Text
Driving Innovation: A Case Study on DevOps Implementation in BFSI Domain
Banking, Financial Services, and Insurance (BFSI), technology plays a pivotal role in driving innovation, efficiency, and customer satisfaction. However, for one BFSI company, the journey toward digital excellence was fraught with challenges in its software development and maintenance processes. With a diverse portfolio of applications and a significant portion outsourced to external vendors, the company grappled with inefficiencies that threatened its operational agility and competitiveness. Identified within this portfolio were 15 core applications deemed critical to the company’s operations, highlighting the urgency for transformative action.
Aspirations for the Future:
Looking ahead, the company envisioned a future state characterized by the establishment of a matured DevSecOps environment. This encompassed several key objectives:
Near-zero Touch Pipeline: Automating product development processes for infrastructure provisioning, application builds, deployments, and configuration changes.
Matured Source-code Management: Implementing robust source-code management processes, complete with review gates, to uphold quality standards.
Defined and Repeatable Release Process: Instituting a standardized release process fortified with quality and security gates to minimize deployment failures and bug leakage.
Modernization: Embracing the latest technological advancements to drive innovation and efficiency.
Common Processes Among Vendors: Establishing standardized processes to enhance understanding and control over the software development lifecycle (SDLC) across different vendors.
Challenges Along the Way:
The path to realizing this vision was beset with challenges, including:
Lack of Source Code Management
Absence of Documentation
Lack of Common Processes
Missing CI/CD and Automated Testing
No Branching and Merging Strategy
Inconsistent Sprint Execution
These challenges collectively hindered the company’s ability to achieve optimal software development, maintenance, and deployment processes. They underscored the critical need for foundational practices such as source code management, documentation, and standardized processes to be addressed comprehensively.
Proposed Solutions:
To overcome these obstacles and pave the way for transformation, the company proposed a phased implementation approach:
Stage 1: Implement Basic DevOps: Commencing with the implementation of fundamental DevOps practices, including source code management and CI/CD processes, for a select group of applications.
Stage 2: Modernization: Progressing towards a more advanced stage involving microservices architecture, test automation, security enhancements, and comprehensive monitoring.
To Expand Your Awareness: https://devopsenabler.com/contact-us
Injecting Security into the SDLC:
Recognizing the paramount importance of security, dedicated measures were introduced to fortify the software development lifecycle. These encompassed:
Security by Design
Secure Coding Practices
Static and Dynamic Application Security Testing (SAST/DAST)
Software Component Analysis
Security Operations
Realizing the Outcomes:
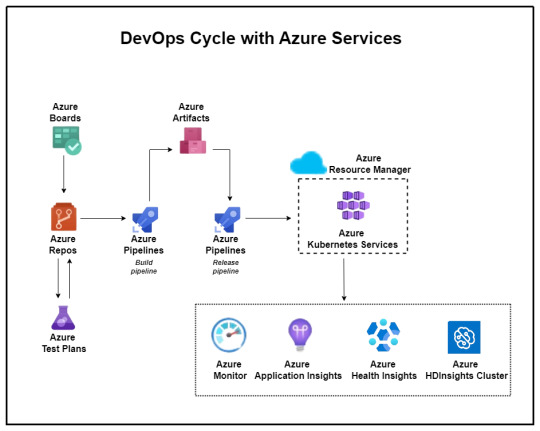
The proposed solution yielded promising outcomes aligned closely with the company’s future aspirations. Leveraging Microsoft Azure’s DevOps capabilities, the company witnessed:
Establishment of common processes and enhanced visibility across different vendors.
Implementation of Azure DevOps for organized version control, sprint planning, and streamlined workflows.
Automation of builds, deployments, and infrastructure provisioning through Azure Pipelines and Automation.
Improved code quality, security, and release management processes.
Transition to microservices architecture and comprehensive monitoring using Azure services.
