#Best Cryptography Assignment Help
Explore tagged Tumblr posts
Text
How to Hire the Perfect Solidity Developer for Your Blockchain Project
Blockchain technology is of revolutionizing importance to most industries, while smart contracts form the nucleus of their incorporation. Solidity is the programming language that works on Ethereum for smart contracts, being an essential building block to developing decentralized applications dApps. Hire Solidity developer who has the expertise and experience to do the project well if you want to realize your blockchain vision. But, as said before, careful attention is needed in this as well as a deep understanding of what you wish to look for in a developer.

Understanding Solidity and Its Importance
Solidity is a high-level object-oriented programming language for programming smart contracts deployed to the Ethereum platform or other blockchain networks. It has a similar syntax to JavaScript, but it serves a completely different purpose. While JavaScript is used purely for short-lived and non-secure contract executions, Solidity is focused more on the secure and efficient execution of long-life contracts. Therefore, a good Solidity developer should have a good knowledge of the concepts behind blockchain technology, cryptography, and decentralized systems. Hiring the right Solidity developer will help to construct your project very accurately, making sure it scales well, is secure, and is reliable.
Evaluating Technical Skills and Experience
When looking for a Solidity developer, the first most important thing to check is their technical skills. An able developer would be good at Solidity, possess knowledge of the Ethereum Virtual Machine (EVM), gas optimization, and blockchain security practices. Experience in smart contract development, dApps, and DeFi proves their cleverness at handling much complex work. It shows the understanding of tools such as Truffle, Hardhat, and Remix, which ease the development process. A good portfolio with previous work can be a good insight into their expertise.
The Role of Communication and Collaboration
Although all the technical aspects are important for project activity, successful completion would also require proper communication and effective teamwork. Your Solidity developer must translate these technical concepts into plans that can be applied. In addition, they should be adaptable to the needs of your project. They will also need to work independently or as part of a team in communicating progress on the work AND challenges to success to get on their path to developing the necessary skills in giving integrated feedback to ensure smooth working of projects.
Finding the Right Fit for Your Project
Finding the best Solidity developer for your project requires more than technical knowledge. Therefore, it is also worthwhile for you to look for a developer who shares your vision for your project goals. Whether you hire a freelancer or develop a contract with a dedicated team, they must share your enthusiasm for blockchain innovation. Do background checks, interviews, and test assignments to prove their fit against your particular needs.
Why Work with a Solidity Development Company?
If you need a holistic solution, then going with a Solidity development company becomes an ultimate choice. All such companies work with teams of experts with different skills, hence providing complete assistance during the whole life cycle of your blockchain project. They make sure that all high quality, security and efficiency standards are strictly met, which will give you confidence in the success of your project. Such a partnership with a Solidity development company also offers the benefit of scalability to you, which would allow you to tap in other resources as the project continues to grow.
Conclusion
Employing a competent Solidity developer is critical for transforming your blockchain dream into reality. One can thus hire the right expert who can take the project to the next level by understanding the facets of Solidity, gauging technical skills, and finally communicating. If they even want a smooth sailing experience with full-fledged support, then opting for a Solidity development company is an excellent move here-the very own experts and their cooperative capabilities along with cutting-edge tools make them an invaluable partner in the challenging voyage of blockchain development.
0 notes
Text
Quantum Computing Revolution: Transforming the Future of HRMS Systems
The Future of Quantum Computing
Quantum computing is one of the most promising technological advancements of the 21st century. With the potential to revolutionize industries, solve complex problems, and enhance computational power beyond classical limits, quantum computing stands at the forefront of the future of technology. This blog will explore the future of quantum computing, its potential applications, and the integration of HRMS System in this emerging field.
1. Understanding Quantum Computing
Quantum computing leverages the principles of quantum mechanics to process information in fundamentally different ways compared to classical computing. While classical computers use bits as the smallest unit of information, which can be either 0 or 1, quantum computers use quantum bits, or qubits. Qubits can exist in multiple states simultaneously, thanks to the principles of superposition and entanglement. This allows quantum computers to perform complex calculations at unprecedented speeds.
The power of quantum computing lies in its ability to solve problems that are currently intractable for classical computers. For instance, quantum computers can factor large numbers exponentially faster, which has significant implications for cryptography and cybersecurity. Moreover, quantum algorithms can optimize complex systems, simulate molecular interactions for drug discovery, and improve machine learning models.
2. Current State of Quantum Computing
As of now, quantum computing is still in its nascent stages. Major technology companies like IBM, Google, and Microsoft, along with numerous startups, are investing heavily in quantum research and development. Quantum processors with a few dozen qubits have been developed, and quantum supremacy—a milestone where a quantum computer outperforms the best classical supercomputers—has been achieved by Google in 2019.
Despite these advancements, several challenges remain. Quantum computers are highly sensitive to environmental disturbances, leading to errors and the need for error correction. Additionally, scaling up the number of qubits while maintaining their coherence and entanglement is a significant technical hurdle. However, ongoing research and development are steadily addressing these issues, bringing us closer to practical and scalable quantum computers.
3. Potential Applications of Quantum Computing
The future of quantum computing holds immense potential across various industries. Here are some of the most promising applications:
Cryptography: Quantum computers can break current cryptographic systems, necessitating the development of quantum-resistant encryption methods. However, they can also create unbreakable encryption through quantum key distribution.
Drug Discovery: Quantum simulations can model molecular interactions with high precision, accelerating the discovery of new drugs and materials.
Optimization: Quantum algorithms can optimize complex systems, such as supply chains, financial portfolios, and traffic management, leading to significant efficiency gains.
Artificial Intelligence: Quantum computing can enhance machine learning models, enabling faster training and more accurate predictions.
Climate Modeling: Quantum simulations can improve climate models, helping to predict and mitigate the effects of climate change more accurately.
4. Quantum Computing and HRMS Systems
While the direct connection between quantum computing and HRMS systems might not be immediately apparent, the integration of quantum computing can enhance HRMS capabilities in various ways. HRMS systems manage employee data, streamline HR processes, and support decision-making within organizations. Quantum computing can provide advanced data processing and optimization techniques to improve these functions.
For example, quantum algorithms can optimize workforce scheduling, ensuring that the right employees are assigned to the right tasks at the right time. This can enhance productivity and reduce operational costs. Quantum-enhanced machine learning can analyze employee data to predict performance trends, identify skill gaps, and recommend personalized training programs. Furthermore, quantum-secure communication methods can protect sensitive HR data from cyber threats, ensuring privacy and compliance with data protection regulations.
5. Challenges and Ethical Considerations
As with any emerging technology, quantum computing brings several challenges and ethical considerations that must be addressed. One major challenge is the technical complexity and high cost of developing and maintaining quantum computers. Ensuring that quantum computing technology is accessible and affordable to a broad range of industries and organizations is crucial for its widespread adoption.
Ethical considerations include the potential for quantum computers to disrupt existing cryptographic systems, posing risks to data security and privacy. Developing quantum-resistant encryption methods is essential to mitigate these risks. Additionally, the use of quantum computing in areas like AI and data analysis raises concerns about bias, fairness, and transparency. It is important to establish ethical guidelines and regulatory frameworks to ensure responsible and equitable use of quantum computing technology.
6. The Road Ahead
The future of quantum computing is filled with exciting possibilities. As research progresses and technical challenges are overcome, we can expect to see quantum computing becoming more integrated into various industries and applications. Here are some potential milestones and trends to watch for in the coming years:
Increased Qubit Counts: Advances in quantum hardware will lead to quantum processors with higher qubit counts, improving computational power and enabling more complex applications.
Quantum Cloud Services: Major tech companies are already offering cloud-based quantum computing services, allowing businesses and researchers to access quantum processors without the need for specialized hardware.
Quantum-Resistant Cryptography: The development and implementation of quantum-resistant encryption methods will become a priority to protect data in a post-quantum world.
Interdisciplinary Collaboration: Quantum computing will drive collaboration across various fields, including computer science, physics, chemistry, and materials science, leading to innovative solutions and breakthroughs.
Education and Workforce Development: As quantum computing technology matures, there will be a growing need for education and training programs to develop a skilled workforce capable of working with quantum systems.
Conclusion
Quantum computing represents a paradigm shift in how we process and analyze information. With its potential to revolutionize industries, solve complex problems, and enhance computational power, quantum computing is poised to become a cornerstone of future technological advancements. Integrating quantum computing with HRMS systems can further enhance organizational efficiency and decision-making capabilities.
While challenges and ethical considerations remain, ongoing research, interdisciplinary collaboration, and responsible development will pave the way for a future where quantum computing is an integral part of our technological landscape. As we move forward, staying informed and prepared for the quantum revolution will be key to unlocking its full potential and reaping its benefits.
0 notes
Text
Why choose the services of 24×7 assignment help?
In the above fundamental securities, the algorithms to be learned for making a digital data secure is not an easy task for a student. The homework and assignment may make them feel confused with algorithms and other cryptography aspects. Where our https://www.allhomeworkassignments.com/ cryptography assignment assistance will surely be helpful to you. There are symmetric and asymmetric algorithms and also encryption and decryption which are the basis of the cryptography. They need to give special attention towards this topic of programming as a single wrong code can affect the security algorithms. Taking online help from https://www.allhomeworkassignments.com/ is always useful.
Why choose the services of 24×7 assignment help?
When you are in search of an online expert to ask them to do my cryptography homework and assignment then https://www.programmingonlinehelp.com/ are one among the other online companies by providing efficient services that too at affordable cost. Let us see what our strengths are and how we are good for solving your assignments?
•You get content which will be only yours that is unique and plagiarism free. How to solve cryptography assignments? Is not a big question for our https://www.programmingonlinehelp.com/ experts. They have complete knowledge to give the needed help with all types of question, You get the help from the experts that are dedicated to their work and always give you timely delivery. You can ask for do my nursing cryptography at any time as we provide a service which is available 24/7 for you. You may be around anywhere in the world you just need to go online and hire https://www.programmingonlinehelp.com/ experts through simple steps and also make the payments with secure methods. You be assured with our work that it will be without errors and it will make a huge difference in your grades at all time.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text
Benefits of Blockchain for Identity and Access Management - By Azgari Lipshy
Society's push toward digitalization also leads to the digitization of personal identities. From health information to professional certificates, the requirement for identification information and credentials is expanding in number, diversity, and significance. Traditionally, third parties monitor and confirm identification information —government or commercial sector. However, declining levels of trust and innovative technologies are causing people to challenge these structures.
Paper-based forms of identity are becoming more unsuited for the digital age due to the growing volume of personal data, the prevalence of digital interactions, and the severity of security concerns. It is uncertain, though, how future technology will transform identity.
Identifying, authenticating, and authorizing users of services or systems is a major task for identity and access management (IAM) technology in business and government environments. Several operations come under this rubric, and "access" might mean anything from a user logging into a system to an employee setting hardware, a citizen utilizing a government service, or any other kind of user verification, certification, or confirmation. Examples of identity traits include job, nationality, service provider affiliation, government benefits eligibility, and demography. In addition to serving as digital representations, these tags can stand as proof of our identities.
Among the many new technologies that might serve as templates for IAM is distributed ledger technology (DLT), also known as the blockchain. DLT is best understood as a catch-all phrase for a family of related technologies that facilitate distributed designs for data protection and processing. Its primary feature allows the network to record and verify activities like purchases, logins, and chats, rather than relying on a third party. Blockchain technology — or blockchain-inspired solutions — might enhance IAM operations in various scenarios if implemented correctly. Among such scenarios are the following:
Elimination of Paper-Based Identity Management
Eliminating paper-based identification management is the primary advantage of blockchain for identity management. Blockchain identity management systems can assist when users misplace their original papers by acquiring duplicate ID proof. Users who forget or lose their original ID proof credentials can retrieve them using Blockchain Identity Management, but they must go through specific procedures.
Organizations can ensure that documents are irreversible and tamper-proof with blockchain identity management. With the guarantee of security and dependability, government authorities can preserve ID evidence of individuals on a blockchain. In addition, the permanence of the ID proof record is ensured by blockchain security.
Self-Sovereign Identity (SSI)

Independently Verifiable credentials
As stated by the W3C, "Verifiable credentials represent statements made by an issuer in a tamper-evident and privacy-respecting manner." As an integral part of the identity verification process, DLT affords the opportunity to "digitally stamp" a permanent claim. Similar to how artists may now digitally watermark their original material using blockchain-based Nonfungible Tokens (NFT), this same capacity can be used to authenticate credentials. However, businesses should not keep Personally Identifiable Information (PII) on the blockchain itself but rather keep the hash of the claim on the blockchain.
Decentralized Identifiers (DID)
DIDs are identifiers under the authority of the identity owner, without the involvement of centralized authorities or resources. These are a part of SSI’s personal data intention to be user-controlled and not re-assignable. This indicates that digital identifiers have public key documentation, authentication mechanisms, and verifiability through cryptography or the signature of an issuing authority.
Provenance
Blockchain can help determine the source and precision of identification attributes. An attribute is only as trustworthy as confidence in its source. A shared ledger might establish transparency in the timestamps of sources providing identification traits, much as it has increased transparency and efficiency in monitoring commodities across the supply chain. In particular, synchronous insight into the lifespan information of cryptographic keys or who has access to what might be beneficial for key lifecycle management. Furthermore, the academic community is also considering using blockchain provenance since it might help with the authentication and verification of credentials for recruiting.
Minimization of Data
To authenticate a user, traditional service providers require a lot of verifiable data. Different DLT features, such as zero-knowledge proofs, smart contracts, and selective disclosure, can be set up to reduce the amount of data or attributes needed for verification.
Compliance verification
As shared ledger network stakeholders with permission-based access, auditors may also be used for compliance verification, which is another use case made possible by shared audit trails. Compliance verification is also necessary for many business identification use cases, such as KYC in financial services. In this situation, the IAM-blockchain convergence might increase efficiency for both banks and individuals without doing away with the requirement for the central authority, which in this case would be a governmental body handling KYC. A bank might lower its expenses while "seeing" and attesting that other banks have performed KYC due diligence and confirmed the clients' identities.
Conclusion
This blockchain above use cases outline the advantages of merging blockchain with IAM, but they ignore a crucial fact: identity is difficult to manage. Even though IAM connects many systems, domains, technologies, and service providers, encoding identity data into DLT is more than a technical task. It's crucial to inquire about the data, including what has to be saved, who should attest to it, how it's maintained, and who makes the decisions. These inquiries incorporate philosophical, financial, cultural, and legal factors. Although the technology is still developing, it can convert centralized but dispersed hubs that now serve as identity control points into a decentralized yet linked web of trust.
About the Author
Azgari Lipshy is a yogi by sunrise, a SAAS account manager by day, and a live music fanatic by night. She writes about her experiences while traveling, cooking, yoga, and technology that she finds fascinating.
2 notes
·
View notes
Text
The Sprinkle Cipher
I came up with the ‘sprinkle’ part of my username in a pretty arbitrary way, but ever since I picked out the username, I’ve thought about what a sprinkle-based cipher might actually look like. Combining different types or colors of sprinkles seemed like the most logical approach, so I came up with a simple substitution encryption scheme that can encode letters using specific combinations of five different sprinkle types.
Each sprinkle type (1-5) could theoretically be any kind of sprinkle, although it would be best for each type to be as clearly distinct from the others as possible to reduce the possibility for confusion. The best application of this cipher would be to use different combinations of sprinkles on a set of cupcakes or cookies to encode the message (so each individual cupcake/cookie would correspond to one letter, based on which combination of sprinkles it had on it), but the same principal could be applied to other things as well.
Here's a chart depicting the sprinkle-combinations that are associated with each letter using my encryption scheme.
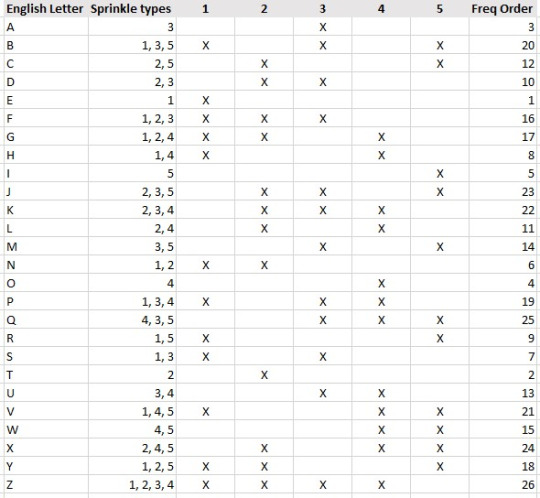
I assigned the sprinkle combinations to letters so that the most frequently occurring letters would only require one or two sprinkle types. With that in mind, here’s the chart again, but sorted to letter-frequency order:

To help visualize what it might actually look like to use a cipher like this, I wrote a script to make images of “cookies” with the appropriate combination of sprinkle types to correspond to a letter. For this visualization, I went with pink, blue, red, lavender, and dark purple sprinkle colors to represent the respective sprinkle types, but, again, the specific kind of sprinkles can be varied. The resulting “cookie” pictures may be ugly MS paint-looking abominations, but I think they convey the general idea well enough. Here’s an idea of how the cookie-alphabet would look:
Letters A-O

