#Do My Cryptography Assignment Help
Explore tagged Tumblr posts
Text
welcome to the clue hunt!
how does this thing work?
to join the search for the 39 clues you will need to concoct a serum that will make you(r branch) all-powerful and set for world domination. follow this blog and/or like this post to register:)
this is an online clue hunt based on tumblr inspired by the 39 clues series. you do not have to have read the series to participate, although it might be more fun if you have!
a list of 39 elements, each with an associated number to account for its quantity in the final serum, has been determined and will soon be circulated across the threads of the interwebs. the goal of this clue hunt will be to collect all of these clues for your branch!
there will be four branches the participants will be loosely divided into based on their interests (will elaborate on this in a bit). the lucians (red, the cunning branch, think codes and logic and conniving), the ekaterinas (yellow, the stem branch), the tomas (blue, the athletic branch, which in the context of this clue hunt translates to gamers/shit that requires good motor skills) and the janus (green, the artistic branch)
each participant will be given a few clues at the start of the game. you will randomly be alloted into branches UNLESS you send an ask to this blog with a preferred branch. to make sure each branch has more or less equal numbers, asking for a specific branch will mean you will be given less clues than other participants at the start of the game (i.e. there is an advantage to random branch assignment).
you will be told your final branch privately and will not be revealed the branches of any other participants.
you will be required to hide the few clues given to you across the interwebs (there won't be many clues don't worry) in internet trails, using codes, links, metaphors, required tasks you need to complete to attain the clue, etc etc. this will largely be up to you and you will be allowed to use your creative license - but you will have to send your trail to this blog to make sure it is workable and not too vague lol. i will edit/fine tune everything and if you can't think of anything i will make a trail for you
if you pick your own branch, you will be required to incorporate the core values of your branch into your trails. so for the janus this means hiding clues in art, for lucians this means codes and cryptography related things maybe, etc etc.
write your tumblr url somewhere near where you leave the clue so people know you left it there!
a map will be provided with the location of each clue around the world, colour coded. so for example, myrrh, a clue from the original series, is an ekaterina clue native to north africa. so, a yellow dot representing myrrh will be marked in this region. this can be used to find out what branches other members are in. for example, if you find out a fellow participant hid the clue myrrh, you can deduce they are from the ekaterina branch because there is a yellow dot in the region it's from. if you are also an ekat, this means you can trust them with your clues because you're on the same team:)
a certain number of clues will not be given to any participants and will be withheld as madrigal clues. these will be hidden by me:)
you can recruit members who haven't registered to help you with your hunt well into the game! however, you need to have registered at the beginning (i.e. be following this blog and like this post) to receive your own clues
any/all forms of cheating and backstabbing will be allowed (for everyone except me/the madrigals that is):D
to help with organizing if you don't want to participate, you can join the madrigals! we are a neutral team who cannot by definition win and are just having fun organizing all this lol
more details including duration, prizes, etc will be shared/updated later!
happy hunting!
tagging people who interacted with my post about this: @the39cluesian @iankabra @yakalll @angelkat-x @icamebackfromnarnia @39addict101 @manicpixiess @bilhert @mediodedios @toiletpotato @39starrygurl @gaslighting69 @nimonaaaa @dinatela @amianislovely @fandom-oracle @sarasanddollar @carpe-astrae @ghost-in-a-cup @cosmo-babe @kadalakari
41 notes
·
View notes
Text
How a quantum scientist, a nurse, and an economist are joining the fight against global poverty
New Post has been published on https://thedigitalinsider.com/how-a-quantum-scientist-a-nurse-and-an-economist-are-joining-the-fight-against-global-poverty/
How a quantum scientist, a nurse, and an economist are joining the fight against global poverty


A trip to Ghana changed Sofia Martinez Galvez’s life. In 2021, she volunteered at a nonprofit that provides technology and digital literacy training to people in the West African country. As she was setting up computers and connecting cables, Martinez SM ʼ23 witnessed extreme poverty. The experience was transformative. That same year, she left her job in quantum cryptography in Spain and enrolled in the MITx MicroMasters online program in Data, Economics, and Design of Policy (DEDP), which teaches learners how to use data-driven tools to help end global poverty.
By 2023, Martinez completed the MIT DEDP master’s program. Today, she is the co-founder of Learning Alliance, a new nonprofit that will counter sub-Saharan Africa’s learning crisis by introducing evidence-based teaching practices to teachers. She plans to move to Africa this summer.
“If someone told me a few years ago, when I was doing research in quantum physics, that I would be starting my own organization at the intersection of education and poverty, I would have said they were crazy,” Martinez says. “From my first MicroMasters course, I knew I made the right choice. The instructors used mathematics, models, and data to understand society.”
Since 2017, the MicroMasters in DEDP program — jointly led by the Abdul Latif Jameel Poverty Action Lab (J-PAL) and MIT Open Learning — has been bringing together former nurses, lawyers, software developers, and others who are ready to make a career change and an impact on the world.
A new way to combat poverty
The MicroMasters in DEDP curricula is based on the Nobel Prize-winning work of MIT faculty members Esther Duflo, the Abdul Latif Jameel Professor of Poverty Alleviation and Development Economics, and Abhijit Banerjee, the Ford Foundation International Professor of Economics.
The pair used a key feature of laboratory science — randomized control trials — and applied it to development economics. For example, to test the efficacy of a new education initiative, researchers could randomly assign individuals to either participate in the program, known as the treatment group, or not, known as the control group. The difference in outcomes can be attributed to the new program.
This approach has fundamentally changed how antipoverty programs are designed and evaluated around the world. It has already boosted immunization rates in India, reduced child marriages in Bangladesh, and increased school attendance in Kenya.
Duflo and Banerjee’s research created a new way forward for poverty alleviation, but there are too few people skilled in evidence-based development economics to bring about meaningful change, says Sara Fisher Ellison, faculty director of the MicroMasters and master’s programs in DEDP and a senior lecturer in the MIT Department of Economics.
“It is vitally important that we have people all over the world who have the skills to run randomized control trials, to read the literature from these trials, and interpret the results to policymakers,” Ellison says.
Andrea Salem was an economics undergraduate student in Switzerland who was unsure about his career when Duflo and Banerjee received their Nobel Prize. Their recognition introduced Salem to a field he barely knew existed, and set him on a path toward using economics to make an impact in the world.
He completed the MicroMasters in DEDP credential and included it in his application for the Paris School of Economics (PSE). Currently taking a gap year from PSE, Salem has an internship with J-PAL’s Morocco Employment Lab. In this role, he works with government officials to evaluate education reforms.
“To get to know the world in all its diversity is a gift,” Salem says. “To live and do research in the same country is a reminder of the important work I’m doing and how much more needs to be done.”
How the DEDP program works
The MicroMasters in DEDP program is open to anyone with a reliable internet connection. Students choose either a track in public policy, which focuses on key issues in high-income countries, or international development, which examines problems prevalent in low- and middle-income countries. They take a rigorous course load in economics, probability and statistics, and data analysis. The program balances flexibility with structure. Students go at their preferred pace in earning the credential, but each course is instructor-led, providing participants with a community of global learners who can regularly participate in webinars and discussion forums.
Students who complete and pass proctored exams in five courses earn a credential. The MicroMasters in DEDP program has awarded more than 10,000 certificates for passed courses and 1,000 DEDP MicroMasters credentials. Credential holders may continue their education by applying to a master’s program at MIT or at one of 19 pathway universities worldwide that either recognize the MicroMasters in DEDP credential in admissions or offer academic credit for the credential as part of an accelerated graduate program. The credential itself is also valuable for professionals as they advance their careers.
The courses are free to audit; there is a fee for each proctored exam. Exam fees are on a sliding scale, ranging from $250 to $1,000, based on a learner’s income and location. DEDP also offers a lottery, available to people who earn less than $10,000 a year, that discounts the price of one course to $100. Martinez was a beneficiary of the lottery in 2021. Without it, she says it would have taken her longer to earn her credential and apply to the master’s program.
Choosing passion and pedigree
Yann Bourgeois SM ʼ22 had a rewarding nursing career working in operating rooms and intensive care units in Belgium. This job gave Bourgeois a firsthand understanding of what happens when human health and needs are neglected. Driven to make a global impact, Bourgeois discovered the master’s in DEDP program while studying public health.
Having overcome personal challenges and socioeconomic adversity, Bourgeois was not sure MIT would consider him for graduate school. When he learned that the MicroMasters credential played an important role in admissions, Bourgeois became hopeful. He enrolled in five MicroMasters in DEDP classes at the same time. It was a bold move for someone who had not taken a math class beyond statistics, but he was eager to submit his graduate school application. By 2022, Bourgeois was an MIT graduate.
“My background doesn’t matter,” Bourgeois says. “The fact that I didn’t know what I wanted to do with my life at 14 or 15 doesn’t matter. All that matters is the skills and passion.”
Bourgeois now works as a labor economist at the World Bank in Washington. His job focuses on improving labor conditions and promoting equitable economic opportunities. His MIT education equipped Bourgeois with rigorous analytical tools to address complex economic problems on an international scale.
Like Bourgeois, Martinez did not believe she had the qualifications to apply for the master’s in DEDP program. Then, she read students’ profiles online and learned about their wide-ranging experiences. After learning more about the program’s inverted admissions process, which prioritizes performance in relevant courses over traditional credentials, she realized that the opportunity might not be out of reach.
“Evidence-based development needs people from very diverse backgrounds,” Martinez says. “And I’m proof that you don’t need the ‘right’ background to work in development economics. The fight against global poverty needs everyone.”
#000#2022#2023#250#Abdul Latif Jameel Poverty Action Lab (J-PAL)#Admissions#Africa#Analysis#approach#audit#background#cables#career#Careers#certificates#change#classes#Classes and programs#Community#computers#course#courses#credential#credentials#cryptography#data#data analysis#data-driven#Design#developers
0 notes
Text
Why choose the services of 24×7 assignment help?
In the above fundamental securities, the algorithms to be learned for making a digital data secure is not an easy task for a student. The homework and assignment may make them feel confused with algorithms and other cryptography aspects. Where our https://www.allhomeworkassignments.com/ cryptography assignment assistance will surely be helpful to you. There are symmetric and asymmetric algorithms and also encryption and decryption which are the basis of the cryptography. They need to give special attention towards this topic of programming as a single wrong code can affect the security algorithms. Taking online help from https://www.allhomeworkassignments.com/ is always useful.
Why choose the services of 24×7 assignment help?
When you are in search of an online expert to ask them to do my cryptography homework and assignment then https://www.programmingonlinehelp.com/ are one among the other online companies by providing efficient services that too at affordable cost. Let us see what our strengths are and how we are good for solving your assignments?
