#Cryptography Homework Help
Explore tagged Tumblr posts
Text
A Primer for Beginners in Cryptocurrency
Cryptocurrency has taken the financial world by storm, a phenomenon held in equal parts awe and scepticism. What is cryptocurrency, and why should beginners care? This guide will answer all these questions and provide a true definition of cryptocurrency, for the uninitiated.
What is Cryptocurrency?

At its most basic, cryptocurrency is any type of digital or virtual currency that uses cryptography for security. Cryptocurrencies — which are not issued by a central government (like the US dollar or Euro), operate on networks known as blockchains. This decentralization means that it is not owned by a single entity, like the central bank of each country.
How Does Cryptocurrency Work?
Decentralization, Transparency and Immutability are the killer features of blockchain technology which is being utilized by cryptocurrencies. A blockchain is a distributed ledger that keeps track of all transactions across a network of computers. When a block of transactions is added to the blockchain, it means that every new transaction in completion (e.g., money moving from one account to another) makes an update on all ledgers for their users.
The opaque and unreliable centralized system is avoided, allowing the data to be secure (distributed AND only YOU hold access), prompt & transparent. Bitcoin, the first and most famous cryptocurrency is a case in point: Bitcoin uses blockchain technology to enable peer-to-peer transactions without an intermediary (like a bank).
Popular Cryptocurrencies

Bitcoin, is the best-known cryptocurrency and there are thousands of other cryptocurrencies with various uses and functionality. Here are a few notable ones:
Ethereum (ETH): Ethereum is a decentralized platform that runs smart contracts (like dApps) on its platform.
Ripple (XRP): While Ripple is designed as a digital payment protocol, it still serves the same use case of enabling instant and cheap across borders.
Litecoin (LTC): Often dubbed as silver to Bitcoin's gold, Litecoin has faster transaction confirmation times.
Why Invest in Cryptocurrency?
There are few reasons for which a realization of benefits can seem attractive in investing this digital currency.
High upside: Cryptocurrencies can also gain value by huge percentages. For example, the early investors of Bitcoin and Ethereum are currently smiling to their bank-account.
2. Diversification: Cryptocurrencies can be added to an investment portfolio in order to diversify it thereby decreasing the risk.
3. Innovation and Technology: Investing in cryptocurrencies is an investment into the underlying blockchain technology, a revolutionary tool with many uses beyond digital currencies.
Risks and Considerations

But of course, as with all investment opportunities there are risks when it comes to digital currencies:
Volatility: Cryptocurrency is known for its price volatility; prices fluctuate rapidly and dramatically.
Regulatory Risks: The regulatory backdrop for cryptocurrencies is definitely a work in progress and future regulations may affect the value of these digital currencies as well as how they can be used.
Security Risks: The blockchain is secure, the platform and exchange on which cryptocurrencies are stored can be hacked.
How to Start with Cryptocurrency
There are some guidelines to help beginners who want to start investing in cryptocurrency.
Do your homework — It is important to be familiar with what you are investing; important to know what you're putting your money into, services like Coursera and NerdWallet provide thorough lessons on cryptocurrency.
Pick a Secure Exchange: Go for the most secure cryptocurrency exchange to purchase and offer cryptos Common exchanges such as Coinbase, Binance and Kraken.
Protect your investments: Store cryptocurrencies in secure wallets. Online wallets are less secure whereas hardware wallets provide advanced security to store.NEO.
4. Start Small — With all the volatility in this market, it would also be prudent to instead make a small investment and then scale into your position from there as you get more comfortable with these markets.
Conclusion

Cryptocurrency is a titanic heavy weight knocking the financial industry off its axis; it opens new doors for wealth and disaster as well. These are the basics of cryptocurrency that beginners need to understand and with a responsible, well-informed entering into it can lead them being successful. successful investment. Besides, due-diligence and strategic thinking at every stage are defining factors for anyone who wants to dive into the roller-coaster world of crypto-investing.
6 notes
·
View notes
Text
Investigating the Interplay Between Math and Computation
Mathematics and computing have been companions for a long time, impacting disciplines ranging from engineering and artificial intelligence to finance and scientific research. An understanding of how maths and computing overlap can go a long way in fostering problem-solving capacity, analytical powers, and scholastic excellence. From unraveling complex equations to constructing algorithms to discovering data science, the interaction between maths and computation is inevitable. Students in need of math assignment help typically find that maintaining a background in both fields results in improved efficiency and precision in their assignments.
This piece discusses the close relationship between computation and mathematics, providing students with useful tips on how to better understand and excel in both disciplines. With the assistance of computational thinking, mathematical modeling, and applications, this guide provides the information necessary to excel in both fields.

The Relationship Between Mathematics and Computation
Mathematics is the foundation of computation, and computation facilitates mathematical discovery and problem-solving. Computation refers to the process of carrying out calculations, which can be done manually, with a calculator, or using sophisticated programming methods. Computational software such as Python, and Wolfram Alpha has transformed the way mathematical problems are solved in modern education. Assignment helpers often recommend the use of these tools to enhance problem-solving efficiency and accuracy in mathematical tasks.
Areas Where Mathematics and Computation Intersect
Algebra and Algorithm Design – Algebraic algorithms are the most common, ranging from solving linear equations to function optimization.
Calculus in Computational Simulations – Differential equations have a wide range of applications in physics, engineering, and computer graphics and are often solved numerically.
Statistics and Data Science – Statistical analysis is highly dependent on computational methods for handling large datasets, identifying patterns, and making predictions.
Cryptography and Number Theory – Techniques of cryptography in cybersecurity are based on number theory and computational methods.
Machine Learning and Artificial Intelligence – Both are based on mathematical principles such as matrices, probability, and optimization, with the help of computational models.
Knowledge of such connections enables students to apply both fields to achieve maximum efficiency and problem-solving potential in mathematical applications.
Computational Thinking in Mathematics
Computational thinking is a problem-solving process that includes breaking down complicated problems, recognizing patterns, and step-by-step building of solutions. It is one of the major aspects of mathematics, especially when solving abstract problems or a high volume of calculations.
Basic Principles of Computational Thinking
Decomposition – Reducing a complicated problem into small, manageable pieces.
Pattern Recognition – Identifying recurring patterns in mathematical problems.
