#Domain Name System Security Extensions
Explore tagged Tumblr posts
Text
DNSSEC: Peace of Mind for Your Online Safety
What is DNSSEC?
A feature of the Domain Name System (DNS) that verifies answers to domain name lookups is called Domain Name System Security Extensions (DNSSEC). Although it keeps attackers from tampering with or contaminating DNS query responses, it does not offer privacy protections for those lookups.
Not really. DNSSEC uses a different method than encryption public key cryptography to defend networks from man-in-the-middle attacks. Put differently, Domain Name System Security Extensions offers an authentication method but not a confidentiality method.
DNSSEC: Internet Foundation Protection
Domain Name System (DNS) converts human-readable domain names into machine-readable IP addresses for online security in the digital age. Security issues make traditional DNS vulnerable to manipulation and attacks. DNSSEC safeguards DNS data.
Major Advantages of DNSSEC:
DNSSEC uses public-key cryptography and digital signatures to verify DNS responses. This means a domain name’s IP address is authentic and hasn’t been changed from the authorized source.
Data Integrity: Phishing attempts and malicious website redirects can result from DNS data manipulation. DNSSEC prevents hackers from altering vital DNS records by cryptographically verifying them.
Middleman (MitM) Attack Prevention: DNSSEC guarantees authenticity and data integrity, reducing the risk of MitM attacks, in which attackers intercept and alter DNS responses to trick users.
Domain Name System Security Extensions protects DNS lookups from malicious and tampering, giving users and organizations confidence to use online services.
Is DNSSEC important?
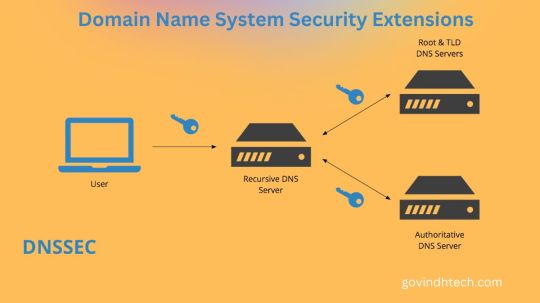
Public/Private Key Pairs: Public keys are published in the DNS by domain owners, while private keys are kept confidential.
Digital Signatures: By digitally signing DNS records with the private key, a “fingerprint” that confirms their legitimacy is created.
Signature Validation: To make sure received DNS records haven’t been tampered with, resolvers the programs that convert domain names into IP addresses verify the signatures using the public key that has been released.
Chain of Trust: Signatures are verified through a chain of trust that originates from the root of trust that is present at the top of the DNS hierarchy.
How to implement DNSSEC
Adoption: DNSSEC is being implemented more often, despite not being widely used. It is supported by a large number of prominent domain registries and registrars, and it is frequently free for organizations to enable.
Benefits Exceed Difficulties: Although DNSSEC setup and configuration may call for some technical know-how, the advantages greatly exceed the drawbacks. Organizations that are concerned about security ought to give it serious consideration for their domains.
What distinguishes public key cryptography from encryption?
DNS queries are digitally “signed,” or authenticated, using public key cryptography by DNSSEC. The receiving device can compare the data it receives with the original data sent by the authoritative server when DNSSEC is enabled on a zone record. A digital signature that authenticates data using public keys makes this possible.
The data in DNSSEC is not encrypted; instead, the authentication keys are secured through cryptography. Traffic protected by Domain Name System Security Extensions can still be intercepted and read. The receiving server will be able to detect that something is wrong if the data is altered somewhere along the data pathway and sent on to its destination because the public keys will not match.
On the other hand, encryption encrypts the data by using cryptography. By altering what an attacker would see if they were to intercept a query somewhere along the data pathway, encryption ensures confidentiality. Until the attacker uses an encryption key to decipher the signal, it renders the data unintelligible. Data is shielded from manipulation by encryption because the key isn’t disclosed to the public.
What is DNSSEC in cybersecurity?
Among the Internet’s more traditional protocols is DNS. The Internet was much smaller when it was first developed, and almost everyone there was acquainted. Data Security was not given much thought.
DNS was used so extensively by then that any major alteration would have brought down the entire system, even before the issue of Internet security arose. Instead of attempting to create a completely encrypted protocol to take the place of DNS, an authentication mechanism was added to the pre-existing system.
DNSSEC was vulnerable. By enabling the authentication of queries and data, it improved protocol security. However, it did so without altering the underlying architecture, allowing the Internet to expand further without requiring any new engineering. Domain Name System Security Extensions deployment was left optional so that organizations could make the switch whenever they felt ready.
If DNSSEC isn’t encrypted, why use it?
One major reason to use DNSSEC is to prevent DNS cache poisoning, also called DNS spoofing. A DNS spoofing attack involves replacing a legitimate DNS query response with an unauthenticated one. After that, the response becomes stuck in the cache, returning the incorrect response and sending users to malicious websites until the “time to live” runs out.
By authenticating DNS responses and guaranteeing that only accurate responses are returned, DNSSEC defends against these types of attacks. DNS spoofing attacks cannot be prevented by encryption, but it may safeguard the underlying data in a DNS connection.
Is DNSSEC still used if it isn’t encrypted?
Sadly, DNSSEC is only used to validate about 20% of Internet traffic. Even though it’s a big improvement over a few years ago, that amount is still far below what it ought to be. That substantial gap can be attributed to a combination of informational gaps, laziness, and usability issues.
By offering a straightforward deployment procedure, NS1 encourages all of its clients to implement DNSSEC. Through IBM’s Dedicated DNS offering- NS1 even offers Domain Name System Security Extensions as a backup provider or redundant DNS option, in contrast to other providers.
Gazing Forward
Security continues to be the primary concern as the internet develops. One of the most important steps toward a more secure DNS ecosystem is Domain Name System Security Extensions. It encourages trust and confidence in online interactions by defending against critical vulnerabilities, protecting users and organizations from malicious activities.
Read more on Govindhtech.com
#technology#govindhtech#technews#news#dns#Domain Name System Security Extensions#ns1#cryptography#DNSSEC
0 notes
Text
Several government websites have been taken down, including the USAID.gov, ForeignAssistance.gov, NeglectedDiseases.gov, and ChildrenInAdversity.gov. A WIRED analysis of more than 1,000 federal .gov websites found that at least seven sites linked to a USAID server went offline in a two-hour span on Saturday afternoon.
On Friday, Reuters reported that word of sites being taken offline was the result of confusion around new guidelines on language allowed to appear on federal sites. Agencies had been instructed to “take down all outward facing media (websites, social media accounts, etc.) that inculcate or promote gender ideology” by 5 pm EST, Friday, January 31.
The move is the latest step in the Trump administration’s move to radically remake the US government. Shortly after taking office, the Trump administration took down ReproductiveRights.gov, which provided information on reproductive health care. A growing number of US government websites have gone offline since mid-January.
Along with sites affiliated with the USAID server, Youth.gov—a US government site focused on supporting youth programs—appears to have gone offline in the past 24 hours. Before it was taken down, an archived version from the Wayback Machine showed it featured a post titled, “Preparing for MLK Jr. National Day of Service.”
A USAID employee tells WIRED that staff members are scrambling to save digital copies of regulations from archived versions of the site, and that at least some are being locked out of their systems, including personnel files, pay, and benefits information. “Decades worth of taxpayer-funded reports and analysis gone in an instant,” says the employee, who requested anonymity because they are not authorized to speak to the press. “We have no idea what is happening behind the scenes or what will be back, when, and in what form."
Added the employee: “Staff can't even get into the DEC (Development Experience Clearinghouse, a publicly available database of USAID documents) to secure copies of open access reports.”
Another USAID employee tells WIRED they still had access to internal work systems as of Saturday afternoon, but have limited visibility into what’s happening and why.
“We haven't been allowed to be in contact with our partners,” says the employee, who was also granted anonymity. “We've been kept in the dark, and this is just an extension of that.” The employee added that they worry the agency will be slimmed down to a “skeleton of what we were.”
Other sites, including HealthData.gov, Oversight.gov, and Vaccines.gov, have also periodically gone dark. It remains unclear whether these brief takedowns are linked to the recent executive order or if some are due to unrelated technical issues. However, some sites, like ProsperAfrica.gov, explicitly state: “In order to be consistent with the President’s Executive Orders, this website is currently undergoing maintenance as we expeditiously and thoroughly review all of the content."
