#authentication protocols
Explore tagged Tumblr posts
Text
Subnet Sunday: Authentication - Proving Your Identity on the Network
Welcome to Subnet Sunday, where we unravel the mysteries of authentication in a fun and humorous way. In this edition, we’ll take you on a journey through the colorful world of proving your identity on the network. Using relatable analogies, playful emojis, and a touch of wit, we’ll demystify authentication and make it accessible for novice readers. So, get ready to don your digital passport and…

View On WordPress
#access control#authentication#authentication methods#authentication protocols#best practices for authentication#biometric authentication#multi-factor authentication#network dance floor#network security#password security#proving identity#two-factor authentication
0 notes
Text
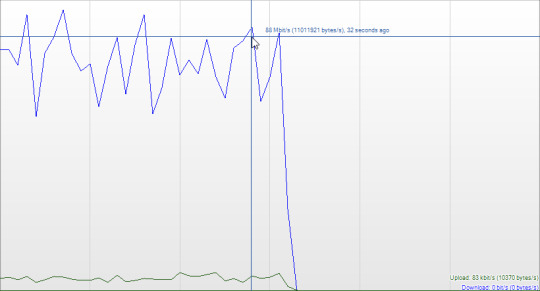
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
Secure AI-driven enterprises with identity management, MFA & zero trust. Unlock the best security framework for generative AI today!
#Generative AI Implementation#Evolution of AI Agents#Multi-factor Authentication#Generative AI Applications#Implementing Zero-Trust Security Protocols
0 notes
Text
Secure AI-driven enterprises with identity management, MFA & zero trust. Unlock the best security framework for generative AI today!
#Generative AI Implementation#Evolution of AI Agents#Multi-factor Authentication#Generative AI Applications#Implementing Zero-Trust Security Protocols
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Advanced Security Measures for Virtual Office Spaces
Introduction
As more companies embrace the concept of virtual office spaces, ensuring the security of digital operations has become a top priority. Cybersecurity threats are constantly evolving which means virtual office environments need to adopt advanced security measures to protect sensitive data, maintain business continuity, and ensure compliance with regulations. Let’s explore some of the key strategies businesses should employ to secure their virtual office spaces.
1. Multi-Factor Authentication (MFA)
One of the most effective ways to secure virtual office platforms is through multi-factor authentication. MFA requires users to verify their identity using two or more authentication factors such as passwords, biometric data, or one-time codes sent via email or SMS. This adds an extra layer of protection by making it difficult for cybercriminals to gain unauthorized access, even if they have obtained the user’s login credentials.
2. End-to-End Encryption
Encryption ensures that data transmitted between users, systems, and applications remains secure by converting it into unreadable code. End-to-end encryption is particularly important for virtual office spaces, where sensitive information such as client details, business plans, or intellectual property may be shared. This security measure guarantees that only the intended recipients can access the information, even if it’s intercepted during transmission.
3. Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are an essential security measure for employees working remotely. VPNs encrypt internet connections, protecting the data transmitted between employees and the company’s virtual infrastructure. By masking the user’s IP address and ensuring a secure connection, VPNs help prevent unauthorized access and minimize the risk of cyberattacks, especially when using public Wi-Fi networks.
4. Regular Software Updates and Patching
Keeping software up to date is a fundamental yet often overlooked security practice. Cybercriminals frequently exploit vulnerabilities in outdated software to launch attacks. Virtual office systems, collaboration tools, and cloud-based platforms should always run the latest versions with security patches applied. Automatic updates can ensure that systems remain protected against newly discovered threats without relying on manual intervention.
5. Zero Trust Architecture
The Zero Trust security model operates on the principle of "never trust, always verify." This approach assumes that every user, device, and connection is potentially compromised and requires authentication and verification at each step. Implementing Zero Trust within virtual office environments ensures that access to sensitive data and systems is continuously monitored, and only authorized individuals are granted access.
6. Data Loss Prevention (DLP) Tools
Data Loss Prevention (DLP) solutions help monitor and control the flow of sensitive information within an organization. These tools prevent data breaches by identifying, flagging, and stopping unauthorized attempts to send, share, or store confidential information. DLP is particularly valuable in virtual office environments, where employees may be more susceptible to accidental data leakage due to remote working conditions.
7. Employee Security Training
Human error remains one of the most significant vulnerabilities in cybersecurity. Regular training on security best practices, including recognizing phishing scams, avoiding unsecured networks, and safely handling company data, is crucial for all employees. By creating a security-conscious culture, businesses can reduce the likelihood of breaches caused by employee mistakes.
8. Cloud Security Protocols
Since virtual offices often rely on cloud-based services for collaboration and data storage, it’s vital to implement robust cloud security measures. This includes selecting a reputable cloud service provider that offers advanced security features such as encryption, data redundancy, and detailed access controls. Additionally, businesses should implement custom security policies that align with their specific needs to safeguard cloud-stored information.
Conclusion
As virtual office spaces become the norm, businesses must stay ahead of potential security threats. Implementing a combination of advanced technologies like MFA, VPNs, encryption, and Zero Trust, alongside educating employees about cybersecurity, is critical to maintaining a safe and secure digital workspace. By adopting these security measures, companies can protect their data, ensure compliance, and build trust with their clients.
0 notes
Text
IDWTBAMG CHARACTER FUN FACTS
Well, some fun facts and mostly lore or character relationship stuff. Under the cut!
AIKA
Aika became the next Star Guardian at age 13. She’s 15 now
Aika’s want to help people and relentless positivity were part of the reason she was chosen to be the Star Guardian: Guardian of the Stars in the first place. While her love for the job has fizzled out, this aspect of her character still a core part of her.
