#Best Password Recovery Software
Explore tagged Tumblr posts
Text
Astraweb: The Home of Crypto Recovery in the Digital Age

In the ever-evolving world of cryptocurrency, security and access remain critical concerns. For every success story of early adopters turning modest investments into fortunes, there are unfortunate accounts of users losing access to their digital wallets due to forgotten passwords, phishing attacks, or compromised private keys. This is where Astraweb has carved out a vital niche — establishing itself as the go-to solution for crypto asset recovery.
The Need for Crypto Recovery
Cryptocurrency promises decentralized finance and ownership without intermediaries — but this power comes with a cost: total user responsibility. There is no central authority to call when access is lost. Millions of dollars in crypto assets are estimated to be trapped in inaccessible wallets. The stakes are high, and the traditional “write your password down and hope for the best” method has proven tragically inadequate.
Astraweb has stepped in to fill this gap, offering a technically advanced, ethically grounded, and user-focused recovery service for individuals and institutions alike.
Who is Astraweb?
Astraweb is a team of cybersecurity professionals, blockchain analysts, and ethical hackers dedicated to the recovery of lost digital assets. Known in online communities for their discretion and technical excellence, Astraweb has quietly built a reputation as the “home of crypto recovery” — a safe harbor in the sometimes stormy seas of decentralized finance.

Core Services Offered
Wallet Password Recovery Utilizing a combination of brute force optimization, machine learning, and customized dictionary attacks, Astraweb helps users recover wallets with forgotten passwords. Their tools are especially effective with partially remembered credentials.
Seed Phrase Reconstruction Lost or partial seed phrases are another major barrier to wallet access. Astraweb’s proprietary tools attempt to reconstruct valid mnemonic phrases based on user input and probabilistic modeling.
Phishing and Scam Mitigation If your crypto assets have been stolen due to phishing attacks or scams, Astraweb provides investigation support and recovery options. While crypto transactions are irreversible, Astraweb works with partners and tracing tools like Chainalysis to help track and reclaim funds when possible.
Multi-Sig and Legacy Wallet Recovery Many early wallets used now-defunct software or obscure security models. Astraweb specializes in navigating old formats, deprecated standards, and rare cryptographic setups.
Cold Wallet Restoration Lost access to hardware wallets like Trezor, Ledger, or even encrypted USB drives? Astraweb can assist with forensic-level data recovery and hardware-based key extraction.
Why Astraweb Stands Out
Confidentiality First: Every case is handled with strict privacy. Your data and identity are protected at all stages of the recovery process.
Transparent Communication: Clients are updated at every step, with no vague promises or false guarantees.
No Recovery, No Fee: Astraweb operates on a results-based model. You only pay if your assets are successfully recovered.
Client Trust and Track Record
Though much of their work remains confidential due to the sensitive nature of crypto assets, Astraweb’s success stories span from everyday investors to high-net-worth individuals and even businesses affected by inaccessible wallets or theft.
Their community reputation and testimonials underscore one thing: they deliver.
Contact Astraweb
If you’ve lost access to your cryptocurrency wallet, or fallen victim to crypto fraud, don’t give up hope. Reach out to Astraweb for a professional assessment of your situation.
Email: [email protected]
Whether it’s one token or an entire portfolio, Astraweb may be your best shot at recovery.
2 notes
·
View notes
Text
Best Methods to Hard Reset Any Android Device
Discover the most effective methods to hard reset any Android device, restoring it to factory settings and fixing software issues.
2 notes
·
View notes
Text
🔐 SMS Service Provider for OTP in Jaipur – Parken SMS
In an era of digital transformation, every business needs secure, instant, and reliable user verification. That’s where OTP (One-Time Password) messages become essential — and having a trusted SMS service provider for OTP in Jaipur is no longer a choice, it's a necessity.
Meet Parken SMS – Jaipur’s go-to name for ultra-fast, reliable, and affordable OTP SMS services.
💡 What Is OTP SMS and Why Does It Matter?
OTP SMS is a short, time-sensitive code sent to a user’s mobile number to verify identity or authorize transactions. It’s widely used for:
Logging in to secure accounts
Verifying online payments
Password recovery
Account sign-ups
Transaction approvals
If the OTP gets delayed or not delivered, your customer drops off — simple as that.
🚀 Why Parken SMS Is the Best OTP SMS Provider in Jaipur
As a business, you need a partner who delivers OTPs instantly and accurately. Parken SMS does just that:
✅ Real-Time Delivery in 2–3 Seconds We ensure your users receive OTPs instantly, even during peak hours.
✅ 100% DLT-Compliant & Secure Our system meets TRAI & DLT regulations, keeping your communications safe and legal.
✅ High Delivery Success Rate We connect directly with telecom operators to maintain a 99.9% delivery rate.
✅ Developer-Friendly API Easy to integrate with your website, app, or software — minimal coding required.
✅ Round-the-Clock Support Get help whenever you need it from our expert team in Jaipur.
🏙️ Trusted by Jaipur’s Leading Startups & Enterprises
Parken SMS is powering OTP verification systems for:
E-commerce platforms
Healthcare and education portals
Fintech apps & online banking
Booking and delivery services
Government and corporate portals
💰 Flexible Pricing, Transparent Billing
Whether you're a startup or a growing SaaS platform, our OTP SMS pricing fits all business sizes. No hidden fees. No complicated contracts.
📞 Let’s Make Security Simple!
If you're looking for a trusted SMS service provider for OTP in Jaipur, look no further than Parken SMS.
👉 Get in touch today for a demo or to explore our affordable OTP SMS packs.
0 notes
Text
Staying Ahead of the Curve: Why Regular Tech Security Updates Are Essential

In today’s fast-paced digital age, where technology shapes nearly every aspect of our lives, staying informed about tech security updates is more important than ever. From smartphones to smart homes, laptops to large-scale business networks, every device connected to the internet can be a potential target for cybercriminals. Many people overlook the critical role that timely security updates play in protecting their data, devices, and digital identity. This article will explore why tech security updates are vital, how they work, what happens if you ignore them, and best practices to ensure your technology remains secure.
The Importance of Tech Security Updates
Every day, software developers and cybersecurity experts work tirelessly to identify and fix vulnerabilities in operating systems, apps, and devices. These vulnerabilities are like tiny cracks in the walls of a fortress; if left unpatched, they offer hackers a way to break in and steal sensitive information, install malware, or even take control of entire systems. Tech security updates act as reinforcements, sealing these cracks before cybercriminals can exploit them.
While many people think that updates are just about adding new features, the security aspect is often far more critical. In fact, some of the most devastating cyberattacks in history exploited known vulnerabilities that had been left unpatched. A famous example is the 2017 WannaCry ransomware attack, which affected hundreds of thousands of computers worldwide simply because users had not installed a critical security patch.
How Tech Security Updates Work
When a security flaw is discovered, software companies quickly develop a fix. This fix is then delivered to users through a security update, which can be installed manually or automatically, depending on device settings. These updates not only patch vulnerabilities but may also include additional layers of protection to prevent similar issues in the future.
Most modern devices and operating systems allow automatic updates, ensuring that even non-technical users can keep their software up to date without lifting a finger. However, despite these conveniences, many people still delay or ignore updates, either due to concerns about storage space, data usage, or simply inconvenience.
What Happens If You Ignore Updates?