Abstraction – Choosing key details and ignoring irrelevant information.
Algorithmic Thinking – Developing logical step-by-step procedures for solving problems.
Students of mathematics who use computational thinking in assignments achieve the work comfortably, leading to satisfactory academic performance. Tutors of homework recommend students do this sort of technique practice in a bid to improve problem-solving capacity.
How Computation Helps Mathematical Education
Since the time computer programs were invented, computation has become a tool of inevitable requirement in mathematical study. From programming and simulation to math packages, computational techniques offer students an interactive platform to understand theoretical concepts.
Advantages of Computational Packages in Mathematics
Visual Representation of Problems – Graph utilities allow visual representation of functions, equations, and mappings in geometry. Automation of Tedious Calculations – Computer calculations aid in saving time spent on tiresome and redundant computations. Prompt Feedback – Immediate feedback allows students to make errors and learn. Real-World Application – Models and simulations base mathematical concepts more.
GeoGebra, Wolfram Alpha, and Python libraries such as NumPy and SymPy allow students to play with mathematical concepts, improving understanding and retention.
Applications of Computation and Mathematics in the Real World
Mathematics and computation not only meet in school but also have an impact on different industries and inventions.
Fields Where Computation and Mathematics Play a Central Role
Engineering – Bridges, airplanes, and circuits are designed using computational models.
Finance and Economics – Stock market predictions, risk calculation, and economic forecasting are all computationally based.
Medicine and Healthcare – Computational biology and data analysis help in medical diagnosis and research.
Artificial Intelligence – Machine learning models employ sophisticated mathematical computation to enhance decision-making.
Cybersecurity and Cryptography – Cryptographic methods provide mathematical solutions to data security.
Gaining an understanding of how mathematics and computation work together allows students to acquire transferable skills that can be used in numerous career options. Assignment helpers and writers typically ask students to do real-life case studies in the expectation of enhancing their competence and improving their performance in studies.s.
Understanding Computation and Mathematics Strategies
To succeed in computation and mathematics, students need to use correct study habits that ensure understanding and application.
Practical Strategies for Success
Learn Programming – Python and MATLAB programming languages make mathematical problem-solving easy. Use Internet Resources – Experiential and visual learning through online websites. Practice Daily – Daily practice of mathematical problems enhances computational skills. Solve Challenging Problems – Problem-solving breaks concepts down into easy-to-grasp bits. Use Maths for Real-Life Scenarios – Practical application of theories to real life enhances understanding.
With the incorporation of such methods, students will learn computational efficiency when solving mathematical problems.
Conclusion: Best Learning with Mathematics and Computation
The interaction between mathematics and computation provides students with an excellent model for solving intricate problems in most fields. From designing algorithms to data science and engineering, the interaction between the two subjects is seen in both learning and actual applications.
By employing computational thinking, using digital resources, and applying math to real life, students develop helpful skills to ensure academic as well as workplace success. Mathematics assignment help seekers can gain significant benefits through their comprehension of how computational devices enable math study.
Under the professional tutelage of Assignment in Need, students are able to expand their understanding, improve grades, and begin enjoying math and computation rather than hating them.
1 note
·
View note
Text
How to Include Crypto in Your Retirement Portfolio 2025
Cryptocurrency is becoming a popular investment option, even for retirement portfolios. If you're considering adding crypto to your retirement plans, here's a detailed guide to help you understand the process and make informed decisions.

Understand the Realities of Cryptocurrency
Cryptocurrency is a digital or virtual currency that uses cryptography for security. Unlike traditional currencies, it operates on a technology called blockchain. Some of the well-known cryptocurrencies are Bitcoin, Ethereum, and Litecoin. However, it's essential to understand that crypto is highly volatile. Prices can swing dramatically within short periods, which can impact your investment's value.
For example, Bitcoin's price soared from around $10,000 in mid-2020 to over $60,000 in early 2021, only to drop below $30,000 later. This volatility can be nerve-wracking but also offers significant growth potential.
Cryptocurrencies are decentralized, meaning they are not controlled by any government or financial institution. This can be a double-edged sword. On one hand, it provides freedom from traditional financial systems, but on the other hand, it means there is less regulation and more potential for fraud and market manipulation.
Make Age-Appropriate Investments
Your age plays a crucial role in determining how much risk you should take with your retirement portfolio. Younger investors, say those in their 20s or 30s, can afford to take more risks because they have more time to recover from potential losses. On the other hand, older investors nearing retirement should be more conservative.
Example: If you're 30 years old, you might allocate 10-15% of your portfolio to cryptocurrencies. But if you're 60, you might want to limit it to 2-5% to avoid jeopardizing your retirement savings.
Younger investors can afford to be more aggressive because they have more time to ride out the highs and lows of the market. If you’re younger, investing a higher percentage in crypto can pay off in the long run due to its growth potential. However, as you approach retirement age, preserving your capital becomes more important. This means you should reduce your exposure to high-risk investments like crypto.
Do Your Homework
Before investing in cryptocurrencies, do thorough research. Understand the technology behind each cryptocurrency, the team running it, and its potential use cases. Look at the historical performance but also understand that past performance does not guarantee future results.
Example: Research projects like Ethereum, which provides a platform for decentralized applications, or Cardano, which focuses on security and scalability. Reading whitepapers, joining community discussions, and following reputable news sources can provide valuable insights.
When researching, pay attention to the problem each cryptocurrency aims to solve and how it plans to do so. This can give you an idea of its long-term potential. For instance, Ethereum's smart contract functionality allows developers to build decentralized applications (DApps) on its blockchain, which has numerous use cases and can drive demand for Ethereum.
Also, be aware of market sentiment and news. Regulatory news, technological advancements, and partnerships can all impact a cryptocurrency’s price. Being informed helps you make better investment decisions and avoid scams or poor-quality projects.
Minimize Risk with Funds
To minimize risks, consider investing in cryptocurrency funds rather than individual coins. These funds, like the Grayscale Bitcoin Trust (GBTC) or Bitwise 10 Crypto Index Fund, spread investments across various cryptocurrencies, reducing the impact of a single coin's poor performance on your overall portfolio.
Example: Investing in a fund means your money is diversified across different cryptos, so if Bitcoin drops in value, gains in Ethereum or other assets could balance it out.
