#CPX
Text

semaninha no last fm colegas
#last fm#week on last fm#tv girl#charli xcx#sabrina carpenter#tim maia#chappell roan#sky ferreira#carlos do complexo#cpx#slipknot#marina sena#megan thee stallion#slipmami#melody#natthazinho#pabllo vittar#sevdaliza#lisa#rosalia#blackpink#blackpink lisa#bella thorne#raça negra#eu abri o twitter pra postar mas esqueci que caiu#twitter#twitter brasil#twitter br#topster#weekster
31 notes
·
View notes
Text
Foot on the Ground Team ⛳


27 notes
·
View notes
Text
Secure out-of-band console and power management for Check Point security gateways - CyberTalk
New Post has been published on https://thedigitalinsider.com/secure-out-of-band-console-and-power-management-for-check-point-security-gateways-cybertalk/
Secure out-of-band console and power management for Check Point security gateways - CyberTalk
Contributed by WTI as part of Check Point’s CPX silver-level partner sponsorship opportunity. WTI is an industry leader in out-of-band network management.
Nobody has time to drive to a site when an ISP drops service or you simply need to reconfigure and/or reboot a switch, router or firewall. Your time is too valuable not to have an out-of-band solution in place. WTI out-of-band solutions comes with a cellular connect and fallback option that gives you secure remote access to console ports as well as control of individual power outlets when your network services are disrupted.
WTI out-of-band management solutions
WTI engineers and manufactures secure out-of-band management solutions for local and globally deployed networks. WTI out-of-band products are designed to ensure uninterrupted access to network devices and services by providing solutions to quickly and effectively respond to problems at distant or hard to reach equipment sites. When a router, switch or security appliance becomes inaccessible and interrupts network services, WTI out-of-band solutions provide redundant, remote console port management and power switching/reboot control to regain access and restore services in mission critical applications.
Even when the network is down, WTI out-of-band console server solutions can provide secure connectivity over primary and secondary ethernet and cellular LTE connections, allowing remote access to console ports and power control functions.
In addition, WTI DevOps allows administrators to configure, deploy and orchestrate WTI out-of-band management solutions across your entire network for automated provisioning, monitoring and disaster recovery of critical infrastructure. Features such as RESTful API, Ansible Playbooks and Python Scripting are supported.
Check Point Software Technologies and WTI
WTI offers a comprehensive out-of-band management strategy for Check Point Security Gateways, allowing your NOC to deal with equipment outages and resulting interruptions of network communication without the need to dispatch support teams to remote branch offices and data centers.
During network outages, WTI’s console server products allow you to establish remote out-of-band connections to console ports on security gateways via secure, authenticated communication protocols. If a reboot is needed, WTI Switched PDU products can provide remote out-of-band access to power switching functions at distant equipment sites. WTI also offers a combination console server plus switched PDU unit for applications that require both out-of-band console access and power reboot control.
WTI out-of-band centralized management provides access and control for all of your network devices, allowing for console data from multiple Check Point devices spread over a global network to be monitored, logged and available to administrators, simplifying the challenge of managing a large number of remote devices while minimizing resources.
With multiple connectivity options, WTI console servers including 4G LTE and/or dual Gigabit Ethernet ports can provide secure access to advanced DNS functions when primary and/or secondary ISP connections are switched or disconnected. WTI’s dual ethernet console servers allow you to remotely configure primary and secondary DNS settings and set up IP tables to maximize availability of security gateways during network outages, ensuring seamless transfers between primary and secondary ISPs. The optional 4G LTE internal modem provides a secure additional alternate path for out-of-band connectivity using security protocols such as IPSec and OpenVPN.
About WTI
WTI designs and manufactures Secure Out-of-Band Management Solutions for local and globally deployed networks. WTI provides redundant OOB console access and power control to mission critical infrastructure … even when the network is down. WTI products can be purchased factory direct and through various channel partners worldwide. Since 1964, WTI has maintained local in-house manufacturing, engineering and technical support. Learn more at www.wti.com.
About Check Point Software Technologies, Ltd.
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading AI-powered, cloud-delivered cyber security platform provider protecting over 100,000 organizations worldwide. Check Point leverages the power of AI everywhere to enhance cyber security efficiency and accuracy through its Infinity Platform, with industry-leading catch rates enabling proactive threat anticipation and smarter, faster response times. The comprehensive platform includes cloud-delivered technologies consisting of Check Point Harmony to secure the workspace, Check Point CloudGuard to secure the cloud, Check Point Quantum to secure the network, and Check Point Infinity Core Services for collaborative security operations and services.
WTI out-of-band management solutions provide Check Point security gateways with:
In-band and out-of-band console access from anywhere.
Remotely reconfigure, revive and restore gateways via SSH.
Connect via ethernet or cellular 4G LTE with optional failover.
Power cycle and monitoring capabilities.
Faster network issue resolution.
Application example
Challenge: Provide secure, authenticated access to configuration parameters on console ports on Check Point security gateways during outages.
Answer: WTI console servers with dual gig ethernet ports ensure secure console port connections via primary and secondary ethernet as well as OOB access via optional LTE cellular modem.
Results: If the primary in-band network fails, admins can initiate secure SSH connections to security gateway console ports via out-of-band, allowing access to configuration parameters and other data used to troubleshoot unresponsive devices and revive network services.
In conclusion, WTI out-of-band management solutions empower your team to regain control quickly and reduce network disruptions. Are you ready to save time, energy and resources? Let’s discuss how WTI can help!
#000#4g#ai#AI-powered#ansible#API#applications#challenge#channel#Channel partners#Check Point#Check Point Software#Cloud#cloud-delivered#CloudGuard#collaborative#communication#comprehensive#connectivity#CPX#critical infrastructure#cyber#cyber security#data#Data Centers#deal#devices#Devops#disaster recovery#DNS
0 notes
Video
youtube
GABIGOL TENTOU M4TAR O RED NA FAVELA E SE DEU MAL | GTA RP
0 notes
Text
TikTok: @christopherpaulx_
0 notes
Text
CPX
Mansour Althani, CEO and Co-founder of CPX, CPX is dedicated to offering the latest advancements in affiliate marketing technology to its clients. With a focus on helping organizations achieve their marketing goals quickly and
1 note
·
View note
Photo