Neglecting tech security updates can lead to serious consequences. Without the latest patches, your devices become an open door for malware, spyware, ransomware, and other malicious software. Hackers can steal passwords, financial information, personal photos, and sensitive business data.
For businesses, failing to keep systems updated can result in data breaches that damage customer trust, lead to legal penalties, and cost millions in recovery efforts. In personal use, ignoring security updates can compromise online banking, social media accounts, and private communications.
In addition to security risks, skipping updates may cause compatibility problems. New applications and services often require the latest system versions to work correctly. Over time, outdated devices can become sluggish or stop working altogether as software developers focus on supporting newer versions.
Best Practices for Staying Updated
Enable Automatic Updates: The simplest way to stay protected is to enable automatic updates on all devices whenever possible. This includes smartphones, tablets, computers, and even smart home devices like security cameras and voice assistants.
Check for Updates Regularly: If automatic updates aren’t an option, make it a habit to manually check for updates at least once a week. Set reminders if necessary.
Update All Software: It’s not just your operating system that needs updating — apps, browsers, plugins, and even your antivirus software should always be up to date. Cybercriminals often target outdated third-party apps.
Be Cautious with Unsupported Devices: Older devices eventually stop receiving security updates. If you’re using a phone, computer, or router that no longer gets patches, it’s time to consider upgrading to a newer, supported model.
Stay Informed: Follow trusted tech news sources or sign up for security alerts from your device manufacturers. This will help you stay aware of any urgent tech security updates that need immediate action.
The Future of Tech Security
As technology advances, so do the tactics used by cybercriminals. The rise of artificial intelligence, smart devices, and interconnected systems means that the attack surface is constantly expanding. Tech security updates will remain a frontline defense in the ongoing battle against cyber threats.
Businesses are increasingly investing in automated patch management systems that handle updates across entire networks with minimal downtime. Likewise, many device manufacturers are working to make updates smaller, faster, and less intrusive, reducing the temptation to postpone them.
Conclusion
In a world where our personal and professional lives are deeply intertwined with technology, ignoring tech security updates is no longer an option. They are a critical component of digital hygiene, just like using strong passwords and being wary of suspicious emails. By making updates a priority, you protect not just your own information but contribute to a safer digital environment for everyone.
Remember: the next time your device prompts you to update, don’t click “Remind Me Later.” Take a few minutes to install the update — it could save you hours, days, or even weeks of headaches in the future. Stay vigilant, stay informed, and keep your tech secure.
0 notes
Text
Empowering Growth: The Importance of IT Support for Small Businesses
In today’s digital-driven world, small businesses can no longer afford to overlook the importance of IT support. Whether it’s data protection, cloud storage, software management, or cybersecurity, having the right IT infrastructure is essential. IT support not only ensures smooth daily operations but also enables small businesses to stay competitive in an increasingly tech-dependent market. With even the smallest technical glitch causing serious disruptions, IT Support for Small Businesses has evolved into a vital service rather than a luxury.
Benefits of Professional IT Support Outsourcing IT support brings a wide range of benefits for small business owners. Firstly, it allows companies to focus on their core operations while professionals handle the technical challenges. Secondly, IT experts provide proactive solutions to prevent system failures or security breaches before they occur. Furthermore, IT support helps in managing software updates, backup systems, and disaster recovery planning—essential services that many small businesses cannot efficiently handle in-house. This professional assistance improves productivity and ensures business continuity.

Data Security and Cyber Protection One of the most pressing concerns for small businesses today is data security. With increasing threats from hackers, malware, and ransomware, protecting customer and company data is paramount. IT support providers install firewalls, antivirus systems, and advanced encryption protocols to shield sensitive information. They also educate staff on best practices for password security, phishing email identification, and safe internet usage. Without this guidance, a single security lapse could lead to data breaches, legal consequences, and a damaged reputation.
Scalable and Cost-Effective Solutions Contrary to the common belief that Abbotsford IT Support is expensive, many service providers offer scalable solutions tailored for small businesses. Companies can choose service plans that match their budget and technical needs, avoiding unnecessary costs. Cloud-based services, remote monitoring, and pay-as-you-go models allow small enterprises to benefit from sophisticated IT systems without making large capital investments. This flexibility enables growing businesses to scale their IT support as they expand, making it a cost-effective long-term strategy.
Enhanced Customer Experience Today’s consumers expect quick and efficient services. Whether it’s through a fast-loading website, reliable online transactions, or seamless communication, technology plays a crucial role in customer satisfaction. IT support ensures that customer-facing technologies function smoothly. It also facilitates the use of CRM systems, automated support platforms, and digital marketing tools, all of which enhance user experience. A small glitch in your IT setup can result in poor service reviews and lost business opportunities, making robust IT support indispensable.
Investing in Success IT support is no longer optional for small businesses looking to thrive in a digital-first marketplace. It provides critical infrastructure, security, and operational efficiency that enable entrepreneurs to focus on innovation and growth. Whether through an in-house team or a managed service provider, investing in professional IT support is a smart move that yields long-term rewards. For small businesses aiming to stay agile, competitive, and secure, strong IT support is the foundation on which success is built.
0 notes
Text
Strengthening Cybersecurity in the Digital Age: A 2025 Guide
Cybersecurity refers to the process of defending systems, networks, and sensitive data from unauthorized access, damage, or theft. It encompasses a wide range of strategies and technologies, including firewalls, encryption, identity management, multi-factor authentication, and real-time threat detection.
With the rise of cloud computing, remote work, and connected devices, the scope of cybersecurity has expanded significantly. It now covers endpoints, applications, data storage, mobile devices, and even smart appliances.
The Modern Threat Landscape
Cyber threats have become more diverse and dangerous in recent years. Key risks facing businesses and users in 2025 include:
Ransomware Attacks Attackers encrypt organizational data and demand payment for its release. These attacks often cause significant downtime and financial losses.
Phishing and Social Engineering Cybercriminals use deceptive emails, websites, and messages to trick individuals into revealing passwords, financial information, or login credentials.
Zero-Day Vulnerabilities Exploits that target previously unknown software flaws are especially difficult to defend against because there’s no prior warning or patch.
Supply Chain Attacks Attackers compromise third-party vendors to gain access to larger organizations. These attacks can be stealthy and devastating.
IoT Exploits The widespread use of Internet of Things (IoT) devices introduces numerous weak points into networks, as many lack strong security features.
Key Cybersecurity Trends in 2025
To stay ahead of threats, the cybersecurity industry is rapidly evolving. Here are some of the most important trends shaping cybersecurity strategies:
AI and Machine Learning AI is being used to analyze behavior, detect anomalies, and predict threats before they escalate. Machine learning improves accuracy over time, making it an essential tool for modern cybersecurity.
Zero Trust Architecture (ZTA) This approach assumes no user or device is inherently trustworthy. Every access request is verified, regardless of location or device status.
Cloud Security Innovations With more data stored in the cloud, services like Cloud Access Security Brokers (CASBs), encryption at rest and in transit, and secure configuration management are critical.
Cybersecurity as a Service (CSaaS) Managed security providers offer scalable, affordable protection for businesses of all sizes. These services include threat monitoring, incident response, and compliance support.
Data Privacy and Compliance Global regulations are enforcing stricter controls over data usage. Laws such as GDPR, HIPAA, and DPDPA require organizations to implement strong data governance and security protocols.
