Don't wanna be here? Send us removal request.
Text
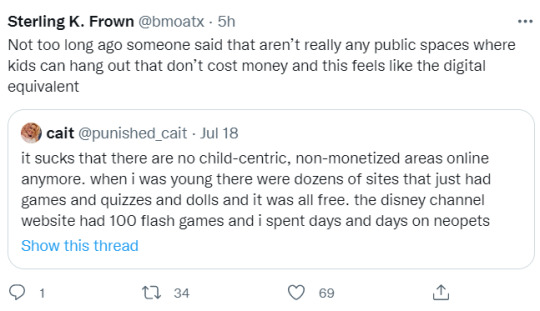
002 Social Media's Silent, Yet Loud, Gaze
The previous discussion doesn’t necessarily account for people experiencing these effects on platforms where their connections are more personal. However, the surveillance dynamics within personal relationships are equally worthy of exploration. Social groups—family, friends, and others—are often forced to share a singular digital space, leading to context collapse. This collapse heightens anxiety as users navigate how they are perceived by multiple groups simultaneously, which can breed mistrust even within the closest of relationships. Particularly, users will analyse interactions on platforms like Instagram, where personal connections are more pronounced than on free-for-all platforms like Twitter. They may approach each interaction with excessive detail, falling into the trap of over-interpretation. For example, someone not responding to a comment or viewing a story without engaging might be perceived as a deliberate act. These ambiguous actions can easily manifest into darker thoughts if not counteracted. What users may not understand is that these actions might simply be a case of social overload or simply nothing. Such behaviours are so inconsequential to others that the outcome as stated is not even considered in the realm possibility. Yet, for the person overanalysing, these perceived slights can feel significant and deeply personal.
This tendency to overanalyse digital interactions is symptomatic of the broader challenges from social media. Platforms amplify even the most minor behaviours, making them feel significant in ways they aren't. This heightened sensitivity can distort our understanding of social dynamics, turning neutral or benign things into something larger. These interpretations then spiral, creating unnecessary tension in both digital and offline spaces. In a world mediated by digital platforms, the lines between connection, observation, and judgment have become marred. Social media has created a unique space where users must navigate an interplay of visibility, validation, and vulnerability. The resulting anxiety, paranoia, and mistrust can deeply impact how we view ourselves and our relationships. Recognising these dynamics so we can reclaim a healthier relationship with these platforms is key. Ultimately, the question we must ask is: How much of our digital anxiety is self-imposed, and how much is engineered by the platforms we use?
#social media#panopticon effect#algorithmic anxiety#digital surveillance#modern anxiety#soft life#soft tech
0 notes
Text
001 Social Media's Silent, Yet Loud, Gaze
"I lied, y'all—delete your Instagram. Everybody on there is plotting, watching, and doesn’t like you. Start over."
Over the past few years, I’ve seen several iterations of this same tweet or sentiment. It got me thinking about whether there are any studies or phenomena that explore how social media contributes to anxiety and hyperawareness due to its borderline surveillance nature. This particular tweet might seem like a throwaway comment, but I think it speaks to larger issues that don’t yet have precise language to describe them. It captures a perfect intersection of social media anxiety, paranoia, and hyper-surveillance. Our digital platforms today almost act as courtyards, and by nature, environments where users feel constantly observed. Likes, comments, and views quantify this, making it feel all the more real and measurable. Whether these metrics tell the full story is a different matter entirely. Nonetheless, users exist in a heightened state of awareness regarding their audience. That audience watches, and a quiet part of our minds tells us that watching is inevitably followed by judgment. This dynamic fosters self-censorship, hyper-vigilance, and anxiety. For some, the mere idea of an audience that closely monitors behaviour can be a source of great stress.
