#DoNotTrack
Explore tagged Tumblr posts
Video
youtube
How To Enable Do Not Track On The Zen Web Browser | PC | *2024
Learn how to enhance your online privacy by enabling the "Do Not Track" feature on the Zen Web Browser. This step-by-step guide will show you how to activate or deactivate this setting, helping you control how websites track your online activity. Perfect for anyone who values online privacy and wants to manage their browsing experience more effectively!
Simple Steps 1. Open the Zen browser. 2. Click on the 3 line hamburger menu in the upper right corner and choose "Settings". 3. Select "Privacy & Security" from the left side pane. 4. In the center pane, under "Website Privacy Preferences", check the box next to "Send Websites A Do Not Track Request".
0 notes
Text
SJ watches: Do Not Track
I really liked the Do Not Track personalised documentary and it's user experience.
Having a choice of episodes really appeals to our modern viewing styles, as does, having information presented in smaller chunks (to suit our multi-tasking habits.)
However, the info presented is not one to be listened to absently (or SPOILER, one that’s going to reassure about what’s happening to all the data we’re constantly sharing...)
The more personal questions and prompts throughout added to the experience and the use of the geolocation right at the start was a great hook of personalised storytelling (displaying what the weather was like where and as I was watching).
It definitely gave me a lot to think about for what I want my own project to achieve and how its mechanics will engage its users – particularly if it has a content element to it.
1 note
·
View note
Text
Do Not Track - a personalised documentary series about privacy and the web economy
Do not track was a completely new experience to me. I didn���t know anything about it or what to expect and was very excited when i understood that, in order to prove that everyone has access to my data, they use my data to give me the kind of information that companies are willing to pay for. The problem is, that for some reason it didn’t work with me.
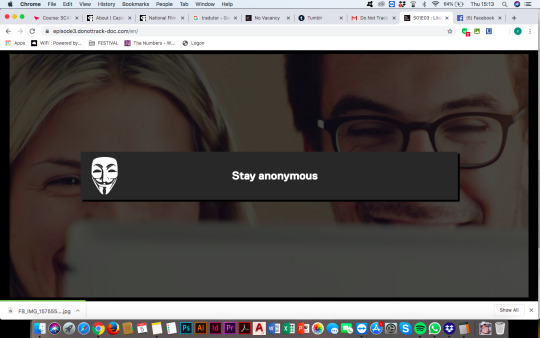
it didn’t give me any option other then to stay anonymous, so every time that I was suppose to have a personalised experienced, they would have to use the data provided for their default user, making my experience zero personalised... frustrating.
The concept of the series is extremely interesting though, and, if it had worked it would definitely be a true personalised and interactive idea. Also the topic they are approaching here is extremely relevant and interesting, and they chose a innovative way of telling this story.
I was very curious about how my habits are being interpreted and if I am a risk taker, a boring person, or whatever. I’m definitely frustrated for not having figured out those patterns as I was even willing to give all my data to found out! =(
Was surprised to realise that it is also another “National Film Board of Canada” series, showing a very direct interest on creative exhibiting formats. Will look for what other formats they found.
1 note
·
View note
Photo

Do Not Track is an excellent feature provided by web browsers like Chrome, Firefox, Edge, and Safari to restrict websites from monitoring your surfing activities. When you keep this setting enabled in your web browser, it informs the websites, analytics companies, and ad networks not to track your browsing activity.
0 notes
Link
Highly recommended. Great use of personalisation and data. Find out how much your really share about yourself online.
2 notes
·
View notes
Text

While Using The VMLOGIN Browser, You Can Find The Property Called “DoNotTrack” Lying In The Navigator. Turn It On When You Want Tight Security and Avoid Being Tracked.
The Default Value Is Unspecified and It Allows You To Make Choices As Per Your Requirement.
𝐂𝐨𝐧𝐧𝐞𝐜𝐭 𝐖𝐢𝐭𝐡 𝐔𝐬:
Free trial link: https://www.vmlogin.us/
Download link: https://www.vmlogin.us/download.html
Tutorials: https://www.vmlogin.us/help/
Telegram Official Channel:https://t.me/vmloginUS
#webapplication#cloudapps#softwareprotection#virtualplatform#dataprotection#Secured#platforms#devicemanagement#resourcemanagement#FullSupport#bestuse#virtualbrowser#searchsafely#datasafety#freesuffering#incognito#Vmlogin#software
1 note
·
View note
Video
youtube
Asignacion #5 Do not Track
0 notes
Text
Gaylor’s DoNotTrack/Dictionary.com
Gaylor’s DoNotTrack episode is unnerving. I have watched the video several times, and only just recently noticed that there was a photo from near where I live implanted as Gaylor is saying “I know where you live”. Even while watching a video about tracking I had not realized to what level DoNotTrack themselves were tracking. I know figuring where someone lives is not that difficult to do with tracking, but that is not what surprised me. What surprised me is how all the other images on the screen distracted me long enough to miss the photo of the city the first several times I watched it. This realization made the whole idea of trackers more real to me. It is one thing to be told that trackers are taking my information, but it is another thing to be shown some of the information they took from me.
DoNotTrack also shows how many trackers a website uses. I remembered Mark mentioning that Dictionary.com uses a ridiculous amount of tracking cookies, so, I entered the website into DoNotTrack. DoNotTrack claims Dictionary.com to have 17 trackers (Gaylor). According to The Washington Post there are 35 trackers Dictionary.com uses (Peterson and Soltani). DoNotTrack is able to find about half as many trackers as the Wall Street Journal investigation. This difference in numbers only shows to me how hard it is too grasp how heavily we are being tracked. Dictionary.com is recorded to drop 39 cookies from just the home page, and has been recorded to get to just under 200 cookies in total (Peterson and Soltani). The information being taken from the trackers maybe used to direct ads and news at us online right now, but consider how important the impact designated results can be. If a person is shown one thing, and only that one thing then they themselves will believe it. That is what brainwashing is; that is what propaganda of all kinds is created to do. The scary thing is, when we are online there is a sense of freedom, a sense of there being no walls to stop us from going wherever there is to go. That sense of freedom is what net neutrality stands for. It starts with showing different people different style of clothing they might want to buy, but what will stop it from turning into a way to divide the world in a similar fashion as Nazi Germany did. Power longs for power. It starts by mapping everyone in the world wide web and falls into shaping nations through using the people in it. That might sound like an over-exaggeration, but then consider the last U.S. election.
Gaylor, “Morning Rituals.” DoNotTrack, https://episode1.donottrack-doc.com/en/.
Peterson, Andrea and Soltani, Ashkan.“Dictionary.com dubs ‘privacy’ their word of the year. But visiting their homepage sets 90 cookies.” The Washington Post, 18 Dec. 2013, https://www.washingtonpost.com/news/the-switch/wp/2013/12/18/dictionary-com-dubs-privacy-their-word-of-the-year-but-visiting-their-homepage-sets-90-cookies/?utm_term=.ff6ed99faa7f.
0 notes
Text
Gaylor’s DoNotTrack
My first feelings after watching Gaylor’s first DoNotTrack episode was shock. Not because I did not know that the web tracks us through cookies, but because of the impactful way the video made me think about it. Normally, I think of cookies as being no big deal. If I am only using my computer for looking up movies and doing school work, then where is the problem? Although after watching this episode, it is very evident that there is a problem. In the video, it is stated that when you’re in the system giving data, that data is used to judge, assert power and make comparisons on other people also using the web. “It’s not about you, but how what you put out there effects other people” was a line that struck me the most, and made me think about my own privacy practices. When using my computer, it is uncommon that I really think about what I’m doing. For the most part, I’m either doing school work or watching netflix, so why should I worry? As I think about it now, there is many things about me that I would prefer others not to know that is out there for any tracker to see. Intimate things that would not normally be shared it saved by cookies, shared by strangers and consumed by corporate leaders. The thought of that is odd to me, and also slightly scary. What do they know? How do I make it so that they do not take my information? Educating oneself about how the web works and how involved one truly becomes when plugging in is crucial in today’s society. With computers and phones in nearly every hand, people must know what kind of information they are sharing with the world whether they mean to or not. Learning about cookies and tracking is necessary when using technology, because otherwise we will be doing exactly what the surveillance driven trackers want: letting privacy perish.
0 notes
Video
youtube
How To Enable Do Not Track In The Mozilla Firefox Web Browser | PC | *2024
Protect your privacy online by enabling the "Do Not Track" feature in Mozilla Firefox. This step-by-step tutorial will guide you through the process of activating or deactivating this setting on your PC. Learn how to send a request to websites asking them not to track your browsing habits for a more secure and personalized experience. Perfect for those who value their online privacy!
Simple Steps 1. Open Mozilla Firefox. 2. Click on the 3 line hamburger menu in the upper right corner and choose "Settings". 3. Select "Privacy & Security" from the left side pane. 4. In the center pane, under "Website Privacy Preferences", check the box next to "Send Websites A Do Not Track Request".
0 notes
Text
DoNotTrack reflection
this web sight connects with my interactions with the internet and social media as i too have been feeling a little sketched out by the internet’s constant eyes on me. As the video discussed the fact that adds are targeted and we are monitored for the growth of sales, I began to put the pieces together of all the pop ups I get on Facebook and Instagram targeting what I search on google. for example, I have recently been looking into leasing a condo at Chancellors Way for second year. i have been furiously searching for this on google and recently the adds promoting this company have been appearing on my Instagram. i am spooked. I have also noticed that if i mention a word for something like “LAPTOP”, i start seeing adds for macbooks on Facebook. I looked into this and apparently many people fear that they are being monitored. SIRI is always recording us so i would not be surprised if this was used to make us buy more. This Do Not Track site raised my awareness of the extent that i am being tracked by showing me all the data they have collected on me. it is terrifying.
0 notes
Text
Something Awesome: Data Thief or Gift Recipient
Okay, we’ve seen more than a few attacks that can be performed when someone clicks a link or navigates to a website.
Cryptojacking
Cross Site Request Forgery
Drive-By Attacks
Zoom 0day
But it’s time to pay homage to the attack that’s hidden in plain site.
tldr; head over to https://fingerprintme.herokuapp.com/ for some fun.
Passive Data Theft
I hesitate to call it theft when in fact we are giving all of this data to every website we visit like a little gift.
Please, accept this bundle of quasi-identifiers as a token of my appreciation.
Many internet users have no idea just how much data is available to websites they are visiting, so it’s worth exploring just what is in our present.

IP Address and Geolocation API
Like any good gift giver, we better write on the tag.
To: <website server> From: <your IP address>
Your IP (Internet Protocol) address is a little 32-bit (now possibly 128-bit) number that uniquely identifies your device on the Internet. This is by design; people need to be able to address you to be able to send you any packets. A static 1:1 mapping of devices to IPs is definitely a massive exaggeration today as as we use technologies to let multiple devices share one IP, dynamically acquire an IP for each session, and our ISPs (Internet Service Providers) may also dynamically assign our IP address.
Nonetheless, IP addresses have (again by design) another function; location addressing. This is because when you’re internet traffic is propagating through the Internet (a global network of routers) it needs to know where it physically needs to go, and fast. Owing to this, the internet has taken on a hierarchical structure, with different ISPs servicing different geographical regions. These ISPs are tiered such that lower tier ISPs service specific subsets of the upper level tier’s region, providing more geographical specificity. It is this property of IP addresses that allows anyone with your IP address to get a rough idea where you are in the world. Moreover, IP addresses from specific subnets like AARNet (for Australian Universities) can be a giveaway for your location.
Try Googling “my ip” or “where am i”. There are many IP to Geolocation API services available. I have made use of https://ipgeolocation.io/, which has a generous free tier 🙏.
User Agent
Every request your browser makes to a server is wrapped up with a nice little UserAgent String bow, that looks a little like this,
User-Agent: Mozilla/<version> (<system-information>) <platform> (<platform-details>) <extensions>
Oh how sweet 😊 it’s our Operating System, our browser and what versions we of each we are running, and if the server is lucky, perhaps a few extra details.
Here are a few examples from MDN:
Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0
Mozilla/5.0 (Macintosh; Intel Mac OS X x.y; rv:42.0) Gecko/20100101 Firefox/42.0
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Why might this be a problem? Allow me to direct you towards my earlier post on Drive-By Attacks. Vulnerabilities are often present in specific versions of specific platforms. If an exploit server detects that your particular version of Chrome for Windows (for example) has a known vulnerability, well then prepare to be infected.

Navigator
Okay, I think we’ve been polite enough, it’s time to rip this packaging open! Ooh what is this inside? It’s an invitation to our browser of course!
When we send off a request to a web server complete with our IP and User Agent string, the web server will typically respond by sending us a web page to render. These days a web page can be anything from a single HTML file with a few verses from a dead poet, to a fully fledged JavaScript application. To support this development, browsers are exposing more and more functionality/system information through a special JavaScript interface called Navigator.
From MDN,
The Navigator interface represents the state and the identity of the user agent. It allows scripts to query it and to register themselves to carry on some activities.
...to carry on some activities... I wonder. The list of available properties and methods is pretty comprehensive so I’ll just point out a few interesting ones.
getBattery() (have only seen this on chrome)
connection (some details about your network connection)
hardwareConcurrency (for multithreading)
plugins (another important vector for Drive-Bys)
storage (persisted storage available to websites)
clipboard (requires permissions, goodness plz be careful)
doNotTrack (i wonder who checks this...)
vibrate() (because haptic is the only real feedback)
While I’ve got it in mind, here’s a wonderful browser localStorage vulnerability I stumbled across https://github.com/feross/filldisk.com. There’s a 10MB per site limit, but no browser is enforcing this quota across both a.something.com and b.something.com...
I have no idea why Chrome thinks it’s useful to expose your battery status to every website you visit... Personally, the clipboard API feels the most violating. It requires permissions, but once given you’re never asked again. Control/Command + V right now and see what’s on your clipboard. I doubt there’s many web pages that you’d actually want to be able to read your clipboard every time you visit.
Social Media Side Channel / CSRF
Okay, now we’re getting a little cheeky. It’s actually possible to determine if a browser has an authenticated session with a bunch of social media platforms and services.
It’s a well known vulnerability (have a laughcry at some of the socials responses), which abuses the redirect on login functionality we see on many of these platforms, as well as the Same-Origin Policy SOP being relaxed around HTML tags, as we saw was sometimes exploited by Cross Site Request Forgery attacks.
Consider this lovely image tag.
<img src="https://www.facebook.com/login.php?next=https%3A%2F%2Fwww.facebook.com%2Ffavicon.ico%3F_rdr%3Dp">
As you can see, the image source (at least originally) doesn’t point to an image at all, but rather the Facebook login page. Thanks to SOP, we wouldn’t and shouldn’t be able to send an AJAX request to this website and see the response. But this HTML image tag is going to fire off a GET request for it’s source no problem.
Thanks to redirect on login, if a user rocks up to the login page with the correct session cookies then we won’t have them login again, but rather we redirect them to their newsfeed; or, as it turns out, whatever the URL parameter next points to. What if we point it to an actual image, say the website icon, such that the HTML image tag loads if we are redirected, and fails if not.
Simple but effective. You can try it for yourself here, by opening my codepen in your browser when you’re signed in to Facebook, and when you’re signed out (or just use Incognito).

Fingerprint Me v1.0
Okay, time for a demonstration. I took the liberty of writing my own web page that pulls all this data together, and rather than store it for a rainy day (like every other page on the web), I present it to the user on a little web dashboard. It’s like a mirror for your browser. And who doesn’t like to check themselves out in the mirror from time to time 🙃
Random technical content: I had to fetch the geolocation data server-side to protect my API key from the client, then I sneak it back into the static HTML web page I’m serving to the user by setting it on the window variable in some inline script tags.
I bust out some React experience, and have something looking pretty (pretty scary I hope) in some nondescript amount of time (time knows no sink like frontend webdev). I rub my hands together grinning to myself, and send it off to some friends.
“Very scary”. I can see straight through the thin veil of their encouragement and instead read “Yeaaaah okay”. One of them admits that they actually missed the point when they first looked at it. But.. but... nevermind. It’s clearly not having the intended effect. These guys are pretty Internet savvy, but I feel like this should be disconcerting for even the most well seasoned web user...
Like that moment you lock eyes with yourself in the mirror after forgetting to shave a few days in a row.

Fingerprint Me v2.0
An inspired moment follows. I trace it back to the week ?7 activity class on privacy:
It is very hard to make a case for privacy. What is the inherent value of privacy? Why shouldn’t the government have our data, we give it to a million services everyday anyway, and receive a wealth of benefits for it. Go on, have it. I wasn’t using it for anything anyway.
It is very easy to make a case for privacy, if there is any sense that someone malicious is involved. As soon as there is someone who would wish us ill it becomes obvious that there are things that the less they know the better.
<Enter great The Art of War quote here.>
~ Sun Tzu
Therein lies the solution. I need to make the user feel victimised. And what better to do it than a green on black terminal with someone that calls themselves a hacker rooting your machine.
DO CLICK THIS LINK (it’s very safe, I promise) https://fingerprintme.herokuapp.com
Some more random technical content: Programming this quite synchronous behaviour in the very async-centric JavaScript was quite a pain. It was particularly tricky to get around the fact that React renders it’s component hierarchy top down, so I needed the parent components to mount empty in order for them to be correctly populated with child components later. It was also a pain to access and render child components conditionally, especially if you want to have sets of child components in different files, as though they aren’t ultimately nested in the DOM, React will treat them as if they are.
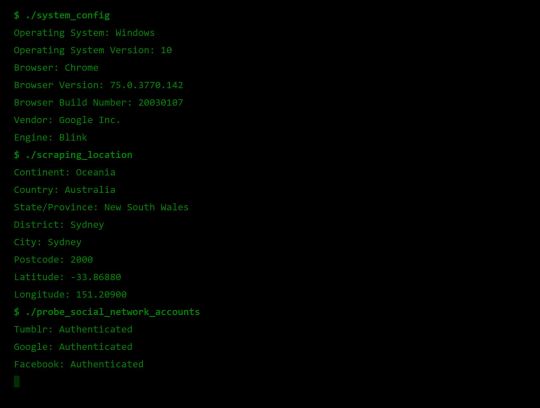
Some User Reviews:
“It feels like I should shut the window”
“This is SO RUDE”
“Battery level. I mean. Literally. How.”
Excellent.
Recommendations
Know what’s in your present, and who you’re gifting it to 🎁
To protect your IP address/location consider using a VPN or ToR
Check out NoScript, a browser plugin that will block JavaScript by default, but allow you to enable it for trusted sites.
Check out and share https://fingerprintme.herokuapp.com 😉
3 notes
·
View notes
Text
In regards to this post (which has suddenly had reblogs turned off for some reason), DNSCloak is a better iOS solution for adblocking than DoNotTrack, which only allows you to block 10,000 domains. That’s not enough to last a day.
0 notes
Text
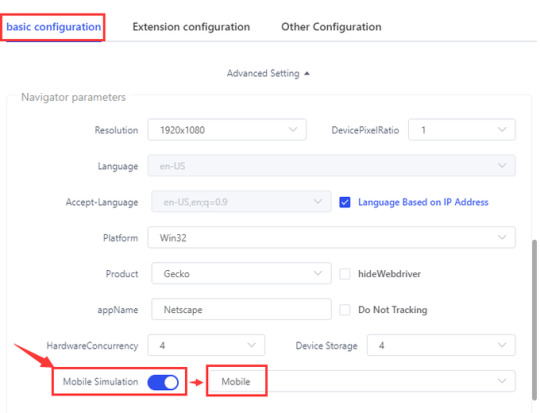
Lalicat anti-fingerprint browser Mobile Simulation And DoNotTrack functions
Lalicat anti fingerprint browser mobile simulation: This is for simulating mobile phone browsers. Desktop in the back indicates the PC mouse mode, and Mobile indicates that the simulated touch screen supports the swipe function.
For details, please view https://www.lalicat.com/mobile-simulation-and-donottrack
1 note
·
View note
Text
Koko Analytics

Koko Analytics. Weil es datenschutzkonform ist, habe ich auf meinen Seiten lange Zeit Statify laufen gehabt. Gefühlt wurde Statify seit langer Zeit zumindest optisch nicht mehr überarbeitet. Slimstats, was ich auch mal am Start hatte wird derzeit nicht mehr weiter entwickelt, scheidet also aus. Außerdem waren mir die Details die Slimstats lieferte schon ein wenig zu viel. Ich wollte eine schlanke Lösung die mir einfach zeigt wie oft meine Seite insgesamt aufgerufen wurde und welche Beiträge besonders beliebt sind. Mehr oder weniger zufällig bin ich dann auf Koko Analytics gestoßen, welches bei entsprechender Einstellung komplett ohne Cookies auskommt und die DoNotTrack Einstellung des Browsers berücksichtigt. Daher habe ich das Plugin einmal für einige Zeit auf meiner Testseite laufen lassen. Datenbankgröße Was bereits nach einer Woche sichtbar war: Koko Analytics geht deutlich sparsamer mit der Datenbank um als andere Statistik Programme. Auch verglichen mit Statify bleibt die Datenbankgröße geringer. Das finde ich grundsätzlich natürlich prima, auch wenn ich bei Statify keinerlei Performanceprobleme festgestellt habe. Optik, Caching und mehr Die Darstellung mit den Balkendiagrammen finde ich bei Koko Analytics sehr ansprechend. Mir persönlich gefällt das besser als die Darstellung bei Statify, was sicherlich Geschmacksache ist. Das Plugin arbeitet problemlos mit Caching Plugins zusammen, getestet wurde mit WPRocket und dem von mir geliebten SWIS Performance. Ich gehe davon aus, das es auch mit anderen Caching Plugins keine Probleme gibt. Ebenfalls mit an Bord ist eine eingebaute "Blacklist" - diese lässt sich zwar im Frontend nicht editieren arbeitet aber meiner Meinung nach zuverlässig im Hintergrund. Die Einträge befinden sich in der Datei 'referrer-blocklist' und enthält die üblichen Verdächtigen. Was mir fehlt Es gibt leider derzeit keine Möglichkeit die Daten zu exportieren und damit beispielsweise in Excel zu erfassen. Ebenfalls nice to have wäre ein Bericht den man sich per e-mail zuschicken lassen kann. Schön wäre ebenfalls ein Datenexport/Import oder gleich die Nutzung einer separaten Datenbank. Beim Neu-Aufsetzen von Wordpress liessen sich so die alten Besucherdaten einfach übertragen. So bleibt nur der Umweg direkt über z.B. PHPMyAdmin die Tabelle zu exportieren und dann wieder zu importieren, was sicher nicht jedermanns Sache ist. Alles in Allem bin ich derzeit mit Koko Analytics sehr zufrieden. Falls der Artikel euer Interesse geweckt hat: Herunterlanden könnt ihr das Plugin hier. Weitere Artikel zu Wordpress und anderen CMS Systemen gibt es in dieser Kategorie. Read the full article
0 notes
Text
The key is to block the ads at the domain level: a DNS-based ad-blocker will return an empty document or a null ip address when any domain on the blacklist is requested, thus allowing you to block the app from even completing any requests for ads (saves on bandwidth too).
I recommend Lockdown for ease of use, but Orbot for versatility with regular expressions. The only downside of Orbot is that the internet gets slower due to being routed through the tor network.
UPDATE: Lockdown sold out and was acquired by Appex, and they Lobotomized the app and made half of the free features subscription based. Use DoNotTrack instead.
In fact, here’s my iOS lockdown list for the tumblr app (there may be some domains that I used for other apps, but I don’t remember which ones were which). You may need to alter some of these based on your location, due to the nature of targeted advertising, and you’ll need to update your block list every so often. I’ll detail instructions on how to do that on iOS at the end of the post, as the process is likely already well documented for android.
THE LIST:
42trck.com
a-iad.1rx.io
a.ad.gt
ad-assets.adsbynimbus.com
ad-delivery.net
ad.adsrvr.org
ad.turn.com
adexp.liftoff.io
ads.celtra.com
aktrack.pubmatic.com
app-measurement.com
apps.sascdn.com
appsrv.display.io
assets.mintegral.com
browser-http-intake.logs.datadoghq.eu
c-<location code>.w.inmobi.com (stuff from inmobi seems like it can be generally blocked, but I need to test that)
cdn-f.adsmoloco.com
cdn.hadronid.net
cdn.liftoff-creatives.io
crashlyticsreports-pa.googleapis.com
creatives.sascdn.com
displayf-tm.everesttech.net
dspbeacons.ihasdsp.inmobi.com
dspbeacons.old.ihasdsp.inmobi.com
et-<location code>.w.immobi.com
g.doubleclick.net
geo-tracker.smadex.com
geo.celtra.com
geolocation-db.com
geolocation.onetrust.com
ghent-gce-bidswitch.net
hubble-02.tmmp.io
ic.de.inmobi.com
ids.ad.gt
impression-<location code>.liftoff.io
impression.link
impressions.onelink.io
impressions.onelink.me
insight.adsrvr.org
maps.googleapis.com (be careful with this one, might break other apps, but I blocked it because it was trying to geolocate me by my IP address)
mfx-<some kind of location code>.mobilefuse.com
mobile.smartadserver.com (these are the people behind the infamous pikaman ad, which tracked the hell out of anyone who clicked it. So yeah, the pikaman knows where you live now)
noti-us.adsmoloco.com
ny1-bid.adsrvr.org
nym1-ib.adnxs-simple.com
ocsp.pki.goog
ocsp.<some kind of location code>.amazontrust.com
onetag-sys.com
pixel.quantserve.com (this one probably stores a tracking pixel)
pixel.tapad.com
pixel.wp.com (Wordpress tracking pixel I think)
playtime.tubemogul.com
r3.o.lencr.org (this one might be associated with windows malware)
rm.aarki.net
rules.quantcount.net
service.idsync.analytics.yahoo.com
spire.aarki.com
suggestqueries.goofle.com
supply.inmobicdn.net
tag.tapad.com
track.celtra.com
trackedevt.1rx.io
turbo.adsbynimbus.com
ups.analytics.yahoo.com
va6-bid.adsrvr.org
vet-<location code>.track.smaato.net
www15.smartadserver.com (this was the domain the pikaman ad sent you through to add a bunch of tracking IDs to your url.)
x.bidswitch.net
To update your blacklist:
Go to settings>privacy>app privacy report.
If it isn’t on, make sure all apps you don’t want to block ads on (yet) are closed, then turn it on.
If it’s already on, turn it off and on again.
Now you gather data. Open the app with the annoying ads and use it as normal for a bit. The donations contacted by the app will be recorded in the privacy report. While you’re at it, record some other apps too (the reason for this will become clear in the next step).
Once you’re satisfied with the data, go back to the privacy report page. Select the app that you’re targeting to view all the domains it contacts. Record any domains that are contacted by more than one app, as those are likely building profiles. Also record any third party domains where the name has to do with ads/tracking/identifiers.
Once you’ve gone through the list, add all the domains you copied down to the custom blacklist in the lockdown app.
To test it out, close and reopen the target app. If it doesn’t function, you may have blocked an important domain; you’ll need to figure out which one it is by testing all the domains you blocked. You can temporarily unblock a domain in lockdown by tapping on its entry in the custom block list.
Now go forth, and be unprofitable (and maybe support this site in other ways)!
Whenever you suggest using a browser-based adblocker to someone complaining about the ads on an app, God sees that and He puts another check mark next to your name in the big book of people who go to Double Hell
250 notes
·
View notes