#network segmentation
Explore tagged Tumblr posts
Text

0 notes
Text
Safeguarding Connectivity: Addressing Vulnerabilities in 5G Infrastructure
In the realm of technological evolution, 5G has emerged as the pinnacle of innovation, promising unprecedented connectivity, lightning-fast speeds, and transformative capabilities. However, amidst the euphoria surrounding this groundbreaking technology, concerns about security loom large. As the 5G landscape continues to evolve, ensuring robust security measures is imperative to mitigate potential risks and safeguard sensitive data.
Understanding the Significance of 5G Security
Defining the Paradigm Shift
5G represents a paradigm shift in wireless communication, revolutionizing industries, and empowering IoT ecosystems. With its enhanced speed, capacity, and low latency, 5G is poised to unleash a wave of innovation across various sectors, ranging from healthcare and transportation to manufacturing and entertainment. However, the proliferation of 5G also introduces novel security challenges that demand proactive solutions.
Addressing Vulnerabilities
The unprecedented speed and connectivity offered by 5G networks amplify the attack surface, rendering traditional security measures inadequate. Cybercriminals can exploit vulnerabilities in 5G infrastructure to launch sophisticated cyberattacks, compromising network integrity and data confidentiality. From DDoS attacks to man-in-the-middle assaults, the threat landscape has evolved, necessitating robust security protocols to safeguard against potential breaches.
The Evolution of 5G Security Measures
Encryption and Authentication
Encryption lies at the heart of 5G security, ensuring that data remains confidential and integrity is maintained during transmission. Advanced cryptography algorithms such as AES and Elliptic Curve Cryptography are employed to encrypt data packets, thwarting eavesdropping attempts by malicious actors. Additionally, stringent authentication mechanisms, including digital certificates and biometric authentication, bolster access control and mitigate the risk of unauthorized access.
Network Slicing and Virtualization
Network slicing emerges as a game-changer in 5G security, enabling service providers to partition network resources into distinct virtual networks tailored to specific use cases. By implementing isolated slices with dedicated security policies, organizations can ensure segmentation and isolation of critical services, minimizing the blast radius in the event of a security breach. Furthermore, network function virtualization (NFV) enhances agility and resilience, allowing rapid deployment of security functions to counter emerging threats.
AI-Powered Threat Detection
In the era of 5G, Artificial Intelligence (AI) emerges as a potent ally in the cybersecurity arsenal, leveraging machine learning algorithms to detect and mitigate threats in real-time. By analyzing vast datasets and identifying anomalies in network traffic, AI-driven security solutions can preemptively thwart cyberattacks before they escalate, thereby fortifying 5G infrastructure against evolving threats.
Collaboration and Regulatory Compliance
Industry Collaboration
The complexity and interconnectedness of 5G ecosystems necessitate collaboration among stakeholders to establish industry-wide standards and best practices. From telecommunication providers and equipment manufacturers to government agencies and regulatory bodies, concerted efforts are required to foster a secure and resilient 5G ecosystem. Information sharing and collaborative research play a pivotal role in strengthening cyber defenses and mitigating emerging threats.
Regulatory Frameworks
Regulatory frameworks serve as a cornerstone of 5G security, providing guidelines and compliance mandates to ensure adherence to security standards and privacy regulations. Regulatory bodies such as the National Institute of Standards and Technology (NIST) and the European Telecommunications Standards Institute (ETSI) play a pivotal role in shaping the security landscape by issuing recommendations and certifications to validate compliance with security protocols.
Conclusion
As 5G continues its inexorable march towards global proliferation, security remains paramount in unlocking its transformative potential. By embracing encryption, network slicing, AI-driven threat detection, and fostering collaboration across industry stakeholders, organizations can fortify 5G infrastructure against emerging threats and embark on a journey towards a secure and resilient digital future.
#5G security#telecommunications#connectivity#innovation#cyberattacks#data breaches#encryption#authentication mechanisms#network segmentation#continuous monitoring#digital infrastructure#technology#privacy#artificial intelligence#nextgeneration connectivity#digital future#cyber security
0 notes
Text
Elevate Your Network Security with Network Segmentation from Century Solutions Group!