•You get content which will be only yours that is unique and plagiarism free. How to solve cryptography assignments? Is not a big question for our https://www.programmingonlinehelp.com/ experts. They have complete knowledge to give the needed help with all types of question, You get the help from the experts that are dedicated to their work and always give you timely delivery. You can ask for do my nursing cryptography at any time as we provide a service which is available 24/7 for you. You may be around anywhere in the world you just need to go online and hire https://www.programmingonlinehelp.com/ experts through simple steps and also make the payments with secure methods. You be assured with our work that it will be without errors and it will make a huge difference in your grades at all time.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text
my biological peer reviewer (sibling) called this theory “fun” and said i should send it, so here goes
my personal theory is the feds ((”federation”)) created the eggs because they decided the best way to enforce “you can never leave” was to give the people something they couldn’t lose, like in the post by tumblr user alexaloraetheris (no relation to the smp) where their friend who might be a deity had said,
"When you die you descend to the underworld with nothing to lose. To keep you, they give you something to lose. When you want to return, they will demand it back. That's why nobody ever leaves. The only way out is to never enter."
i’m thinkin that on egg D-Day, at the end of the countdown, the feds weren’t gonna give the eggs back. they were just gonna hide them forever, or do something else, anything else, just keep them away from their surrogate parents, because then the people would just be STUCK, because people could theoretically take their eggs and leave, but if the eggs are missing, gone without a trace, then the residents CAN’T LEAVE, because presumably the eggs are STILL THERE, SOMEWHERE, IN NEED OF HELP AND RESCUE, if only the residents could find them ON THE ISLAND. if they leave the island while the eggs are missing, they are abandoning these things that have become their children.
but then in came the brazilians. and shit went south. because see, the spenglish (spanish / english) streamers were INVITED, but the brazilians CRASHED; the feds didn’t INVITE THEM, they weren’t EXPECTING THEM, but they can’t let these guys leave either, so they PANIC, and they scramble to give the brazilians the same thing--something to lose. the new egg had a brazilian jersey, homie was TAILOR MADE for them to pack bond with. the feds didn’t have time to send out multiple eggs, it was all or nothing, so they picked something they could reasonably assume all five of them would find endearing because they don’t know shit about these guys--they had a week to observe the OG batch, but all they know about these newbies is the brazilian flag on their boat--and so they sent the little egg out to become THEIR THING, the thing they couldn’t afford to lose.
it leaves open why the eggs are cracked too, bc idk what’s going on there lol, either 1: the eggs cracked because they’re hatching and the feds picked that date bc they wanted to yoink the eggs before they got Too Powerful, or 2: the feds were the ones to crack the eggs as an excuse for why they vanished--returning the eggs untouched would open too many questions the feds don’t want them asking; this way, instead of being concerned specifically with “why were the eggs missing”, the residents presume they know the answer--the cracks.
but yea i’m just gonna add as an aside that personally i think cucurucho / osito bimbo / the white fucker is way more active again because the feds are still scrambling to keep up with the brazilians (which, again, the feds weren’t expecting), and the binary fuckwad came in to put the fear of god into the newbies--maybe so they didn’t get too focused on the morse code transmissions; iirc max was theorizing that both osito and binary were part of the federation ? and if so it does make sense that the binary entity went to fuck with cellbit immediately after cellbit was introduced to the conspiracies of the island, yknow, a warning shot. i think they want them to be focused on the eggs.
BUT THAT’S JUST A THEOr
#i'm spitballing into the void bc i'm losing my mind lol if you read this send me some luck thank you#qsmp#someone send me to a nice farm with plenty of space to run i have lived too long#can't wait until someone smarter than me cracks the code#data and network security tried to teach me cryptography but HOO BOY it didn't do shit to help me here#i popped some of the words into a brute force caesar cipher#and also a tool that could roughly check for substitution ciphers#and yeah didn't find shit so uh#im gonna leave it to the one who's an ARG master yknow i think he's got it handled#(i thought about using an online tool to translate this but then realized i Do Not trust translators i can't verify)#(like i've definitely used google translate on my french assignments but the thing is i speak enough french to verify that)#(duolingo spanish + english/french cognates doesn't leave me confident and im not asking my unconnected spanish speaking friend to check it)#((i refuse to admit to her face that i've sunk so deeply into this hell-))#(like spanish is such a common language for english speakers to learn that i'm sure they've honed the eng/span trans pretty well BUT)#(i don't trust it lol and id just prefer not to put something on my blog that i can't verify)#(so apologies and uh translate at your own risk k love you byeee)#shut up vic
71 notes
·
View notes
Text
me, lying on the floor of my room playing obey me: if you wanna be my lover, you gotta get with my friends !!
me: *remembers all my responsibilities*
me:
me:
me, continuing: make it last forever, friendship never ends !!
#my cryptography lab is due tonight and i havent started it and then i need to help mellisa register for her classes#and do her statistics assignment#and i just wanna lay here and try to 100% our destiny on extreme#i did finish working out tho#so theres that#but now i gotta shower#i just 😭😭 want to lay down 😭😭#i write posts not tragedies
2 notes
·
View notes
Text
It's the first time I posted something I actually translated...It's my friend's work, and he asked me to post it to Tumblr👉👈 I'm not sure if there are any romantic contents... English is not my mother language, if you guys have any idea about the fic please comment below, thanks~
The War of the Forsaken—Chapter 1
London, 1985.
Agent Helen Park took a sip of her warm coffee and then stretched out after finishing today's business.
In 1981, Perseus's plan to detonate all the nuclear bombs in Western Europe was completely smashed by Russell Adler's team, and Perseus seemed to dropped off the face of the earth.
No one have sign of the activities of Perseus now, not the CIA, MI6 or even the KGB. The authorities believed that Perseus has been killed in the melee of Solovetsky. But since the body was not found, the task of tracking Perseus must continue.
However, four years of aimless search has obviously made the authorities of the United States and Britain impatient. The power of the Soviet Union is fading, and the War in Afghanistan has made the Union worse. The KGB's overseas intelligence network has also been damaged bit by bit. The authorities begin to think that Perseus is no longer an important target.
Park's tracking team was forced to disband, and the original team members were assigned to needed positions.
Although she is seriously understaffed, she somehow managed to get some scattered clues through her own relationship.
And she's been sorting out these clues for weeks.
Most of them are useless and repetitive information, and there is very little valuable information. What she can learn now is that CIA agents stationed in Afghanistan are being systematically arrested and tortured recently.
Most of the agents were hit in the head by blunt instruments after being tortured, and they were in a coma. When they woke up, they lost part of the memory of the interrogation to some extent. There was only water on the ground and a few rags left at the scene of the interrogation.
This is unlike what Perseus would do, most of the agents have little to do with the War in Afghanistan. Some of the agents only have the task of monitoring a senior official in Afghanistan. If Perseus wants to help the Soviet Union win the military action in Afghanistan, it will not do any good for him to torture these agents. On the contrary, it will make it easier to reveal his whereabouts.
When the information was sent to Park's e-mail, it was marked "delete after reading".
Of course, Park will do it, but she will extract all the information first, and then delete the email.
She hasn't had time to read today's email. She wants to copy down the content before she gets off work and analyze it slowly after she gets home.
Park opens her email and clicks in the latest one.
However, the moment she saw the content of the email, her heart acetated and she got goose bumps.
"There was an agent who remembered what happened. He claimed that the interrogator was a 30-year-old woman, blonde hair, calling herself"Bell ", has a London accent and can speak fluent Russian."
Bell, the memory that she dares not touch like an exposed nerve, has been conceal for four years.
In Solovetsky, she saw the girl in a pool of blood, and Adler, who asked Park to help carry the body.
1981, West Berlin hideout.
"Where's Woods?And Mason? And Adler? " Bell just got out of a battle, she took a bath, pushed open the door of the bathroom, but found that three of them disappeared.
"They went to meet Hudson. I'm glad you're back safe and sound." Park said as she wrote at her desk.
"Maybe that's the British luck." Bell recalled the situation when she was hunting down by the Soviet infantry chariots.
"It's not just luck that made you stay in the MI6, is it?" Park put down her pen, turned to the Bell and said, "The team say that you are the a cryptography master in the whole Ministry."
"I taught myself when I was in the university, when my brother was just killed in a terrorist attack……May him rest in peace. " Bell picked up the 63 rifle leaning against the wall, unloaded the mag, and then pulled the bolt to withdraw the gun. She skillfully unloaded the gun for routine maintenance.
There was a subtle change in Park's expression, but her professionalism immediately calmed her down.
"I heard you graduated from Oxford, too?" Asked Bell.
"Yes."
"Do you know Professor McFarlane? I might not have choose this job without him."
"I think you should have a rest. Chatting too long is not good for the next mission." Park diverted the topic.
"I must clean the dirt inside the gun before I go to bed... I do know I really need a rest. My thoughts are a little messy these days." Bell replied.
London, 1985.
"You know it's against the rules of MI6. Even allies can't contact each other's intelligence personnel without permission."
The speaker is a tall, thin man with a bushy beard. He lean against the railings of the Thames River to enjoy the scenery of late autumn. On the other side of the river is the retired cruiser Belfast.
"I heard that you are going to sent a team to an observation mission in Afghanistan. Maybe there would be a place for me?" Park asks.
"The CIA didn't invite MI6 to the mission. I'm not sure I can convince Hudson to let you in." The tall man replys, "your boss won't agree either."
"I'll take care of the bureaucracy of MI6. Just squeeze me in. Don't worry, my action is also for the benefit of the free world. "
"I've always believed in you, Park, but I also want to remind you not to mess around." The man left with his hands in his pockets.
Park can understand his worry, since he has taken this job, he will have many kinds of worst assumptions in his subconscious.
On the battlefield of Afghanistan, the Soviet army is still deadlocked with the Afghan soldiers. The observation team organized by the CIA nominally represents the United Nations, but they provides military training and weapons for the Afghan soldiers in the dark.
Even when the Soviet Union is on the wane, NATO never dared to despise the "Red Giant".
#black ops cold war#cod#helen park#call of duty cold war#cod black ops cold war#cod fic#cold war bell#russell adler
12 notes
·
View notes
Note
Your assigned prime number kin is:
171276729503059590728814613096579756523401278257538768906082514060131793456094633761719251656683454535396415964718792024126329723421881233711494716860017918165543390553804372831795407373574376609009718354105652405928652435809408610918828813909694960949518802308891022683597008592181586696151240908190388528817
Feel free to go do some cryptography with it or something idk
I'll use this to help safeguard my avatar fanfiction or something lmao.
1 note
·
View note
Note
hi there! i’m a high schooler and i’m seriously considering majoring in computer science when the time comes. do you think you could maybe talk a little bit about what it’s like studying comp sci? if you can. i hope you’re having a great day
hope you’re having a great day too!