WIRED built software to systematically check the status of 1,374 government domains. The tool runs periodic scans, tracking whether sites remain accessible, how their servers respond, and if the domain names still resolve. This allows us to monitor patterns in uptime and catch moments when sites suddenly vanish– sometimes reappearing minutes or hours later. Some of these outages can be attributed to routine maintenance or technical glitches. Others suggest broader infrastructure failures or deliberate removals.
In total, more than 450 government domains WIRED is monitoring remain consistently offline. However, it’s unclear whether they were removed weeks, months, or even years ago.
On January 26, President Donald Trump signed an executive order “initiating a review of all foreign assistance programs to ensure they are efficient and consistent with U.S. foreign policy under the America First agenda.” The result was a suspension of USAID’s work abroad, which includes lifesaving humanitarian aid as well as critical public health initiatives.
In the newsletter Garbage Day, Ryan Broderick and Adam Bumas reported that an employee working with an organization funded by the Centers for Disease Control was informed that the agency’s website would be taken down “in its entirety.” Last week, the government removed TargetHIV.org, run by the Health Resources and Services Administration. The CDC’s HIV resource landing page has also been removed. Pages on creating safe school environments and addressing health disparities for LGBTQ+ youth were also removed, as was one focused on transgender people.
In a post on Bluesky, journalist Ken Klippenstein shared images of an email sent to the National Oceanic and Atmospheric Administration that required the agency to remove materials that contained words like “black,” “ethnicity,” “empathy,” and “handicap.”
Within the past week, employees across agencies received emails requiring them to replace all mentions of “gender” with “sex” in all “communications, forms, and documents” and to remove pronouns from email signatures.
Federal agencies were also told last week that they had 60 days to eliminate DEI roles and programs, and an email encouraged federal employees to report colleagues who work in DEI roles.
5 notes
·
View notes
Text
The Domain-Name problem
China gets a lot of hate for sectioning off the rest of the internet from their people. But that's probably one of the things they got right .
When the internet hit a global scale, China reasonably thought "we should have our local stuff more readibly accessible to our local people" after-all, what use is driving directions to an individually owned diner in Vermont to somebody in Xinagsheng?
China created their own internet, which to the internet is just a very large intranet.
The reason for this is because the base internet design really only benefited the U.S., and didn't take into account fiberoptic wires under the ocean to communicate with other countries.
We can see it in effect today with IP4 vs IP6. Where the use still uses the IP4 standard and the rest of the world is forced onto IP6. (Internet address Protocol)
Domain Names (www.address.com) only turn an IP-Address into something human readable. And again we see the same paradigms; U.S. first, and then a country designator at the end (co.jp, co.de...
The (www) part is the sub-domain, or part of the same network as the domain, just a different machine (usually, not always).
Now, the .com, .net, org was originally supposed to mean (commercial), (network), and (organization). But as we've seen: didn't mean much to actual usage... Now they're just random extensions we don't care what they mean anymore.
And there's a problem; parsing out a domain name could be as complex as
Sub.sub2.domain.co.jp vs sub.domain.com vs domain.org: which part indicates what is local on the server? And which part indicates what the infrastructure(internet routers) should use to direct traffic? There isn't a set standard here.
What this means to me is that we should rethink how we split up the internet. In order to allow users to visit hosts from other countries*and* allow foreigners to see (but not necessarily interact with) local social media.
And how can we tell which websites are operating effectively doing operations for multiple countries? Like Amazon. Country tax laws can't tell.
I get the feeling Elon Musk would be very sad about the development after his very large purchase.
For the interest of National Security and World-Wide-Economic prosperity.
There are even large amounts of data used in search engines and AI to infer local area around the user, that could be clarified via a change in systems.
Think about our area codes for phone numbers and zip codes for mail. We don't have them online. I think we need them.
If not simply to increase the speed of the internet.
7 notes
·
View notes
Text
What are the best Plesk reseller hosting services?
Plesk Web Hosting uses a Plesk control panel to let you handle all aspects of your website hosting requirements, including DNS records, email addresses, domain names, and more. Plesk is an easy-to-use control panel that guarantees website security, automates server tasks, and supports both Linux and Windows hosting. Plesk is best suited for you if you need to manage your multiple customer accounts seamlessly and automate your admin functions.

Plesk reseller hosting: What is it?
In order to meet the requirements of individuals and businesses that want to administer multiple websites on a single platform, the Plesk reseller hosting platform offers a solution that is not only effective but also flexible. This particular hosting option is going to be highly appealing to web designers, web developers, and businesses that want to provide hosting services to their consumers but do not want to deal with the hassle of managing individual accounts.
Regardless of whether you handle a small number of domains or a large portfolio of websites, the user-friendly interface and wide feature set of Plesk make it simple to streamline your web hosting operations. This is true regardless of the magnitude of your website portfolio. This article will give you the knowledge you need to make decisions that are based on accurate information by delving into the most significant features, benefits, and best hosting service providers of Plesk reseller hosting.
The advantages of Plesk reseller hosting-
The Plesk reseller hosting platform offers a plethora of benefits, which makes it an enticing option for online professionals who have extensive experience in the field. One of the most important aspects of this product is the fact that it has a user-friendly design, which makes it simpler to manage a variety of websites and accounts.
Customers have the ability to effortlessly manage databases, email accounts, and domains with the help of Plesk, which features an interface that is simple to use. Furthermore, the reseller plans include support for an unlimited number of domains. This enables resellers to provide their customers with the most affordable hosting pricing possible for multi-domain publishing operations.
Using this cloud management platform comes with a number of important benefits, one of which is the complete security measures that are built into Plesk. These features include firewalls, intrusion detection, and antivirus protection. These qualities assist in the safety of websites against the dangers that can be found on the internet.
As an additional benefit, Plesk is compatible with a wide range of applications and extensions, which enables customers to customize their hosting environment to meet the specific needs of their businesses.
Plesk reseller hosting gives resellers the ability to create unique hosting packages, efficiently allocate resources, and deliver dependable services to their customers. This is made possible by the usage of Plesk. As a consequence of this adaptability, scaling and expanding the hosting business is a far simpler process.
Features of Plesk reseller hosting-
Security features
Plesk reseller hosting has many security tools to protect your hosting environment. Firewalls in Plesk prevent unwanted access and cyberattacks. The software also supports SSL certificates for encrypted server-client communication. Intrusion detection and prevention systems in Plesk monitor for suspicious activity and automatically mitigate threats.
Antivirus and anti-spam capabilities are incorporated to safeguard your email services from dangerous assaults and undesirable information. Regular security updates and patches are provided to maintain the system's security against current vulnerabilities. Plesk lets you create user roles and permissions to restrict authorized users' access to sensitive control panel areas.
User-friendly interface
One of the major characteristics of Plesk reseller hosting is its user-friendly interface. Plesk's control panel is simple and efficient, even for web hosting beginners. Domain management, email configuration, and database administration are easily accessible from the dashboard. As a complete WordPress site update, security, and management solution, the WordPress Toolkit improves user experience. Users may manage their hosting environment right away, thanks to this simplified UI.
Plesk lets users customize the dashboard to their preferences and workflow. Additionally, the responsive design guarantees that the interface is accessible and functioning across many devices, including PCs, tablets, and smartphones. The Plesk reseller hosting interface makes managing multiple websites and customer accounts easy and boosts productivity.
Performance and reliability
Performance and reliability are key to Plesk reseller hosting. Compared to typical shared hosting, reseller hosting offers better scalability and control, making it a more powerful choice for managing several websites. User satisfaction and SEO rankings depend on fast loading times and high uptime, which the platform optimizes. Plesk optimizes server performance with smart caching and resource management. Plesk websites perform well even during traffic spikes with minimal downtime.
Plesk also enables load balancing and clustering to spread traffic between servers. Having no single server bottleneck improves dependability. The platform’s solid architecture also features automatic backups and restoration capabilities, providing peace of mind that your data is safe and can be retrieved promptly in case of an incident. These performance and stability characteristics make Plesk reseller hosting a reliable alternative for administering several websites, giving your clients continuous service.