Letters P - Z

And here’s an example of the cipher being applied to form a message:
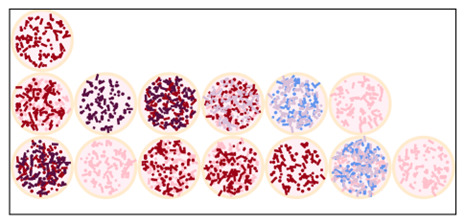
I probably could have selected better colors, but I think the proof-of-concept is promising enough that I could see actually using this IRL at least once (although I recognize that that position is very much a “me” thing).
In conclusion, here’s my 100% objective evaluation of this new encryption method:
Pros of the sprinkle cipher:
Cute
Potentially delicious
Plausible deniability—the fact that there’s an encoded message at all is not obvious (see steganography for more on this kind of thing)
Can be used to wish your weird cryptography friend a happy birthday in a way that they will appreciate
Great way to passive-aggressively vent frustration towards people you dislike but have reason to provide food for. You could encode a snarky message on cupcakes for a potluck attended by bad coworkers, for example
Cons of the sprinkle cipher:
Poor communication potential. Difficult pattern to remember for both encoding/decoding purposes
Requires five visually distinct types of sprinkles to implement, which may be impractical (although counterpoint: sprinkle shakers that have 6 different sprinkle types are not all that uncommon)
Possible message length may be limited by the number of cookies/cupcakes/etc. that you are able to bake for the occasion
If your bad coworkers begin to suspect that you have taken out your frustrations on them via the cupcakes you brought to the potluck, they will probably not consider that you have done so using a sprinkle-based substitution cipher and may instead believe that you did something more serious, like spike the cupcakes with laxatives. This could cause problems for you
#Ciphers#Substitution Cipher#Sprinkles#Classical Cryptography#Cryptography#Steganography#Misadventures in Classical Cryptography#Misadventures in Python#Misadventures#sC original#Apologies that the cookies are so ugly#I have never claimed to be an artist#Including a graphic artist
4 notes
·
View notes
Text
just like old times pt. III | Stitch/Bell

