#Data Confidentiality
Text

Work Data!
#star trek#star trek tng#tng#star trek the next generation#the next generation#data soong#star trek data#I have to be so careful about doodling at work because we reuse paper and it could have confidential client information on the back#but this piece just has a list of generic child support guidelines on it 😂💛✨#he’s made with ballpoint pen and a dry highlighter =)
60 notes
·
View notes
Note
I just found the demo and it's really neat! I can guess where the other half of my briefing went. 👀 I did run into a possible inconsistency, though, and I wanted to ask about it. Early on MC and the others can have a reputation for what kind of matchmaker they are (for elaborate stories, or high ethics, etc.) ... but how is it possible to achieve a reputation if everything is supposed to be confidential, and if the matchmaker's own memories of everything they did for a case will be wiped each time they finish? And how does that affect Wyatt? How do we take credit or blame for how cases turn out if we can't remember them? Sorry for the rambling - I'm just trying to puzzle out how the process works.
Hey, thank you! Glad to answer the questions.
but how is it possible to achieve a reputation if everything is supposed to be confidential, and if the matchmaker's own memories of everything they did for a case will be wiped each time they finish?
The only things that get wiped entirely are the identifying information about the souls (names, appearances, socials) and the visions. The professional experience that a soul-link builds up is altered in their memory to disconnect it from two particular souls but to still keep it since it's useful. Let's say that for their plan, a soul-link used Empathy to sneak inside a club without being on the invite list to talk to someone. After the case is done, they would still recall this experience, although maybe in the form of "eh, snuck into some rooftop party" or "spoke to some person that was quite tipsy".
Another way to think of it is to imagine them as memories that went through natural absorption and distortion, just much faster and, well, unnaturally.
And how does that affect Wyatt?
I'm assuming you mean the shared case? It was the same for Wyatt. MC has the option to worry about their shared memories if they want to be friends or beyond with Wyatt, but you quickly learn that those were kept intact. They just don't recall each other using the names Selma and Vivian and everything in that orbit.
Hope this clears it up for you!
#soulmatesinc if#asks#infosec breach#this is a confidential data protection policy but soul-link style lmao
24 notes
·
View notes
Text
the way in which this team of apparently highly trained police officers goes about researching their cases is so frustrating. like what do you mean you're only checking whether kao used his phone after he left art's place after you found out he left at all. why did you just. assume. kao died there at the studio. and why has it taken you literal days of thinking of 'hey maybe we should find out if kao has anyone he trusts he can stay with while hiding'. all of these things should be at the top of the list. full phone records, lists of family and friends. you've got a missing person who may or may not be dead and you're just kind of winging the case as you go???
#the sign the series#literally the most frustrating part about this entire series#like it's great that these boys get ton of free time to go hang out and have dinners and whatnot#while working on highly time sensitive confidential murder cases#but also. please read a book or two on forensics.#do NOT even start on the forensics girl#she's cute and I love her but she's terrible at her job#why is she dissecting bodies AND coming to crime scenes to look for evidence#those are separate jobs#'we found fungi in the lungs of the victims' great! well done! what kind of fungi. was it the same one in each victim.#was it one of gazillion types of fungi to show up in houses/basements or one of even more types to show up in forests#also why are these same guys working the case and interrogating suspects also the ones looking for evidence#there's people for that#actually why aren't these suspected crime scenes constantly swarming with officers doing a multitude of jobs#(also on a related note why was tarn fixing up phaya in the ambulance and why was the paramedic just kind of. uh. not there???)#(literally just a dude in a paramedic suit there to close the ambulance and leave lmao)#there's way too much theorizing - and acting on those theories - happening on way too little information#data data data you can not make a brick without clay etc
7 notes
·
View notes
Text
literally how has AI not been banned yet
#i have not seen ONE single good helpful use of AI#like everyone who posts about it is just complaining about it causing more problems....#its stealing from copyrighted work. its plagiarizing essays#work has had to send out 2 separate emails now begging people not to upload research data into AI databases#confidential patient data is being spewed out#there was that whole thing with zoom i saw earlier this week mining video calls for things to upload to ai#today i saw another article about ppl with eating disorders using ai to generate diet plans well below the recommended calorie intake#it has no way to filter when people are using it to harm themselves#AND my friends just linked me to another source from an author who had entire books written under her name with ai#made by some random dude hoping to get easy money from ppl seeing her name associated with the book#please. ban it. kill it. we can think for ourselves i promise it wont kill us#but noooo!! we gotta keep the tech bros and entrepreneurs happy!!
6 notes
·
View notes
Text
i went to an escape room today. it was actually so fun. my damn my brain i tired. we got out though!
#10/10 would highly recommend#i also started making a daiya sorter when i got home but holy shit it’s a lot of data#data*#shout out to ix for helping me out with that!#i didn’t get to watch any ball game today though#but it’s alright#i can watch one tomorrow while i plot in the data for the sorter#manifesting that luigs is going to pitch in the next upcoming game#» confidential
5 notes
·
View notes
Text




[2022 Entertainment survey conducted by Joynews24 Part 3]
Participated by 200 industry officials
Best Couple of the Year (Dramas):
#5 - Lee Jong Suk x Lim #YoonA
Best Chemistry of the Year (Movies):
Hyun Bin x Yoo Hae Jin/ Daniel Henney/ Lim YoonA/ Jin Sun Kyu
7 notes
·
View notes
Text
Discover the Truth with Bond Rees Investigations - Your Trusted UK Detective Agency

Uncover the truth with Bond Rees Investigations, the UK’s leading private detective agency. Our expert team offers discreet and professional services, including private investigations, lie detector tests, tracing services, corporate investigations, and data recovery. With a 98.7% success rate, we ensure confidentiality and accuracy in every case. Trust Bond Rees to provide the answers you need.
#Private Investigations#UK Detective Agency#Lie Detector Tests#Tracing Services#Corporate Investigations#Data Recovery#Discreet Services#Professional Investigators#Confidential Investigations#Missing Persons
0 notes
Text
Translation Services for Clinical Studies and Clinical Reviews
Accurate translation services for clinical studies are crucial for medical research. Precise translations ensure that clinical reviews maintain the integrity and reliability of the original data. Inaccuracies can lead to misinterpretation; compromising patient safety and the efficacy of treatments. Leveraging professional translation services can enhance communication between international…

View On WordPress
#biotech translation services#certified medical translation services#clinical data translation#clinical protocol translation#clinical report translation#clinical review interpretation#clinical study report translation#Clinical study translation#clinical trial translation services#expert medical translators#global health translation services#health care translation certification#Healthcare translation services#informed consent form translation#language services for clinical research.#live captioning for medical conferences#medical document translation#medical interpreter services#medical literature translation#medical research translation services#Medical Terminology Translation#Medical transcription services#medical translation confidentiality#medical translation quality control#medical translation services#multilingual clinical research#multilingual patient consent forms#multilingual transcription for clinical trials#Patient Information Leaflet Translation#patient questionnaire translation
0 notes
Text
youtube
Proactively manage data exposure risks with full visibility into all encryption keys and related data services across multi-cloud environments. Identify hidden risks and compliance gaps and future-proof your data security against the looming post-quantum threat.
Use Key Insight to:
Discover at-risk AWS/Azure data services
Assess security policy and compliance gaps
Remediate corrective actions at scale
#encryption#key management#cloud security#data privacy challenges#data security#data privacy#data security challenges#blockchain#confidential computing#Youtube#Fortanix#key insight
0 notes
Text
How Bias Will Kill Your AI/ML Strategy and What to Do About It
New Post has been published on https://thedigitalinsider.com/how-bias-will-kill-your-ai-ml-strategy-and-what-to-do-about-it/
How Bias Will Kill Your AI/ML Strategy and What to Do About It
‘Bias’ in models of any type describes a situation in which the model responds inaccurately to prompts or input data because it hasn’t been trained with enough high-quality, diverse data to provide an accurate response. One example would be Apple’s facial recognition phone unlock feature, which failed at a significantly higher rate for people with darker skin complexions as opposed to lighter tones. The model hadn’t been trained on enough images of darker-skinned people. This was a relatively low-risk example of bias but is exactly why the EU AI Act has put forth requirements to prove model efficacy (and controls) before going to market. Models with outputs that impact business, financial, health, or personal situations must be trusted, or they won’t be used.
Tackling Bias with Data
Large Volumes of High-Quality Data
Among many important data management practices, a key component to overcoming and minimizing bias in AI/ML models is to acquire large volumes of high-quality, diverse data. This requires collaboration with multiple organizations that have such data. Traditionally, data acquisition and collaborations are challenged by privacy and/or IP protection concerns–sensitive data can’t be sent to the model owner, and the model owner can’t risk leaking their IP to a data owner. A common workaround is to work with mock or synthetic data, which can be useful but also have limitations compared to using real, full-context data. This is where privacy-enhancing technologies (PETs) provide much-needed answers.
Synthetic Data: Close, but not Quite
Synthetic data is artificially generated to mimic real data. This is hard to do but becoming slightly easier with AI tools. Good quality synthetic data should have the same feature distances as real data, or it won’t be useful. Quality synthetic data can be used to effectively boost the diversity of training data by filling in gaps for smaller, marginalized populations, or for populations that the AI provider simply doesn’t have enough data. Synthetic data can also be used to address edge cases that might be difficult to find in adequate volumes in the real world. Additionally, organizations can generate a synthetic data set to satisfy data residency and privacy requirements that block access to the real data. This sounds great; however, synthetic data is just a piece of the puzzle, not the solution.
One of the obvious limitations of synthetic data is the disconnect from the real world. For example, autonomous vehicles trained solely on synthetic data will struggle with real, unforeseen road conditions. Additionally, synthetic data inherits bias from the real-world data used to generate it–pretty much defeating the purpose of our discussion. In conclusion, synthetic data is a useful option for fine tuning and addressing edge cases, but significant improvements in model efficacy and minimization of bias still rely upon accessing real world data.
A Better Way: Real Data via PETs-enabled Workflows
PETs protect data while in use. When it comes to AI/ML models, they can also protect the IP of the model being run–”two birds, one stone.” Solutions utilizing PETs provide the option to train models on real, sensitive datasets that weren’t previously accessible due to data privacy and security concerns. This unlocking of dataflows to real data is the best option to reduce bias. But how would it actually work?
For now, the leading options start with a confidential computing environment. Then, an integration with a PETs-based software solution that makes it ready to use out of the box while addressing the data governance and security requirements that aren’t included in a standard trusted execution environment (TEE). With this solution, the models and data are all encrypted before being sent to a secured computing environment. The environment can be hosted anywhere, which is important when addressing certain data localization requirements. This means that both the model IP and the security of input data are maintained during computation–not even the provider of the trusted execution environment has access to the models or data inside of it. The encrypted results are then sent back for review and logs are available for review.
This flow unlocks the best quality data no matter where it is or who has it, creating a path to bias minimization and high-efficacy models we can trust. This flow is also what the EU AI Act was describing in their requirements for an AI regulatory sandbox.
Facilitating Ethical and Legal Compliance
Acquiring good quality, real data is tough. Data privacy and localization requirements immediately limit the datasets that organizations can access. For innovation and growth to occur, data must flow to those who can extract the value from it.
Art 54 of the EU AI Act provides requirements for “high-risk” model types in terms of what must be proven before they can be taken to market. In short, teams will need to use real world data inside of an AI Regulatory Sandbox to show sufficient model efficacy and compliance with all the controls detailed in Title III Chapter 2. The controls include monitoring, transparency, explainability, data security, data protection, data minimization, and model protection–think DevSecOps + Data Ops.
The first challenge will be to find a real-world data set to use–as this is inherently sensitive data for such model types. Without technical guarantees, many organizations may hesitate to trust the model provider with their data or won’t be allowed to do so. In addition, the way the act defines an “AI Regulatory Sandbox” is a challenge in and of itself. Some of the requirements include a guarantee that the data is removed from the system after the model has been run as well as the governance controls, enforcement, and reporting to prove it.
Many organizations have tried using out-of-the-box data clean rooms (DCRs) and trusted execution environments (TEEs). But, on their own, these technologies require significant expertise and work to operationalize and meet data and AI regulatory requirements.
DCRs are simpler to use, but not yet useful for more robust AI/ML needs. TEEs are secured servers and still need an integrated collaboration platform to be useful, quickly. This, however, identifies an opportunity for privacy enhancing technology platforms to integrate with TEEs to remove that work, trivializing the setup and use of an AI regulatory sandbox, and therefore, acquisition and use of sensitive data.
By enabling the use of more diverse and comprehensive datasets in a privacy-preserving manner, these technologies help ensure that AI and ML practices comply with ethical standards and legal requirements related to data privacy (e.g., GDPR and EU AI Act in Europe). In summary, while requirements are often met with audible grunts and sighs, these requirements are simply guiding us to building better models that we can trust and rely upon for important data-driven decision making while protecting the privacy of the data subjects used for model development and customization.
#ai#ai act#AI bias#ai tools#AI/ML#apple#Art#autonomous vehicles#Bias#birds#box#Building#Business#challenge#Collaboration#collaboration platform#compliance#comprehensive#computation#computing#confidential computing#data#Data Governance#Data Management#data owner#data privacy#data privacy and security#data protection#data security#data-driven
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
anyways
can't believe i spent two hours on the bus just to spend one hour at work checking a databank smh
#pls just let me work remotely i'm begging#i could've sorted this in an hour at home#without having to go out in the fucking rain lol#yeah yeah confidential government data
1 note
·
View note
Text
US nuke reactor lab hit by 'gay furry hackers' demanding cat-human mutants • The Register
I think tumblr should see this because I think this is funny
#/personal#absolutely not good that employee data and confidential info is leaked#but their reasoning for doing so is funny
0 notes
Text
Understanding CPRA: A Guide for Beginners
The California Privacy Rights Act (CPRA) is a data privacy law that was passed in California in November 2020 as an extension and expansion of the California Consumer Privacy Act (CCPA).
The CPRA introduces new privacy rights for consumers and additional obligations for businesses. The law is expected to go into effect on January 1, 2023.
Why Do We Need CPRA?
The CPRA came about to address some…

View On WordPress
#Automated Decision Making#California Consumer Privacy Act#California Privacy Protection Agency#California Privacy Rights Act#CCPA#Compliance#Confidentiality#Consent#Consent Management#Consumer Rights#CPPA#CPRA#Data Breach#Data Deletion#Data Practices#data privacy#Data Processing#data protection#Data Rights#Data Security#Digital Age#Enforcement#Information Protection#Non-compliance#personal data#Privacy Notice#Privacy Policy#Right to Correct#Right to Delete#Sensitive Personal Information
0 notes
Text
The Grayzone has obtained slides from a confidential Israel lobby presentation based on data from Republican pollster Frank Luntz. They contain talking points for politicians and public figures seeking to justify Israel’s assault on the Gaza Strip.
Two prominent pro-Israel lobby groups are holding private briefings in New York City to coach elected officials and well-known figures on how to influence public opinion in favor of the Israeli military’s rampage in Gaza, The Grayzone can reveal. These PR sessions, convened by the UJA-Federation and Jewish Community Relations Council, rely on data collected by Frank Luntz, a veteran Republican pollster and pundit.
[...] The Luntz-tested presentations on the war in Gaza urge politicians to avoid trumpeting America’s supposedly shared democratic values with Israel, and focus instead on deploying “The Language of War with Hamas.” According to this framing, they must deploy incendiary language painting Hamas as a “brutal and savage…organization of hate” which has “raped women,” while insisting Israel is engaged in “a war for humanity.”
[...] Luntz’s Gaza war presentation puts his poll-tested tactics back in the Israel lobby’s hands, urging pro-Israel public figures to stay on the attack with incendiary language and shocking allegations against their enemies.
In one focus group, Luntz asked participants to state which alleged act by Hamas on October 7 “bothers you more.” After being presented with a laundry list of alleged atrocities, a majority declared that they were most upset by the claim that Hamas “raped civilians” – 19 percent more than those who expressed outrage that Hamas supposedly “exterminated civilians.”
Data like this apparently influenced the Israeli government to launch an obsessive but still unsuccessful campaign to prove that Hamas carried out sexual assault on a systematic basis on October 7. Initiated at Israel’s United Nations mission in December 2023 with speeches by neoliberal tech oligarch Sheryl Sandberg and former US Secretary of State Hillary Clinton, a recipient of hundreds of thousands of dollars in donations and speaking fees from Israel lobby organizations, Tel Aviv’s propaganda blitz has yet to produce a single self-identified victim of sexual assault by Hamas. A March 5 report by UN Special Representative on Sexual Violence Pramila Patten did not contain one direct testimony of sexual assault on October 7. What’s more, Patten’s team said they found “no digital evidence specifically depicting acts of sexual violence.”
They also advice to use different language for Democrat and Republican voters, which inadvertently provides one of the most succinct explanation of the difference between the two genocidal parties that I've ever come across:
To make their arguments stick, Luntz recommends pro-Israel forces avoid the exterminationist language favored by Israeli officials who have called, for example, to “erase” the population of Gaza, and to instead advocate for “an efficient, effective approach” to eliminating Hamas.
At the same time, veteran pollster acknowledges that Republican voters prefer phrases which imply maximalist violence, like “eradicate” and “obliterate,” while sanitized terms like “neutralize” appeal more to Democrats. Republican presidential candidates Nikki Haley and Donald Trump have showcased similar focus-grouped rhetoric with their calls to “finish them” and “finish the problem” in Gaza.
One of the slides, illustrating what language to use:
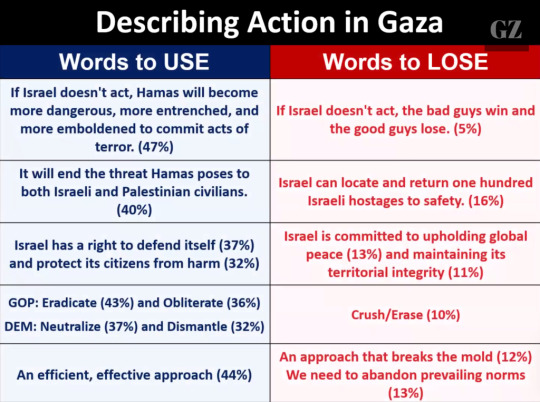
There are several more slides in the article. I recommend reading the whole thing, start to finish. One more thing I'd like to highlight though:

Luntz acknowledges Israel’s mounting PR problems in a slide identifying the most powerful tactics employed by Palestine solidarity activists. “Israelis attacking Israel is the second most potent weapon against Israel,” the visual display reads beside a photo of a protest by Jewish Voices for Peace, a US-based Jewish organization dedicated to ending Israel’s occupation of Palestine.
“The most potent” tactic in mobilizing opposition to Israel’s assault on Gaza, according to Luntz, “is the visual destruction of Gaza and the human toll.” The slide inadvertently acknowledges the cruelty of Israel’s bombardment of Gaza, displaying a bombed out apartment building with clearly anguished women and children fleeing in the foreground.
But Luntz assures his audience, “It ‘looks like a genocide’ even though the damage has nothing to do with the definition.”
According to this logic, the American public can become more tolerant of copiously documented crimes against humanity if they are simply told not to believe their lying eyes.
. . . full article on GZ (6 Mar 2024)
5K notes
·
View notes
Text



[2022 Entertainment survey conducted by Joynews24 Part 2]
Participated by 200 industry officials
#YoonA mentioned in:
-Scene stealer of the year (movie) with #ConfidentialAssignment2
-Rediscovered Star of the year with a shining presence in drama with #BigMouth
2 notes
·
View notes