If we want to circle back to theory, this phenomenon could loosely tie into the panopticon effect. In the panopticon model, prisoners in a courtyard are under constant observation from a central watchtower, whether or not guards are actively watching. Similarly, social media creates the feeling of being perpetually observed by an invisible audience, even if no one is engaging with you. Unlike the prisoner-guard relationship, however, this surveillance is two-way; users are both watchers and watched. They are an actor in the very same structure they repel. These dynamics seem to go unnoticed, or the self-absorption takes precedence, making the dots difficult to connect. The new age of Elon Musk’s Twitter (post-2022) exacerbates this phenomenon. The loss of a personal timeline, and by extension, the loss of key interactions one may have had previously, the introduction of a "For You" page filled with content antithetical to you (said to be intentional to boost engagement through discord), and the emergence of tiered experiences via premium features have fundamentally altered the platform’s social dynamics. What once felt like a communal courtyard now feels distant and fragmented, amplifying feelings of disconnection. This shift feeds into what can be termed algorithmic anxiety. Unaware to many who may be experiencing such, social media algorithms prioritise specific interactions, such as engagement driven by controversy or outrage. However, when more seemingly normal content is given centre stage, it can amplify feelings of exclusion for users. For instance, when users post content that receives fewer likes or interactions, they might interpret this as evidence of being disliked or ignored. Unlike the physical panopticon, where observation is implied, visibility on social media is explicit through notifications and engagement metrics. These tangible markers often lead users to draw conclusions—accurate or not—about their social standing. Furthermore, there isn't particularly a clear-cut way to drive content engagement or visibility, this unpredictability can intensify that feeling of being scrutinised. This can further stress users and erode trust in their digital relationships. This paranoia often spills into offline relationships that also occupy a digital space, such as friendships on social media. Research has shown that heightened social media use can lead to negative comparisons and damage to self-esteem. By comparing themselves to the curated, idealised lives of others, individuals may feel alienated for failing to fit predefined molds or expectations. This alienation can harm perceptions of their social relationships. Everyone yearns for connection, even in digital spaces, and the fear of exclusion can make users particularly sensitive. Some have reported sensing hostility or judgment from their online mutuals, even without concrete evidence to support these feelings. This ties into rumination and confirmation bias, where even ambiguous behaviours can become a point of contention. A 2020 study published in Psychiatry Research found a connection between social media use and paranoia. Increased usage, especially during periods of isolation, was associated with heightened feelings of persecution. This suggests that the surveillance-like nature of social media platforms, combined with their tendency to amplify insecurities, may play a significant role in these psychological effects.
#social media#panopticon effect#algorithmic anxiety#digital surveillance#modern anxiety#soft life#soft tech
0 notes
Text
Inheritance Tax: Legacy Code
After a few tumultuous weeks of hacking away at legacy code in the hopes of bringing it to a viable and secure state, there has been a clear cause for reflection. Maintaining software is an integral part of software development. The moment a codebase is deployed, it joins the ranks of entities clamouring for attention and care. It is an inevitable fact of life. In some instances, it's not so much the security updates that bring the most hassle, as that is to be expected; but sometimes it is the sheer breadth and depth of the application. From all ends you hear of the horrors of people's encounters with legacy code, often with the original owner long gone, leaving the current team to grapple with maintenance. This becomes increasingly pertinent when the legacy application is vital to business functioning, creating a dilemma of letting go versus managing a behemoth. You find fear rooted in the challenges associated with migration, and while warranted, there's a hope that fear can be replaced with a desire for ease and efficiency over a pompous technicality. In the contemporary landscape, out-of-the-box or low-code solutions have gained popularity, and the primary reason one might opt for a custom application is to fulfil a specific niche. But you find that most organisations are not offering substantially different services. There's usually a business that has either done it before you or done it after you and has done it better. It's about finding the appropriate service platform and outsourcing. An example I recently came across is Kraken Technology, which provides an out-of-the-box system for energy providers ready to be plugged in.