The BFSI company embarked on a transformative journey towards establishing a matured DevSecOps environment. This journey, marked by challenges and triumphs, underscores the critical importance of innovation and adaptability in today’s rapidly evolving technological landscape. As the company continues to evolve and innovate, the adoption of DevSecOps principles will serve as a cornerstone in driving efficiency, security, and ultimately, the delivery of superior customer experiences in the dynamic realm of BFSI.
Contact Information:
Phone: 080-28473200 / +91 8880 38 18 58
Email: [email protected]
Address: DevOps Enabler & Co, 2nd Floor, F86 Building, ITI Limited, Doorvaninagar, Bangalore 560016.
#BFSI#DevSecOps#software development#maintenance#technology stack#source code management#CI/CD#automated testing#DevOps#microservices#security#Azure DevOps#infrastructure as code#ARM templates#code quality#release management#Kubernetes#testing automation#monitoring#security incident response#project management#agile methodology#software engineering
0 notes
Text
Firewall Friday: Network Security - Protecting Your Network from Threats
Welcome to Firewall Friday, where we dive into the exciting world of network security with a touch of humor and relatable analogies. In this edition, we’ll explore the importance of network security and how firewalls act as the guardians of your network, protecting it from potential threats. Get ready to embark on a hilarious and informative journey as we use common analogies, playful emojis, and…

View On WordPress
#access control#brute force attacks#data encryption#employee education#firewall#hackers#intruders#intrusion prevention#multi-layered defense#network protection#network security#packet inspection#patch management#security incident response#spoofing
0 notes
Text
Looking back I feel like the Disney employees probably should have reacted more strongly to the prison gates that got installed at employee entrances
#that's shaped like a joke but i watched that change happen#also i suspect that some undisclosed security incident happened that this was a response to#but i still feel like there probably was a better way to do that
2 notes
·
View notes
Text
I'm looking forward to packing up to move so much!! and then opening it all again there where I end up and setting up my home 😊 I'm not someone who likes unpacking after a trip, but when it's your whole home going somewhere new and exciting, I feel like it's different. I'm saying goodbye to so many things I don't need anymore, or never needed, and for the first time in my life getting to choose exactly what's going to be in my space, with an actual budget for things I need or even just want, and nobody else to impede me bring in their own stuff. ahhh it took so many years to get to this point but I can't wait!!!
#and I was very happy to come to this place too#for the majority of my time here I've been very pleased#I still remember my excitement when I learned we had a bathtub#I hadn't had a bathtub in my dorm so I felt like we were in luxury#and truly. despite the roaches and the blinds and the breakin#it's been a very reasonable apartment#with a responsive manager#there's tons of space. the floors are gorgeous. in-unit washer and dryer#even my aunt and uncle have to go to the basement for that in their fancy complex#a big room for me. a decent kitchen. came with a microwave. and fairly clean#great location. and despite the one incident. actually very secure#but in my new place I can host!!!! I can spread out!! use the bathroom whenever!! get a kitty cat!!#bake!! come home noisily at all hours! not tiptoe in the mornings!! play music!! be free!!#I'm so excited for my family and friends to visit :3#mutuals this means you too!! come to the east coast!#and this is a new renovation so hopefully my cousin can come without her allergies acting up#my aunt and uncle have hosted so many times I would be so happy to return the favor#cor.txt
2 notes
·
View notes
Text
Top Cyber Insurance Policies: Finding the Right Coverage for Your Needs
In today’s digital landscape, businesses of all sizes are increasingly vulnerable to cyber threats. From data breaches to ransomware attacks, the repercussions of cyber incidents can be devastating, leading to financial loss, reputational damage, and legal consequences. As a result, cyber insurance has emerged as a crucial component of risk management for organizations. This article will guide you through the top cyber insurance policies available, helping you find the right coverage for your specific needs.

Understanding Cyber Insurance
What is Cyber Insurance?
Cyber insurance is designed to protect businesses from the financial repercussions of cyber incidents. This includes coverage for data breaches, network failures, and other cyber-related risks. Policies typically cover costs associated with incident response, legal fees, regulatory fines, and even business interruption.
Why is Cyber Insurance Important?