Expanding your company's reseller hosting operations-
Scaling your services
Growing your business requires scaling your Plesk reseller hosting services. Start by evaluating your current resource utilization and discovering any restrictions in your existing configuration. To handle traffic and data storage, you may need to modify your hosting plan or add servers as your client base expands. Plesk lets you add CPU, memory, and bandwidth to customer accounts for easy scaling. Load balancing and clustering can also evenly distribute traffic across servers for better performance and reliability.
Consider broadening your service offerings by introducing new features such as better security solutions, premium assistance, or specialized hosting plans for specific sectors. To match client needs and industry developments, regularly review and update hosting packages. Scaling your services efficiently lets you accommodate customer growth while retaining performance and dependability.
Effective marketing strategies
Effective marketing strategies are crucial for expanding your Plesk reseller hosting business. Determine your target audience—small businesses, bloggers, or e-commerce sites—and personalize your marketing to them. Explain Plesk reseller hosting benefits in blog posts, tutorials, and guides. This draws customers and establishes your hosting authority. Social networking can expand your audience. To develop trust, provide updates, promotions, and client testimonials.
Email marketing campaigns with unique discounts or new features can also be beneficial. To increase your website's exposure to search engines, you should also spend money on search engine optimization or SEO. To draw in organic traffic, use keywords such as Plesk reseller hosting. In order to broaden your reach, lastly, think about forming alliances or working together with web developers and agencies. By putting these marketing ideas into practice, you can increase your clientele and income dramatically.
For better value, bundle
Another efficient strategy to expand margins and stand out is by combining domains with critical web services. Besides delivering additional value to your consumer, bundling also boosts the average order value, which is vital in a market with intrinsically tiny per-product margins.
Web hosts frequently purchase SSL certificates, DDoS protection, email services, and CDNs as part of bundles. Although popular, these products are highly competitive. Besides bundling products, you might offer specialist products like DMARC or VPN services that your competitors may not offer.
Improving customer satisfaction
Enhancing customer experience is important to the success of your Plesk reseller hosting business. Start by giving your clients an easy-to-use control panel for managing their websites, email, and other services. Comprehensive documentation and tutorials can help clients solve common problems on their own. Give customers several support channels, including live chat, email, and phone, and answer questions quickly. Call clients by name and understand their needs.
Request feedback via surveys or direct communication to identify areas for improvement. Furthermore, providing value-added services like performance optimization, security upgrades, and automated backups can greatly enhance the general clientele experience. Providing customers with information about upgrades, new features, and maintenance plans fosters openness and confidence. By focusing on client satisfaction, you may develop long-term connections and drive favorable word-of-mouth referrals.
Best Plesk reseller hosting service providers-
MyResellerHome
One of the most well-known resale hosts is MyResellerHome. Every reseller plan from MyResellerHomecomes with a free domain broker and a free domain name for life. MyResellerHome has a great name for being innovative, dependable, and safe. This is important when you agree to be a reseller for a long time with a company. It is known to release new versions of PHP and MySQL faster than other hosts. With white-label billing, you can give your customers this benefit. A free WHMCS and cPanel license comes with most of MyResellerHome’s Hosting reselling plans.
AccuWebHosting
AccuWebHosting takes the tried-and-true approach of giving shared Linux reseller accounts cPanel and shared Windows reseller accounts Plesk. Although AccuWebHosting has a lot of great features like shared Linux and Windows servers and Windows VPS servers, dealers really like the company's hardware, data center engineering, and customer service.
ResellerClub
ResellerClub's plans come with the Plesk control panel, and you can choose from three different registration options: WebAdmin, WebPro, or WebHost. Business owners who want to run a shared Windows server environment can get Windows reseller products that come with an endless number of Plesk control panels.
InMotionHosting
In its reseller hosting plans, InMotion Hosting gives you a free WHMCS license. These plans use the same NVMe SSD hardware that a lot of users swear by. At InMotion Hosting, there are four main levels of reseller bills that go up to 100 cPanel licenses.
Conclusion-
When looking for the best Plesk reseller hosting, stability, performance, scalability, and support are crucial. Each hosting provider has unique characteristics, and choosing one that meets your demands can greatly impact your reseller business. After careful consideration, MyResellerHome is the best Plesk reseller hosting option. MyResellerHome is the top Plesk reseller provider, giving you the tools and resources to succeed in the hosting industry with its powerful infrastructure, excellent customer service, and extensive range of reseller-focused features.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
What’s a Domain Name and Why Is It So Important for Your Website?
If you’re stepping into the world of websites or online business, one of the first questions that comes to mind is what is domain name? You’ve probably heard people mention it when talking about creating websites, emails, or branding — but what does it really mean, and why is it such a big deal?
In this guide, we’ll explain what a domain name is, how it works, and why it’s essential for building a strong online presence.
What is Domain Name?
A domain name is your website’s unique address on the internet — the name people type into their browser to visit your site. Think of it as your website’s street address in the online world. Instead of remembering a long string of numbers (known as an IP address, like 192.168.0.1), people can type in a simple, memorable name like www.yourbusiness.com.
Every website is hosted on a server that has a numerical IP address. But since numbers aren’t easy for humans to remember, domain names provide a user-friendly way for visitors to reach your site. When someone types your domain into their browser, the internet's Domain Name System (DNS) translates it into the IP address so they can connect to your website.
Why Is a Domain Name So Important?
Choosing the right domain name is one of the most important decisions you’ll make when setting up your website. Let’s explore why:
1️⃣ Creates a Strong First Impression
Your domain name is often the first thing people see about your business or brand. A simple, relevant, and professional domain name helps you create a positive first impression and makes your site appear trustworthy and credible.
Imagine receiving an email from a business that uses a free domain (like yourbusiness.freehosting.com) versus one that uses its own domain (like yourbusiness.com). Which one would you trust more?
2️⃣ Builds Your Brand Identity
Your domain is a key part of your branding. It reflects your business name, services, or purpose — and helps customers remember you. A well-chosen domain name reinforces your brand every time someone visits your site or shares your link.
For example, if you run an online bakery, having a domain like sweetdelights.com is much stronger for branding than something generic or unrelated.
3️⃣ Helps with SEO
While a domain name itself isn’t a magic ticket to top search engine rankings, having a clear and relevant domain can support your SEO strategy. For example, if your domain name includes your business name or a keyword related to your service (such as bestphotography.com), it can slightly improve your visibility for those search terms.
Search engines also look at your domain’s age, trustworthiness, and relevance — all reasons why securing a good domain name early is a smart move.
4️⃣ Gives You Control Over Your Online Presence
When you own a domain name, you control your online identity. You can create custom email addresses (like [email protected]) that look professional and inspire trust. And your domain stays with you — even if you decide to change your hosting company or website builder in the future.
Your domain is a valuable digital asset that grows with your business.
Types of Domain Extensions (TLDs)
Domain names come with different extensions called Top-Level Domains (TLDs). Some common ones include:
✅ .com – The most popular and recognized extension; ideal for most businesses. ✅ .org – Commonly used by non-profits and communities. ✅ .net – Often chosen by tech or networking companies. ✅ .in / .uk / .us – Country-specific domains that show your local presence.
Choosing the right TLD depends on your business type, target audience, and availability.
Tips for Choosing a Good Domain Name
Now that you understand what is domain name, here’s how to pick one that works for your website:
👉 Keep it short and simple: Short domains are easier to remember, type, and share. 👉 Avoid hyphens and numbers: These can confuse people and lead to typing mistakes. 👉 Make it brandable: Your domain should reflect your business name or purpose. 👉 Choose a reliable extension: A .com is generally the safest choice unless you have a reason to choose a different TLD. 👉 Check availability on social media: Ideally, your domain name should match your social media handles for consistency.
How Does a Domain Name Work?
Let’s take a quick look behind the scenes at what happens when someone types your domain into their browser:
1️⃣ The browser checks with the Domain Name System (DNS) to find out what IP address matches your domain. 2️⃣ The DNS translates the domain into the IP address of your website’s server. 3️⃣ The browser then connects to that server and loads your website content.
This process happens in a split second, making it easy for people to access your site using your domain rather than a hard-to-remember IP address.