With a custom-built service, there's a cost associated with not only the gradual accumulation of technical debt but also the responsibility of training end-users and documenting processes. Hence, the appeal lies in ongoing support and the ease associated with low-code solutions. While people desire innovation and automation, it doesn't come without a burden. Each step associated with custom-built code, which is readily offered, incurs a massive cost that may not necessarily offset what would simply be a yearly fee. Even then, there's no consideration for the cost associated with opportunities—what else could you be doing with that time, effort, and resources to strengthen the business. OOB and low-code applications are easily integratable and often require only a few plugins or a handshake. This contrasts favourably to building a fully custom security component. Service providers have made it a point to make their services simple to integrate, baring in mind today's security challenges. There's an apprehension that lies in the fact that, although an OOB service may address high-level needs, it might not fully consider its specificity to an organisation and its unique requirements. Many software applications start as a buildable shell, allowing configuration according to an organisation's needs. However, organisations can adapt, discovering more efficient processes that challenge preconceived notions. This adaptability filters out outdated business models while lightening the workload for developers. Efforts can be focused on more innovative, smart, and slim solutions. I think it's imperative to emphasise the slimness of solutions, as that is how we find ourselves wrestling with the present conundrum of dealing with legacy code. There's a certain glory that comes with having a role people may associate with intelligence. However, in an effort to maintain this facade, people may forsake the simplest and easiest solutions, neglecting the overarching goals of cost-effectiveness, adaptation, and easy integration within a company. There is value in asking if this is relevant to the end user. When we consider IT in a holistic sense, we give more consideration to practicality over vain recognition. The real marker of a great application or system is the ease associated with it.
0 notes
Text
technologists who lack radical/revolutionary politics argue that new tech will lead to social change, ignoring the fact that we are (and have been) perfectly equipped to address many of societys ills. our states are perfectly aware of our nutritional needs, and our collective agricultural output is astronomical. the computers we already have are more than enough to handle the incredibly complex logistics of getting things where they’re needed, without hyper ‘intelligent’ super computers. it’s not a lack of fancy new tools keeping us from progress, it’s a lack of social and political will.
45 notes
·
View notes
Text
Isn't being scared of AI kind of... cliché?
Social media has recently been flooded with perfectly crafted art facilitated by Midjourney AI software. And with this many of us have now become privy to the niche which is AI Art. The capabilities of these programs are immeasurable but with time we are starting to see the possibilities. From the both captivating and harrowing feeling that follows laying your eyes on an AI rendering of heaven to the pit that forms in your stomach realising the people in an image never actually existed.
AI stands for Artificial Intelligence and it is the simulation of human intelligence through the use of machines. This branch of computer science focuses on the desire to produce machines that mimic humans in the way we perceive, synthesise and infer information. The vastness of data that is generated by all facets of society makes it humanly impossible to process at a rate that brings any value, hence, AI.
AI can be split into three subcategories, artificial narrow intelligence which is limited or focused intelligence. Artificial general intelligence which levels with human abilities and then artificial superintelligence which surpasses it. We experience AI and its differing levels everyday, most namely, Apples Siri. AI art is just another subdivision in a grand library of capabilities.
The inception of software like Midjourney have spurred debate after debate. Some including the potential for AI art to be used to deceive or mislead people, AI art ownership, surveillance, the displacement of human artists and so on.
Polaroid images of black heavy metal girls in the late 90s surfaced and underneath peoples curiosity was a level of fear, and rightly so, due to their realistic nature. This gives us a peak into the very real potential for AI art to be used to deceive or mislead people. AI-generated art or media could be used to create fake news or propaganda, or to impersonate real people or organisations. This could have serious consequences, as people may not realise that they are being shown falsehoods. And in some instances, may act based on false information. The manipulation of history is not a new concept, nor is the photoshopping of images a boundary that has not been crossed. The idea that what we perceive may be simply manufactured is justifiably a cause for concern. As of now, its always the hands. That is the immediate tell tell when staring at these AI-generated images but what if at some point it stops being the hands.
Another ethical issue with AI art is the potential for it to perpetuate and amplify biases and discrimination. AI algorithms are only as unbiased as the data they are trained on, and if the data used to train an AI art system is biased, the resulting art will reflect this. The implication of this is the us of AI art to reinforce negative stereotypes or to exclude certain groups of people. And we must be honest with ourselves, there is a bias that has mangled existing AI systems even before the emergence and popularisation of AI art, however, it sells. If the bias proves lucrative there's no incentive to rectify it or retrain with new data. Some things may seem broken but that is exactly how they want it.