In the ever-expanding digital landscape, a one-size-fits-all approach just won't cut it. That's where network segmentation comes in – like creating digital neighborhoods within your network, each with its own security measures and access controls.
Why is network segmentation crucial? Picture your network as a bustling city . Without proper segmentation, a breach in one area could spread like wildfire, jeopardizing your entire infrastructure. But with segmented networks, we're building digital fortresses, containing threats and minimizing their impact.
Don't let your network become a free-for-all – trust Century Solutions Group to implement smart segmentation strategies and keep your data safe and sound. Your security is our top priority! #NetworkSegmentation #CyberSecurity #CenturySolutionsGroup
1 note
·
View note
Link
Class C IP Checker - Analyze Your IP Network Segmentation
#Class C IP Checker#Free Micro Tools#IP analysis#network segmentation#IP management#SEO tools#IP class distribution#network management
0 notes
Text
Server Saturday: Controlling Access to Your Network - A Guide to Access Control
Welcome to Server Saturday, where we embark on a humorous and informative journey into the world of network access control. In this edition, we’ll unravel the mysteries of access control, using common analogies, playful emojis, and a funny tone to help novice readers understand this essential aspect of network security. Get ready to tighten the reins and control who enters your digital kingdom!…

View On WordPress
#access control#activity logging#authorization#biometric authentication#credential theft#network perimeter protection#network security#network segmentation#password cracking#principle of least privilege#privilege escalation#RBAC#security policies#user authentication
0 notes
Text
the way that even in early usa, extended families often lived together or within walking distance
the idea that each nuclear family should have its own house, own appliances, own everything and that adult children should move out at 18 is a relatively recent post-WWII, suburbanization-era invention
and it just so happens to be highly profitable
#segmentation of the customer even#this is why charming acres and 1950s features the way it does#1950s popularized the image of the self-contained upwardly mobile nuclear family#the game is rigged#extended family living was increasingly framed as backward immigrant or rural#suburban nuclear family became a national identity project and it survives in marketing materials and specific targeted consumerism#consumerism Cold War ideology and gender roles (housewife breadwinner etc.)#bc from a business perspective splitting extended families into individual homes was a gold mine#not owning a home not having a perfect family unit needing help from relatives staying with your parents past 18#or relying on community all became loaded with stigma#the use of words like codependent and socially incestuous applied liberally furthered the agenda#pop psychology gets over applied#they’re often over-applied in contexts where people are simply staying close surviving together or choosing mutual care#what gets labeled as pathology is not weird at all and historically common and culturally valid… it’s just not as profitable#making them question bonds that may be loving supportive and necessary#thinking about this a lot being more embedded in an extended network again#anyway spn does this well!#abusing the lower class then calling them Weird for huddling together when upper classes are in fact the ones who are flagrantly nepotism#when in fact upper class is Weirder and 9-10 times the one salivating over the Idea is upper class#i feel like if you miss this you miss Everything#surburbia is weird and isolating on purpose
24 notes
·
View notes
Text
do you guys remember that one ad where megatron excitedly announces that he loves pounding the autobots. and pound cake
#saw it on yt again after years#god bless the era of whacky promos like the ask megatron segmet for shows on the network. you are so missed#anyway I was crying laughing 🪦✨✨✨✨✨✨✨#yes we know pound was not intended like that. but it's funny anyway#😭😭😭✨💀✨✨#transformers#tf#tfp#transformers prime#tfp megatron#megatron#transformers stuff#maccadam#kuni talks#random#observations#*segment not segmet sorry
58 notes
·
View notes
Text
One of my favourite bits from the ccf hosting is johnny (eventually joined by chicken) annoying double d and the rest of the show is just these little comments before he snaps and calls on baboon to chase them
#⭐️#edd’s host segments are my favourite they’re so silly#i also love the specials. it’s fun how they got weasel to do it on special occasions#cartoon network
7 notes
·
View notes
Text
Thoughts on Bit City episode 1
Let me just start off by saying that I think objectively it was a good episode. Many people have pointed this out already, but the 1D reunion was definitely a standout, Tommy was so funny in that. I also thought the end segment was funny, and a good note to end on.