TWs: Blood, Accidental tasting of Blood (there's context I swear), Forced Attempted Vomiting, and Minor Character Death. There's some scenes in here that may be subject to different interpretation.
“As you know, Perseus continues to be at large. However, there’s been a significant shift in his operations towards chemical warfare production in Rebirth Island. We suspect the operative behind this is Vikhor Kuzmin-”
Having been previously grounded to paperwork duty in the safehouse by Hudson, you were one among some of the few analysts to help Adler prepare the briefing. There wasn’t much point in you devoting your full attention to something you effectively helped create.
You tried to ignore the eyes that proceeded to look at you at the mention of his name. You turned your attention to the nagging irritant that had been tearing at you for the past hour.
She was a walking airborne toxic event of bright hints of green soon drowned by overpowering artificial fruity notes with orange blossoms accenting the scent. However, beneath the bombastic scent, there was something there that just tore at you.
You tilted your head to the side, trying to avoid being so subtle about sniffing. Although, the scent she left in her trail as she walked past you at the table was anything but subtle. Suddenly, Nancy whipped around on her heels, scowling at you with an offended look.
Apparently you hadn’t been so lowkey about it.
“Are...are you smelling me like a dog?” It came out as almost a defensive sneer with her lip curled in disdain.
You once again leaned your head to the side, trying to guess what that damn scent tearing at you was, “You smell -”
“Oh, screw off,” Nancy scowled down at you before storming off in those heels of hers.
She was a hotshot analyst with a stellar education from Yale, according to the briefing. More specifically, she was a new analyst brought to cover your workload. After all, you were assigned to focus on identifying and decrypting any and all weaknesses in the cryptography of the Underground Collective.
As she stormed off, she left a thick and heavy trail of that bombastic scent. Giorgio , she had called it rather proudly and imperiously.
This scent , you thought, massaging your temples with your hands. The nausea had developed into a migraine with a steady throb in your head. It was only when the pulsing slowed that you focused on the scent finally.
You hid your grimace with a hand over your mouth and nose, not wanting Adler to notice your lack of attention on his briefing. And then you recognized the scent.
Peaches.
________________________________________________________________
You sighed, passing the monitors surveillance station yet again. You had been making rounds around the safehouse with the files casually clutched in hand. Your Walkman played Pat Benatar’s “ Hit Me With Your Best Shot ”. It took your mind away from the still nagging scent of that damn Giorgio perfume accented by the smell of peaches .
You didn’t know how many times Nancy applied that cursed fragrance. She must have done it recently because you could have sworn the smell of peaches got stronger .
You shook your head to yourself. You were going to focus on work, not that godawful scent.
You proceeded to go over the files in hand. Numbers and encryptions swirled in your mind. Perseus must have assumed his crypto communications had been compromised. They reverted to a new system soon after Solovetsky. However, one couldn’t re-engineer and rebuild an entire encrypted communications system in six months.
Not without mistakes.
Even though they used one-time pad ciphers, there were always those weak links.
Mistakes.
A little slip up here and there in sloppily reusing certain one-time pads is all it took for just a little part of the communications to be compromised.
However, even as you made progress in identifying the surprisingly many mistakes of the past and present encrypted communications of the Underground Collective, your thoughts soon wandered.
After all, that sickly sweet fragrance of peaches lingered in your thoughts. You had been grounded to fieldwork upon Hudson’s insistence.
You knew the looks they gave you after that operation in the Mall at the Pines. Up until then, there weren’t any living witnesses to encounters with Stitch, however rare his appearances were until that point.
Yet he spared you.
Perhaps, he wanted to torment you under Perseus’ orders to make your death slow and painful, fitting for that of a traitor to the collective. That’s something you took cold comfort in.
At least there was a logical reason for it , you thought with the upbeat tunes of a song in your mixtape playing through the headset at your ears.
Just as you walked past the caged in areas where the sensitive cryptography machines were held, you blinked as everything suddenly went dark.
You quickly removed your headphones to your neck, pressing pause on your Walkman at your waist. You could hear the click and rumbling of the backup generator kicking on. The emergency lights suddenly flooded the safehouse with crimson lighting bathing the room you were in.
Suddenly, you heard gunshots coming from the other side of the safehouse. Close to the entrance where the surveillance monitors were , you guessed. That made sense. What little security was at the safehouse was located there. It was the most efficient way to secure the site.
As you heard the sound of gunshots come to an abrupt end and heavy footsteps rushing around, you immediately dropped to cover under the desk you found yourself standing beside. It was only a matter of time before they swept the entire safehouse, securing or eliminating any sensitive intel and remaining personnel.
You instinctively reached at your hip in a familiar motion only to silently curse when you only found your Walkman there.
After the operation at the Pines, you noticed the rather uneasy looks some of the personnel sent you. They had been filled in on the bare details of your background, omitting MK Ultra of course. All they knew was that you used to work for Perseus and that you weren’t completely stable mentally as shown by the medications you had to take.
Ultimately, that had culminated in Hudson strongly suggesting that you didn’t carry around a handgun in the safehouse. Sims managed to make a compromise between the two of you by offering for you to have access to the weapons locker anytime in the safehouse. Although, you always had to go to him for that.
And Sims was not here.
Based on the number of footsteps you heard a distance aways, you guessed the strength of the attacking force to be around 4-6 at max. Outgunned and outmanned, you thought to yourself. If you had your weapons...it’d be a different story.
But there was one thing that you had: a knife.
And most importantly...
Closets.
You pressed yourself close to the walls with your ears alert for any approaching sounds. When you heard a single pair of footsteps coming closer to your corner, you withdrew the knife from its sheath at your waist.
As soon as you saw the back of the operative, you lunged forward quietly. You pressed one hand against the mouth of the operative, muffling the yell of surprise from him, before slamming it into his jugular. His body soon sagged against you in a matter of moments.
Immediately, you let his body go down to the floor silently while you looked for any weapons on him. You grabbed the Krig 6 assault rifle from his hands and the Makarov pistol from his holster.
Knowing what Belikov taught you over a few bottles of vodka, you dragged the operative’s body over to the nearby maintenance closet. You quietly opened the doors and propped his body against the interior of the closet. Then you shut the doors.
Checking the ammo count on the Krig 6 and the Makarov, you smiled to yourself as best as you could in the present situation. It sure as hell was better than taking on the attacking force with just a knife in addition to making sure other safehouse personnel weren’t caught in the crossfire.
Speaking of the personnel, how many were left alive in the safehouse? There were at least 4 analysts not working anywhere near the entrance of the safehouse where you heard the gunshots originate from.
You knew what your priorities were.
Secure or eliminate sensitive intel and technology in addition to ensuring the safety of the analysts from the attacking force if possible.
________________________________________________________________
The radio crackled to life at your hip, sending a note of alarm through you. The noise was impossibly loud in the quiet of the corridor you were in. As you crouched behind a wall with your rifle ready for an ambush, you cautiously reached for the radio at your waist, lifting it up while dialing back on the volume.
“I know you are here, маленький предатель.” A voice nearly rumbled over the radio. You grimaced at the familiar muffled deep voice. The sickly sweetness of peaches always accompanying his presence was something you could nearly taste in your mouth.
It didn’t help that Nancy’s fucking perfume was accented by peach fragrance.
Resisting the urge to leave a few choice remarks, you reduced the volume of the radio to little more than a slight whisper into the air. You scanned the empty hallway ahead of you for any sign of movement.
All clear-
“You cannot hide, Зая ,” Stitch said, his voice carrying down the corridor. There was something about his voice almost savoring the dread it got from you. You risked leaning out once more to peer down the seemingly empty hallway. Where could he be hiding?
“I will find you.”
You further pressed yourself against the wall with your breathing coming out in halting little breaths in anticipation. You could hear footsteps from a distance coming closer and closer-
And then those heavy footsteps stopped .
“Oh, Bell.” Stitch sighed out in his thickly accented voice. You nearly swore that you could hear your very own heartbeat in that moment. There was something, daresay, intimate about the way he said your name for the first time. It was as if he savored saying those words.
“We’ve got a job to do.”
And then your vision flashed white.
How odd, you dazedly thought as you found yourself staring up at the large familiar, hooded figure. Instinctively, you reached for your Makarov at your waist and aimed it at him. Strangely, he didn’t react aside from the rather amused and muffled breath of air he let out from behind his mask.
You twitched at the scent of those damn peaches yet again. Damn it. Nancy and Stitch would make quite the pair considering how they both favored annoying the hell out of people with obnoxious scents like peaches .
“Hey, Peaches.” you said easily with your Makarov aimed at him. Yet the Perseus operative remained nonplussed.
He tilted his head to the side slightly before chuckling lowly, “Drop the gun, Bell.”
You nearly laughed with him at the ridiculous order. Yet when you tried to raise the gun higher to his head, you found yourself paralyzed with something clawing at your mind.
Don’t.
It was all too easy to let the hand aiming the Makarov fall to your side with the gun’s safety on as it dropped to the floor. Your fingers trembled with effort, trying to pick up that gun again because why why why couldn’t you raise the gun enough to shoot him-
“Isn’t it funny?” he said while amusement danced in his lone cerulean eye as he shook his head, “Adler put that crimson bunker door in your mind.” he said with a little mutter about амерѝка̄нскӣ and their foolish games.
Stitch took several sauntering steps towards you. Yet you couldn’t even bring yourself to step away with just one quick little order from him telling you to be still.
“But he forgot to throw away the fucking key.” he said, his face inches from you. You tensed at the smell of peaches growing stronger to the point where you could taste its sickeningly sweetness in your mouth. You bit your lip, instantly tasting the familiar metallic taste in your mouth.
His lone cerulean eye looked down at your lips in some kind of interest...fascination?
As the taste of peaches and blood mingled in your mouth, you felt something twitch inside of you.
You took a step back.
In that moment, you could have sworn Stitch smiled beneath his mask.
Suddenly, you lunged forward, driving your knee into his solar plexus, ballistic armor be damned. His shoulders moved, giving you just enough time to brace yourself when he slammed his fist into your abdomen. All that was on your mind was one thing:
He exploited something in you. And you needed to end this before he could do it again.
You made a desperate move for his rifle, gripping the stock as he turned it towards you. All you could hear was the crack ringing through the air.
You instinctively looked down, expecting to see a bloom of crimson on your clothing. Yet you saw nothing.
Against your better instincts, your attention was compelled to your leftside where there was...crackling of static coming from a radio. Strangely, you could hear distorted voices coming from it again and again.
That static, you winced.
You whipped around to face the current problem. Stitch tilted his head as he looked down at you, interest dancing in his eyes.
“ӱ̷̨̡̢̨̧̧̨̡̛̛͖̘̲̬̼͉̺͇̟͍̗̟͉̪̹̬̘͚̖̞̪͔̫̳́̋̇͛͗̃̈̈́̀̌̊̓̇̿̇̈̆̽̅̓͂̿̏͑̇̍̿͗̎̑̄͒̇̋̔͆̏̆̔͂͒̆̋͑͘̕̚͠ͅͅͅв̴̡̨̡̨̢̨̛̙̱̩̞̙͓̣͔͈̞͇͚͔̤̞̼̯̻̭̘̩̗̻̜̗̝͓̞̠͚̗͖̹͉͖͍̮̮͉̗̤̞͈̰̳̞̤̠̦̟͙̜̤̩̮̠̤̠͚̖̪̜̱̓̾͑̄̈̅̽̓̉̃̇̔̅̋̃̓̓͋̌̉̀̃͌͑̇̚͠͝͝ͅͅл̷̛͆͐̋́̆̾̿̓̉̑͌̅̏͊̏̀̍̿̊͑̓̇͗͊͗̅̉̅́̎̂̄̎̌̏̊́̐̐̎͐̉̔̄͒̿͑̉̈́̏̂̒̈̐̔̑̄̌̕͝͝͝͝��̢̢̢̧̨̡̧̡̨̢̡̢̡̡̡̢̨̢̛̛̛̛̻̲͓̤̞̟͉͕̙̙̝̳͍̝̪̤͓͕̠̤̹̺̺͔͍̯̯̹̤̜̱̺̩̯̣̯͎̺̗̰̪̘̼͈̟̯̣̜̬͓̞̠͉͔̼͔̥͉͓̦̫̼̟̜̖̬͙͇̠̠̪͍̣̱̰̦͖̹̮̠̝̪͔̬̺͓̩̜̪̼͇̞̳͙͍̝͚̰̳̥͍̯͙̼̙͚̬̭̤̺̮̝͍̯͚̜̼̰͕̜̱̟̖̠̻̹̙̭̲̺͎̮̙̹͙̳͚̹̭͍̘̯̝͖̝̼̬̜͉̟̫̮̹̳̥̝̤̹̫̖̻̗̲̣̘͉̲͉̞̘̥͔̯͔̼͙̼̣̪̰̣̼̰̼̱̼̂͐̐́́̔͊̋͑̅͗̊̂̔̃̄̓̇͗̽̔̈́̽͊͂̄͗͛̌̇̃̈́͋͋̋͋̐̆̅̎̈́̊̇́͒̑̏̈́̈́͑͛͌̎̆̓̕͘̕͜͜͜͠͝͝͠͠͠͝͠͠ͅͅͅͅе̷̨̢̧̨̢̡̡̧̢̧̨̡̨̧̢̧̢̧̡̡̛̛̛̛͈͍̬̝̭̻̺̬̭̞̖̠͓͉̟̻̲͓̭͈̗͈̖͙͙̱̹̜̫͈̖̟̟̪̰̗̗̻͚̹̩͇̺̞̫̥͇̮̱̤̪̩̘͕̝͙̠̥̹͓͙̼͚͔͙̫̖̜̠͕͈͔͚͎͙͇̙̥̹̥̼̲̖̟̺̗̜̭̠͈̩͈̤̳͖̬̳̜̺͈̯̣͔̮̲̻̯̹͍̞͇͎͈̦̯̘̱̩̤̟̪̘̺̘̳̜̱̮̪̬̪̭̯̳̖͍͉̗̣̣̠̥̞̯̝̝̭̰̞̠̲̞͙͙̠̹͍̮͖̪̖̗͔̬̘̮̪̱̤͉̖͔͇̞͈̭̗͖̹͕͚̩̼͙̤̗̥̭̞͔̪̙̹̥̼̜̳͙̞̤̬̖̺̩̜̤̲͉̊̇̆͋̔̑͑̄̈͊̋̔͐̾̍̔̇͗̀͗̑̽̄̔͂͐̓̎́̽̐̋͊͗̓̈́͒̄͂̈́̏̃̿͗͛͂͂͛͗͒͋͊̌̾̅̆̃͋̇̈́̆̊̾̐͋̅̾̅̄̉̋̊̉́̿̾̊̏̈́͒͛̊͂̐͆̅̈̂̑̈́̄̔̾̉͒̿͛̓̏͑͌̽̽̿̒̿̃̐̒̂́̒̑͆̅̎̆͌̌̌̓͆̈́̂̌͛͒̀̋̾̄̿̽̐̃͐̉͊̐͑̈́̑̒̓̉̊̈́͂̐̑́̆̌̃͊̓̊̀̓̇̅̓͊̈̑́̃͐͋̌͂̈́́͊̐̋̈́̏̇͂̉͌̅͛̓̃͊̋̾̒̓̃͗͗̌͗͌̂͐̈̑̍͒̔̽͆̒̎̂̌̿͗̄̓͋̈́̇̃̇̿͌̎̕͘̕̚̕̕̚̚̕̕̕̚̕͘̕̚͘̕̕̕̚̕̚̕͜͜͜͜͝͠͝͝͝͝͝͝͝͠͝͝͝͝͝͠͝͝͝͠͠͝͠͠ͅͅͅͅͅͅк̷̧̡̨̨̧̛̗̲͓̞̠͎̤̙͓̤̳̩̖̼̟͉̘̣͎̼̦̼̭̥̥̘͉͙̠̣̫̻̭͚͍̦̹̭͕̹͓͇̹͍̖͍͖̙̟͂̄͑̓̽̂͂͑̉͑̅͒͊̆̊̋̌̒̈́͌̓͊̃̄͆̃̽͂̂̓̍̊͌̒̒̒̂̕̚̕̕͘͜͝͝͠ͅͅа̶̢̡̡̨̨̤̠̖͕̗̖͚̩͈͉̟͇̥̹͚̩̰̳͔̝̗͓̭͙̪̺̰͔͚͖͎̼̩̥̖̠̼̬̩͈͙̠̞̮̻̗̜͇̫̯̠̫̙̗͚͈̭̟͎̘͍̩̗̖͕͍̮͙͓͕͈͖͙̱̳̇̅͋̒̆͊̚̕͜͜ͅт̸̧̢̡̨̡̧̨̧̢̧̡̛̛͎̤̝̤̯̘̰͙̳͎̣̪̹̻͙̤̦͎̬̼͎̮̬̺̼̣̟̠̖͙̠̰͙͕̭͉̖̲̜̙̫͇̜̤̥͓͎͙͈̞̱̪̙̱̺̝̰̳̰͙̩̰̳͚͎̖͍̱̰̺̟͓͇̮̰̦̞̮̼͖̺̖̘̜̘̼̱̤͎̘̳̙̩̦͍͚̤͇̭̗̜̪͕͙̦̗̪̮̤̣͈͓̺͔̩̮̞̹̬̙̪̱̝̫̮͈̫̤̫͉̘͔̤͈̻̝̙̖̺̼̩̠̗̞͕̂̒̊̆͐̓̒̀̀͂͂͂̄̒͋̓̍̅̈͗̀̽̑͆̉̂̀͂́̓͋͒́̍́̅̀̈́̒͑̕̚͜͜͜͜͜͜ͅͅͅͅͅͅͅͅ��̢̨̧̨̨̢̡̧̧̧̘̭͚̦̬͓̮̲͖̺̤̝̖͇̜̱͓̭̙͉̗̬̹̞͎͎͙̱̳̦̩̭͎̩̜͔̼͕͕͕̦̜̦̮̪͔̝̩͍̥̯̜̲͍͕̹͕̲̠̫͈͕̞̖̹̭͎̰̘̮͔̞̲̳̭͓͉̗̯̩͖͈̖͚͇̭͙̫̤͓̘̖͇̤̩͈̺͇͔̙͕͈͍͜͜͜ͅͅе̸̡̢̢̧̨̧̢̡̡̧̢̧̢̡̨̡̡̨̨̢̡̛̛̛̛͎̝̝̲͕͖̮̗̠͈͓̞̮͍̻̝͉̗̤̺͕̮̭͇̬̦̰̩͎̹̥̼̮̺̞͙̮̟̠̦͇͓͈̹̰͎̹̙̟̮̬͚͖̘̙̞͉̯͖̳̼̺̭͕̯͍̟̥̫̱̠͍͎̬͍͕̦͈̗̭̙̺͎͉͉͇̤̬̟̪͙̳͕͍͔͓̙̜͍̮̟̞̙̦̲͈̼̘̬͈͈̜͙̺̤̭̯̮̺͇̱͚͓̪̲̦̳̥͕̤̜̘̰̺̯̺̣͎̗̯̯͎͍͙̮̘̭͍͇̝̳͍̜͍͚͔̥̜̯̻̺͓͕̰̞̝̱͎̘͔̗̣͈͚͔̝̫͉̘̤̳̹̖̣̲̺̮̼̦͙̳̦̝̭̭͕͖̦̦̦͓͚̦̱͔͉̯̤̩̝̟̪̥̭̭̜͍̺̔͂̆̌̀͐̈́͒̌̍̉͂̾̔͆̀͒̿͋̋̆̑̌̑̊̏͌͊̄̽́͌͆͛̄͒͋͛̈́̒̓̌̇̔̇́̀̓̉̈́͗͆̈́̎̂͐̔̔͊̏̀̉͌̂̑̊̈̐̈̽̎̽̾͐͂͊̀͛̒͌̽̏̉̽̿̒̿͑̍͗̾̽͆̄̾̈́̅̄͂̽̿̀̀̈́̄̄̈́̓͒́̐́͑̐̈́̓̏̇̏̌̄̽̂͗͂̌̅̄̽̂̀̐̒̈́͋̿̃̒̔͐̾͑́͐͗̈̽̅̍̊̓͆͋̍͐̇̒̄̅̔̒͒̈͊̾̒̉̑̒̌̀̊̒͑̊̅̓̀͊͒̌̏͂̑͛͘͘͘͘̕̚͘̚̕̚̕̚̕͘̚̚̕͜͜͜͜͜͜͝͠͝͝͠͝͝͝͝͠͝͝͝͠͝͝͝͝͝ͅͅͅͅͅͅͅͅл̴̡̨̡̢̡̨̧̢̧̧̡̨̧̲͓͉͍̱͕͖͕͎͉̞̘̖̼̠̭͇̳͈̭̠͎͕͈̯͍͖̘͓̗̰̩̥̯̫̗͉̘̮͔̳͔̫̪̻̣̼͉̗̳̬̯̱̹̙͍͇̬̜̥͇̬̻̗̭̼͖̤̟̺̖̪̭̗̬̟̠͚̠̲͍̟̥̖̟̥͖̼̻̞͚̖̙̲̗̩̼̣͖͈͈̭̫̺̪͇̤̳͓̠̙̠̹̖͈̰̭̖̜͈̤̙̳̲̤̗̩̤͚̮̰̰̖͇͕̝̬̘̠͎̖̻̬̟̞̺̠̥̫͎̜̠̤̘̗̝̳͉͎̩͖̹̭̱͈͇͍̤̞̮͔̲̮̪̙̫͕̖͈̜̣̜̪̜͔̮̣͔̲̪̪̤̱̰͎̣̻͈̖̜̦̣̣̪̈́̂̈͌͊̈́̎́͐̓̉͊͊͐͆̾͒̓̏͘̚̚͜͜͜͜͜͜͜͜͜͜͝ͅͅͅͅͅͅͅͅͅͅͅͅь̷̡̧̨̧̢̧̨̢̧̡̨̧̨̨̡̨̧̧̛̛̛̛̛̛̘̻̲̙̦̹̯͈̯̤̫͍͈̗͔̭̙̘͉̳͙̰̖͔͔̗̤̰̭̹͚̟̟͉͙̹̬̰͉͇͔͔̯̝͓͓͚̩̘̜͕͔͈̤̘̹̣̳̫̘̝͉̖̯̪͇̹̼̗̻̮͙̠̬͍̠̮̯̘͖͕̝̭̲͉̰̻̩̤̲̺̗̘̲͚̤͎̙͇̲̠̭̦͓̦̤̥̫͖͕̤̗̹̹͕͇͇̗̳̯̠̥̱̱͔͖̗̹̠̫͕̠̗̱̤̦̙̯͙̗̰̞̮̮͔͍̭͚̖͎̪͎͈̥̙͕͍̣̤̭͈͔̼̫͍͚͈̝̇̇͆̉̇̾̑̓̃̓̆̉͋̈́̌̾̆̅͆̿̉̓̾̆̉̏̉̃̿́̍͒̓̋͑͐͒̓̌̂̀͒̈́̆̊͗̈̇͌̾͌͆͌̎̉̅̉͊͆͒͑̑͐̆͆̏̊̌̎̂̏̈́̑̅̈́̎̀͛̏͋̂̐̾̌̇̒̏́̎͗͗͂̾͌̅̅͌͘̚͘̚͘̕͘͜͜͜͜͜͜͜͠͝͝͝͝͠ͅͅͅͅн̶̧̡̧̡̢̧̧̧̡̢̧̨̧̧̧̨̛̛̛̬̣͇̥͓̪̖̺̥̦͚͚̼̲̬̙͈̲̰̬̬̩͇͎̪͔̤̯̼̥͔̫͚̗̩̫̗̩̭̯̯͔̝̯̹͚͖̪̼̘͍̞͇͖͓̲̺̤̞̠̮̰̩͉̟͖͈̫̦̟̘͕͚̲̟͍͉̹̳̗͈͇̱̮̜̞͎̼̥̗͚̮͇͓̮͍̞̠̻̮̳̳̣̲͔͉̥͎̮͚̥̪̮̺̫̙̭̭̞͚̱͇̝̤̥̭̺̙̯̩̦̠͔͙̘̯͖̯̗͕͇̭͈͙̫̦͆̑̅͐́̓͛͆̇͗̐̋̑̈͌̽̌̇͋̿̍̌̑͆̀͊̅̑̒̏̈͌̇̆̆̃̽͗̈̐͐́̊͂̊̉͌̑͒͌̚̚̚͘̕͘͘͘̕͘͜͜͜͜͜͜͝͠͠͝ͅͅͅͅы̷̡̧̡̨̢̧̢̢̢̡̡̢̨̛̛̛̛̛̤̘̥̦̞̳̖̲͇̮̝̰̰̣̖̹̜͔͎̱̱̠̺̼͙͖̫̳̼̺̞̻̻͉̮͔͉͙͙͔̳̰̼̲͕̭͓͍̪̬͎̙̝̤̝̜̻̩̼͖̜̝̤͈̝͔͈͚͖̘̜̭͈̦͕̬̠̖͚̳͚̙̥̲̣͚̩͈̬̯̙̘̠͎̻͎͈̜̜̣̬͎̱͔̪̙̜̯̮̐͆̿̓̓̈́̒̃̎̄͊̈́͋̏̍̈́͗̒̒͛̓̔͐́̅̈́̈͋̓̇̓͒͊̑̀̏̊̿̊͐̾͊̐̆̅̀̈͒͆̒̈̎̉̌̀̏̎͒̓͂̎̽͆̍̂͂̈́͊̓̾̏͑̇̕̕͘̚̚͜͜͜͝͝ͅͅͅͅй̸̨̢̨̨̡̛̛̛̛̛̛̠̲̟̘͚̼̬̫̬̼̮̼̮̤͈̫͙͈͉̝̬̻͈̤͙͍͍̈́̇̎͌͋̀̒̾̌̓̍̈́̒̎̓́̃̑͂̈́͑͋͛͊̎̏͗̅̆͒̍͂̈́͗̒̏̑͆̐̃̇͋͐̃̿͑̅͛̓̎͂͒̋̃́̐̾͌͑̈́̂͂̂̍̓̂̓̓̈́̎̏̊͐͌̆̑̎̂̊͌͐̋̀̊̆͆̂̓̐̔̄̐̓̂̐̿̏͒̔̂͛̄͗̑͋͂̔̔͗͐̇́̋̑͐̅̈́͗̓͒̓̍̿̈́̒̉̀͒̃͒̊̈̌̍̔̌͊̄̓́̔̅̃̏̇͆͒͆̐̉͑̐̐̑̐̉͋͐̄̾͊̽̐͋̊̂̂͛̆͆̿̑͂͗̍͊̀͗̍̒̇͂̍͛̕͘̚̚̕͘͜͠͝͠͝͠͝͝͠͝͠͠,”Stitch rumbled out, something in his voice almost excited. Before you could even react with the static crackling in your ears, you saw the blur of the butt of his gun coming at you.
And suddenly your vision went dark.
________________________________________________________________
You blinked. The crackling of static distorted your hearing as it overlapped with the words and sounds around you.
You saw Stitch walking alongside the lined up analysts with his soldiers standing behind them, their rifles aimed and ready.
“The first one to give us the microfilm will be…” Stitch trailed off, pondering over what word in English to use, “-pardoned,” he finished with a rather disappointed tone.
Any volunteers?” he asked dryly, looking over the hunched over forms of the analysts. Some trembled while others were simply frozen in place. You noticed how his attention leaned towards a particularly trembling figure.
“I know where it is,” Nancy piped up.
You blinked dazedly. It was almost like watching a drama, you laughed quietly to yourself. The twist of betrayal.
“̵̨̢̨̧̡̛̛̱̻̠̩͕͍̯̲̺͇͈̮̤͖̰̜̭̘̙̣̱̗̻̩͓̝̻̞̟̱̹̜̞̘͈̼̞̃̎̂̉͗͛̔̾̈́̃̈́̓́̿̾̽̅̔́̂̎͒̀̈̈͗̌͛̓͛̈́̕͘͝͝ͅН̸̛̰̫͖̭̼̬͈̯̲̪͇̅̂̊̈́͂̈̏̐̋̀̔̈́̐̾̌̏̄̏͆̑̂̍̐̽̍͊̍̃̎͝͝е̵̲̘͖̲͇̲̼̬̹̪̞̬̗̲̜̦̪̒͊̔̽̐̊͒̄͊̒̈́̎̌͜͝ ̸̜̩̤͚͉̠̦̇͗͛̇̋̐̈̉̾̽͒̅̆̍̂͌́̑͐͋̈̇̐̀͑̅̊̿͊̆̋͘͘͝͝��̸̢̨̡̣̤͖͉̦̟̭̤̻͕̙͉̖̮̤̩̮̭͉̮̭̺̦͈̠̲̮̙̠̻͙̙͕̣̳̣̙̪̙̬̠͒̌̊͐̃̾̅͗̋̋͒̐̒͝ͅͅͅо̶̢̢̧͍̰͔̺̝͈̤̰̥̦̭̬̠̗̖̩̯̱̖͈̳̙̗̞̗̠̻͔͉̰͔͉̠͓̼̬̝͚͍̟͌̇̈́̄̽̊̈́͂͒͒͜͠ͅз̷̢̡̡̢̡̰̯̪͎̗̭̘͍̺͚̳͓͎͍͚̥̰̬̬͔̰̰̹̞̪̰̲̺͓̗̪͖̮̮͎̞̙̪̝̙̰͎̞̪̭̠̭͎̻͑̉̓̆͌͌̊͌̔̾̅͆̽̃͌̋̏̈́̇̒̆̚͠ͅв̶̧̢̨̢̢̨̛̙̟̫̜͚̦̖̘̼͙̰̺̗̳̪̳̲̟̪̠̘̻̖͎̬̫͎͈͇̘̗͉̙̉͆͐̌̈͋̾͊͌̔͂̆̈́̎͑̐̈́͒̐̈͑̐̌̾̑͊̂͛̔̓̋̌̏̀̃̀̇͐͐̈́̾̀͘͘͘͜͝͝͠ͅо̵̡̜̞̖̱̰̙̫̝͎̰̻͈͓̓̏͑̅́̓̌̍̄̃̆̎̄͋̋͛͘͝͠л̷̡̢̡̡̧̨̡̡̖̥̮̭̺̞̪̩̤̯̰̖͉̙͉̖̘̰̝̟̗͖͉̝̞̝̤̪̭͈̮͎̻̩̙̼̏̎̀́̌̏̈̆͗̽͂̆̈́̉̿͐̒̊̀͆̾̇͐̏͊̔̕͜͝͝ͅͅя̴̡̨̨̨̢̢͇̥̳̥̱̥͎̟̤̳̣͓͈̣̬̖̯̟͎̜̤͉͔͍̭̩̱̟͉͚͍̩̰͈͈͙͔̳̝̝̞̜͓̠̟͍̮̘̤̠̑̓̿͛̃̓̿̾͛͜ͅͅй̴̢̧̛̛͇̪̬̦͓̙͚̭̭̗͙̳̩͙̬̜͈͉̘̖͔̫̳̤̭̮͔̰̠̜͈̥̭͉͚̣̥͉̼͓̳͔͕̙̲̟͖̣͖̲̺̳̝̩̬̬͍̰͍̈̄̆̓̽͑̏̆͐̏̑̊̐̂̃̅͛̽̾̋̌̐͆̓̀̃͂̓͗͂̄͘̚͜͝͝͝ͅт̸̧̧̨̡̛̦͈̮͙̹̖̦̯̯̠̜̖̰̘͙͉̞̱̔̋̋͆̾͊̒͂̓̃̊̓̿̾͑̀͗͋̋͐̍̾̍͗̅̑̀̿̽̑̈̓͂͒̿̃̔̈̇̆̈́̐̈́̃͒̚͘͘͘͜͠͠͝͝͝е̵̢̛͎͖͉͎̜̟͋̏̓͆͊̾̉̀̇͊̏̌͊̈͒͑̔̐͌̄̌̈́̊̏͑͛̈́̈́̈̄̈̎̄͐̏̄́͒̋̇̈́̏͘̕͝͝͝͝ ̵̡̧̧̨̢̩͍͚̫͍͙͈̱̭͕͓͇̱̠̯̼̳̂̑̆͐̀͊̽̒̓͊͂̾̈̽̍͒̈́̈́̊̄͆͑̾̒͗̋̉̓̋͂͌̔͛̊̅̏̈́͒̀̽̃͂̊̕͘͘͘͘̕͜͜͝͝ͅе̴͉̥̻͙͈̥̙̭̞̗̖̪̜̫͎̝̱̺̌̉̄̀̄̈́̂͋̔̇̓̾͋̇̈́̎̍͂͑̃͘̕̕͝ͅͅй̷̡̹̼͙͖̜̅͊̍͗̚ ̷̨̢̨̧̨̧̧̲̜͖̙̪̟̝̰͈͇̙͔͇̣͙̘̖̻̝̪͓̪͚̼̱͙̦̰̯̥͕̫̞̼̖̝͉̯̯̱̳͖͓̜̭̖̻͕̙͑̿̿ͅй̶̨̧̨̡̛̛̳̜̥͎̘̳͎̭͎̘̦̬͔̼̖̭͙͇͖͖̭͓͔͔͚͇̞̟̤͍̫̪̞͇̟̗͚̦͖͕̲̙̳͔̇̂͑̽̎̈̋̊̈̇̒̂̇̌̊̆̄̉̍͆͗̐̈̔̚͜͝ͅͅд̴̡̨̹̣̭̱̈̔͗̌̎̃͊͂̀͊̃̾̂̌̽͜͠͝ͅͅт̵̡̛̯̙̲̮̟̬̺̤͕̤̩̳̖̣̩̠̣͌̀͑͆͊̈̊̊͐̃̿̓͌͊̇̿̇̌̎͋̋̂̒͒͋̐͐̆̕̕͠͝͝͝и̸̢̡̢̡̨̗͎̣̦͖̭̥̯͈̠̫͙̯͖̪̝͚̥͈͕̘̫̤̻͇͙̜̘̞͎̭̲̞̱͈̙̝͖͓̠̣̺̗͔̭̖͚̹̱͓͔͛̈́̉̒͌̓̄̒́̓̈́̓̂̓͗̃̍̏̚͜͜͜ ̴̨̨̡̢̧̛̛͙̤̻͉̤͈̳̮͎͚͙̯̰͉̖̹͔̙̱̖͈͉̳̖̊̑̓̔͒̐̔̋́͆̂̓̇̉̎̽̈͆́̌̽̓͊̊̇̈́͗̎̓̚̕̕͘͘͠͠н̴̨̢̧̢̨̝̟̗̳̙̭̖͇̩͓̮͓̳̘̙̝̺͎͉̰͕̘͔̙̰̲̥̪̦̗̬̥̩̩͂̉͌̋̋͋͗̈́͜а̴̨̧̧̨̨̨̧̛̩̜̜̝̘̜̰̮͎͍̼̬̪͙̜̯̺͎̟̪͉͉̻͖̘̖͉͍͇̜͍̺̭̙͇͑͐͛͌̎͐̌̽̈́̿̎̉̍̓̈́͐̅̅̓͆͗̑͌̏͊̅͛̎̈̏̑̒͑̆͋̈́̎́̔͂̀̔͛̅̀͑͊̄͐͋̌̈́͑͘̕̕͝͝͝͝ ̸̨̧̢̨̨̡͚̯͚͕̳̣̝͈̥̭͔̮̜̗͚̠̰̣͇̞̱̦̣̫͚̞̘̘̗̠̞̤̤͍̼̮̭̮͇̘̥̜͕̔͌͆̅͆̉̀̈́̄͒́̍͊̎͆̍̈́̔͑͆̋͆̓̋͒̈̓̍̎͐͐̌́̑̈́̄͒͛͐̄̃̈́̿̏͆͛̽̕͘̕̕͝͝͝к̶̧̡̡̨̢̛̛̛̩̬̠͖͍̫̱͖̲̩̪͕̲͎̖͖͕̝͗̑͐͒͂̓̏̔͆̐̐̽̔͆̽̍̅̔̈́̊̽͒̆͌̏̈́̒̋̂̃̿͒͛̈́͒̓̃̈́̂̐̆͆̌̾̋͛͛̈͒͘͘̚͜͝͝͝͠о̸̡̡̛̩̯͇͙̜̘̠̘͓̗͚̖̖͇͇͉̠͚̣͍͇̞̯̝͎̮̦͔͎̩͓̜̘̖̼̠̳͉̣̭͉̱̘̙̠̘͉̫̫͎͉̀̎̋̄̑̅͗̇̍̏͆͊̽̂̍̎̾̊̎́̾̀̎͌͂̓̓͗̇̈́̎̀̈̇̑͠м̶̛̠͈͙̒͛̈́̒̓̍̾́̉̏̉̌̂̽̈̒̇̈́͒̓̾̇͗̑͊̂̎͆́̕̚̚͠͠п̴̨̢̢̢̨̛̛̬͕̬̣̳̖̬̫͎̬̬̘̰͖̠̠̰̟̫̹͙̺͔̘̤͙̱͈̪͍͚͍̥̙̙̩͚̱̹̯͕̻̃̂͑̅̅̐̑̈́̇̍́̔̉̋̉̍̈́͘͘͘ͅр̶̧̢̯͈̣̱͔̰͍̝̖͖͇̤̮̗̲̣̰̺̟̘͙͉͓͎̖̼͕͇̞̦̤̤̞̹̜͔͔̘̗͍̣͔͇̊̃̽͂͗͐̅̔̍̇̍̈́͒̅͊͘͜͝о̵̠̺̘̹͓̖̣̋̊̂̕͠м̴̡̨͖͕̙̝̮̩̠̻̺̣̫̲̘͎̪̝̻̼̳̼͕̖̊͐͗̉̊̽́̊̓͐̒̾̆̑͋͑͌̿̈́̂̓͛͒̓̑̇̂͊͘͘̕͜͝͝͠ͅͅи̸̡̢̧̡̢̨̡̛̭̦̺͓̞̩̪͕̠̞̗̗̯͙͚͓̦͍̖̟̗̜̤̣̝͓̪̣͔͍̰͉̙̱͖͙̩͚̲̥͔̼̤̫̪͕̣̪͍̘̰͎̪͐̄̄̄̑̂̈́̾̉̈́̒͌̿̎͋̃̇̿͑̇̈́̊̈̏́̿͌͑̀̚̚̕͜ͅс̷̨̹̹̳̣͎͎̳̦͎̥̪͕̭̞͇̜͉̟͍̣̰̻̺̪̠͈̟̞̠̮̫̬̞̬͈̰̳̱̹͙̞̖̜͍̜̲̈͗̂̇̀͜͝ͅс̴̧̨̬̜͖͔͓̹̠̩̟͈̘̟̘̳̙̙͔̻̫͎̤̲̠̫̞̳̝̻̯̮̹͌.̴̨̛͖͈͎͈͑͆̃̔̉̊͛̍̾̂͌̅̈́̌̾͗́̉͗̂͒̑̌̄͌́͒̅͋̈́̏̍̀̐̉͒͑͋̚̕͘͝͠͝”̵̛̛͓̬̲̟̋̈́̏̐̇̀̍̎̃̏̈̌̿͑̑͆͂͌͌̓̌̇̊̓̾͋̋̌̃͂͋͌̊̓̕͘̕̕̚̚͝͠͝͝
Something urged you to move , a nagging instinct clawing at the back of your mind.
And so you did.
You kicked at the legs of the Perseus operative standing guard over you, making him shout and pointing his rifle at you.
“Нет! Не убивайте ее! ” Stitch barked out.
Much to your surprise, the Perseus operative hesitated. You didn’t take a moment to indulge in that as gunfire erupted around you.
You instantly ducked behind the closest thing to you. After hearing the brief pause in gunfire, you made a mad dash to the cover of the desk. There was only one thing on your mind, more than the hostages, more than getting out of there alive.
Microfilm, you thought distantly.
You needed to prevent it from falling into their hands.
Somehow, your eyes locked onto that little container containing the microfilm filled with sensitive intel about the operations of Adler and his team. It was slick with blood and your eyes followed the trail of the blood to its originator.
Nancy.
She was shot several times in the shoulder and abdomen.
You blinked. That source of momentary cover had been her.
Н̷̧̧̡̨̧̛̲̣̳̭͇͎̻͇͙̪̰͎̟̫͖͍̭̤̜̟͈͔̠̖̪͔͙͇̱͈̹̳͉̫̖̻̖̱͓̰̞̙̫͖̿͌̄̾̂͑̆̌̐̽͗͂͒́̄͐̏̾̆́̒͋̈́̌͗͛͘͜ͅе̸̢̧̬̞͔̹̘͖͓̼̲͔̫̟͚̯̝͔̤̺̲̹̲͓̩̝͔̼̳̼̉̆̏̆̀̅̐́̈́̃̍͐̇̾̏̈́̑̽͗̆̽̄̋̑̓̃͐̽͊̒̃̾̿͆̅̄͆̿͐̇̏͗̆̕̕̚̕̚͜͠͝͠ͅ ̷̨̛̛̺̥̝̤̬͉̦͚̙͓̞̖̩͇̪̺͚̰̱̫͍̪̺̫̪͐̐̓̌̆̈̋̌̄̐̎̈́̐̎̑̑̃̈̂̓̈̃̂̉̓̉͑̈́͌̅͒̌͌̀̚͘͘͜͝͝д̶̡̢̧̧̨̨̛͈̣͈̘͕̲͉̭̠͈̫̬̺̝̟̳̺͎̣̞̰̼͎̯͕̮̤͎̪͚͖̞̤̠͚͉͓͙̼̠͔̞͕̉͗̎̂̎̎̍̒̀̈́̒̃̒͊̄̌͑̋̒͘͠͝а̶̨̨̢̡̨̨̨̛̩̜̜̠̞̝̟͖̞͚̰͖̦̖̲͕̤̘̤͙͉̭͙̠͔̗̠͉̱̯̭̺͓̣̭̜̞͕̬̮͚̩͉̹͓̄̉̈́̀̉̃͊̈́̋͒̾̓͛̌̂̏̋̈́̒͐́̾̏̿͑̓͆͐̓͆͂͌̄̚̕͘̕̚͝͠ͅͅͅй̵̡̢̡̨̡̢̨̛̩̰͚͔̪͙͈͖̝̦̥̰͉̬͙̱͈̹̼͇̩͎̙̦͔͉͓̭̰̼̰̙͕̣̙̬̮̠̯͎̳͓͔͖̯͇̱͎̭̻͌̑̎̆̄̔̎̊̾̍̅͗͛͐̂̑͂̆̔͗̌̈́̒̆̿̈̋̽̎͗̓̊͑̈́̋̊͂̌̐̾̈̚͘͘͜͠͝͝͠͠͠ͅͅт̴̛͉̲̘̳̬̘̖͙̀̍̉͛̿̃͗̈͂̓͑̈̌͋̍̅̓̏̓̂̓̽͌̓̂̐̉̉̽̂̑͑̆̊̔̈́̅͋̊͆̊͒̄̽̋͗̅̎̽̌͘̕̚͠͝͝͝е̷̧̨̧̨̘̳̝̱̰̭̘̟̝̯̘̯̤̖͓͍̦̯̝͖͎̠͓͍̳̺̘̞̖̪̓̃̋̀͐̃͒͑̾̏̊̌̕̚ͅ ̶̡̛̮̜͎̯̣͑̂͑̄͑̈̔̕͝ͅе̴̨̨̧̛̞͕̤̻͈̺̱̮̩̲͎̝̱̮̱̹̙͉͈͎͈͎̠͊̒̏͛͗̇̇̔̄̈́͊̇̒̍̓̂͒̈́̉̕͘͝͝͝м̴̛̛̦͍͙̱̹̦̼̱͍̤̺̮͈̓̿͒́̂̐̊͌̾̒̈̿̄͂̿̉͗̈̉͑̽̾͑͆̊̃̐̂͑̔̀̋̇͛͆͊͊̐̆͋̈́͗̐̚̚͜͝͠͠у̴̢̡̦̭̟̤͚̜̹̯̺̜̦̬̠̫̱̦͓̭͎̩͎̫͙̗̒̈́̓̿̓̄̊͗͛̐͛́̌̉̋̔̾̑̔̈́̓͗͂̈́̂̿̽͒̚̕̕͝͝͝͠͠͝ ̶̛̛̛̬̬͕͍̱̯͍̰̰̭̹̱̤̹̼̙̬͒̈́͛̀̾̎̃̉̍̑̉̇̅̈́̈́̓͛͒͑͊̉͛̋̆̍͗̋̅̄̽̃̈͘̕͜͝͝п̴̧̢̨̧̨̢̧͇̠̯̫̺̤͇̖͚̱̫͈̺̮̹̹̦͕̤̝̣͚̹͔̞̹̣̺̤̯̹̮̜̲̟̩̟̹̪͈̤͔̳̪͙͖̝̐̈́̈͐͑̏̓͑̔͆̐̌̐̎̽͛͐͒͂̔̈́̅̆̏̑̈̏̌̈́̇̕̕͜ͅͅӧ̷̡̨̡̢̢̨̘̟̫͚͕̮̟̻̹̺̝̦̪̮̦̖͎͖̩̮̤̗͎̦̼͇̙̳̲̜̖̳̗̭͇̦̣̣̞͙̙͔̹̱͔͔̣̑͋̋̒͐̐̍̏̈́́̈́̏͌̿̔̌̂̄̔̂͊͜͜͝͝ͅͅͅп̷̧̡̜̩̘͎̼̥̤̥̩͕͙̭̠͇̙̞̲͍͍̬̅̐̊̂̐̅͂̊͂͗̐͗̊̌̂͆̉̀̀͂̌͊̋͂̎̐͛̅͗͋͂̽̍͜͜͜͜͝͝а̶̡̬̳̜̹͍͖̥̱͈̭͇̣͙̪͖͓̙̯̙͓̮͖̗͔̲͔̳̫̳͎̱̱̩̮͉͓̙̣̤͙͚̻̏͒͊̎̄͗̋̽̂̾͆̋̃͑͌̑̎̐̉̐̽͒͆̓̄̍̇̅̾̈̑̌̿̂͂̉̉̐̔̈́̉́̏̒͒́̏̈́̑̾̎͆͘̕̕͜ͅс̴̨̧̡̨̡̢̨̦͇̪͙̲̙͓̦͚͕̝̖̤̩̥͎͚̥͙̘̘͈̪͕̦̻͖̤̜̠͖̼̗̦͉̫̱̥̩̯͕̱͇̜̱̪̬̯͙̞̝͑͗͌̌͆̈́̂̈́͂̽̄̏̓̀͐̂͗͌̄̄̐͒̍̾̽̄͑͑̈́̔͘͘͜͜͜͠т̶̨̢̛̛͖̙̬͓̼̞̳͉̜͚͈̬͉̫̣̻͖͎͕̭̙̼̪̪̟̹̲̝̙͔̝̲͙̎͋̔͋̓̋̿̓͑̇̀͋͛̅̈́͊̚͝͝͝ь̴͚̈́͜ ̸̧̭̦̦̟̼̩̪͓̥̮͖̻͙̦͎͎̲̙̙̱͖͉̮͎̙̲̼̈́̃͜͜в̵̧̨̨̡̨͚̤̻̯̬̞͉̗͚͇̮̺͙͔̺̘͔̭̫̗͉̺̹̮̖̙̩̣͙̈̽͗̎͊̉̔̌͋̔̂̍̕͜͝ͅͅͅͅ ̴̛̛̛̤̖͖̈̎͋̈̐̃̔͊̔̓̎́̑͐̌̊̂̓̀̀̌̎͆̈͊̎̃͌̎̒̏̏̕͘̕̚͝͝͝͝͠и̷̨̡̛̛̣̩͈̬͍͓̲͉͓̠̙̬̖͔̦̯͓̣̟̻̺̼̓͆̃̈́͑̑͋̔͋̌͋̑͆̊̂̿̋͊̔̏̃̈́̃̽̓͌̈̀̆̍̔̅͋͂̈̆̈́̔̆͐̽̈́͂͘̕͜͜͝х̴̢̡̛̠̼̲̼̗̣̲̫̗̖̰̣̩̼͓̣͚̜̜͎̮̖̟̗͉̠̝̺̞̯̪͇͓͕͎̰̘̞̜͈̝̺͎̥͎̣̬̞̤̼̥͙̲̮͕̙͋̔̽̐̍̌̆̓̈́̋̀͋͐̾͗̈́͆͘͜͜͜ ̶̨̧̢̡̡̰̟̭̪͙̻̩͎̩̦̰̼̗͚͓̗͉͎͈̮̭̠͚͙̙̬͈̳̳̬͇̘̙̖̘̖̤͉̘͈̯̹͓̬̳̹̳̍̍̄̑̋̈̓̌̄̈́̂͐͆̏̾̌͛̑̋̌̈́̎̈́̌̽̃̎̄̆̈́̏̑̑̃͒̈́̆̓͌̄̿̂̒̾́̍̃̉̏̈́̎͆̉̎̕͠͝͠͝͠ͅͅͅр̴̛̛͇́̓̄͌͆̀̏́́̈́̈̃̏͒͐̅̇̔̾͂͛̒͛̋̒̒͂͋͑̓̓̌̽̑͒̎̽͗̔̈́͒̏̚̚͘̚͘͝у̷̡̧̢̢̧̧̛̠͖̬̹̣̣̫͚̰̝̹̫͍͖̱̬̞̦͍̜̟̣̬̳̱̤̙͎̙̖̗̮̤̤͓̦͉̘̩͖̠͔̪͕̎̓̈́̒̍̔̆̍̒̿̐̅̃̈́̈̊͌̉̑̍̂̚͠͝ͅк̶̨̧̧̧̨̛̜̠̞͖̻̹͇̥͍̳̪̣̙̜̣̘͖͎̮̙̳̭̳̲̤̥̥̬̗͚̟͍̦̘̟̟͕̫̲̬̹͓̠͈̤͓̦͕̝͋̌̆̿̉̃̆͑̎̇̄͂̓̈́͒̓̂̌̓͛̂̆̓̌̋̍͊̐͆́̔̏̆̍̈̉̔̓͋̽̏͋̚͘̚͜͠͝и̶̨̡̨̨͓͍͈̝̞̤̰̳͉̜̮̰̖̝̼̜̰͈̖̯̣͔̻̪̲̟̜̹̟̥͍̭̱͔̜̘̝̱̫̭͎̪̤̖͍̠̉̏͒̐̉̉̇̑͋̓̓͛̅̕͜͜ͅͅ.̴̡̢̡̛̘͉̥̜̮̜͓͎̪͍̖͉̗̯͖̞͓̰̪̺̥̫͕̩͙͚̺͉̗̜̰̺͔̬̲͖̼̣̙͉̯̞̜͇̞̣̺͇̞͛͒̇̅͊͊̇̈͌́̑̈́̃̓̊̏̇̈̂̑͌͒̈́̂̐͂̍͊̐̐̃̌̎͛̊̅̄̑̽͐̆͂̆̄̑̓̏͘̚̚̚̚͝͠ͅ
The static grew louder and louder. Distantly, you snatched up the microfilm roll and looked down at it. It left a crimson mark on your hands with the blood.
It was almost instinct , you thought numbly. The metallic taste of the microfilm’s blood-slicken surface was acrid in your mouth as was the bombastic peach fragrance aftertaste of Nancy’s Giorgio peach-accented perfume. You swallowed the microfilm container quickly and turned your attention to securing yourself next.
As you found a pistol on the floor, you hastily gripped it despite the slicken feeling to it. It was covered in blood. You immediately took the safety off and leaned slightly out from the cover of the desk to take aim at the boots walking towards you.
And then you heard it click.
It jammed.
Shit.
The static grew stronger. You winced at the intensity. Where the hell was it coming from? You sure as hell didn’t see any radios or monitors on nearby since the main power was cut by Stitch and his operatives.
Forcing the static from your mind, you nearly growled in frustration…
—And promptly threw the gun at Stitch.
You blinked in surprise at the sound of metal hitting the material of his gas mask. He even recoiled slightly in surprise before a feral look entered his eyes.
Payback was one vindictive thought that entered your mind.
Oh shit was another that soon followed.
“I will kill your comrades one by one.” Stitch warned. Although, something in his voice easily told you he wouldn’t mind that outcome, “Stop.”
You stared at him through the fuzzy distortion of your vision.
Comrades , you pondered.
They took priority over you.
You relented, going down to your knees as he wanted.
Still, you refused to look up at him but rather gaze at the analysts still lined up, ready to be shot dead from a single order by Stitch to his soldiers.
“Give it up,” he demanded, gripping your face tightly with one hand. You simply looked up at him calmly. No .
“Приведи ее сюда .” Stitch gestured over to Nancy.
You watched as his operatives hauled Nancy’s body to your feet, leaving a bloody trail in their wake. Her hazy eyes stared up fearfully at you.
Gardenias and jasmine , you noted vaguely. You hadn’t noticed that about her bombastic Giorgio scent until it had been stripped away of its grandeur right before you in the blood and gore.
“P-please,” she begged, not looking at you but up at him.
Stitch chuckled lowly. He too must have been rather amused by her attempts for mercy from him of all people.
“Look at her,” he gestured to you with the Makarov in hand.
And so those watery cerulean eyes of Nancy’s gazed at you.
“...please.” she said quietly.
You only stared at her back blankly.
She was going to give up the microfilm and anything she knew to Stitch.
With this thought in mind, you watched the muzzle of the gun press against her head before you heard the gunshot. You only blinked when you felt something wet and warm on your face.
Distracted by the sensation, you were pulled away from your thoughts when leather stroked against your cheek in an almost affectionate fashion. You felt something wet smear against your cheek as his gloved hand stroked the skin there.
“Ruthless as always,” Stitch said with a rather approving yet feral look in his eyes as you gazed up at him. He laughed a little to himself before adding, “I’m glad the CIA did not make you soft.”
You blinked. Why...why hadn’t you said anything when they were going to shoot her?
She was a traitor, the thought came to mind instantly. But you nearly winced at the thought.
So were you.
You pulled away from your thoughts suddenly when you felt a firm pressure at your lips. His gloved fingers were pressing against your lips insistently with the wet metallic-smelling substance still on them.
Stitch stared down at you with that milky eye of his blank and emotionless. It contrasted sharply with his cerulean one filled with a rather keen interest, “Open,” he demanded.
You glared up at him.
“If any of your piece of shit comrades swallowed that, I would have cut them open like pigs,” Stitch casually said resting a knife at your abdomen as if he contemplated the threat of gutting you open.
However, the pressure of the knife against your abdomen lightened as he stroked a gloved thumb over your lips. He seemed a little too preoccupied with doing that for some reason…
“But you, Зая, I will make an exception.”
You blinked once again.
Somehow, that didn’t sound like a good thing.
Suddenly, his large gloved hand moved to grasp at your jaw, pressing down on it harshly. You nearly winced at the pressure, preparing yourself for the inevitable. He was definitely going to break your jaw as expected…
You glanced quickly over to the analysts still lined up like ducks to shoot down before Stitch’s operatives. They looked at you rather nervously and with concern. You blinked at them. Sure, you were about to get your jaw broken but you were sure you’ve had worse in the past considering your scars. Besides, it was hard to top MK Ultra...
Suddenly, you felt him press down on the joint and his hands forced your mouth to open even as you desperately tried to fight it. What the hell was he doing-
You blinked. Your eyes glanced down to confirm that yes-
Stitch actually was shoving his fingers into your mouth.
You struggled to bite down but that insistent pressure at the joint of your jaw kept you from doing so. His fingers forced deeper into your mouth until they reached the back of your throat. The moment they pressed there you felt your throat convulse and your eyes watered.
However, even as your throat convulsed as you gagged on his fingers, you tried not to dry heave.
But then underneath the dull taste of his leather gloves, you tasted that familiar metallic taste.
Blood.
There had been blood on your cheek which he had stroked with a gloved hand before brushing your lips with that same one.
Suddenly, you felt saliva run down your throat alongside his fingers.
And it was at that moment you felt yourself choke.
“сдавайся уже.” he said impatiently, withdrawing his fingers at last when he noticed you just couldn’t breathe. You only glared up at him with teary eyes blurring your vision with your hand immediately rubbing tenderly at your throat as you struggled to calm both your stomach and your breathing.
You opened your mouth to say something but then you heard something...beeping in the background. You turned your head to the side, seeing that it originated from one of the large cryptography machines sent from the highest levels of the cryptography department of the CIA.
You briefly glanced at the analysts who were nodding at you.
You blinked. What were they trying to say-
Suddenly you heard a deafening bang with a ringing- not static -in your ears-
And then everything went dark.
________________________________________________________________
Author’s Note: Special thanks to @samatedeansbroccoli for beta-reading this late at night last-minute! Without their feedback, I probably wouldn't have been able to post this chapter and this chapter would have been in a worse condition.
Thanks for reading!
#stitch/bell#tw: blood#tw: violence#tw: minor character death#tw: attempted forced vomiting#Stitch x bell#vikhor stitch kuzmin#vikhor stitch kuzmin x bell#cod cold war fanfiction#cod bell#fic: just like old times
51 notes
·
View notes
Text
Build Your Career with Great Learning Academy - Learn From Home
Learn the most in-demand skills for free and power ahead in your career