Financial Protection: Cyber incidents can lead to significant costs, including legal fees, customer notification, and credit monitoring. Cyber insurance can help mitigate these expenses.
Compliance: Many industries have specific regulatory requirements regarding data protection. Cyber insurance can help businesses comply with these laws.
Reputation Management: A data breach can severely damage a company’s reputation. Insurance can provide resources for public relations efforts to manage the fallout.
Key Coverage Areas in Cyber Insurance Policies
When evaluating cyber insurance policies, it’s important to understand the various coverage areas they may include:
1. Data Breach Coverage
This coverage addresses the costs associated with a data breach, including customer notification, credit monitoring services, and legal fees.
2. Network Security Liability
This protects against claims resulting from unauthorized access to a company’s network, including attacks like DDoS (Distributed Denial of Service) and malware infections.
3. Business Interruption
Cyber incidents can disrupt operations. This coverage compensates for lost income and additional expenses incurred during the downtime.
4. Cyber Extortion Coverage
This covers ransom payments and associated costs in the event of a ransomware attack.
5. Regulatory Coverage
This provides coverage for fines and penalties resulting from regulatory investigations or lawsuits related to data breaches.
6. Media Liability
This protects against claims arising from online content, such as copyright infringement or defamation.
Top Cyber Insurance Policies
Let’s explore some of the top cyber insurance policies available in the market today. Each of these policies has distinct features and benefits, making them suitable for different types of businesses.
1. Chubb Cyber Enterprise Risk Management
Chubb offers a comprehensive cyber insurance policy that caters to businesses of all sizes. Their coverage is designed to address a wide range of cyber risks.
Key Features:
Extensive data breach coverage.
Cyber risk assessment tools.
Access to a network of cybersecurity experts for incident response.
Best For: Medium to large enterprises looking for robust coverage and expert support.
2. AIG CyberEdge
AIG’s CyberEdge policy provides tailored coverage options, making it suitable for various industries.
Key Features:
Coverage for first-party and third-party costs.
Incident response services included.
Risk management resources to help prevent incidents.
Best For: Organizations seeking customizable coverage that aligns with their specific risk profile.
3. Travelers Cyber Insurance
Travelers offers a cyber insurance policy that combines coverage for data breaches and cyber liability with proactive risk management services.
Key Features:
24/7 incident response support.
Coverage for business interruption and data recovery.
Access to cybersecurity training resources.
Best For: Businesses that value proactive risk management alongside traditional coverage.
4. Beazley Breach Response
Beazley specializes in cyber insurance and offers a unique approach with their Breach Response policy, focusing on incident response.
Key Features:
Comprehensive first-party coverage for data breaches.
Access to forensic experts for breach investigation.
Coverage for public relations efforts post-breach.
Best For: Organizations that want a strong focus on incident response and management.
5. CNA Cyber Liability Insurance
CNA’s policy is designed for small to medium-sized businesses, offering essential coverage at an affordable price.
Key Features:
Coverage for data breaches, cyber extortion, and network security.
Risk assessment and training resources included.
Tailored packages based on industry needs.
Best For: Small businesses looking for budget-friendly, essential coverage.
How to Choose the Right Cyber Insurance Policy
Selecting the right cyber insurance policy for your business involves several critical steps:
1. Assess Your Risks
Before shopping for a policy, conduct a thorough risk assessment to identify your vulnerabilities. Consider factors such as the nature of your business, the types of data you handle, and your current cybersecurity measures.
2. Understand Your Coverage Needs
Determine which coverage areas are essential for your organization. Consider whether you need extensive data breach coverage, business interruption protection, or other specific types of coverage.
3. Compare Policies
Request quotes from multiple insurers and compare the coverage options, limits, and exclusions. Look for policies that offer the best value for your specific needs.
4. Consult with Experts
Engage with a cybersecurity expert or an insurance broker specializing in cyber insurance to help you navigate your options. They can provide valuable insights and recommendations.
5. Review and Update Regularly
Cyber threats are constantly evolving, and so are your business needs. Review your policy regularly and update it as necessary to ensure you have adequate coverage.