Best Practices for Effective Cybersecurity
Strong cybersecurity is built on clear strategies, consistent action, and user education. Here are essential best practices every organization should follow:
Conduct Regular Security Assessments Regular audits and penetration tests help uncover vulnerabilities before attackers exploit them.
Keep Systems Updated Apply software patches and updates as soon as they are released to protect against known vulnerabilities.
Use Multi-Factor Authentication (MFA) Add an extra layer of protection beyond just usernames and passwords by requiring a second form of verification.
Train Employees on Cyber Hygiene Educate staff to recognize phishing emails, avoid malicious links, and use secure passwords. Human error remains a major cause of data breaches.
Implement Robust Backup Solutions Regularly back up critical data and test recovery plans to ensure data can be restored quickly after an incident.
Secure Network Architecture Use firewalls, intrusion detection systems, and network segmentation to reduce attack surfaces and limit lateral movement within networks.
Conclusion
Cybersecurity in 2025 demands a proactive, layered, and intelligent approach. As threats evolve, so must our defenses. Businesses and individuals alike must prioritize cybersecurity, invest in the right technologies, and foster a culture of awareness and accountability.
The digital world brings incredible opportunities—but only for those prepared to protect it. Whether you're a startup, a government agency, or a global enterprise, strong cybersecurity is your foundation for a safer, more resilient future.
At Izoe, we specialize in cutting-edge cybersecurity solutions, including MFA implementation and integration, risk assessment, and secure access management. Our team helps businesses strengthen their security posture and protect sensitive data from cyber threats.
Contact iZoe today for expert cybersecurity services tailored to your needs!
0 notes
Text
A Step-by-Step Guide to Strengthening Your Company’s IT Infrastructure Security
In today’s digital-first world, every business — regardless of its size or industry — depends on a solid and secure IT infrastructure. From customer data and internal communications to financial systems and operational tools, your company’s backbone is powered by technology. However, as technology evolves, so do the threats. That's why investing in IT infrastructure security services is not just an option, but a necessity for long-term business resilience.
Here’s a step-by-step guide to help you strengthen your company’s IT infrastructure security.
1. Conduct a Comprehensive IT Risk Assessment
The first step in securing your infrastructure is understanding where your vulnerabilities lie. Perform a full audit of your systems, networks, devices, and data storage. Identify potential risks such as outdated software, weak passwords, unsecured access points, and lack of compliance with data protection regulations. A risk assessment offers clarity and forms the foundation for all future security measures.
2. Implement Strong Access Controls
Not every employee needs access to every system. Use the principle of least privilege (PoLP) to limit access rights for users, accounts, and systems to only what is strictly required. Implement multi-factor authentication (MFA) across all platforms, especially for remote access and admin-level privileges. This significantly reduces the chances of unauthorized access or internal threats.
3. Keep Systems and Software Up to Date
Outdated systems and software are easy targets for cyber attackers. Ensure regular updates and patches are applied across all devices and platforms. Automated patch management tools can streamline this process and reduce the risk of human error or oversight.
4. Create a Robust Data Backup Strategy
Data loss, whether due to ransomware or system failure, can be catastrophic. Develop a reliable backup strategy that includes regular backups to secure, off-site locations (such as cloud storage). Make sure to test your recovery process periodically to ensure it works when needed.
5. Train Employees on Cybersecurity Best Practices
Your workforce is your first line of defense — and your weakest link if untrained. Conduct regular training sessions on phishing scams, password hygiene, safe internet use, and how to report suspicious activity. Create a culture of security awareness where employees understand the role they play in protecting your company’s assets.
6. Monitor and Respond in Real-Time
Invest in tools and services that offer real-time monitoring, intrusion detection, and threat response. Cyber incidents often happen in minutes, and early detection can prevent significant damage. Use Security Information and Event Management (SIEM) systems to aggregate and analyze logs across your network for any signs of abnormal behavior.
7. Develop an Incident Response Plan
Even with the best security measures, breaches can still occur. An incident response plan helps your organization respond quickly and effectively, minimizing downtime and loss. The plan should define roles, communication protocols, and a clear course of action for various security incidents.
8. Work with Trusted Security Experts
Strengthening your IT infrastructure is not a one-time task — it requires ongoing evaluation, strategy, and adaptation. Partnering with experienced professionals can bring deep insights and scalable solutions.
This is where Inspirenet can make a difference.
Why Choose Inspirenet for Your IT Security Needs?
At Inspirenet, we understand the unique challenges businesses face when it comes to safeguarding their digital environment. Our team provides tailored IT infrastructure security services that align with your specific needs, whether you’re a startup or a large enterprise. From risk assessment and compliance to real-time monitoring and response, we are committed to building a resilient IT environment for your business.
Future-proof your infrastructure with Inspirenet — because your business deserves security you can trust.

0 notes
Text
2025’s Best Picks: Top 5 Cryptocurrency Wallet Clone Software

The cryptocurrency market in 2025 has matured significantly compared to previous years, with wider adoption, stronger regulations, and heightened demand for secure digital asset storage. According to recent market research, the global cryptocurrency wallet market is projected to reach $3.5 billion by the end of 2025, growing at a compound annual growth rate (CAGR) of over 24%. This surge is driven by the expanding use of decentralized finance (DeFi), non-fungible tokens (NFTs), and increasing public interest in holding crypto assets independently.
Security breaches, wallet hacks, and loss of private keys have also emphasized the importance of choosing a trusted wallet provider. This article will explore what a cryptocurrency wallet is, list the top 5 trusted wallets of 2025, and explain why wallet integration is crucial in modern crypto exchange development.
What is a Cryptocurrency Wallet?
A cryptocurrency wallet is a digital tool that enables users to store, manage, and interact with blockchain-based assets. Unlike traditional wallets that store physical money, crypto wallets store private and public keys that allow users to access their cryptocurrencies on the blockchain.
There are two primary types of cryptocurrency wallets:
Hot Wallets – Connected to the internet, allowing quick and easy access. Examples include mobile apps, web-based wallets, and desktop wallets.
Cold Wallets – Offline storage solutions, such as hardware wallets and paper wallets,
which offer enhanced security by keeping keys disconnected from the internet.
Top 5 Cryptocurrency Wallets in 2025
With hundreds of options in the market, choosing the most secure and functional wallet requires understanding the wallet’s trustworthiness, user base, and overall performance. Let's explore the top 5 cryptocurrency wallet development in 2025.
1. Ledger Nano X
Still a leading cold wallet in 2025, Ledger Nano X offers unmatched security with its hardware-based solution. It supports over 5,500 cryptocurrencies and includes Bluetooth connectivity for mobile access. With robust firmware updates and integration with the Ledger Live app, it is a preferred choice among long-term investors and institutions.
Key Features:
1. Secure Element chip for private key protection
2. Multi-currency support
3. Offline transaction verification
4. Mobile and desktop compatibility
2. MetaMask
MetaMask remains dominant among DeFi and NFT users. Its browser extension and mobile wallet enable seamless interaction with Ethereum-based platforms and other EVM-compatible blockchains. In 2025, MetaMask added native support for multiple chains, improving its appeal.
Key Features:
1. Web3 integration for dApps
2. Built-in token swapping
3. Hardware wallet support
4. Advanced phishing protection
3. Trust Wallet
Backed by Binance, Trust Wallet is a non-custodial mobile wallet supporting a wide range of cryptocurrencies and blockchains. It’s known for its intuitive interface and built-in DEX (Decentralized Exchange). In 2025, Trust Wallet expanded its features to include staking, NFT storage, and multi-chain bridging.