I'm sure the series will grow on me, but for this specific episode, I kind of didn't feel like I was the target audience lol. I mean, I know some pop culture stuff, but... yeah I just don't really get very invested in a lot of stuff about musical artists. I barely know anything about Sabrina Carpenter, I haven't even listened to her music since she was on Girl Meets World. I don't even know much about 1D, but maybe that's for the best because I'm sure they got some stuff wrong lol
Overall, I also don't think the late-night show aesthetic really appeals to me personally. I think I always felt like late night shows were so distant from the type of content I watch (except for like, MAD on Cartoon Network? Which I don't think Smosh is aiming for lmao) and that has not changed at all lol. I also personally was never really a fan of the reunion videos -- they're definitely funny, but I never got excited for them because I don't watch reality TV. I think the appeal of a video or series doesn't just depend on whether it's funny or not, but also the overall brand and vibe.
But again, these are all MY PERSONAL OPINIONS. I do think I'm probably in the minority here, and I'll still watch the show going forward. Even if it doesn't really seem like my type of vibe. It's not like I hate it lol I'm just not crazy about it.
#smosh#bit city#also idk maybe the transitions between the segments could feel less slideshow-ish but that's such a nitpick#i do wonder how they develop the visual direction of series on youtube though.#sometimes when a visual brand is too involved with the content it comes across as corporate. but sometimes I want a lil bit of that lol#then again I think my content preferences are a little childish. I just mentioned MAD on Cartoon Network.
7 notes
·
View notes
Text
Computer Networking gives you so many good fantasy names. I'm naming my next character VLAN
11 notes
·
View notes
Text
Engineering Network Services
#engineering network services#network engineering it services#engineering services network#network engineering services#micro segmentation#network operations
12 notes
·
View notes
Text
Zero Trust Security: Strengthening Data Protection Strategies
Zero Trust Security: A Paradigm Shift in Cybersecurity
Enhance your cybersecurity posture with Zero Trust Security. Learn about its principles, benefits, and implementation strategies for proactive defense against evolving cyber threats.
Zero Trust Security has emerged as a groundbreaking approach in the realm of cybersecurity, challenging conventional notions of perimeter-based protection. In today's dynamic threat landscape, organizations are compelled to reevaluate their security strategies, prompting a paradigm shift towards a more proactive and adaptive defense mechanism.
Understanding the Concept of Zero Trust
Contrary to traditional security models that operate on the assumption of trust within the network perimeter, Zero Trust advocates for a skeptical approach. It mandates continuous verification of every user, device, and application attempting to access the network, regardless of their location or origin.
Principles of Zero Trust Security
The fundamental principles of Zero Trust revolve around the principles of least privilege, micro-segmentation, and strict access controls. By enforcing granular access policies and segmenting network resources, organizations can minimize the attack surface and mitigate the risk of lateral movement by malicious actors.
Implementation of Zero Trust Architecture
Implementing Zero Trust Architecture entails a holistic approach encompassing network segmentation, identity verification, and behavior analysis. Leveraging advanced technologies such as multifactor authentication (MFA) and encryption, organizations can establish a Zero Trust perimeter that adapts to evolving threats in real-time.
Benefits of Zero Trust Security
The adoption of Zero Trust Security yields manifold benefits, including enhanced threat visibility, improved compliance adherence, and reduced susceptibility to data breaches. By assuming a zero-trust stance, organizations can fortify their defense posture and safeguard critical assets from internal and external threats.
Challenges in Adopting Zero Trust Model
Despite its transformative potential, the adoption of Zero Trust poses several challenges, including complexity in implementation, legacy infrastructure constraints, and cultural resistance. Overcoming these hurdles requires a concerted effort, coupled with a strategic roadmap tailored to the organization's unique requirements.