What my first year of studying computer science was like
obligatory preface that courses differ between universities and colleges. i study in australia.
The biggest challenge I faced per se going into comp sci was how nothing I did at school prepared me for it. The kind of content I’ve learnt wasn’t similiar to school and the assignments have been very different. No analytical essays and scientific reports for me (there has been essays and reports tho). In my school IT class I learnt basic HTML and CSS which was the only programming knowledge I went into comp sci with. (Id also gotten pretty far on khan academy’s JavaScript course in like year ten but I’ve forgotten all of that now lol).
I have four units a semester and have completed my first year (of 3, although I’m taking less units this year so I’ll finish in 3.5 years).
What I actually did in my first year:
Semester 1 (pre-major picking, two of these were for the other major option)
Learnt general computer hardware and how it functions. The assignment was using a raspberry pi to do something that used hardware (the pi), software (basic code) and the internet (I used twitter). My project is on Twitter at SunsetIFB102
Group project app design stages. Like drawing the layouts, getting feedback, then digital sketches then semi fancy looking sketches (not comp sci major)
Python! I really liked this. Taught the basics of python and in general programming. It was kind of intimidating how many people had coded before so I had to focus on ignoring them and learning for myself. Also really salty I was 1% off a high distinction for the whole unit AGH
Databases and SQL. This would’ve been a useful unit if the lecturer was, how do I put this kindly, good at his job. (Not comp sci major, although definitely use databases later on)
Semester two (all comp sci major)
C# , basics of object oriented programming principles. Which is a fancy way of saying it taught how you should write your code so it’s laid out effectively.
C, how to program microprocessors. Basically how to program hardware machines. C is mostly used for machines like ATMs, a fridge perhaps, probably a roomba and other single purpose kind of things. Also from this I can program arduinos and read arduino code easier since arduino code is a C/C++ hybrid. (This and the previous unit had high fail rates and were honestly Tough)
Information security (apart of network security minor) This unit talked about processes of protecting information in organisations and on a single person level. Basics of cryptography was discussed and hashes and how ways information is kept secure when transferring between objects (like over the internet)
Computation mathematics (apart of intelligent systems minor). This was a weird unit to me and was mostly math majors. It taught all these different equations which allow you to make approximations. Honestly confused how it’s used for computers but we learnt MATLAB and it’s a pre requisite for an intro to robotics unit I’m taking this year :)
So yeah, that’s an account of what I actually studied. Reading over it it seems way more impressive than it probably was. Computer science isn’t easy (well, unless you want to scrape a pass each time) but it isn’t horribly difficult. It’s how different it is to high school work that can trip you up. I can’t make aesthetic studyblr notes on paper because its all on my computer and can’t turn it off when studying because I need it.
My assignments are typically big coding projects, exams (multiple choice if a coding unit) and essays if it deals with theory (like info sec did).
This coming semester I’m learning Java and GUI’s (graphical user interfaces), JavaScript and HTML and whatever else for web applications, and discrete maths which seems to be for notation used later on... it looks very strange.
Hope this helps! If you have any more questions feel free to DM me!
Also if anyone else wants to add their experiences, feel free to reblog with your tips.
#computer science#software engineering#engineering#comp sci#studyblr#study tips#tips#help#stem#stem studyblr#stemblr#women in stem#women in tech#women in science#university#college
107 notes
·
View notes
Text
[previous con: block out]
Again, obligatory spoiler and wow... I’m wondering if it’s because I’m approaching the halfway point of the series [so far] that’s why these analysis posts keep on getting longer and longer? With the previous episode being an emotional whumpage on Nick, it seemed interesting that another member of this party would be hit as well... and not just metaphorically...

Part 1 - Episode 9 - The Man in the Middle Attack
A social worker comes to the house to help Nick open up, and it works -- until Molly and Jeremy find Nick’s secret cell phone.
The Con: Man-in-the-middle attack (MITM)
To quote wiki: In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe they are directly communicating with each other. [x]
In this particular case the two parties communicating are the Thompsons (whom in an act of concern had called a social worker to their home to help with Nick) and a social worker (an actual employee of the foster care system that isn’t a part of Nick’s ring of con artists).
The attacker? None other than Nick herself! To get back on track with her long con, Nick needs to make sure that the Thompsons’s trust and relationship with her was still in tact. Fearful that it’ll all come crashing down on her, Nick contacts Sam to assist her with the MITM. Sam insists that his own connections down at social services [and cue me not being surprised at all that it’s true to life for there to be corruption in govt. offices] made sure to slip Nick’s “case folder” in the bag of her assigned social worker, Ingrid. For the time being all Nick had to do was continue her act and convince this social worker on the fact that she’s content with the Thompsons.
When Ingrid arrives and informs the family that she was here to observe Nick and the Thompson family environment, Nick does her best to sell Ingrid on the idea that she gets along great with the family, even more so controlling the conversations away from the Thompsons and implementing her own complimentary tales. And for the most part it works... That is until Ingrid points out 1. she’s been a social worker for YEARS and can tell when she’s being manipulated and 2. don’t think that she didn’t notice that for all that Nick is extolling about how great her new family is, not once did they [the Thompsons] say how they feel about her! With concern for Nick, Ingrid advises they figure out a way that Nick can feel safe around the Thompsons to share her true self with them. Realizing that she can’t lie her way out of this, Nick reveals the barest hint of her real self: her own insecurities and doubt.
For the past couple of episodes, Nick has been slowly getting to know the Thompsons beyond being the “people that hurt her family” that we’ve been told (via phone conversations between her and Tony, her father). Her growing connection to every member of this family has been causing her to start doubting not just herself, but her own relationship with her dad, the one connection she has left of the life she had lost. It made sense that of all the “truths” she could have admitted to the Thompsons, Nick’s fear of betraying her “dad” by forming attachments to her new life was the one that she could give without truly hurting Tony or even herself (and her cause).
Before moving on to the next con, there are two more instances wherein MITM was enacted (both happening one after the other, post Ingrid’s visit).
First the minor one: Sam Harbaugh to Liz/Ed and Nick. In a momentary panic, Nick texted 911 to Sam’s cell phone and shortly thereafter he, in disguise as another one of Nick’s “social workers,” arrived to fix the situation... only for Nick to quickly insist that everything was okay after all. Before he left, in a surprisingly honest and sweet gesture, Sam departed a couple of personal information about Nick to Liz/Ed in an effort for them to bond with her. Though they were geniunely nice info for any parent to have, apparently it also sent a message to Nick (and the audience) that her former foster family actually did care about her (to some capacity). It’s the same foster family [of con artists] that earlier in the series we were made to believe that Nick didn’t have the best of relationship with. Once more this series reminds us that not everything is what you see.
The second one was... well, it was a LITERAL man in the middle attack: in this case, Nick, who was literally between Molly and Jeremy, attacked Jeremy. Frustrated with everyone, and including yet another adult (this one being a social worker), seemingly not seeing Nick the way he sees her; Jeremy stumbles upon what he thinks might finally be the key to the mystery that is Nick Patterson: a hidden cell phone in a vent above her bed. Because it made sense that only someone with something to hide could keep a secret second cell phone hidden in an out of reach space, right?
[Okay, full disclosure on this part: 1. I typed majority of this section at around 12 AM so my thoughts are a bit jumbled, and 2. rewatching this scene still pisses me off like it did the first time.]
There’s a lot of things that I enjoy about this show and one of them was that they weren’t afraid to have heart-wrenching moments of clarity like this one: where you realize that though Nick’s reasons for hiding her second phone probably had more to do with her con, there are legit children (both in actual homes, in foster care and orphanages) that NEED a hidden phone, or a hidden SPACE, because their current environment isn’t safe for them. That hidden object or a hidden safe space existed for these children as a necessity for their survival.
When Nick started arguing how she needed that phone “just in case”, I realized that regardless of her actual intentions, that phone was a safety net for her. And when Jeremy said that he “didn’t get it,” the first time I watched this exchanged I legit yelled “That’s because you’ve never been in a situation to need it!” I understand that Jeremy’s still a teen and that he’s really privileged to be given the chance of growing up in a safe suburban home with his family, but that’s what made it both frustrating and heartbreaking: he’s still a kid and a lucky one at that, so of course he wouldn’t understand any if at all the plights (good and bad) that Nick had to go through to get to this point.
We’re on episode nine, the final episode before the finale of Part One, and since Day One they’ve been building up the conflict between Nick and Jeremy to a troubling boiling point. At this time both teens have been emotionally wrought and through the wringer and it wouldn’t take much before their mutual distrust coupled with their unstable tension to create one big blowout!
And boy did it ever: Accusations flew, anger was traded back and forth, steps towards the other were taken, steps were taken back, and when one got way too close for comfort, Nick swung and her fist landed on Jeremy hard enough to Fade to black.
25 notes
·
View notes
Text
Trust Me: Chapter 9
I cannot thank y’all enough for your patience. Hopefully the fact that it’s a relatively big chapter a little bit kinda makes up for the wait? Either way, thank you so much for reading, and I love you <3
Chapter 1 Chapter 8 AO3 Chapter 10
Warnings: A brief mention of the wounds from previous chapters’ violence, very briefly implied nsfw/daddy kink (to skip it, just don’t read the text messages after “Aww, you’re so sweet!”
Author’s Note: Again, the cipher is crackable with the information you have. (I’d argue that this one might be a bit harder, because I gave you fewer/subtler clues, but if you get how it’s encrypted, decoding it is a lot easier.) Shoutout to y’all who got last chapter’s! <3
Word Count: 3,660
Tag List: @ccecode @emo-sanders-sides-loving-unicorn @ren-allen @ilovemygaydad @bloodropsblog @funsizedgremlin @raygelkitty @roxiefox23 @thomasthesandersengine @spookyingarbageisland @band-be-boss-blog
"The truth, however ugly in itself, is always curious and beautiful to the seeker after it," Virgil muttered. Running his hand through his hair, he looked up to see that it was 8:30. He'd been at his desk staring at a copy of the note for over two hours. There was something familiar about the phrase; the feeling that he'd heard it before played in the back of his mind, just out of reach. He was sure that it was the key to solving the entire thing.
God, I wish I remembered more from that cryptology class I took in college. Okay, time for a new approach. Clean slate, let's go through what we know about him, Virgil thought.
He's a man in his late twenties or early thirties. He's highly intelligent and well-educated, likely with a medical background of some sort. He's a mission-based killer, set on punishing people he feels got away with things, things the system should have punished them fore. Before Jason Dean, it seems. That change in victimology must be connected to why he sent this note, so I'll put a pin in that for now; I'll talk to Vincent about the autopsy report when he's done with it.