Conclusion
Cyber insurance is a vital component of modern business risk management. As cyber threats continue to evolve, having the right coverage can make all the difference in your ability to respond to incidents effectively. By understanding the key coverage areas, exploring top policies, and following best practices for selection, you can find the right cyber insurance policy to protect your organization. Prioritize your cybersecurity strategy today, and ensure your business is equipped to face the challenges of tomorrow’s digital landscape.
0 notes
Text
0 notes
Text
Achieving NIST and DORA Compliance: How We Can Help Companies Build Cybersecurity and Operational Resilience
In today’s fast-paced digital environment, cybersecurity and operational resilience are at the forefront of corporate priorities. With the increasing frequency of cyberattacks and strict regulatory requirements, companies must adapt and align with internationally recognised frameworks and regulations such as the National Institute of Standards and Technology (NIST) and the Digital Operational…
#AIO compliance solutions.#AIO Legal Services#AML compliance#business continuity#corporate governance#cyber risk mitigation#cybersecurity framework#data protection#digital security#DORA compliance#EU Regulations#GDPR compliance#ICT risk management#incident response#legal services for businesses#NIST compliance#operational resilience#regulatory compliance#risk management#third-party risk management
0 notes
Text
#CrowdStrike Incident Response#How CrowdStrike Transformed Incident Response#CrowdStrike Security Solutions#Impact of CrowdStrike on Incident Response#CrowdStrike Cybersecurity Innovations#CrowdStrike and Modern Incident Response#Incident Response with CrowdStrike#CrowdStrike Threat Detection#CrowdStrike Security Platform Benefits#CrowdStrike Cyber Defense Strategy
0 notes
Text
🍻
#you know they never told me when i started working hospitality ten years ago that I'd end up acting as a first responder so often#cant stop thinking about an incident today where i sat with someone through the aftermath of a seizure#and helped them feel safe and respected and maintain their dignity only to be told off for not kicking them out of the oub immediately afte#its insane how often i get deputised to help security with an incident have to take point because theyre scared to do anything#and then get criticised for my approach#employer send me through first response training challenge#also stop being weird and hostile about disabled people challenge#anyway. the world keeps turning and people keep being deserving of patience and grace and dignity.#my thoughts
1 note
·
View note
Text
Elephant Raids FCI Warehouse in Chakulia, Sparks Panic
‘Ramlal’ breaks into rice storage, later damages temple wall Forest department’s quick response team drives away wild tusker after night of chaos JAMSHEDPUR – A wild elephant, locally known as ‘Ramlal’, broke into a Food Corporation of India (FCI) warehouse in Ward No. 10 of Chakulia on Friday night, causing panic and damage. The tusker broke through the main gate of the FCI compound and targeted…

View On WordPress
#जनजीवन#Chakulia elephant raid#elephant population Chakulia#FCI warehouse damage#food storage security#forest department quick response#human-elephant conflict Jharkhand#Jharkhand wildlife incidents#Life#Nagababa temple damage#Ramlal elephant Jamshedpur#wildlife management East Singhbhum
0 notes
Text
New MOVEit transfer vulnerabilities that require patching (2024) - CyberTalk
New Post has been published on https://thedigitalinsider.com/new-moveit-transfer-vulnerabilities-that-require-patching-2024-cybertalk/
New MOVEit transfer vulnerabilities that require patching (2024) - CyberTalk


EXECUTIVE SUMMARY:
Remember last year’s MOVEit meltdown? Get ready for a reprise…
For anyone who missed last year’s madness, MOVEit Transfer is a popular managed file transfer product sold by Progress Software, which provides business applications and services to more than 100,000 organizations globally.
In 2023, the software code for the MOVEit Transfer product was found to contain multiple vulnerabilities, leading to a rash of ransomware attacks, and data exposure for thousands of organizations.
The level of business exploitation was so severe that it impacted the results of this year’s “Data Breach Investigations Report” (DBIR) from Verizon.