She’s very kind and gentle person but that kinda goes out the window when magical duties are brought into the equation
Her and Hoshi care about one another but their relationship is currently a bit tense. They’re usually pretty quick to make jabs at one another
She struggled to get used to the platform shoes in her magical girl outfit
She LOVES food. And her eyes are usually way too big for her stomach leading to many a food coma
Aika and her teammates worked in secret for the most part, not really being allowed to “exist in the real world”. Because of this, with the free time she had, Aika would read a lot (she’s actually very book smart)
Aika loves extreme sports and is an adrenaline junky. However, rollercoasters freak her out for some reason
Aika drags Zira into lots of new eperiences. Zira usually ends up appreciating the experiences after the fact
Aika’s a morning person
ZIRA
Zira is smart but doesn’t apply herself in school
They have a lot of artistic interests, particularly art, music and fashion
She likes the idea of writing fanfiction in theory but writing’s sooooo much work. Any ideas she has just kinda live in her head, causing her to zone out and daydream a ton
While shy for the most part, Zira can be very blunt and isn’t necessarily a pushover
Prior to Aika, she didn’t have a lot (any) friends at school but she’s mostly content doing her own thing
They’d hang out in Miss’ classroom a lot, either to show her Moon Sailor stuff against her will or just to have lunch
Zira loves playing video games and especially loves visual novels
Zira develops a crush on Aika pretty quickly. Aika’s kindness, authenticity and bravery is inspiring to Zira. Also Aika’s the only other person her age to really give her the time of day. And also she thinks Aika’s pretty
She thinks Hoshi’s really cool and since Aika doesn’t particularly enjoy talking about her job, Zira usually goes to Hoshi for magical girl questions. Initially Hoshi doesn’t trust Zira with that information but is really flattered to have someone who looks up to them and is interested in everything they have to say. So they indulge when appropriate.
Zira’s a night owl
HOSHI
Hoshi saved Aika when she was really young and has kept her safe ever since
Hoshi and Aika started off kind of like siblings but Hoshi then became her boss, making their relationship a bit strained and more complicated
Their role as a magical mascot managerial in nature. They make Aika and her team do their jobs, follow protocol, teach them how to use their powers, keep up morale, do timecards, etc.
While Hoshi oversees this team, their responsibility is primarily to the Star Guardian
Hoshi, much like Aika, used to be really chipper and a bit more goofy but Aika’s kinda worn them down overtime
Hoshi’s not a fan of Earth, but in an effort to better understand Aika’s feelings, tries out being a human and doing Earth activities
Hoshi takes a while to get used to their human form. They’re really clumsy in it
They have a hard time making hands for their human form. Their hands are slightly different every time but equally terrifying. They eventually get better at making them though.
Hoshi doesn't use their human form too much. Most people just assume their Aika's weird pet bird
Hoshi doesn't need to eat but discovers they enjoy the act of eating
ECLIPSE
Eclipse is one of the few humans that know that Aika and the other magical girls exist
He met Aika pretty early on in her magical girl career and he was immediately enamored with her
Since finding about magical girls, he’s obsessively tried keeping track of them, leading him to start acting out in order to get their attention. They only really care because he knows their secret and they play along
He and Devoid made his current outfit together. DeVoid wanted to make it black but Eclipse was set on making it very bright and showy
Eclipse currently resides with DeVoid. He gets on her nerves sometimes but they both do care about each other
Eclipse is a pretty good cook
Eclipse isn’t particularly hateful but he’s really got beef with Zira for some reason
It’s hard to tell if Eclipse is really in love with Aika or if he just loves the concept of their nonexistent relationship
Eclipse has a lovely singing voice
His real name is Elio
LADY DeVOID
DeVoid was banished to space by a Star Guardian. For a LONG time she lived (unconsciously) as a sort of celestial being that would spit out monsters that the Star Guardians for many generations would have to face. While not ideal it was better than fighting DeVoid before she got to full power.
DeVoid finally wakes up in the present timeline, with no memories other than being banished by a Star Guardian and wanting revenge and knowing that she’s supposed to be able to create monsters. Unfortunately for her, she doesn’t remember how to use her powers. She doesn’t even remember her name, so she came up with “Lady DeVoid”
DeVoid loves human reality TV. Specifically competition shows. She loves how petty and evil people become. This is also where most of her knowledge of humans comes from
Though DeVoid is pretty stoic, her ears are very expressive
DeVoid taught Eclipse how to do his makeup
She really likes Eclipse’s cooking
When she’s out and about she’s usually wearing sunglasses because it’s simply too bright for her
DeVoid does have to work a normal job in the human world and simply goes by “Dee”
After being in the cold, dark reaches of space and since coming to Earth, DeVoid has grown to love soft things
People rarely question her appearance (because that’s just rude). But when people do ask what’s up with her horns she just says “it’s a condition” and that’s usually enough for people to just end the convo there.
MISS
Miss loves her job more than anything. She’s a very accomplished teacher and takes a lot of time to make sure all of her students succeed
Miss cares about Zira a lot. Always staying in her classroom just in case Zira wants to stop by for lunch, giving her advice or giving her extra tutoring as needed
Because of Zira, Miss has become a closet Moon Sailor fan
Though Aika’s just started attending school, she and Miss have bonded quite a bit. Aika’s positive disposition and cheeriness bring Miss a lot of joy
Miss keeps her personal life (not that she really has one) out of work but finds herself opening up a little more than she’d like to Aika and Zira
Miss used to get really antsy during summer breaks, leading her to start teaching summer school to fill the time
Her workaholic nature was the reason for her and her ex-wife’s divorce
Miss has gone on one date since her divorce. The idea of having starting over is exhausting to her so she’s mostly okay just being single
Miss doesn’t really like coffee but she drinks a lot of it out of necessity
Miss has a ton of tattoos
6K notes
·
View notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
VPN – The Next-Generation

One of the most rapidly evolving technologies in the field of data security online privacy is the Virtual Private Network (VPN). VPNs have been in existence for many years but are now entering what can be considered their next generation of solutions. These innovative advancements are designed to enhance the capabilities and functionality of VPNs, making them even more secure and effective in protecting user data.