He seems divided; some of the torture is methodical, but some of it seems more motivated by rage than purpose. And then there's how he treats them. Mission-oriented killers don't often torture their victims; the payoff is from the kill itself. But he's feeding them, keeping them alive for a while so he can torture them.
Does he want them to know what he's done? That's it. He wants them to recognize their 'sins', perhaps even repent for them. He needs the validation that comes from them acknowledging his power and that he is correct.
Everything he does has a literal meaning and a symbolic one, he continued. Nothing has only one meaning. On the surface, he's saying that he knows that what he's doing is wrong, legally at least, but he finds it beautiful. Interesting choice of wording. Not right, not just. Beautiful. It feels like he cares more about the torture than the mission. But then why the remorse with the pseudo-burial? He's so full of contradictions. And then there's the bit at the end. "Publish me", he said, not "publish this". Which goes back to the fact that he's got one hell of an ego; he wants the focus on him. Which directly flies in the face of most mission oriented killers- they want the focus on their message.
I would almost think that there might be two unsubs, but two people being this organized and methodical is extremely unlikely. He's way too egotistical to cooperate with a partner, however submissive said partner might be.
So, we've got an incredibly smart unsub who knows it and feels like he isn't getting the attention he deserves. A younger child, maybe? Not that that would help us find him. Round up every smart, egotistical younger son in the city. We'd get the founders of every tech start-up in the city; it'd be Gentrifiers-R-Us. Virgil shook his head to clear out the unhelpful thoughts. Focus, Virge. You're on a clock. So, what kind of encryption does someone like that send? What kind of encryption has each word represented by three numbers? It's not a trifid cipher; none of the numbers would be bigger than three, and these numbers range from 1 to 192. Most number ciphers assign a number to each letter; no way in hell all of the words are three letters, and 192 and 26 do not play well together mathematically. Think, Virgil.
Fuck. Okay, let's try another new angle. The series of numbers at the end. Clearly not part of the message. 10 digits, but clearly not a phone number. 055 certainly isn't a US area code, and the number isn't long enough for a foreign dialing code plus the rest of the phone number. Wait. Maybe it's backwards? 310 is Los Angeles.
Virgil took out his phone and dialed 310-053-3550, heart in his throat. It rang twice before an automated voice informed him that "the number you have dialed is no longer in service". Damn. His heart started beating in an entirely different way when he saw that he had some new texts.
6:22 [Patton]- Hi cutie! Are you free, by any chance? It's been a really bad day, and seeing you always makes me feel so much better. <3
6:50 [Patton]- I was thinking we could get some dinner and then watch a movie or something at my place
7:48 [Patton]- Virge?
Virgil's stomach dropped. Oh god do they think I'm ignoring them? Oh shit. He quickly typed out a reply.
8:53[Virgil<3]- Hey, Pat, I'm here. I'm so, so sorry you're having a bad day. I can't hang out tonight, though. :'( I'd be with you if I could, though. It's been a rough one for me, too. Wanna talk about what's been bringing you down?
Their reply was almost instant.
[Patton]- Virgil! :D Aww, stormcloud, it's okay. Life happens; it wouldn't be healthy for either of us if you dropped everything when I'm just a little down. Besides, it was nothing, really. Just me being dramatic lol
Virgil felt himself blush at the endearment, but his brow furrowed reading the rest of the message.
[Virgil<3]- You sure? It also isn't healthy to bottle up your emotions. I care a lot about you and am always here if you want to talk about anything.
[Patton]- God, you're the sweetest! <3 I care a lot about you too. I promise, though, I really am fine. Do you wanna talk about what's bumming you out?
[Virgil<3]- I really wish I could, but I actually have to get back to it. I'll message you later <3
[Patton]- okie dokie. Don't work too late, okay?
He chuckled as he put his phone away and looked back at the note on his desk. Heather and Kurt are obviously people, Ram probably is too. Who are they, and what do they mean to him? The phone on his desk started to ring; Virgil jumped.
"H- hello? Detective Mason here." Virgil cursed himself for the shaky greeting.
"Virgil! I'm glad you're still here. It's Vincent. You said you wanted to know as soon as the autopsy was done; I'm waiting for a couple of particulates to come back, but the bulk of it is ready for you."
"Vincent, you are a lifesaver. I'll be down in a minute."
"Did you know that the candy Life Savers was invented in 1912 as a summer confectionary alternative to chocolate, which has a melting point of approximately 86 degrees?"
"I definitely did not know that, but I did know that they started as mints and didn't become the fruity candy we associate most with the brand now until the mid-1920s."
"Fruit flavors were introduced in 1921, to be exact, but they did not have holes in them like the mints did until 1925, which is probably the date to which you were referring."
Virgil laughed. "Damn, I thought I had you. I'll be right down." He hung up the phone and left for the morgue.
Three minutes later, he found himself being hugged by Dr. Nigel-Murray.
"I'm as touch-starved as the next gay, but why the hug? We just saw each other, like, five hours ago." Virgil looked slightly down at Vincent with a small smile.
"I'm sorry, I'm trying to curb my workplace-inappropriate tendencies, but, barring once during a time of great stress, people in general don't respond in kind to my facts." Virgil's heart broke for the vulnerability and pain in his voice, and he made a mental note to learn as much trivia as possible.
"That's a damn shame. You're a great guy, Vince- let's get coffee or something once I've cracked this damn code."
"That sounds quite lovely, actually. What code, if I may ask?" Vincent's smile was appropriate for the fact that they were at work, but Virgil could tell that he was practically bouncing with excitement internally.
"Our killer sent a reporter a coded message. I've got about 21 hours to crack it if I want to get this guy to come to me."
"Not to overstep, but I've dabbled a bit in cryptography; perhaps I could be of some assistance?"
"I'd love another set of eyes on this, actually. Thank you! Here, give me your number, and I'll text you a picture of it once we've wrapped up here." Virgil pulled out his phone and unlocked it to find that his messages with Patton were still pulled up. He tried to stop himself from smiling, but he couldn't.
Vincent chuckled. "He must be pretty special, to get a smile like that out of you." Virgil blushed.
"Uh, yeah, they are. At least, I think so. I hope so." Virgil fidgeted with the hem of his shirt, refusing to make eye contact.
"Sorry about the pronoun flub. So, tell me about them!"
Virgil hesitated; opening up about his feelings certainly wasn't one of his strong suits, but he liked Vincent and wanted to be his friend.
“They’re incredible. Their name is Patton, and they run We Hart Coffee just a few blocks from here. They’re so funny and kind, and I’ve never seen a smile like theirs. It’s so genuine and infectious. The world genuinely is a brighter and happier place around them.”
“You really love them, huh?”
“I- What? No. No way. That’s way too cliche. We meet in a coffee shop and are in love within a couple of weeks? This is real life, and stuff like that only happens in movies and fanfiction. And completely unrealistic. What?" Virgil snapped, seeing the grin on Vincent's face.
"Trust me, Virgil. My first doctorate advisor, Doctor Brennan, was in deep denial of her love for her partner, Agent Booth. They're now happily married with two kids. I know what repressed love looks like, and you, my friend, have it in proverbial spades."
"I'm not sure that that's the right use for that cliche, and besides…" Virgil sighed, running a hand through his hair. "So what if you're right? Even if I did love them, which I don't, they don't love me back."
"Not yet, perhaps, but you're a great guy, Virgil. Smart, funny, caring, and quite handsome. If I were into men, I'm certain I would be half in love with you, myself. Just give them time."
"Christ, Vince, I'm gonna cry at work and ruin the tough-guy aesthetic I work so hard to maintain."
Vincent hummed his disbelief. "As much as I love chatting with you, I believe you're here about a murder. Follow me, if you will."
"Right. Murder." Virgil muttered before following him into the lab.
"So, you know who he is. 18 year old Mission High student Jason Dean. You saw the burns, frostbite, and acid damage. We were able to determine that the frostbite was caused by liquid nitrogen, and the killer used hydrochloric acid. We also found that while he was less dehydrated than the part victims, likely due to being held for only about a week, as opposed to two or three like previous victims, he was far more malnourished than the others."
"God, why is he changing so much? A kid, a shortened timetable, not feeding him. What was the cause of death?"
"Strychnine poisoning."
"See, that's a huge departure, too. All of the previous torture was from knives and hands. Why the sudden change to substances? Did he get injured, or is something else limiting his manual dexterity?"
"I don't know about any of that, but strychnine is a fairly popular poison in popular culture; Agatha Christie used it three times- in Mysterious Affair at Styles, The Coming of Mr. Quin, and How Does Your Garden Grow?, and Arthur Conan Doyle used it in-"
"Oh. OH. Vincent, I love you, you know-it-all." Virgil started pacing, running his fingers through his hair.
"I beg your pardon?"
"The Murder of Roger Ackroyd."
"What? Strychnine wasn't used in The Murder of Roger Ackroyd; Ackroyd was stabbed."
"Yes, I know. The note the killer sent. At the bottom of the code, he wrote 'the truth, however ugly in itself, is always curious and beautiful to the seeker after it'. It seemed so familiar, but I couldn't place it until you just brought up Agatha Christie. Poirot said it in The Murder of Roger Ackroyd. The number. I'm an idiot."
"Breathe, Virgil. I assume that you just cracked the code?"
"Not quite. But I cracked our unsub. I knew it. I knew he'd hand me the answer. I can't believe it took me this long to figure it out."
"Okay, so how does The Murder of Roger Ackroyd help you?"
"Under the quote is a thirteen digit number. I'd bet my life that it's an ISBN for a specific printing of the book. It's an Arnold Cipher. Each series of three numbers is a page, line, and word. It was staring me in the face. I truly am Boo-Boo the Fool." Vincent was puzzled by Virgil's last sentence, but Virgil was far too agitated for questioning it to be prudent.
Virgil took a deep breath. "Okay, sorry about that. So, back to Jason?"
"Oh, right. Jason. Um, the only other thing of note that we have found at this point are fibers from a 1950s Volkswagen Beetle."
"That's gonna help a ton, as well. Vincent, you are my hero!" Virgil scooped him up into a big hug before leaving the morgue, leaving Vincent speechless for the first time in his life.
Virgil ran back up to his desk, furiously typing in his password. It took him three tries to correctly enter the number into the San Francisco Public Library website's search bar. He eventually got it, and there it was. The Murder of Roger Ackroyd by Agatha Christie. And two copies were available. The library didn't open until 12 pm the next day, however, so he went home after setting an alarm on his phone and sending a quick text to Patton.
9:52 [To:Patton]- Hey, wanna get dinner tomorrow night?
He was ecstatic to see a message from them when he got home.