Crypto funds are managed by professionals who have expertise in the field, which can be beneficial if you are not confident in making individual investment decisions. These funds also provide exposure to multiple cryptocurrencies, offering a more balanced approach to investing in the volatile crypto market.
Allocate Cryptocurrency in Your Retirement Portfolio
When allocating cryptocurrency in your retirement portfolio, it's essential to find the right balance. A common strategy is to follow the 5% rule—keeping no more than 5% of your portfolio in high-risk investments like cryptocurrencies. This approach ensures that while you benefit from potential high returns, you also protect your retirement savings from excessive risk.
Example: If your retirement portfolio is worth $200,000, consider investing around $10,000 in cryptocurrencies and the rest in more stable assets like stocks, bonds, or mutual funds.
Another strategy is to use the core-satellite approach, where the core of your portfolio consists of traditional investments like stocks and bonds, and the satellite portion includes higher-risk assets like cryptocurrencies. This method allows you to take advantage of the growth potential of cryptocurrencies while keeping the bulk of your portfolio in more stable investments.
Understand These Facts if You're New to Cryptocurrency
If you're new to cryptocurrency, here are some crucial facts:
Security is paramount: Always use secure wallets and platforms to store and trade your crypto.
Be aware of taxes: Cryptocurrency investments are subject to capital gains taxes.
Stay informed: The crypto market is dynamic. Regularly update yourself with news and trends.
Example: Use hardware wallets for storing large amounts of crypto to protect against hacks and ensure you report your crypto earnings accurately during tax season.
Security is crucial because cryptocurrencies are a prime target for hackers. Using hardware wallets, which are physical devices that store your crypto offline, can provide a higher level of security compared to online wallets. Always use reputable exchanges and enable two-factor authentication for added security.
Understanding the tax implications is also important. In the U.S., cryptocurrencies are treated as property for tax purposes, meaning you need to report any gains or losses on your tax return. Keeping detailed records of your transactions can help ensure you comply with tax laws.
Keep an Open Mind
The world of cryptocurrency is constantly evolving. New technologies, regulations, and market trends can change the landscape quickly. Keeping an open mind and being adaptable will help you make better investment decisions.
Example: When Ethereum 2.0 launched, it introduced a shift from proof-of-work to proof-of-stake, changing how the network operates and potentially affecting its investment appeal. Being open to such changes allows you to capitalize on new opportunities.
Staying flexible and open to new developments is crucial in the fast-paced world of crypto. For instance, decentralized finance (DeFi) platforms have emerged, offering financial services like lending and borrowing without traditional banks. These innovations can provide new investment opportunities and ways to earn returns on your crypto holdings.
Consult a Professional
Given the complexities and risks involved in investing in cryptocurrencies, consulting with a financial advisor can be very beneficial. David Kassir, a top crypto financial advisor in the USA, offers specialized services to help you navigate the crypto investment landscape.
For more information, visit Cryptocurrency Advisory Services.

Including cryptocurrency in your retirement portfolio can offer significant growth potential but comes with substantial risks. By understanding the realities of crypto, making age-appropriate investments, doing your homework, minimizing risk, and keeping an open mind, you can better navigate this exciting investment frontier.
0 notes
Text
Why choose the services of 24×7 assignment help?
In the above fundamental securities, the algorithms to be learned for making a digital data secure is not an easy task for a student. The homework and assignment may make them feel confused with algorithms and other cryptography aspects. Where our https://www.allhomeworkassignments.com/ cryptography assignment assistance will surely be helpful to you. There are symmetric and asymmetric algorithms and also encryption and decryption which are the basis of the cryptography. They need to give special attention towards this topic of programming as a single wrong code can affect the security algorithms. Taking online help from https://www.allhomeworkassignments.com/ is always useful.
Why choose the services of 24×7 assignment help?
When you are in search of an online expert to ask them to do my cryptography homework and assignment then https://www.programmingonlinehelp.com/ are one among the other online companies by providing efficient services that too at affordable cost. Let us see what our strengths are and how we are good for solving your assignments?
•You get content which will be only yours that is unique and plagiarism free. How to solve cryptography assignments? Is not a big question for our https://www.programmingonlinehelp.com/ experts. They have complete knowledge to give the needed help with all types of question, You get the help from the experts that are dedicated to their work and always give you timely delivery. You can ask for do my nursing cryptography at any time as we provide a service which is available 24/7 for you. You may be around anywhere in the world you just need to go online and hire https://www.programmingonlinehelp.com/ experts through simple steps and also make the payments with secure methods. You be assured with our work that it will be without errors and it will make a huge difference in your grades at all time.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text
lads, one of the frustrating things about accidentally following in your muse’s footsteps and enrolling in wizard school (STEM masters program) is you actually have to do the homework when you’d rather be writing the muse, because the homework is what will help you write the muse better
at least this chapter is cryptography, which i find more immediately applicable and might actually absorb, fingers crossed
anyway utter an incantation in my honor, pls & thank
9 notes
·
View notes
Text
Cloud Computing Project Help
Cloud Computing Assignment Help.
Cloud computing is one of the flourishing fields of computer science. A lot of students choose this line of study due to the promising career aspect. However, they also face difficulty to complete a Cloud computing homework as they lack the in-depth understanding of the technical concepts. Hiring a subject expert to assist you with your Cloud computing assignment and help you learn the complex ideas would be a wise option
https://www.bestassignmentsupport.com/programming-assignment-help/cloud-computing-assignment-help.php is a renowned name in the industry for delivering exceptional quality academic aid to students. Our professionals can give you the much-needed Cloud computing assignment help to draft A+ quality paper.
Seeking Cloud computing assignment help service from us can get you the top-quality academic support as well as professional referencing and proofreading assistance. Contact us for further query.
Impeccable Cloud Computing Assignment Writing Help On Varied Topics
Our Cloud computing homework helpers have the perfect combination of academics and professionalism to provide extraordinary assistance for excelling in the subject. Each of them possesses extensive knowledge in Cloud Computing to provide assignment writing help in any complicated topic, including:
· CloudSecurity and Trust management
· Cloud cryptography
· Fundamentals of Cloud Computing
· Cloud Architectures
· Cloud Delivery Models
· Cloud Risk Management
· Planning a Migration to the Cloud
· Managing the Cloud Infrastructure
· Public Clouds and Service Offerings
· Cloud Capabilities and Platform Features
· Quality of Service in Cloud computing
· Google's NoSQL system
· Emerging Cloud Software Environments
· Cloud engineering
Don’t panic if you can’t find your assignment topic on the list or if you are in a dilemma about our Cloud computing assignment writing quality. Hit the button below to check some of the recent work samples of our experts and get in touch with us to know more.