O tempo é nosso amigo... Só ele é capaz de mostrar o oculto... . . . #life #vida #negra #taticharmosinha #mulheresempoderadas #monitoradapordeus24hrspordia #mulheresempreendedoras #saogoncalogram #sdvsaogoncalo #saogoncalo #niteroigram #sdvniteroi #niteroi #black #cpx (em Brazil) https://www.instagram.com/p/CnLVGFkuwER/?igshid=NGJjMDIxMWI=
#life#vida#negra#taticharmosinha#mulheresempoderadas#monitoradapordeus24hrspordia#mulheresempreendedoras#saogoncalogram#sdvsaogoncalo#saogoncalo#niteroigram#sdvniteroi#niteroi#black#cpx
0 notes
Text
Ódio do bem: “Você é podre”, ataca âncora da GloboNews contra Rodrigo Constantino
Ódio do bem: “Você é podre”, ataca âncora da GloboNews contra Rodrigo Constantino
O comentarista político Rodrigo Constantino criticou a jornalista Leilane Neubarth após ela publicar uma foto de seu neto, de apenas 7 anos, usando um boné com a sigla CPX, igual ao utilizado por Lula (PT), em evento de campanha no Complexo do Alemão, no Rio de Janeiro.
“Esquerdista caviar irresponsável que não mede esforços para lacrar”, escreveu Constantino em resposta à publicação de…