When discussing ethical issues regarding AI art we must not overlook the surveillance piece. AI art systems, like many systems and services, could be used to track people's movements or to gather sensitive personal information, potentially violating their privacy rights. More often than not, people are not aware that their activities are being monitored or that their personal information is being collected. Often users have to create an account or log in from existing social media. This provides leeway in guidelines that are all too often overlooked and then exploited.
An issue of popular debate and at the forefront is the exploitation the labour of human creators. As it stands, AI art systems such as Lensa are used by consumers to generate content at which they pay a fee. This occurs without compensating the human creators who trained or fed the data to the system. This then links to the potential for AI art to displace human artists. As AI art systems become more sophisticated and widespread, consumers will turn to them to create art more efficiently and at a lower cost than human artists, potentially leading to job loss.
In conclusion, the ethics of AI art is a complex and multifaceted issue that raises a number of important questions and concerns. These ethical issues highlight the importance of considering the potential consequences of AI art and taking steps to ensure that it is used ethically and responsibly. This may involve establishing ethical guidelines for the development and use of AI art, as well as ensuring that human creators are fairly compensated and that the rights and interests of all stakeholders are considered.
10 notes
·
View notes
Text
002 Tech: 46.1 billion light-years
*Plays Ravyn Lenae Xtasy*
Just over a year and a half left of my 4-year software engineering apprenticeship. 56.25% through... can you tell the finish line is constantly on my mind? I will continue with the time markers when giving my thoughts and feelings on my journey. It's a reminder that time passes abundantly quickly if you let it.
Our code base is vast. That has been my recent realisation. Not that I was not aware of this fact previously, but it has become so much more poignant. It is a true testament to go through a domain and have a real handle on it. I like to imagine the domain of my present workplace could be likened to that of Vhagar from House of the Dragon.
In light of the redundancies at Twitter and many other tech companies, this begs the question of how we knowledge share and processes of documentation. Often times we see that teams are riddled with a single point of failure, a single team member with niche knowledge, leaving the team in disarray should they be absent. To the point of documentation, those in an agile camp may be of the mind that excessive documentation is useless as it becomes obsolete given the pace of software development. I take the more measured view of Suzanne Robertson who suggests that agile doesn't necessarily do away with documentation but looks to leave a trail of information. This may encompass use cases and an acceptance criteria following the inception of a project. Later on, it may look like a well-written test in the source code which reveals the purpose and functionality of the product or service.
We can also question, whether our code is too complex or whether our architecture is robust or excessive? As trite as it may seem, I've also realised that employees hold the heart of the companies. Their fingers are the gateway to the realised dreams of the wider business. It is then bittersweet when employees that have been with a company for nearly a decade part ways. All that knowledge, history and passion... literally into the deep as they take on the challenge of a new role. It is then necessary to ask, what can companies do to stop haemorrhaging staff? Big tech companies view employees as dispensable and replaceable. There is a real disregard for the domain expertise acquired over the years an this only ends up hurting the consumer.
The industry is in an interesting place. Where it's heading, I'm not too sure, but it feels like there's a revolution on the horizon. So, to the figure in my title that may seem completely arbitrary, how far is it to the edge of the universe?
Our code base is vast because tech is vast. And tech is vast because the universe is vast.
0 notes
Text
001 Case Study: Why do IT Projects Fail?
I. INTRODUCTION
This report will examine the 2015 Instructional Technology Initiative (ITI) project. It will detail the nature of the project and seek to identify the problems that resulted in its failure.
II. BACKGROUND
This section will provide context to the ITI and shed light on its ultimate goals.
The ITI was an attempt to bridge the digital divide in the Los Angeles Unified School District (LAUSD) by providing e-enabled learning tools for all students.
This goal was facilitated through the purchase and distribution of iPads among students, teachers, and administrators in an effort to aid classroom learning. The iPads were configured with security and curriculum specific content, while in other cases they were configured for standardised testing.
I chose this project because I have been reading around the topic of digital exclusion.
III. ITI PROBLEMS
This section will examine the problems with the ITI and their scale.
One problem during the ITI rollout was that the learning content on the iPads was not fit for purpose. The district employed various apps which included resources developed by Pearson Education. Reports suggest that the content “was not written in accordance with applicable teaching standards” and they found the materials to be incomplete (AIR, 2015).