#CloudComputingAssignmentHelpers#CloudComputingAssignmentHelp#CloudComputingHomeworkHelp#CloudComputingProjectHelp#CloudComputing#bestassignmentsupport.com
1 note
·
View note
Text

7-10/100
It’s been a little challenging to keep up with posting lately. I decided to go home this weekend to help my parents around the house, especially since my dad recently got a hernia. Until he gets back on his feet, I wanted to give them as much as my time as possible. I pinky promise I’ve been productive. To compensate, I’ll disclose a few productive tidbits of my missed days:
7/100:
Listened and took notes from a bioinorganic lecture
Had my first day of the semester for being an intro biology lab teaching assistant (but I also worked last semester)
Did an assignment for my Modern World class
8/100:
Listened and took notes from a Codes and Cryptography lecture
Began Codes and Cryptography homework
Took notes for my upcoming Modern World class (pictured above)
9/100:
Helped my mom by doing some grocery shopping
Helped cook dinner for my parents
10/100:
Found a really neat recipe for vegan/gluten-free mug cakes
Did laundry
Helped cook dinner with my parents
I’m looking forward to returning back to campus tomorrow and getting more school work done with my day off. Also munching on the vegan/gluten-free cookies my mom made for me to bring back.
10 notes
·
View notes
Text
Cryptography 101: How a Symmetric Key Exchange Works (Basically)
Syndicated from Medium
Webster’s dictionary defines cryptography as… I’m just kidding. This blog post is about cryptography, though just an intro.
Just to start somewhere, let’s go over the Diffie-Hellman Public Key encryption method, which uses a symmetric key algorithm. That means that the same cipher is used to encrypt and decrypt a message. In the feature film National Treasure, the cipher on the back of the United States constitution is an example of a symmetric key.*
A lot of digital cryptography is based on what is known as a trapdoor function. The function is difficult to reverse engineer when given just the result of said function. For the purposes of illustration we are just going to use a “door function” (not a real thing). I’m making up that terminology for the purposes of this example. We will pretend that our function is difficult to reverse engineer (but you will see that it is not).
Example trapdoor function (a real thing):
You know there are two numbers that when multiplied, result in 17,078,781,140,149. Without the hint that one of those numbers is 1,766,021, it would be time consuming, if not fairly difficult to determine which two numbers were multiplied to result in 17,078,781,140,149. That ‘hint’ is the trapdoor. (The other number was 9,670,769. With the trapdoor you can divide 17,078,781,140,149 by 1,766,021 and figure that out for yourself).
Example door function (again, not a real thing):
You know there are two numbers that when multiplied, result in 15. No hint is required to determine that the two numbers were 3 and 5. Technically this is still a trapdoor function, we are just calling it a “door function” because it is easy to reverse engineer just by looking at it. Just to repeat, I made up “door function”. I thought it was vaguely humorous and I appreciate whimsy.
I manage to wrap my head around Public Key cryptography like this: multiply a Public Key and a Secret Key to get a common cipher, aka a Shared Secret. Your Public Key and Secret Key are both different than the other person’s Public and Secret Key, but both sets of keys, when multiplied, result in the same shared secret. This is way simplified and the actual math involves Totients and a Modulus but this is Cryptography 101, The Intro Lesson.
Let’s get a cast of characters together to illustrate an example. Meet Ajay, Beyonce, and Christina. Each person’s Public Key is generated by multiplying their Secret Key by 5. Again, in real life, the math in that calculation is sliiiiightly more complicated, but suspend your disbelief with me for then next few paragraphs. It might go without saying but everyone’s Public Key is known by everyone else. It’s public.
Behold, a handy chart to keep it all straight:

Now for the fun part. Ajay writes a message “Hi Beyonce, have you seen the movie Speed?” This message is for Beyonce’s eyes only, so Ajay multiplies his Secret Key by Beyonce’s Public Key and uses the result to encrypt it.
Multiplying those keys results in 75. This is the shared secret between Ajay and Beyonce. For demonstration purposes, our encryption method is to interleave the shared secret between every character of the message, and decryption is removal of all instances of the shared secret. It is quite elementary, but just pretend that on the internet, this makes it impossible to read.
When we apply this totally believable encryption method to the message, this gives:
“H75i75 75B75e75y75o75n75c75e75,75 75h75a75v75e75 75y75o75u75 75s75e75e75n75 75t75h75e75 75m75o75v75i75e75 75S75p75e75e75d75?”
Look at how difficult it is to read now, Internet!
Ajay sends that encrypted message and no one can read it (are you still pretending?!), because they don’t know the shared secret (75). Even if some unnamed nefarious character had Beyonce’s and Ajay’s Public Keys, 25 and 15, neither of these numbers alone help to decrypt the message.
Beyonce receives the message, but due to a Shakespearean misunderstanding, she thinks the message is from Christina. So she uses Christina’s Public Key, 10, with her Secret Key, 5, to decrypt the message. She computes 10 * 5 and gets 50. But when she uses this shared secret and removes all the 50s from the message, it remains encrypted.
Further confusion continues, and now Christina thinks Ajay sent the message to her. Christina uses her Secret Key, 2, and Ajay’s Public Key, 15, to get a shared secret of 30. This too, fails to decrypt the message.
After a bit of hilarity and hijinx, the misunderstanding is resolved. Beyonce knows the message is from Ajay and is intended only for her. She multiplies her Secret Key, 5, and Ajay’s Public Key, 15, to get, wait for it… 75. Their shared secret. Removing all 75s from the message gives:
“Hi Beyonce, have you seen the movie Speed?”
Boom.
Because only Ajay & Beyonce’s shared secret worked to decrypt the message, Beyonce knows for sure that the message was intended for her and that it was sent by Ajay. Ajay “digitally signed” the message because he used his Secret Key.