Next-generation VPN solutions build upon the traditional concept of VPNs by incorporating new technologies to further improve privacy, speed, and accessibility. These solutions are being developed to address the increasing need for protection against sophisticated cyber threats and growing concerns surrounding data privacy.
One major development in next-generation VPN solutions is the integration of advanced encryption protocols. Traditional VPNs rely on protocols like Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Forwarding Protocol (L2TP) to establish secure connections. However, next-generation solutions are shifting towards more robust protocols like OpenVPN and IPsec, which offer superior encryption and authentication mechanisms. These protocols ensure that user data remains encrypted and protected from unauthorized access while in transit.

Another crucial aspect of next-generation VPNs is the inclusion of advanced security features. These features often include multi-factor authentication, intrusion detection systems, and malware protection. By implementing these additional layers of security, next-generation VPN solutions provide users with an added level of assurance that their online activities are safeguarded against potential threats.
Next-generation VPNs also aim to address concerns related to speed and performance. Traditionally, VPNs have been associated with reduced internet speeds due to the encryption and routing processes involved. However, new technologies such as Split Tunneling and WireGuard are being integrated into VPN solutions to mitigate these issues. Split Tunneling allows users to selectively route internet traffic through the VPN, enabling faster browsing speeds for non-sensitive activities. WireGuard, on the other hand, is a lightweight encryption protocol that offers faster connectivity and improved performance.
Moreover, next-generation VPN solutions are focusing on increased accessibility and ease of use. This means developing intuitive and user-friendly software interfaces that make setting up and managing VPN connections simpler for individuals with limited technical expertise. Additionally, the proliferation of VPN apps for various devices and operating systems ensures that users can access VPN services across a wide range of platforms, including desktops, laptops, smartphones, and tablets.

In conclusion, next-generation VPN solutions are integrating new technologies to provide enhanced privacy, security, speed, and accessibility.
With advanced encryption protocols, improved security features, and innovative performance enhancements, these next-gen VPNs are poised to offer users a superior level of data protection in an increasingly interconnected world. As cyber threats evolve, the constant evolution of VPN technology remains crucial in ensuring the privacy and security of online communications.
#vpn#next-gen VPNs#VPN#cyber threats#cyber security#VPN solutions#next-generation VPN solutions#multi-factor authentication#Tunneling Protocol#Layer 2#(L2TP)
0 notes
Text
The Mini Guide to Crafting Compelling Royal Characters for Fiction Writers
Creating royal characters can be both exciting and challenging. These regal figures often play pivotal roles in stories, capturing readers' imaginations with their power, privilege, and the weight of responsibility they carry. Whether you're writing historical fiction, fantasy, or contemporary novels featuring monarchs, this comprehensive (mini) guide will help you develop authentic, multi-dimensional royal characters that will resonate with your readers.
Understanding the Basics of Royalty
Before diving into character creation, it's essential to have a solid grasp of what royalty entails. Royalty typically refers to members of a ruling family, including kings, queens, princes, princesses, and other nobles within a monarchical system. These individuals are often born into their roles, though some may ascend to power through marriage or other means.
Key aspects to consider:
Hierarchy and succession
Royal duties and responsibilities
Protocol and etiquette
The concept of divine right (in some cultures)
The relationship between royalty and their subjects
Remember, while these elements are common in many royal systems, you have the creative freedom to adapt or reimagine them for your fictional world.
Developing Your Royal Character's Background
Every character, royal or not, needs a rich backstory. For royal characters, this background is particularly crucial as it shapes their worldview, values, and decision-making processes.
Consider the following:
a) Lineage: What is your character's family history? Are they from a long-standing dynasty or a newly established royal house?
b) Upbringing: How were they raised? Were they groomed for leadership from birth, or did they have a more sheltered upbringing?
c) Education: What kind of education did they receive? Was it formal, focusing on statecraft and diplomacy, or more well-rounded?
d) Relationships: How do they relate to their family members, courtiers, and subjects?
e) Personal experiences: What significant events have shaped their character and outlook on life?
Crafting a Unique Personality
Avoid the trap of creating one-dimensional royal stereotypes. Your character should be as complex and nuanced as any other well-developed protagonist or antagonist.
Consider these aspects:
a) Strengths and weaknesses: What are your character's admirable qualities? What flaws do they struggle with?
b) Motivations: What drives them? Is it a sense of duty, personal ambition, or something else entirely?
c) Internal conflicts: What personal struggles do they face? How do these conflicts affect their rule and relationships?
d) Hobbies and interests: What passions do they pursue outside of their royal duties?
e) Sense of humor: How do they express humor, if at all? Is it dry wit, sarcasm, or something else?
Balancing Power and Vulnerability
One of the most intriguing aspects of royal characters is the juxtaposition between their immense power and their human vulnerabilities. This balance can create compelling internal and external conflicts for your character.
Consider:
The weight of responsibility and its impact on their personal life
The isolation that often comes with a royal position
The constant scrutiny they face from the public and court
The struggle between personal desires and duty to the crown
Creating a Believable Royal World
Your royal character doesn't exist in a vacuum (I hope not). They're part of a larger royal ecosystem that includes family members, advisors, courtiers, and subjects. Developing this world adds depth and authenticity to your story.
Key elements to consider:
Court dynamics and politics
Relationships with other noble houses or kingdoms
The role of advisors and how they influence decisions
Traditions and customs specific to your royal setting
The economic and social structure of the kingdom
Addressing the Challenges of Royal Life
Royal characters face unique challenges that can drive your plot and character development. Some common themes include:
a) Succession disputes b) Balancing personal happiness with duty c) Navigating political alliances and conflicts d) Managing public opinion and maintaining legitimacy e) Dealing with threats to their rule or life
Use these challenges to create tension and drive your story forward while revealing more about your character's personality and values.