9:55 [Patton]- Absolutely! You got the problem worked out? :D
10:10 [Virgil <3]- I found the solution, and will get it resolved by the end of the week. I'll pick you up on Friday at 7? We'll take a walk in the park and then House of Prime Rib, on me?
[Patton]- Are we celebrating something? Or are you trying to tell me you want to be my sugar daddy? ;P
[Virgil <3]- Trust me, Pat, if I had sugar daddy money, I'd love nothing more than to spoil you rotten. But nah, it's a combination of a small celebration and an apology for being unavailable today and for the next few days until Friday. (and i may or may not be buttering you up in hopes you'll share what's bringing you down)
[Patton]- Aww, you're so sweet! <3 (Can I call you daddy anyway?)
[Virgil <3]- Only if you want to be rewarded, baby. ;)
[Patton]- I'll be a good boy for you, daddy, I promise.
Virgil noted their preferred appellation and responded in kind with a wicked smile.
--------
The next morning, Virgil woke up half an hour before his alarm was set to go off, feeling more relaxed than he had in months. I'm finally going to get this guy.
Figuring there was no point in just waiting around, he got ready and went right to work. He knew Captain Sanders would want a breakdown of the previous night's findings before he could start following the leads he had gotten from Vincent the previous night.
He got to the station and immediately started looking into Jason Dean and the possible claim that he was a murderer. It didn't take him long to find that three Mission High students committed suicide 2 months prior named Heather, Kurt, and Ram. Virgil tracked down the police reports for the deaths. By all accounts, they appeared to be through-and-through suicides. If Jason did kill them, the killer would need to be quite close to either one of the victims or Jason himself. Linking the suicides would imply that he's close to all of them. Maybe through school? Science classes are more than likely to have liquid nitrogen and hydrochloric acid. Any teacher would have access, but I'll look more into science teachers in particular. He's displayed some anatomical knowledge as well.
Captain Sanders walked into the precinct, calling for Virgil to follow him into his office.
"So, what do you have?" he asked, after they'd arrived and shut the door.
"The note is a book cipher based on Agatha Christie's The Murder of Roger Ackroyd. The library has a copy of the specific edition I need to crack it, so I'm going to pick that up at noon, as soon as the library opens. Looking into the 'murderer' thing, there were three suicides at Mission High 5 months ago, whose names match the three not-coded words in the note- Heather, Kurt, and Ram. If they were murdered by Jason, that means the killer is close to one of them, most likely Jason himself. I think that's what the killer is alluding to in the note, but we'll see once I've decoded it. Add in the liquid nitrogen, and it points to a teacher, likely a science teacher. So I'm going to crack the code and look for other insights into him and look into Mission High science teachers. I have an updated profile, and I'll email that to you right away."
"That sounds wonderful, Mason. You've been doing excellent work; we're glad to have you."
Virgil shifted his weight from foot to foot. "I'm just doing my best, sir. If you'll excuse me, the library is about to open, and I'd like to get the book as soon as possible."
"Sounds great to me! Just send me that profile before you go."
"Will do, sir. Thank you." Virgil turned and left the room, hurrying to his computer before rushing to the library.
--
A short while later, he was back at his desk with a battered copy of The Murder of Roger Ackroyd. It wasn't difficult to decode the message, but it did take a bit of time and a lot of counting and re-counting. Word by word, the message became clear: He killed Heather, Kurt, and Ram. Find the weapon; I know he had it. It is your evidence.
Virgil sat back in his chair once he'd finished, puzzled by what the note revealed that he hadn't already deduced. 'He' has to be referring to Jason. He knew we'd find out the reasons for him choosing the previous victims, but he needed to be sure we'd know why he thinks Jason deserved to die. I looked at the police reports for those deaths; the gun used to kill Ram and Sweeney was recovered on-site and is in police custody. He's obsessed with his mission, though. He wouldn't make this claim if he wasn't sure. I'll look into that once we've caught our killer. For my peace of mind, at least. Virgil cracked his knuckles and picked up his phone.
"Roman Prince, SFGate, how can I help you?"
"Roman, it's Detective Mason. Can you come down to the station right away?" The responding scream was so loud, Virgil had to move his phone away from his ear. "I'll take that as a yes?"
"Absolutely, Detective. I will be there as soon as physically possible."
"Don't break any traffic l-" The line went dead, cutting Virgil off.
--
Far sooner than could have been legal, Roman skidded to a stop in front of Virgil's desk.
"HelloVirgildidyoucrackthecode?DoIgettowritearesponse?CanI-"
"BREATHE, Roman." Virgil stood, grabbing him by the shoulders. "Yes, I cracked the code. Yes, you will publish a response tonight. But I'm writing it. I assume your laptop is in your bag?" Roman simply nodded- he knew that if he tried to speak, he'd start rambling again. "Fantastic. Let's get going."
45 minutes (and one call from Captain Sanders to Dan Humphrey about how not allowing it to be posted immediately would be obstruction of justice) later, a new post was live on SFGate's website. It was 4:02 pm, two hours before the deadline.
An Open Letter to U N Owen
It was a pleasure hearing from you. While I obviously cannot condone your methods, you are correct that our justice system is imperfect, and those imperfections need addressing. You gave me quite a puzzle, and I enjoyed solving it. It was clever, but not clever enough. I hope you'll forgive me for not following your directions; please let me know if this is inadequate.
Vq rwv kv dnwpvna, aqw'tg ytqpi. Jg fqgup'v jcxg kv, yg fq. Yg'xg jcf kv htqo vjg xgta dgikppkpi. Dwv aqw cntgcfa mpqy vjcv. Aqw'tg hct vqq engxgt vq jcxg pqv mpqyp vjcv. Wpnguu K'o qxgtguvkocvkpi aqw, yjkej ku c fghkpkvg rquukdknkva. Aqwt qvjgt cuugtvkqp jcu dggp pqvgf, cpf K uygct vq aqw vjcv K yknn rwtuwg vjcv qpeg yg ugvvng vjku ocvvgt dgvyggp wu.
Hqt pqy, vjqwij, aqw ujqwnf mpqy vjcv aqw'xg iqvvgp unqrra, cpf vjcv kv'u qpna c ocvvgt qh vkog dghqtg K hkpf aqw cpf tgrca aqw kp vjg ngicn hqto qh vjg eqkp aqw icxg vjgo. Aqw yknn (ogvcrjqtkecnna) jcpi hqt vjku.
Sincerely,
Det. Mason Poirot II
--------------------
Logan refreshed SFGate.com for the thirteenth time that day and was finally rewarded for his tenacity; the post was less than five minutes old. He read it twice, rage simmering in his chest and a smile on his face. "Detective Mason," he said to his empty apartment, "a worthy adversary indeed. The game is on."
#virgil sanders#logan sanders#sanders sides fanfiction#ts ff#roman sanders#patton sanders#moxiety#analogical#prinxiety#sanders sides#trust me#trust me fic#my writing#serial killer au
9 notes
·
View notes
Text
Cryptographic Methods Used By Cryptography Assignment Help Professionals
Cryptography Assignment Help going before the forefront age was feasibly synonymous with encryption, the change of information from an understandable state to obvious hot air. The originator of an encoded message shared the unraveling technique anticipated that would recover the main information just with proposed recipients, thusly blocking unfortunate individuals from doing moreover. The cryptography writing Help regularly utilizes the name Alice ("A") for the sender, Bob ("B") for the planned beneficiary, and Eve for the foe. Since the improvement of rotor figure machines in World War I and the approach of PCs in World War II, the strategies used to complete cryptology has turned out to be progressively perplexing and its application more boundless. Prior cryptography was viably synonymous with encryption, however, these days Cryptography Assignment Help is chiefly in light of numerical hypothesis and software engineering practice.
Cryptographic Methods Used By Cryptography Assignment Help Professionals
Symmetric-key Cryptography: Both the sender and the collector share a solitary key in Cryptography Assignment Help . The sender utilizes this key to encrypt the plaintext and send the figure content to the recipient. On the opposite side, the beneficiary applies a similar key to decode the message and recuperate the plain content.
Open Key Cryptography: This is the most progressive idea in the last 300-400 years. In Public-Key Cryptography two related keys are utilized. The open key might be unreservedly appropriated, while its combined private key, remains a mystery. The general population key is utilized for encryption and for decoding private key is utilized. https://www.programmingonlinehelp.com/ have the best cryptography assignment writing services
Hash Functions: No key is utilized as a part of this calculation in Cryptography Assignment Help . A settled length hash esteem is processed according to the plain content that makes it unthinkable for the substance of the plain content to be recuperated. Hash capacities are likewise utilized by numerous working frameworks to encrypt passwords.
symmetric-key cryptography
Symmetric-Key Cryptography alludes to encryption strategies in which both the sender and recipient share a similar key. This was the main sort of encryption openly known until June 1976. Symmetric key figures are executed as either piece figures or stream figures. A piece figure enciphers contribution to squares of plaintext instead of individual characters, the information shape utilized by a stream figure. The Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) are square figure plans that have been assigned cryptography benchmarks by the US government. In spite of its expostulation as an official standard, DES remains very prevalent; it is utilized over an extensive variety of uses, from ATM encryption to email protection and secure remote access.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text

7-10/100
It’s been a little challenging to keep up with posting lately. I decided to go home this weekend to help my parents around the house, especially since my dad recently got a hernia. Until he gets back on his feet, I wanted to give them as much as my time as possible. I pinky promise I’ve been productive. To compensate, I’ll disclose a few productive tidbits of my missed days:
7/100:
Listened and took notes from a bioinorganic lecture
Had my first day of the semester for being an intro biology lab teaching assistant (but I also worked last semester)
Did an assignment for my Modern World class
8/100:
Listened and took notes from a Codes and Cryptography lecture
Began Codes and Cryptography homework
Took notes for my upcoming Modern World class (pictured above)
9/100:
Helped my mom by doing some grocery shopping
Helped cook dinner for my parents
10/100:
Found a really neat recipe for vegan/gluten-free mug cakes
Did laundry
Helped cook dinner with my parents
I’m looking forward to returning back to campus tomorrow and getting more school work done with my day off. Also munching on the vegan/gluten-free cookies my mom made for me to bring back.
10 notes
·
View notes
Text
Satori (Between the Lines) - Part 1
Sakura’s hand fidgets around Ino’s as she stares up at the surprisingly nondescript building. It is a bit shabby, certainly not befitting the reputation spoken of among civilians in hushed tones.
Konohagakure Intelligence Division.
Sakura swallows and clutches tighter to Ino, willing herself to walk through the door. Why, oh why, does she have to be here?
“Relax, Sakura-chan!” Ino says, watching Sakura with those guileless, confident blue eyes. When she looks at Sakura that way, she feels like she can do anything. “You’ll be working with my dad most of the day and everything he does is boring!”