Needless to say, but I’m saying it anyway, we used easy numbers, easy algorithms (multiplication), and an insanely simplistic “encryption” method. But this is the essence of the Diffie-Hellman Public Key encryption method, symmetric key cipher. Wikipedia has the real math if you are interested.
There are other encryption methods and even other Public Key exchange encryption methods. Search the web for PGP and RSA if you want to venture out of the kiddie pool.
That concludes today’s lesson. Below is optional homework. Be sure to keep an eye out for Cryptography 101, Lesson Two: Asymmetric key algorithms or How to explain coprime numbers succinctly to kindergarteners.
If you would like to play along at home, dear reader, use your browser console to play around with the concept.
The console can be accessed the following ways — Chrome: View > Developer > JavaScript Console Firefox: Tools > Web Developer > Web Console Safari: download Chrome or Firefox Edge: download Chrome or Firefox
And the code…
const ajaysSecretKey = 3 const beyoncesSecretKey = 5 const commonFactor = 5
function createPublicKey(secretKey, commonFactor) {
return secretKey * commonFactor }
function signPublicSecretKey(publicKey, SecretKey) { let commonCypher = publicKey * SecretKey return commonCypher
}
function encryptMsg(message, commonCypher) { let encrypted = Array.from(message).join(commonCypher) console.log(message) console.log(`when encrypted becomes:`) console.log(encrypted) console.log(``) return encrypted }
function decryptMsg(message, commonCypher) { let re = new RegExp(commonCypher,`g`) let decrypted = message.replace(re, ``) console.log(message) console.log(`when decrypted becomes:`) console.log(decrypted) console.log(``) return decrypted }
const ajaysPublicKey = createPublicKey(ajaysSecretKey, commonFactor)
const beyoncesPublicKey = createPublicKey(beyoncesSecretKey, commonFactor)
const sharedSecret = signPublicSecretKey(ajaysPublicKey, beyoncesSecretKey)
console.log(``)
let ajaysMsg = `hi Beyonce, have you seen the movie speed?`
let ajaysEncryptedMsg = encryptMsg(ajaysMsg, sharedSecret) let ajaysDecryptedMsg = decryptMsg(ajaysEncryptedMsg, sharedSecret)
*I have not seen National Treasure so that cipher analogy may not be applicable. I just wanted to soften the topic with a pop culture reference. Did it work?
2 notes
·
View notes
Text
Cryptographic Methods Used By Cryptography Assignment Help Professionals
Cryptography Assignment Help going before the forefront age was feasibly synonymous with encryption, the change of information from an understandable state to obvious hot air. The originator of an encoded message shared the unraveling technique anticipated that would recover the main information just with proposed recipients, thusly blocking unfortunate individuals from doing moreover. The cryptography writing Help regularly utilizes the name Alice ("A") for the sender, Bob ("B") for the planned beneficiary, and Eve for the foe. Since the improvement of rotor figure machines in World War I and the approach of PCs in World War II, the strategies used to complete cryptology has turned out to be progressively perplexing and its application more boundless. Prior cryptography was viably synonymous with encryption, however, these days Cryptography Assignment Help is chiefly in light of numerical hypothesis and software engineering practice.
Cryptographic Methods Used By Cryptography Assignment Help Professionals
Symmetric-key Cryptography: Both the sender and the collector share a solitary key in Cryptography Assignment Help . The sender utilizes this key to encrypt the plaintext and send the figure content to the recipient. On the opposite side, the beneficiary applies a similar key to decode the message and recuperate the plain content.
Open Key Cryptography: This is the most progressive idea in the last 300-400 years. In Public-Key Cryptography two related keys are utilized. The open key might be unreservedly appropriated, while its combined private key, remains a mystery. The general population key is utilized for encryption and for decoding private key is utilized. https://www.programmingonlinehelp.com/ have the best cryptography assignment writing services
Hash Functions: No key is utilized as a part of this calculation in Cryptography Assignment Help . A settled length hash esteem is processed according to the plain content that makes it unthinkable for the substance of the plain content to be recuperated. Hash capacities are likewise utilized by numerous working frameworks to encrypt passwords.
symmetric-key cryptography
Symmetric-Key Cryptography alludes to encryption strategies in which both the sender and recipient share a similar key. This was the main sort of encryption openly known until June 1976. Symmetric key figures are executed as either piece figures or stream figures. A piece figure enciphers contribution to squares of plaintext instead of individual characters, the information shape utilized by a stream figure. The Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) are square figure plans that have been assigned cryptography benchmarks by the US government. In spite of its expostulation as an official standard, DES remains very prevalent; it is utilized over an extensive variety of uses, from ATM encryption to email protection and secure remote access.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text
Information Systems Homework Help
Information Systems Homework Help
Information Systems Homework Help Lecture slides prepared for “Cryptography and Network Security”, 8/e, by William Stallings, Chapter 8 – “Random Bit Generation and Stream Ciphers”. An important cryptographic function is the generation of random bit streams. Random bits streams are used in a wide variety of contexts, including key generation and encryption. In essence, there are two fundamentally…
View On WordPress
0 notes
Text
Information Systems homework help
Information Systems homework help
Provide a reflection of at least 500 words (or 2 pages double spaced) of how the knowledge, skills, or theories of these courses Cryptography and Legal Regulations-Compliance Investigation have been applied, or could be applied, in a practical manner to your current work environment. If you are not currently working, share times when you have or could observe these theories and knowledge could…
View On WordPress
0 notes
Text
Solve Your Geometry like A Pro with the Geometry Solution Manuals
Are the different lines, circles, and angles getting on your nerves? Have you been trying to solve them but still to no avail? There are these geometry textbook solution manuals that will help you solve every other sum with ease.
The geometry solution manuals will help the students understand and learn better. With the help of solution manuals, the students clarify all their doubts and improve their results.
A brief introduction on geometry and its branches
Geometry is one of the oldest branches of mathematics. It deals with the angles, sizes, shapes, and dimensions of the properties of space we see in our daily life.
Some of the important concepts in geometry include axioms, points, lines, planes, angles, curves, surfaces, manifolds, length, area, volume, symmetry, dimensions, etc.
Geometry is divided into some major branches which include algebraic geometry, discrete geometry, differential geometry, Euclidean geometry, convex geometry, and topology.