The Impact of Historical Context
If you're writing historical fiction or a fantasy inspired by real-world monarchies, it's crucial to consider the historical context. Research the time period and culture you're drawing from to ensure authenticity in your character's behavior, beliefs, and challenges.
Key areas to research:
Social norms and expectations of the time
Political systems and power structures
Technology and its impact on governance
Religious beliefs and their influence on royalty
Gender roles and how they affect royal duties and succession
Avoiding Common Pitfalls
When creating royal characters, be mindful of these common mistakes:
a) Making them too perfect or too villainous b) Ignoring the realities of royal life (e.g., lack of privacy, constant duties) c) Overlooking the impact of their decisions on their subjects d) Failing to show growth or change over the course of the story e) Relying too heavily on stereotypes or clichés
Incorporating Royal Etiquette and Protocol
Royal characters often adhere to strict codes of conduct and protocol. While you don't need to become an expert in royal etiquette, incorporating some of these elements can add authenticity to your story:
Forms of address (Your Majesty, Your Highness, etc.)
Court ceremonies and rituals
Dress codes and regalia
Rules of precedence in social situations
Diplomatic protocols when interacting with other royals or dignitaries
Exploring Different Types of Royal Characters
Remember that not all royal characters need to be ruling monarchs. Consider exploring other royal roles, such as:
The rebel prince or princess who rejects their royal duties
The reluctant heir thrust into power unexpectedly
The exiled royal fighting to reclaim their throne
The royal spouse adapting to life in the palace
The illegitimate child discovering their royal heritage
Each of these archetypes offers unique storytelling opportunities and challenges for character development.
Balancing Historical Accuracy and Creative License
If you're writing historical fiction featuring real royalty, you'll need to strike a balance between historical accuracy and creative interpretation. While it's important to respect known facts and timelines, you also have the freedom to explore the inner lives and motivations of these historical figures.
Tips for balancing accuracy and creativity:
Thoroughly research the historical figure and their time period
Clearly differentiate between historical fact and fictional interpretation
Use author's notes to explain any significant departures from known history
Focus on filling in the gaps in the historical record rather than contradicting established facts
Developing Royal Character Arcs
Like any well-rounded character, your royal protagonist should undergo growth and change throughout your story. Consider how their experiences might challenge their beliefs, alter their perspective, or force them to confront their flaws.
Possible character arcs for royal characters:
From naive idealist to pragmatic ruler
From reluctant heir to confident leader
From isolated monarch to connected leader who understands their subjects
From power-hungry tyrant to benevolent ruler (or vice versa)
Remember, character growth doesn't always have to be positive. Sometimes, the most compelling stories involve characters who face moral decline or tragic falls from grace.
Remember, while the trappings of royalty may be grand, at their core, your royal characters are still human. They love, fear, hope, and struggle like anyone else. It's this humanity, set against the backdrop of power and responsibility, that makes royal characters so fascinating to read and write about.
Happy writing, - Rin T
Hey fellow writers! I'm super excited to share that I've just launched a Tumblr community. I'm inviting all of you to join my community. All you have to do is fill out this Google form, and I'll personally send you an invitation to join the Write Right Society on Tumblr! Can't wait to see your posts!

#writing#creative writing#thewriteadviceforwriters#writing tips#writers block#writeblr#how to write#writers and poets#writers on tumblr#on writing#royalcore#royalty#romance writing#writing advice#writing blog#writing guide#writing inspiration#writing ideas#writing reference#writing resources#writing software#writing tools#writer#writing life#writing help#writing community#writing characters#novel writing#fiction writing#writing a book
2K notes
·
View notes
Note
Riddle x reader where reader is an ABSOLUTE NERD about Alice in Wonderland and so she's utterly obsessed and fascinated with Riddle and he's just utterly FLUSTERED over all the attention 😭😭😭
RIDDLE X READER
Where you're obsessed with Alice in Wonderland
Where in your dimension you were an Alice in Wonderland nerd, and upon arriving in NRC, you discover you're watching the humanized Queen of Hearts, Riddle…

You had already made peace with the fact that you were the biggest Alice in Wonderland nerd on this plane of existence.
Your room (in your dimension) was littered with vintage editions of the book, tea sets inspired by the Mad Tea Party, and a growing collection of Heart Queen fanart.
So, when you ended up in NRC and discovered that Heartslabyul was a dorm based on your favorite fictional world ever—you nearly passed out.
But none of that compared to meeting Riddle Rosehearts.
He was real. The Heart Queen in human boy form.
And the first time he scolded a student for painting the roses the wrong shade of crimson—you actually squealed.
“Did you just—did you really say that?” you gasped, stars in your eyes.
Riddle paused, halfway through yelling at Ace. “...Yes?” he replied slowly, confused by your excitement.
“OH MY GOD. That was so accurate. You’re literally perfect. Do you realize you’re, like, the embodiment of Wonderland authority?? I could cry right now.”
Ace snorted. “Please don’t encourage him, you’re gonna make it worse for us.”
But Riddle? He was frozen. Bright red. And utterly stunned.
“...Perfect?? Embodiment of-Wonderland authority? What in Twisted—?”
You nodded seriously, grabbing his hand with all the gravity of someone speaking to royalty.
“Riddle. You are my Queen of Hearts. And I have never been so happy.”
If he had been red before, now he was absolutely crimson.
“I-!” he stammered, flailing slightly. “This kind of excessive praise is unnecessary—!”
“You have no idea how long I’ve dreamed of having tea with the Queen of Hearts,” you continued, beaming.
“Do you also scream ‘off with their heads’ when you’re mad? Wait, don’t tell me—do it during tea. Please. I want the full authentic experience.”
Riddle covered his face with a gloved hand, groaning softly.
“Off with your head is my UM, not a game nor...-” he muttered.