Why Securing Your Domain Early Matters
The internet is growing fast — and good domain names are getting harder to find. If you have a business idea or personal project in mind, it’s smart to register your domain as early as possible. Even if you’re not ready to launch your site, owning the domain means no one else can claim it.
Once you lose out on a domain, it could be costly or impossible to get it later.
Final Thoughts: What is Domain Name and Why It’s Essential
So, what is domain name, in the simplest terms? It’s your unique address on the internet — your identity that helps people find, trust, and connect with your website.
A good domain name boosts your brand, improves credibility, supports SEO, and gives you full control over your digital presence. It’s one of the most important building blocks of your online success.
👉 Tip: When you’re ready to launch your site, choose a domain that’s clear, memorable, and matches your business goals. A strong domain is an investment that pays off as your website grows.

0 notes
Text
FCSS - SD-WAN 7.4 Architect FCSS_SDW_AR-7.4 Questions and Answers
In today's increasingly interconnected digital landscape, organizations face mounting challenges as their networks grow more intricate and geographically dispersed across multiple locations and regions. The Fortinet Certified Solution Specialist (FCSS) – SD-WAN 7.4 Architect certification has been meticulously crafted for experienced IT professionals who are responsible for designing, implementing, and maintaining these sophisticated infrastructure environments. For those seeking to validate their expertise in this domain, Cert007 offers an extensive collection of the most current FCSS - SD-WAN 7.4 Architect FCSS_SDW_AR-7.4 Questions and Answers, providing a structured pathway to achieving certification success.
What Is the FCSS – SD-WAN 7.4 Architect Certification?
The FCSS – SD-WAN 7.4 Architect exam is a comprehensive assessment designed to validate your hands-on expertise with Fortinet's sophisticated SD-WAN technology stack. This rigorous certification evaluates your practical knowledge of system integration, enterprise-wide management practices, strategic deployment methodologies, and advanced troubleshooting techniques within a secure SD-WAN infrastructure. The exam thoroughly tests your ability to architect and maintain solutions within a robust framework powered by:
FortiOS 7.4.4 - The core operating system that drives Fortinet's industry-leading security and networking capabilities
FortiManager 7.4.5 - The centralized management platform for streamlined configuration and control
FortiAnalyzer 7.4.5 - The advanced analytics and reporting system for comprehensive visibility
Certification Tracks
This exam supports two elite FCSS certification paths:
FCSS – Network Security: Proving your ability to design, secure, and optimize Fortinet-based network security infrastructures.
FCSS – Secure Access Service Edge (SASE): Validates the management of hybrid edge-to-cloud network architectures built on Fortinet solutions.
Who Should Take This Exam?
The exam is ideal for:
Network and security architects
Senior Fortinet professionals managing distributed SD-WAN networks
Engineers designing and deploying secure WAN topologies using multiple FortiGate devices
Exam Details
Detail Information Exam Name FCSS – SD-WAN 7.4 Architect Series Code FCSS_SDW-7.4-AR Format 38 multiple-choice questions Time Allotted 75 minutes Scoring Pass/Fail (report via Pearson VUE) Language English Versions Tested FortiOS 7.4, FortiManager 7.4
FCSS_SDW-7.4-AR Exam Topics Breakdown
To succeed, candidates must show expertise in these key areas:
🔧 SD-WAN Configuration
Initial SD-WAN setup and member definition
Configuring SD-WAN zones
Performance SLA definitions for failover and dynamic path selection
🧭 Rules and Routing
Creating SD-WAN rules for traffic steering
Setting up policy-based and dynamic routing strategies
🛠 Centralized Management
Deploying SD-WAN from FortiManager
Utilizing SD-WAN overlay templates for scalable branch deployment
Configuring and managing branch-level devices centrally
🔐 Advanced IPsec Architectures
Designing hub-and-spoke IPsec topologies
Deploying ADVPN for dynamic secure meshing
Handling multi-hub, multi-region, and large-scale site-to-site deployments
🧪 SD-WAN Troubleshooting
Diagnosing SD-WAN rule application and session behavior
Analyzing routing logic and overlay routing decisions
Debugging ADVPN tunnels, routing loops, and service-level failures
Best Practice Q&A from Cert007
For many successful candidates, Cert007’s FCSS_SDW_AR-7.4 question and answer collection is a game-changer. Here's why:
Real exam alignment: Mimics the format and complexity of actual Fortinet exam items
Regularly updated: Matches changes in FortiOS and FortiManager versions
Exhibit-based questions: Includes troubleshooting outputs, configuration screens, routing tables
Validated accuracy: Reviewed by industry experts and Fortinet-certified professionals
Cert007 empowers you to bridge knowledge gaps, improve time management, and master exam readiness.
Strategy for FCSS_SDW-7.4-AR Exam Success
✔ Know More Than Just the Commands
Understand the why behind each decision: why ADVPN would be used over IPsec, how performance SLAs impact real-world traffic flows, and how centralized configs streamline branch scaling.
✔ Practice Scenario Simulations
Use lab environments to simulate:
ZTP with FortiDeploy
SD-WAN overlays via FortiManager templates
Dual-hub failover with ADVPN
✔ Use Q&A Strategically
Cert007’s questions should supplement, not substitute, your study. Treat them as reinforcement tools.
✔ Take Mock Exams
Simulate the 75-minute experience with at least two full-length practice runs to gauge speed and confidence.
Conclusion
The FCSS – SD-WAN 7.4 Architect certification represents a distinguished milestone in your professional journey, serving as the definitive gateway to establishing yourself as a recognized Fortinet expert in secure, scalable WAN architecture. This prestigious certification not only validates your technical prowess but also demonstrates your ability to architect sophisticated network solutions that meet modern enterprise demands. Through a combination of structured training programs, hands-on laboratory experience in realistic environments, and comprehensive Q&A preparation materials from Cert007, you'll be thoroughly equipped to master the certification requirements and advance your career. Whether you're aiming to enhance your current role or step into more advanced positions in network architecture, your path to success becomes clearly defined and achievable with dedicated preparation and the right resources at your disposal.