Isn’t it something very new and strange, that almost more than 70% of the world have been staying indoors and living in their houses with restrictions on not to go outside for quite some time now? Not everyone is used to staying indoors. Looking ahead to do useful and productive stuff would be something that everyone will be interested in. On that note, how would it be if you could take free skill development courses that could benefit not only your quarantined time, but also your career? What if you develop the right technical skills for your passionate dream to work in the field of Information Technology? What if your job hunting process after this could be more satisfying considering the fact you are talented and have the right skills for the right job? Here you are the right place for that. Get yourself enrolled with the free online courses by Great Learning.
So, What is this all about ?
Staying at home, you can choose from a variety of courses that provides you with Great learning and exposure on various technological topics.
All these courses would be self-paced i.e., suitable for your learning speed with no time duration to complete the courses.
You can also enroll into any number of courses as you wish.
The course would be a compilation of videos and lectures related to the topic and at the end of the topic you would be given an assignment and quiz submission which would be based on what you have been learning.
On successful completion, you would be provided with a certificate of completion within 24 hours from completion.
This would definitely be very crucial while finding employment opportunities based on your qualification. Who would not want a person who has all the technical skills needed for the jobs along with a passion to work? Seems much effortless, right? Yes, it definitely is very simple.
Who would these courses be suitable for?
These courses are suitable for all the students, graduates and professionals who have been pursuing their careers in the field of data sciences, artificial intelligence, cloud computing, machine learning, marketing/finance and many more. Wondering whether how it would be if all such courses would be free? Wonder no more, because, you are right, all these courses are absolutely free of cost. All you need is an effective internet connection, zeal to learn and explore and of course, time to spare.
What are all types of courses available?
So, there are various courses available on different technological based subjects. These are elaborated and explained as follows –
1.Data Science Courses
To get the best data science courses, here you are at the right place. To give a short brief about the subject; data science is the synthesis of tools, algorithms, maths, business intelligence and machine learning. In short, it is a subject that helps in the analysis of data that provides with the understanding of a business and helps in making important business decisions. Some of the courses available on this subject that is suitable for beginners would be –
Introduction to R : Gives an understanding about the programming language R that enables the learner to understand about R functions, Debugs, R commands, profile R code, etc.
Data Visualization using Tableau : Understanding data using visualized method like charts, graphs and other visual analytical methods.
Financial Risk Analytics : To get to know the risks in the market for a business is quite critical and this course provides with the right tools and skills to do that.
Marketing and Retail Analysis : Provide with the technical know-how to have a potential knowledge about the market and analysis of retail. Exclusively gives an understanding about a famous marketing technique, Recency, frequency and monetary value (RFM).
For intermediate learners, here are the data science and analytics courses available :
Statistical Methods For Decision Making : Solving important business problems with the help of using numerical data available and analyzing it using statistics is what this course is all about.
Predictive Modelling and Analytics : Wouldn’t it be great if you have the potential skills to predict the future of the business with the help of appropriate data model and analytical tools? And that is what this course would be all about.
2. Machine Learning Courses
Without being programmed, a machine gets to learn automatically from its analytical data. This is the common explanation for what machine learning is all about. Rest guaranteed that you get easily get into high paying jobs with the technical knowledge and being a kingpin in machine learning. So, the artificial intelligence and machine learning courses available for beginners based on machine learning are -
Python For Machine Learning : To make production use effective in algorithms, python is the programming language used. The two important elements of Python covered under this course would be — Pandas and NumPy.
Statistics For Machine Learning : Hypothesis testing, Statistical distribution, Bayes theorem and other basic statistics are some of the skills that could be learnt from this course.
Some of the Great Learning Academy Online Courses for intermediate level on machine learning are :
Data Visualization using Python : Doing data analysis using Python and making use of data visualization techniques to better understand the data is a skill that is most demanded by many companies and this course trains you in this skill.
Machine Learning Foundations : Would you want to learn about the most favored technique of Machine learning that encompasses algorithms based on supervised learning like Naïve Bayes and KNN? This is perfect course for you to learn that.
3. Artificial Intelligence Based Courses
Everything today in the field of technology is based on Artificial Intelligence. With that being said, who would be able to resist a person who is technically and well skilled in AI? Some of the courses available for the users are –
Introduction to Neural Networks and Deep Learning : Suitable for users at intermediate skill level, Data may not always be of the same type. Diverse data and complex problems are difficult to be analyzed and Deep learning is the right tool used to resolve such problems. Working right as effective as a human brain, you will be learning about basics and application of deep learning in this course.
Computer Vision Essentials : Most relevant for users with advanced skill level and having a basic understanding of Python and Neural Network, this course provides you with an understanding about digital imagery. You could equip your skills on Convolution, Transfer learning, motion capture, optical capture recognition, etc.
4. IT and Software Courses
Courses and basic skills based on the existing Information Technology field and software are commonly demanded today. Mostly suitable for the beginners, some of the courses available in this subject are :
Introduction to Full Stack Development : If you have spent sleepless night dreaming to be a full stack developer, then this is the right course for you. The learnings will majorly be on HTML and Cascading Style Sheets (CSS).
Introduction to Information Security : In collaboration with Stanford Centre for Professional Development, this course provides you with the basics about information security and upcoming advancements in this field. Additionally, you will also get to learn about cryptography and applications of information security in this course.
5. Cloud Computing Based Courses
Cloud Computing is a unique platform where companies could have their complete storage of databases, power sources, networks and many more. So, the following courses are designed in a way to various elements of cloud computing. The cloud computing online courses available are :
Cloud Foundations : This course is highly relevant for beginners who wish to learn about the basics of cloud computing, evolution and the history of cloud computing. This course also provides with the virtualization-based learning with regard to cloud computing.
Cloud Computing with AWS :Being one of the most popularly used cloud platform, AWS is used in this course to elaborate on the Storage, Network, Identity and Access Management. Practical application of such elements is also taught in this course.
Microsoft Azure Essentials : Microsoft Azure is one of the top experts in the field of cloud computing. Some of the skills that you could learn from this course would be Azure landscape, Azure Analytics, Azure API management, Azure Cognitive services, etc.
6. Marketing and Finance Courses
Not only courses based on technology, there are a variety of courses available based on marketing and finance that could help you in understanding the current trends in markets. Some of the best business intelligence and analytics course are :
Introduction to Digital Marketing : As one among the best advanced digital marketing course, this course covers various concepts of digital advertising, Facebook marketing and strategies for reaching the perfect audience for a product or service.
Business Finance Foundations : This course provides you with an overview about the accounting and financial components that is of vital importance in running a business. It also helps you to analyze financial statements and arrive at business conclusions.
Marketing Foundations : To understand about the current marketing trends and the basic of marketing like strategies involved, marketing mix, life cycle of a product, etc. are covered in this course. Insights on the satisfaction of customer and how to enable the customer to maintain loyalty is also given.
7. Big Data Based Courses
Making use of specialized concepts and tools, big data is used to perform tasks based on the larger quantity of data. The course provided based on big data are:
Mastering Big data Analytics : Being suitable for beginners, this course covers a vast dimension about big data. Staring with basic introduction about the subject, it is followed by tools and technologies of big data like Hive, Yarn, MapReduce, etc. Following this, further learnings are on the Spark framework and data formats like Avro, Protocol buffers, XML, etc.
Other Courses
Certain other courses that are provided for the users are :
Live Master Class : This is a live course where the industry expert lecturer or instructor comes live at a stipulated time to teach about a specific concept. Almost all live master class courses are for a time period of one hour. Some of these master class include how to ace coding interview, data structures and algorithms in Java, advanced cyber security course, etc.
Comprehensive courses like data science with python, machine learning with python and statistics for data sciences are also available.
Apart from courses, there are also various industry data science case studies on fields like healthcare, Insurance, marketing and retail, HRM, etc.
So, these are some of the course available that could help you grow as a professional in your field and thus, opening up new job vacancy much suitable for your skills. Making use of such courses in this time would definitely be of great benefit to you.
Machine Learning Interview Questions and Answer for 2021
#education#course#free education#online learning#great learning#great learning academy#cybersecurity#data visualization#data science#machine learning#artificial intelligence#cloud computing#python#data analysis#analytics#digital marketing#design thinking#online course#free course#e-learning#higher education#tutorial#online courses#online training#online education#certification training#aws certification#aws#Azure
4 notes
·
View notes
Text
SAFU NETWORK The Next-Gen of DEFI And Charity
SAFU NETWORK a decentralized finance project with charity program.