Sakura thinks back to whispers snatched among parents on the playgrounds and in the civilian markets, away from shinobi. It is surprisingly simple for a child enrolled in the Academy to eavesdrop on such adult conversations. In the moment, Sakura felt giddy, really feeling like a true ninja as she gathers information to share with Ino. Now, remembering the tawdry tales of severed limbs and hypnosis, Sakura regrets her eagerness.
She never expected to be assigned a field experience assignment with Konohagakure Intelligence Division.
“Sakura,” Ino says, taking in her stiffness and pallor. “Seriously, tou-chan has already promised me that he’ll keep an eye on you. You’ll just be sorting paperwork. You won’t be anywhere near the actual action.”
“Promise?” Sakura asks.
“Promise,” Ino replies, tucking Sakura’s hand into the crook of her arm and dragging her forward. “C’mon. I have to head over to my assignment too. Genma-senpai is surprisingly a stickler about punctuality. I don’t want him tattling to Mizuki-sensei!”
Somehow, Sakura’s feet begin to move and they pass through the heavy doors into the building. There is an artificial cheer about the place, an austere colorfulness perhaps sharpened by the lack of natural light. There are no windows, though Sakura didn’t really expect there to be any. The halls are silent even as they pass by people. Most wear masks and walk with a lethal grace. Some wear leather aprons and gloves. These Sakura turns her gaze away from. It is strange to see Anbu walking around beneath the florescent lights, as they so often work in shadows. Sakura and Ino head up a few flights of stairs, making their way into an open office space.
“Tou-chan!” Ino exclaims, releasing Sakura and bounding toward her father. They embrace, Inoichi chuckling as he ruffles his daughter’s hair. “I brought Sakura!”
“Hello, Sakura-kun,” Inoichi greets, reclaiming his seat and smiling at her kindly. Sakura has always liked Ino’s father, the laugh lines in his face making him kind. “I’m glad you were able to make it. Ino, I’ll see you at dinner. You should hurry along to your post.”
With one last squeeze of encouragement, Ino is gone and Sakura is left feeling bereft.
“Come with me,” Inoichi says, leading Sakura across the hall. They enter into a small, cramped room, furnished with a chair, desk, and stacks upon stacks of documents. They’re nearly swimming in papers. “Take a seat,” Inoichi says, taking pity on the girl. He sees the way she folded in on herself the moment Ino left her side. He waits for her to take a seat in the sole chair in the room before he pushes a large stack of documents her way. “While you are here, Sakura-kun, you will be sorting the missives that come in from our informants.” He points to the top left corner of one of the documents. “Feel along the edges there.”
Sakura does so. “There’s...raised dots?”
Inoichi nods. “Yes, that let’s us know which department the document goes to. Can you tell me the pattern on that one?”
Sakura concentrates, running the pad of her finger across the paper. “There’s a vertical line of three dots, followed by two single dots.”
“Well done, Sakura-kun!” Inoichi praises, taking the file and discreetly double-checking it as he places it into one of the boxes. “That is the signature for the quartermaster.” He passes her a scroll. “This displays all of the codes as well as the departments each code is meant for. You will be sorting these during your time here. With the preparations for the chunin exams, we’ve become a bit backlogged. Take your time; there’s no need to rush.”
Sakura looks over at the large pile of documents, finding them quite daunting despite Inoichi’s encouragement. She picks up the next one, blinking as she realizes that she cannot read any of the text. The symbols are neither hiragana or katakana. They don’t even seem to be kanji.
It’s strange, especially as Sakura prides herself on being an excellent reader. Her bedroom stacked full of books and worn library card are testament to her love of reading. She’s one of the very few people in her class who can even read kanji.
“Yamanaka-san,” Sakura begins, voice barely above a whisper. Inoichi turns his attention her way regardless. “What are these?”
“Ah,” Inoichi says. “All of these documents are written in code to keep prying eyes from reading their contents.” Sakura flushes guiltily. “You do not need to concern yourself with that, just make sure they are sorted into the right piles and someone else will decipher the codes.”
Sakura nods meekly and takes a seat, running her fingertips along the next document. Two horizontal dots followed by a cluster of four all bunched together. She checks the scroll he gave her. “This is for the Council of Elders. Where do I need to place it?”
“Council of Elders: Shimura, Utatane, Mitokado,” Inoichi replies almost to himself, stepping away from her and rummaging around for a series of small boxes stacked upon each other. He comes back, placing down the boxes with a smile to Sakura. “This here is where you’ll place the documents once they are sorted.”
Sakura looks at the boxes, taking in the names that go alongside each of the individual boxes. She slips the document for the Council into their respective box.
Inoichi looks her over, making sure she’s settled. Sakura looks small, swallowed by the large chair and the disorganized pile of documents around her. Still, she seems comfortable enough, already running her fingers over the next document. “I have to get back to my duties,” he says, waiting until she looks up at him. “I’ll be right across the hall if you need anything.”
Sakura nods, watching as Inoichi leaves the room. Then she turns back to the documents at hand, a determined smile set upon her face.
It is time to get started.
“How’s your assignment going?” Sakura asks, passing Ino a bento box.
Ino sighs, showcasing stained fingers. “I think my hands are going numb from all of the polishing and sharpening I’ve been doing. Genma-senpai is a perfectionist, but now I know the right balance to both short and long form kunai and shuriken.” She changes the position on her chopsticks, holding them like a weapon. “I can throw a kunai perfectly now.”
“That’s great,” Sakura replies, as she finishes a bite of sticky rice. “Could you show me later?”
“Of course,” Ino says. “Tou-chan says you’ve been doing a good job with the Intelligence Division.”
It’s a leading statement, one that makes Sakura light up. “It was scary at first, but the people there are really nice.” She pauses, nose wrinkling. “There’s one lady, Anko-san, she’s kind of scary, but she’s also funny and secretly nice. I think she’s the one who leaves me umeboshi sometimes.”
“And how’s the work itself? Tou-chan said that you sort documents. It sounds kind of boring,” Ino says.
“No, not at all!” Sakura replies, emphatically. “All of the documents are written in code. All sorts of different codes. Remember when Mizuki-sensei covered cryptography?”
“My ears are burning!” a voice sings out behind them.
Both girls jump, turning to look at Mizuki who is crouched behind them, giving them a quizzical smile.
They are seated out on a grassy hill on the Academy property, where many students hang out between and after classes. It’s one of Sakura’s favorite places in Konoha, allowing her to look out over the downtown merchant section of the civilian sector. It’s comforting, as the Haruno clan has a shop among the section, run by her aunt and uncle. When her parents are out of town, being able to see the Haruno shop is soothing.
“Hi Mizuki-sensei,” Ino greets. “We’re just talking about our field experience assignments.”
“You’re working with Shiranui-san in the armory, aren’t you Ino?” Mizuki says, stroking his chin. “Sakura, you’re in the Intelligence Division with Yamanaka-san?” Both of them nod. “Cryptography, huh? You cracked any codes, Sakura?” His smile is kind and teasing.
Sakura bites her lip. “Not really,” she says. “I can tell which codes are the same and even the patterns, but not really any of the words.” That isn’t quite right. She has managed to decipher certain small words and even repeated code names but she has yet to figure out the contents of any of them.
“Well, if you want to get better at cryptography, there’s some books I can suggest for you,” Mizuki says. He has a soft spot for Sakura, the quiet, intelligent first-generation student studying to be a shinobi. There’s a common ground between them; she’s a younger reflection of who he once was, before all the destruction and pain.
“That would be great!” Sakura exclaims, grinning up at him.
“Just make sure to share any secrets you learn with me,” he says, winking.
She is almost vibrating wiggling with excitement and anticipation as they head back to class after Mizuki promises to compile a list.
It is time to get to work.
Sakura frowns down at the document before surreptitiously glancing up and around. No one is in the room with her, however, Sakura cannot help feeling a guilty squeeze as she scribbles something on her sheet of paper. She’s cycling through substitution ciphers, seeing if any stick.
R.
The rest of her sheet is filled with blotted out letters, crossed out nonsense words that she attempted a variation on the same substitution cipher on. Cipher cracking, at least the process of learning it, is slow going.
E.
This is a document for the Council of Civilians; Sakura assumes that it has the least amount of security when compared to the documents for the Hokage or clan heads.
P.
There is a slight murmur and Sakura pauses, fighting to keep her expression neutral as a pair of conversing adults, both wearing gloves and aprons covered in a dark, viscous liquid, pass by. Once she is certain they are gone, Sakura returns to her paper.
O.
Sakura’s guilt is assuaged slightly by the knowledge that deceit and deception are the bread and butter of shinobi. While many in Konoha are trained for full-frontal assault, the class of shinobi is dedicated to stealth and espionage. Konoha is still in the mindset of gearing students up to be soldiers, not shinobi.
Sakura does not want to have a career as cannon fodder.
R.
So really, Sakura thinks to herself, this is just applied practice of the skills that will be vital to her one day. In fact, they may just be vital now.
T.
Sakura’s victorious smile is so wide that it hurts her cheeks. This is the first time she has decrypted a full word.
At least, she believes it to be the intended word.
The encryption leaves no spaces between any of the letters so she’ll have to continue the process to see if the rest of the message aside from “Report,” makes sense.
Still, it is rewarding to see some progress.
With determination fueling her, Sakura sets to her task once more with fervor, silent room filling with the sound of her pen scratching away.
Sakura inhales deeply, settling further into her seat as she takes in the scents of old paper and warmth and coziness. The library is a second home to her, more so when her parents are out of town as they are right now. She rubs her fingers along the parchment within the book, enjoying the coarse texture of the heavy paper.
There are only a few people in the library at midmorning like this and Sakura likes the quiet. A couple of civilians and a chunin guard who is on break are the only other occupants of the library.
Sakura bends her head back over her book, picking up where she left off on scytales and their function within cryptography. Apparently, scytales fell out of fashion in Konoha during its early days, when the First Hokage ruled, but they are still popular in Iwa and Suna. She wonders if there are any scytales in the Intelligence Division’s storage or if she herself could create one. She wants to try it out with Ino.
The slight rustling of clothing draws Sakura out of her reading. She looks up, blinking as a boy takes the seat across from her. The boy is tall and lithe, wearing a partial mask that obscures his eyes and ears but leaves his nose and mouth clear. Between his dark hair neatly combed hair and mask, Sakura guesses that he’s an Aburame. She’s never seen him before, even though he’s certainly of age to attend the Academy, as all good clan children do.
“Hello,” Sakura greets warily, shifting her book closer to her chest. “I’m Sakura.”
He cocks his head to his side, assessing her. She can feel the weight of his gaze and she flushes. “I know,” he replies.
“You do?” Sakura asks with a frown. “How?”