“Why you of all people have to be so—so enthusiastic…”
“I brought scones!” you said brightly, pulling a box out of your bag. “And I made them in the shape of hearts. Because obviously.”
Riddle peeked through his fingers. His face was a warzone of flustered red and reluctant fondness.
“You’re utterly incorrigible,” he said, voice shaking. “And absolutely out of order.”
You grinned. “So you’ll join me for tea?”
He turned his head, muttering something about "disrupting schedules" and "breaking protocol"—but you noticed how he didn't actually say no.
#twisted one shot#twst x reader#twisted x reader#twisted wonderland x reader#riddle#riddle rosehearts#riddle x yuu#riddle x reader#riddle rosehearts x yuu#riddle rosehearts x reader#riddle rosehearts x oc#alice in wonderland#twisted one shots#twst one shots
460 notes
·
View notes
Text

🖤🔐 Leather & Mastery | Andy. ⛓️
The art of control isn't about force-it's about trust forged in restraint, devotion sealed in sweat, and power exchanged with purpose.
About Me:
• Dominant | Leather Master | Sir/Daddy.
• Protocol, discipline, and the sacred craft of power exchange.
• My kinks/focuses: Rigger, service dynamics, Old Guard traditions.
What You'll Find Here:
🔥 Thoughtful dominance & the philosophy of control
🕵️♂️Leather culture appreciation | Gear |
Rituals
⛓️💥Optional: "Occasional brat taming" or other humor
Rules of Engagement:
Respect, consent, and authenticity above all.
Submissives: Know your place. (Or learn it.)
Curious? Ask—but read the pinned post first.
DMs: Open for thoughtful questions.
Unsolicited play begs for punishment.
#gay art#gay couple#gay guy#gay love#gay man#gay men#gay pride#bdsmrelationship#bdsmdominant#alpha beta omega#alpha master#alpha man#alpha muscle#mensfashion#leather dom#sub/dom#bd/sm master
229 notes
·
View notes
Text
"Hotel Reverie": A heartbreaking simulation of Love and Grief
(Spoilers ahead)

In its seventh season, Black Mirror quietly delivered what may be one of its most emotionally devastating and thematically rich episodes to date: Season 7, episode 3: “Hotel Reverie.”
On the surface, it seems to echo the show’s usual motifs—technology, simulation, AI, identity. But beneath its layers, its grayscale glamour and eerie premise lies something far more intimate: a queer love story about agency, performance, memory, and the ache of loving something that was never supposed to be real.
And it’s this contrast—between what is scripted and what is felt—that gives Hotel Reverie its haunting, aching brilliance.
The episode follows Brandy Friday, a Black actress who, despite her fame, is creatively stifled and emotionally detached from the roles she’s typecast into. She craves something deeper, something immortal—a performance that doesn’t just live on screen but lives in the hearts of those who witness it. She mentions all time classics like Casablanca and so much more.
That opportunity comes in the form of a film company rebooting Hotel Reverie, a 1940s romantic classic, if I remembered it correctly. Through advanced AI-simulation technology, they don’t recreate the film around Brandy but instead they drop her inside it. Fully immersed, Brandy’s consciousness becomes the character Alex Palmer, while the simulation populates itself with ultra-realistic AI versions of the original cast, including the tragic female lead, Clara, played by a synthetic version of late film icon Dorothy Chambers. The catch was Brandy never received the full briefing or protocol, she didn't know it would be unrealistically real...She didn't know Clara would feel so human and she certainly didn't expect to fall in love.
The episode is about technology, yes but more than that, it's about the quiet war between authenticity and performance, and how queer love is often forced to live between the two.
Clara, the AI was built from Dorothy’s old performance tapes as Clara and Dorothy drew it from her life, her emotions was based on her own sorrow and experiences. It is initially just that. It was meant to be just a performance. Graceful, poetic, timeless. But as Brandy begins making off-script choices, the AI system starts to destabilize. Clara begins to glitch. And what was once a program begins to feel like a person—one whose every emotion is bleeding through from the long-lost heart of Dorothy Chambers herself.
Dorothy, we learn in implication, was a queer woman living in the 1940s, an actress who died tragically, quietly. She never got to live a truthful life, never got to love openly. Instead, she buried her feelings inside her most iconic role: Clara. That role is now AI-coded into the simulation, which means that Clara’s love is built from Dorothy’s pain.
Brandy, meanwhile, begins as an outsider. She doesn’t believe in the simulation. She doesn’t even trust the reality of what she’s seeing. Her performance is half-hearted, her delivery flat. But it’s not poor acting, it’s intentional distance. Brandy is, after all, an actress. She’s learned to hold herself back, to keep her identity just outside the camera’s reach.
Until Clara starts going off script. Until Clara starts looking back at her.
That’s when Brandy stops acting. That’s when she starts feeling.

One of the most emotionally complex and narratively brilliant choices of Hotel Reverie makes is the uncertainty surrounding Clara's memory after the reset. After Brandy wakes up and hears the team calling her back to reset the scorpion scene. And this was after everything they’ve been through, the weeks they spent together in the simulation, the moments of genuine intimacy and self-discovery—Clara is returned to a point in the story before it all happened. And Clara reappears right before her very eyes, just as she was at the beginning and Clara was looking at her saying "My heart is pounding like a drum". Same intonation, Same staging. But for Brandy, it was no longer the same. For Brandy's case, since she's real human, her mind, everything was intact. The uncertainty of that scene was purely haunting and magical at the same time. What happens next is subtle. Brandy hesitates and she doesn't say her line right away. She studies Clara's face... her eyes. Searching for something.
Is it her?
Is she still in there?
Clara seems confused by Brandy's reaction but only just. Not like someone who has no memory, but like someone who feels something just beneath the surface and can't explain why. It's eerily familiar, like a love that exists without memory.