View On WordPress
1 note
·
View note
Photo

CPX na selfie… #selfie #self #cpx #cpxdoalemão ©Magnesio 2022. Fotografias protegidas pela Lei de Direitos Autorais - Lei nº 9.610. (em São Paulo, Brazil) https://www.instagram.com/p/Ck8taw6Ojdg/?igshid=NGJjMDIxMWI=
0 notes
Text
The Story of the Menominee River Sugar Company 1903-1955
The Story of the Menominee River Sugar Company 1903-1955
Menominee, Michigan, situated far from the world’s financial centers a hundred years ago, much as it is today, nevertheless placed itself directly in the middle of one of the hottest business booms of the early twentieth century – sugar. The small community that dared to plant a footprint in world commerce occupies a slivered point of land that dips into Lake Michigan at a point so close in…
View On WordPress
#alex jones the one show#alex jones wife#beatrice egli#beatrice egli 2022#beatrice egli freund#cachorro#cpi data release today#cpi report#cpx#gaspar rivas#gato#muharem huskovic#oostende#river plate#tottenham vs eintracht frankfurt#universidad de chile vs
0 notes
Text

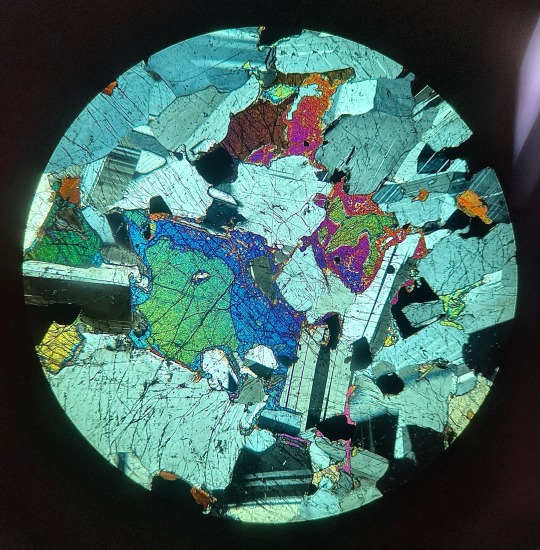
the sample vs the thin section
#prob my fave from my current lab <3 clinopyroxene [diopside] my beloved#cpx and plag r my faves#geology#sherrie’s shit#science with sherrie
118 notes
·
View notes
Text
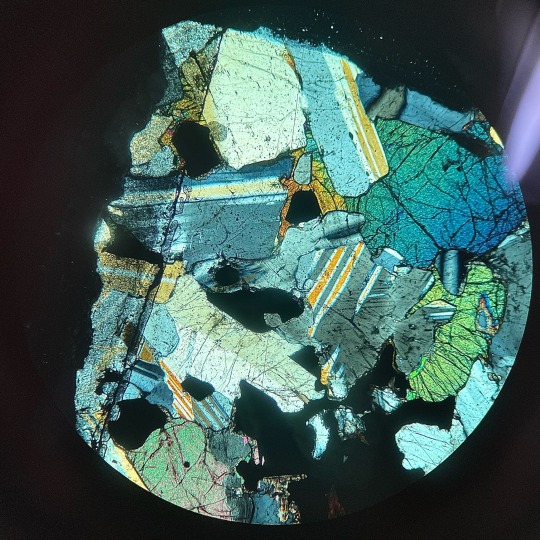
And how is the diabase holding up against hydrothermal alteration?


To shreds, you say?
#geology#in which cube is a geologist#this is a diabase#it should have nice plag and cpx crystals in there along with the amphiboles and the opaques#but nah#the water eated it#top is cross polar#bottom is plane
9 notes
·
View notes
Text
Mastering the CISO role: Navigating the leadership landscape - CyberTalk
New Post has been published on https://thedigitalinsider.com/mastering-the-ciso-role-navigating-the-leadership-landscape-cybertalk/
Mastering the CISO role: Navigating the leadership landscape - CyberTalk