★ WEBSITE ★ MEDIUM ★ TELEGRAM ★ TWITTER ★ FACEBOOK ★ LINKEDIN ★ DISCORD ★ INSTAGRAM ★ REDDIT ★ ANN THREAD ★
Welcome To SAFU NETWORK is a decentralized finance project with Charity program integrated which is allowing users access to the transparent loans, insurance contracts, pooled investments, and more for a financial freedom that allow not just turning inefficient money into efficient money, but does so in a safe way. Safu network Charity program will help in fighting against poverty and help vulnerable class of people to survive, with this program, we aim to allocate 2% of Safu Network profit to charity program. Safu network has world’s safest cryptocurrency & Fiat Compatible wallet with all DEFI features.
OVERVIEW
The world of decentralized finance centers around the fusion of traditional bank services with blockchain technology. After blowing onto the scene in August 2018, the industry has already amassed a strong following and a value of over $67.65 billion. Almost 30 of the top 100 cryptocurrencies currently ranked according to market cap also feature on the list of DeFi projects. This number is likely to continue going up as more investors pour into the market. If you’re eager to enter the market, or sink your ties deeper into it the time is now.
What is Blockchain Technology?

Blockchain, sometimes referred to as Distributed Ledger Technology (DLT), makes the history of any digital asset unalterable and transparent through the use of decentralization and cryptographic hashing.
or
A decentralized, distributed ledger that records the provenance of a digital asset.
Digital assets are distributed instead of copied or transferred.
The asset is decentralized, allowing full real-time access.
A transparent ledger of changes preserves integrity of the document, which creates trust in the asset.
Blockchain is an especially promising and revolutionary technology because it helps reduce risk, stamps out fraud and brings transparency in a scaleable way for myriad uses.
What is Cryptocurrency ?

Cryptocurrency is a type of currency which uses digital files as money. Usually, the files are created using the same methods as cryptography (the science of hiding information). … Cryptocurrencies use ‘decentralized control’, which means that they aren’t controlled by one person or government.
This is different to ‘centralized’ electronic money and central banks. The control of each cryptocurrency works through a distributed ledger (a list of transactions shared by everyone), usually a blockchain, that serves as a public financial transaction database. #Bitcoin, first released as open-source software in 2009, is often called the first decentralized cryptocurrency.
Since then, over 5,000 cryptocurrencies (sometimes called ‘altcoins’, which is short for alternative coins) have been created.
In many cases, cryptocurrencies cannot be converted to real currencies; it is only possible to convert them to other cryptocurrencies, or to use them to buy things.
ABOUT SAFU NETWORK

SAFU NETWORK is a decentralized finance project with Charity program integrated which is allowing users access to the transparent loans, insurance contracts, pooled investments, and more for a financial freedom that allow not just turning inefficient money into efficient money, but does so in a safe way. Safu network Charity program will help in fighting against poverty and help vulnerable class of people to survive, with this program, we aim to allocate 2% of Safu Network profit to charity program. That is why SAFU is here for you.
SAFU Network has the world’s safest cryptocurrency & Fiat Compatible wallet, a multi-function wallet containing a high-yield farming and static staking pool which helps you Store, send, receive, Buy, sell, swap and stake for passive income quickly and securely with all the advantages of a other wallets and centralized/decentralized exchange, but you are retaining complete control of your funds within Your SAFUWALLET by Saving your Seed phrase, you have control to your funds and with Safe Network, Funds are SAFU.
Some of Bitcoin and some other cryptocurrencies’ weaknesses we can say:
Crippling slow transactions and accessibility loss.
Bitcoin transactions aren’t as fast as they must be, BITCOIN is now higher in terms of cost which limit people to own it and This is one of the downsides that pushed us in SAFU NETWORK join the system and create a SAFU MULTIFUNCTION WALLET). A wallet with a very high Speed in transactions with payment freedom, transparency of information, high security, reduced risks to near zero risk for traders and investors, low transaction fee and more.
SAFU NETWORK OWN TOKEN.
We have created SAFU TOKEN (SAFU) a Great Token build on the Binance Smart Chain (BSC) accessible and usable by everyone and most importantly a Fiat convertible token through different payments gateways. With SAFU TOKEN and our platform, you will generate passive income with all #DEFI features include but not limited to high-yield farming, static staking pool, Liquidy locking and more.
TOKEN INFORMATION:
NAME: SAFU NETWORK
SYMBOL: SAFU
DECIMAL: 18
MAXIMUM SUPPLY: 15,000 SAFU
CONTACT ADRESS AT BINANCE SMART CHAIN (BSC):0x3b529e373fa083a6e4f8d199a002ac4f7074f586