Earlier this month, Progress Software contacted users about two high-severity vulnerabilities, CVE-2024-5805 and CVE-2024-5806. Both are categorized as authentication bypass-style vulnerabilities. Each one has been assigned a 9.1 severity score.
To allow adequate time for patching, the information was under embargo until June 25th. This appears to have been a wise move, as just hours after being made public, at least one vulnerability is seeing active exploit attempts in the wild.
The Shadowserver Foundation has detected exploitation efforts that hone in on honeypot systems, in particular.
The new bugs
“To be clear, these vulnerabilities are not related to the zero-day MOVEit Transfer vulnerability we reported in May 2023,” said a Progress Software spokesperson.
CVE-2024-5806 is an improper authentication vulnerability in MOVEit’s SFTP module, which can potentially lead to authentication bypass in some instances.
Cyber security researchers have noted that this CVE could be weaponized to “impersonate any user on the server.”
CVE-2024-5805 is another SFTP-associated authentication bypass vulnerability, which affects MOVEit Gateway version 2024.0.0.
Action items
As a cyber security leader, have your team check on whether or not your MOVEit Transfer software is up-to-date. Patches are available for all vulnerabilities.
Communicate to your team that these vulnerabilities are a priority, as they have serious business implications. If patching hasn’t yet been completed, emphasize the importance of patching quickly. After patching, confirm successful implementation.
Additional considerations
Reassess your organization’s vulnerability to ransomware attacks. Take a layered approach to cyber security and consider additional cyber security measures. You might want to invest in proactive processes like vulnerability assessments and red teaming. In addition, review and update your incident response plan, as to address potential MOVEit Transfer exploitation attempts. Further information
As compared to the MOVEit Transfer exposure numbers from last year, experts say that the numbers appear similar – the geographies and networks where MOVEit Transfer is observed also mirror those of the 2023 incident.
See CyberTalk.org’s past MOVEit Transfer coverage here. Get more insights into software supply chain vulnerabilities here.
Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#2023#2024#analyses#applications#approach#Articles#authentication#breach#bugs#Business#business applications#code#cyber#cyber attack#cyber security#cyberattack#data#data breach#Foundation#incident#Incident Response#insights#it#leadership#module#MOVEit#MOVEit Transfer#networks#newsletter
0 notes
Text
Developing an Access Control Policy: Key Elements to Include
Access control is a crucial part of the security structure of an organization. This system makes sure that only people who are given permission can access certain resources, protecting sensitive information from being used by those without permission. Also, access control prevents possible breaches, which are actually more common than most believe. 38% of decision-makers in different organizations state that they have boosted their security measures after a breach, which is a good number overall, showing awareness for access control in businesses of different scopes and sizes.
When creating an access control policy, businesses or decision-makers must plan it well and ponder over many things. Below, we discuss a few key elements to include when creating an effective access control policy.
Define Roles and Responsibilities
The first part of creating an access control policy is to determine the roles and duties in your organization. This means finding out who needs access to what information and resources. When you categorize your workers by their jobs, it can simplify granting access to resources. Also, this helps make sure that only people who need access for a specific task are allowed in.
Additionally, using role-based access control (RBAC) is a good method for handling user access. RBAC lets you give permissions to roles instead of people, making it easier to manage who can do what. This way of managing access improves safety and also makes things more efficient when bringing in new workers or switching roles within an organization.
Regularly Review and Update Access Rights
Check if access rights are still suitable for each user's role. By doing periodic reviews, you can locate and remove unnecessary permissions which reduces the possibility of unauthorized entry. These evaluations should occur no less than once a year or when there is a substantial alteration in an employee's duties or the structure of the organization.
Also, automated tools for access management can make access reviews more efficient and accurate. These tools assist in finding accounts that are not linked to any user, excessive permissions given to a person, and other security dangers. They help with fixing these issues quickly.
In this context, it is vital to include proper identity governance administration (IGA) solutions. In essence, IGA systems, which manage identities and control access according to rules, form a complete method. They combine identity governance with identity administration, providing improved functionality. These systems are particularly useful for auditing purposes and fulfilling compliance needs.