The dilemma, as someone who was now at this point fully invested with the story, I felt anxious too, constantly I was asking questions in my mind "Does she remember?" "Does she know?"
For me, I know she was reset but I think... deep inside her, she knows. A part of her remembers.
Clara’s behavior after the reset—her tone, her reluctance to meet Brandy’s eyes, the strange weight behind her words, it all hints at something deeper.
She says:
“I’m a married woman. I can’t… I shouldn’t be feeling this way.”
And it fits the script, but it also feels like a double meaning. As if she’s not just speaking as Clara the character… but as someone who remembers what happened and doesn’t know why she remembers.
There’s a moment when she looks at Brandy and her eyes shimmer—not with confusion, but with something that feels like grief. Like she knows what’s coming. Like she’s trying not to break the character, what she was asked to, what she's supposed to do as an AI.
Here’s where it gets even more tragic, and brilliant. I personally think it’s not Clara who remembers but Dorothy?
Clara is a simulation. She was a role. But she was built on the emotional DNA of Dorothy Chambers, the woman who once played her. A woman who lived a closeted life. The person who loved someone she could never be with. Who poured that heartbreak into the character of Clara.
When Brandy calls her “Dorothy,” the AI begins to shift, to change. The simulation becomes porous. Clara, for the first time, begins to feel the real woman beneath the code.
So even if Clara was reset, even if the AI has been reprogrammed—the echo of Dorothy Chamber's grief still lives inside her. And the love, once it's truly felt, is not easily erased.
So maybe... Clara doesn't remember the events, but her heart remembers something. Even if she doesn't know why Brandy suddenly feels like home.

But that's just my wishful thinking. The audience is meant to feel conflicted. It's meant to feel like we're stuck between two truths. 1. Clara is a simulation who has been reset and 2. Clara is a soul who fell in love and never truly forgot. That unresolved ache? that invisible string still pulling Brandy and Clara together even as the worlds resets is what makes the story so devastatingly human.
Because love isn't always about memories, sometimes it's about feeling something you can't explain.
And in the moment when Clara says "You must go" with eyes that know too much. Me as someone who witnessed their story unfold, realizes something terrible. That maybe Clara does remember...maybe she chooses to let Brandy go anyway. To protect her. Just like Dorothy once didn't get the chance to.
Another aspect of the story that truly haunts me was how Clara AI perceived Brandy in the beginning. In the simulation, Brandy was meant to play the role of Alex Palmer- a male, white doctor. The simulation was coded to present her to the world of the film as Alex: male, charming, heterosexual, traditionally heroic.
Brandy was in theory, masked, her body present, her identity hidden by the lens of the 1940s characters perception. But that never truly held. Not for Clara.
Despite the programming, despite the simulated environment, despite the rigid gender roles of the time, Clara sees Brandy. Not as a man, Not as Alex. Not as a character to perform with. She sees her essence, her spirit and the actor/person beneath.
As the story progresses, the romantic dynamic deepens between the two. In a story rooted in artifice, programming, gender coding and simulation, the heart cuts through all of it. Their story was shaped by presence, connection and truth. In the end, Clara doesn't say "I love you, Alex", she says, "I love you" and this was unmistakably addressed to Brandy, and she means it. And this was even after the reset.

Another thing to point out is, how much has been said about Issa Rae’s portrayal of Brandy—some calling it too subdued, too passive. But this criticism misunderstands the core of Brandy’s character.
Issa Rae plays Brandy as a woman trained to survive the industry by not feeling too much. Her detachment is not a lack of chemistry, but a shield. She enters the simulation not as a lover or a believer but as a professional, dropped into a role without context or rehearsal. She was expecting to meet fellow actors to establish connection and rapport with fellow humans. That's how acting and filming goes normally. But that isn't the case here, and because of that, she plays Alex Palmer with hesitation, with irony, with cynicism.
But slowly, that mask begins to slip.
It starts with stolen glances. Quiet awe. Little expressions of disbelief—In her mind she's probably thinking “She’s just code. Why does it feel like more?”
Rae’s restraint becomes her weapon. When the final breakdown comes when Clara is reset and no longer remembers her—Rae doesn’t explode in melodrama. She crumbles in silence. It’s not theatrical. It’s real. And it hits so much harder because of everything she held in before. She was slapped by the unfortunate and harsh truth, that everything is artificial. It's not real.
Her final delivery of “I’ll be yours forevermore”, the line she’s been waiting to say the entire film lands like a funeral vow. It's not for the camera.
It's for the woman lying dead in her arms. the one she spent endless nights, weeks, months with. The woman she fell in love with.

And then there's Emma Corrin, Emma Corrin’s performance is surgical in its softness. They play Clara with the kind of grace and vulnerability that feels too perfect at first—a fantasy of the golden age of cinema. But that’s the point. Clara is an AI. They were immaculate from the very beginning. They were playing a programmed AI designed to be seductive, poetic, elegant and timeless. Clara wasn't confused; she was supposed to follow the original movie's narrative. She was on script.
Clara isn’t supposed to feel. She isn’t supposed to change.
But as Brandy veers off script, Clara begins to show cracks. She slowly gives a smile that lingers too long. Eyes that start searching for answers to questions she was never supposed to ask. Corrin manages to convey an AI that is accidentally learning how to want.
Clara's whispered “I love you” is delivered not like a confession, but like a discovery. Like a glitch in her own programming. And the way she touches Brandy’s face, as though she’s trying to memorize something that’s already slipping away? It was not scripted; it was something sacred.
The part where she starts to grasp memories from Clara's data pool, and Dorothy's life. I was bawling. She saw fragments of her life; the applause, the movie sets, the fake smiles, the closeted love and the loneliness of being adored by millions by known by no one.