“You come to the library quite often. Every Tuesday, Thursday, Saturday, and Sunday at the very least, if not more often. I am at the library everyday; it was not difficult to observe the most frequent purveyors of the library, including yourself. I overheard the librarian say your name,” he says, a slight smile on his face as he gives the explanation. He doesn’t seem or sound smug, though Sakura cannot be sure.
“Alright,” Sakura says, bringing the book even closer to her chest. She isn’t sure how she feels about this, this invasion of her sanctuary. She hasn’t noticed the boy’s attention over the past months, but now, sitting in front of him, he doesn’t seem to have ill intentions. “Obviously, I have not been nearly as observant. What is your name?”
His smile widens. “What do you believe it to be?”
Sakura straightens up, putting the book down on the table as she chooses to engage in his offered game. It is her turn to look him over. “I know that you are of the Aburame clan,” she says, concentrating on him. As she pays him closer attention, Sakura hears the slightest buzzing noise emanating from beneath his skin. Her mouth pulls down into a thoughtful frown. Shino is already a host as well, but she has never heard him buzz like that. Perhaps this boy’s control is lacking?
“You don’t attend the Academy, even though you’re older than me. Did your parents choose not to enroll you? No, you are from one of the founding clans; all children are enrolled unless they are found to be lacking or dangerous to other students.” She hears the buzzing increase ever so slightly in pitch as a frown tugs away the boy’s smile. Got him. “You struggle to control your bugs, which is why you are not enrolled in the Academy.”
Sakura looks at the boy and, for a moment, she fears she’s overstepped. Then his scowl clears away and he begins to clap. “Bravo,” he says. “You may not yet be self-aware, but you do possess skills in observation. In time, you will hone your self- and situational awareness or you won’t make it far in this career. But still, you haven’t answered my question. What is my name?”
“The only Aburame that I have met is Shino,” Sakura says, pausing at the boy’s nearly imperceptible flinch. “Shibi-sama is the clan head,” she continues, again catching the way he flinches.
Whoever he is, he is much more closely related to the clan head than she thought. Sakura stops for a moment, closing her eyes as she pictures the genograms that they made in class a year ago. Sakura enjoyed making hers at the time, but the main interest in the class was clan children comparing genograms to each other, side by side. It was a competition of sorts for them, a measurement of how successful their clan was.
As such, Sakura made special note at the time of the genograms of the four noble clans of Konoha, Choji’s, Ino’s, Hinata’s, and Shino’s, as well as Sasuke’s genogram since the Uchiha ran the Konoha Military Police Force.
There is only one person this boy can be.
“You are Aburame Torune,” Sakura says, opening her eyes once more. “Shibi-sama has adopted you, right? Shino is your cousin and now adopted brother.”
He nods, a bright smile gracing his features. Her victory feels like a triumph for him. “Well done.”
“So why approach me now?” Sakura asks, looking at him with new eyes. Aburame Torune, the adopted son of the clan head. “You’ve been watching me for weeks, months even. What changed?”
He turns his gaze downward, embarrassed. “I just thought it was time to introduce myself.” His eyes light on her stack of books. “How is your study of codes going?”
“Well,” Sakura says, looking down over her selection of titles. Most are Mizuki’s recommendations, but some she has gathered based on citations within other cryptography books. Sakura has made a fine dent in the library’s collection and she believes she can finish them all within the next month. “I’ve learned transposition and substitution ciphers well; at this point, I can usually recognize them on sight.” She gestures down to her current book, on the history of subterfuge. “Now I’m getting some historical examples of steganography.”
Torune nods, though he doesn’t really seem to understand. Sakura doesn’t mind. In fact, she bites her lip, warring with herself for a moment.
“Would you like to go stick hunting with me?”
“Stick hunting?” he repeats, obviously lost. “Why sticks?”
“We need them to create scytales,” Sakura says, nodding decisively. She stands, packing away her things. “We’ll need to find three sticks of equal thickness. One for Ino. One for me. One for you.”
Torune’s responding grin is a breathtaking thing as his buzzing picks up in frequency. There’s something soothing, almost melodic about the hum. “Lead the way.”
The two children head for the door eagerly, leaving behind a neat towering pile of books.
Sakura keeps her concentration on the documents before her, ignoring the uproar outside the door. She is well-used to how loud Anko and her associates can be at this point and she barely flinches when they get started.
That is, until a large man barges into the room.
“Where is it?” he roars.
Sakura’s hand immediately goes to the kunai strapped at her calf, pausing as Inoichi charges in after the man. She keeps her grip on the kunai, watching, assessing as Torune often reminds her to do.
Ibiki stops, blinking at her. “Who are you?”
“Ibiki, I need you to calm down. This is Haruno Sakura, she’s the Academy student assigned to Konoha’s Intelligence Division for her field assignment,” Inoichi says, getting between Ibiki and Sakura, hands up in a placating gesture.
“I don’t have time to be calm,” Ibiki says, voice slightly lowered from the bellow it was but moments ago. He is huge and hulking, making the small room feel even smaller. He wears a thick black leather trench coat, one that is similar enough to the leather aprons worn by other Torture and Interrogation Force operatives: his job is obviously related to wetwork. The only aspects of him exposed, his face and hands, are heavily scarred. “I need a document right now!”
They both round on Sakura, looking at the stacks and stacks of unsorted documents.
“Which document do you need, Ibiki?” Inoichi asks, pinching the bridge of his nose.
“I need Fox’s report on his infiltration of Kirigakure’s hunter-nin,” Ibiki says, cold gaze on Sakura. Sakura realizes with a start that the shininess of his leather coat is fresh blood. She turns her gaze down to the remaining documents, searching. “The report is for the Council of Elders.”
Inoichi glances at the boxes, sighing. “These things take time; everything is in code. Sakura-kun hasn’t sorted those—”
“Here!” Sakura calls, interrupting Inoichi in her excitement. She’ll be mortified later, when she’s out of the moment and aware of the possible ramifications of interrupting a clan head. She picks up the scroll, proffering it to Ibiki. “This is the document you need.”
Sakura’s smile fades at the stunned silence that greets her. Ibiki snatches the document from her, running his finger along the border to make sure it is addressed correctly. He squints at the document, frown making his scarring even more severe.
“I’m no code breaker, but I do recognize Fox’s unique handle here,” he tells Inoichi. He raises his eyes, locking onto Sakura. She swallows, tempted to duck her head and hide away. She resists, however, and stays steady. “How did you figure it out so quickly?”
“I’ve…” Sakura squeaks. She stops, clearing her throat. “I’ve been studying ciphers in my free time.”
“Since you started here.”
It isn’t a question, but Sakura nods anyway. “I wanted to do a better and more efficient job here.”
“That’s why Ino has a scytale!” Inoichi exclaims.
“I made one for her,” Sakura says softly. “We write messages to each other.”
Ibiki moves suddenly, striding forward and slamming his hands down on the table before Sakura. She bites the inside of her cheek to keep from jumping. His face is impassive and Sakura bites down on her cheek until it bleeds.
Then, he grins, the pull warping his scars into an expression even more terrifying than his scowl. It looks uncomfortable on his face, as if the muscles are unused to it. Sakura gets the sad feeling that he doesn’t smile too much.
Inoichi makes a noise, as if he wants to interfere.
“There’s someone I want you to meet, girl,” Ibiki says, amusement thick in his voice.
Sakura, reading the apparent mischievousness in his face, gulps.
#my fic#satori (between the lines)#sakura haruno#torune aburame#sakura & torune#sakura & ino#ibiki morino
226 notes
·
View notes
Text
Photo stamp remover 8.3 key


You can now deploy Horizon Connection Servers and Horizon Agents in different data centers across WAN, as long as the Horizon Agents are located within 120ms of the Connection Servers.
HTML Access is now supported in an IPv6 environment.
You can now connect to the event database using SSL.
See Using the Legacy Microsoft CryptoAPI Standard. If you have a use case requiring use of the legacy CryptoAPI standard, you can still do so.
By default Horizon now uses the Microsoft Cryptography API: Next Generation (CNG) standard.
Cross-Origin Resource Sharing (CORS) is now enabled by default.
See Add vCenter Server Instances to VMware Horizon. Deployment type allows you to specify whether your vCenter is in a private data center or in a specific public cloud data center.
When adding a vCenter Server instance, you can now select a deployment type.
Manage Machine Maintenance - used for toggling machines manually to and from maintenance state.
Manage Machine Alias and User Assignment - used for machine user assignment and machine alias assignment.
Both new privileges are children of the Manage Machine privilege: See Privileges for Managing Machines and Object-Specific Privileges.
Role creation and edit now offer two new privileges applicable to access groups.
You can now use smart card caching emulation for non-Microsoft Windows client connections.
Users belonging to untrusted domains can use SAML authentication, True SSO, and smart card authentication.
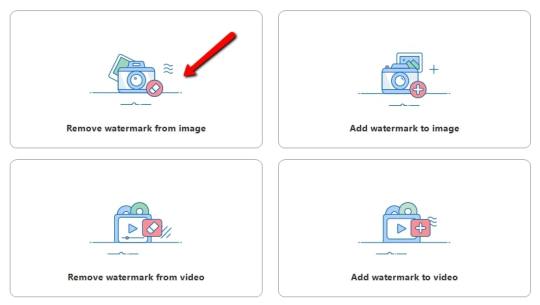
See Using VMware Horizon Desktop Recording.
You can record desktop sessions for troubleshooting and auditing sessions.
See VMware Configuration Maximums for detailed scalability metrics.
Horizon supports 20,000 desktops and sessions per Pod.
See Estimating Memory Requirements for Virtual Machine Desktops.
5K and 8K client display resolutions are now supported (Blast only).
See Choosing ClonePrep or Sysprep for Customizing Your Virtual Desktops.
Microsoft Sysprep is now supported for customizing instant clone virtual machines.
See Worksheet for Creating an Instant-Clone Desktop Pool.
When creating or editing a desktop pool with session type Application and Desktop or Application, you can select the Bypass Session Timeout setting to allow application sessions to run forever.
See Worksheet for Creating an Automated Instant-Clone Farm in Horizon.
The Bypass Session Timeout setting allows application sessions to run forever.
The actual release date can vary based on business needs and engineering schedule changes to address critical customer requirements. This information is grouped by installable component.īeginning with this release, version numbering is based on the planned year and the month of the release. VMware Horizon version 2106 provides the following new features and enhancements.
Nonoperational Features in This Release.
No Longer Supported Features in This Release.