Key Components of Zero Trust Framework
The Zero Trust framework comprises several key components, including continuous authentication, real-time threat intelligence, and adaptive access controls. By integrating these components into the security infrastructure, organizations can establish a dynamic defense ecosystem capable of thwarting sophisticated cyber threats.
Real-World Examples of Zero Trust Implementation
Numerous organizations across diverse industries have embraced Zero Trust Security to fortify their digital resilience and protect sensitive data assets. Case studies highlighting successful Zero Trust deployments underscore its efficacy in mitigating emerging cyber risks and preserving business continuity.
Zero Trust vs. Traditional Security Models
In contrast to traditional security models characterized by perimeter-centric defenses, Zero Trust embodies a proactive and context-aware approach. By scrutinizing every transaction and user interaction, Zero Trust mitigates the risk of insider threats and lateral movement, thereby enhancing overall security posture.
Importance of Identity and Access Management (IAM) in Zero Trust
Identity and Access Management (IAM) serve as the cornerstone of Zero Trust Security, facilitating secure authentication and authorization processes. By implementing robust IAM protocols, organizations can ascertain the legitimacy of user identities and enforce granular access controls across heterogeneous environments.
Zero Trust in Cloud Environments
Cloud environments represent a prime target for cyber adversaries, necessitating a Zero Trust approach to mitigate inherent risks. By implementing cloud-native security solutions and leveraging Zero Trust principles, organizations can mitigate data exposure risks and safeguard cloud workloads from unauthorized access.
Best Practices for Implementing Zero Trust Security
Successful implementation of Zero Trust necessitates adherence to best practices encompassing network segmentation, endpoint protection, and user behavior analytics. By embracing a Zero Trust mindset and fostering a culture of security awareness, organizations can bolster their cyber resilience and adapt to evolving threats.
Future Trends and Evolution of Zero Trust
The evolution of Zero Trust Security is marked by advancements in artificial intelligence, machine learning, and predictive analytics. As organizations embrace Zero Trust as a foundational principle, the paradigm will continue to evolve, ushering in a new era of proactive and adaptive cybersecurity defenses.
Conclusion: Embracing Zero Trust for Enhanced Security
In conclusion, Zero Trust Security represents a paradigm shift in cybersecurity, emphasizing the importance of continuous verification and strict access controls. By adopting Zero Trust principles, organizations can fortify their defense posture, mitigate emerging threats, and safeguard critical assets against evolving cyber risks.
Unique FAQs After The Conclusion
What distinguishes Zero Trust Security from traditional security models?
How does Zero Trust mitigate the risk of insider threats?
What role does identity and access management (IAM) play in Zero Trust?
Can legacy infrastructure be integrated into a Zero Trust architecture?
What are the key challenges associated with implementing Zero Trust Security?
#Zero Trust Security#Cybersecurity#Network Segmentation#Identity and Access Management#Cloud Security#Threat Intelligence#Data Protection#Insider Threats#Authentication#Access Controls
0 notes
Text
Project "ML.Satellite": Image Parser
In order to speed up the "manufacturing" of the training dataset as much as possible, extreme automation is necessary. Hence, the next step was to create a semi-automatic satellite multispectral Image Parser.
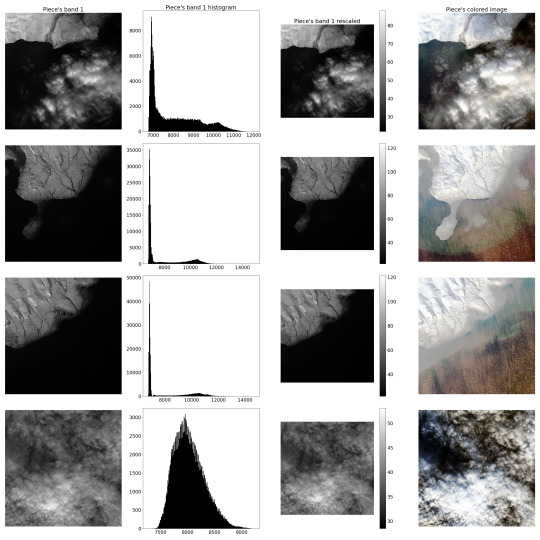
Firstly, it should carve the smaller pieces from the big picture and adjust them linearly, providing radiometrical rescaling, since spectrometer produces somewhat distorted results compared to the actual radiance of the Earth's surface. These "pieces" will comprise the dataset. It was proposed to "manufacture" about 400 such "pieces" in a 500 by 500 "pixels" format.