In some cases, staff went ahead to utilise the resources but found that the technology fell short performance wise. This paired with the lack of technical support rendered the system useless.
The most concerning issue was that of safety and security. The district found their safety measures were futile.
The ITI Director reported that “only 2 of 69 schools in the initial pilot were still attempting to use the tool... less than 5% of the target student body had reliable access to the content” (Calleam, 2022). Additionally, across three schools 185 students disabled safety controls. In total ITI cost the district 1.3billion dollars and had to be discontinued.
IV. REASONS FOR ITI’S FAILURE
This section will address reasons for ITI’s failure, drawing on project management themes.
It was identified that learning materials on the iPads did not meet the requirements. This is an example of risk transfer as LAUSD opted for an external service provider. ITIL highlights the dangers of this as external providers are less likely to be aligned with the business. Furthermore, despite outsourcing, LAUSD failed to check the learning apps against their requirements.
Moreover, adequate testing was bypassed both in respects to the performance of the iPads and the safety measures.
V. CONCLUSION
In conclusion, the failure of ITI emphasises the importance of project management and the need for consideration of possible risks. In the future LAUSD may consider trusted suppliers and the steps they can take for better service integration.
VI. REFERENCES
American Institutes for Research (AIR). (2015). Evaluation of LAUSD’s Instructional Technology Initiative Year 2 Report, 2015. (online) Available at: https://www.air.org/sites/default/files/downloads/report/LAUSD-Instructional-Technology-Initiative-August%202015.pdf
Calleam (2022). Los Angeles Unified School District – Why Do Projects Fail? (online) Available at: https://calleam.com/WTPF/?p=7626
The Open University. (n.d.). TM254. Managing IT: the why, the what and the how. (online) Available at: https://learn2.open.ac.uk/course/view.php?id=209356
1 note
·
View note
Text




Nokia Magazine Ads From Dazed & Confused Magazine (2003)
6K notes
·
View notes
Photo
We often hear about children being lost in digital spaces but have we ever stopped to think about the war on safe digital spaces? This is very indicative of the time we’re living in.
2 notes
·
View notes
Text
Service Management Failures: Nick stole Ben’s Flow
Recently, as an offspring of my software engineering degree, I've studied the likes of ITIL and service management as a whole. After completing the module, I quickly found parallels in my everyday life which resembled the rather ridiculous and fictitious case study underpinning my studies called “Ben’s Folly”. It is in part naivety and circumstance that means I’ve not found myself at the end of an ill-equipped or broken service. Until now.
A service in itself is an activity which is intangible and cannot be stored, or owned. It is consumed at the point of sale. The whole idea is that value is delivered to customers through the facilitation of specific outcomes. Service management is “ an approach that emphasises the importance of coordination and control across the various functions, processes and systems necessary to manage the full lifecycle of services“.
The five core aspects of service management are service strategy, service design, service transition, service operation and continual service improvement. I won't go into detail for each core process but will touch on those reflected in my experience.
*All names are revised*
Nick’s folly is as follows... Greenwich Photohouse makes for a unique viewing experience. It provides comfortable screening while maintaining a quaint and trendy atmosphere void from the mainstream theatres. Photohouse offers a venue hire service in which customers can rent screens and other spaces per hour. These details and prices are not available on the website so customers must fill in an email form online and wait to be served. Once contacted by Nick the manager, customers can proceed to make a booking. Nick deals with venue hires solely. Headquarters is understaffed and subsequently, Nick finds himself overstretched. As Nick is based at headquarters, he has minimal knowledge of the Greenwich Photohouse venue other than what he has read. The employees based at Greenwich Photohouse are unable to process bookings despite being familiar with the venue and eventually hosting the booked events. Furthermore, there is no clear per-hour price list for venue spaces in the theatre that are not screening rooms (e.g. bars, cafes etc.). Nick often finds himself having to estimate a price that “sounds about right”. Overall, the venue hire process can span over weeks and this results in many bookings not being fulfilled.