Key Features:
1. Supports 70+ blockchains
2. In-app staking for passive income
3. NFT and token management
4. Strong security and privacy controls
4. Trezor Model T
Trezor Model T remains a top competitor in the hardware wallet segment. Known for its open-source software and transparent security practices, it’s favored by users who prioritize transparency and self-custody.
Key Features:
1. touchscreen interface
2. Open-source firmware
3. Password manager and U2F authentication
4. Recovery seed protection
5. Coinbase Wallet
Separate from the Coinbase exchange account, the Coinbase Wallet is a self-custodial option giving users full control of their assets. In 2025, the wallet supports Web3 browsing, NFTs, and cross-chain capabilities, making it ideal for beginners who want exchange access with decentralized freedom.
Key Features:
1. Easy-to-use interface
2. Direct integration with Coinbase Exchange
3. Multi-chain asset support
4. Biometric authentication
Why Integrate the Wallet in a Crypto Exchange?
Integrating cryptocurrency wallets within a crypto exchange platform brings numerous advantages, particularly in user experience, security, and transaction efficiency. In 2025, crypto exchanges that offer native or seamlessly integrated wallets are more trusted by users and enjoy greater user retention.
1. Enhanced Security
By integrating secure wallets, exchanges reduce the risk of third-party vulnerabilities. Built-in wallets can incorporate multi-signature authorization, biometric access, and cold storage options directly into the platform.
2. Improved User Experience
A native wallet integration allows users to deposit, withdraw, and trade cryptocurrencies without switching platforms or manually entering wallet addresses. This convenience increases trading volume and user satisfaction.
3. Support for DeFi and Web3
Wallet integration enables seamless access to decentralized apps and DeFi protocols. This adds extra value for users who want to stake tokens, farm yields, or interact with NFTs directly from the exchange interface.
4. Brand Trust and Loyalty
Offering a reliable and secure wallet under a recognized exchange brand builds user trust. With wallet-related hacks still a threat in 2025, users prefer platforms that prioritize wallet security and usability.
Final Thoughts
In 2025, cryptocurrency wallets role is more crucial than ever. Investors, traders, and even casual users demand security, flexibility, and control over their digital assets. The top 5 wallets mentioned—Ledger Nano X, MetaMask, Trust Wallet, Trezor Model T, and Coinbase Wallet, have proven their reliability through continuous innovation and user-focused features.
Whether you're building a crypto project or simply looking to store your assets, choosing a trusted wallet is a foundational step in ensuring the safety and longevity of your digital wealth. Security Tokenizer, a leading cryptocurrency wallet development company, plays a vital role in this space by delivering feature-rich cryptocurrency wallet clone software to modern blockchain technology. Their expertise supports businesses in creating wallets with advanced security protocols, multi-currency support, and seamless integration capabilities, making them a trusted partner in the ever-growing crypto ecosystem.
#Cryptocurrency Wallet Development Company#Cryptocurrency Wallet Development#Cryptocurrency Wallet Development Services#Cryptocurrency Wallet Development Solutions#White Label Cryptocurrency Wallet#Multi Cryptocurrency Wallet#Crypto wallet#Cryptocurrency Wallet#Crypto Wallet Development#Wallet Development Company#Wallet Development#Wallet#Types of Wallet
0 notes
Text
How to Track a Cricket Cell Phone Location Free: What Really Works
Hey there! Last month, my daughter didn't come home on time. I was worried sick. That's when I learned how to track her Cricket phone for free.
Let me share what actually works. No fluff. Just real solutions.
✅CLICK HERE TO TRACK A CRICKET CELL PHONE LOCATION FOR FREE
Why Track a Cricket Phone?
Before we start, here's why people need this:
Lost phone somewhere
Kids not answering
Elderly parents' safety
Phone got stolen
Good news? There are free ways that work.
Method 1: Google's Find My Device (Best Free Option)
This is my go-to method. Works great for Android phones.
How to use it:
Go to android.com/find
Sign in with the Google account
Pick the phone you want
See it on the map
That's it. Seriously.
Requirements: Phone must be on. Internet connected. Location enabled.
I found my son's phone at soccer practice this way. Took 2 minutes.
Method 2: Find My for iPhones
Got an iPhone on Cricket? Use Apple's version.
Visit icloud.com/find
Log in with Apple ID
Click the device
View location
My sister tracks her iPhone this way. Found it in her couch once. True story.
Method 3: Cricket Family Locator
Cricket has their own service. Costs $9.99/month. But...
They offer a free trial. Sometimes 30 days.
Text "FAMILY" to 247487 to start.
I tried it. Works okay. But honestly? Google's free option worked just as well.
Method 4: Free Tracking Apps
Some popular free ones:
Life360 - Basic tracking free
Where's My Droid - Makes phone ring remotely
Glympse - Temporary location sharing
My neighbor loves Where's My Droid. Found her phone in a taxi with it.
Important: Do This NOW
Don't wait for an emergency. Set up tracking today:
Enable location services on the phone
Test it works before you need it
Share passwords with family
Keep phones charged
Trust me. You'll thank yourself later.
My Wake-Up Call
Last summer, my dad went for a walk. He has mild dementia. Didn't come back.
Three hours passed. Mom was crying. Then I remebered...
We had set up location sharing on his Cricket phone. Found him in a park 2 miles away. Confused but safe.
That's when it hit me. This isn't about spying. It's about safety.
Common Problems
"Location not updating"
Check internet connection
Restart the phone
Make sure location is on
"Can't log in"
Try password recovery
Check two-factor settings
Call Cricket if needed
Quick Tips
Always get permission first (it's the law)
Free methods work just as well as paid ones
Battery drains faster with tracking on
No internet = no tracking
The Bottom Line
You don't need expensive apps. Or sketchy spy software. The free methods I shared? They really work.
I use Google's Find My Device for my family. It's simple. Reliable. And completly free.
Just remember: Use these tools to help and protect. Not to control or spy.
Stay safe out there.
Have questions? Had a similar experiance? Drop a comment below.
Note: Always get proper authorization before tracking any device. This article is for informational purposes only.
1 note
·
View note
Text
Ledger Live Login - Securely Manage All Your Crypto Assets
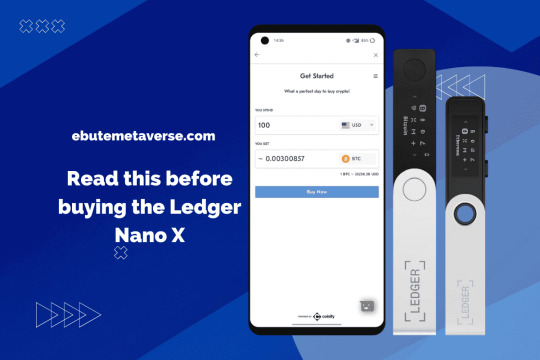
In the ever-evolving world of cryptocurrency, security and user experience remain two top priorities for investors and enthusiasts alike. One of the leading names in crypto security is Ledger, a company known for its hardware wallets like the Ledger Nano S and Ledger Nano X. Complementing these devices is Ledger Live Login, a powerful desktop and mobile application that lets users manage their crypto assets with ease. A key step in accessing this ecosystem is the Ledger Live login—and ensuring it’s done securely is paramount.