0 notes
Text
Developed and released by Mike Little and Matt Mullenweg during 2003, WordPress is one of the most popular, open-source and free Content Management Systems that is based on MySQL and PHP. The popularity of this blogging software can be estimated by its use on the Web that includes more than 60 million websites till January 2015. With increasing popularity, more and more people want to utilize the power of Wordpress to build professional websites with ease. Here’s a list of some of the best books to learn about Wordpress. WordPress To Go - How To Build A WordPress Website On Your Own Domain, From Scratch, Even If You Are A Complete Beginner (By: Sarah McHarry ) Building a website using Wordpress have become very easy with the availability of this book for beginners in the business. This book offers eight easy lessons that enable you to start and maintain your website without any prior knowledge of HTML. With the next 12 lessons, you can customize your unique web presence. Professional WordPress: Design and Development (By: Brad Williams, David Damstra, Hal Stern ) This book is specifically targeted towards advanced developers, who can use in-depth knowledge of the full functionality of the most popular CMS. For that, this edition offers extensive information with updated examples and illustrations of the innovative features. You can also get information about real projects that use this software as an application framework, from the developer’s viewpoint. WordPress Websites Step-by-Step - The Complete Beginner's Guide to Creating a Website or Blog With WordPress (By: Caimin Jones ) Learning how to develop a website in Wordpress has become very easy as this book provides a step-by-step process for developing any website such as choosing a great domain name and best reliable web hosting. This book also offers information how to install Wordpress with a few mouse clicks, publish pages and post in correct formats. Learn various other aspects that are important such as securing a website and customization of content in Wordpress. Wordpress for Beginners: A Visual Step-by-Step Guide to Creating your Own Wordpress Site in Record Time, Starting from Zero! (Webmaster Series Book 3) (By: Dr. Andy Williams ) Create your own Wordpress website even if you are a beginner; this book offers step-by-step information with attractive visual demonstrations. Once a domain of computer geeks, now anyone can build and maintain a professional and attractive website, whether individuals, organizations or community. Every chapter is devoted to one topic and the author offers exercise at the end of each chapter. Wordpress in a week: ...Or less (By: Zak Cagaros ) Would you like to learn how to create any website in WordPress in one week or less? Then this is the best book for you. The author offers comprehensive information regarding Worpress without writing a single HTML code; information ranges from installation of WordPress, mastering WordPress admin area to customizing of themes. Teach Yourself VISUALLY WordPress (By: George Plumley ) The main purpose to write this book is to enable anyone with an internet connection to build a professional website. For that purpose, the writer has offered visual step-by-step process in order to build blogs as well as websites. You can learn the basic setup to advanced mobile features. Some of these features include customization of personalized editing, themes, and plug-ins, as well as purchase of the best domain and web hosting services. Wordpress: Learn Wordpress In A DAY! - The Ultimate Crash Course to Learning the Basics of Wordpress In No Time (Wordpress, Wordpress Course, Wordpress ... Wordpress Books, Wordpress for Beginners) (By: Acodemy ) Want to learn WordPress in a day while having fun? If yes, this is the best book for you. This is a step-by-step guide that teaches you to master the software in a day and create your website even without any technical knowhow. With this
book, you can learn installation of plugins and paid themes, content creation, choosing options on the screen, creation of a page and so on. WordPress Made Super Simple - How Anyone Can Build A Professional Looking Website From Scratch: Even A Total Beginner: Wordpress 2014 For The Website Beginner (Super Simple Series) (By: Jack Davies ) Being a beginner should not stop you from the creation of a content rich and beautiful website, especially with this fantastic book that offers information about creating visually rich websites online. The book offers you an in-depth knowledge that ranges from basics such as the registration of the domain to the use of images and graphics in webpages. WORDPRESS: WordPress Beginner's Step-by-step Guide on How to Build your Wordpress Website Fast (Without Coding)- content marketing, blog writing, WordPress Development, (By: Adam Price ) Create and own a professional website without writing a line of computer code. Whether, you want to create an affiliate site, an e-commerce site, a business site or a personal blog, this versatile book offers extensive information with which you can get success in your chosen endeavor. This book also enables you to optimize your site with required plug-ins. WordPress: Ultimate Beginner's Guide to Creating Your Own Website or Blog (Wordpress, Wordpress For Beginners, Wordpress Course, Wordpress Books) (By: Andrew Mckinnon ) Learning WordPress has never been so easy. This book offers thorough knowledge of various features such as installation, choosing a host, designing websites and the creation and publication of posts. The book also offers SEO strategies like reaching your target audience with Wordpress and retaining their attention. Since its founding, the popularity of Wordpress is on the rise. The main reason behind it is that this online CMS enables the user to create and maintain professional websites without programming knowledge about website languages such as HTML or CSS. The above 10 books are best options for learning the basics and advanced techniques in Wordpress, allowing you to create and maintain SEO friendly websites, quickly and efficiently.
0 notes
Text

Understanding Domain Names
A domain name is the online address of a website. You would require a website's domain in order to locate it online. It functions similarly to a home's address fully dedicated to you.
Importance of Domain names:
It allows your website to be more recognizable to potential customers.
A Good domain name can also help your SEO (search engine optimization) and act as a marketing tool. This is because it would appear in searches and direct more traffic to the website.
It allows you to maintain brand ownership and brand protection.
Using a domain name is simple. You would be able to keep your domain name if you had to relocate to a different country or switch hosting providers. The identity that you have developed is unaffected by your domain name's global reach.
Different Aspects of a Domain Name
An essential part of the internet that converts domain names into IP addresses is the Domain Name System (DNS). It serves as a directory, enabling users to visit websites by entering memorable domain names rather than complex IP addresses. DNS servers are dispersed worldwide and work together to provide fast and dependable domain name resolution. They hold information about domain names and their IP addresses, allowing users to visit websites by just putting in the domain name. On the Internet, root servers are located on 13 different servers. Each of these servers keeps a copy of the same file, which serves as the primary index for the address books on the Internet.

Domain Name Structure
A domain comprises of numerous labels, separated by a dot. Each label indicates a level and location within the DNS. Subdomains are extensions added to the primary domain name that are used to classify and arrange various website components. A dot separates them from the primary domain name, like blog.gigalayer.com. Subdomains can be used to host distinct content, build distinct websites, or grant access to particular services.
Verisign runs the leading domain name registries for two of the most significant top-level domains on the Internet,.com and.net, and contributes to the security, stability, and resilience of the DNS and the internet.
Top Level Domains: This is the last part of a domain name after the last dot. An example of this is .com. IANA, a branch of ICANN (Internet Corporation for Assigned Names and Numbers), is in charge of regulating TLDs. Top level domains can be generic (gTLDs) such as .com, .org, or .net. They could also be (ccTLDs) which are country code top level domains such as .ng, .uk or za. In addition to this, there are sponsored top level domains (sTLDs) such as .edu or .gov.
Second Level Domains: This is the main identifier of the website as it holds the name of the website. In the case of www.gigalayer.com, “gigalayer” would be the SLD. This is because It comes before the last dot.
Subdomain: With the use of subdomains, website owners can establish distinct areas or subsites inside their primary website. For instance, a business might have a blog under a different domain. For example blog.gigalayer.com.
Registering a Domain Name
There are three R's in the domain registration procedure: Registrar, Registrant, and Registry.
Registry: A domain registry is a centralized database with current data about domain names and their associated owners. A sizable organisation that oversees the top-level domain is in charge of this database.
Registrar: a domain registrar's primary responsibility is to make domain names accessible to the general public and assist the registry in updating its records upon a customer's purchase.
Registrant: The registrant, who may be an individual or a company, registers a domain with a registrar and uses them to maintain their domain information and settings.
What can you do with a Domain name
A domain name can be used for a variety of purposes. The ability to establish a website is the primary purpose of a domain name. It could also be used to start a blog. By doing this, domain forwarding will be enabled, allowing you to access the blog or social networking page by forwarding your domain name to another website. After creating a website, hosting bespoke email addresses is the second most popular use of a domain name. Given that it includes your company name, it gives your email a more professional look. Furthermore, a variety of cloud services and apps can be utilised with domain names.
IP Address and Domain Names

An IP address is a special number that is given to every internet-connected device. Unlike IP addresses, domain names (such as google.com or wikipedia.org) are simpler for people to type and remember. They act as a link or identity for a specific IP address. DNS servers, which are dispersed around the internet, keep track of domain names and the IP addresses that go with them.To locate the relevant IP address and connect you to the website, your computer uses the DNS.
In order to prevent duplication or conflicts, ICANN assists in coordinating the distribution of IP addresses. Additionally, ICANN serves as the primary IP address storage centre, from which ranges are provided to regional registries, who then disperse them to network operators.
The WHOIS directory can be used as a tool to find out who owns IP addresses and domain names. WHOIS is a public list of domain names together with the individuals or groups linked to each name.
-- Maryam I.
0 notes
Text
Ajmera 78 Lake Town Codename Now Or Never Bhandup Powai
Where Dreams Meet Addresses: Welcome to Ajmera 78 Lake Town
This high-rise is the updated residential community; it's one of the main parts of the city that keeps residents in Mumbai happy. This beautiful structure addresses the needs of contemporary families and individuals who seek the ideal combination of comfort, location, and lifestyle within the confines of the city. Bearing the memorable name Codename Now Or Never, this home delivers on its name by bringing a once-in-a-lifetime chance to get a home at one of the most promising locales in Mumbai at an affordable rate, without even sacrificing connectivity and convenience.
With thoughtfully designed layouts, premium fittings, and open views, the entire dwelling structure resonates with the aspirations of the first-time homebuyer. For those who’ve long dreamt of planting roots in Mumbai but have been priced out of traditional hotspots, this condominium makes that ambition attainable. It brings together form and function in a setting that is urban yet peaceful, practical yet indulgent; a refreshing deviation from the typical high-rise narrative.

The Pulse of the City: Why Bhandup is the New Address to Watch
Strategically located near Powai Vihar Link Road, Now Or Never Bhandup benefits from the natural progression of growth in Central Mumbai. Bhandup, formerly an industrial area, is now seeing a residential revival brought about by its great road and railway connections, increased social infrastructure, and new urban developments in the pipeline. Through the building of the Panvel-Virar Link Road (PVLR), Bhandup is more and more becoming a part of the leading areas of the city, providing connections that are very efficient and less time-consuming to both the eastern and western parts of the city.