Algebraic Geometry
It is the branch of geometry that deals with the zeros of the multivariate polynomials. The application of algebraic theory comprises cryptography, string theory, etc.
Discrete Geometry
It deals with the relative position of a simple geometric object. The application of this comprises using lines, triangles, points, circles, etc.
Differential Geometry
This type of geometry uses techniques of algebra and calculus for solving problems. The problems include general relativity in physics and the process of analysis of data on nonflat surfaces.
Euclidean Geometry
This type of geometry deals with the study of plane and solid figures based on axioms and theorems including points, lines, angles, planes, solid figures, etc.
Convex Geometry
This type of geometry uses the techniques of real analysis. It has uses in the application in optimization and functional analysis in number theory.
Topology
It deals with the properties of space under continuous mapping. It deals with metric spaces, proximal continuity, proximal spaces, initial and final structures, hyperspace topologies, separation axioms, etc.
Career Options
Students with a degree in geometry have a wide rand of career options. They can become architects, cartographers, drafters, mechanical engineers, surveyors, urban and regional planners, etc.
The Utility of Solution Manuals
With a good result and a great personality and character, any candidate will be hired by a good company. While the improvement of a person's personality and character depends on oneself; a student can improve their grades by taking help from solution manuals.
A solution manual is useful to students in many different ways.
A solution manual helps working students manage their studies and work. With the solution manuals, a student can get enough to self-study and revise before their exams. Students, who could barely manage time for themselves, now have ample time to learn.
Students who have anxiety issues and face trouble communicating with their teachers in class can take benefit from the solution manuals. The solution manuals will help the students instantly and they do not have to stammer in the classroom anymore.
Students who feel pressured with the subject can now relax at ease. Because the solution manuals are here to guide them!
Are all solution manuals trustworthy?
With the rising popularity of solution manuals, every other company sells them. But half of them are either plagiarised or inaccurate.
If students want to purchase solution manuals online, they need to be careful. The student must also realize that solution manual work is the best guide. A guide is meant to pave the way when you are lost.
The solution manuals must not be used as mere copy and paste materials. Students should use solution manuals only when they have doubts or are unable to solve the questions.
Where do we get the best solution manuals?
Crazy for Study is an online academic platform that helps students with instant homework and assignments. It also provides the best solution manuals to students.
It has solution manuals for every kind of subject; be it engineering, mathematics, or social science. Starting from the major to the minor subjects, it has solution manuals for all. There are many advantages of using solution manuals from Crazy for Study.
Step-by-Step Guidance
The solution manuals provide a detailed step-by-step guide to the course oriented textbook questions. It helps the students get a better grasp of the different concepts.
Plagiarism-free
The solution manuals provide 100% authentic and lucid content. The writers are subject matter experts who make sure that they write original content and not copy from other sources. The subject matter experts have adequate knowledge in their respective fields of education.
Error-free
The editing team checks every sentence meticulously to avoid spelling and grammatical mistakes. They ensure that the content is accurate and up to date before publishing.
Practice Questions and Reference materials
The solution manuals provide additional materials. The practice questions help the students understand better, and the reference materials help them analyze the different concepts and ideas. The solution manuals also have various quizzes to help them with better learning.
Wide range of materials
Crazy for Study has access to more than fifty million textbook solutions. Each subject has a wide range of solution manuals from which the students can choose accordingly. It also includes almost all the essential topics of a particular subject. The students will not regret buying solution manuals from them.
Q/A forum
The website also has a Q/A forum that helps students inquire about their doubts and queries. If the students subscribe, they can ask fifty new questions to the experts' team and the pre-existing ones.
Get the best solution manuals of geometry at affordable prices and enjoy the digitalized content from any corner of the world. Learn better and be a genius among your friends with the solution manuals of geometry.
0 notes
Text
5 Things Meme
I was tagged by @nyhne. Thanks! I tag @a-study-in-shakespeare 5 Things in My Bag • a shit-ton of pens -- if I don't have at least with me at all times, then what's the point? • a shit-ton of gum wrappers -- I will literally stick my gum wrappers in my bag despite there being a trash can three feet away. It's just one of my...things. • various forms of ID -- school, work, driver's license • my handy dandy multi-tool -- bigger and better than a Swiss Army knife and waaaaay more useful. When I switch out bags, I feel naked if I forget my multi-tool • a calculator -- again, something I always feel like I need even tho my phone has a calculator on it?? 5 Things in My Room • Christmas lights • An ancient keyboard that belonged to my aunt-in-law that pretty much helped launch her music production career. But the amp and some of the controls are shot and I still can't decide what to do with it. I'd rather practice on the piano downstairs and we'd have to get some adapters and software and stuff to make this thing compatible with out laptops if we were to start recording our own music because this keyboard is from the 70s. • An original lithograph print I bought at an art show one year at school • A dwindling stack of to-be-read books that are actually being read! • My copy of The Death of Ivan Iliich that I bought from an antique book dealer when I visited Savannah, Georgia. It was the only thing in that shop I could afford -- and it lists the author as Count Lyof Tolstoi, which I thought was pretty cool. It also includes two other short stories by unknown authors and advertisements for other books and publishers in the back. I think it was published in the 1890s? 5 Things I Want to Do in My Life • attend a Hack-a-thon • get a cover-up tattoo for the one on my ankle. I was 19 when I got it, and I liked it at the time. But now, not so much. • travel across Europe with my two best friends • pass my certification test(s) • visit Asia 5 Things I'm Currently Into • ethical hacking • cryptography • learning French and Russian • I've been getting back into exercising and try to do a few exercises in the evening. I can't wait for the weather to start cooling off and the humidity to go away so I can start taking walks/jogging in the morning. • sewing my own skirts. I've made four so far, and I've found some cool patterns for shirts I haven't tried yet. 5 Things in My To-Do List • write • finish homework • update my résumé • make posters for an upcoming movie night my math club is sponsoring • maybe get a haircut?? I'm still undecided....
4 notes
·
View notes
Text
Skills
Bookmarks for quick access to other sections:
Job Application Home
Analytical Skills
Time Management
Community & Professionalism
Something Awesome
Technical ability Criteria - If you know how to program, did you write any tools/scripts/programs to help you achieve anything in this course?