Cindi Carter, Field CISO West at Check Point, and Pete Nicoletti, Field CISO East at Check Point, recently advanced the following discussion at Check Point’s flagship event, CPX 2024.
The evolving CISO role is an important and interesting topic in cyber security, which is why we’re empowering you with foundational, value-driven perspectives here. Elevate your cyber security organization with first-hand guidance from those at the forefront of innovation and excellence.
In an age of digital transformation, the role of the Chief Information Security Officer (CISO) has undergone and is still undergoing a profound evolution. No longer confined to technical risk mitigation, today’s CISOs must be strategic business partners, skilled communicators, and catalysts of cultural change within their organizations.
A recent industry panel at the influential CPX 2024 conference in Las Vegas shed light on the shifting demands facing security leaders. As Dan Creed, CISO at Allegiant Travel Company, stated, “Ask SolarWinds what the consequences are…” for CISOs who fail to effectively communicate security priorities to the broader business.
The expanding attack surface
The root of this challenge lies in the expanding attack surface brought about by digital transformation. While past breaches often stemmed from vulnerabilities in corporate infrastructure, the greatest risks now emanate from employee devices and cloud-based services. As IT has transitioned from a cost center to a revenue driver, CISOs must integrate with lines of business and advise on strategic decisions.
IDC’s survey of 847 cyber security leaders reflects this shift, with only 12% citing technical skills as the most important CISO attribute. Instead, respondents highlighted leadership, team-building, and business management as the critical competencies.
“The consequence of not establishing those relationships [is] you get a culture at the company of ‘Well, it’s not my responsibility,’” one CISO warned, echoing the experiences of organizations like SolarWinds and MGM, where security lapses occurred due to a lack of security awareness and ownership among employees.
Fostering a security-aware culture
Successful CISOs are addressing the security awareness challenge by adopting a more user-centric approach, making security transparent and easy to use. As Pete Nicoletti, Field CISO at Check Point, explained, “Security should lubricate business and make it faster.” This could mean streamlining cumbersome VPN processes or transitioning to passwordless authentication.
Some CISOs are even experimenting with financial incentives, tying security culture metrics to bonus pools. “If your department does better, it increases your bonus pool above the norm […] and if you don’t, then it hits your bonus.”
Cultivating C-suite partnerships
CISOs must also cultivate stronger partnerships with their C-suite counterparts. IDC’s survey revealed discrepancies in how CISOs and CIOs perceive the CISO’s role, underscoring the need for better alignment.
Creed recounted a recent example where the Allegiant Travel board made decisions about connected aircraft without involving the CISO, leading to a last-minute “fire drill” to address cyber security requirements. “Do you think the board, when they first started talking of going down this path of ‘we’re going to expand the fleet’, considered that there might be security implications in that?” he asked.
Educating executives on security risks
To bridge this gap, CISOs must proactively educate executives on the business implications of security risks and advocate for a seat at the strategic decision-making table. As Russ Trainor, Senior Vice President of IT at the Denver Broncos, suggested, “Sometimes I’ll forward news of the breaches over to my CFO: here’s how much data was exfiltrated, here’s how much we think it cost. Those things tend to hit home.”
The evolving CISO role demands a delicate balance of technical expertise, business acumen, and communication prowess. CISOs who master these skills will not only mitigate cyber threats, but also position themselves as indispensable partners in driving their organizations’ digital transformation and growth.
“A lot of CISOs are rather gun-shy; hesitant to talk to the business about cyber security. Do better in trying to foster that human connection,” says CISO Cindi Carter.
For more insights like this, please see CyberTalk.org’s past coverage. Lastly, to receive cutting-edge cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2024#aircraft#analyses#approach#Attack surface#authentication#awareness#board#bridge#Building#Business#business management#C-suite#catalysts#CFO#challenge#change#Check Point#chief information security officer#cios#CISO#CISO role#CISOs#Cloud#communication#conference#CPX#cutting#cyber#cyber attack
0 notes
Video
youtube
REAÇÃO DO PAULINHO O LOKO COM NOVO LÍDER DO ILEGAL | GTA RP
0 notes

