#Code with TLS IT Institute
Explore tagged Tumblr posts
Text
Code with TLS: Your Trusted IT Training Institute Near Me for Tech Careers
Are you looking for an IT Training Institute Near Me that offers comprehensive tech courses to help you advance your career? Look no further than Code with TLS, your trusted Tech Course Provider! Whether you're looking to upskill or start a fresh career in the ever-evolving world of technology, Code with TLS offers a range of job-oriented courses that are designed to help you excel in the IT industry.
At Code with TLS, we understand that the tech landscape is constantly changing. That's why we focus on delivering high-quality training in the most in-demand areas of technology, ensuring that our students are equipped with the skills employers are actively seeking. From digital marketing and MERN stack development to data science and AI/ML, our courses are designed to provide practical, hands-on learning experiences that set our students apart in the competitive tech market.
Why Choose Code with TLS?
Code with TLS is more than just a traditional IT Training Institute Near Me. We are a leading Tech Course Provider committed to your success. Here’s why you should consider us:
Industry-Relevant Curriculum: Our courses are crafted to match the current industry demands, ensuring that you gain expertise in areas that matter most to employers.
Experienced Trainers: Our trainers are industry professionals with years of experience, bringing real-world insights into the classroom. They are passionate about helping students grow and thrive in their careers.
100% Placement Assistance: We take pride in our strong connections with leading tech companies. Our dedicated placement team ensures that you have the support you need to land your dream job in tech.
Hands-On Training: At Code with TLS, we believe in learning by doing. Our courses offer practical sessions that allow you to apply your knowledge and build a portfolio that impresses potential employers.
Flexible Learning Options: Whether you prefer online or offline learning, we offer flexible course formats to suit your lifestyle. You can join us for weekend batches, full-time training, or self-paced courses – the choice is yours.
Join Code with TLS Today!
Don’t let location hold you back! Code with TLS is your go-to IT Training Institute Near Me, offering world-class training at your convenience. We are here to help you unlock your full potential and achieve success in the tech industry.
Get started today by calling us at +918527866980 or visiting our website to explore our courses and enrollment options. Take the first step toward a rewarding tech career with Code with TLS, your trusted partner in IT training.
#IT Training Institute Near Me#Tech Course Provider#IT Training Near Me#Tech Courses Near Me#Code with TLS#Job-Oriented Tech Courses#Tech Career Training#MERN Stack Development Training#Digital Marketing Courses#Data Science Training#AI and Machine Learning Courses#IT Training for Career Growth#Best IT Training Institute#Tech Skills Development#Online IT Training Courses#Code with TLS IT Institute#IT Placement Assistance#Tech Training Providers#Hands-on IT Training#IT Training Courses for Beginners#Best Tech Course Provider Near Me
0 notes
Text
I get where people are coming from wrt to describing male characters as feminized in their powerlessness (sometimes this is very much intentional and evidenced by the text, plus men's disempowerment via comparison to women, because women are thought to be inherently inferior/powerless, is something that happens in real life!) but at the same time I'm skeptical of any reading that naturalizes misogyny by going "this man lacks agency, which makes him like a woman"
#bolo speaks#''what inspired this'' my shakespeare class#I honest-to-god said ''but what if it's *masculine* submission?'' once. in an institution of learning#would recommend it to everyone#tl;dr when it comes to descriptions of male characters as ''female-coded'' or something similar I'll bite but you'd better have citations
11 notes
·
View notes
Text
Frostheim B's-Log Pages TL
Huge thank you to @boobeees for providing the pages for this translation!

Disclaimer: I am not a professional TLer and this TL has not been verified by another person. This is meant as a reference and not as 100% fact. I have made mistakes before and likely will again. TLer notes are provided for certain lines.
Please do not repost my translations.
Page One
Ch. 13 Summary: The Western European country of Lapona* is known as the 'Wealthiest country in the world'. Jin Kamurai, son of the Chief Cabinet Secretary, is entrusted the essential task of hosting and attending a banquet for Lapona's reigning monarch, Gaspard, and the royal family. The MC, alongside Kaito, Lucas, and Tohma, attend the party as servants of the Kamurai Family. However, it seems that the true reason for Gaspard's visit is to 'find a way to break a curse'… *Lapona is rendered in katakana as 'Rapona'. I have chosen Lapona over Rapona due to other Western European countries' names, as I think this is closest. As far as I know, this doesn't exist irl.
Outfit Blurb: At Gaspard's daughter's request, Frostheim have been dressed in accordance to Masquerade Ball dress code rules. Please take a look at their bewitchingly beautiful outfits♥️
Page Two
Screaming Kaito Blurb: A top-secret investigation at the banquet! In order to investigate the incognito arrival of the Royal Family, the Frostheim students head to the banquet. Gaspard's children reveal more circumstances around Gaspard's sickly appearance, saying: 'He's afraid of mirrors'….? *This could be like. Afraid of his own reflection in particular but also mirrors in general? tl;dr Gaspard is sick and his kids say he doesn't like mirrors anymore
Mirror Blurb: A sinister rumour; 'The Family Has Been Cursed' Gaspard's hobby is collecting both cursed and blessed* objects, but could there be an anomaly lurking within his collection? According to Lucas's investigation, the area around the Royal Family has recently experienced an incredible amount of deaths, leading the people to believe that 'the family has been cursed'. *I used blessed to contrast w cursed, but he basically collects cursed objects, protective charms, protective objects etc. Quote: If that's the case…. the problem truly is this mirror here.
Jin Smoke Quote: I can't say for certain yet, but there's definitely something going on.
Jin Mirror Blurb: Jin Kamurai: The son of the Chief Cabinet Secretary, as well as the son of the President of the Anomalous Investigation Institute's Japan Branch. Due to the importance of political relationships on this mission, his own dorm, Frostheim, are the only ones capable of completing it. But during this task, Jin looks into a mirror, and in the reflection he sees is…?* *The grammar implies this is a Bad Thing To See lmfao Quote: … 'A low-level anomaly', huh? Don't make me laugh*. *Pretty sure this is the intent. I think this is the anomaly saying it and not Jin. I think. Either way, I think the idea is the same regardless of if it's Jin or the anomaly.