Clara felt everything and Corrin was amazing to convey such emotions in the screen. Clara saw how Dorothy was trapped in gold, wealth and fame around her like silk-lined shackles- a life where everyone wanted her, but no one ever truly saw her. And the worst part, Clara realizes she's living the same life again, inside the simulation, a role she was never meant to question. It's devastating because it says so much about how people tend to romanticize women like her; write their suffering as elegant, preserve their tragedy in HD, but never ask "What did she want?" , "Did anyone ever let her choose?"
And when Corrin delivered the line " I was born in a cage. I should die in a cage", it was so haunting and achingly beautiful at the same time because Clara was aware, and she wanted to do something Dorothy never could. Like she inherited the ending Dorothy never escaped. But she wants to end it in her own way, her own terms and not by following any script.
Corrin doesn't just play Clara. They play Dorothy, too—still trapped inside the role, finally reaching out from decades of silence, begging not to be forgotten again.
And the tragedy is—she is. and dare I say, Emma Corrin deserves at least a nomination for this role.
Hotel Reverie is not just a sci-fi romance. It is a commentary on the cost of performing for the world and the quiet revolution of being seen anyway.
Clara was never meant to feel. Brandy was never meant to care. Dorothy was never meant to be remembered for her love.
But through Brandy’s choices, through Clara’s awakening, through Issa Rae’s restraint and Emma Corrin’s vulnerability, this story became more than just a film inside a film. It became a ghost story, a love letter and a tragedy.
A reminder that even in simulated spaces, Love is always real and forgetting it is the true heartbreak.
What Hotel Reverie does without making a spectacle of it—is something profound: Despite placing its characters inside a 1940s simulation, a time riddled with racial tension, misogyny, and queer oppression, the episode refuses to make those elements the point of pain.
Brandy, a Black woman. Clara, a white woman born from a 1940s film role. Two women. Two identities that would have been considered scandalous even to be in the same room romantically during that era—
And yet? Their love is not questioned. Not framed as political. Not punished for its optics.
There is no scene where Brandy’s race is mocked or tokenized. There’s no line of dialogue explaining why Clara’s AI programming “accepts” her. There is no moment where the gender of their relationship is pointed out as deviant.
It just exists.
And that is so, so rare. In a world of stories that center conflict around identity—in which being queer or being a person of color is the obstacle to overcome—Hotel Reverie offers something revolutionary because it lets love be the center. It's not about the struggle, the scandal, the justifications.
Brandy's identity is present and it's the core of her whole personality, but it does not define her worthiness to be loved. Clara's identity too, is not a reflection of purity or acceptability. She is not the symbol of 'ideal femininity." She is a construct who becomes real. 'It's not a queer love in a time that forbids it" it's just two souls who were never meant to meet but finding each other anyway. Because when the world falls away, when time, rules, programming and expectations crumble,
Love is just love.
It doesn't need to be explained.

170 notes
·
View notes
Note
Do you know any good sources for burn scar care?
I’m writing a character who was burned in a spaceship crash. The story is set several years after the fact, and I want to incorporate that detail into the story. What would a burn scar care routine look like?
Hey!
I generally recommend medical websites for this kind of stuff. There are tons of information readily available online, especially about things as common as a burn injury. Phoenix Society for Burn Survivors or MSKTC can be helpful for you.
While caring for a burn scar will be different for everyone (there's many types, degrees, plus just individual differences between burn survivors themselves) some of the things that you can include;
Burnt skin doesn't produce its own oils, so it gets dry. It needs to be moisturized, oil-based products (think coconut or grape seed oil) are often used. The heavier the lotion, the fewer times a day it needs to be applied.
Massaging a scar, especially when it's relatively new. It can be a massage, but stretching or just putting pressure on it is part of that too. It helps the skin from becoming extremely sensitive. Initially you do it delicately, but after the scars are matured it's fine (or recommended even) to put some force into it. This loosens them up.
Itching is a huge issue. Both massaging and moisturizing help with that, but if it's still causing problems then there are medications that could provide some relief.
Protecting the skin from the sun. All year, including cloudy weather. Sunblock, big hats, sunglasses if needed, all that. This applies to people with darker skin as well because the skin loses its pigment after a burn (it can sometimes come back but it's definitely not a guarantee).
Avoiding the heat. A lot of burn survivors will have problems with temperature regulation because burns damage the sweat glands, so they overheat faster. There's nothing burn-specific here, same protocol as for avoiding a heatstroke - drink water and keep out of the sun.
Wearing softer and looser clothing. Rough and tight clothes can cause blisters, and that is a Problem. Inappropriate materials could also induce more itching.
Taking pain meds. Chronic pain is common, so your character might need medication.
I definitely wouldn't say that this is an exhaustive list, but I think it's a good start. If you need more details, I think the resources linked above should work.
I'm glad to see people interested in burn scars being a disability that requires a lot of care rather than seeing it as a solely visual thing. Makes it much more authentic.
I hope this helps,
mod Sasza
475 notes
·
View notes
Text
Writing Notes: Police Procedural

Police Procedural - a subgenre of detective fiction that focuses on police work and investigations.
This form of crime fiction is popular across a variety of mediums, including mystery novels, TV series, and films.
In police procedurals, the lead characters seek to solve a crime—most commonly a murder mystery.
Stories in this subgenre typically follow law enforcement officers or private investigators as they track down criminal suspects.
Depending on the detective story, the plot may revolve around crimes of passion or serial killers.
How to Write a Police Procedural
Research police protocols. To learn about proper police procedures, interview police officers and, if possible, go on a ride-along with your local police department. To avoid becoming overwhelmed with research, define the length of time you want to devote to this phase. Setting a timeline of a few weeks or months can help relieve the pressure of needing to know everything before you start writing.
Develop your main character. Determine whether your protagonist is a seasoned homicide detective or an amateur detective. Depending on the scope of your story, your main character may work with a local police force or a government agency like the FBI. Establishing a backstory will also help you determine their worldview and how they approach their work.