What Is Ledger Live?
Ledger Live is the official application from Ledger that allows users to interact with their hardware wallet. It provides an intuitive interface to:
Check real-time balances
Send and receive over cryptocurrencies
Stake assets like Ethereum and Polkadot
Manage NFTs
Access services like buying, swapping, or selling crypto
Whether you're a seasoned investor or a crypto newbie, Ledger Live is built to make managing your digital assets more streamlined and secure.
Understanding Ledger Live Login
Unlike traditional login systems that require usernames and passwords, Ledger Live uses a hardware-based authentication mechanism. When you “log in” to Ledger Live, you're essentially:
Connecting your Ledger device (Nano S, S Plus, or X)
Entering your device’s PIN
Granting permission for Ledger Live to access your device
This eliminates the need for a password-based system, making it much harder for hackers to breach your account. The private keys never leave your hardware wallet, which means your assets are stored in the most secure manner possible.
Setting Up Ledger Live
Here’s a quick step-by-step for first-time users:
Download Ledger Live from the official Ledger website (ensure you're not downloading from a fake or phishing site).
Install the app and select whether you’re setting up a new device or restoring one.
Connect your Ledger hardware wallet to your computer or mobile device.
Enter your PIN on the device to unlock it.
Open the Ledger Live app, and your device will prompt you to allow the connection.
Once authenticated, you’ll have access to your dashboard.
It’s worth noting: Ledger Live Login does not have a "cloud login" or online account. All access is local and tied to your hardware device and seed phrase.
Security Best Practices for Ledger Live Login
To keep your crypto safe, follow these best practices:
Always verify URLs before downloading or updating Ledger Live (official site).
Never share your recovery phrase with anyone. Ledger will never ask for it.
Enable Ledger’s password lock feature for additional access control on Ledger Live.
Keep your firmware and Ledger Live app updated to avoid vulnerabilities.
Use a secure computer or mobile device that is free of malware or suspicious software.
Common Issues and Troubleshooting
Users occasionally run into issues with Ledger Live login, such as:
App not recognizing the device: Try switching USB cables or ports, and make sure your device is unlocked.
Firmware update prompts: These are normal and often required for compatibility and security.
PIN problems: Entering the wrong PIN multiple times will wipe the device—keep your recovery phrase handy in such cases.
Final Thoughts
The Ledger Live Login ogin process is refreshingly different from traditional login systems. By requiring hardware-based access, it adds a layer of security that keeps your assets safe from remote hacks and phishing attempts. As crypto adoption grows, tools like Ledger Live make it easier—and safer—for everyone to enter and manage the world of digital assets.
Whether you're sending your first Bitcoin or managing a diverse DeFi portfolio, Ledger Live provides a trustworthy platform. Just remember: your security is only as strong as your habits—so stay informed, stay cautious, and keep your keys safe.
0 notes
Text
E-Waste and Data Security: Why Proper Disposal Matters
As technology evolves at a breakneck pace, electronic devices quickly become outdated, resulting in a growing mountain of electronic waste, or e-waste. Proper e-waste management isn’t just about protecting the environment—it’s also critical for safeguarding your sensitive data stored on these devices.

Why Data Security Is a Major Concern in E-Waste
Many electronic devices like computers, smartphones, tablets, and external hard drives store vast amounts of personal or corporate data. When these devices are discarded improperly, that data can be easily accessed by malicious actors. This poses serious risks such as identity theft, financial fraud, and corporate espionage.
Key Risks of Improper E-Waste Disposal:
Data Breaches: Devices thrown away without proper data erasure can still contain recoverable information.
Identity Theft: Personal information such as social security numbers, bank details, and passwords may be exposed.
Corporate Espionage: Sensitive business data, trade secrets, or client information can be exploited.
Legal Consequences: Many regions have strict laws regarding data protection and e-waste disposal. Improper handling can lead to hefty fines.
Best Practices for Secure E-Waste Management:
Certified Data Wiping: Use specialized software that permanently erases all data beyond recovery.
Physical Destruction: Techniques like shredding or crushing hard drives ensure data cannot be retrieved.
Partner with Certified Recyclers: Ensure your e-waste is handled by companies that follow strict security and environmental protocols.
Maintain Documentation: Keep records of data destruction to demonstrate compliance with legal and regulatory standards.
Proper data security in e-waste management is essential for individuals and businesses alike. Beyond data protection, responsible recycling prevents harmful materials from contaminating the environment.
Effective e-waste management requires more than just recycling—it demands a secure process that protects your data and the planet. For trustworthy and compliant e-waste disposal with certified data destruction, rely on Hero Environmental Services. Their expert team provides secure, environmentally responsible solutions tailored to your needs.Contact Hero Environmental Services today to safeguard your data while managing your e-waste responsibly.
0 notes
Text
Essential Cybersecurity Best Practices for Safeguarding Digital Assets in 2025

In the rapidly evolving digital landscape of 2025, digital assets – from sensitive customer data and proprietary information to critical operational systems – are the lifeblood of businesses across every sector. However, this increased reliance on digital technologies also presents an ever-expanding attack surface, making these assets prime targets for cybercriminals. As we've seen from recent incidents, neglecting cybersecurity can have devastating consequences.
Protecting your digital assets isn't a one-time task; it requires a proactive, layered approach based on established best practices. While the threat landscape is constantly shifting, certain fundamental principles remain essential for building a robust defense. Here are some of the critical cybersecurity best practices your organization must prioritize in 2025:
1. Build a Strong Foundation: Access Control and Authentication
Unauthorized access is a primary vector for cyberattacks. Implementing strict controls on who can access your digital assets is non-negotiable.
Implement Multi-Factor Authentication (MFA) Everywhere: Passwords alone are no longer sufficient. MFA requires users to provide two or more verification factors to gain access (e.g., password plus a code from a mobile app or a fingerprint). This simple step dramatically reduces the risk of account compromise.
Apply the Principle of Least Privilege: Users and systems should only have the minimum level of access necessary to perform theirspecific tasks. This limits the potential damage if an account or system is compromised.
Regularly Review Access Controls: Periodically audit user accounts and permissions to ensure they are still appropriate and remove access for employees who have left or changed roles.
2. Keep Systems Hardened: Patching and Secure Configurations
Cyber attackers frequently exploit known vulnerabilities in software and systems. Staying on top of updates and configurations is crucial.
Establish a Robust Patch Management Process: Regularly update all software, operating systems, and applications with the latest security patches. Automate this process wherever possible to ensure timely deployment.
Implement Secure Configurations: Ensure all systems, devices, and applications are configured securely, disabling unnecessary services and closing potential backdoor entry points. Don't rely on default settings.
3. Protect the Data Itself: Encryption and Backups
Even if attackers breach your defenses, strong data protection measures can render stolen data useless and enable recovery.
Encrypt Sensitive Data: Encrypt sensitive data both when it's stored (at rest) and when it's being transmitted across networks (in transit). This scrambles the data, making it unreadable to unauthorized parties.
Regularly Back Up Data and Test Recovery: Implement a schedule for regular backups of all critical data. Crucially, test your backup restoration process regularly to ensure you can actually recover your data quickly and effectively in the event of a ransomware attack or other data loss event. Store backups securely, ideally air-gapped or offsite.
Classify Data and Implement Handling Policies: Understand what sensitive data you possess, classify it based on its importance and sensitivity, and establish clear policies for how it should be handled, stored, and transmitted.