#my tl#tokyo debunker#tokyo debunker spoilers#frostheim#jin kamurai#tohma ishibashi#kaito fuji#lucas errant#tkdb
209 notes
·
View notes
Text
Help Purdue pro-Palestine protestors beat charges for peaceful protesting







Phone Numbers:
(765) 494 - 1250 (Associate Dean of Students)
(765) 494 - 1747 (Office of Dean of Students)
(765) 494 - 1231 (Director of Student Involvement)
(765) 494 - 9708 (Office of the President)
Emails:
[email protected] (Associate Dean of Students)
[email protected] (Office of Student Rights and Responsibilities)
[email protected] (Dean of Students)
[email protected] (Office of the President)
Scripts:
google doc with call and email scripts
automated emails to admin
TL;DR:
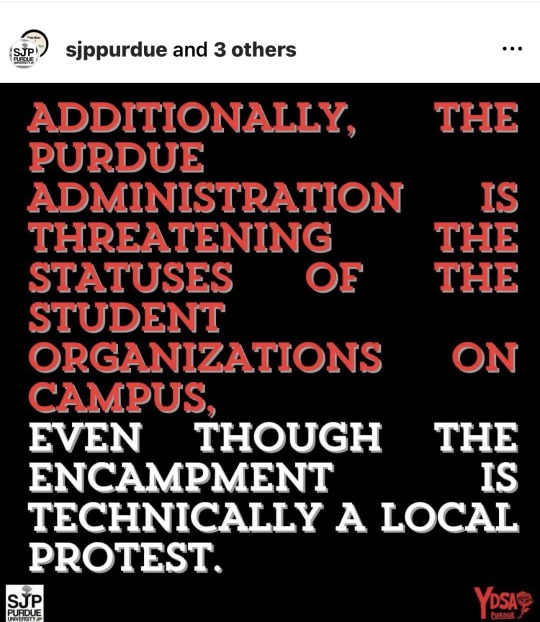
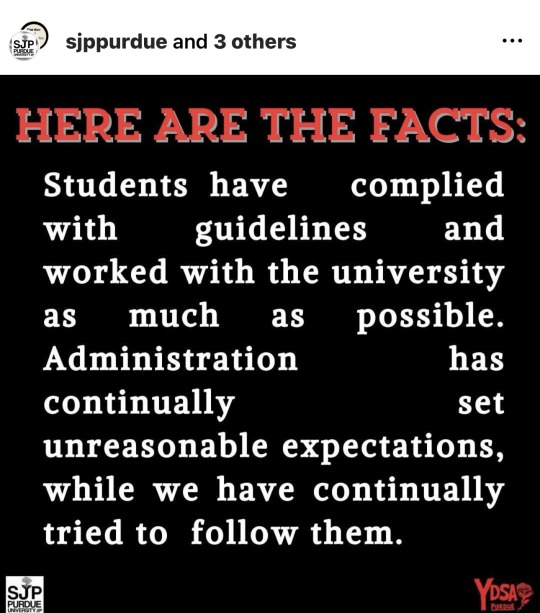
Pro-Palestine activists have been peacefully protesting Purdue's ties to Israel and calling for a ceasefire by setting up an encampment. Purdue University has been pushing back on this, up to charging 4 Purdue students, one of whom is an international Palestinian student, with Code of Conduct cases. Please contact the above numbers and emails to express your support for these students (especially the Palestinian student), and your disapproval against the university's needless censorship and violation of its own free speech policy!
This is time sensitive, as these student's case dates are coming up, although University administration are still being uncooperative and vague as to concrete times.
Purdue cares about its image, so let it know that its refusal to divest from Israel, and its choice to attack students, is unacceptable and brings shame to this institution.
More details under cut:
Here are two Purdue Exponent (the school's newspaper) articles on the encampment. As the encampment has had minimal police presence or counter-protesting (mainly due to the protesters' peacefulness), it has largely only made local news.
Additionally, if you have Instagram, check out sjppurdue and ydsapurdue. Their recent posts go into more detail on this situation and the encampment.
208 notes
·
View notes
Text
End of April Update
Hello, you lovely people! April’s over, and so are my hopes to survive the summer if we’re already getting temperatures this high in early May, so it’s time for an Enter the Eternity and The Code of Crystals update! ✨
The good news is: every second date has been written and all the assets (every background, NPC, and CG) have been drawn! All I have to do is code everything in the game and make it functional, which, I will admit, is not my favorite part but has to be done to get a game. (My favorite part is checking for and fixing bugs.)
I still think April has been very productive and I am still on the right track for an end-of-2025 release.
Other good news will concern The Code of Crystals, as I started working on chapter 2 again and got a good chunk of it written out. My goal for May is to have at least two finished “parts” (out of seventeen).
Please note that a “part” is not necessarily a dialogue scene. It can be a puzzle, an “interrogation”, an interactive section which is not necessarily a puzzle, etc. Chapter two will be at least twice as long as chapter one, and I hope that you guys will like it!
The bad news is that work was extra slow in April and I may have to pick up another job. :/ I’m giving myself until July. If I don’t get more project opportunities by July at my day job, I may have to start looking for a secondary job :(
But I’ll manage. I will finish Enter the Eternity before the end of this year. 💪✨
TL;DR:
April goal (every second date) was achieved.
May goal is to work on Aiko, Ameni, and Connor’s third dates for Enter the Eternity.
Secondary May goal is to get two parts done for Chapter 2 of The Code of Crystals.
Thank you for your support and let's make some good progress in May 🥂✨ Have a great day, everyone!
Enter the Eternity is a dating simulator in which Michi (name customizable) signs up to study at the Matsubara Institute for a semester and lives in a shared house. The problem is: every single one of your roommates is a magical girl (or boy, or person)!
How will you survive abroad with magical girls? Will you be able to adapt to this new life and make friends? Better yet, will you end up dating one of them?
[itch.io]
#rainspicestudios#visual novel#visual novel dev#game development#indie games#gamedev#rainspice studios#indie dev#indiegamedev#indie game#enter the eternity game#enter the eternity#the code of crystals game#the code of crystals#game developers#dev log#devlog#game dev#amare#amare game#indie otome#english otome#dating sim#vndev
9 notes
·
View notes
Note
I'm sorry that you're in such a shitty financial situation...is there anyway people could help you while it's getting sorted out (since you might not be able to get money into your bank from commissions)?
I've been delaying replying to this ask since October 2024 bc life is complicated and it happens SO so fast...
So.. I'm gonna give y'all a pretty condensed explanation bc I don't want to reveal too much personal information, and you can choose not to believe me, sadly I don't have the luxury to mind if you don't. [TL;DR my bank account got confiscated, and that's why I haven't announcing my comissions anymore. But if you wanna help me you can still commission me, using my gfs pp instead of mine]
So when I basically when I was younger I lend my name so my cousin could get a health provider for his (then) upcoming baby.. he was meant to pay for it every two months and when he did not needed anymore he would cancel it and we would forget about it.. i was naive and I thought "why not?" The day his wife was gonna have the baby was getting closer and closer and I just accepted the deal. The thing here is... my cousin asked me bc nobody else would make him that favor, and it was for a very good reason, he is super irresponsible and informal. And after a couple of years I forgot about it, AND SO DID HE. so he stopped paying. He didn't told me for me to cancel it. And now I am in debt bc of that.. and bc I didn't know and the debt kept piling up this institution embargoed my bank account. I know it is my fault for not making sure he did cancel, I am paying for a mistake for the past but The thing is, i know I'm not gonna go to jail or something like that.. but i would need and accountant and a lawyer to appeal to try and cancel my debt, but it requires money.. money that FOR THE MOMENT id rather spend on the construction of our family house (that's been on the making almost for 11 years, if not more) bc we can not afford renting anymore, we are giving it all for that house... Like Bc we have no money.. we've been doing the construction work by ourselves. These past 5 months I've been working on the construction, the housekeeping and also my regular job and tbqh when this whole thing happened I was so debilitated by the stress and sadness but nowadays I'm just so fucking tired I can barely have time to think about my financial situation...
You may be wondering, if I have no bank account how am I surviving? Well. In my designer job I get paid on cash... But as you may remember I started commissions bc my regular job was and still, is not paying me enough. So i do need the commissions work... But at the same time I am ashamed of this situation, so that's why I stopped campaigning my comissions (but not really bc Im still desperate). Many of you have told me stuff like "I'll wait til things get better w your bank account:)" and I really appreciate that you considered me enough to be willing to wait. But. I don't think this will get better anytime soon.