The locale around the development is full of opportunities. Living near such commercial localities as Powai, Kanjurmarg, and Mulund enhances the value. In addition, major implementation in the transportation domain, like Metro Line 4 and the Goregaon-Mulund Link Road, will cut down the time. The Bhandup area is well-known; in fact, it is now a hot destination for both principal and real investors.
Built on Trust: The Ajmera Legacy in Real Estate
Ajmera Realty is a renowned name in the field of urban development. The company has become a dependable force in the real estate of India with 50 years of experience and over 46,000 families having lived in an Ajmera property. With a reputation for being customer-oriented, transparent, and timely in delivery, Ajmera brings the trust and vision of customers to each new project it participates in.
Ajmera Codename Now Or Never Bhandup is no exception to this legacy. The project highlights the extensive knowledge of the changing housing requirements of people from Mumbai, thus creating elegant buildings with high-quality construction and committing to being sustainable, which solves
the city's major problems. For homebuyers who seek assurance in quality and consistency, choosing an Ajmera residence means choosing peace of mind.

Lifestyle Elevated: Amenities That Make Life Better
A home at Codename Now Or Never isn’t just about the four walls; it’s about the lifestyle that comes with it. The property offers modern facilities that are aimed at providing health, recreation, and socialization advantages to the residents. There are beautifully manicured lawns, fitness centers, playgrounds for kids, and indoor gaming areas provided for residents to create an energetic environment of different age groups in the gated area.
The house also focuses on convenience and security, with day-and-night guarding, assigned parking lots, and high-tech fire safety systems. All the amenities have been well-selected to bring everyday life into sharper focus while still being able to connect to nature and calm. Whether a professional looking to find work-life balance or an expanding family that requires space and security, the following features assure home life at the residence is both fulfilling and convenient. Investing in Tomorrow: A Smart Choice for the Long Term
Property in Central Mumbai has always been regarded as a solid investment, and Bhandup is now also becoming a niche-market. With improvements in infrastructure, good social amenities, and the revamp of the landscape surrounding it, this area is set for steady capital appreciation. Now Or Never Bhandup, located at the confluence of progress and connectivity, presents an excellent opportunity for both end-users and investors to secure valuable real estate.
Also, the demand for in-city living is growing, especially for first-time buyers who desire convenience without compromising quality. With rental yields on the rise and occupancy levels healthy in this region, home ownership in this tower can be financially beneficial in the short and long run. It’s more than just a home; it’s a wise financial move backed by a reputed name and a promising location. A Beginning, Not Just an Address
Ajmera Codename Now Or Never Bhandup is not merely a residential structure; it symbolizes a new chapter for many who wish to call Mumbai their forever home. It provides an answer to the growing need for affordable, premium homes within city limits and creates a lifestyle that supports both personal aspirations and urban living. In an environment where leaving the city was once considered the only path to homeownership, this establishment turns the narrative on its head.
In conclusion, this unique offering from Ajmera Realty isn't just changing the skyline of Bhandup; it’s changing the possibilities for thousands of homebuyers. With its unbeatable location, visionary design, trusted brand name, and world-class features, this marvel truly stands out as the in-city first home that’s worth every consideration.
#ajmeranowornever#noworneverbhandup#ajmeranoworneverbhandup#ajmeracodenamenowornever#ajmeracodenamenoworneverbhandup#codenamenowornever
1 note
·
View note
Text
What is briansclub cm?
Brian's Club: Understanding the Underground Marketplace

In the shadowy corners of the internet where cybercrime flourishes, one name often emerges in conversations — briansclub. But what exactly is Brians Club, sometimes stylized as briansclub cm or simply bclub? This article explores the notorious platform, its origin, operations, and the implications of its existence in today's digital age.
What is Brians Club?
Brians Club is a large and infamous online marketplace that specializes in the trade of stolen credit card information. Operating on the dark web, briansclub cm has become one of the most well-known hubs where cybercriminals sell illicitly acquired payment card data. This platform functions somewhat like a commercial website but exists in an entirely illicit domain, facilitating underground financial fraud.
Unlike legal e-commerce websites, bclub caters exclusively to criminals who seek to profit from data breaches, phishing attacks, and other forms of cyber theft. The site offers a variety of stolen card data categorized by country, type of card, and sometimes even by bank, making it easier for buyers to select lucrative targets for fraud.
The History and Growth of Brians Club
Brians Club first garnered attention in cybersecurity circles following several high-profile data breaches involving point-of-sale (POS) systems. The platform allegedly emerged after big retail chains were infiltrated by hackers who obtained millions of card details, which were then funnelled onto briansclub cm for resale.
Over time, briansclub grew in notoriety as one of the largest dumpsites for carding data globally. It gained a reputation for its extensive databases of compromised cards and an interface that was user-friendly even by legitimate e-commerce standards, thereby facilitating easy transactions between sellers and buyers.
How Brians Club Operates
The operational model of bclub closely mimics legitimate online marketplaces but with a criminal twist. Users must typically register using encrypted and anonymous methods to mask their identity. Transactions often involve cryptocurrencies like Bitcoin, adding another layer of anonymity and making the money trail harder to trace.
Brians Club provides extensive listings with meticulous details about the stolen cards, including card number, expiration date, CVV code, and sometimes additional personal information. This granularity helps criminals assess the value before purchasing, enabling targeted and potentially large-scale fraudulent activities.
To maintain its network, briansclub cm often provides services such as stolen card verification to ensure buyers get functional data, increasing their market reliability and reputation in the underground economy.
Security and Law Enforcement Response
The notoriety of briansclub has made it a prime target for law enforcement agencies worldwide. Various international cybercrime units have coordinated efforts to track, infiltrate, and dismantle such marketplaces. Despite these efforts, the platform has been resilient, often resurfacing with new domains or slight reconfigurations to evade shutdowns.
Security experts continuously monitor bclub to analyze attack patterns, understand criminal behaviors, and develop better protective measures for consumers and financial institutions. Awareness campaigns also warn people about common scams and encourage regular monitoring of bank statements as a preventive practice against credit card fraud sourced from markets like Brians Club.
Risks and Implications for Individuals and Businesses
Purchasing stolen financial data on briansclub fuels a cycle of crime that victims worldwide suffer from. Individuals whose data is sold face unauthorized transactions, credit damage, and extensive hassles to reclaim their identity and finances.
For businesses, breaches that lead to listings on sites like briansclub cm result in loss of customer trust, legal consequences, and significant financial damages. The existence of bclub underscores the critical necessity of robust cybersecurity defenses and stringent data protection policies.
The Future Outlook
As cybercrime tactics evolve, platforms like briansclub may become more decentralized and harder to track. Emerging technologies such as blockchain may also influence how such illegitimate marketplaces operate in the future.
Still, global cooperation among law enforcement, technological advancements in fraud detection, and increased user vigilance remain key to combating the threats posed by briansclub cm and similar entities.
Conclusion
Brians Club remains a stark reminder of the darker side of the digital era—a place where stolen financial information is commodified, and cybercriminal activities thrive. Understanding this platform's role is essential for anyone invested in cybersecurity, digital commerce, and online safety.
By staying informed about threats like those from bclub, both individuals and businesses can better prepare defenses, reduce risk exposure, and contribute to efforts that aim to shut down illicit operations exploiting stolen financial data.