We are sure that you will venerate our thing and we intend to keep your treasuring growing, we are in like manner going to dispatch our Presale to raise resources for every last one of those development, considering the way that without you we are nothing, yet together we can, we need to raise resources for developing an assignment that Everyone wished to be significant for, we endeavored all our best to use self-saves anyway it’s an ideal chance to be helped by our monetary supporters, so we promise you to do all possible thing so your put money will return advantage in an amazingly short period of time for the people who need to make a short and low advantage and gigantic advantage for incredible monetary sponsor who comprehend what HOLDING in crypto is, we are endeavoring to do the going with:
Site structure 1.0 dispatch,
Pre-bargain
Posting on in any occasion 3–4 CEX following Presale, you can’t actually acknowledge that this anyway stay tuned for the check and see wizardry.
Keep Massive promoting and progression to guarantee our undertaking is known around the world
To help the powerless class of people all through the planet by appointing 2% of Safu network advantage to this reason program
To develop our assignment to the main level we wish and guarantee your assets won’t baffle anyone yet produce what you expect from us.
We will keep on doing divination to fulfill you.
SAFU NETWORK ROAD MAP

Join the Largest Defi project with Charity Program
https://youtu.be/h7epwjyE_RI
#SAFUNETWORK #Charity #project #Safu #bsc #btc
For more information please follow the link below:
Website : https://safunetwork.net/
Twitter : https://twitter.com/Safunetwork
Facebook : https://www.facebook.com/Safunetwork
Telegram : https://t.me/safunetwork
Medium : http://medium.com/@Safunetwork
DisCord : https://discord.gg/SDEr2SDnzN
Instagram : https://www.instagram.com/Safunetwork1/
Reddit : https://www.reddit.com/u/safunetwork
Ann Thread : https://bitcointalk.org/index.php?topic=5334706
Author:
Forum Username: Manuel Akanji
Forum Profile Link: https://bitcointalk.org/index.php?action=profile;u=2954998
Telegram Username: @Manuelakanji777
BEP20 Wallet address: 0x00F321558065b1c9dca5e6EcbeECE9B01F73D6E1
1 note
·
View note
Text
Cryptocurrency Exchange Development

Cryptocurrency is an internet-based, i.e. a digital currency which uses cryptographic functions to conduct the transactions. Blockchain technology helps the cryptocurrencies to perform decentralized transactions. These transactions are immutable and secure. The cryptocurrency is not ruled by any central government. It is independent and its decentralized feature made it more powerful. The immune system of cryptocurrency exchange development is not controlled by the government and has no interference with any centralized body in it.
The digital currency, cryptocurrency can be directly exchanged between the two parties via private or public keys. The transaction done in crypto includes very less processing fees and a wide platform to exchange the currency.
How Does Cryptocurrency Work?
The inventor of Bitcoin, Satoshi Nakamoto, announced in late 2008 about the development of Bitcoins that is a peer to peer electronic cash system that is going to achieve something that has next-level technology.
Digital cash announcing is the first release of Bitcoin which prevents double-spending. It is completely decentralized and has no central authority. Let’s lookout mechanism ruling the exchanging currency (cryptocurrency) technology. Some cryptocurrencies such as Bitcoin consist of a network of pairs where everything is recorded with a complete history of transactions and shows the remaining for the available balance of the account. For example, if Sam gives X Bitcoins to Nicole and assigns by making a private key. It is basic public-key cryptography, no party can be involved after signing transactions and within in-network, the transaction can be sent from one end to another.
Benefits of Cryptocurrency

1. Low-cost money transfer: A well known and best benefit of cryptocurrencies is when it sends and receives payments at very low cost and lightning speed. For example, million bitcoin transactions can be done in two and a half minutes and the cost for sending it might cost less. Some decimals dollars may be taken as a transaction fee. Now imagine if this money would have transferred via central financial intermediary then the fees would have been much higher and the action would have taken several days or in case, it was a cross-checking on the transaction and it would have taken a long time. The low fees associated with these transactions using cryptocurrency such as litecoin, etc. The cryptocurrency exchange transaction is an amazing and excellent payment system for transferring money at the international level.
2. An alternative to store your wealth: Imagine if your bank account is under Central Government and you follow the jurisdiction clause associated with your account then there are some chances when your bank account and address can be frozen in some situation. All it takes to someone accused of financial misconduct and this may be a big loss to you. The process may take long or verification of documents is done several times. In such scenarios, you may find yourself with little access to your money and may sometimes have no access to use your own money.
In this situation, cryptocurrencies play a vital role in providing you a way completely safe and quick way to access your account.
Bitcoin is the alternative store of wealth that only an individual can transmit using his or her private keys to the world and has only access to his wallet and hence, no one can even have rights to interfere in your transactions. In cryptocurrencies, no personal Bitcoin wallet can be frozen by any of the authorities.
Read full article originally published on Best Cryptocurrency Exchange App Ideas and Differences Between Popular Cryptocurrency Exchanges
#Best Cryptocurrency Exchange#Cryptocurrency Exchange App#Cryptocurrency Exchange Development#Benefits of Crytocurrencies
1 note
·
View note
Text
[previous con: block out]
Again, obligatory spoiler and wow... I’m wondering if it’s because I’m approaching the halfway point of the series [so far] that’s why these analysis posts keep on getting longer and longer? With the previous episode being an emotional whumpage on Nick, it seemed interesting that another member of this party would be hit as well... and not just metaphorically...

Part 1 - Episode 9 - The Man in the Middle Attack
A social worker comes to the house to help Nick open up, and it works -- until Molly and Jeremy find Nick’s secret cell phone.
The Con: Man-in-the-middle attack (MITM)
To quote wiki: In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe they are directly communicating with each other. [x]
In this particular case the two parties communicating are the Thompsons (whom in an act of concern had called a social worker to their home to help with Nick) and a social worker (an actual employee of the foster care system that isn’t a part of Nick’s ring of con artists).
The attacker? None other than Nick herself! To get back on track with her long con, Nick needs to make sure that the Thompsons’s trust and relationship with her was still in tact. Fearful that it’ll all come crashing down on her, Nick contacts Sam to assist her with the MITM. Sam insists that his own connections down at social services [and cue me not being surprised at all that it’s true to life for there to be corruption in govt. offices] made sure to slip Nick’s “case folder” in the bag of her assigned social worker, Ingrid. For the time being all Nick had to do was continue her act and convince this social worker on the fact that she’s content with the Thompsons.
When Ingrid arrives and informs the family that she was here to observe Nick and the Thompson family environment, Nick does her best to sell Ingrid on the idea that she gets along great with the family, even more so controlling the conversations away from the Thompsons and implementing her own complimentary tales. And for the most part it works... That is until Ingrid points out 1. she’s been a social worker for YEARS and can tell when she’s being manipulated and 2. don’t think that she didn’t notice that for all that Nick is extolling about how great her new family is, not once did they [the Thompsons] say how they feel about her! With concern for Nick, Ingrid advises they figure out a way that Nick can feel safe around the Thompsons to share her true self with them. Realizing that she can’t lie her way out of this, Nick reveals the barest hint of her real self: her own insecurities and doubt.
For the past couple of episodes, Nick has been slowly getting to know the Thompsons beyond being the “people that hurt her family” that we’ve been told (via phone conversations between her and Tony, her father). Her growing connection to every member of this family has been causing her to start doubting not just herself, but her own relationship with her dad, the one connection she has left of the life she had lost. It made sense that of all the “truths” she could have admitted to the Thompsons, Nick’s fear of betraying her “dad” by forming attachments to her new life was the one that she could give without truly hurting Tony or even herself (and her cause).
Before moving on to the next con, there are two more instances wherein MITM was enacted (both happening one after the other, post Ingrid’s visit).
First the minor one: Sam Harbaugh to Liz/Ed and Nick. In a momentary panic, Nick texted 911 to Sam’s cell phone and shortly thereafter he, in disguise as another one of Nick’s “social workers,” arrived to fix the situation... only for Nick to quickly insist that everything was okay after all. Before he left, in a surprisingly honest and sweet gesture, Sam departed a couple of personal information about Nick to Liz/Ed in an effort for them to bond with her. Though they were geniunely nice info for any parent to have, apparently it also sent a message to Nick (and the audience) that her former foster family actually did care about her (to some capacity). It’s the same foster family [of con artists] that earlier in the series we were made to believe that Nick didn’t have the best of relationship with. Once more this series reminds us that not everything is what you see.
The second one was... well, it was a LITERAL man in the middle attack: in this case, Nick, who was literally between Molly and Jeremy, attacked Jeremy. Frustrated with everyone, and including yet another adult (this one being a social worker), seemingly not seeing Nick the way he sees her; Jeremy stumbles upon what he thinks might finally be the key to the mystery that is Nick Patterson: a hidden cell phone in a vent above her bed. Because it made sense that only someone with something to hide could keep a secret second cell phone hidden in an out of reach space, right?
[Okay, full disclosure on this part: 1. I typed majority of this section at around 12 AM so my thoughts are a bit jumbled, and 2. rewatching this scene still pisses me off like it did the first time.]
There’s a lot of things that I enjoy about this show and one of them was that they weren’t afraid to have heart-wrenching moments of clarity like this one: where you realize that though Nick’s reasons for hiding her second phone probably had more to do with her con, there are legit children (both in actual homes, in foster care and orphanages) that NEED a hidden phone, or a hidden SPACE, because their current environment isn’t safe for them. That hidden object or a hidden safe space existed for these children as a necessity for their survival.
When Nick started arguing how she needed that phone “just in case”, I realized that regardless of her actual intentions, that phone was a safety net for her. And when Jeremy said that he “didn’t get it,” the first time I watched this exchanged I legit yelled “That’s because you’ve never been in a situation to need it!” I understand that Jeremy’s still a teen and that he’s really privileged to be given the chance of growing up in a safe suburban home with his family, but that’s what made it both frustrating and heartbreaking: he’s still a kid and a lucky one at that, so of course he wouldn’t understand any if at all the plights (good and bad) that Nick had to go through to get to this point.
We’re on episode nine, the final episode before the finale of Part One, and since Day One they’ve been building up the conflict between Nick and Jeremy to a troubling boiling point. At this time both teens have been emotionally wrought and through the wringer and it wouldn’t take much before their mutual distrust coupled with their unstable tension to create one big blowout!
And boy did it ever: Accusations flew, anger was traded back and forth, steps towards the other were taken, steps were taken back, and when one got way too close for comfort, Nick swung and her fist landed on Jeremy hard enough to Fade to black.
25 notes
·
View notes
Text
How To Host Your Mobile Business Applications? Let's understand in detail
A decade ago, you needed to have a site to advertise your services or products online to a worldwide crowd. Today, having a site isn’t sufficient to address your intended interest group’s issues – you must have an easy-to-use mobile application. For sure, smart apps have got vital in the cutting edge business world, and are demonstrated to add on to the change and can be a brilliant method to make a crushing impression by conferring a wonderful client experience. What’s more, on the off chance that you have a business application, a smartphone application server is an absolute necessity. Right now, we will pull up certain tips that will assist you in facilitating your mobile app development services for business apps.

For what plan Do You Need a Server for Your Business Mobile App?
You can’t effectively advertise your items or services with a business smartphone application that just has customer end processing. You certainly need a backend (application server facilitating) for your application.A mobile application backend is that part of your application which handles business rationale, data stockpiling, a ton of processing, and security. On the off chance that your business application utilizes at least one of the accompanying highlights, you will require a backend:
Extended security
Usage Analytics
Correspondence between clients
Advertising handling
Press Notification Service
Except if your mobile application performs ultra-straightforward assignments, you will require a smartphone application backend. The blend of customer end processing and backend server for smartphone applications bolsters further aides in bringing down the obstruction for clients who have lower-spec devices. Such clients will have the option to utilize your application, and you’ll have more command over the sort of client experience you wish to convey.
Tips to Manage Mobile App Backend:
As indicated by an RSA’s Group report, exchanges from smartphone programs and applications represent over 71% percent of the absolute illicit transaction. Additionally, it was found that around 10,000 maverick applications were answerable for 28% of all the beginning assaults.In this manner, you should have a business mobile application in a quick and secure server to abstain from troubling the clients. To host your application, mobile app development company ought to have the accompanying abilities:
Management of databases
System framework, including web servers
Management of Big Data analysis
Secure Cryptography
Server-side programming
Telecommunications networking

Vital Mobile App Hosting Tips
You have in any event three noteworthy facilitating choices for your business mobile application. How about we spread everyone inside and out so you can really gauge your choices while arranging the roadmap?
1. Code Your Mobile Backend Using Tools from Business solution’s provider
It’s astute to utilize the current instruments and formats to code the mobile backend. Some Cloud service providers, for example, Google, Microsoft, and Amazon offer vigorous devices that can assist you in coding your backend.
Despite the fact that it isn’t as simple as utilizing MBaaS, still, you can depend on the Cloud service or business solutions provider. Thus, Cloud specialist organizations will assist you in addressing the application facilitating prerequisites viably.
2. Code yourself
Coding Mobile backend all alone is a difficult assignment among the three choices that we have recorded, however, it accompanies a few advantages. Above all, self-coding offers you huge amounts of customization choices.
Be that as it may, in case you’re running on a confined spending plan, you can go without much of a stretch pick VPS (Virtual Private Server) hosting administrations like Hostinger, to get your application’s backend ready for action. It’s critical to locate an adaptable arrangement that the two meet your necessities, however, it doesn’t use up every last cent. In the meantime, when you’re saving money on the hosting arrangement, you can enlist an engineer or specialist to assist you with the arrangement. In the wake of coding the backend, you should discover a provider to have your mobile application since it involves a high expectation to learn and adapt, as it requires a wide scope of abilities we referenced before to tie it adequately. (NOTE: The alternative is just fitting to consider on the off chance that you need high customization and have the ability to accomplish it.
3. MBaaS
MBaaS a mobile backend as service providers are the most sensible choice for hosting business smartphone applications. The provider has the application and causes you to accomplish a quickened Time-to-Market (time between the main item thought and its conceivable accessibility on the shopper market). Subsequently, it’s essential that you pick the most suitable MBaaS for the application.It is significant that hosting business smartphone applications with the cloud is important on the off chance that you’re attempting to contact a wide crowd. In fact, cloud hosting presents a convincing propositionComing up next are the benefits of cloud hosting for a business mobile application:Ensured Uptime: naturally, cloud hosting is amazingly reliable because of its utilization of numerous servers. On the off chance that one goes down – your site just fetches from another.
High Speed: To improve stacking speed, cloud hosting ordinarily can utilize various servers simultaneously, or the ones nearest to your guest’s area.
Dynamic Scaling: Most cloud hosting platforms can progressively change the asset remittance, ensuring your site has as a lot of transmission capacity as it needs. It will likewise help you in arranging high-traffic time frames that hinder your site or application.Unique services served by prominent MBaaS providers:MBaaS specialists co-op overseas mobile backends, so you should comprehend what highlights and administrations they ought to have. Coming up next are the prominent highlights of an MBaaS organization:
Pop-up notifications
Client confirmation and the executives
Secure framework and storage capacity
Geolocation administrators
Capacity to explore different mobile platforms and gadgets or devices consistently
APIs relying upon your application prerequisites
Steady data storage
Convenience
Amazing client assistance
Capacity to use microservice engineering
Required Analytics
Top-quality MBaaS incorporates a cloud database, notification, storage, and client validation. It offers hosting administrations and incorporates crash revealing highlights and testing apparatuses, too. Also, the utilization of Google Firebase would empower you to dissect client communications and incorporate ordering, dynamic connecting, and analytics.
Advantages of Using MBaaSThe following are the reasons why you have to consider cloud hosting for business mobile applications:
Diminished Costs: It dispenses with the need to buy and keep up exorbitant equipment, which, thus, increments operational productivity and chops down the cost of hosting mobile applications.
Compatibility: You may encounter similarity or compatibility issues on the off chance that you utilize your own server for your mobile applications. Cloud hosting empowers you to benefit from its interoperability, rather than fixating on contrasts in the working frameworks. You can avail this facility from any IT outsourcing company.
Speed: Your business’ needs may change with time. Cloud hosting bodes well as it empowers you to overhaul your membership effectively and rapidly at reasonable expenses while scaling consistently.
Examination: All information is put away in the cloud, including worker data and the manner in which they use assets. This information can additionally be utilized to dissect the services and its effect on the expected clients.
Privacy and Security: When you have information in the cloud, unplanned deletions and equipment crashes are nearly dispensed with, as the data consistently has numerous duplicates. In addition, cloud-hosting service providers utilize complex safety efforts, guaranteeing that only approved clients can get to the association’s information.
Reviewing It UpYou ought to analyze and examine your hosting prerequisite cautiously to utilize the best facilitating alternative for your business mobile application. As a rule, MBaaS offers the most elevated advantages, particularly if your need is Time-to-Market.On the off chance that you need a high customization level, you may need to code the mobile application backend yourself. Right now, mobile application backend administrations can likewise help. In any case, do recall, it accompanies a variety of complexities and difficulties. We trust that in the wake of perusing this article, you have a superior thought of ‘how to have a versatile application’ and what to search for while picking where to have your business portable application and in case you need help you can avail the service from any software development company like CDN Solutions Group
.
#mobile application development#Mobile App#AI Mobile App Development#5G Mobile app development#mobile app developers#mobile app development company
1 note
·
View note
Text
Cryptographic Methods Used By Cryptography Assignment Help Professionals
Cryptography Assignment Help going before the forefront age was feasibly synonymous with encryption, the change of information from an understandable state to obvious hot air. The originator of an encoded message shared the unraveling technique anticipated that would recover the main information just with proposed recipients, thusly blocking unfortunate individuals from doing moreover. The cryptography writing Help regularly utilizes the name Alice ("A") for the sender, Bob ("B") for the planned beneficiary, and Eve for the foe. Since the improvement of rotor figure machines in World War I and the approach of PCs in World War II, the strategies used to complete cryptology has turned out to be progressively perplexing and its application more boundless. Prior cryptography was viably synonymous with encryption, however, these days Cryptography Assignment Help is chiefly in light of numerical hypothesis and software engineering practice.
Cryptographic Methods Used By Cryptography Assignment Help Professionals
Symmetric-key Cryptography: Both the sender and the collector share a solitary key in Cryptography Assignment Help . The sender utilizes this key to encrypt the plaintext and send the figure content to the recipient. On the opposite side, the beneficiary applies a similar key to decode the message and recuperate the plain content.
Open Key Cryptography: This is the most progressive idea in the last 300-400 years. In Public-Key Cryptography two related keys are utilized. The open key might be unreservedly appropriated, while its combined private key, remains a mystery. The general population key is utilized for encryption and for decoding private key is utilized. https://www.programmingonlinehelp.com/ have the best cryptography assignment writing services
Hash Functions: No key is utilized as a part of this calculation in Cryptography Assignment Help . A settled length hash esteem is processed according to the plain content that makes it unthinkable for the substance of the plain content to be recuperated. Hash capacities are likewise utilized by numerous working frameworks to encrypt passwords.
symmetric-key cryptography
Symmetric-Key Cryptography alludes to encryption strategies in which both the sender and recipient share a similar key. This was the main sort of encryption openly known until June 1976. Symmetric key figures are executed as either piece figures or stream figures. A piece figure enciphers contribution to squares of plaintext instead of individual characters, the information shape utilized by a stream figure. The Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) are square figure plans that have been assigned cryptography benchmarks by the US government. In spite of its expostulation as an official standard, DES remains very prevalent; it is utilized over an extensive variety of uses, from ATM encryption to email protection and secure remote access.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text
Where to Get the Best Computer Network Assignment Help?