The first issue with the above service lies in the service strategy. Nick, the deputy manager in charge of the venue hire email, struggles to keep on top of the inbox. He often takes 1-2 days to reply if he has not completely ignored an email. As a result, exchanges are drawn out over long periods. This hinders the supply of service, venue hire, to be supplied to present and potential customers.
The second issue lies in the service design and the limited communication channels. We've now entered an age of no phone calls where companies limit phone call usage from customers or completely halt/suppress it. Where this falls over is when there is no sufficient and robust process to accommodate requests usually discussed over the phone. The only avenue for venue hire is to book through email which we identified has a low success rate. Nick and Photohouse seem to be unaware that they are introducing constraints on the way in which prospective customers can make a booking.
As we lack context for the service in place prior to the present one, if one ever existed, we cannot comment on service transition. Briefly, service transition posits that a service should not be abandoned before the new service is tested and implemented successfully. Furthermore, it views services as enduring which require strategies for coping with the resulting systemic failures.
We can see that with the venue hire, there is no systematic mechanism for ensuring that whatever is supposed to be happening actually is. This shows a lack of service operation. If Nick is indisposed then there should be an employee that can step in to assist customers.
As there is no fully working service in place, there is little scope for systematic service improvement.
This covers a good majority of service management in relation to the above case study. This analysis helped me to deeper understand some concepts that were primarily theoretical to me. Service management as a whole is expansive but there are useful short videos available online that give the general gist.
#service management#itil#case study#service strategy#service design#service operation#soft life#soft tech
0 notes
Text
Nollywood subliminally told me to go into tech
Recently, I was studying the Technology Adoption Lifecycle model (Rogers, 2003; Moore, 1999). The model assumes there are five subsects of consumers, all with differing roles in the assimilation of technology. You find a small percentage as the innovators, followed by a slightly larger group, the early adopters. A chasm forms before you reach the early majority and the late majority, making up nearly seventy percent, and finally, with some hesitation, the laggards. The chasm is relevant in that those to the left of the chasm can imagine the future benefits of technology, and it reflects in their eagerness to adopt it. Those to the right are seen as more pragmatic and bound to reliability. Crossing that chasm is what puts you at the cusp of breaking into the mainstream.
Although it may not be considered chasm crossing, the BlackBerry was notable in creating the groundwork for the success of the iPhone, defining the concept of a smartphone before it really took precedent. The BlackBerry featured a mini keyboard and did away with the flip. It genuinely felt like you held the future, at least at the time. It was a handheld Personal Digital Assistant (PDA), and it brought together email, contacts, calendaring, and web browsing facilities as standard, with a built-in digital camera and music player.
The BlackBerry wasn't quite a status symbol globally as the iPhone was positioned, but in the West of Africa, Nigeria, it was a different case. The BlackBerry was an object of desire and appealed to the divide in Nigerian society. One might push back and say that BlackBerrys were a big deal everywhere, but Nollywood even went to the extent of producing a film called "Blackberry Babes," which touched on the elusive lives people led in an attempt to possess a BlackBerry. It's undeniable that Nigerians use phones as a status marker. I think this desire, both good and bad, honed in the groundbreaking nature of such technology, and even for myself as an impressionable teenager, it fed into the consumerist frenzy which, luckily, with age, has somewhat dissipated.

I believe it is important to speak about how revolutionary mobile phones have been. We're believed to be in a post-PC world, and I think this is particularly poignant for some parts of the world. We've reached a stage where a desktop or a laptop is not a necessity because the mobile outperforms in terms of intuition, range of services, and integrated software. In 2008, Mary Meeker predicted mobile internet use would surpass desktops by 2014, and present figures confirm that this was indeed the case. That's not to say they are completely eradicated. However, even with the mobiles valuable use, there's a desire that they will not simply bridge the gap or be in place of well-needed infrastructure. Let it be the innovators spirit that has pushed the mobile phone across that chasm that also makes Nigeria and Africa a viable platform for technological advancement and investment. For sure, the talent is there, and the world reaps the benefits annually from this most precious export.