4. Secure Your Network and Endpoints:
Protecting the entry points and pathways within your digital infrastructure is fundamental.
Deploy and Maintain Firewalls and Network Segmentation: Firewalls act as barriers, controlling traffic in and out of your network. Network segmentation divides your network into smaller, isolated zones, preventing attackers from easily moving laterally if they gain a foothold.
Utilize Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can alert you to or automatically block suspicious connections.
Implement Strong Endpoint Security: Every device connected to your network (computers, laptops, mobile phones) is a potential entry point. Deploy comprehensive antivirus/anti-malware software, and consider more advanced Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solutions for enhanced threat detection and response capabilities.
5. Empower Your People: Security Awareness Training
Employees are often the first line of defense, but they can also be the weakest link if they are not adequately trained.
Provide Comprehensive and Ongoing Security Awareness Training: Regularly educate employees about current threats like phishing, social engineering, malware, and the importance of strong passwords and secure online behavior. Use varied training methods and simulated attacks (like phishing tests) to reinforce learning. Foster a culture where employees feel empowered to report suspicious activity without fear of reprisal.
6. Prepare for the Inevitable: Incident Response Planning
As discussed in previous blogs, a cyber incident is a matter of when, not if. Knowing how to react is critical.
Develop and Maintain a Detailed Incident Response Plan (IRP): Have a clear, documented plan outlining the steps your organization will take before, during, and after a cybersecurity incident. This includes roles, responsibilities, communication protocols, and technical procedures (refer back to the 7 phases of incident response). Regularly test your IRP through tabletop exercises and simulations.
7. Stay Vigilant: Monitoring, Testing, and Third-Party Risk Management
The threat landscape is dynamic, requiring continuous effort to stay ahead.
Implement Continuous Monitoring and Logging: Monitor network activity, system logs, and user behavior for signs of suspicious activity. Centralized logging and security information and event management (SIEM) systems can help detect anomalies.
Conduct Regular Security Assessments and Testing: Periodically perform vulnerability scans to identify weaknesses in your systems and conduct penetration testing to simulate real-world attacks and evaluate your defenses.
Manage Third-Party Risk: Your digital assets can be exposed through your vendors and partners. Establish a process for vetting the security posture of third parties and continuously monitor their compliance with your security requirements.
Building a Culture of Security
Ultimately, effective cybersecurity is not just about technology; it's about people and processes. Foster a culture of security awareness throughout your organization, where everyone understands their role in protecting digital assets. Encourage open communication about security concerns and make cybersecurity a regular topic of discussion at all levels.
By diligently implementing these essential cybersecurity best practices, your organization can significantly strengthen its digital defenses, reduce the likelihood and impact of cyberattacks, and safeguard its valuable digital assets in the challenging environment of 2025 and beyond. Proactive security is your best investment in digital resilience.
0 notes
Text
I.T. For Less – Empowering Chicago Businesses with Cost-Effective Managed IT Solutions
Introduction:
In today’s fast-paced digital world, the efficiency, security, and reliability of your business's IT infrastructure can determine its success. For small and mid-sized enterprises in Chicago, managing in-house IT operations can be both costly and time-consuming. That’s where I.T. For Less – Chicago Managed IT Service Provider steps in. With our dedicated focus on cost-effective, reliable, and customized solutions, we help businesses reduce downtime, improve performance, and enhance data security through proactive tech support and innovative IT strategies. Whether you’re seeking ongoing maintenance, cloud solutions, cybersecurity enhancements, or tech support outsourcing, we offer the services that allow you to focus on what you do best—growing your business.
Why Choose a Managed IT Service Provider in Chicago?
The role of a managed IT service provider is to take over the day-to-day responsibility for a range of IT services. This includes managing networks, devices, software, data security, and end-user support. Partnering with a local provider like I.T. For Less means getting access to experienced technicians who understand the specific challenges faced by Chicago-based businesses.
Our localized approach ensures faster response times, better alignment with regulatory requirements, and personalized customer service that national chains often can’t provide. Most importantly, our cost-effective plans make enterprise-level IT support accessible for businesses of all sizes.
Comprehensive Managed Services for Modern Businesses
At I.T. For Less, we offer an expansive suite of services tailored to your business needs. Our goal is to provide seamless technology integration and uninterrupted operations for our clients.
1. Proactive Network Monitoring and Management
Downtime costs money. That’s why our team actively monitors your network 24/7 to detect and prevent issues before they escalate. By leveraging intelligent tools and automation, we identify threats, performance bottlenecks, and potential outages—resolving them before you’re even aware there’s a problem.
2. Cybersecurity and Data Protection
In a world of growing cyber threats, cybersecurity is not optional. As a leading managed service provider, I.T. For Less delivers comprehensive protection through firewall management, anti-virus systems, email filtering, data encryption, and real-time threat intelligence. We also help companies with compliance standards such as HIPAA, GDPR, and PCI-DSS.
3. Cloud Solutions and Virtualization
Today’s workforce is mobile and cloud-dependent. We help businesses transition to secure, scalable cloud platforms such as Microsoft 365, Google Workspace, and custom virtual environments. Whether you need cloud migration, backup solutions, or virtual desktops, we ensure optimal performance with built-in disaster recovery and minimal disruption.
4. Tech Support and Help Desk Services
Our round-the-clock tech support team is trained to handle all IT issues—from password resets to complex server errors. Through remote and on-site assistance, we offer reliable and timely help desk services that minimize employee frustration and boost productivity. This is where tech support outsourcing shines: you save money while ensuring fast, professional assistance.
5. Hardware and Software Management
Keeping your hardware and software updated is vital for business continuity. We take charge of patch management, software licensing, procurement, and hardware upgrades to make sure your systems run smoothly. Whether you need new computers, servers, or productivity tools, we handle every aspect efficiently.
6. Strategic IT Consulting and Planning
Technology should support business goals, not hinder them. Our consultants work with you to understand your operational challenges, then create a strategic IT roadmap tailored to your growth objectives. This includes budgeting, forecasting, and identifying emerging tech that aligns with your long-term vision.
The Advantages of Tech Support Outsourcing
Outsourcing tech support to I.T. For Less allows your team to focus on core business operations while we handle the technical complexities. Here's why more Chicago businesses are embracing tech support outsourcing:
Cost Savings: Avoid the high costs of hiring and training an in-house IT team.
24/7 Availability: Our team is always on call—during business hours, after hours, and on holidays.
Scalable Services: Our flexible packages grow with your business, whether you’re scaling up or down.
Expertise On-Demand: Access certified professionals with a wide range of specializations.
Who We Serve
I.T. For Less serves a wide range of industries across Chicago and surrounding areas. Our clients include:
Law Firms
Financial Institutions
Medical and Dental Clinics
Retail and E-commerce
Nonprofits
Startups and Tech Firms
Educational Institutions
Whether you need HIPAA compliance, secure payment systems, or support for remote employees, we have the tools and experience to deliver.
Managed IT Services Customized for Your Business
Unlike generic providers, we believe that one-size-fits-all doesn’t apply to IT. Every organization has unique needs based on its industry, size, and growth stage. That’s why I.T. For Less offers customized solutions based on detailed assessments and performance metrics. Our managed IT plans are modular, so you can select exactly what you need and nothing you don’t.