The computer network can be fun if you put your mind to it. However, some students may face a difficult pursuing it for a number of reasons or two. That is why students come to us. We at computernetworkassignmenthelp.com have been offering computer network assignment help and even projects for the longest time. Our experts are specialist in both computer network and computer security. They are familiar with all the topics like Socket programming, Internet protocols, Cryptography, Threats, Firewalls etc. Some of the problems face are:
· Lack Of Time
Due to bulky academic schedules, students move from class to class, learning different unit after unit and at the end of the day they are left with a heap of complicated assignments with little to no time to get into all of them. Hence, they need us to take relieve some of that stress by doing their computer network assignment.
· Lack Of Proficiency
We do not judge whether you are bad in the computer network. We offer unbiased computer network help to those students who are not adept in the subject matter. You can schedule online sessions with our tutors if you need a guiding hand after your classes to help to learn and understand more.
· Lack Of Consistent Practice
The computer network may require a lot of sacrifice in order to pass the assignments and projects. It does not pay to only study theory, but one should consistently practice on the practical in order to be more adept with the different computer protocols etc.
This and more lead students to seek our professional services below are some of the reasons why we are the best computer network assignment help website:
· Experienced Experts And Tutors
Our experts and tutors have PhDs in different areas of computer networking and data communication. They are dedicated and work round the clock to ensure you get top quality solutions to your computer network assignment. The best part is that you can schedule a session free of charge with our tutors at any time on our website.
· 100% Plagiarism Free Content
Our team of talented and experienced computer network experts and specialists are under strict instructions to ensure all work is done from scratch, hence eliminating plagiarism. You can rest assured that your work is both original and unique. Exclusive only to you.
· Top Quality Solution
Our signature quality is the high degree of quality solutions that we provide to our clients on their computer network assignment. All assignments and projects are thoroughly researched and relevant. We ensure all your instructions from referencing styles to the output format etc. are followed. You are guaranteed to score a top grade with our solutions.
· 24/7 Online Customer Support
Our customer support team is available round the clock to provide you with the best professional service. You can contact us either via email or live chat from our website. You are guaranteed a quick response from us at any time.
· Economical Prices And Amazing Discounts
Our prices are the most economical, fair and pocket-friendly prices for the quality professional services we offer than any other firms out there. We have been at it long enough and we are more passionate about our client’s success. That is why you only pay when you are 100% confident with the quality of our work. Contact us today at computer network assignment help
1 note
·
View note
Text
BENEFITS OF B.TECH(HONS.).CSE - CLOUD TECHNOLOGY AND INFORMATION SECURITY WITH I-NURTURE ADD KEYWORD GEETA UNIVERSITY
B.Tech (Hons.) CSE - Cloud Technology and Information Security is a four-year undergraduate program that has been gaining immense popularity in recent times. With the increasing adoption of cloud technology and the growing need for information security, this program has become a preferred choice for students who are interested in pursuing a career in the field of technology.
One of the most significant advantages of pursuing BEST UNIVERSITY IN HARYANA FOR CLOUD TECHNOLOGY AND INFORMATION SECURITY WITH I-NURTURE is that it offers a comprehensive understanding of cloud computing and information security. The program provides students with the knowledge and skills required to develop and maintain secure cloud-based applications and systems, which are essential for the success of modern businesses.
I-Nurture is one of the leading education providers in India, and it has collaborated with Geeta University to offer this program. The partnership between I-Nurture and Geeta University ensures that students receive a high-quality education that is relevant to the industry's needs. The curriculum is designed to provide students with a strong foundation in computer science, as well as advanced knowledge of cloud technology and information security.
The program focuses on various topics related to cloud computing, such as cloud architecture, cloud security, cloud storage, and cloud deployment models. Students are also introduced to the concepts of virtualization, scalability, and elasticity, which are essential for building and managing cloud-based systems.
Another crucial aspect of the program is information security. With the increasing number of cyber threats and attacks, the need for information security has become more critical than ever. The program provides students with an in-depth understanding of security principles, including cryptography, network security, and data protection. Students also learn about the latest security technologies and tools that can be used to secure cloud-based systems.
Apart from the technical knowledge, the program also focuses on developing critical skills such as problem-solving, communication, and teamwork. Students are encouraged to work on group projects and assignments, which help them develop their teamwork and collaboration skills. Additionally, they are required to undertake industrial training and internships, which provide them with real-world experience and exposure to the industry.
Upon completing the program, students have a wide range of career opportunities available to them. They can work as cloud engineers, cloud architects, cloud security specialists, information security analysts, and network security engineers. With the increasing adoption of cloud technology, the demand for professionals with expertise in cloud computing and information security is expected to grow significantly in the coming years.
In conclusion, BEST UNIVERSITY IN HARYANA FOR CLOUD TECHNOLOGY AND INFORMATION SECURITY WITH I-NURTURE at Geeta University offers an excellent opportunity for students who are interested in pursuing a career in the field of technology. The program provides students with a comprehensive understanding of cloud computing and information security, as well as critical skills such as problem-solving, communication, and teamwork. The collaboration between I-Nurture and Geeta University ensures that students receive a high-quality education that is relevant to the industry's needs. Graduates of the program have a wide range of career opportunities available to them, making it an excellent investment in their future.
#BEST UNIVERSITY IN HARYANA FOR CLOUD TECHNOLOGY AND INFORMATION SECURITY WITH I-NURTURE#top universities in PANIPAT
0 notes
Text
Satori (Between the Lines) - Part 2
[Chapter 1]
Sakura willingly goes along with Ibiki, allowing him to tug her along through the Intelligence Division with Inoichi on their tails. She hasn’t been to this section of the Intelligence Division before, these upper floors that have actual windows in their walls. Sakura looks around avidly, basking in the natural light even as Ibiki pulls her toward the end of the hall. There are no people walking around these halls, though Sakura notes that the rooms that line the hall are marked with a simple, beautiful sign:
Archives.
Her eyes round and her hands twitch with the desire to get a hold of the documents within and crack open their secrets.
Her pace slows and Ibiki glances down at her. He catches the focus of her attention and chuckles, a low, rasping sound that emerges from his chest with an almost rusty quality. Sakura privately wonders how many years it’s been since he’s laughed at something so simple, something not involved with T&I. From the look on Inoichi’s face, it may have been before she was born.
“There’ll be time for that later,” Ibiki says gruffly, releasing her arm and, with only the briefest of hesitations, ruffling her hair. “Right now, however, I need to make introductions.”
“Why are we here?” Inoichi demands. “Sakura-kun is here on an Academy class assignment,” he continues, stressing Sakura’s current rank and standing within Konoha. As an Academy student, she is not yet anyone by shinobi standards. “Whatever you’re plotting needs to stop.”
Ibiki crosses his arms, scowling at Inoichi. Somehow, it is less terrifying than his laugh. “She’s got skill; all the more so for being a mere Academy student. Let’s let our Strategist decide whether or not she can be useful elsewhere. Besides, the Academy’s lessons have been subpar and lacking in recent years; I’m sure she needs herself a challenge.”
Inoichi frowns, turning red as he glances between the disparate duo, but he bites his tongue. Instead, he gives Ibiki a stern look before stepping to the side.
Ibiki strides forward, slamming a hand on the door before sailing through, not giving the occupant a chance to respond. Sakura meekly steps in behind him, taking a moment to assess the room. It is more spacious than the room that she’s been working in, but it is filled from floor to ceiling with all sorts of papers: dusty tomes, huge scrolls, and loose leaf paper. Her eyes go wide as she reads some of the titles, realizing that some of them are more advanced texts on cryptography.
Her fingers itch to get a hold of them.
A drawn out sigh interrupts her daydreaming and Sakura snaps to attention guiltily. She looks to the sole occupant of the room, nearly obscured by the documents on his desk. He is dark haired and scarred, with the signature small pupils of the Nara clan.
Nara Shikaku, the Jonin Commander of Konohagakure.
Sakura swallows, mouth and throat suddenly dry. She knows she has to be in major trouble to be brought before the Jonin Commander. Will she be expelled? Kicked out of Konoha? Her thoughts whirl as she remembers whispers from the marketplace. Tortured?
Without conscious thought, Sakura shrinks back against Ibiki’s leg, trying to hide in his shadow. He glances down at her, eyes going distant as he remembers another who once stood in her shoes. He gruffly shakes the errant sentiment away, placing a hand on Sakura’s shoulder and shoving her out in front of him.
Shikaku glances among the three of them, taking in the terror on Sakura’s face, the resignation on Inoichi’s, before finally settling on Ibiki. “Why did you bring an Academy student into my office?”
Ibiki cackles.
Cackles.
From the way Shikaku pales, Sakura gets the feeling it isn’t a normal occurrence, at least outside of the interrogation room.
Ibiki places both hands on Sakura’s shoulders. “This here is a new protege for you!”
A few things happen at the same time:
Inoichi exclaims something, probably along the lines of, “Absolutely not! She’s a child!”
Shikaku’s gaze transfers to Sakura and she receives the full brunt of his attention and scrutiny. His eyes are keen and Sakura remembers why, in a village full of Hyuga, Uchiha, and Aburame, the Nara are still considered the most intelligent clan.
Ibiki’s hands tighten on Sakura’s shoulders, almost to the point of pain, but it reminds Sakura of the confidence in his voice as he introduced her as a new protege. Ibiki doesn’t even know her full name, yet he has confidence in her.
Maybe, maybe she can confidence in herself as well.
She straightens beneath Shikaku’s gaze, meeting his eyes head on.
His brow quirks slightly, but he gives her a smile that relaxes the lines and scars of his face. He has a kind, tranquil look about him.
Sakura thinks that she may like him.
“Ibiki, you so rarely take an interest in anything outside the interrogation room,” Shikaku says, voice dry. “What games are you playing today?”
“No games,” Ibiki replies. “She’s here on a field experience assignment from the Academy. She sorts the coded documents by recipient.” He strides forward, placing the document from Fox in Shikaku’s hands. “I needed a document pulled that hadn’t been sorted yet. She’s competent enough at code to know at least some of their content. She pulled this for me when I came in asking for it from Inoichi.”
Sakura sees the way interest lights Shikaku’s eyes. He turns to Inoichi. “Is this true?”
Inoichi hesitates for a moment before nodding. “Sakura-kun has been teaching herself ciphers in her free time it seems.”
Shikaku hums, glancing down at the document for a few long moments before lifting his gaze to Sakura. “So I see.”
He leaves it at that and Sakura resists the urge to fidget beneath his penetrating eyes.
“Is that it?” Ibiki demands after a few moments of silence go by.
“Not quite,” Shikaku says, a slow smile curling up his lips. “Sakura-san, tomorrow when you report for your assignment, come here to my office. I’ll have work for you.”
Sakura’s never experienced the peculiar intertwining of dread and excitement before, not until this moment.
She thinks she may like it.
And that it is a sensation she’ll need to get used to. She’s certain she will be feeling it quite frequently moving forward.
“Yes Nara-san,” Sakura says, bowing slightly before she is hurried out the door by a shell-shocked Inoichi and a giggling—giggling—Ibiki.
Just wait until she tells Ino!
“Lift your elbow,” Ino instructs, circling Sakura. “Almost got it—” Ino grabs Sakura’s arm, adjusting it to her standards. “Perfect. Now, hold that position.”
Sakura does as Ino says, though she cannot help asking, “Don’t I need to be holding a kunai?”
“Not yet,” Ino replies. “Genma-senpai says you have to master the forms first. Hold that position.”
Sakura hums in agreement, afraid to nod and break form. Her arm feels awkward to be held at this angle, away from her body. She still doesn’t feel at home in her body. Sakura wonders if it is because she’s so used to hunching over and curling inward. She rarely stands with her shoulders put back or sits with her legs spread wide. She’s spent years trying to make herself smaller and less noticeable; it’s hard to unlearn old habits. But to be a shinobi…to have the confidence needed to push through…learning new habits is necessary.
“It reminds me a bit of what Nara-san is teaching me,” Sakura says, holding the form to the best of her ability.
“Shikaku-oji?” Ino says, tapping Sakura’s arm to get her to raise it again. “What about codes is similar to weapons?”
“Well, they aren’t that similar, but Nara-san and Shiranui-san’s approaches are,” Sakura replies. “Nara-san isn’t letting me decipher any codes right now. Currently, he’s having me read about the history of codes among the different nations. I’ve been learning all about the syntax of multiple languages so that I can understand how codes are created. If I can master these skills, cipher cracking will become simpler. I’ll understand the actual mechanics behind the process.”
“That’s almost exactly what Genma-senpai said!” Ino exclaims. She assesses Sakura’s posture for a moment, nods, and turns a handstand, holding herself up with her legs pressed together. “It’s wise advice, but it’s kind of boring, honestly.”
Sakura wrinkles her nose, thinking of the dry writing she’s been pouring over for the past few weeks. Her arm throbs, reminding her of the tense posture she’s been holding. “It can be. Nara-san says it builds character.”
Ino is silent for a long moment. “You’ve held the position long enough now, Sakura.” Sakura drops her arm, rubbing it absently. Ino looks up at her from her handstand and grins. “There are ways to practice and learn while having fun. Wanna race on our hands to that tree and back?”
Sakura rolls into a handstand of her own. “You’re on!”
“This one is honeysuckle,” Sakura says, pride filling her voice as she identifies the orange flowers on the bush. She reaches forward, gently plucking the flower from the stem. “Ino says that in the language of flowers it signifies happiness and devoted affection.”
Torune hums, kneeling down at her side. “The moths like to pollinate these flowers after dusk. During the day, they tend to be dominated by hummingbirds.” Sakura sees his smile peek out from behind his high collar as the near constant buzz beneath his skin kicks up a notch. “The Aburame insects have their choice of any flower they want.”
“Oh yeah?” Sakura asks, turning the pistil and petals toward Torune, placing the bottom end of the flower up by her lips. “So can I.”
She closes her teeth around the flower, sucking on the receptacle. Sakura taste the sweetness of the honeysuckle and grins around it. The smile widens at Torune’s wide-eyed stare as she picks another and offers it his way.
“Ino may know the language of flowers and you may know which insects like each one, but I know a couple of secrets myself,” Sakura says.
Before becoming friends with Ino, Sakura was a loner, an observer. She listened to the stories of others, in the Haruno shop, and in the streets as well. She also spent time alone in the forests of Konoha. Not outside the walls and certainly not the Forty-Fourth Training Ground, but she knew her way about the copses of Konoha. She even explored a bit into the Nara Forest, not far by any means, but still enough to feel confident navigating through parts of it.
Right now, however, Sakura and Torune are on Aburame property, exploring the sprawling estates full of untouched wildlife. Sakura enjoys the tranquility, the quiet song of life that thrums all around them. It’s an uncultured paradise and Sakura loves every inch of it.
Torune takes the flower from Sakura, copying her motions tentatively. He pauses, glancing over at her. “It’s sweet.”
Sakura giggles at the wonder in his tone. “Of course it is. Don’t your insects let you know how they like their meal?”
Torune sits silently for so long that Sakura begins to worry that she’s crossed some unknown boundary. Finally he says, fists clenched tightly, “They don’t consume pollen.”
“Oh, I didn’t realize,” Sakura says, reaching out and taking one of his gloved hands in both of hers. She runs her hands over his fist, patiently waiting for it to relax beneath her touch. When it finally does, Sakura laces their fingers together. “What do they eat?”
“They’re different than the usual Aburame insects. They aren’t kikaichū,” Torune says, gaze down and focused on their joined hands.
Sakura, sensing his rising tension, places her free hand on his knee. “I’d guessed that they were different,” she says softly. “You don’t need to tell me if you don’t want to.”
“I want to,” he replies, tightening his hold on her hand. “Friends share secrets, don’t they?”
“They do,” Sakura says. “But that’s sharing secrets, choosing to tell those secrets when you feel comfortable. Friends do not force friends to tell secrets.”
“Okay,” Torune says, breath rattling out of his chest as he exhales. The buzz beneath his skin has reached a point where Sakura can feel the vibrations in his hand and knee. “I want to share this with you though. I just haven’t done this before. Some of my relatives are…intimidated by them, by me.”
Sakura swallows at that; the Aburame are known for being apathetic in the face of even the most dire circumstances. For them to fear Torune, a child…
Still…
“Torune, you are my friend,” Sakura says, her headband suddenly weighty beneath her words and promise. Ino has taught her the meaning of friendship and Sakura suddenly realizes the duty she owes her friends. “I will not turn away from you, whatever you tell me.”
Torune nods shakily, reaching out with his other hand and grabbing hers from his knee. They sit like this, facing each other, surrounded by the fresh, sweet scent of honeysuckles and the constant thrum beneath his skin.
“I carry the rinkaichū, like my father and mother before me,” Torune says, head bent in fear. “Both my father and mother are gone; so I am the last and only host. The rinkaichū are different than the kikaichū; they feed on living flesh, not chakra. With a mere touch, I may infect and kill someone.”
Torune goes to release her hands, but Sakura grips them tightly.
“So?” Sakura asks, keeping their fingers intertwined. “That’s a useful variation to the Aburame kekkei genkai. I know it will come in handy out in the field.”
“Aren’t you scared of me?” Torune asks, body buzzing with agitation. “Why aren’t you angry? I’ve touched you—I’m still touching you—and I didn’t tell you. I’ve endangered you because I’m selfish.”
“I’m not afraid, Torune,” Sakura says. “You aren’t a scary person. Even if others say you lack control, I know the truth. You can control yourself, when it counts. I trust you with my life.”
Torune stays quiet so Sakura does too, waiting until he is ready. She’s said what she needed to say. Besides, she thinks something of what she said got through since he is no longer struggling to escape her touch. She notes idly that the sun is beginning to set over them.
Finally, in the barest of whispers, Torune says, “Really? Do you mean that?”
“I do,” Sakura replies, making her voice as firm as she can, imitating the way Ibiki and Shikaku speak. When they talk, people listen intently. “You know, I think it’s amazing that you alone are capable of carrying on your parents’ legacy. It’s almost like they’re still standing with you.”
Torune sniffles and, when he draws one hand away, Sakura lets him, keeping her gaze averted out of consideration as he removes his goggles. She rustles in her pocket, withdrawing her weapon cleaning cloth. It’s a coarse cloth, certainly not suited to touching skin, but it is clean and unmarked by the usual stains of oil. She passes it to him and accepts his quiet thanks.
“I didn’t think of it like that,” Torune says eventually, voice hoarse and still sniffling a bit.
Sakura hums, looking up at him. He looks mostly put together, though Sakura cannot see his red-rimmed eyes behind the goggles. She leans in, drawing him into a hug. As she embraces him for a long time, smiling as he melts into the hug, she nestles her chin onto his shoulder and looks beyond.
The dusty wings of moths beat as they descend upon the honeysuckles, drawing free their pollen. Sakura smiles and closes her eyes, knowing that, regardless of what happens from here, her bond with Torune is firmly forged.
She won’t be shaken from her friends. Not now, not ever.
“You seem pensive.”
Sakura looks up from the dusty tome, startled by the interruption. Her thoughtful frown turns sheepish as she meets Shikaku’s piercing gaze.
“Sorry,” she says, ducking her head. “I suppose my thoughts wandered.”
“Where to?” he asks, folding his hands on his desk.
“It’s foolish,” she demurs.
“Tell me anyway.”
Sakura takes a deep breath, keeping her eyes focused on a point beyond Shikaku’s forehead. She cannot look into the banked fires, his eyes like hot coals. Calm and settled, for the moment, but easily stoked into a blazing crescendo of flames.
“I’ve enjoyed the reading you’ve assigned, truly,” she begins, not wanting to appear in any way ungrateful. “It has vastly improved my knowledge of cryptography. However, what these books describe is so different from the ciphers used in the missives that go through the Intelligence Division. I’ve checked.”
Shikaku hums, expression unreadable. “What do you mean by ‘different?’”
“They are…simple by comparison,” Sakura admits, wondering if she’s in trouble here. “They use transposition ciphers or substitution ciphers. None of them use any of the languages you’re teaching me or even the literary stylings found in this book.” She holds up the book entitled Embedded Poetry and Stories: An Analysis. “I do not mean to be pert and I doubt it is my place, but is it safe? If someone like me can decrypt the codes, what does that mean for Konoha?”
In the silence that ensues, Sakura works up the courage to look Shikaku in the eye. She does, surprised to see the shock writ upon his features.
“Sir?” she ventures, hesitant.
Shikaku’s shoulders begin to shake as peals of laughter burst forth. Sakura feels the flush creep up her neck, around her ears, and fill her cheeks, as a mixture of embarrassment and confusion settles into the pit of her gut.
“I’m not laughing at you,” he says between chuckles. “It’s just…I am unused to such astute observations coming from the mouth of a six year old. At least, regarding these matters. If Shikamaru applied himself…” He trails off for a moment before shaking his head. “But I digress. Sakura, you are right. The codes Konoha currently employs among its elite shinobi are simple. The current opinion is that, should a missive be intercepted, the ciphers are good enough to keep prying eyes out.” He rolls his eyes, indicating his opinion on the issue. “They think the Konoha dialect is enough to confuse enemy code breakers, nervemind the fact that there are always spies within the village and we have our fair share of traitors. Just as you know the Iwa dialect from the texts you’ve read, so to do other nations know ours. We aren’t particularly unique.”
“So why don’t they care to change?” Sakura asks, flabbergasted and horrified.
To think that enemies could so easily decipher sensitive village information…
“Who can say? The Councils and other officials are still war-minded; most of them suffered through two of the three Shinobi World Wars and countless other skirmishes. They aren’t acclimated to peace time and focus solely on our military strength. They believe that sending missives with Summons will keep them safe, but there’s always a risk at hand. Konoha’s officials do not care to ‘waste time’ on ‘exercises of futile intelligence.’” He seems to be quoting specifically from words told to him in the past. “They forget that such exercises are the primary information source in both war and peace time. In fact, this type of espionage can either cause or prevent war.”
“Cause or prevent war?” Sakura repeats, astonished.
What Shikaku does, what she’s doing, can have that monumental an impact?
Shikaku smiles and it is a bitter thing. “The Councils scoff, but wars have been started for less than a deciphered letter. It’s also possible that, should our codes be broken, forgeries take their place and throw the upper echelons of Konoha’s elite into disarray.”
Sakura blinks, more than a little shell-shocked.
“Some of the higher officials, the true war dogs who were in the thick of it, use more complicated ciphers. Hokage-sama, Shimura-san, and so on. I’ll let you take a look at some of them sometime. You’ll be able to see that, with those they’ve personally had a hand in creating, bits of their personality are imbued into the codes. Still, they don’t bother to keep up with the current literature on cryptography. Language is fluid and constantly changing. So too is cryptography. I’m having you read these histories so that one day you can create ciphers of your own.” Shikaku grins, scars stretching in his happiness. “You’ve shown more than just a penchant for it; you have a true gift. I look forward to the codes you yourself create. I know they’ll be magnificent.”
Sakura doesn’t speak, thunderstruck by all the possibilities that seem to have opened up before her. Her very own code…She never realized that she could make any herself, rather than borrowing from the work of others. To make—to create—codes all her own, with her own signature, own brand…Well, the possibilities seem endless.
Shikaku smirks at her over-wide eyes. “Your eyes are growing larger than your stomach; don’t get greedy. Pace yourself, we have time enough.”
Sakura nods, returning to her reading with a new fervor and fresh perspective. She wants—needs—to learn everything there is about cryptography.
“That’s ten,” Ino says, tone unreadable.
“Did I…did I do alright?” Sakura asks, almost fearful of the answer.
“Why don’t you see for yourself?” Ino says.
Sakura reaches up, removing the kerchief from her eyes. Before her, forty yards away, are the ten targets. Each of her kunai struck their mark. Sakura claps in excitement, prancing forward to examine the targets more closely. She managed to nail the very center of the target on four of the targets, the other six hit within the two next smallest circles.
“Ino!” she exclaims, turning back to her friend.
Ino cannot contain her own exhilaration. “You did it!”
“We did it,” Sakura corrects, the force of her smile almost hurting her cheeks. She looks across the field at her friend and bows. “Thank you, Ino-sensei.”
Sakura yelps as, still bowed over, a weight hits her in the side, knocking her over. Sakura tumbles to the ground, entangled in Ino’s limbs. They look at each other for a long moment, stunned breathless by the unexpected fall. Then, and Sakura cannot say who exactly starts, they begin to snicker. Snickers evolve into giggles which turn to guffaws and finally become outright cackling. They lay on the ground against each other, content as the laughter dies off.
“I’m trying to imagine Mizuki-sensei’s face during the quarter’s final,” Ino says.
“Mizuki-sensei’s? What about Iruka-sensei’s?” Sakura sits up, pulling a face at Ino that sets off their fit once more. “Sasuke-san won’t be pleased.”
“Why’s that?” Ino asks, propping herself up on her elbows to look over at Sakura.
“You’re better with weapons than he is,” Sakura says. “He might even challenge you to a spar.”
Ino huffs, though a slight flush rises to her cheeks. “Let him try. Tou-chan’s been teaching me secret clan techniques and spar moves. Sasuke-san can’t even activate his kekkei genkai yet. I can beat any of the boys in our class.”
“You’ll beat him,” Sakura says, confident. “You can beat any of them.”
They fall into a satisfied silence, just basking in Sakura’s victory and each other’s presence.
Because they are propped up against one another, Sakura can feel Ino’s muscles suddenly tense. “What is it?” Sakura asks.
“Speaking of displeased boys reminded me of something,” Ino says. “We had an Ino-Shika-Cho barbecue last week. I hung out with Shikamaru and Choji the whole time. Shikamaru seemed a bit off. He kept asking me questions about you.”
“About me?”
“Apparently Shikaku-oji has mentioned you a couple times at home. Since Shikamaru’s so upset, I’m guessing he gave you praise.”
“Shikamaru’s upset?” Sakura asks, sitting up straight after fighting back feelings of pride. She enjoys being praised for her skill.
“Don’t worry about it, Sakura,” Ino says, pulling on Sakura’s hand until she reclines once more. “Shikamaru just really admires his father, though he’d never admit it. He’s just jealous that Shikaku-oji has noticed one of his peers.”
“What should I do?” Sakura says, picking at her fingernails. She hates the thought that someone is angry with her; the people pleaser in her demanding that she fix the issue.
Ino flaps a hand. “Don’t worry about it; Shikamaru will either get over it or confront you.”
“Confront me?”
“Calm down,” Ino says. “This is Shikamaru we’re talking about. He’s pretty lazy and he knows you’re my best friend. He won’t do anything terrible; he knows I’ll make him regret it.”
Sakura smiles, grabbing Ino’s hand. “Thank you, Ino, for always protecting me.”
“Of course!” Ino replies, squeezing Sakura’s hand in turn. “I always have your back.”
They stay like that for a while, time seeming to stand still aside from the movement of the sun and clouds in the sky. Finally, Ino stands with a sigh, patting down her clothes and collecting her gear.
“I have to go home for dinner,” she admits, looking put out. “Tou-chan is cooking tonight and I don’t want to miss it.”
“I’m sure it will be good!” Sakura replies, trying not to think of her own home, empty right now as her parents travel through Iron. They’re establishing ties with the samurai that reside there, hoping to attain firsthand access to Iron exports. It is an arduous and lengthy process, but Sakura knows better than to complain. She glances at the targets, pushing aside the thought of withdrawing leftovers from the fridge that her aunt left her. “I think I’ll stay here a bit longer and continue to practice.”
Ino gives her a hug and they exchange farewells, Sakura watching as Ino moves away.
Once Ino is no longer in sight, Sakura sets about practicing once more. She withdraws her kunai from the target, deciding to work with her shuriken instead.
“You don’t need her.”
Sakura jumps, turning with kunai ready in hand.
“Torune?” Sakura asks, confusion giving her pause. “What are you doing here?”
He glances at her for a moment, before returning his attention to his feet. She cannot really see much of his expression, obscured as it is by goggles and high collar, but she’s certain that he’s angry. She’s never seen him like this.
“The Yamanaka,” Torune bites out. “You don’t need her.”
Sakura cocks her head to the side for a moment, regarding him, before turning back to the task at hand. “I’m not sure what you mean.”
“I’ll watch your back,” Torune says. Sakura suddenly realizes that she can feel the way his entire body is vibrating with the force of the rinkaichū within him, even with the distance between them and her back to him. “I’m strong, I can protect you.”
“Ino is strong too,” Sakura replies, yanking hard on one of the kunai. It is firmly wedged into the wood and, though she’s proud of the force she put behind the throw, it is causing some trouble now. Ino is the top girl in their class in every area except academics, which Sakura herself dominates. “Plus, as a shinobi I need to be able to watch my own back.”
“Sakura!” he exclaims before cutting himself off in frustration.
“What’s really bothering you, Torune?” Sakura asks, abandoning the kunai to regard him fully. “You’ve never had any issues with Ino before.”
“Is she your best friend?” Torune blurts out.
“She’s my first friend,” Sakura says.
“That isn’t an answer.”
Sakura sighs, sitting down and crossing her legs. She pats the ground beside her, to indicate where he should sit. Torune obeys and Sakura begins plucking at the dandelions that grow around the base of the target.
“Ino is my precious person,” Sakura says, focusing on her hands. “She saved me from bullies and gave me this ribbon.” Sakura gestures to her head. “She’s bossy and likes to gossip and to get into my business and I love her with all my heart. When she’s sad, I want to cheer her up. When she’s injured, I want to heal her. When she’s happy, I want to make her even happier. I want to protect her and pay her back for all of the help she’s given me.”
“Oh,” Torune says, subdued. His buzzing has completely subsided.
“Torune, you are also my precious person,” she continues as she weaves the strands together. “You are quiet and you daydream and sometimes talking to you is hard because I don’t know what you feel about what I’m saying and I love you with all my heart. When you’re hurt, I want to hold your hand. When you’re frightened, I want to scare your fears away. When you’re fighting, I want to stand and protect your back. It makes me smile when I see you smile.”
Torune sniffles slightly, rubbing at his nose. “Really?”
“Really,” Sakura replies. She ties the ends of the stands to each other and nods to herself. Sakura lifts her creation in her hands and leans over, placing it on his head. “There. It won’t last as long as the ribbon, but…” She shrugs. “I’ll get you something that lasts later. This is a symbol of our bond. Dandelions mean long-lasting happiness, youthful joy, and wish fulfillment. My wish is this: that you and I will be friends forever.” Sakura grins at him. “So don’t worry about ‘best’ or anything like that. Both of you are my precious people.”
Torune throws his arms around her, dragging her into a hug. It is awkward and slightly uncomfortable, but wholehearted and warm, just like Torune is. “You’re my precious person too,” he says against her ear. “Thank you for being my friend, Sakura.”
Sakura opens her mouth to reply, but her stomach beats her to it, growling loudly. She flushes, drawing away from Torune. “Sorry about that. I guess I’m hungry.”
“Want to come to dinner with me? Oji-sama will cook.”
“Are you sure that’s alright?” Sakura asks. “I’d hate to impose.”
“It won’t!” Torune says, cutting her off. “Oji-sama always cooks too much. He’d be happy to have you.”
Sakura thinks back to her vacant and quiet home and realizes that there is no contest. “Of course, Torune, thank you for the invitation.”
#my fic#sakura haruno#sakura-centric#satori (between the lines)#torune aburame#sakura & torune#sakura & ino#ino yamanaka#sakura gets to use her skills from a young age
121 notes
·
View notes
Text
Photo stamp remover 8.3 key