0 notes
Text
The Cloud in 5 minutes
Although Snapchat has become a faded version of its former self with platforms such as Instagram and Tiktok leading the charge, I still find one use that will forever have me bound. This is the Snapchat memories feature. It allows me to make infinite memories without a second thought to memory or storage. So how exactly is this done. Well, the cloud.
The cloud refers to software and services that are accessed over the internet as opposed to through your computer locally. Cloud computing aims to foster on-demand availability of computer system resources, especially data storage and computing power. Additionally, this does not require direct management from users. Cloud servers may operate according to function and therefore be distributed among several data centers.
There are three main categories cloud computing fall into: Infrastructure-as-a-Service (IaaS), Platforms-as-a-Service (PaaS), and Software-as-a-Service (SaaS). Snapchat could be classified as Iaas as it offers storage resources on demand.
The seamless switch from the USP of 10 second clips to cloud storage is smart given the competition. Simply due to this feature, many users that have migrated to the likes of Tiktok will remain on Snapchat. If there’s one thing people cherish, it’s memories.
#the cloud#cloud computing#tech#tiktok#instagram#snapchat#data storage#iaas#paas#saas#soft life#soft tech
0 notes
Text
Not a Jordan to my Name: The Lost Update & Locking
I’m sure we’ve all had our own unfortunate experiences with the snkrs app and exclusive sneaker drops in general. And this is the part where I say resellers don’t deserve anything nice in life.
I’ve got to a space where I no longer fret about sneakers selling out... and anything in general. Why is that? Because I learnt about databases. In fact, I purchased two pairs of Jordans today. Let me elaborate using the example of an online sneaker sales application.
We can think of the application process for allocating sneakers as a sequence of three sub-processes:
Step 1 : check sneaker availability,
Step 2 : allocate sneaker,
Step 3 : make sneaker unavailable to others
In the case of sneakers, multiple users may attempt to purchase sneakers at once. When sneaker buyers undergo this process, it will result in sneakers becoming unavailable if sold, and this must be reflected in real-time so that the data for the sneaker availability is valid. In this instance, two users may select a sneaker at the same time not allowing for an update (to show the sneaker is unavailable) to be executed in the database. This is an example of the lost update problem, where two queries by different users are executed simultaneously.
This is resolved through the use of transactions. A database will not allow another user access to items (through locking), such as sneakers before a transaction has been completed. Once complete if the transaction was successful the sneakers will become unavailable. Otherwise, the sneakers may undergo another transaction by a new user. This often means items will appear to be sold out when in fact they are locked in a number of transactions that are not yet final.
Hence it often pays to stay on a site as hype dwindles down to see if a sold-out item becomes available upon a transaction failing. This is likely to happen as many transactions are timed or people simply change their minds.
So how do we manage this...
Optimistic concurrency management assumes that two queries on the same item will not have to be executed at the same time. Therefore, the application copies the data to be performed on from the database (at the beginning of the transaction) and once it is ready to update it, it will check to see if the data has since changed. If not, then it performs the update; otherwise, it must rerun a new transaction. Pessimistic concurrency management takes the approach of locking data during a transaction. This entails limiting access to the data so that it cannot be performed on until unlocked.
The pessimistic strategy is the recommended approach as it gives a more accurate idea of sneaker availability. This results in less disappointment for customers. The optimistic approach could see someone through the majority of the transaction and fall through which is frustrating for users.
So next time a pair of sneakers you’ve been eyeing sells out, consider lingering on the website for 30 minutes to an hour.
#tech#database#the lost update#locking#sneakers#jordans#optimistic concurrency#pessimistic concurrency#data#soft life#soft tech
0 notes
Text
03:39 AM
I wouldn't say I was one to watch life go by, however, one thing the pandemic broke me out of was wanting to do something and then waiting for an extended period before pursuing it. That was what tech triggered for me. That was the courage it instilled. Now I do everything that slightly intrigues or excites me. And in some cases, alone.
Life waits for no one so I don't intend on waiting for life. It is liberating driving my life and not at 20mph.
That’s one thing I’ll give tech. It made me brave and just pursue. No thinking, just pursue!
0 notes
Photo
I mean, not me but I giggled.
2 notes
·
View notes