1. PowerShell CertUtil command and Keylength scripts (reference)
2. Something Awesome Project Web Crawler
Python programming (reference)
Understanding and knowledge of HTML and different tag types (reference - see web crawler) (reference 2)
Relational Databases/Relational Schema and SQL (reference 1) (reference 2) (reference 3 - See all source code and the basic “emailAnalysis.py”)
3. Something Awesome Security Upskilling
Understanding of some common network packets (reference 1) (reference 2)
Information Gathering (reference)
Scanning and Network Discovery (reference 1) (reference 2) (reference 3)
Password Cracking (reference 1)
Research Skills Criteria - Did you spend time researching "The history of...", how to defeat security measures, or something else?
One of the issues discovered in Week 5 of my something awesome project was how to get more websites to not block my GET request. As such, I had to research a way to trick websites into thinking my traffic was a standard user (using a web browser). To get around this I found these websites (Python Documentation; Stack Overflow).
To learn a bit more about C and reverse engineering, I also conducted some research to get me up to speed (as I am completing this course as a general education course, I am from the school of Information Systems). [blog 1] [blog 2]
Also, earlier in the term we were giving some “human weaknesses of the week” and research tasks for homework. I completed some of these additional tasks. [blog 1] [blog 2]
Lastly, I also researched Kasiski’s method (after it appeared in a lecture Kahoot). A question on this ended up coming up in the mid-term exam and I ended up narrowing the answer down to 3 or 6, I ended up guessing “3″... The answer was 6 but I am still happy that I applied my knowledge and got close. I did not write a blog post on this, but these are the resources I used (reference 1) (reference 2)
Practical Skills Criteria - Did you improve any practical skills like lockpicking, cracking combination locks, communicating security concepts to non-security people, etc?
1. Learning a new skill!
Deciding to learn (reference 1)
Starting out (reference 2)
More practise and results! (reference 3)
2. NSA Cryptography - I practised these sort of problems for many hours and got this question correct in the mid-sem exam.
3. Cybrary Labs and Kali VM - I have also practised some of the skills I have learnt from my something awesome upskilling project and completed some Cybrary.it labs.
Blog 1
Blog 2
0 notes
Text
Lectures & Tutorial 07
Richard gave a lot of homework this week...
Homework:
Tutorial Case Study: Privacy and Biometrics Previously I was not highly concerned with the collection of my personal data by Google, Facebook, Apple, etc; and the main reason behind this is for the convenience. Google maps suggests automatically the places I frequently travel to, like work, home and uni. I use Face ID on my phone to make payments and login to my accounts. I enjoy this ease of use. After the tutorial I reflected upon how much data I am giving away and how that data could be exploited for objectives that do not align with my intentions. For example, Apple aggregating my expense information to better market products to me: I have no choice over this...
Top ten web security risks
Injection
Broken Authentication and Session Management
Cross-Site Scripting (XSS)
Insecure Direct Object References
Security Misconfiguration
Sensitive Data Exposure
Missing Function Level Access Control
Cross-Site Request Forgery (CSRF)
Using Components with Known Vulnerabilities
Unvalidated Redirects and Forwards
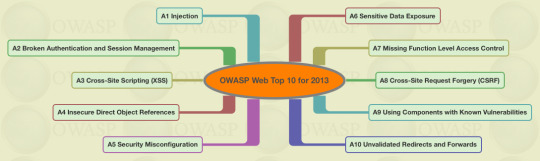
Link.
NIST NATIONAL VULNERABILITY DATABASE This is actually great as I have just started to investigate the possibilities of XSS and SQLI. This vulnerability database lists many current and fresh issues that give some insight into what approaches should be taking when testing web apps. Link.
Read up about the NSW LPI and think about what assets they have and what risks arise from them having been privatised The NSW LPI was the division responsible for land titles, property information, valuation, surveying, and mapping and spatial information in the Australian state of New South Wales. Privatising these assets releases their control and jurisdiction of these assets to financially driven entities. This means that the enforcement on assets that hold cultural value and significance such as historical buildings and park-lands might be re-zoned to align with the economy’s interests. There exists a higher risk to lose the assets with non-financial value. Link. Work out the current state of bio-metrics as an authentication strategy Bio-metrics are regarded as the best (single) means of user authentication to the casual intruder. They also prevent against password stealing ware (PSW) which grabs auto-fill data and saved payment card details. Most tech companies such as Apple and Google who provide bio metric authentication are pushing for this to be a common method of authentication for websites and apps. This would be another measure towards improving user authentication. Link.
Read about Transport for NSW idea of using facial recognition rather than opal cards This is a controversial topic. For Opal to use face recognition to authenticate and identify it’s passengers, means that it would have to store mass amounts of customer data - both images and video - which creates a very high value target for hackers. This data is also connected with location and time tracking. The guardian, linked below, discusses the privacy risks this would pose, HOWEVER, the public concern is more focused on the fact of whether or not it is technologically feasible, not on the fact it would pose major privacy risks. Link.
Read about the San Francisco ban on bio-metrics San Francisco has banned the use of bio-metrics by police. This is because of the fear that the technology will be overused and move the United States in the direction of an overly oppressive surveillance state. There was a recent push for the use of these bio-metric systems following this mass shooting, however, there was a widespread public backlash as many showed strong discomfort with the idea. In this case, the American people seem to value their personal privacy over the additional security of widespread bio-metric identification. Link.
Read about the uni research allegedly helping Chinese security forces use to track and detain Muslim Uyghur citizens in Xinjiang Apparently in 2017 UTS signed a lucrative deal with CETC (Chinese state-owned military tech company) that developed software for Chinese security forces to use to track and identify citizens; however recently this same technology was used to track and detain Muslim Uyghur citizens in Xinjiang. I don’t what UTS was expecting when they assisted in the development of this, it seems quite intuitive that this could and will eventually be misused by the military for purposes UTS possibly found as a human ethics violation. Link.
China’s goals and recent developments with bio-metrics: China’s goals and implementation:
Identify a person from the 1.3 billion population in just 3 seconds using facial recognition.
Security personnel wearing eye-wear to detect people
Face-reading drones
Wearable microchips in uniforms that help with admin tasks such as authentication and monitoring
AI generated media... (news anchors)
Loudspeakers to yell at children when they got too close to water
Livestock farming and monitoring using AI
Link.