Implement Strong Authentication Mechanisms and Establish Access Monitoring and Logging
Creating an access control policy is very important for safeguarding delicate information. Important parts are forming and describing roles, using strong methods for authentication such as multi-factor authentication (MFA), and regularly updating these techniques to handle changing risks.
Monitoring and keeping records of access activities is crucial for noticing and dealing with security incidents. Constant monitoring means paying attention to who uses what data, at what time, and from where. This aids in recognizing uncommon or unapproved entry habits that might imply a security violation.
Keeping careful records of access activities can assist in forensic inquiries if a security event happens. These logs need to have data like user IDs, times of access, what was accessed and the actions executed. They should be stored safely and reviewed frequently to follow the access control policy.
Develop a Robust Incident Response Plan
Security incidents can happen even with good prevention. So, it's important to prepare a strong incident response plan. This ensures your organization is ready to react fast and well in case of security breaches. The plan should describe the roles everyone has in case of a breach, how people are informed of the incident, as well as what actions need to be taken to restore functionality and normalcy.
Regular drills and training sessions for the incident response team are important to make sure they are ready to handle incidents. These exercises must imitate various breaches and give chances for members of the group to rehearse their tasks in a controlled setting.
In Conclusion
Developing an access control policy is a basic part of protecting an organization's important information and resources. By setting up roles and duties, putting in place good authentication methods, creating access observation and recording, often checking over and changing access rights, as well as making a strong response plan for incidents, organizations can create a safe environment that reduces the chances for unauthorized entry while improving general security posture.
Regular updates and continued improvement of the access control policy are necessary to adjust to changing threat scenarios as well as guarantee the continuous safeguarding of crucial assets.
Share in the comments below: Questions go here
#access control#security structure#sentitive information#security measures#safeguarding information#multi-factor authentication#incident response plan
0 notes
Text
Guard Against Financial Frauds as Data Leakage Becomes Rampant: Insights from RBI Officials
In an era where digital transactions and online banking have become the norm, safeguarding financial information has never been more critical. The Reserve Bank of India (RBI) officials recently highlighted the increasing threats of financial fraud due to rampant data leakage. This blog post delves into the nuances of this pressing issue and offers strategies to protect your financial data. The…

View On WordPress
#Cyber-attacks#Cybersecurity#Data leakage#Digital transactions#Encryption methods#Financial data protection#Financial fraud#financial institutions#Identity theft#Incident response plan#Phishing scams#RBI officials#Security audits#Two-factor authentication#Vulnerability assessments
0 notes
Text
House Votes to Advance Bill That Could Ban TikTok in the U.S.
Legislation Passed: The House voted in favor of a bill that could lead to a ban on TikTok in the US unless ByteDance sells it to an American company. Senate Expectations: The bill, now heading to the Senate, is expected to pass there as well. Security Concerns: US politicians have security concerns over TikTok’s data sharing with the Chinese government, given ByteDance’s obligations. Potential…

View On WordPress
#access control#AI News#automated incident response#bytedance#cayman#cybersecurity#data collection#data security#douyin#ethical AI#house bill#identity management#model security#national security#News#red teaming#threat detection#tiktok#vulnerability assessment
0 notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
1 note
·
View note
Text
How to Protect Your Business From Cyber Threats
Cybersecurity is a major topic every business owner should be discussing. Here is some info from FRC that we hope helps.
Imagine we’re sitting down over a cup of coffee, and you’ve just asked me how to shield your trucking business from the ever-looming shadow of cyber threats. It’s a digital age dilemma, but I’m here to walk you through some straightforward strategies to bolster your defenses. First off, let’s talk about the elephant in the room: cyber threats. They’re not just a problem for the tech industry;…

View On WordPress
#access control#antivirus software#cloud storage#cyber attacks#cyber threats#cybersecurity#cybersecurity laws#data protection#digital transformation#employee training#encryption#firewalls#incident response#legal compliance#malware#network security#password policies#phishing attacks#ransomware#secure communication#software updates#trucking industry#vendor security#VPN
0 notes