted Emails
Welcome to Webinar Wednesday! 🎉 Today, we’re tackling the pesky world of spam and empowering you with effective strategies to block those unwanted emails. But don’t worry, we won’t let these digital nuisances ruin our inbox party. Instead, we’ll approach the topic with a humorous tone, using analogies and emojis to make it easy for even the most novice readers to understand. So, grab your virtual…

View On WordPress
#blocking unwanted emails#combatting spam#disposable email addresses#effective spam strategies#email filters#protect email address#recognize spam#reporting spamcombatting spam#spam prevention#unsubscribe from newsletters#whitelist trusted senders
0 notes
Text
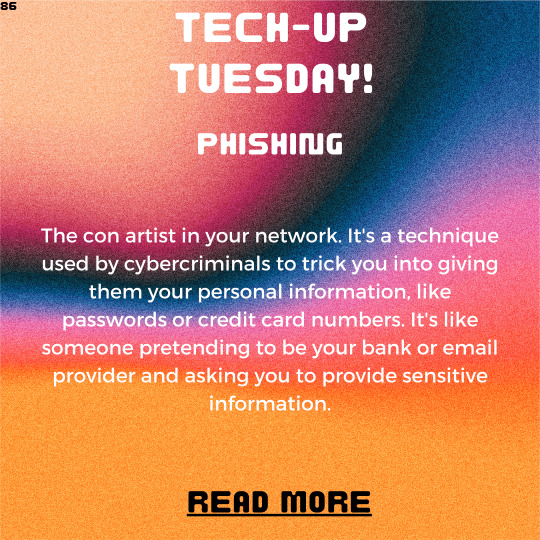
Tech-Up Tuesday: Phishing 101 - How to Recognize and Avoid Email Scams
Welcome to Tech-Up Tuesday! 🎉 Today, we’re diving into the world of phishing and equipping you with the knowledge to recognize and avoid those sneaky email scams. But fear not, we won’t let these cyber tricksters get the best of us. Instead, we’ll tackle the topic with a humorous twist, using analogies and emojis to make it easy for even the most novice readers to understand. So, grab your…
View On WordPress
#avoiding email scams#cyber anglers#email scams#online security#phishing#phishing prevention#recognizing phishing#social engineering#spoofed sender#two-factor authentication
0 notes
Text
Mesh it Up Monday: Ransomware - The Real-Life Villain in the Cyber World
Welcome to Mesh it Up Monday! 🎉 Today, we’re delving into the captivating realm of ransomware, the real-life villain of the cyber world. But fear not, we won’t let this digital menace intimidate us. Instead, we’ll tackle the topic with a humorous twist and analogies that even a novice can relate to. So, fasten your virtual seatbelts, put on your cybersecurity capes, and let’s dive into the…

View On WordPress
#CryptoLocker#cyber world#cybersecurity heroes#data security#Locky#Petya#ransomware#ransomware protection#ransomware threats#WannaCry
0 notes
Text
Server Saturday: The Importance of Antivirus Software for Your Servers
Welcome to another exciting edition of Server Saturday! 🎉 Today, we’re going to delve into the fascinating world of antivirus software and explore why it’s crucial for your servers. 🖥️✨ Why Antivirus Software Matters Imagine your servers as a bustling city, with data flowing through its virtual streets like busy commuters. Just like in any vibrant city, there are bound to be some unsavory…

View On WordPress
#antivirus software#best antivirus solutions#cyber threat prevention#digital security#malware defense#real-time protection#server protection#server safety#server security#virus protection
0 notes
Text
Firewall Friday: Clients - Connecting Your Devices to the Network
Welcome to Firewall Friday, where we bring you another entertaining and informative blog post about the world of networking! Today, we’re diving into the realm of “clients” – those delightful devices that connect to networks and keep us connected. In this hilarious and comprehensive guide, we’ll use analogies, emojis, and our signature funny tone to explain clients in a way that even a novice…
View On WordPress
#client devices#clients#connection dance#connection problems#emojis in clients#firewall#gaming consoles#laptops#network connectivity#smart home devices#smart TVs#smartphones#types of clients#Wi-Fi issues
0 notes
Text
Webinar Wednesday: Decoding Decryption - Understanding the Process of Securing Data
Welcome to another exciting Webinar Wednesday! Today, we’re diving into the intriguing world of decryption, where we unravel the secrets of securing your data. Get ready for an informative and entertaining session as we decode the process of decryption using analogies, emojis, and our signature funny tone. So, grab your virtual seat and let’s begin! Introduction to Decryption: Unlocking the…

View On WordPress
#data security#decryption#encryption algorithm#key management#layered security#lock and key analogy#online transactions#regular updates#secure communication#strong encryption
0 notes
Text
Mesh it Up Monday: Authorization - The Key to Secure Network Access
Welcome to another Mesh it Up Monday, where we delve into the world of networking with a sprinkle of humor and a whole lot of knowledge! Today, we’re going to unlock the secrets of authorization and discover how it acts as the key to secure network access. So grab your virtual keychain and let’s dive in! Chapter 1: The Magical Key 🔑✨ Imagine you’re at the entrance of a fabulous party. You…
View On WordPress
#access control#authentication#authorization#authorization methods#biometric authentication#digital signatures#network access#network dance floor#network security#RBAC#role-based access control#two-factor authentication#username and password
0 notes
Text
Subnet Sunday: Authentication - Proving Your Identity on the Network
Welcome to Subnet Sunday, where we unravel the mysteries of authentication in a fun and humorous way. In this edition, we’ll take you on a journey through the colorful world of proving your identity on the network. Using relatable analogies, playful emojis, and a touch of wit, we’ll demystify authentication and make it accessible for novice readers. So, get ready to don your digital passport and…

View On WordPress
#access control#authentication#authentication methods#authentication protocols#best practices for authentication#biometric authentication#multi-factor authentication#network dance floor#network security#password security#proving identity#two-factor authentication
0 notes
Text
Server Saturday: Controlling Access to Your Network - A Guide to Access Control
Welcome to Server Saturday, where we embark on a humorous and informative journey into the world of network access control. In this edition, we’ll unravel the mysteries of access control, using common analogies, playful emojis, and a funny tone to help novice readers understand this essential aspect of network security. Get ready to tighten the reins and control who enters your digital kingdom!…

View On WordPress
#access control#activity logging#authorization#biometric authentication#credential theft#network perimeter protection#network security#network segmentation#password cracking#principle of least privilege#privilege escalation#RBAC#security policies#user authentication
0 notes
Text
Firewall Friday: Network Security - Protecting Your Network from Threats
Welcome to Firewall Friday, where we dive into the exciting world of network security with a touch of humor and relatable analogies. In this edition, we’ll explore the importance of network security and how firewalls act as the guardians of your network, protecting it from potential threats. Get ready to embark on a hilarious and informative journey as we use common analogies, playful emojis, and…

View On WordPress
#access control#brute force attacks#data encryption#employee education#firewall#hackers#intruders#intrusion prevention#multi-layered defense#network protection#network security#packet inspection#patch management#security incident response#spoofing
0 notes