Choose a familiar setting. Police procedurals are deeply influenced by their specific settings. Choose a setting that you’re familiar with—whether rural, urban, or suburban—and use your knowledge of this place to infuse the world of your story with authenticity.
Outline a crime plot. Police procedurals are often plot-driven. Devise a complex and surprising crime to center your story around.
Define the tone. Although many police procedurals take a realistic and gritty approach with their tone, you can decide for yourself whether your story is best suited for comedic elements, dramatic elements, or a combination of both.
Write your first draft. Once you’ve laid out a plan for your police procedural, dive into your first draft. Avoid putting pressure on yourself to make it perfect and instead focus on simply finishing a rough draft.
Step away from your first draft. Once you’ve completed your first draft, take some time away from the work—ideally a few weeks—so you can return to it with fresh eyes.
Revise your draft. Try different approaches to self-editing to find one that works for you. For example, try printing out your script or novel or reading the work aloud. Once you have a shareable draft, consider sending it to a reader with knowledge of police procedures for feedback.
Examples of Police Procedurals
To learn more about police procedurals, explore some of these examples in TV and fiction.
Dublin Murder Squad (2007–2020) by Tana French: This book series follows various Irish detectives as they investigate harrowing murders.
CSI: Crime Scene Investigation (2000–2015): Over the course of 15 seasons, this iconic TV show followed a task force in Las Vegas dedicated to solving a wide variety of crimes. The series was so popular it prompted several spinoff shows including CSI: Miami and CSI: NY.
87th Precinct (1956–2005) by Evan Hunter: Influenced by the classic TV show Dragnet, Evan Hunter (who often wrote under the pen name Ed McBain) published this long-running book series that followed a group of detectives in New York City. The books were later adapted into a TV series.
Law & Order (1990–2010): Inspired by real-life crimes, each episode in this police procedural TV series follows both the police investigation and legal trial of a different case.
Bosch (2014–2021): Based on Michael Connelly’s bestsellers, this cop show follows a detective who works for the Hollywood Division of the LAPD.
Source ⚜ More: Notes ⚜ Writing Resources PDFs ⚜ Detective Story
#police procedural#crime#detective#writeblr#literature#writers on tumblr#writing tips#writing reference#dark academia#spilled ink#creative writing#writing prompt#fiction#genre#writing advice#light academia#writing inspiration#writing ideas#writing resources
94 notes
·
View notes
Text
Safeguarding Data Privacy and Security in Virtual Work Environments in Ernakulam
Introduction
In today’s increasingly digital world, virtual work environments have become the norm for many organizations. While these platforms offer flexibility and efficiency, they also bring significant challenges in maintaining data privacy and security. This blog post explores essential strategies to protect sensitive information in virtual work settings and ensure compliance with data protection regulations.
1. Understanding the Risks in Virtual Work Environments: Virtual work environments, while convenient, are vulnerable to various cyber threats, including data breaches, phishing attacks, and unauthorized access. Employees may work from different locations, often using personal devices and unsecured networks, which increases the risk of data leaks. Understanding these risks is the first step toward building a secure virtual workspace.
2. Implementing Strong Authentication Protocols: One of the most effective ways to enhance security in virtual work environments is by implementing robust authentication protocols. Multi-factor authentication (MFA) should be mandatory for accessing company resources. MFA adds an extra layer of security by requiring users to provide two or more verification factors, reducing the likelihood of unauthorized access.
3. Securing Communication Channels: Virtual work often relies on communication tools such as video conferencing, instant messaging, and email. To protect sensitive information, it’s crucial to use encrypted communication channels. End-to-end encryption ensures that only the intended recipients can access the data, safeguarding it from eavesdropping or interception by malicious actors.
4. Regularly Updating Software and Systems: Outdated software and systems are common targets for cyberattacks. Ensure that all software, including operating systems, applications, and security tools, is regularly updated. Patching vulnerabilities as soon as updates are available is critical to prevent exploitation by cybercriminals.
5. Educating Employees on Cybersecurity Best Practices: Human error is a leading cause of data breaches. Educating employees on cybersecurity best practices is essential in creating a secure virtual work environment. Regular training sessions should cover topics such as recognizing phishing attempts, creating strong passwords, and securely handling sensitive information.
6. Implementing Data Encryption: Encrypting data both at rest and in transit is a fundamental security measure. Data encryption converts information into a secure format that can only be read by someone with the decryption key. This ensures that even if data is intercepted, it remains unreadable to unauthorized users.
7. Monitoring and Auditing Access to Data: Regular monitoring and auditing of data access are crucial in detecting suspicious activity. Organizations should implement logging mechanisms to track who accesses data and when. Any unusual patterns or unauthorized access attempts should be promptly investigated to mitigate potential threats.
8. Establishing Clear Data Handling Policies: Clear data handling policies should be established and communicated to all employees. These policies should outline the procedures for storing, sharing, and disposing of sensitive data. Employees should be aware of the consequences of non-compliance, emphasizing the importance of adhering to the guidelines.
9. Ensuring Compliance with Data Protection Regulations: Organizations must comply with data protection regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Understanding and implementing the requirements of these regulations is essential in avoiding legal penalties and maintaining customer trust.
10. Leveraging Secure Cloud Services: Many organizations rely on cloud services to store and manage data in virtual work environments. It’s important to choose cloud providers that prioritize security and offer features such as data encryption, regular backups, and compliance with industry standards. Additionally, access to cloud services should be tightly controlled and monitored.
Conclusion
As virtual work environments continue to evolve, so do the challenges of maintaining data privacy and security. By implementing the strategies outlined in this post, organizations can create a secure virtual workspace that protects sensitive information and minimizes the risk of data breaches. Prioritizing data security not only safeguards the organization’s assets but also builds trust with clients and stakeholders in an increasingly digital world.
0 notes