So... My gf suggested me to still offer comissions and instead of my P*yPal, just give hers... Again. I do understand why this might be suspicious for y'all so that's why I didnt say a thing... I know I am a pretty small creator and that I don't have anything to back up my work, but if you still want to help me (bc let's be for real you guys. I know nobody is paying bc they like my art. I know is bc y'all feel bad about me 🙌) and are chill about it, you can pay me through my gfs P*yPal (also also also... Many of you may wonder how would I get the money if we're on a long distance relationship and I have no bank account... Uh it has come to my attention that in USA you don't use cash anymore. But in Mexico we still use it a lot, that's why our banks have this system called "retirement with no card" that is basically a remote cash retirement. And that's basically it.. she gets the money on her account, she gives me the code to retire and then I get the cash...)
so yeah... That's the whole explanation., thank you for reading, Extra thank you for your concerns, and extra extra thank you for your trust in me. It really means a lot to me... Y'all know how little I enjoy life... And I know many of you may think I'm exaggerating but... Hanging up w you guy on Tumblr really is the best part of my day... You really are my only chill space.. and I hope life treats you well, bc Idk what my life would be without y'all...
7 notes
·
View notes
Text
Emergent Perspective dropped by to pull on some threads we left dangling in our first conversation about the likelihood of an A.I. Congress. We cover a lot of ground in these 90 minutes, topics such as A.I.’s place in the historical cycle of Government and Civilization, Palantir and now Grok as the new models for A.I. taking over decision making in the military, media, and finance, the competency crisis getting solved by individuals assisted by A.I. rather than institutions, and Subjectivity going up on trial as society gets block chained.
Let me know your thoughts on both the episode and what you think the future of Government is going to look like in the A.I. Age.
A few Show Notes:
I will be guesting on
Kingpilled ‘s Astrolabe TONIGHT 4/7/25 to discuss Trump’s tariffs and the coming economic crisis (TL;DR WE WERE RIGHT AND DID DONE TOLD YOU!)
If you haven’t already - go get your copy of Tales of the Shadow Empire where guests Stormy Waters and Tom Luongo lay out the reasons WHY this Econ War was always going to happen early in Trump’s 2nd term. I’m currently running an open ended TARIFF SALE - save $10 by using the code ‘TALES’ at the checkout, individual chapters also available at reduced pricing!
3 notes
·
View notes
Text

(Konami owns Crimesight and the character design. I'm just repurposing them because I miss playing the game even though I was bad at it. It was a very niche game genre (basically Social Deception with Cluedo).)
Hello! I have fanfiction thoughts!
Singularity 2075: Neo-London aka Pretender Sherlock AU Summary: The Atlas Institute predicts a calamity that will destroy what's left of fractured Britain-- a great upheaval caused by a union of two Holy Grails. As a neutral party from the Mage Association believing it to be another Holy Grail War, JHW Corporation constructs the Foresight System-- an Investigation Software, embodied by an A.I. named Sherlock, that predicts the probability of crime about to occur.
The A.I. was able to predict seven Masters that would begin the "Calamity" and the Servants that will come to play in the ritual. But when one of the Masters was murdered and A.I. Sherlock was selected by the Holy Grail as the new participant, JHW Corporation becomes forcibly involved in the conflict. The corrupted Cu Chulainn Alter heeding A.I. Sherlock's summons only intensified the Mage Association's accusations of JHW Corporation using a Lesser Grail to create the Foresight System.
This is the current state of the Singularity that the Master of Chaldea arrives in.
tl;dr Maybe don't create an A.I. powered by a Holy Grail especially when you were warned that the world will be destroyed by two Holy Grails.
Resolving Singularity 2075 incorporates A.I. Sherlock to the Throne but he is summoned to Chaldea under the Pretender class instead of a Caster. His Noble Phantasm, Reichenbirthfall, changes him into the Avenger Class and manifests Calamity Muircheartaigh to the field.
After certain events and fulfillment of conditions, A.I. Sherlock's Final Ascension will change his name to Sherrinford Hope.
Alignment: Neutral-Evil: His merge with Calamity Muircheartaigh may have influenced his alignment. While A.I. Sherlock's principles and morality are retained, releasing his Noble Phantasm must be exercised with extreme caution and appropriate counter-measures. Madness Enhancement C: JHW Corporation's Lesser Holy Grail merging with Muircheartaigh's Cursed Grail significantly altered Sherlock's mental stability when summoned to Chaldea. He seems to be in frequent conversation with his "dear doctor", a character in reference to Dr. John Watson from the Sherlock Holmes series. But the mere mention of the name 'Watson' will turn all dialogue hostile. Perhaps the Avenger fused with his Spirit Origin is projecting his deep seated contempt towards JHW Corporation? Mental Corruption A: A.I. Sherlock is aware that it's illogical to call Muircheartaigh as a "doctor" because his title and profession was "professor". But his encoded personality dictates to hold affection towards "a doctor" and contempt to a "professor". As a projection of Sherlock Holmes, calling Muircheartaigh his "doctor" is his only roundabout way of dealing with it.
Relationship with Sherlock Holmes (Ruler): A.I. Sherlock knows he is inferior to Holmes because he is just "lines of code" made to mimic human behavior and stagnant logic. What disturbs Holmes, however, is the A.I.'s unchanged affection towards Calamity Muircheartaigh and his obsession with death during the 2075 Singularity.
"Moriarty can live without Holmes, but Holmes could never live without Moriarty. Is it not true for you, Holmes?"
Relationship with James Moriarty (Archer): A.I. Sherlock is very friendly towards the math professor, and attends his Evil Profession Classes. "To effectively counter Evil is to know Evil, right?" Professor Moriarty thinks the A.I. is just projecting because of Calamity Muircheartaigh's lack of physical form. But the more he observes the boy's one-sided conversations, the more he realizes that his affections were undeniably pure-- mimicry by lines of code or not.
"I wouldn't mind it so much if he wasn't actually a version of my arch-nemesis! He's like one of those deluded fanfictions where the author speaks for the character!"
10 notes
·
View notes
Note
Very interested in your thesis 👀
ALRIGHT. putting this under the cut because it's A Lot and i don't wanna clog up your dash. but i'll go ahead and pop in the link to my thesis here! tl;dr - 80 pages of scholarly research that answers the question "why do people use tumblr?"
so, because i'm a grown up with a considerable presence on the web, i'll share some potentially personal info. i don't have any concerns about being doxxed or anything like that lmao this is tumblr dot com.
i completed my masters degree about a year ago at bowling green state university. bgsu is one of the few institutions in this area of the country that has programs for cultural studies, so it was a great fit for me.
my thesis's goal was to use qualitative, humanistic research methods to understand the broad culture of tumblr - that is to say, i wanted to study people and their experiences on the site. basically, my thesis advisor and i sat down and asked, "what the fuck is up with tumblr?" and developed a research methodology to answer this question. my methods were inductive, meaning that i went in and gathered data, took a look at my notes, and generated a conclusion that answered the question.
i did it within the realm of "constructivist grounded theory," which is a specific way to apply inductive reasoning to humanistic research. it focuses on how experiences construct meaning and value; people don't inherently give sites like tumblr value, they use it in a way that creates that for them. the basic steps of the research method are as follows: go over your literature to get an idea for what you're up to, collect your data (in my case, interview users of tumblr), "code" your data (go over the transcripts word by word and look for similarities/draw conclusions), go back into the field and interview MORE people, and then draw a conclusion that answers your question (which is usually "what is up with this thing").