P.S.: Below are example images of the procedure described above. (Novaya Zemlya Archipelago)
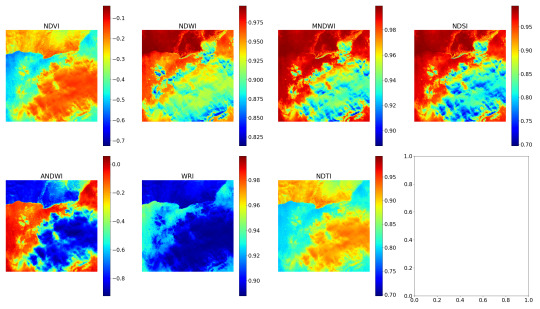
Secondly, it should calculate some remote sensing indexes. For this task, a list of empirical indexes was taken: NDVI, NDWI, MNDWI, NDSI, ANDWI (alternatively calculated NDWI), WRI and NDTI. Only several of them were useful for the project purposes.
P.S.2: The following are example images of the indexing procedure.
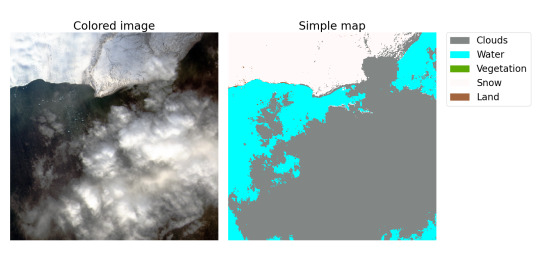
Lastly, it should compute the "labels" for the "pieces" describing a schematic map of the territory on image splitting this territory into several types according to the calculated indexes. To simplify segmentation, in our project, a territory can consist only of the following types: Clouds, Water (seas, oceans, rivers, lakes…), Vegetation (forests, jungles…), Snow and Land (this class includes everything else). And, of course, Parser should save the processed dataset and labels.
P.S.3: Below are sample image of a colored "piece" and a simple map based on the label assigned to this "piece". Map may seem a drop inaccurate and it's not surprising, since as far as I know, indexes are empirical and by definition cannot be precise. As a result, if it is possible to create a sufficiently accurate model that predicts analytical classification, then it may be possible to create a model that classifies optical images better than analytics.
#student project#machine learning#neural network#ai#artificial intelligence#computer vision#image segmentation#segmentation task#satellite#remote sensing#optical sensors#geoinformatics
0 notes
Text
youtube
#Breast cancer classification#deep learning#patch-based learning#histopathological images#5-B network#artificial intelligence#medical imaging#cancer diagnosis#convolutional neural networks#image segmentation#computer-aided diagnosis#multi-class classification#pathology AI#tumor detection#feature extraction#machine learning#healthcare AI#precision medicine#automated diagnosis#CNN model.#Youtube
0 notes
Text
the shingo honkowa story was neither bad nor good nor particularly interesting on the whole, but it did feel like it was made for shingo
(which it may have been, given that it's honkowa's 25th anniversary, goro is the main host, and there are rumors of shingo being in a drama series on the same network next year)
also, it's funny that everything he's been in for the past several years (except maybe anonymous? i remember so little of it idc) has involved him doing sloppy fight scenes. just throwing people around and getting slammed into things. even inu charlie had him punch a guy, and that was a soft romcom. it's like watching people get mauled by a giant teddy bear.