How can you detect Man in the Middle eavesdropping? One method of detecting a MitM attack is by constantly validating if the certificates presented to you by the website is issued by a legitimate CA. The best method of doing this is using a tool to keep track of the changes relating to the certificates you use, so if there is a major change, such as Google updates its private key, you can check manually if this is actually the case.
Web of trust (PgP) and PKI. (how PGP does authentication - web of trust) Public Key Cryptography Infrastructure (PKI) can be implemented in two different ways: first using certificates and certificate authorities, secondly, using trust relationships between regular users. The first implementation is the commonly used method of certification used by websites. The second implementation was first used by OpenPGP. This is implemented by GNU Privacy Guard (GnuPGP) which nearly all linux distributions rely on for package integrity verification. Link.
10 Risks of PKI
Anyone can become a CA with enough work, and then they are by default ‘trusted’
Your private key is ‘steal-able’
You cannot detect a ‘compromised’ CA
Only a single CA is needed to validate a website, PKI doesn’t cross verify
CA verifies certificates but is not an authority over the contents of the certificate
User’s aren’t included in the security design (they could play a role in the validation process)
A CA could actually be a CA + Registration Authority (RA). The RA+CA model is less secure as the link between the two could become compromised
The CA could possibly misidentify the certificate holder (a malicious individual could impersonate the certificate holder)
If/When the technology progresses and updates to a new encryption standard, all the certificates need to be updated or revoked using the Certificate Revocation Lists (CRL)
PKI was implemented as due to a minimal impact solution and even though it is not a perfect system, the industry is run by “business and the prominent voices are those with something to sell.”
Link.
Find examples of (serious) fraudulent certificates being issued For this I researched a company called DigiNotar, a Dutch Certificate Authority. This company ‘detected’ a security breach on September 3rd 2011 which resulted in fraudulent issuing of certificates. 300,000 Irinian Gmail users were the target of the hack and Bruce Schneier says that the attack may have been “either the work of the NSA or exploited by the NSA.” however, this has been disputed with others saying NSA had only detected a foreign intelligence service using the fake certificates. Some are even pointing fingers at the 21 year old Irinian student who claimed to have hacked 4 other certificate authorities. Once 500 fake certificates were identified, DigiNotar became blacklisted. Link.
Learn about the steps in a TLS handshake Here is a summary of the steps published by IBM (steps in [ ] are optional):
Client sends ‘hello’ containing:
random byte string
SSL or TLS version
CipherSuits supported
Data compression methods
Server responds with ‘hello’ containing:
Chosen CipherSuite
Session ID
Another random byte string
Digital certificate
[Client certificate request]
Client verifies certificate
Client sends to server containing:
Random byte string encrypted using server public key
[Client certificate or ‘No digital certificate’]
[Server verifies client certificate]
Client sends server ‘finished’ message encrypted with secret key
Server sends client ‘finished’ message encrypted with secret key
They now exchange messages encrypted with the shared secret key
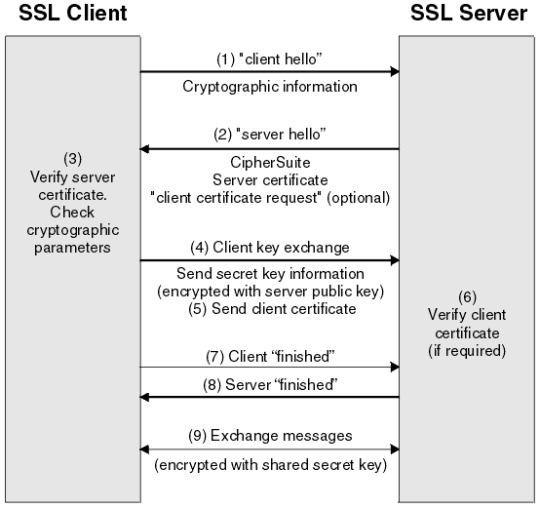
Link.
0 notes
Text
The Best Online Provider of Computer Science Homework Help

Computer Science has become one of the high ranking disciplines and it continues to grow thanks to the great technological advances we have in the 21st century. With almost every company becoming tech-oriented today, the need to for the technical know-how relating to computers and information systems is on the rise.
With all this popularity, Comp science also comes with its share of difficulties which aspiring computer scientists (the students), should be ready to tackle in the course of learning. Being a technical course, some of the units comp science students face require much effort in terms of research and knowledge for one to be comfortable with Cats and assignments. This is never a reality for most students considering the fact that the time allocated to a single semester is very short with so much to do.
The field of computing is becoming highly competitive out there and good grades on your certificate can be a huge boost in ensuring you become more lucrative to employers. Assignments are some of the key factors that can boost your overall GPA and getting expert computer science assignment help is the best way of ensuring you always have the best grades in your assignments.
We at theassignmenthelper.com understand your need for better grades and that is why we are committed to providing professional computer science homework help. We have highly experienced computer science tutors who are dedicated to providing you with quality assignment solutions and tutor guidance. Computer science is quite a vast field that requires extensive knowledge and experience. At the assignment helper, we have confidence in our experts, who have been professors of computer science in leading universities, to handle any assignment you may have. Some of the topics we have covered include:
· Digital Fundamentals and architecture
· Data structures and Procedural Programming
· Mathematical foundations for computer science
· System Software and Operating systems
· Software Engineering
· Relational Database management systems (RDBMS) and Oracle
· Visual Programming (visual basic)
· Software testing
· Information systems security and Cryptography
· Data mining
· Programming lab (C++ and Java)
· Programming languages
Our mission is to create an easily accessible online computer science homework solving platform that is reliable and very efficient in offering top quality solutions. For this reason, we have distinguished our services from most of our competitors by ensuring our clients have access to only the best. Here are some of the reasons why students have trusted us over the years in getting them quality computer science assignment help:
· High-quality assignment solutions that attract lucrative grades
· 100% plagiarism-free solutions
· Round the clock services
· Timely delivery of all assignment solutions
· Total confidentiality of client information
· Greatly affordable prices.
If you are in need of computer science homework help for whatever reason then we are a one stop for all your comp science assignment troubles. Get in touch with us today via email or live chat and we will respond immediately. Let us help you get your assignments done and see your grades skyrocket.
0 notes