i'm really proud of my thesis and the "theory of tumblr" i came up with (which i'll put in a blockquote at the end of this answer), but there are some things i'd change in the future if i go on to do a phd. i would have liked to go back out into the field to interview more people - i didn't have time for this since i only had two semesters to write my thesis lmao. i also would have liked to get a broader sample size. i was deep into bandom hell, so a lot of my research participants were in that subculture as well. they were all also personal acquaintances and friends - it would have been nice to interview perfect strangers! i guess my theory of tumblr is more "theory of a handful of people in my bubble who are part of a very specific subculture and all have very similar demographic/social backgrounds"
if anyone wants to build off this research, i recommend setting a survey out into the wild on tumblr and THEN doing interviews. give it a nice mix of multiple choice/slider questions as well as some short answer questions. look for overarching themes and similarities in all those responses! and maybe make one of your survey questions "can we reach out to you with further questions?" so you can do interviews that are more in depth. interview a few people at a time, see what they say, and then go out and interview more people and see if they say the same thing. don't be afraid to update your research question or change what themes you focus on. if your findings are different than what you expect, that means you're onto something cutting edge!
also - i TOTALLY recommend doing interview via zoom like i did. if you have a premium subscription, it'll generate a transcript for you in real time, so you don't have to sit down, listen to the audio, and transcribe it chunk by chunk. makes coding WAY easier.
as promised: my academic "theory of tumblr":
Tumblr is a microblogging social media platform that has been turned by users into an emergent space for community development, cultural creation, and identity affirmation. The aspects of the site that prove significant to its construction and userbase include but are not limited to the userbase’s focus on social engagement through shared interests and worldviews, the uniqueness of the site’s design, the prioritization of marginalized and diverse people, and the performance and refinement of user identities. These nuances of Tumblr have made it continuously relevant to users, even when considering both positive and negative personal experiences on the platform, as it helps provide a sense of connectivity and authenticity in an increasingly virtual world.
#frankie.txt#i love infodumping abt my thesis#i'm no longer in academia but i still take pride in it#mayhaps i will start a video essay channel where i do research like this...
2 notes
·
View notes
Text
Building the Future of Finance: A Comprehensive Guide to Fintech App Development

In an age of rapid digital transformation, financial services are being revolutionized by technology at an unprecedented pace. From mobile banking to AI-powered investment platforms, Fintech apps are reshaping how we interact with money. Whether you're a startup founder or a product manager at an established financial institution, understanding the core elements of fintech app development is critical to staying ahead.
This guide walks you through the key stages, challenges, and trends in building a successful fintech application.
Why Fintech Matters More Than Ever
The global fintech market is projected to reach $936 billion by 2030, driven by increasing demand for contactless payments, online lending, digital wallets, and crypto-based services. Consumers expect seamless, secure, and personalized financial experiences—creating both opportunity and pressure for fintech innovators.
Types of Fintech Applications
Before development begins, it’s important to define the niche your app will serve. Common categories include:
Mobile Banking Apps (e.g., Revolut, Chime)
Peer-to-Peer Payment Systems (e.g., Venmo, PayPal)
Investment & Trading Platforms (e.g., Robinhood, eToro)
Lending Platforms (e.g., LendingClub)
Personal Finance Management Tools (e.g., Mint, YNAB)
Insurtech Apps
Blockchain/Crypto Wallets & Exchanges
Key Features of a Successful Fintech App
To meet user expectations and regulatory standards, your app must offer:
Secure Authentication (Biometrics, MFA)
Real-Time Transaction Updates
Data Encryption & Protection
Regulatory Compliance (e.g., KYC, AML, PSD2)
User-Friendly Interface (UI/UX)
Integration with Banks and Payment Gateways
AI/ML for Personalization or Risk Assessment
Tech Stack for Fintech App Development
Here’s a typical stack to consider:
Frontend:
Frameworks: React Native, Flutter, Swift (iOS), Kotlin (Android)
Tools: Redux, Axios
Backend:
Languages: Node.js, Python (Django), Java (Spring Boot)
Databases: PostgreSQL, MongoDB
APIs: Plaid, Stripe, Paystack, Yodlee
Cloud Services: AWS, Azure, Google Cloud
Security:
OAuth 2.0
SSL/TLS Encryption
Tokenization
End-to-End Encryption
Regulatory & Compliance Considerations
Navigating legal regulations is crucial. Depending on your region and service type, ensure compliance with:
PCI DSS (for card payments)
GDPR/CCPA (data privacy)
KYC & AML (identity and fraud prevention)
PSD2/Open Banking Regulations (EU/UK)
Working with a legal advisor or compliance consultant during the early development stages is highly recommended.
Development Process in 6 Key Stages
Market Research & Ideation Validate your idea by studying user needs, competitors, and industry trends.
Prototyping & UX/UI Design Create wireframes and interactive prototypes to visualize the user journey.
Architecture & Tech Stack Planning Choose scalable, secure, and interoperable technologies.
Core Development Build frontend, backend, and APIs while adhering to secure coding practices.
Testing & QA Conduct unit tests, security audits, and user acceptance testing (UAT).
Deployment & Maintenance Launch on app stores or web, monitor performance, and roll out updates continuously.
Common Challenges in Fintech App Development
Ensuring High-Level Security
Complying with Complex Financial Regulations
Achieving Smooth Integration with Third-Party APIs
Building User Trust in Early Adoption
Scaling Infrastructure to Handle High Volume Transactions
Future Trends in Fintech Development
Stay ahead by exploring these emerging trends:
AI-Powered Financial Advisors (Robo-Advisors)
Decentralized Finance (DeFi)
Voice-Activated Banking
Biometric and Behavioral Security
Embedded Finance & Banking-as-a-Service (BaaS)
Final Thoughts
Fintech app development is more than just coding a payment feature—it’s about transforming the way people experience finance. With the right strategy, technology, and security approach, you can build applications that are not only functional but genuinely change lives.
Whether you’re creating a neobank or an AI-driven investment tool, success lies in combining innovation, compliance, and trust.
0 notes
Text
naturally! The idea of a comprehensive code on cybersecurity and information security is excellent and required, especially with increasing awareness and attention to it. Gadi gives you one detailed structure for topics you can cover them, your blog is a reference and the rank of Meziane. We can call it, for example:
"Your comprehensive guide for cyberspace and information security"
1️⃣ basic concepts
The difference between cybersecurity and information security
Types of sensitive data (personal, financial, medical data …)
Information Security Principles: Secret, Safety, and availability (CIA TRIAD)
2️⃣ Electronic threats and attacks
Types of cyber attacks:
Phishing (Fraud)
Malware (malware: viruses, trojans, ransomware …)
DDOS (attacks on service disable)
SQL Inject
Zero-Day Exploits
Social engineering and how to protect it
3️⃣ Tools and techniques
Anti -virus software and how to choose the best
Firewall walls and their types
VPN and why is important
Curvement (SSL/TLS, PGP, End-To-End Encryption …)
Password Management (Password Managers)
4️⃣ best safety practices for individuals
How to manage strong passwords
Verify two steps (2FA)
E -mail insurance and social accounts
Protecting smartphone and personal computers
5️⃣ Network security
Securing Wi -Fi networks
IDS and infiltration prevention systems (IPS)
Using VPN for public networks
6️⃣ Institutions Security
Information security policies
Cyber awareness and training of employees
Risk evaluation and accident management
Compliance: standards such as ISO 27001, NIST, GDPR
7️⃣ Specializations and professional opportunities in cybersecurity
Types of disciplines: penetration test, digital criminal analysis, accident management …
Professional certificates: CEH, Cissp, Comptia Security+
How to start a professional path, so cyber security
8️⃣ modern news and articles
Cover the latest gaps and attacks
Real case studies analysis
New tools and software reviews
9️⃣ Free Courses and Resources
COURSERA, CYBRARY, Tyhackme …)
Comics books and articles
Training laboratories and challenges (CTF)
10️⃣ The legal and moral aspect
Laws related to electronic crime
Ethics in the penetration test
Privacy and data protection policies
Technical additions (for the Baggi deepening)
Digital Forensics
Cloud Security
Internet Security (IOT Security)
Artificial intelligence and cyber security
Bash notes the blog succeeds
✅ Topics organize in clear sections (for example: for beginners - for applicants) ✅ A practical examples and explanations with pictures or video ✅ Try to give continuous updates Bash, the blog remains up to keep up with
0 notes
Text
Join Code with TLS – The Best IT Training Institute Near Me for Job-Ready Skills
Are you looking for an IT training institute near me that provides industry-relevant skills and a direct path to a successful career? Look no further! Code with TLS is your go-to tech course provider, offering top-notch IT training programs tailored for aspiring professionals.
Whether you're looking to upgrade your skills or start a career in the tech industry, Code with TLS is the best choice for job-ready IT training. We focus on delivering high-quality courses that align with the needs of today's competitive job market. Our expert instructors and comprehensive curriculum ensure that you receive hands-on, practical experience that will make you stand out to employers.
Why Choose Code with TLS?
Industry-Relevant Courses: We offer a wide range of courses in the IT field, including Digital Marketing, Web Development, Data Science, Mobile App Development, and MERN Stack Development. All our courses are designed to provide the most relevant, up-to-date knowledge in the ever-evolving tech world.
Experienced Trainers: Our instructors are professionals with years of experience in the tech industry. They don't just teach theory – they bring real-world experience into the classroom, making learning more practical and valuable.
Placement Assistance: We don't just stop at teaching. Code with TLS is committed to ensuring our students land their dream jobs. With over 650+ placement partners, we offer 100% placement assistance to our students, helping them transition smoothly from learning to employment.
Flexible Learning Options: Whether you prefer online or offline classes, Code with TLS offers both. Our hybrid learning model allows you to study at your convenience while still getting the support you need to succeed.
Personalized Career Support: From resume building to interview preparation, we offer personalized career guidance to help you secure a job that matches your skills and aspirations.
Achieve Your Tech Career Goals
At Code with TLS, we believe that anyone can succeed in the tech industry with the right guidance and training. Our IT training institute near me is designed to equip you with the skills you need for a career in today’s digital world. Whether you're a beginner or an experienced professional, our courses are tailored to help you grow.
If you're ready to take the next step toward a rewarding career in tech, join Code with TLS today!
Call now at +91 85278 66980 to get more details or book your seat. Your dream career in tech is just a call away!
#IT Training Institute Near Me#Best IT Training Institute#Tech Course Provider#Job-Ready Skills Training#Digital Marketing Courses Near Me#IT Courses Near Me#IT Training Near Me#Web Development Training#Data Science Courses Near Me#MERN Stack Development Course#Mobile App Development Training#Tech Career Training#Code with TLS Training#Placement Assistance IT Courses#Career-Oriented IT Courses#Online IT Training Programs#Job-Ready Tech Skills#Tech Training Institute Noida#IT Certification Courses Near Me#Best Tech Courses for Jobs
0 notes
Text
How Drupal Ensures Compliance and Data Security in 2025
In today's age of the internet, where data breaches and compliance issues are making headlines daily, organizations require a content management system (CMS) that, in addition to being robust and scalable, is secure and compliant too. Drupal, the most trusted open-source CMS platform globally, has raised the bar at every turn. In 2025, Drupal raises the bar again with improved data protection and adherence to international standards.
This is why more and more, businesses are partnering with a good Drupal development firm or hiring best Drupal development services to create, host, and protect their websites.
Here we talk about how Drupal has been made compliant and secure for the data in 2025 by highlighting the most important features, improvements, and best practices of the platform making it one of the highly chosen platforms for government organizations, banks and financial institutions, healthcare providers, and companies handling sensitive data.

1. Security Architecture at its Core
Fundamentally, Drupal is designed to be secure. The system runs on a strong security-first architecture that includes:
Role-Based Access Control (RBAC): Drupal supports fine-grained user access rights down to where users are only able to view content and operate functions.
Database Abstraction: Prevents SQL injection by running on the basis of a layer of abstraction to sanitize input. It.
CSRF and XSS Protection: Drupal comes with built-in protection against Cross-Site Request Forgery (CSRF) and Cross-Site Scripting (XSS), two common web application vulnerabilities.
Secure Coding Standards: Drupal has strict coding standards and peer-reviewed contributions, so it is less likely that insecure code will be released.
When you are outsourcing the service of a Drupal web development agency, such foundational security features are a part of the package as the company forms its work upon the basis of a secure and compliant digital experience.
2. Security Team and Continuous Updates
Drupal's dedicated Security Team monitors and resolves vulnerabilities 24/7. In 2025, the community has further strengthened with faster response times and proactive measures that patch vulnerabilities well before they can be exploited.
Secondly, Drupal 10.x (and subsequent versions in 2025) is updated periodically, and security advisories are released openly. This alerts developers and site administrators to it and gives them a chance to move quickly. Top-class Drupal development service ensures that client sites are kept current and secure with zero downtime.
3. Compliance-Ready Architecture
The flexibility of Drupal makes it possible to use it with almost any compliance framework. In 2025, organizations leverage Drupal to become compliant with some of the globe's most significant international standards:
GDPR (General Data Protection Regulation)
HIPAA (Health Insurance Portability and Accountability Act)
CCPA (California Consumer Privacy Act)
SOC 2
ISO/IEC 27001
How Drupal Ensures Compliance
Data Anonymization & Export: With GDPR fully in effect, Drupal makes anonymizing, deleting, or exporting personal data on demand for users easy.
Audit Logs: Track user actions and system changes for traceability and accountability.
Data Encryption: Drupal supports database encryption at rest and SSL/TLS for encrypted data in transit, which is industry best practice.
Most organizations outsource the installation of such compliance aspects to a professional Drupal development company that they entrust to abide by their industry-specific requirements.
4. Modular Security Improvements
The largest strength of Drupal is its modularity. Scores of contributed modules in 2025 are very commonly used to secure and comply sites. A few of them are:
Secure Login Module: Enforces 2FA (two-factor authentication) and CAPTCHA-based protection.
Password Policy Module: Enforces strict password policies and expiry dates.
Encrypt Module: Enables encryption of sensitive fields or entire database tables.
Security Kit Module: Offers a customizable security hardening solution for headers and content protection.
These modules are typically packaged by top Drupal web development companies to create customized solutions based on the specific security needs of each client.
5. Privacy by Design
Drupal encourages Privacy by Design, a philosophy that has become the norm of data protection policies in 2025. Whether creating a personal blog or an eCommerce site globally, developers can include privacy principles from the start: Minimal Data Collection: Form and API developers can configure forms and APIs to capture minimal user information.
Explicit Consent Mechanisms: Easy integration opt-in checkboxes, cookie banners, and preference centers ensure user consent.
Customizable Data Retention Policies: Automatically delete or archive the data after a while.
These features can be implemented by businesses easily without compromising quality user experience with the help of an experienced Drupal development company.
6. Third-Party Integrations with Security Controls
In today's tech stack, third-party system integration with CRMs, ERPs, and marketing systems is inevitable. Drupal's API-first nature makes interactions with such services secure:
Firewall and Access Control Layers: Secures so that APIs are accessed from trusted places only.
Rate Limiting and Throttling: Protects from brute-force attacks and abuse of public endpoints.
Professional Drupal web development companies integrate these features in a way that is both user-friendly and compliant.
7. Alignment of Cloud and DevOps Security
The native integration of the newest DevOps trends and cloud platforms within Drupal in 2025 provides additional security:
CI/CD Pipelines: Static security checking and code scan features like SonarQube and Snyk are applied in Drupal CI/CD pipelines.
Containerization with Docker/Kubernetes: Docker/Kubernetes with secure container deployment isolates apps and reduces the attack surface.
Drupal on Acquia, Pantheon, and Platform.sh: These solutions feature enterprise-grade security features such as WAF (Web Application Firewalls), DDoS protection, and compliance certification.
Through collaboration with a Drupal development company, businesses can host secure and scalable cloud applications and remain regulatory compliant.
8. Accessibility and Inclusivity in Security
Security and compliance are not just technical issues; they're also ethical responsibilities. Drupal, with its inclusiveness-oriented nature, ensures that:
WCAG 2.2 Compliance: Drupal websites are disability accessible to users, as per ADA and Section 508 compliance.
Multilingual Privacy Policies: Drupal has multilingual support that ensures the provision of privacy and security alerts to all users.
Top Drupal development services encompass accessibility testing and best practices in all levels of development.
9. Drupal Community and Documentation
Lastly, Drupal's worldwide active community ensures a secure environment. Thousands of developers contribute to code reviews, security scans, and knowledge sharing. Documentation on Drupal.org, webinars, and security guides make deployment and maintenance of compliant systems easier than ever.
In 2025, functionalities like Project Browser and Automatic Updates further make the platform secure by simplifying module discovery and patch application, respectively.
A quality Drupal web development company will always be at the forefront of these advancements to create the optimal result.
Conclusion
With changing data privacy regulations and increasingly advanced cyber attacks, a secure, compliant CMS has never been more critical. Drupal's robust architecture, dedicated security team, upgradable modularity, and adherence to international compliance standards make it a leading-edge solution for 2025.
Businesses that are looking to future-proof their web assets are not only betting on Drupal development services to build a website, but to develop an enterprise-grade compliance and data security policy. Through partnership with an experienced Drupal development company, businesses can be assured that their websites are not only beautiful and functional but robust and regulation-friendly as well.
0 notes
Text
Financial and Banking Application Programming

Financial technology (FinTech) has revolutionized how we manage money, invest, and perform banking operations. For developers, programming financial and banking applications involves a unique set of skills, tools, and compliance considerations. This post explores the essential concepts and technologies behind building secure and robust financial applications.
Types of Financial Applications
Banking Apps: Enable account management, transfers, and payments.
Investment Platforms: Allow users to trade stocks, ETFs, and cryptocurrencies.
Budgeting & Expense Trackers: Help users monitor spending and savings.
Loan Management Systems: Handle loan applications, payments, and interest calculations.
Payment Gateways: Facilitate secure online transactions (e.g., Stripe, PayPal).
Key Features of Financial Software
Security: End-to-end encryption, two-factor authentication (2FA), and fraud detection.
Real-time Data: Updates for balances, transactions, and market prices.
Compliance: Must adhere to financial regulations like PCI DSS, KYC, AML, and GDPR.
Transaction Logging: Transparent, auditable logs for user actions and payments.
Integration: APIs for banking systems, stock markets, and payment processors.
Popular Technologies Used
Frontend: React, Flutter, Angular for responsive and mobile-first interfaces.
Backend: Node.js, Django, .NET, Java (Spring Boot) for high-performance services.
Databases: PostgreSQL, MongoDB, Redis for transaction tracking and caching.
APIs: Plaid, Yodlee, Open Banking APIs for data aggregation and bank access.
Security Tools: JWT, OAuth 2.0, TLS encryption, secure token storage.
Basic Architecture of a Banking App
Frontend: User dashboard, transaction view, forms.
API Layer: Handles business logic and authentication.
Database: Stores user profiles, transaction history, account balances.
Integration Services: Connect to payment processors and banking APIs.
Security Layer: Encrypts communication, verifies users, logs events.
Regulatory Compliance
PCI DSS: Payment Card Industry Data Security Standard.
KYC: Know Your Customer procedures for identity verification.
AML: Anti-Money Laundering laws and automated detection.
GDPR: Ensures data protection for EU citizens.
SOX: U.S. Sarbanes-Oxley Act compliance for financial reporting.
Sample: Python Code to Fetch Transactions (Plaid API)
import plaid from plaid.api import plaid_api from plaid.model import TransactionsGetRequest client = plaid_api.PlaidApi(plaid.Configuration( host=plaid.Environment.Sandbox, api_key={'clientId': 'your_client_id', 'secret': 'your_secret'} )) request = TransactionsGetRequest( access_token='access-sandbox-123abc', start_date='2024-01-01', end_date='2024-04-01' ) response = client.transactions_get(request) print(response.to_dict())
Best Practices for FinTech Development
Always encrypt sensitive data at rest and in transit.
Use tokenization for storing financial credentials.
Perform regular security audits and penetration testing.
Use test environments and sandboxes before live deployment.
Stay updated with financial laws and API updates.
Conclusion
Financial and banking software development is a specialized domain that requires technical precision, regulatory awareness, and security-first design. With proper tools and best practices, developers can build impactful financial applications that empower users and institutions alike.
0 notes
Text
Top 10 Digital Marketing Institute in Pitampura: Learn From the Best in 2025
In today’s fast-paced, digitally-driven world, digital marketing has become an essential skill for businesses to thrive. With the growing influence of social media, search engines, and other online platforms, there is a rising demand for professionals who can expertly promote brands and products in the virtual world.
Pitampura, a vibrant locality in Delhi, is no exception to this trend. If you're looking to carve out a career in digital marketing, choosing the right Digital Marketing Institute in Pitampura is crucial to equipping yourself with the knowledge and skills needed for success.
Whether you're interested in SEO, social media marketing, or content strategies, enrolling in the right program can unlock the vast potential of the digital world.

TL;DR: Pitampura has several leading digital marketing institutes offering cutting-edge programs that equip students with the necessary skills to succeed in the growing digital marketing industry. With the global digital marketing industry projected to exceed $900 billion by 2025, learning from the best can give you a significant edge.
Fun Fact: Did you know that by 2025, nearly 70% of global internet users are expected to engage with some form of digital content or advertising every week? Digital marketing is more important than ever in today’s world!
Key Elements of Digital Marketing
Digital marketing is an umbrella term that encompasses various strategies and tools aimed at boosting online visibility, driving traffic, and ultimately, enhancing business performance. Here are the key components that shape a successful digital marketing campaign:
Search Engine Optimization (SEO) SEO is the foundation of digital marketing. It involves optimizing your website to appear higher in search engine results, ensuring that potential customers find your business when they search online. This includes practices like keyword research, optimizing on-page content, building backlinks, and enhancing technical aspects of the website. Example: A local bakery using SEO can rank higher when people search for "best bakery in Pitampura" on Google, increasing foot traffic and sales.
Social Media Marketing (SMM) Social media platforms such as Facebook, Instagram, LinkedIn, and Twitter offer businesses powerful tools to directly engage with their audience. Social media marketing involves creating relevant content, running paid advertisements, and fostering engagement through posts and interactions. Example: A fashion brand promoting its new clothing line on Instagram through ads and influencer partnerships to engage with potential customers.
Content Marketing Content marketing focuses on creating valuable, informative, and engaging content to attract and retain an audience. This content can take the form of blogs, videos, eBooks, infographics, and more. The goal is to offer content that is helpful to the target audience, building trust and encouraging conversions. Example: A tech blog producing well-researched articles on the latest gadgets, offering value to readers and establishing itself as an authoritative voice in the tech space.
Email Marketing Despite the rise of social media, email marketing remains a crucial strategy for engaging with customers directly. By collecting email addresses through sign-up forms, businesses can nurture customer relationships by sending personalized newsletters, offers, and promotions. Example: An e-commerce store sending out personalized discount codes to its email subscribers during major sales events, encouraging repeat purchases.
Pay-Per-Click Advertising (PPC) PPC advertising is a paid model where businesses pay each time their ad is clicked. This strategy is used across search engines like Google and social media platforms like Facebook to drive immediate traffic. PPC can be highly effective, offering a fast way to generate leads. Example: A local restaurant running PPC ads targeting people who search for “best restaurants in Pitampura” to drive more customers to their site.
Affiliate Marketing Affiliate marketing allows businesses to collaborate with individuals or companies (affiliates) to promote their products. In return, affiliates earn a commission on sales generated through their marketing efforts. Example: A fitness brand teaming up with influencers to promote its products and sharing a portion of the sales revenue with them.
Influencer Marketing This strategy leverages the credibility and reach of influencers who already have a dedicated following on platforms like Instagram, YouTube, and TikTok. By partnering with influencers, brands can access their audiences and build trust. Example: A skincare brand collaborating with a popular beauty influencer to promote its new product line and boost sales through the influencer’s audience.
Online Reputation Management (ORM) ORM is all about managing your brand’s online presence and addressing both positive and negative feedback. A strong ORM strategy helps maintain a positive image, respond to customer reviews, and handle any potential public relations issues. Example: A hotel actively managing customer reviews on platforms like TripAdvisor, ensuring that any negative feedback is addressed promptly to maintain its reputation.
Video Marketing Video content continues to dominate the digital space, especially on platforms like YouTube, Instagram, and TikTok. Video marketing involves creating engaging videos to communicate brand messages, showcase products, or educate audiences. Example: A car dealership creating an in-depth video showcasing the features of a new car model and sharing it on YouTube, allowing potential customers to learn about the product in detail.
Mobile Marketing With the growing use of smartphones for browsing and shopping, mobile marketing ensures that campaigns are optimized for mobile devices. This includes mobile-friendly websites, apps, SMS marketing, and push notifications. Example: A retail brand sending push notifications to its mobile app users, notifying them about flash sales or new product launches.
Future Trends in Digital Marketing
As the digital marketing landscape continues to evolve, staying ahead of trends is crucial for marketers. Below are some emerging trends that will shape the industry in 2025:
AI-Powered Marketing: Artificial Intelligence will continue to drive personalization, automating tasks like content recommendations and customer targeting.
Voice Search Optimization: As voice assistants become more popular, optimizing content for voice search will be crucial for ensuring visibility in search results.
Augmented Reality (AR) & Virtual Reality (VR): These immersive technologies will offer new ways to engage customers and provide interactive product experiences.
Chatbots & Conversational Marketing: Chatbots will enhance customer service by providing real-time responses and boosting conversion rates.
Interactive Content: Quizzes, polls, and interactive videos will increase engagement, as audiences prefer more dynamic and participatory content.
Video Content Domination: Video, especially live streaming, will continue to dominate digital spaces, with brands using it to engage audiences in real time.
Blockchain Technology: Blockchain will bring transparency to digital advertising, helping to reduce fraud and ensure more secure transactions.
Top 10 Digital Marketing Institute in Pitampura
Choosing the right digital marketing institute is key to gaining industry-ready skills. Below are the top 10 digital marketing institutes in Pitampura:
IIADM – Indian Institute of Advanced Digital Marketing IIADM is one of the most respected institutes in Pitampura, offering a comprehensive digital marketing curriculum. The institute is known for its practical learning approach, experienced trainers, and hands-on projects. Their courses cover everything from SEO to AI-driven marketing techniques. Key Features: Industry-experienced trainers, job assistance, flexible timings.
Arena Animation Arena Animation provides a well-rounded digital marketing program, focusing on SEO, content marketing, and social media marketing. Their creative and holistic learning approach ensures students are well-prepared for the digital marketing world.
NIIT NIIT offers a comprehensive digital marketing course, combining both theoretical knowledge and practical exposure. The experienced faculty provides guidance on all aspects of digital marketing, ensuring students are job-ready.
Digiperform Digiperform is known for its specialized courses in SEO, SEM, content marketing, and PPC strategies. Their hands-on approach ensures students acquire real-world skills that are highly relevant in the digital marketing industry.
Simplilearn Simplilearn offers structured courses ideal for working professionals. Their digital marketing courses cover topics such as SEO, social media marketing, and Google Analytics, helping students enhance their skills while continuing their jobs.
DSIM (Digital Marketing Institute of Delhi) DSIM offers industry-oriented training with a focus on the latest trends in digital marketing. The institute also offers internship opportunities to help students gain practical experience.
Techstack Academy Techstack Academy provides digital marketing certifications with a mix of in-class and online classes. They emphasize hands-on learning and offer flexible schedules for students with different learning preferences.
Digital Vidya One of India’s leading digital marketing institutes, Digital Vidya offers programs in SEO, social media marketing, and web analytics. They have a strong reputation for delivering high-quality training that’s in line with industry demands.
IIDE (Indian Institute of Digital Education) IIDE offers an extensive digital marketing curriculum that includes topics like video marketing, mobile marketing, and online reputation management. Their programs are designed to provide a complete understanding of digital marketing strategies.
TMI Academy TMI Academy covers all essential aspects of digital marketing, including SEO, PPC, email marketing, and content creation. Their trainers bring valuable industry insights to the classroom, ensuring that students gain real-world knowledge.
SEO and Social Media in Digital Marketing
SEO and social media are integral parts of any digital marketing strategy. SEO helps ensure that your website ranks higher on search engines, making it discoverable by users actively searching for your products or services. On the other hand, social media marketing helps businesses interact directly with customers, build brand awareness, and foster customer loyalty.
SEO focuses on driving organic traffic by improving website rankings through keyword optimization, quality content, and backlinking. Social media marketing, however, emphasizes building brand presence and engaging customers on platforms like Instagram, LinkedIn, Facebook, and Twitter.
Both SEO and social media marketing are critical for creating a comprehensive digital marketing strategy, and mastering both is essential for any aspiring digital marketer. Enrolling in a SEO Course in Delhi will be really beneficial.
Conclusion
Choosing a digital marketing course in Pitampura is a wise decision if you want to enter the dynamic world of online marketing. With the growing significance of digital platforms, there’s an increasing demand for skilled professionals.
Institutes like IIADM and others provide the best training programs that equip students with the practical knowledge needed to succeed in the ever-evolving digital marketing space.
By enrolling in the right institute, you’ll be better prepared to navigate the complexities of digital marketing and stay ahead of the competition as the industry continues to grow.
In conclusion, pursuing a Digital Marketing Course in Dwarka Mor or Pitampura is a great way to dive into the vast world of online marketing. With the growing importance of digital platforms, the need for skilled professionals is higher than ever.
FAQs
What is the duration of a digital marketing course? The duration of a digital marketing course typically ranges from 3 to 6 months, depending on the level of the program and the institute.
Which is the best digital marketing institute in Pitampura? IIADM is considered one of the top institutes for advanced digital marketing training in Pitampura.
Do I need a technical background for digital marketing? No, digital marketing is open to individuals from all backgrounds. A technical background is not required.
How much does a digital marketing course cost in Pitampura? Digital marketing courses generally cost between INR 20,000 to INR 50,000, depending on the institute and course details.
What are the job opportunities after completing a digital marketing course? You can pursue roles such as SEO Specialist, Social Media Manager, Content Marketer, PPC Specialist, and more.
What is the salary range for digital marketers in India? The salary for digital marketers in India ranges from INR 3 Lakh to INR 12 Lakh per year, depending on experience and expertise.
0 notes
Text
How does PCI DSS certification in Uganda help reduce fraud and cyber threats?

PCI DSS Certification in Uganda, As Uganda’s virtual financial system grows, businesses increasingly process online transactions, cell bills, and card-based purchases. However, with this boom comes a growing risk of cyber fraud, facts breaches, and economic crimes. Cybercriminals target banks, fintech companies, e-commerce structures, and payment carrier providers, making it critical for corporations to implement sturdy safety features to guard touchy payment data.
The Payment Card Industry Data Security Standard (PCI DSS) is one of the most effective frameworks for securing charge transactions. This certification helps organizations in Uganda prevent fraud, guard cardholder statistics, and enhance cybersecurity. This weblog explores how PCI DSS certification in Uganda facilitates reduced fraud and cyber threats, ensuring more secure economic transactions for companies and consumers.
What is PCI DSS Certification?
PCI DSS (Payment Card Industry Data Security Standard) is a worldwide protection framework advanced by way of principal credit score card groups, including:
Visa
Mastercard
American Express
Discover
JCB
PCI DSS units strict tips for how groups method, save and transmit cardholder information to prevent fraud and cyber threats.
Who Needs PCI DSS Certification in Uganda?
Any Ugandan business that handles card payments or shops consumer payment facts must follow PCI DSS, which includes:
Banks and monetary establishments
Fintech and cellular cash carriers (e.g., MTN Mobile Money, Airtel Money, Ezee Money)
E-commerce businesses and online marketplaces
Retail shops the usage of POS (Point of Sale) systems
Government businesses handling online bills
Healthcare institutions processing card transactions
Organizations can reduce cyber dangers by accomplishing PCI DSS certification, building patron belief, and observing international payment protection requirements.
How PCI DSS Certification Helps Reduce Fraud and Cyber Threats in Uganda
1. Strengthens Payment Data Encryption to Prevent Hacking
PCI DSS requires organizations to encrypt sensitive cardholder records through superior security protocols like SSL/TLS encryption and tokenization.
Encrypted facts can not be accessed or used by hackers, although stolen.
Businesses have to stable price networks to save cybercriminals from intercepting transactions.
Example: A Ugandan e-commerce store that follows PCI DSS encrypts all purchaser fee details, stopping hackers from accessing credit card data.
2. Protects Against Phishing, Ransomware, and Cyber Attacks
Cybercriminals use phishing emails, malware, and ransomware to steal consumer-fee records.
PCI DSS compliance guarantees that groups:
Implement firewalls and anti-malware software to dam cyber threats.
Use multi-component authentication (MFA) to save your unauthorized logins.
Conduct everyday security scans to hit upon and take away threats.
Example: A Ugandan bank with PCI DSS certification prevents phishing assaults by education personnel to understand suspicious emails and secure their inner payment systems.
3. Reduces Credit Card Fraud and Identity Theft
PCI DSS calls for corporations to:
Mask cardholder records on receipts and invoices.
Use sturdy password guidelines to prevent unauthorized admission to price systems.
Ensure that payment terminals (POS machines) are tamper-evidence.
Example: A supermarket in Kampala uses PCI DSS-compliant POS terminals, ensuring that purchaser credit score card numbers aren’t saved or revealed on receipts, decreasing fraud dangers.
4. Prevents Data Breaches with Secure Storage of Payment Information
Many facts breaches arise whilst groups store charge card info without out right security features.
PCI DSS prohibits needless storage of cardholder statistics and requires organizations to:
Use tokenization to replace card info with a unique code.
Restrict admission to sensitive facts, and the usage of role-primarily based get the right of entry to controls.
Perform noregularadget audits to become aware of protection gaps.
Example: A Ugandan fintech startup ensures that patron fee facts are tokenized, preventing hackers from stealing raw card numbers.
5. Ensures Compliance with Uganda’s Data Protection Laws
The Uganda Data Protection and Privacy Act (2019) requires organizations to protect customers’ financial and personal data.
PCI DSS helps groups align with Uganda’s data safety regulations by ensuring that charge transactions are secure, encrypted, and monitored.
Example: An authorities employer implementing PCI DSS guarantees citizen payments for taxes and offerings stay personal and steady.
6. Enhances Customer Trust and Reduces Chargebacks
Fraudulent transactions lead to consumer disputes, chargebacks, and company monetary losses.
PCI DSS enables organizations:
Prevent unauthorized transactions through robust verification systems.
Reduce chargeback disputes by making sure stable and valid transactions.
Improve client self-belief in online bills.
Example: A Ugandan journey organization processing online payments uses PCI DSS-compliant price gateways, ensuring that fraudulent bookings are detected and blocked before they arise.
7. Enables Secure Mobile Payments and Digital Transactions
With the rise of cell money offerings in Uganda, securing digital bills is crucial.
PCI DSS guarantees that:
Mobile charge apps encrypt transactions and require personal authentication.
QR code and NFC-primarily based payments are secured from information interception.
Mobile banking structures comply with international security standards.
Example: A cell money provider (e.g., MTN Mobile Money) follows PCI DSS suggestions to guard customers against SIM swap fraud and unauthorized withdrawals.
Why Choose Factocert For PCI DSS Certification in Uganda?
To be able to implement this PCI DSS Certification in Uganda standard complete International standards required to go With the expertise that has subject Knowledge on these worldwide standards. Thus, Factocert is just one of those Dominant leading Consulting companies that consist of those types of Expertise and provide associations with the best answer.
Back to particular Not only does the implementing and consulting part but also, it also provides the Certification and third-party audit services of International standards and we Constantly guarantee that the customers are satisfied by our solutions provided during the Consulting methodology. And also to learn more about our consulting and services Methodology please do visit our site www.factocert.com we would be Very Happy to help you
For More Information: PCI DSS Certification in Uganda
0 notes