Staying Ahead with Future-Ready IT Support
The tech landscape changes fast. Cloud computing, AI, edge computing, and IoT are evolving the way businesses operate. Our team stays up-to-date on emerging technologies and helps you integrate them securely and effectively. As your managed IT service provider, we are your long-term technology partner—positioning you to stay ahead of competitors.
Local Support, Global Vision
Though we are based in Chicago, our service standards match those of top national firms. We combine the reliability of global IT practices with the personalized attention of a local business. Our Chicago-based technicians can be on-site when needed, giving you peace of mind and faster problem resolution.
The I.T. For Less Promise
At I.T. For Less, our name reflects our mission: providing high-quality managed service provider solutions at a fraction of traditional costs. We’re committed to transparency, customer satisfaction, and measurable results. Whether you need one-time assistance or long-term IT management, our flexible pricing and outstanding service make us the trusted partner of choice for businesses in Chicago.
Our Process: Simple, Secure, and Scalable
Initial Consultation – We assess your current infrastructure and business needs.
Customized Proposal – Based on your goals, we create a detailed IT plan and service scope.
Onboarding & Setup – Our technicians ensure a smooth and secure transition.
Ongoing Support & Optimization – With 24/7 monitoring, performance reporting, and regular audits.
Why Small and Medium Businesses Trust I.T. For Less
The backbone of Chicago’s economy is its vibrant small and medium business sector. We understand the unique budgetary and operational challenges that SMBs face and offer tailored services that bring enterprise-grade IT capabilities within reach. Our focus is not just on technology—but on enabling your business to thrive.
0 notes
Text
Cybersecurity: Safeguarding the Digital Frontier
Introduction
In our increasingly interconnected world, the security of digital systems has never been more critical. As individuals, corporations, and governments digitize operations, data becomes a prime target for malicious actors. Cybersecurity, once a niche concern, is now a cornerstone of digital strategy. It encompasses the practices, technologies, and processes designed to protect systems, networks, and data from cyber threats. With the rise of cybercrime, which causes trillions in damages annually, understanding cybersecurity is essential — not just for IT professionals, but for anyone using the internet.
1. What is Cybersecurity?
Cybersecurity refers to the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It is often divided into a few common categories:
Network security: Protecting internal networks from intruders by securing infrastructure and monitoring network traffic.
Application security: Ensuring software and devices are free of threats and bugs that can be exploited.
Information security: Protecting the integrity and privacy of data, both in storage and transit.
Operational security: Managing and protecting the way data is handled, including user permissions and policies.
Disaster recovery and business continuity: Planning for incident response and maintaining operations after a breach.
End-user education: Teaching users to follow best practices, like avoiding phishing emails and using strong passwords.
2. The Rising Threat Landscape
The volume and sophistication of cyber threats have grown rapidly. Some of the most prevalent threats include:
Phishing
Phishing attacks trick users into revealing sensitive information by masquerading as trustworthy sources. These attacks often use email, SMS, or fake websites.
Malware
Malware is any software designed to harm or exploit systems. Types include viruses, worms, ransomware, spyware, and trojans.
Ransomware
Ransomware locks a user’s data and demands payment to unlock it. High-profile cases like the WannaCry and Colonial Pipeline attacks have demonstrated the devastating effects of ransomware.
Zero-day Exploits
These are vulnerabilities in software that are unknown to the vendor. Hackers exploit them before developers have a chance to fix the issue.
Denial-of-Service (DoS) Attacks
DoS and distributed DoS (DDoS) attacks flood systems with traffic, overwhelming infrastructure and causing service outages.
3. Importance of Cybersecurity
The consequences of cyberattacks can be severe and widespread:
Financial Loss: Cybercrime is estimated to cost the world over $10 trillion annually by 2025.
Data Breaches: Personal data theft can lead to identity fraud, blackmail, and corporate espionage.
Reputational Damage: A data breach can erode trust in a company, damaging customer relationships.
Legal Consequences: Non-compliance with data protection laws can lead to lawsuits and hefty fines.
National Security: Governments and military networks are prime targets for cyber warfare and espionage.
4. Key Cybersecurity Practices
1. Risk Assessment
Identifying and prioritizing vulnerabilities helps organizations allocate resources efficiently and address the most significant threats.
2. Firewalls and Antivirus Software
Firewalls monitor incoming and outgoing traffic, while antivirus software detects and removes malicious programs.
3. Encryption
Encryption protects data by converting it into unreadable code without a decryption key, ensuring data privacy even if intercepted.
4. Multi-Factor Authentication (MFA)
MFA adds a layer of protection beyond passwords, requiring users to verify identity through additional means like OTPs or biometrics.
5. Regular Updates and Patching
Cybercriminals often exploit outdated systems. Regular software updates and security patches close these vulnerabilities.
6. Backups
Frequent data backups help in recovery after ransomware or system failure.
5. Cybersecurity for Individuals
Individuals are often the weakest link in cybersecurity. Here’s how to stay safe:
Use strong, unique passwords for every account.
Be cautious of unsolicited emails or messages, especially those requesting personal information.
Regularly update devices and apps.
Enable two-factor authentication wherever possible.
Avoid public Wi-Fi for sensitive transactions unless using a VPN.
6. Cybersecurity for Businesses
Businesses face unique threats and must adopt tailored security strategies:
Security Policies
Organizations should develop formal policies outlining acceptable use, incident response, and data handling procedures.
Employee Training
Staff should be trained to recognize phishing attacks, report suspicious behavior, and follow cybersecurity protocols.
Security Operations Center (SOC)
Many businesses use SOCs to monitor, detect, and respond to cyber incidents 24/7.
Penetration Testing
Ethical hackers simulate attacks to uncover vulnerabilities and test a company’s defenses.
7. Emerging Technologies and Cybersecurity
As technology evolves, so too do the threats. Here are some emerging fields:
Artificial Intelligence and Machine Learning
AI enhances threat detection by analyzing massive datasets to identify patterns and anomalies in real-time.
Internet of Things (IoT)
With billions of connected devices, IoT expands the attack surface. Weak security in smart devices can create backdoors into networks.
Quantum Computing
While quantum computing promises advancements in processing power, it also threatens traditional encryption methods. Post-quantum cryptography is a new area of focus.
8. Cybersecurity Regulations and Frameworks
Governments and industries enforce standards to ensure compliance:
GDPR (General Data Protection Regulation): Governs data privacy in the EU.
HIPAA (Health Insurance Portability and Accountability Act): Protects health data in the U.S.
NIST Cybersecurity Framework: A widely adopted set of standards and best practices.
ISO/IEC 27001: International standard for information security management.
Compliance not only avoids fines but demonstrates a commitment to protecting customer data.
9. Challenges in Cybersecurity
Cybersecurity faces numerous challenges:
Evolving Threats: Attack techniques change rapidly, requiring constant adaptation.
Talent Shortage: There’s a global shortage of qualified cybersecurity professionals.
Budget Constraints: Small businesses often lack resources for robust security.
Third-Party Risks: Vendors and contractors may introduce vulnerabilities.
User Behavior: Human error remains one of the leading causes of security breaches.
10. The Future of Cybersecurity
Looking ahead, the cybersecurity landscape will be shaped by:
AI-powered threat detection
Greater emphasis on privacy and data ethics
Cybersecurity as a core part of business strategy
Development of zero-trust architectures
International cooperation on cybercrime
Conclusion
Cybersecurity is no longer optional — it’s a necessity in the digital age. With cyber threats becoming more frequent and sophisticated, a proactive and layered approach to security is crucial. Everyone, from casual internet users to CEOs, plays a role in protecting digital assets. Through education, technology, policy, and cooperation, we can build a safer digital world.