You can now deploy Horizon Connection Servers and Horizon Agents in different data centers across WAN, as long as the Horizon Agents are located within 120ms of the Connection Servers.
HTML Access is now supported in an IPv6 environment.
You can now connect to the event database using SSL.
See Using the Legacy Microsoft CryptoAPI Standard. If you have a use case requiring use of the legacy CryptoAPI standard, you can still do so.
By default Horizon now uses the Microsoft Cryptography API: Next Generation (CNG) standard.
Cross-Origin Resource Sharing (CORS) is now enabled by default.
See Add vCenter Server Instances to VMware Horizon. Deployment type allows you to specify whether your vCenter is in a private data center or in a specific public cloud data center.
When adding a vCenter Server instance, you can now select a deployment type.
Manage Machine Maintenance - used for toggling machines manually to and from maintenance state.
Manage Machine Alias and User Assignment - used for machine user assignment and machine alias assignment.
Both new privileges are children of the Manage Machine privilege: See Privileges for Managing Machines and Object-Specific Privileges.
Role creation and edit now offer two new privileges applicable to access groups.
You can now use smart card caching emulation for non-Microsoft Windows client connections.
Users belonging to untrusted domains can use SAML authentication, True SSO, and smart card authentication.
See Using VMware Horizon Desktop Recording.
You can record desktop sessions for troubleshooting and auditing sessions.
See VMware Configuration Maximums for detailed scalability metrics.
Horizon supports 20,000 desktops and sessions per Pod.
See Estimating Memory Requirements for Virtual Machine Desktops.
5K and 8K client display resolutions are now supported (Blast only).
See Choosing ClonePrep or Sysprep for Customizing Your Virtual Desktops.
Microsoft Sysprep is now supported for customizing instant clone virtual machines.
See Worksheet for Creating an Instant-Clone Desktop Pool.
When creating or editing a desktop pool with session type Application and Desktop or Application, you can select the Bypass Session Timeout setting to allow application sessions to run forever.
See Worksheet for Creating an Automated Instant-Clone Farm in Horizon.
The Bypass Session Timeout setting allows application sessions to run forever.
The actual release date can vary based on business needs and engineering schedule changes to address critical customer requirements. This information is grouped by installable component.īeginning with this release, version numbering is based on the planned year and the month of the release. VMware Horizon version 2106 provides the following new features and enhancements.
Nonoperational Features in This Release.
No Longer Supported Features in This Release.
It always gives me accurate results.These release notes include the following topics: I’ve used it for a really long time and never once had a problem. This one does a great job removing photo background online as well as replacing. With its user-friendly and ad-free interface, a first-time user can create the most stunning photo with the fancy background templates it offers. It’s so much better than any other tools I’ve used before. This is exactly what I’ve been looking for. I successfully changed the background of my passport photo to white with this amazing tool. It not only erases my photo backgrounds but also provides multiple templates. This online background eraser does what it promises and does it very well. The AI technology helps me remove image background online with a single click. One of the best online photo background erasers by far.

0 notes