#but i do wonder if some roles are written with him in mind or if they just need a big endearing guy and he's the biggest name that fits#both feel equally plausible and there's the 3rd possibility that they change things after he signs on#also also idk if it's that big actors just do so much but i've noticed that networks seem to cast them in 2 things at once#like if they have a drama series or movie coming up then they'll also appear in a special drama or anthology not long before#and i assumed it was so folks would be primed to see said actors in the bigger production via the smaller budget production#(in the same way that the d.isney channel starts airing segments related to upcoming major releases about a year in advance)#anyway!! prayer circle for more shingo on our screens
0 notes
Text
Virtual Network Services Market: Forthcoming Trends and Share Analysis by 2030
Global Virtual Network Services Market size is expected to grow from USD 33.11 Billion in 2023 to USD 263.14 Billion by 2032, at a CAGR of 25.9% during the forecast period (2024-2032)
Virtual Network Services (VNS) refer to cloud-based or software-driven solutions that offer networking functionalities and services remotely over the Internet. These services are designed to enhance and optimize network operations by providing features such as routing, security, WAN optimization, and more without relying on physical infrastructure.
Virtual network services are used in many different industries. In the business world, VNS makes it possible for distant employees to connect securely and access company resources with ease. Additionally, it simplifies network administration, making it simpler to scale and more flexible to adjust to shifting business requirements. Within the telecommunications industry, virtual network services (VNS) allow service providers to provide their clients with innovative and reasonably priced services such as network function virtualization (NFV), software-defined wide-area networks (SD-WAN), and virtual private networks (VPNs).
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/4885
Updated Version 2024 is available our Sample Report May Includes the:
Scope For 2024
Brief Introduction to the research report.
Table of Contents (Scope covered as a part of the study)
Top players in the market
Research framework (structure of the report)
Research methodology adopted by Worldwide Market Reports
Leading players involved in the Virtual Network Services Market include:
Oracle Corporation (US), VMware LLC (US)Microsoft Corporation (US), Verizon Business (US), IBM Corporation (US), The Hewlett Packard Enterprise (US), Citrix Systems, Inc. (US), Lumen Technologies, Inc. (US), Cisco Systems, Inc. (US)
Moreover, the report includes significant chapters such as Patent Analysis, Regulatory Framework, Technology Roadmap, BCG Matrix, Heat Map Analysis, Price Trend Analysis, and Investment Analysis which help to understand the market direction and movement in the current and upcoming years.
If You Have Any Query Virtual Network Services Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/4885
Segmentation of Virtual Network Services Market:
By Type
On-premise
Cloud-based
By Application
Banking, Financial Services and Insurance (BFSI),
Public Sector
Healthcare
IT
Telecommunication
An in-depth study of the Virtual Network Services industry for the years 2023–2030 is provided in the latest research. North America, Europe, Asia-Pacific, South America, the Middle East, and Africa are only some of the regions included in the report's segmented and regional analyses. The research also includes key insights including market trends and potential opportunities based on these major insights. All these quantitative data, such as market size and revenue forecasts, and qualitative data, such as customers' values, needs, and buying inclinations, are integral parts of any thorough market analysis.
Market Segment by Regions: -
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
Key Benefits of Virtual Network Services Market Research:
Research Report covers the Industry drivers, restraints, opportunities and challenges
Competitive landscape & strategies of leading key players
Potential & niche segments and regional analysis exhibiting promising growth covered in the study
Recent industry trends and market developments
Research provides historical, current, and projected market size & share, in terms of value
Market intelligence to enable effective decision making
Growth opportunities and trend analysis
Covid-19 Impact analysis and analysis to Virtual Network Services market
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Acquire This Reports: -
https://introspectivemarketresearch.com/checkout/?user=1&_sid=4885
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assist our clients grow and have a successful impact on the market. Our team at IMR is ready to assist our clients flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, specialized in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyze extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Contact us:
Introspective Market Research
3001 S King Drive,
Chicago, Illinois
60616 USA
Ph no: +1 773 382 1049
Email: [email protected]
#Virtual Network Services#Virtual Network Services Market#Virtual Network Services Market Size#Virtual Network Services Market Share#Virtual Network Services Market Growth#Virtual Network Services Market Trend#Virtual Network Services Market segment#Virtual Network Services Market Opportunity#Virtual Network Services Market Analysis 2023
0 notes