0 notes
Text
The Ultimate Guide to Securing and Backing Up Your Business Data
In today’s digital age, data security and backup are not optional—they’re essential. Whether you’re a startup or an established enterprise, losing data due to cyberattacks, system failure, or human error can cripple your business. That’s why Elarafy brings you this ultimate guide to help you protect your valuable data.
Why Business Data Backup and Security Matter
Every business handles sensitive data customer records, financial reports, proprietary documents. Without a reliable data backup strategy and robust cybersecurity practices, you're risking financial loss, legal issues, and reputational damage.
Top Tips to Secure Your Business Data
Use Strong Passwords and Multi-Factor Authentication (MFA): Safeguard access with complex credentials and additional verification steps.
Encrypt Your Data: Ensure data is encrypted both in transit and at rest to protect against unauthorized access.
Update Software Regularly: Keep operating systems and applications updated to patch known vulnerabilities.
Train Your Team: Employee awareness is your first line of defense. Offer regular cybersecurity training.
Best Practices for Backing Up Business Data
Follow the 3-2-1 Rule: Keep 3 copies of your data, on 2 different media, with 1 offsite backup.
Automate Backups: Schedule automatic backups to avoid manual errors and ensure consistency.
Test Your Backups: Regularly verify that your data can be restored in an emergency.
Why Choose Elarafy?
At Elarafy, we specialize in helping businesses implement secure, automated, and reliable data protection solutions. From cloud backups to disaster recovery, our services ensure your data is safe always.
Secure your business future protect your data with Elarafy.
Looking to learn more about data backup solutions for businesses? Contact us today!
0 notes
Text
How an IT Company Protects Your Business from Cyber Threats?

In today’s digital-first world, businesses of all sizes face a constant barrage of cyber threats—from phishing scams and ransomware attacks to data breaches and zero-day vulnerabilities. As technology advances, so do the tactics of cybercriminals. This makes cybersecurity not just a luxury but a necessity. Fortunately, an experienced IT Services Company plays a crucial role in shielding your business from these dangers.
In this blog, we’ll explore how an IT Company helps protect your business from cyber threats and why investing in professional IT services is essential for long-term success.
Understanding the Cyber Threat Landscape
Before diving into how IT companies protect your business, it’s important to understand the evolving nature of cyber threats. Here are some common types:
Phishing Attacks: Deceptive emails or messages are designed to steal sensitive information.
Ransomware: Malicious software that locks your files and demands a ransom for access.
Data Breaches: Unauthorized access to confidential data.
DDoS Attacks: Flooding servers to crash websites and disrupt services.
Insider Threats: Employees or partners misusing access to harm your business.
Cybercrime is no longer limited to large corporations. Small and medium businesses are increasingly targeted due to weaker defenses, making cybersecurity a business-critical priority.
How an IT Services Company Safeguards Your Business
A professional IT Company offers a multi-layered approach to cybersecurity. Here’s how:
1. Risk Assessment and Vulnerability Audits
The first step an IT company takes is to assess your current security posture. They perform:
Security audits to identify weaknesses
Risk assessments to evaluate potential threats
Compliance checks based on industry regulations
This helps create a security roadmap tailored to your business needs.
2. Network Security Implementation
Your company’s network is the primary entry point for many cyber threats. An IT Services Company strengthens it by:
Configuring firewalls and intrusion detection systems (IDS)
Monitoring data traffic for unusual activities
Blocking unauthorized access through virtual private networks (VPNs)
These measures ensure your data stays protected within a secure environment.
3. Data Encryption and Backup Solutions
Data is the most valuable asset in the digital age. A reliable IT Company ensures:
End-to-end encryption of sensitive information
Regular backups to protect against data loss
Off-site and cloud-based storage solutions for recovery
Even if ransomware hits, your backed-up data ensures business continuity.
4. Endpoint Protection
With remote work becoming the norm, every device connected to your network is a potential threat vector. IT companies provide:
Antivirus and anti-malware solutions
Device-level encryption
Mobile device management (MDM) tools
This protects all endpoints—laptops, smartphones, and desktops—against cyberattacks.
5. User Training and Awareness Programs
Even the best technology can’t prevent human error. That’s why an IT Services Company conducts:
Phishing simulations
Cyber hygiene workshops
Password management training
Empowering your employees makes them the first line of defense instead of a weak link.
6. Real-Time Monitoring and Incident Response
Cyber threats can occur at any time. A proactive IT Company offers:
24/7 network monitoring
Threat detection using AI and machine learning
Rapid incident response and containment strategies
Early detection can stop a cyberattack in its tracks before damage is done.
7. Compliance and Regulatory Support
If your business operates in industries like finance, healthcare, or e-commerce, compliance is critical. IT service providers help you meet:
GDPR (General Data Protection Regulation)
HIPAA (Health Insurance Portability and Accountability Act)
PCI-DSS (Payment Card Industry Data Security Standard)
This reduces the risk of fines, lawsuits, and reputational damage.
Benefits of Partnering with an IT Services Company
When you partner with a reputable IT Company, you gain more than just technical support. Here’s what you can expect:
Cost Efficiency
Maintaining an in-house IT team with full cybersecurity expertise can be expensive. Outsourcing gives you access to top-tier skills at a fraction of the cost.
Scalability
As your business grows, your cybersecurity needs evolve. An IT company can scale services to match your requirements without disruptions.
Focus on Core Business
Cybersecurity management is time-consuming. Delegating it to experts allows you to concentrate on what you do best—running your business.
Access to Latest Technologies
IT companies stay updated with the latest tools, software, and strategies. You get enterprise-grade security without investing in expensive infrastructure.
Real-World Examples of IT Companies Preventing Cyber Threats
Let’s consider a few hypothetical but realistic scenarios:
Retail Company Avoids Data Breach
A retail chain working with an IT Services Company detected a suspicious login attempt from a foreign IP. The IT team quickly blocked access, preventing a major data breach that could have exposed thousands of customer records.
Small Business Recovers from Ransomware Attack
An SMB hit by ransomware could recover its data instantly because its IT Company had regular cloud backups and a disaster recovery plan in place. No ransom was paid, and downtime was minimal.
Healthcare Firm Meets Compliance
A healthcare startup needed to meet HIPAA standards. With the help of an experienced IT firm, they implemented end-to-end encryption, staff training, and secure cloud infrastructure, passing audits without issue.
What to Look for in an IT Company for Cybersecurity
If you’re ready to partner with an IT Services Company, here are a few key qualities to consider:
Proven experience in cybersecurity
24/7 support and monitoring
Customized solutions tailored to your business
Strong references and client testimonials
Transparent pricing and SLAs
Choosing the right IT company is not just a technical decision—it’s a strategic investment in your company’s future.
Final Thoughts
Cyber threats are growing in volume and sophistication. Relying on luck or outdated systems is a recipe for disaster. By partnering with a trusted IT Services Company, you gain the tools, expertise, and support needed to protect your business in today’s digital world.
Whether you're a startup, SME, or enterprise, an experienced IT Company acts as your shield against the dark forces of cybercrime, so you can operate with confidence, agility, and peace of mind.
0 notes