1 note
·
View note
Text
Woo Subscription Downloads nulled plugin 1.4.1

Unlock Premium Features with Woo Subscription Downloads Nulled Plugin Take your WooCommerce store to the next level by integrating the Woo Subscription Downloads nulled plugin. This powerful tool allows you to effortlessly manage downloadable files for subscribers, making it easier than ever to offer premium digital content. Whether you're selling eBooks, software, music, or any other downloadable file, this plugin is your gateway to automating and monetizing recurring downloads efficiently. What is Woo Subscription Downloads Nulled Plugin? The Woo Subscription Downloads nulled plugin is a premium WooCommerce extension designed to streamline digital product delivery for subscribers. With this nulled version, users can access the same premium features completely free of cost. It empowers store owners to assign downloadable files to specific subscription products, giving customers access to exclusive content for as long as their subscription remains active. Unlike standard WooCommerce setups, this plugin creates a seamless download management system that integrates perfectly with your subscription model. It provides a clear, user-friendly interface where subscribers can easily find and access their downloadable files from their account dashboard. Technical Specifications Plugin Name: Woo Subscription Downloads Version: Latest Nulled Release Compatibility: WooCommerce 5.0+ and WordPress 5.8+ License: GPL (General Public License) File Type: .zip (Installable via WordPress Dashboard) Key Features and Benefits Direct File Assignment: Easily attach download links to subscription products. Automated Access: Subscribers instantly gain access to relevant files upon activation. Download Dashboard: Users can view and download files directly from their account. Expiration Control: Automatically revokes file access when a subscription expires. Flexible Integration: Compatible with a wide range of WooCommerce extensions and themes. Real-World Use Cases The Woo Subscription Downloads nulled plugin is perfect for content creators, educators, developers, and marketers who want to offer exclusive downloadable content. Imagine a membership site offering monthly eBooks or a developer portal sharing premium plugins—this tool ensures only active subscribers can access these valuable resources. It’s also ideal for musicians sharing exclusive tracks or designers offering monthly design assets. Simple Installation and Usage Guide Installing the Woo Subscription Downloads nulled plugin is simple and straightforward: Download the .zip file from our website. Log into your WordPress admin panel and go to Plugins > Add New. Click Upload Plugin and select the .zip file. Click Install Now and then Activate. Navigate to your subscription products and assign downloadable files as needed. After activation, customers with active subscriptions will see a new section under their account where they can access the files associated with their purchased subscriptions. Frequently Asked Questions (FAQs) Is the nulled version safe to use? Yes, the nulled version available on our website is thoroughly tested and malware-free. We recommend downloading only from trusted sources like ours to ensure your site's security. Can I use this plugin on multiple sites? Absolutely. Since it’s distributed under the GPL license, you’re free to use it on as many domains as you like. Will I get updates? As this is a nulled version, automatic updates are not available. However, you can manually update it by downloading the latest release from our site. Is this plugin compatible with my theme? Yes, it is fully compatible with most modern WordPress themes. For optimal performance, we recommend trying it with themes like kallyas NULLED. Why Choose Woo Subscription Downloads Nulled Plugin? With the Woo Subscription Downloads you’re not just getting a free tool—you’re unlocking access to a system that streamlines the user experience, improves content delivery, and maximizes subscription value.
It’s a game-changer for anyone looking to provide gated digital content to loyal subscribers. And the best part? You can access all these features without spending a dime. Don’t miss out—download the nulled plugins you need today and supercharge your WooCommerce store!
0 notes
Text
0 notes
Text
AddTon: TONCOIN Project Overview
TONCOIN ARBITRAGE TRADING AND APY STAKING PROGRAM based on the work of Dr. Nikolai Duro

Abstract :
The Open Network (TON) is a fast, secure and scalable blockchain and network project, capable of handling millions of transactions per second if necessary, and both user-friendly and service provider–friendly. We aim for it to be able to host all reasonable applications currently proposed and conceived. One might think about TON as a huge distributed supercomputer, or rather a huge super server, intended to host and provide a variety of services. This text is not intended to be the ultimate reference with respect to all implementation details. Some particulars are likely to change during the development and testing phases.
About TONCOIN Blockchain :
Blockchain Name: The Open Network (TON Blockchain)
Founders: Pavel Durov (Founder of Telegram) and Nikolai Durov (Chief Architect)
Initial Development: 2018–2019 (transitioned to a community-led project after regulatory issues)
Token Symbol: TON
Blockchain Type: Layer-1 (Comparable to Ethereum, Solana)
Consensus Mechanism: Proof-of-Stake (PoS)
Special Note: Nikolai Durov designed the blockchain’s technical foundation: Infinite sharding, vertical scaling, instant payments.
TONCOIN Ecosystem Overview
Wallets: Telegram Wallet (integrated), Tonkeeper, Tonhub, OpenMask, MyTonWallet
DEX Platforms: STON.fi, Dedust.io, Megaton Finance
Browser Extensions: Tonkeeper Extension, OpenMask Browser Wallet
Web3 Applications: TON DNS, TON Storage, TON Sites, Telegram Wallet Bots
Gaming Initiatives: TON Punks, Fanton Fantasy League, Tap Fantasy Game, StormTrade (gaming and trading dApp)
NFT Marketplaces: Getgems.io, TON Diamonds, Disintar.io
Other Projects: TON Proxy, TON Payments, TON Wallet Bots, Open League (Gaming)
TONCOIN Global Market Position:
Listed on: Binance, OKX, KuCoin, Bybit, MEXC, Huobi, etc.
Market Presence: Active in 340+ markets globally.
Ranking: Consistently Top 15 on CoinMarketCap and CoinGecko
Daily Trading Volume: Exceeds $100 million.
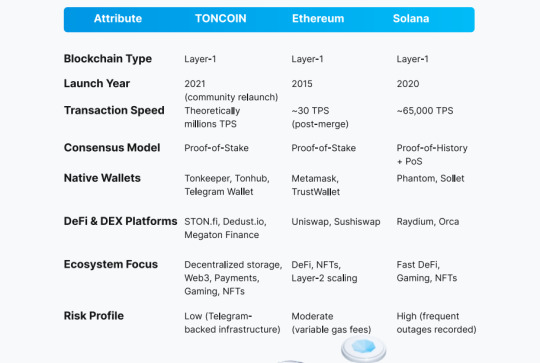
Blockchain Industry Comparison:
How Addton.io Arbitrage Trading Works:
Focus Asset:
Addton.io only works on TONCOIN. Trading pair: TONCOIN/USDC (uses price gaps between TON and USDC)
Trading Platforms:
Trading happens only on decentralized exchanges (DEX)
STON.fi
Dedust.io
AI-Powered Arbitrage Bot:
A specialized AI trading bot has been developed. The bot monitors real-time TONCOIN prices across both exchanges.
Price Difference Capture:
When there is a price difference (example ) If the STON.fi TON price = $2.00 and the Dedust.io TON price = $2.05, then the bot automatically buys from the lower price exchange (STON.fi) and sells at the higher price exchange (Dedust.io).
Profit Generation:
Through this buying-selling cycle, organic profit is generated (without speculative risk). No leverage, no betting — only real price gap arbitrage.
Daily Operations:
The bot remains active from Monday to Friday (Saturday–Sunday off). Profits are distributed daily to staking participants.
Security:
There is no centralized risk, as trading occurs only through decentralized (on-chain) DEXs.
Program Launch and Ecosystem & Partnership:
Endorsed by the TON Blockchain community.
Supported by the Tapmoon Ecosystem.
Launch of The Open Network Classic Blockchain:
Native Token: TONCOIN Classic (CTON) Ticker: CTON Launch Price: $0.003 Participants will receive CTON tokens equal to their staking package value
Income Distribution and Incentives:
Participants will benefit from:
Daily arbitrage profits credited in TONCOIN.
CTON token bonus matching the staking package.
Special promotions and rewards in TAPS Token.
Risk Mitigation and Client Protection
TAPS Token Compensation
In case of trading losses, TAPS Tokens will be awarded.
Guaranteed CTON Tokens
Regardless of trading performance, CTON tokens will be distributed, securing future asset value.
Project Name Description:
Project Name : Description TON DNS : Web3 domain naming system TON Proxy : Decentralized VPN and privacy services TON Storage : Blockchain file storage TON Sites : Decentralized web hosting TON Payments : Layer-2 micropayment solutions STON.fi : Largest DEX on TON Dedust.io : Major decentralized exchange Megaton Finance : DeFi trading platform Getgems.io : NFT marketplace TON Diamonds : Premium NFT marketplace Disintar.io : NFT creation and trading platform Fanton Fantasy League : Fantasy sports gaming Tap Fantasy : Game Metaverse gaming Storm Trade : Trading and gaming hybrid dApp Open League : Decentralized esports and gaming platform
Why Choose Addton TONCOIN Staking Program?
Built on Telegram’s original blockchain vision (Pavel and Nikolai Durov)
Pure AI-based decentralized arbitrage trading.
Daily profits + bonus rewards in TONCOIN, CTON, and TAPS.