It always gives me accurate results.These release notes include the following topics: I’ve used it for a really long time and never once had a problem. This one does a great job removing photo background online as well as replacing. With its user-friendly and ad-free interface, a first-time user can create the most stunning photo with the fancy background templates it offers. It’s so much better than any other tools I’ve used before. This is exactly what I’ve been looking for. I successfully changed the background of my passport photo to white with this amazing tool. It not only erases my photo backgrounds but also provides multiple templates. This online background eraser does what it promises and does it very well. The AI technology helps me remove image background online with a single click. One of the best online photo background erasers by far.

0 notes
Text
Annotated edition, Week in Ethereum News, April 13 issue
The newsletter didn’t get sent until Monday morning, so a bit late for me. The reason why is that last week I was busy securing the 4 major sponsors necessary to keep this newsletter free for everyone. Hopefully news on that front will be coming soon. I’ll be very grateful to the folks who help Week in Ethereum News stay free, and hopefully you will be too. As I’ve told everyone I talked to, as an editor, the product will remain the exact same. As a publisher, it’s very important to me that it’s a productive relationship for everyone.
Here’s the most clicked, preserved in a screenshot since my tweets auto-delete
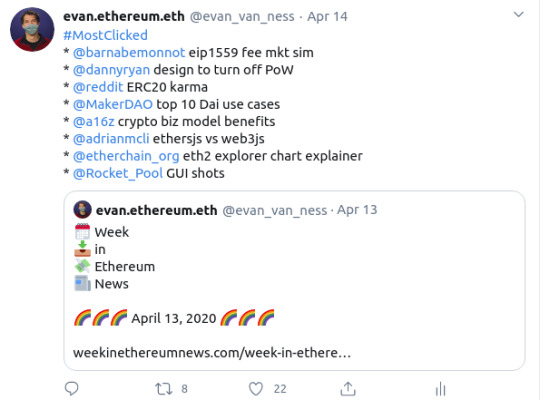
People are excited that the fee market is getting simulated. This particular piece is probably a bit too simplistic, but Barnabe will be publishing more soon, with more realistic assumptions about endogenous demand.
People are excited because the fee market change will 1) make it easier for app devs to get their user transactions included and 2) because every transaction will burn some ETH, and 3) it kills economic abstraction forever, something I remember Gavin pushing quite hard in 2015 and 2016.
Meanwhile, Danny published a design on turning off PoW. Even though it’s long, it’s still rough and just an initial plan. The focus has been on launching the eth2 chain, but as soon as it is launched, the goal is to turn off the wasteful electricity burn (and issuance!) of PoW.
Eth1
EIP1559 fee market change simulations, assuming demand is exogenous
EVM Bytecode Merklization – merklize code chunks for block witnesses, estimates 40-60% reduction
Some more estimates on code merklization based on recent blocks
One important bit of stateless Ethereum is trying to merklize code chunks to shrink the witness size so that full nodes do not have to hold the full state. Two different estimates published this week on how important and feasible it is.
Eth2
Bitfly’s explanations of eth2 block explorer charts
PegaSys’s Teku client fully syncs with the Lighthouse testnet
Latest Nimbus client update. Getting up to the multi-client testnet spec, networking improvements, interop ready with Lighthouse
SigmaPrime’s update fuzzing the eth2 clients. Catching bugs, new fuzzing engine
Work on formally verifying the eth2 spec using Dafny
A look at the GUI for Rocketpool’s decentralized staking pool
Aditya’s how FFG is implemented in Eth2 explainer
The clients are all speeding into launching the multi-client testnet. I suppose the other stuff mostly speaks for itself.
Eth2, post-BeaconChain launch
A design for merging eth1 and eth2 clients to turn off PoW
Better attestation aggregation algos
Verifiable precompiled contracts
An approach for cross-shard transfers at EE level
Perhaps people forget that when Ethereum launched in July 2015, it didn’t actually do anything. It’ll be the same with Eth2, so on the research front things shifted awhile ago towards all the things necessary to make eth2 work.
Stuff for developers
Solidity v0.6.6 and v0.6.5 – ‘immutable’ new major feature, tuple assignment bugfix, and memory array creation overflow bugfix
Truffle v5.1.21 adds Solidity’s immutable
wighawag’s Buidler Deployment Plugin
Not new, but a comparison of ethers.js and web3js
Example of using web3modal (former web3connect) with vanilla Javascript
MelonJS v1 to interact with Melon’s deployed code
Tool for decoding Ethereum storage
Arrays and maps in Solidity
Yul+ Remix plugin
Chainlink redeployed ETHUSD contract; 2 weeks to migrate from old code
Maintaining offchain NFT data using IPFS
SQL queries on DuneAnalytics tutorial
Django with web3py tutorial
Lots of devs excited about immutable.
One problem Ethereum has is that everyone prefers RicMoo’s ethers.js yet most people still use web3js because the tutorials push new devs to it.
Ecosystem
discv5: an explainer of Eth networking’s peer discovery protocol
Eth brand survey
I really appreciate Dean’s networking explainers, I find them quite well-written, and it makes me a little mad that he’s a high school dropout who writes better than I do.
Enterprise
from the founder of Simple, Sila: payments API to take on ACH
EEA mainnet survey
Hyperledger Besu v1.4.3 – adds eth/65 for better networking, issue found for private transactions created with v1.3.4 and before
Besu now running eth/65 too, which as we found out a few weeks ago, cuts bandwidth usage by a crazy amount. A nice change from Péter Szilágyi.
Governance, DAOs, and standards
MakerDAO’s 13 improvement proposals to decentralize governance
TheLAO launches April 28
how to create a bankless DAO
EIP2593: Escalator algo fee market change
This week a lawsuit was filed against Maker. Personally I think if you’re running to the US courts to bail you out (or assisting that effort) of your use of leverage, then you deserve all the opprobrium that you get.
Application layer
Reddit is rolling out the tokenization of it its karma for more than just r/EthTrader?
Status v1.2, adds Waku to replace Whisper for better messaging
SmokeSignal.eth, post by burning Dai interface prioritizes higher burn
Autumated dollar cost averaging of your stablecoins on Uniswap
Suggestions and programs in Colony
Overview of DxDAO’s Omen prediction markets
Inspect, DeFi transparency registry
Fairmint’s continuous securities offering is live on mainnet
The Reddit thing seems like an unintentional leak, where they were trying to roll it out to just one more community but it got in the app, and now they’re unsure what to do it. But they’ve been playing with this for years - I believe a job listing first surfaced for a dev to play with this stuff in late 2016 (may have been early 2017)
My weekly DeFi ratio: i’ll call it 3/8 to be DeFi, which is lower than normal. On the other, the BTC++ could have very easily been in this section (it’s all a bit arbitrary, no?) as well as the 10 Dai use cases post, etc... which would have changed it quite a bit.
Tokens/Business/Regulation
PieDAO’s BTC++ is live on mainnet, a token of comprised of multiple versions of locked/synthetic BTC
Is tokenized BTC on Ethereum good for ETH?
Top 10 use cases of Dai
NFTScribe – attach a message onchain to an NFT while you own it
a16zcrypto: crypto’s biz model isn’t that different but who benefits is
Jesse Walden’s article is now the #2 most clicked - by the time I do the #MostClicked, it’s usually pretty steady, but this time it moved up quite a bit in the subsequent 24 hours.
Betteridge’s Law of Headlines suggests the answer is no, but of course the answer is actually yes. People using ETH is a good thing, even if it is to speculate on the price of unsustainable memecoins. It’s impressive how many people are finding different ways to bring the orange memecoin into ETH, using different trust assumptions on BTC side or different use cases.
Case in point: Atomic Loans did a big push yesterday, where you can lock up BTC and get stablecoins. Pretty juicy rate to lend at - 9% for USDC and 9.5% for Dai.
General
Chicago DeFi Alliance formed to connect market makers and DeFi startups
CryptoHack: online puzzles to learn cryptography
UTokyo paper on digital courts
You can join the trusted setup ceremony for Semaphore, a zk privacy layer for apps
The CryptoHack site moved up and would have made the most clicked. Not a shocker that this audience wants to learn more crypto. Even app devs probably need to learn that the best architecture often involves more crypto and less state storage.
If you haven’t done a trusted setup ceremony, I highly recommend doing one. Contribute your entropy to the future! Semaphore is very neat gadget to help app developers be able to add privacy, which is a very needed layer to prevent dystopia.
0 notes
Text
Assignments Based On Cryptography Techniques
Assignments Based On Cryptography Techniques
The following are the three different Online Cryptography Techniques that a student must learn as part of the computer science course when they want to excel in cryptography concepts.
Public key cryptography - It explains the asymmetric encryption where there would be two key cryptosystems used to keep the connection secure between the sender and the receiver. If you are stuck in writing the assignment on this topic, you can seek our experts' help. https://www.allhomeworkassignments.com/ are available round the clock to offer you with the required help.
Secret key cryptography – This Online Cryptography Technique would make use of a single key. The sender will use this key while sending a message to the receiver, and the same key is shared with the recipient so that they can decode the message and read it. In this type of technique, there is only one key that is used for encryption and decryption. Many students get confused with this concept and look for help. Without taking stress on you, hire us. https://www.allhomeworkassignments.com/ have professionals who do extensive research in writing the assignment for you.
Hash function - The integrity of the message is checked using the hash function to ensure that a hacker does not compromise the data. It makes use of a particular length has to value over a key.
Get The Best Cryptography Assignment Help Online
Our https://www.programmingonlinehelp.com/ Programming Assignment Help experts provide affordable cryptography coursework help to global students. They ensure that students get excellent grades by adhering to the guidelines, deliver clean codes and provide well-commented solution.
Cryptography is used to hide data – to render data unintelligible through its transformation into an unreadable state - and to ensure that data has not been altered in transit. If you are stuck in writing the assignment on this topic, you can seek our https://www.programmingonlinehelp.com/ experts' help. It can also be used to ensure the authenticity of the data as well as the authenticity of the data source. Cryptography supports confidentiality, integrity and authenticity in cryptography homework help It does not support availability
Hire Cryptography Assignment Help Experts to Boost the Grades
Cryptography or cryptology is the training and investigation of strategies for secure correspondence within the sight of outsiders called enemies. Cryptography is related with the way toward changing over normal plain content into garbled content and the other way around. It is a technique for putting away and transmitting information in a specific frame so those for whom it is proposed can read and process it. Cryptography Assignment Help shields information from burglary or alteration, as well as be utilized for client confirmation.
All the more, by and large, Online Cryptography Topics is tied in with building and investigating conventions that avert outsiders or the general population from reading private messages; different perspectives in data security, for example, information classification, information honesty, confirmation, and non-renouncement are key to present-day cryptography. Present-day cryptography exists at the crossing point of the controls of arithmetic, software engineering, electrical designing, correspondence science, and material science. Utilizations of Cryptography Assignment Help incorporate electronic trade, chip-based installment cards, computerized monetary standards, PC passwords, and military correspondences.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes