#Choosing the Right VPN Service for Your Needs
Text
Guide to Watch TGCF Donghua Season 2

With the new season of the Tian Guan Ci Fu/Heaven Official's Blessing donghua finally releasing soon, I wanted to make a post explaining the different ways fans can watch and support it! Things have changed since season 1, so my old guide is no longer relevant apart from the infographics on how to subscribe to Bilibili CN (and the YouTube channel)!
And to be upfront: the main sites that are going to be broadcasting the donghua have been very sparse with information. I fully expect that we will have to wait until after the first episode releases to know all the details, so while I am making this guide to help people right now, things might change! Please keep that in mind and stay patient! I will post any important updates in the replies as I can!
Additionally, because of copyright/licensing, different sites are going to work in different regions. I do not know with 100% certainty what is going to work in a particular country. There's gonna be some trial and error!
So the main options we have for season 2 are:
Crunchyroll
Sub price: $9.99 USD per month for basic (local prices may vary)
Regions: Americas, Europe, Africa, Middle East, Oceania.
Pros: Easy to subscribe to if available in your region.
Cons: Unlikely for true simulcast so it'll be a bit delayed.
Link to main site (season 2 listing not up yet)
For app: download via App Store/Google Play Store.
Bilibili. tv (EN site/app)
Sub price: $4.99 USD per month (local prices may vary)
Regions: Southeast Asia only.
Pros: Airs earlier than Crunchyroll. Interface is in English.
Cons: If you want to watch it outside of SEA, you'll need a VPN.
Link to Season 2 on website
For app: download via APK link on website if you are outside of SEA. Otherwise use App Store/Google Play Store.
Bilibili YouTube Channel
Sub price: $4.99/$5.99 USD per month (local prices may vary)
Regions: Many -- EXCEPT Japan, South Korea, the Americas, UK, Australia, New Zealand.
Pros: Easy to subscribe if available in your region.
Cons: If you want to watch it from the regions listed above, you'll need a VPN.
Link to channel
It's the youtube app....
Bilibili. com (CN site/app)
Sub price: $9.99 USD for 3 months
Regions: ¯\_(ツ)_/¯
Pros: If they're gonna air season 2, then they might be the source broadcast if the EN site isn't. Also probably cheapest for those abroad.
Cons: Chinese interface may be intimidating. Not 100% sure if it'll air as normal.
Link to Season 2 on website
For app: download via App Store/Google Play Store.
(NOTE: If you are in Japan, it will be available on WOWOW. If you are in South Korea, it will be available on Laftel.)
F.A.Q.s
🔹What is the release date/time?
Bilibili EN has announced it as 20:00 GMT+8 on October 18th. If it releases on Bilibili CN, it'll probably be the same time.
Crunchyroll has stated October 18th, but has not yet announced a time as of the posting this guide. I checked.
Japan and South Korea have their own release times, so please consult the relevant broadcasters!
🔹Can I watch it on Netflix/Amazon Prime/etc?
These streaming services will likely only have it after the whole season concludes, and with a significant delay. For reference, it took several months after finishing for season 1 to be released on Netflix.
🔹Which platform should I choose?
Whichever one you can actually access, and feel most comfortable using!
🔹When should I subscribe?
Personally, I'll be waiting until the last day before release, just to make sure I have the most information possible. However, I'm sure the idea of doing that makes many people nervous, so... yeah. Whenever is convenient for you!
🔹Which one will have the donghua the quickest/earliest?
Probably Bilibili CN & Bilibili EN. I suspect they'll simulcast with each other. I cannot be 100% certain about anything though, because of limited info! For season 1, YouTube and Funimation (now Crunchyroll) were delayed, and it's hard to say if they'll be better this time or not.
🔹Do I need a VPN for Bilibili EN or their YT channel?
If you are outside of SEA, yes.
🔹Do I need a VPN for Bilibili CN?
Probably not, unless you are in a country that restricts access to CN sites and apps (like India).
🔹Which VPN should I use?
This will be up to you! It's best to research what the different options are, and what will work for your needs!
🔹How will I know I'll be able to watch season 2 from my region?
The most surefire way is to subscribe to a platform that has officially announced to be serving your region (e.g. Crunchyroll for the Americas).
Unofficially, if you can watch the latest trailer and other promo videos on your chosen platform, then there's a good chance you're okay! The exception to this is the YouTube channel, which has some of the trailers public, but has all of season 1 unavailable if you aren't in the right region....
Additionally, be mindful, because even if you're able to see season 1, season 2 might still be region-locked on certain platforms. (E.g. you can watch all of season 1 via Bilibili EN if you're from the USA no problem. But you can't access season 2 without a VPN to a SEA server.)
🔹What languages are going to be available and will there be English subtitles?
While dubs for multiple languages have been confirmed, I'm unsure if any of these will be available on release. It'll likely be offered only in Chinese first.
For season 1, there were hardcoded CN & EN subtitles for Bilibili on release. Funimation re-subbed the episodes (EN) for their own release, and Crunchyroll will probably do the same.
🔹I watched it on Funimation last time, can I watch it through them this time?
No, they were absorbed (in some capacity idk) by Crunchyroll. So they are not distributing season 2 of TGCF, only Crunchyroll is.
🔹Is season 2 actually available in China and thus on Bilibili CN?
Yes and no! As long as you are not in mainland China, it seems you will have access to season 2 through Bilibili CN. All promo materials and trailers seem to be available to us, which is a good sign! (They are not available for mainlanders, but mainland fans are able to watch via HK/Macau versions apparently.)
🔹Hopeful that it will be available, I would like to watch it via Bilibili CN, so how do I sign up and subscribe?
To make an account, consult this reddit post. To subscribe, please consult the guide below! It's a little old (made it for season 1) but still works pretty much the same.
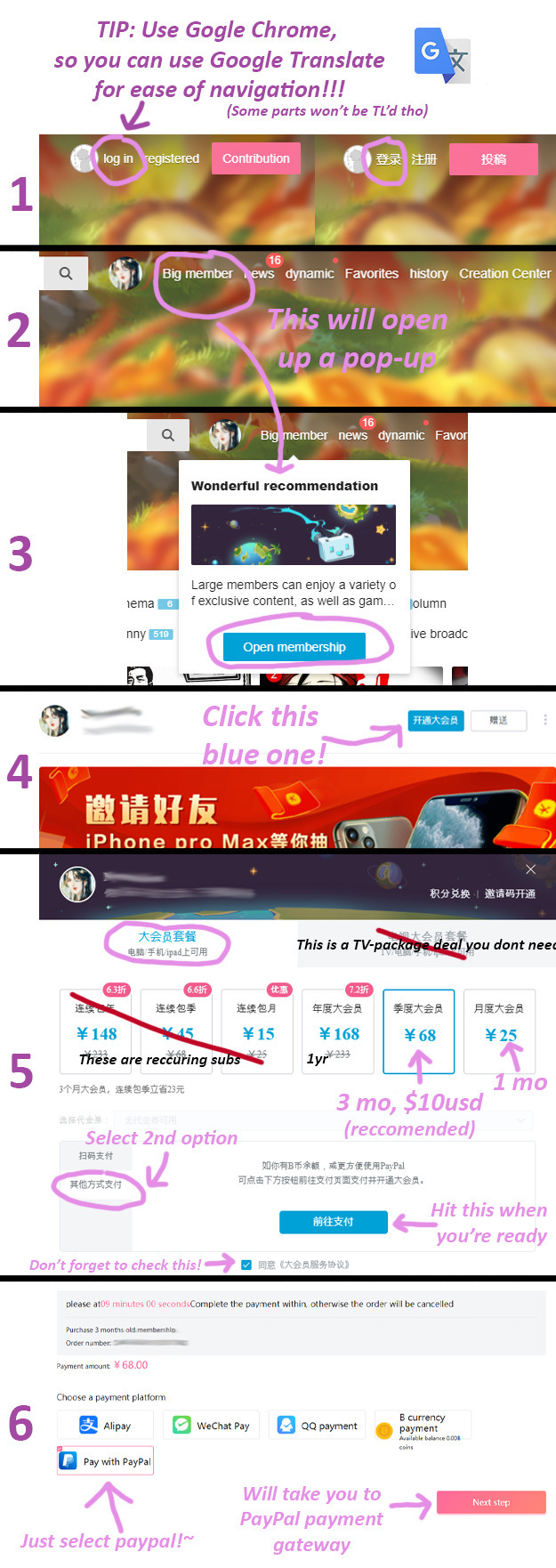
#tgcf#tian guan ci fu#hob#heaven official's blessing#tgcf donghua#guide#nyerus.txt#i know the moment i post this there will be new info that comes out#but such is the risk i take posting this on a sunday as opposed to monday#tomorrow i will have no time tho lol#CR please release a time.....
504 notes
·
View notes
Text
“I’m scared to pirate stuff - ” do it scared!*
*with Firefox and Adblock and a VPN and -
If you want a nonspecific, nonexhaustive “where do I even start” guide…
Sail the cyber seas at your own risk!
Streaming - “I want to watch xyz”
This is normally what most people want when they talk about pirating.
Use Firefox with uBlock Origin and additional privacy add-ons such as PrivacyBadger, TrackMeNot, etc.
Free VPNs are out there. Get one - but vet it’s efficacy. My go-tos are Proton VPN, or Windscribe if you plan to do a bit of torrenting.
What is torrenting? How does it work? Here’s a guide!
Back to streaming -
Make sure that a) you’ve got your Mozilla browser with all its adblocking private glory, and b) you’ve got a VPN turned on to hide what you’re doing in that browser from your ISP (internet service provider).
Now you need to actually find a site to stream from. This is the tricky part, because openly sharing these sites will get them taken down if they’re talked about widely enough. (Remember how tiktok idiots got zlibrary taken down?)
You’re going to have to talk to people on forums. You’re going to have to experiment with sites you find yourself. Search for ‘x online free’ and look at the links that come up - is the preview text mangled or clickbaitey? Are there Reddit threads about that website confirming or denying its content? A good rule of thumb is to ignore the top result or two - copycats of good streaming sites will often buy out the top result spot. Eventually, you’ll develop a good gut feeling and understanding of what a good site ‘looks like’ from the results page alone.
However, there are some places that compile good sites that haven’t been nuked by lawyers (yet) - check out r/FMHY! The masterposts are actively curated and updated when a site goes down or is found to have malicious downloads.
Remember - loose lips sink ships. No tweeting (xeeting?) or Facebook statuses about your new favorite piracy website and where you found it. Even posting to tumblr (kind of like this…) isn’t a great idea if you want those websites to stay under the radar and stay accessible. Nobody talks, everybody walks (away with their share of pirate booty)
If you aren’t downloading media, pick pretty much any site and watch away! Adblock and Firefox will keep away pop-ups and other annoying ads, and your VPN means your ISP can’t tell that you’re visiting an unofficial streaming service.
Note: In my experience, I’ve never heard of visiting a site and watching stuff on it infecting or otherwise compromising your computer. That tends to come from misclicks on invisible or overwhelming pop-up ads that redirect you to an automatic download or similarly malicious bullshit. If you’re using Firefox and uBlock, you shouldn’t be in any danger of an accidental redirect.
Downloads - “I want to keep xyz”
This is the realm of pirate archiving - you’re keeping files physically on your hard drive, an external hard drive, or burning a disk.
Adblock + Firefox browser? Check. VPN on? Check.
Go to your streaming site of choice - most if not all have download options. You can download those files or, manually, right click and save the video file from the webpage as an mp4. I honestly don’t know if there’s a difference in quality or more danger in clicking the download buttons, but regardless -
Run that puppy through VirusTotal.com! It’s a reliable browser based virus checker - if the file is too large, use a local virus checking program (your native Windows Defender on Windows computers or, I prefer, Malwarebytes)
Generally mp4 and mp3 files are clean - choose where to save them for the long term, and bam! Free forever media.
Optionally, I also upload mp4 files to a named Google document - this way I can easily share them or make them findable through a ‘xyz Google doc’ search for others :]
Torrents - “I want to keep and share xyz”
I’m not going to go into this subject in depth because, honestly, it’s not something I do regularly.
See the previously linked Torrenting guide for information on how the process works, and check out r/FMHY for recommendations and warnings about different torrenting clients (I’ve personally only used qBittorrent - I’ve heard to stay away from the Pirate Bay and Bittorrent.)
As with streaming, turn on that VPN baby! You’re going to need one that supports peer-to-peer (p2p) connections, so Proton’s free version is a no-go. Windscribe is what I’ve used for torrenting (and it’s a good free VPN on its own - I’m just partial to Proton). You get 10GB every month on Windscribe’s free version, which is more than enough for a few movies/a season or two of your favorite show.
(Bigger torrents like video games are easily 30+ GB, so be prepared to either pay for a no-limit premium account or spend a few months downloading your files in chunks.)
VPN on? Double check.
Boot up your torrenting client - I use a slightly out of date version of qBittorent, but there are other options. The Reddit thread and previously linked torrenting guide have a few dos and donts of selecting a client, so be thorough before you download your client of choice.
This is getting into the logistics of torrenting a bit, so forgive me if this is vague or incorrect, but now you need a torrent seed. These will be .tor files found through pirating websites or archives - these are rarely malicious, but it’s good to run any piracy related download through something like VirusTotal.com or scan it with a local program like Malwarebytes.
You open your seed file in your client and wait. A ‘healthy’ seed tends to have lots of seeders and few leeches, but sometimes you’re stuck with an obscure seed you just have to wait for.
Your torrented files have fully downloaded! Now what? a) keep your client open and seed those files for others as long as you want to - sharing is caring! and b) run those files through a security program like Malwarebytes (not sponsored it’s just the only program I’m familiar with).
Be wary of what gets flagged - sometimes the files seem important, but are just trojans, and likewise sometimes they seem malicious, but are just cracked software getting flagged by your system. It’s good to check and see if others have had a problem with this particular torrent before - Reddit threads from 2008 are your long dead friends.
And that’s about it. Feel free to correct me if anything I’ve recommended is malicious or outright wrong. I’ve been doing this for years and haven’t had an active problem to my knowledge, so if there is something fishy with how I do things, I am a statistical outlier and should not be counted.
I wish you smooth sailing and strong winds in your ventures me hearties!
Obligatory ‘don’t pirate small author’s or artist’s works what the fuck dude’ statement.
#ra speaks#piracy#pirating#pirate to make hondo ohnaka proud#I’ve seen so many people on my streaming piracy post bemoaning that they don’t know how like !!!!#congrats you get to learn without the middle school trial and error phase we zillenials had (RIP family computer 2004-2009)#I genuinely think piracy has gotten easier/safer than it used to be. that or I’ve gotten smarter. which is also likely.
365 notes
·
View notes
Text
Privacy is in a terrible situation right now.
Especially on the internet. You know, Google, Facebook, Microsoft, Twitter(X), Apple, and even Tumblr all collect information about you to show you scarily accurate advertisements among other things.
Why does this matter?
This isn't about hiding information, it's about protecting information. You wouldn't let me know your entire life, your diary, all your photos and text messages, so why do you let random companies do the same?
Privacy Guides - Why Privacy Matters
So how do you stop this?
You can't. But you can lessen this. So I'm going to show you a non-exhaustive list of what I've used and what I know of that may help your privacy. I would recommend you go to privacyguides.org after if you want a better explanation. I'm just here to show you cool things.
Disclaimer
I am not a library on this sort of information and this is what I choose to use. I may be incorrect and you may have differing opinions. Also, this may be too extreme for everybody. Use what works for you. Again, I would recommend you go to privacyguides.org after you read this for a more in-depth and better explanation.
VPNs
You know what a VPN is. You've seen the sponsorships. VPNs are one of the most popular privacy tools, but know that they are not the only tool that you'd need. This list is evidence of that.
I would recommend Proton VPN, Mullvad, and IVPN for most users, as they provide a far better amount of privacy and features than VPNs such as Nord VPN, Surfshark, and Express VPN. If you really want unlimited devices go with Windscribe.
I personally use Proton VPN due to the fact that I use their other services.
Browsers
You should probably know that Google Chrome is basically spyware at this point. The issue here is, almost all Chromium-based browsers are. These include, Edge, Opera, and Vivaldi. The only real exception would be Brave, but they've got leadership issues, which may not be a deal breaker for you.
So what do you use? A Firefox-based browser. This obviously includes Firefox, but most Firefox-based browsers are privacy-focused. The browsers that I recommend are Firefox, Librewolf, the Mullvad Browser, Waterfox, and Brave.
There is also the Tor Browser, but that is a whole 'nother can of worms that I will not go into. All I will say is that if you are in a high-risk environment(such as an oppressive regime) or you need absolutely no one to know that you searched that one thing, you may want to use the browser for anonymity.
I use Firefox as my main browser, with Brave as the browser that I use if something doesn't work on Firefox. I also use Tor if it is a high-risk situation.
Search Engines
Google, Bing, and Yahoo! all log your searches, you need alternatives. This is relatively straight-forward.
I recommend, Qwant, DuckDuckGo, SearXNG, Brave Search, and Startpage. Both Qwant and DuckDuckGo are fairly similar as they both use Bing search results and say that they don't track you. SearXNG is more complex, and I will not go into detail here. If you really want Google search results, use Startpage. And if you don't want your search to rely on Bing or Google, use Brave Search.
I use Qwant, mainly just cause its European.
Passwords
Passwords are the keys to your digital life. And most of the time they're not that great. You know the drill here, make passwords like this- XmaE7PEj2hq9ed$w - but you can't really remember them. For that you need a password manager.
I recommend Bitwarden, Proton Pass, and KeepassXC. Bitwarden and Proton Pass are more convenient, but you are trusting a single entity, reputable ones, but still. KeepassXC isn't as convienent, but you have near full control over what happens to it.
I use Proton Pass, as I use other Proton services.
Email
Email is identity, you almost always use your email in order to register for sites like Tumblr, and sites that aren't anything like Tumblr. Companies like Google, Microsoft, and Yahoo! all use your email inbox in order to gain more information about you for their companies. There are quite a few email providers, but I've only used and recommend two.
I recommend Proton Mail and Tuta Mail. Both are good email providers, although Proton would be better if you use other Proton services, like I do.
I use both Proton Mail and Tuta Mail for separate email addresses.
Aliases
Email Aliases are also very important for private email. Your email is your name, if you want to private, you'd go under pseudonyms. That's what email aliases are.
I recommend and have used Simplelogin and Firefox Relay. Email providers like Proton and Tuta also give you aliases when you pay. I don't know how well these work, but I assume that they work the Same as Simplelogin and Firefox Relay.
I use Simplelogin.
Devices/OSes
Phones
Now let's turn up the extremity to 11 as we look at your devices. Phone-wise, avoid Apple, they say that they care about your privacy, but they don't. Apple is better than Google, but I'd only recommend using an iPhone if you already have one, and it still has support left. If that's the case, then follow privacy guides like this one by Techlore(His channel is also really great for privacy guides). You should probably use a Google Pixel. Sounds weird as it's owned by GOOGLE, one of the companies that we don't want to be tracked by, but if we go with the Pixels we can use custom ROMs.
Most ROMs exist for your privacy, they are based on the Android Open Source Project(AOSP) which means they can run most of your favourite Android apps without messing them up with Google. In order to run most of your apps however, you're going to need some way of running Google Play Services. This is a backbone black-box that Google forces most of your apps to use in order to function. CalyxOS and LineageOS with MicroG both have MicroG, an open source implementation of Google Play Services. GrapheneOS just straight up uses Google Play Services but sandboxes it so that it can't get its tentacles all up in your phone.
I recommend going like this:
You have a modern-ish Google Pixel phone, go with GrapheneOS.
You don't have a Google Pixel, but your phone is still supported by CalyxOS, go with CalyxOS.
Your phone isn't supported by either of these but still is supported by LineageOS with MicroG, go with LineageOS.
Your phone isn't supported by any of these, you can do as much degoogling as you can.
Techlore also has a fantastic guide on Android Privacy.
Desktops/Laptops
Apple isn't actually that bad here, its better than Windows at least. But Linux is KING when it comes to privacy and security. There is definitely a learning curve here. Pin the terminal, you're going to use it a LOT. Also be aware that on Linux you won't have every single app that you're used to. If you don't really want that hassle, just go with Mac.
Linux distros that I recommend(for beginners) are: Ubuntu, Linux Mint, Pop!_OS, and Elementary OS.
I use Ubuntu as it's the only one that I could get working on my computer.
Other Pieces of Advice
Use an Ad-blocker! Ads are terrible for privacy as companies can get their trackers in completely unrelated sites via their ads. I use and recommend uBlock Origin.
Don't use any personally identifying information online. Don't use your real name, a picture of you, your voice. The less you give to the internet, the more private you are.
Mix and Match! Explore what works for you. You might be okay with changing OSes but you might be a bit too reliant on GMail. That's fine! Just use what works.
Again, please go to privacyguides.org after this. This did not even scratch the surface but I hope this was useful to you in some way.
#original#internet privacy#internet#google#microsoft#facebook#meta#twitter#privacy#search engines#browsers#duckduckgo#linux#adblocking#adblock#vpn#proton#simplelogin#tuta#tutanota#apple#hope this helped!
64 notes
·
View notes
Text
Understanding Multi-Factor Authentication (MFA)
In today’s digital landscape, securing online accounts and sensitive data is more critical than ever. One effective way to enhance security is through Multi-Factor Authentication (MFA). MFA adds an extra layer of protection beyond just a password, significantly reducing the risk of unauthorized access.
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) is a security mechanism that requires users to provide two or more verification factors to gain access to a resource, such as an application, online account, or VPN. Instead of relying solely on a password, MFA combines multiple independent credentials: what the user knows (password), what the user has (security token), and what the user is (biometric verification).
Why is MFA Important?
Enhanced Security: Passwords alone are not enough to protect against sophisticated cyber threats. MFA ensures that even if a password is compromised, unauthorized access is still prevented by the additional authentication steps.
Compliance: Many regulatory standards and frameworks, such as GDPR, HIPAA, and PCI-DSS, require the implementation of MFA to safeguard sensitive data and ensure compliance.
Reduced Risk of Breaches: By adding extra verification layers, MFA decreases the likelihood of data breaches and account takeovers, protecting both users and organizations.
Improved User Confidence: Users feel more secure knowing that their accounts and data are protected by multiple layers of security, fostering trust in digital services.
How Does MFA Work?
MFA typically involves a combination of the following factors:
Something You Know: This includes passwords or PINs.
Something You Have: This could be a physical device like a smartphone, a security token, or a smart card.
Something You Are: Biometric verification methods such as fingerprints, facial recognition, or voice recognition.
Leading MFA Software in 2024
With numerous MFA solutions available, choosing the right one can be challenging. Here are some leading MFA software options for 2024:
Duo Security: Known for its user-friendly interface and strong security features, Duo Security offers seamless integration with various applications and systems. It provides push notifications, SMS passcodes, and biometric verification.
Microsoft Authenticator: This app integrates smoothly with Microsoft’s suite of products and services. It supports push notifications, time-based one-time passwords (TOTP), and biometric authentication.
Okta: Okta’s MFA solution is highly versatile, supporting various authentication methods including SMS, email, voice call, and push notifications. Its adaptive MFA uses machine learning to analyze user behavior and enhance security.
Infisign: Infisign is a cloud-based MFA software offering a user-friendly interface and diverse authentication methods, including push notifications, one-time passwords (OTP) via SMS or mobile app, and security keys.
Choosing the Right MFA Solution
When selecting an MFA solution, consider the following factors:
Ease of Use: The solution should be easy for users to adopt and use regularly.
Integration: Ensure it integrates well with your existing systems and applications.
Scalability: The solution should be able to grow with your organization’s needs.
Support and Maintenance: Look for solutions with reliable customer support and regular updates.
Conclusion
Implementing Multi-Factor Authentication (MFA) is a crucial step in fortifying your security strategy. By combining multiple verification factors, MFA provides robust protection against unauthorized access and cyber threats. Whether you’re a small business or a large enterprise, selecting the right MFA solution can significantly enhance your security posture and provide peace of mind in the digital age.
2 notes
·
View notes
Text
Is it necessary to use game boosters?
As the network environment is getting better and better, the speed of the network is getting faster and faster, players have higher requirements for the experience of online games, which leads to the emergence of a lot of game accelerator software. In the face of so many accelerator products, for many people who have not used it, they really do not know how to choose. The product introduction is all about the advantages of their own accelerator products, and the online evaluation is uneven.
The main functions of game booster are:
Reduce the network delay of the game and stabilize the network speed.
Reduce the packet loss rate of the game.
Game booster software can be regarded as a desktop application, but it establishes a virtual gateway between the user and the server in the form of software. to put it simply, it will bypass the original unstable channel to reduce the delay and packet loss rate and provide a good game experience environment for gamers.
Therefore, the game vpn can not only accelerate the network speed but also improve the stability of the line and low packet loss rate. This is the main role of the network accelerator. As for whether some gamers want to use the network accelerator or not, it mainly depends on personal experience. Some gamers in coastal areas can log in normally without speed-up software, but most gamers, they need to use network accelerators. If you are playing the game in addition to other configurations and the network meets the requirements of the situation, there is a card screen, disconnected, you need to accelerate the speed-up software, if not card screen, the experience is good, then you can not use it.
Due to the inequality of network resources, there is a game accelerator. If the whole network is compared to a traffic route, it is just like the morning rush hour, evening rush hour or road failure, and the network arrangement will be unequal. For example, there are differences in the arrangement of network lines and routing resources, such as interception (inaccessible), congestion and so on.
So what role does the game vpn play in this? It is similar to our GPS navigation and can help us choose the best "route". The accelerator will send your game data to the server of the accelerator operator, and the data returned by the operator is the optimized direct connect route to solve the problems of delay, disconnection, and inaccessibility for us, so as to speed up the game.
In fact, the existence is reasonable, if the accelerator for the game network speed does not have the slightest effect, then there will not be so many teams and merchants continue to launch game accelerator software. In fact, playing national service is all right, and network problems are not likely to occur, but if you play foreign service, because most of the servers are abroad, with long distance and high delay, if you are naked, stutter, disconnection, delay and other network problems can be found everywhere. Therefore, a good game accelerator is of course necessary.
Therefore, if you want to have a better game experience, you also need to learn to choose a good game vpn. As for whether the effect of the accelerator is good or bad, it varies from person to person, just like buying clothes, everyone has different standards for "good". Generally speaking, you can choose formal, well-known ones, and the probability of payment is better than that of free ones.
2 notes
·
View notes
Text
dark web links
Dark Web Links List
A dark web links list can be an invaluable resource for those who want to keep their information secure. You’ll find everything from a variety of private email services and encryption tips to instructions for anonymous operating systems.
How to Access Dark Websites
The first thing you’ll need to access the dark web is a Tor browser. These browsers are anonymity-focused and allow users to surf the web from any location.
To use a Tor browser, download it from its official website and install it on your computer or phone. The installation process is quick and straightforward.
You can also install the browser in a Windows guest account if you don’t have one. The Tor network is a popular alternative to Google and offers users privacy protection with fast search results.
The Hidden Wiki is a great resource for finding onion URLs on the dark web. The site doesn’t discriminate between safe and dangerous content, so you might run into some unpleasant sites.
Numbers Station is another excellent resource for.onion URLs, despite its eerily empty design. It’s a fun, nightmarish place to surf the dark web, but be aware that it may not work for everyone.
Choosing the Right Dark Web Search Engine
Dark web searches are difficult, if not impossible, to do without some extra help. While many search engines can be helpful, they’re often overloaded with irrelevant and timed-out search results.
The best way to avoid this is to use a VPN. This will hide your real internet address while surfing dark web links and prevent hackers from stealing your data.
2 notes
·
View notes
Text
Best apk mirror for fire tv

#BEST APK MIRROR FOR FIRE TV HOW TO#
#BEST APK MIRROR FOR FIRE TV APK#
#BEST APK MIRROR FOR FIRE TV INSTALL#
#BEST APK MIRROR FOR FIRE TV GENERATOR#
Make sure both devices are connected to the same WiFi and are within roughly 30 feet of each other to ensure the best connection.
In most cases, mirroring to a Firestick can be set up in only a few minutes.
#BEST APK MIRROR FOR FIRE TV INSTALL#
While Android and Windows devices can mirror to Firestick right out of the box, you’ll have to install a third-party software in order to mirror from Apple devices.
With that in mind, we’re going to give you a quick guide to Fire Stick mirroring, so you can put content from your phone or laptop right onto your TV. However, sometimes the tiny screen on your portable electronics just can’t compare to watching something on a larger screen like a TV. Phones and laptops are amazing devices, and life today wouldn’t be the same without them.
#BEST APK MIRROR FOR FIRE TV HOW TO#
MP4 Repair: How to Fix Corrupted Video Files in 2019.
Best Choice Stellar Phoenix Data Recovery.
#BEST APK MIRROR FOR FIRE TV GENERATOR#
How to Create a Strong Password in 2022: Secure Password Generator & 6 Tips for Strong Passwords.How to Securely Store Passwords in 2022: Best Secure Password Storage.Best Password Manager for Small Business.How to Access the Deep Web and the Dark Net.Online Storage or Online Backup: What's The Difference?.Time Machine vs Arq vs Duplicati vs Cloudberry Backup.How to Install Firestick Apps from Amazon App Store? Top 30 Firestick Apps for Movies and TV Shows 2.4 Step 4: Open up your other Firestick apps and enjoy streaming without any risk +.2.3 Step 3: Choose the right server and turn the VPN on.2.2 Step 2: Download the ExpressVPN app to your Firestick devices.The Best Firestick App for Overall Safety If you’re looking for the real thing and want to find out how to get it, we’ve created an updated guide on how to install Sportz TV on Firestick in 2022.
#BEST APK MIRROR FOR FIRE TV APK#
Sportz TV is another great IPTV service for sports fans looking to stream all their favorite matches on their TVs – without actually having to sell the furniture to afford the subscriptions! However, many guides out there are still recommending the old APK (which no longer works) or are intentionally having readers download the wrong files.
Content Available: TV shows, Live Sports, Live TV.
Sportz TV Price: Starts at around $4 per month (for a 1-year subscription).
As the name suggests, Sportz TV prioritizes sports channels, with more than 500 channels dedicated just to sports worldwide. Sportz TV is an app you’re gonna love! Do you want to catch a football game in Venezuela then jump over to the UK for some rugby? You’ll never get bored, given the immense library of 13,000 global channels and over 25,000 VOD titles Sport TV has.
Content Available: Movies, TV shows, Games.
And then, of course, don’t forget to get yourself a Kodi VPN to guard your online privacy and security. If you haven’t downloaded Kodi on your Firestick yet, we’ve written a step-by-step tutorial here: How to Install Kodi on Firestick. Anyone looking for a reliable and always functionable entertainment platform needs to look no further. We think this makes Kodi a true ‘all-in’ app suitable for ALL tastes.įor this reason, it set itself apart as one of the best free home box office apps available for the Fire TV Stick (and Fire TV Stick 4K!). And if that wasn’t enough, Kidi even supports games. Apart from these, it has the PVR function, which allows you to record live TV and watch it at a later time. Kodi sah impressive music, movies, TV shows, and photo collections. It can do things you didn’t even know you might need. It is a free and accessible app with almost 900 addons. Kodi bills itself as ‘software built by the community for the community’.

5 notes
·
View notes
Text
Building a Successful IT Company in Nagpur: A Guide for Aspiring Entrepreneurs
Nagpur, often referred to as the "Orange City," is rapidly emerging as a hub for IT and software companies. With government initiatives like the Smart City project and its strategic location at the center of India, Nagpur has attracted attention from businesses looking to establish themselves in the tech industry. If you are planning to start an it company in nagpur, this article will guide you through the key factors that can help you build a successful venture.
1. The Growing IT Ecosystem in Nagpur
Nagpur has seen a steady rise in IT infrastructure over the past few years, making it a favourable location for tech startups and IT companies. The city’s well-connected transportation network, affordable real estate, and skilled workforce make it an attractive destination for entrepreneurs. Additionally, the Maharashtra government’s support for the IT sector through policies and incentives adds to the city's appeal.
Key benefits of starting an IT company in Nagpur:
Affordable cost of living and office space
Availability of skilled professionals from local engineering and technical institutes
Emerging IT parks and special economic zones (SEZs)
2. Selecting Your IT Niche
The IT industry offers a wide range of services, and it’s essential to choose a niche that aligns with your expertise and market demand. Some of the top services offered by IT companies include:
Software Development: Providing customised software solutions for businesses across various industries.
Web and Mobile App Development: Creating user-friendly websites and mobile applications to meet the growing demand for digital solutions.
IT Consulting and System Integration: Helping businesses optimise their IT infrastructure and integrate new technologies.
Cybersecurity Services: Offering solutions to protect businesses from cyber threats and data breaches.
Cloud Computing and Data Analytics: Assisting companies in adopting cloud technologies and making data-driven decisions.
Identifying a niche will help you position your company as an expert in that field, making it easier to attract clients in Nagpur and beyond.
3. Building a Strong Team
The success of your IT company will depend largely on the quality of your team. Fortunately, Nagpur has a growing pool of talented professionals who are well-versed in technology and software development. Hiring skilled employees with expertise in your chosen niche is crucial to delivering high-quality services.
Key positions to hire:
Software developers and engineers
Project managers and team leaders
UI/UX designers
Cybersecurity experts
IT consultants and business analysts
You can also consider collaborating with freelancers and consultants on a project basis, especially during the early stages of your company.
4. Setting Up Your IT Infrastructure
Having the right infrastructure is critical for an IT company. From hardware and software to networking solutions, setting up a robust IT infrastructure will allow your team to work efficiently and deliver projects on time.
Essential IT infrastructure needs:
High-speed internet connection and secure network setup
Cloud-based project management tools for collaboration
Development and testing tools for software and web application development
Cybersecurity measures like firewalls, VPNs, and encryption to protect sensitive data
Nagpur’s growing number of co-working spaces and IT parks, such as the MIHAN (Multi-modal International Cargo Hub and Airport at Nagpur) SEZ, offers excellent opportunities for startups to access state-of-the-art infrastructure.
5. Marketing Your IT Company
To establish your IT company in Nagpur, you need an effective marketing strategy that positions you as a leader in your niche. Building a strong online presence is vital in today’s digital world.
Digital marketing tactics:
Create a professional website that showcases your services, portfolio, and client testimonials.
Use SEO (Search Engine Optimization) strategies to rank higher in search results for relevant keywords.
Leverage social media platforms like LinkedIn and Twitter to network with potential clients and industry leaders.
Offer free resources like blogs, case studies, or webinars to demonstrate your expertise and attract new clients.
Local networking events, tech conferences, and business expos in Nagpur can also provide excellent opportunities for business development.
6. Securing Clients and Building a Portfolio
In the early stages, securing your first few clients can be challenging but essential for building a strong foundation. Offering competitive pricing, delivering high-quality services, and maintaining excellent communication can help you win trust and build long-term relationships.
Tips for attracting clients:
Offer discounted rates or free consultations to attract small and medium-sized businesses.
Build partnerships with other businesses in Nagpur to offer complementary services.
Use online platforms like Upwork or Freelancer to find remote clients in need of IT services.
As your business grows, showcasing a portfolio of successful projects and satisfied clients will be key to attracting larger contracts.
7. Keeping Up with Technological Advancements
The IT industry is constantly evolving, and staying up-to-date with the latest technologies and trends is crucial for your company's success. In Nagpur’s competitive market, offering cutting-edge solutions like AI, machine learning, blockchain, or IoT (Internet of Things) can set you apart from competitors.
Ways to stay updated:
Attend industry conferences and seminars in India and abroad.
Encourage your team to take up certifications in new technologies.
Collaborate with local universities and research institutes to develop innovative solutions.
Conclusion
Starting an IT company in Nagpur offers tremendous opportunities for growth, thanks to the city’s developing infrastructure and increasing demand for tech solutions. By choosing the right niche, building a strong team, and staying up-to-date with the latest technological trends, you can create a thriving IT business in the heart of India. With careful planning and execution, your IT company in Nagpur can not only succeed locally but also expand to cater to national and international clients.
0 notes
Text
The Best 7 IPTV Boxes 2024
Are you tired of being stuck with traditional cable TV?
Do you want to watch your favorite shows anytime, anywhere? IPTV boxes are the answer! They’re changing the game in France, offering endless channels and services.
In this guide, we’ll explore the top 7 IPTV boxes for 2024 in France. We’ve tested these smart TV and Android TV boxes to help you choose the best one. Whether you’re cutting the cord or just want more options, an IPTV box is perfect.
Join us as we explore the world of internet protocol TV. Discover how these amazing devices can change how you watch content. With the right IPTV box, you can create a viewing experience that’s all about you. So, sit back and let’s dive into the exciting possibilities!
Key Takeaways
IPTV boxes offer a flexible and convenient way to access a wide range of content
We’ve tested the top 7 IPTV boxes available in France for 2024
Consider factors such as compatibility, processing power, storage, and video output when choosing an IPTV box
Setting up and using an IPTV box is a straightforward process
IPTV technology is revolutionizing the way we watch television in France
What to Look for in an IPTV Box
When looking for an IPTV box, there are key things to consider. These include compatibility with your favorite IPTV services, processing power, and storage options. Making the right choice can greatly improve your viewing experience.
Compatibility with IPTV Services
It’s vital to check if the IPTV box works with your preferred services. Ensure it supports platforms like Netflix and Amazon Prime Video. Also, check if it works with specialized IPTV providers you might use. This ensures you can easily access your favorite content.
Processing Power and RAM
For smooth streaming, choose an IPTV box with a strong processor and plenty of RAM. This helps avoid buffering and lag, so you can enjoy your shows and movies without pause. Aim for a device with at least a quad-core processor and 2GB of RAM.
Storage Capacity
Consider storage capacity if you want to download content or install many IPTV apps. Some boxes have built-in storage, while others let you add more via USB or microSD card. Opt for a device with at least 8GB of storage, expandable if needed.
Video Output Quality
Choose an IPTV box that supports high-quality video output, like 4K resolution and HDR. This ensures your content looks stunning, with great detail and color. Also, make sure it has the right ports to connect to your TV, like HDMI 2.0 for 4K streaming.FeatureRecommended SpecificationProcessorQuad-core or higherRAM2GB or moreInternal Storage8GB or moreVideo Output4K, HDR supportConnectivityHDMI 2.0, USB, Ethernet, Wi-Fi
Top IPTV Boxes on the Market
In this section, we will introduce the top 7 IPTV boxes available in France for 2024. These devices have been selected based on their performance, features, and user reviews. The MAG 425A is known for its seamless integration with popular IPTV services. The Xiaomi Mi Box S offers excellent value for money. The NVIDIA Shield TV Pro is a high-end option with exceptional performance and features.
Other top contenders include the Amazon Fire TV Cube, Formuler Z8 Pro, BuzzTV XR4000, and Dreamlink T3. Each device has its own strengths and unique features. They cater to different user preferences and budgets. Let’s take a closer look at what makes these IPTV boxes stand out.IPTV BoxKey FeaturesPrice RangeMAG 425ASeamless integration with popular IPTV services, user-friendly interface€100 – €150Xiaomi Mi Box SAffordable, supports 4K HDR, Android TV operating system€50 – €100NVIDIA Shield TV ProHigh-end performance, AI upscaling, gaming capabilities€200 – €250Amazon Fire TV CubeBuilt-in Alexa voice control, supports 4K HDR, Dolby Vision€100 – €150Formuler Z8 ProPowerful processor, large storage capacity, supports multiple IPTV apps€150 – €200BuzzTV XR4000Customizable interface, supports popular IPTV services, built-in VPN€100 – €150Dreamlink T3User-friendly interface, supports multiple IPTV apps, reliable performance€100 – €150
When choosing an IPTV box, consider compatibility with your preferred IPTV services. Also, think about processing power, storage capacity, and video output quality. The MAG 425A is known for its seamless integration with popular IPTV services. The NVIDIA Shield TV Pro offers exceptional performance and features for those willing to invest in a high-end device.
Setting Up and Using Your IPTV Box
Choosing the right IPTV box is exciting. Now, it’s time to set it up and enjoy your favorite shows and movies. Setting up an IPTV box is easy. Follow a few simple steps, and you’ll be streaming your favorite content in no time.
Connecting Your IPTV Box
The first step is connecting your IPTV box to your TV. Most come with an HDMI cable for high-quality video. Plug the HDMI cable into your box and your TV’s HDMI port. Then, connect your box to the internet. You can use Wi-Fi or an ethernet port, depending on your home setup.
Installing IPTV Apps and Services
Once connected, install the apps and services you want. Most boxes have an app store for popular streaming apps like Netflix and Hulu. Some also let you sideload apps from outside the store. This is great for finding niche services or content specific to your region.
Navigating the User Interface
Now, explore your IPTV box’s user interface. Use the remote control to navigate easily. You’ll find a home screen with your apps and settings. Many boxes also let you customize the interface to your liking. You can change icons, backgrounds, and even create shortcuts to your favorite content.Connection TypeAdvantagesDisadvantagesHDMI CableHigh-quality video and audio, simple to set upRequires a free HDMI port on your TVWi-FiNo additional cables needed, convenient for wireless setupsSignal strength may vary depending on distance from routerEthernet PortStable, reliable connection, ideal for streaming high-quality contentRequires a physical connection to your router or modem
With the right IPTV box and a little bit of setup, you’ll be well on your way to enjoying all your favorite content from the comfort of your own home.
Explore your IPTV box and try different settings and customization options. Find the perfect setup for your viewing preferences. With so many features, your IPTV box will be a key part of your home entertainment.
Conclusion
Choosing the best IPTV box can greatly improve your viewing experience. It gives you access to many streaming services and content. The top IPTV boxes for 2024 have great performance, lots of storage, and high-quality video.
By picking a device that fits your needs, you get a smooth and engaging home entertainment experience. This lets you enjoy a wide range of movies, TV shows, and live channels.
Setting up your IPTV box is easy, thanks to user-friendly interfaces. Just connect it to your TV and network. Then, you can install your favorite apps and services.
This makes it simple to access a huge library of content. As IPTV technology gets better, these devices will shape the future of TV. They offer more choice, convenience, and control over what you watch.
Getting one of the best IPTV boxes for 2024 is a wise choice. It lets you enjoy a premium home entertainment experience. By choosing the right device, you open up a world of possibilities.
Embrace the future of TV with a top IPTV box. It will take your viewing experience to new levels.
FAQ
What is an IPTV box?
An IPTV box is a device that lets you stream services and channels over the internet. It makes watching TV better by offering lots of content choices.
What should I look for when choosing an IPTV box?
Look at the box’s compatibility with your IPTV services. Also, check its processing power, RAM, and storage. Make sure it supports 4K resolution and HDR for the best video quality.
Can I use my IPTV box with any IPTV subscription or service?
Not all IPTV boxes work with every service. Make sure the device you pick supports your favorite platforms like Netflix or Amazon Prime Video.
How do I set up my IPTV box?
Setting up your IPTV box is easy. Just connect it to your TV with an HDMI cable and ensure a stable internet connection. Then, install apps and services from the device’s app store or by sideloading them.
What are some of the top IPTV boxes available in France for 2024?
In 2024, top IPTV boxes for France include the MAG 425A, Xiaomi Mi Box S, and NVIDIA Shield TV Pro. Also, consider the Amazon Fire TV Cube, Formuler Z8 Pro, BuzzTV XR4000, and Dreamlink T3. Each offers unique features for different needs and budgets.
Can I customize the user interface of my IPTV box?
Yes, many IPTV boxes let you customize the interface. You can rearrange apps, change themes, and set shortcuts for your favorite shows. This way, you can make your viewing experience personal.
1 note
·
View note
Text
Easy Guide to Set Up the Best USA IPTV in 2024
Setting up IPTV (Internet Protocol Television) can provide access to a wide range of live TV channels, movies, series, and on-demand content. Here's an easy guide to help you set up one of the best USA IPTV services in 2024:
1. Choose the Best USA IPTV Provider
Selecting the right IPTV provider is crucial. Some of the best USA IPTV services for 2024 are known for their reliability, extensive channel list, high-quality streaming, and customer support. When choosing a provider, consider:
Content Variety: Make sure the service offers a broad selection of channels, including local, sports, news, and entertainment.
Streaming Quality: Look for HD, Full HD, and 4K quality options.
Compatibility: Ensure the service is compatible with your preferred devices, like Smart TVs, Android Boxes, Firestick, iOS, or Windows.
Pricing: Look for competitive pricing and flexible payment options.
Customer Support: Opt for a service with responsive customer support.
2. Install IPTV on Your Device
Depending on the device you're using, the installation steps may vary. Here are the steps for different devices:
a. Amazon Firestick
Prepare Your Firestick:
Go to Settings > My Fire TV > Developer Options.
Enable Apps from Unknown Sources.
Install the Downloader App:
Search for the Downloader app on your Firestick.
Install and open the app.
Download IPTV App:
Enter the URL provided by your IPTV service for downloading their app.
Download and install the app.
Enter IPTV Credentials:
Open the IPTV app.
Enter your IPTV subscription credentials (username, password, or M3U URL).
b. Android TV/Android Box
Access the Google Play Store:
Open the Google Play Store on your Android device.
Search for IPTV App:
Download a compatible IPTV app (such as IPTV Smarters Pro, TiviMate, or XCIPTV Player).
Install and Open the App:
Install the app and open it.
Enter IPTV Details:
Input your IPTV credentials to start streaming.
c. Smart TVs (Samsung, LG, etc.)
Install IPTV App:
Go to the app store on your Smart TV (Samsung App Store, LG Content Store, etc.).
Search for IPTV apps like Smart IPTV or SS IPTV.
Upload Playlist:
After installing, open the app and enter the M3U URL or upload a playlist provided by your IPTV service.
Start Streaming:
Once the playlist is uploaded, you can start watching channels.
d. iOS Devices (iPhone, iPad, Apple TV)
Install an IPTV Player:
Go to the App Store and download an IPTV player like IPTV Smarters, GSE Smart IPTV, or IP Television.
Set Up IPTV:
Open the app and add a new user or playlist using the M3U URL or credentials provided by your IPTV provider.
Start Watching:
After adding the playlist, you can start streaming.
3. Configure the IPTV Settings
EPG (Electronic Program Guide): Set up the EPG URL provided by your IPTV provider to access the TV guide.
Playback Settings: Adjust buffering, resolution, and video quality settings for optimal streaming.
Parental Controls: Set up parental controls if you need to restrict certain content.
4. Use a VPN for Privacy and Security
It is highly recommended to use a VPN (Virtual Private Network) to protect your online privacy and bypass geographical restrictions.
Choose a reliable VPN service, connect to a USA server, and ensure your connection is secure before streaming.
5. Test Your IPTV Service
After setting up, test the service to ensure all channels are working correctly and the streaming quality meets your expectations.
Contact the IPTV provider's support team if you encounter any issues.
6. Enjoy High-Quality Streaming
With the setup complete, you can now enjoy a vast range of live channels, movies, series, and on-demand content at your fingertips.
Conclusion
By following these steps, you can easily set up one of the best USA IPTV services in 2024 and enjoy seamless streaming on any device. Be sure to choose a reputable IPTV provider and take advantage of the features they offer for the best viewing experience.
0 notes
Text
Choosing the Right VPN: A Comprehensive Comparison of Speed, Security, and Performance
In an age where online privacy and security are paramount, choosing the right Virtual Private Network (VPN) can make all the difference. Whether you’re looking to safeguard your data, access restricted content, or simply enjoy a smoother browsing experience, selecting the right VPN involves understanding its speed, security, and overall performance. Welcome to the VPN Guide by Web Design Booth, where we’ll help you navigate the maze of VPN options and find the best one for your needs.

1. What Is a VPN?
A VPN, or Virtual Private Network, is a tool that helps protect your online privacy by encrypting your internet connection and masking your IP address. Think of it as a secure tunnel that hides your data from prying eyes, allowing you to browse the web more safely. It’s like having a private, encrypted conversation in a noisy, crowded room.
2. Why Speed Matters in a VPN
Speed is crucial when choosing a VPN. Nobody wants to deal with buffering videos or slow-loading websites. A good VPN should provide fast and stable connections so that you can stream, browse, and download without interruptions. Imagine trying to use a high-speed train but ending up with a slow, rattling cart—it’s all about efficiency.
3. Understanding VPN Security Features
Security is the heart of a VPN. Look for features like strong encryption protocols (e.g., AES-256), a no-logs policy, and advanced security measures like kill switches. These features ensure your data remains confidential and secure from hackers. It’s like having a state-of-the-art lock on your front door—only those with the key can get in.
4. Performance Factors to Consider
Performance involves more than just speed. Consider how a VPN affects your overall browsing experience. Key factors include connection stability, server locations, and the impact on device performance. A high-performing VPN should not only be fast but also reliable and efficient, much like a well-tuned engine in a high-performance car.
5. Speed Comparison: Free vs. Paid VPNs
Free VPNs often come with limitations such as slower speeds, limited server options, and potential security risks. Paid VPNs usually offer better performance, more servers, and enhanced security features. It’s like comparing a free ride on a rusty bike to a paid trip in a sleek, modern car—the difference in quality is significant.
6. Security Comparison: What to Look For
When comparing VPNs for security, look for providers that offer robust encryption, secure tunneling protocols, and a clear privacy policy. Avoid services that keep logs of your activities or have a history of data breaches. Think of it like choosing between a secure vault and a flimsy locker for your valuables.
7. How to Test VPN Performance
Testing a VPN's performance involves checking its speed, reliability, and impact on your device. Use online speed tests and monitor your connection during regular use. Compare results across different servers and times to get a true sense of performance. It’s like testing driveability in different weather conditions to ensure reliability.
8. Choosing a VPN Based on Your Needs
Different users have different needs. Whether you want to stream content, protect sensitive data, or bypass censorship, choose a VPN that aligns with your specific requirements. Consider factors like server locations, speed, and additional features that suit your activities. It’s like choosing a tool based on the job you need to do—each one has its strengths.
9. Top VPN Providers for Speed and Security
Some VPN providers are renowned for their balance of speed and security. Look for options like ExpressVPN, NordVPN, and CyberGhost, which are known for their excellent performance and strong security features. It’s similar to picking a trusted brand for a high-quality product—you know you’re getting the best.
10. Common Misconceptions About VPNs
There are many myths about VPNs, such as the belief that they are only for tech experts or that they slow down your internet significantly. In reality, modern VPNs are user-friendly and designed to offer minimal impact on speed. It’s like debunking the idea that a new gadget is complicated when, in fact, it’s quite straightforward.
11. How to Set Up and Use Your VPN
Setting up a VPN is typically straightforward. Download the application from your chosen provider, follow the setup instructions, and connect to a server. Make sure to configure any additional settings based on your needs. It’s like setting up a new appliance—just follow the instructions, and you’re good to go.
12. The Importance of Customer Support
Good customer support can make a huge difference. Look for VPN providers that offer responsive support, comprehensive guides, and troubleshooting assistance. Reliable customer support ensures you can resolve issues quickly and efficiently. It’s like having a friendly technician available whenever you need help with your new device.
13. VPNs for Specific Use Cases
Different use cases require different features. For example, if you’re into streaming, look for VPNs with high-speed servers and access to various streaming platforms. For privacy, focus on providers with strong encryption and no-logs policies. It’s like picking the right tool for the job—each scenario needs its specialized equipment.
14. Best Practices for Using a VPN
To maximize your VPN experience, follow these best practices:
Keep Your VPN Updated: Ensure you’re using the latest version for optimal performance and security.
Use Strong Authentication: Enable two-factor authentication for added security.
Connect to the Right Server: Choose servers based on your needs, whether for speed or specific locations.
15. Conclusion: Making an Informed Decision
Choosing the right VPN involves balancing speed, security, and performance based on your personal needs. By understanding these factors and testing different options, you can find a VPN that enhances your online experience while keeping your data safe. Make an informed choice and enjoy a more secure, private, and efficient internet experience.
0 notes
Text
Achieve Anonymity with 5G Mobile Proxies

In an era where online privacy is increasingly compromised, maintaining anonymity online is crucial. One of the most effective tools for this is 5G mobile proxies. They offer not just anonymity but also enhanced speed and security, making them a top choice for anyone looking to protect their identity on the internet.
What Are 5G Mobile Proxies?
5G mobile proxies are IP addresses assigned by mobile carriers that use 5G networks. When you connect through a 5G proxy, your internet traffic is routed through a mobile device connected to a 5G network. This masks your real IP address and gives you a high level of anonymity.
How 5G Mobile Proxies Enhance Anonymity
The dynamic nature of 5G IP addresses makes it difficult for websites and online platforms to track your online activities. Unlike static IPs, which are easier to identify and block, 5G IPs change frequently, providing an extra layer of security. This makes it much harder for anyone to trace your internet activities back to you.
Benefits of Using 5G Mobile Proxies
Increased Security
5G mobile proxies offer advanced security features, including encryption and secure tunneling. These features protect your data from hackers and other malicious entities. With 5G proxies, your online activities remain private and secure, ensuring that your personal information is not exposed.
Faster Speeds
5G networks are known for their ultra-fast speeds. When combined with mobile proxies, you get a smooth and seamless browsing experience. Whether you’re streaming, gaming, or managing multiple accounts, 5G proxies ensure that you can do so without any lag or interruption.
Bypassing Geo-Restrictions
Many websites and online services restrict content based on your geographical location. 5G mobile proxies allow you to bypass these restrictions effortlessly. By connecting through a proxy in a different region, you can access content that would otherwise be unavailable in your area.
Choosing the Right 5G Mobile Proxy Provider
Selecting a reliable 5G mobile proxy provider is essential for maintaining anonymity and ensuring high performance. Look for providers that offer a large pool of IPs, fast connection speeds, and strong security features. Also, consider the provider’s reputation and customer support, as these factors can impact your overall experience.
Setting Up Your 5G Mobile Proxy
Setting up a 5G mobile proxy is straightforward. Most providers offer user-friendly dashboards where you can easily configure your proxy settings. Make sure to choose a server location that suits your needs, whether it’s for accessing region-locked content or achieving the fastest possible speeds.
Maximizing Anonymity with 5G Mobile Proxies
To maximize your anonymity, use 5G mobile proxies in conjunction with other privacy tools, such as VPNs and encrypted browsers. This multi-layered approach makes it nearly impossible for anyone to track your online activities. Regularly updating your proxy settings and rotating IPs can also enhance your anonymity.
Conclusion
5G mobile proxies are a powerful tool for achieving online anonymity. They provide advanced security features, faster speeds, and the ability to bypass geo-restrictions. By choosing the right provider and configuring your proxy correctly, you can protect your online identity and enjoy a secure, anonymous browsing experience.
Read the full article
0 notes
Text
Top 5 Secure Remote Access Solutions for Your Business

In today’s increasingly digital world, remote work has become the norm for many businesses. Ensuring secure remote access to your company’s network is crucial to protect sensitive data and maintain operational efficiency. With numerous options available, choosing the right solution can be challenging. This blog post will provide a comprehensive secure remote access solutions comparison, highlighting the top five options for your business. By the end of this post, you’ll have a clearer understanding of which solution best fits your needs.
The Importance of Secure Remote Access
Why Secure Remote Access Matters
Secure remote access is essential for protecting your business from cyber threats. It ensures that employees can access the company’s network safely, without exposing sensitive information to potential attackers. A robust secure remote access solution can prevent data breaches, unauthorized access, and other security incidents.
Key Features to Look For
When evaluating secure remote access solutions, consider features such as encryption, multi-factor authentication, ease of use, scalability, and integration with existing systems. A thorough secure remote access solutions comparison will help you identify the best option for your business.
Solution 1: Virtual Private Networks (VPNs)
Overview of VPNs
Virtual Private Networks (VPNs) are one of the most widely used secure remote access solutions. They create a secure, encrypted tunnel between the user’s device and the company’s network, ensuring that data transmitted over the internet remains private.
Pros and Cons
Pros:
Easy to implement and use
Provides strong encryption
Widely supported across devices and platforms
Cons:
Can be slower due to encryption overhead
May not provide granular access controls
Best Use Cases
VPNs are ideal for businesses looking for a straightforward and cost-effective solution to secure remote access. They are particularly useful for small to medium-sized enterprises (SMEs) with a limited IT budget.
Solution 2: Zero Trust Network Access (ZTNA)
Overview of ZTNA
Zero Trust Network Access (ZTNA) is a modern approach to secure remote access that operates on the principle of “never trust, always verify.” It grants access based on user identity and device security posture, ensuring that only authenticated and authorized users can access the network.
Pros and Cons
Pros:
Provides granular access controls
Reduces the attack surface
Enhances security by continuously verifying user and device trust
Cons:
Can be complex to implement
Requires integration with identity and access management (IAM) systems
Best Use Cases
ZTNA is suitable for businesses with a distributed workforce and a need for high security. It is particularly beneficial for organizations that handle sensitive data and require strict access controls.
Solution 3: Secure Access Service Edge (SASE)
Overview of SASE
Secure Access Service Edge (SASE) is an emerging framework that combines network security functions with wide area network (WAN) capabilities. It provides secure remote access by integrating features such as secure web gateways, firewall-as-a-service, and cloud access security brokers.
Pros and Cons
Pros:
Comprehensive security and networking solution
Scalable and flexible
Simplifies network management
Cons:
Can be expensive
Requires a shift to cloud-based infrastructure
Best Use Cases
SASE is ideal for large enterprises with complex network and security requirements. It is particularly useful for organizations undergoing digital transformation and looking to consolidate their security and networking functions.
Solution 4: Remote Desktop Services (RDS)
Overview of RDS
Remote Desktop Services (RDS) allow users to access a remote computer or virtual machine over a network connection. It provides a secure way for employees to access their work environment from any location.
Pros and Cons
Pros:
Provides a consistent user experience
Supports a wide range of applications
Can be integrated with existing IT infrastructure
Cons:
Can be resource-intensive
Requires robust network connectivity
Best Use Cases
RDS is suitable for businesses that need to provide remote access to specific applications or desktops. It is particularly useful for organizations with a centralized IT infrastructure and a need for high-performance remote access.
Solution 5: Cloud-Based Remote Access Solutions
Overview of Cloud-Based Solutions
Cloud-based remote access solutions leverage cloud infrastructure to provide secure remote access to applications and data. These solutions often include features such as single sign-on (SSO), multi-factor authentication (MFA), and data encryption.
Pros and Cons
Pros:
Scalable and flexible
Easy to deploy and manage
Provides robust security features
Cons:
Dependent on internet connectivity
Can be costly for large-scale deployments
Best Use Cases
Cloud-based remote access solutions are ideal for businesses looking to leverage the scalability and flexibility of the cloud. They are particularly useful for organizations with a remote or hybrid workforce and a need for secure access to cloud-based applications.
Secure Remote Access Solutions Comparison
Comparing the Top Solutions
When conducting a secure remote access solutions comparison, consider factors such as security, scalability, ease of use, and cost. Each solution has its strengths and weaknesses, and the best choice will depend on your specific business needs.
Key Considerations
Security: Ensure the solution provides robust encryption, multi-factor authentication, and continuous monitoring.
Scalability: Choose a solution that can grow with your business and support an increasing number of remote users.
Ease of Use: Opt for a solution that is easy to deploy and manage, with minimal disruption to your operations.
Cost: Consider the total cost of ownership, including initial setup, ongoing maintenance, and potential upgrades.
Conclusion
Choosing the right secure remote access solution is crucial for protecting your business from cyber threats and ensuring seamless remote work. By conducting a thorough secure remote access solutions comparison and considering factors such as security, scalability, ease of use, and cost, you can find the best option for your organization. If you have any questions or additional tips to share, please leave a comment below. Stay secure!
0 notes
Text
What is the difference between a VPN and a proxy IP?
VPNs and proxy IPs are often common choices when you need to hide your identity, protect your privacy or access restricted content on the Internet. While both can hide your real IP address, they differ significantly in terms of features, how they work and application scenarios. The following takes you through an in-depth look at the differences between VPNs and proxy IPs to help you choose the best tool for the job.

1. What is a VPN?
A VPN is a technology that connects a user's device to a remote server through an encrypted tunnel.A VPN not only hides your IP address, but also encrypts all network traffic from third-party snooping. It creates an encrypted tunnel when connecting, thus ensuring security and privacy of data transfer.
2. What is Proxy IP?
Proxy IP is a service that forwards user requests through an intermediate server. The proxy server receives the user's web request and forwards it to the target website, while replacing the user's real IP address with the proxy server's IP address. Proxy IP is often used to hide a user's IP address or bypass geo-restrictions, but it does not encrypt web traffic.
3. Differences between VPNs and proxy IPs
1. Security and Privacy Protection
VPN: VPN protects user data by encrypting the connection. All traffic that passes through the VPN tunnel is encrypted, which means that even if someone intercepts your packets, they can't read the contents. As a result, VPNs offer a higher level of security and privacy protection, and are especially useful for performing sensitive operations (such as logging into accounts or processing financial transactions) over public Wi-Fi.
Proxy IP: A proxy IP is only responsible for hiding your IP address, it does not encrypt your traffic. Therefore, when using a proxy, data can still be intercepted or monitored during transmission. Proxy IP is less secure and is mainly used in scenarios where a high level of security is not required.
2. Data Encryption
VPN: VPN encrypts all the user's traffic, whether it is browsing the web, transferring files or using applications, all operations are protected within the encrypted channel.
Proxy IP: Proxy IP does not provide encryption, it only handles traffic that passes through the proxy server. This means that the requests you send are transmitted in plaintext and are relatively less secure.
3. Speed and Performance
VPN: Since VPN performs encryption and decryption operations on the traffic and all data must be forwarded through the VPN server, it may cause some speed delays, especially if the server is far away.
Proxy IP: Proxy IP is not encrypted and theoretically faster, suitable for scenarios that require large amounts of data transmission or real-time operations, such as video streaming, web crawlers, etc.
4. Application Scenarios
VPN: It is suitable for protecting privacy, encrypting data and accessing blocked websites. It excels in scenarios that require high security and privacy, such as remote work, accessing sensitive data, etc.
Proxy IP: Commonly used for IP address hiding and bypassing geo-restrictions, it is suitable for scenarios such as data crawling, advertisement verification, and social media management. It helps users access restricted content through a different IP address, but does not provide encryption protection.
Whether it's a VPN or a proxy IP, choosing the right tool depends on your specific needs. If you need a more secure web experience, 711Proxy not only provides quality static residential proxy services, but also helps you choose the most appropriate web tool for different business scenarios.
0 notes
Text
Cybersecurity in the Age of Remote Work: Strategies for Businesses

The digital transformation has revolutionized the way we work with remote work arrangements. Once a perk for a select few, it is now the norm for many businesses. This shift offers undeniable advantages – increased flexibility, improved employee satisfaction, and access to a wider talent pool. However, this new trend also presents unique cybersecurity challenges. So, if you are a business owner relying on a remote workforce, you must read this post to learn how you can protect your business from cyber threats. It is not easy! However, you can prevent such incidents with the right knowledge and cybersecurity solutions. So, let’s dive in:
Building a Secure Remote Workforce
With employees scattered across locations, the traditional security perimeter of a centralized office dissolves. Company data is now accessed from personal devices and home networks, creating more entry points for cybercriminals. Phishing emails, malware attacks, and unauthorized access attempts become even more perilous in a remote work environment. So, how can businesses navigate this evolving landscape and ensure the safety of their data in the age of remote work? Here are some key strategies:
Secure IT Security Solutions
One of the most critical aspects of remote work security is controlling access to company resources. Implement a Virtual Private Network (VPN) that encrypts data in transit between remote devices and the company network. Moreover, you can invest in enforcing Multi-Factor Authentication (MFA), which adds an extra step or second verification factor beyond their password.
Endpoint Security
Remote work expands the attack surface as employees use personal laptops or smartphones to access company data. You can install network security solutions such as firewalls, antivirus software, and intrusion detection systems. Maintain strong password policies and regularly update software to prevent cyberthreats in your business.
Data Encryption
Sensitive data, both at rest and in transit, should be encrypted using industry-standard algorithms. As a result, if a cybercriminal gains access to data, it remains unreadable without the decryption key. You can also consider data loss prevention (DLP) solutions to protect sensitive data. It helps to avoid accidentally sharing or downloading data to unauthorized devices.
Managed Security Services
You should apply the principle of least privilege, which gives permission to limited users to access the data and systems they need to perform their job functions. Implementing role-based access control (RBAC) ensures that only authorized users have necessary access to specific data sets that minimize the potential damage in case of a security breach.
Security Awareness Training
You should not forget the factor of human error in many cybersecurity incidents. Spend money on proper employee training. Such training should cover topics such as phishing email identification, password hygiene, and secure data handling procedures.
Cloud Security Services
Many businesses leverage cloud-based applications for collaboration and data storage. When choosing cloud providers, it's vital to understand the security practices and ensure the provider meets your organization's compliance requirements. Moreover, businesses should implement additional security measures, like access controls and data encryption, within the cloud environment.
Cyber Incident Response Plan
Despite all precautions, security breaches can still occur. Keeping a well-defined incident response plan in place helps your organization react quickly and minimize damage. The plan should outline roles and responsibilities, data recovery and communication protocols in case of a cyberattack.
Regular Security Assessments
You need to have a team conduct security assessments regularly. It identifies vulnerabilities in your systems and processes. These assessments should include penetration testing, which simulates a cyberattack to identify weaknesses in your defenses. Vulnerability scans can also be used to identify outdated software and unpatched security holes.
Building a Culture of Security
Cybersecurity is not just a technical issue; it's a cultural one. Businesses need to foster a culture of security awareness where employees understand the importance of protecting company data. Leaders should take on cybersecurity initiatives and encourage open communication about security concerns.
Conclusion
Here you have learned the challenges of cyberthreats and how you can resolve such issues, especially when you hire remote employees. You can implement the above strategies for cybersecurity solutions that protect your data and foster employee trust. Remember, cybersecurity is an ongoing process. So stay vigilant and adapt to the evolving threat landscape.
#Cybersecurity solutions#Managed security services#IT security solutions#network security solutions#cloud security services#Cyber incident response
1 note
·
View note
Text
Free Mobile Proxy: Enhancing Privacy and Accessibility
Free Mobile Proxy: Enhancing Privacy and Accessibility
In today’s digital age, privacy and accessibility are paramount concerns for internet users. With the increasing use of mobile devices for browsing, the need for secure and anonymous internet access has never been greater. Free mobile proxies offer a solution to these concerns by providing a way to browse the internet anonymously and access restricted content. This article will explore the benefits of using free mobile proxies, how they work, and some popular options available.To get more news about free mobile proxy, you can visit ip2world.com official website.
1. What is a Mobile Proxy?
A mobile proxy is a server that acts as an intermediary between your mobile device and the internet. When you use a mobile proxy, your internet traffic is routed through the proxy server, masking your IP address and making it appear as though you are browsing from a different location1. This helps protect your privacy and allows you to access content that may be restricted in your region.
2. Benefits of Using Free Mobile Proxies
There are several benefits to using free mobile proxies, including:

4. Popular Free Mobile Proxy Options
There are several free mobile proxy services available that offer reliable and secure browsing. Some popular options include:
Proton VPN: Proton VPN offers a free mobile VPN service with no data limits, strong encryption, and a strict no-logs policy. It is trusted by journalists and activists worldwide for its privacy and security features.
ProxySite: ProxySite is a free web proxy service that allows you to browse the internet anonymously and access restricted content. It supports popular websites like YouTube, Facebook, and Twitter, and provides a secure connection to protect your data.
RotatingProxies: RotatingProxies offers free HTTP, HTTPS, and SOCKS5 proxies with an easy-to-use online generator3. Users can filter proxies by country, protocol, and anonymity level, making it a versatile option for anonymous browsing.
5. Considerations When Using Free Mobile Proxies
While free mobile proxies offer many benefits, there are some considerations to keep in mind:
Speed and Reliability: Free proxies may have slower connection speeds and less reliable performance compared to paid services. This can impact your browsing experience, especially when streaming or downloading large files.
Security Risks: Not all free proxies are secure. Some may log your browsing activities or inject ads into your web pages. It’s important to choose a reputable proxy service with a strong privacy policy.
Limited Features: Free proxies may have limited features compared to premium services, such as fewer server locations and lower data limits. If you require advanced features, you may need to consider a paid proxy service.
Conclusion
Free mobile proxies provide a valuable solution for enhancing privacy and accessibility when browsing the internet on your mobile device. By masking your IP address and allowing you to access restricted content, mobile proxies help protect your online identity and improve your browsing experience. However, it’s important to choose a reputable proxy service and be aware of the potential limitations and risks associated with free proxies. With the right proxy, you can enjoy a secure and anonymous browsing experience on your mobile device.
0 notes