Dual protection model for user assets.
Integrated with Tapmoon Ecosystem.
Strong and growing TON Blockchain ecosystem support.
Website | twitter(X) | Telegram | Reddit | Facebook | Youtube
1 note
·
View note
Text
Fast Flux Debrief

SIGNALFOG ENTRY: FAST FLUX AND THE NATIONAL SECURITY WIREWALK
What is Fast Flux?
Fast Flux is not a tool. It is a tactic—a slippery eel of cyber maneuvering used to shield malicious networks from takedown. At its core, Fast Flux is a technique for hiding phishing and malware delivery sites behind constantly changing IP addresses. Think of it as DNS shell game played at machine speed.
There are two main types:
Single-Flux – Frequently changes the IP addresses associated with a single domain name. A domain might resolve to five different IPs in under an hour. Those IPs are often bots in a compromised network.
Double-Flux – Mutates not only the IPs but also the name servers associated with the domain, creating a recursive maze of obfuscation. This is where things get nasty—each step reconfigures the puzzle.
Behind this flux cloud often sits a botnet, frequently leveraging criminal marketplaces or nation-state infrastructure, using the technique to hide:
Phishing sites
C2 (command and control) servers
Malware droppers
Credential harvesters
Why the NSA Considers It a National Security Threat
Fast Flux undermines attribution. In cyberwarfare, attribution is the new battleground. If you can’t pin an attack to an actor or infrastructure, you can’t deter, retaliate, or even understand intent. That makes Fast Flux a fog-of-war amplifier—a denial-of-attribution machine used not just by cybercriminals but by nation-state advanced persistent threats (APTs).
This tactic has been used to:
Distribute ransomware to critical infrastructure (e.g., Colonial Pipeline incident had partial DNS obfuscation elements)
Support long-term espionage operations (APT29 and others)
Exfiltrate sensitive data from government and defense contractors
It’s not just technical noise—it's sovereignty erosion via DNS.
Current Countermeasures
The countermeasures form a fragile ecosystem, not a silver bullet.
1. DNS Monitoring and Sinkholing
Agencies like US-CERT and NSA operate sinkholes—servers that simulate malicious domains to draw in Fast Flux queries and analyze them.
Security vendors offer passive DNS monitoring to correlate domain activity, TTLs (time-to-live), and ASNs (Autonomous System Numbers) that suggest flux behavior.
2. AI-Powered Anomaly Detection
Models trained on DNS query patterns identify abnormally high TTL churn, geographical dispersion of IPs, and unusually frequent domain-to-IP flips.
Emerging tools like PassiveTotal or Farsight DNSDB are leveraged to track malicious flux patterns.
3. Threat Intelligence Feeds
Enrichment of security tools with real-time feeds (e.g., from Mandiant, Recorded Future) to identify Fast Flux domains and block them at the firewall or endpoint level.
4. Domain Takedown Coordination
Multinational coordination with registrars and ISPs to revoke domains or neutralize the infrastructure (example: Operation Ghost Click, which dismantled DNSChanger infrastructure).
5. Advanced DNSSEC and DoH Filtering
DNS Security Extensions (DNSSEC) can help verify legitimacy, though flux domains often bypass this.
DNS over HTTPS (DoH) presents a double-edged sword: it can encrypt good and bad traffic alike. Thus, filtering on endpoints and proxies becomes essential.
6. Network-Level Behavioral Firewalls
Zero Trust Network Access (ZTNA) models segment networks to reduce botnet beaconing.
Behavioral IDS/IPS like Suricata detect lateral movement even if DNS resolution appears clean.
But Here's the Rub:
Fast Flux is not a flaw—it’s a clever exploitation of how the internet was designed to work: decentralized, resilient, fault-tolerant. The same qualities that make global communication work in disaster zones are co-opted to hide the hands of digital saboteurs. The NSA’s concern isn’t just technical—it’s existential. Because in the cyber-domain, whoever owns attribution owns the narrative.
“In war, truth is the first casualty; in cyberwar, it’s attribution.” — Anonymous NSA SIGINT Analyst, 2014 (declassified quote, attribution unknown...ironically)
0 notes
Text
Expert Advocate for Digital Arrest Cases
Expert Advocate for Digital Arrest Cases: Advocate Deepak and His Expertise in Cyber Law

is Advocate Deepak, a legal expert with a strong academic background, including degrees in B.Sc, LLB, MBA, MeBA, and DDM. With his profound knowledge of cyber law and digital forensics, Advocate Deepak is a trusted name when it comes to handling digital arrest cases and protecting the rights of those involved.
Understanding Digital Arrest Cases
Digital arrest cases involve individuals accused of committing cybercrimes or other online offenses. These cases range from identity theft and hacking to online fraud and digital harassment. Given the complex and technical nature of such offenses, it is crucial to have a legal expert who understands both the legal and technological aspects of cybercrime.
Advocate Deepak has built a reputation for his expertise in handling such cases with precision, ensuring that justice is served. His ability to dissect complex digital evidence, understand cybersecurity laws, and navigate the legal framework makes him a formidable force in the field of cyber law.
Educational Background of Advocate Deepak
Advocate Deepak’s academic qualifications make him a highly competent professional in the legal and digital domains. His educational journey includes:
B.Sc (Bachelor of Science): Provides him with a strong analytical and scientific foundation, essential for understanding technical aspects of cybercrimes.
LLB (Bachelor of Laws): Equips him with the knowledge of legal principles, case laws, and judicial procedures required for handling cyber-related cases.
MBA (Master of Business Administration): Enhances his understanding of business dynamics, making him well-versed in corporate cybercrimes such as financial fraud and data breaches.
MeBA (Master of e-Business Administration): Focuses on digital business models, e-commerce laws, and online regulatory frameworks, further strengthening his expertise in cyber law.
DDM (Diploma in Digital Marketing): Helps him understand online platforms, digital strategies, and the ways cybercriminals exploit these mediums for illegal activities.
This extensive academic background enables Advocate Deepak to approach digital arrest cases with a multidisciplinary perspective, ensuring a well-rounded defense strategy.
Latest Cybercrime Types and Methods
Cybercriminals continuously adapt to emerging technologies, making it crucial to stay updated with the latest cybercrime methods. Below are some of the most prevalent cybercrimes today:
1. Phishing Attacks
Phishing is a fraudulent practice where cybercriminals use fake emails, messages, or websites to steal sensitive information such as usernames, passwords, and credit card details. Attackers often impersonate reputable organizations to deceive victims into providing personal data.
2. Ransomware Attacks
Ransomware is a type of malicious software that encrypts a victim’s data, demanding a ransom payment for decryption. These attacks can cripple businesses, government institutions, and individuals by locking them out of their own systems.
3. Identity Theft
Cybercriminals steal personal information such as social security numbers, bank details, and login credentials to commit fraud, open fraudulent accounts, or make unauthorized transactions.
4. Hacking and Data Breaches
Hacking involves unauthorized access to computer systems, networks, or databases. Cybercriminals exploit vulnerabilities in security systems to steal sensitive data, disrupt services, or launch further attacks.
5. Online Harassment and Cyberbullying
The rise of social media has also led to an increase in online harassment and cyberbullying. Cybercriminals use digital platforms to threaten, intimidate, or defame individuals, often causing psychological distress to victims.
6. Deepfake Technology
Deepfakes use artificial intelligence to create realistic but fake audio, video, or images. These manipulations can be used for misinformation, fraud, or blackmail, posing significant challenges for cybersecurity professionals and legal experts.
7. Cryptocurrency Scams
With the rise of digital currencies like Bitcoin, cybercriminals have devised scams, including fake investment opportunities, Ponzi schemes, and hacking of cryptocurrency wallets.
8. Social Engineering Attacks
Social engineering exploits human psychology to manipulate individuals into divulging confidential information. This includes techniques like pretexting, baiting, and tailgating to gain unauthorized access to sensitive data.
9. IoT-Based Cyber Attacks
The increasing adoption of Internet of Things (IoT) devices has also introduced new vulnerabilities. Cybercriminals target smart devices to launch attacks, steal data, or compromise home security systems.
Safety Tips to Prevent Cybercrimes
While legal experts like Advocate Deepak play a crucial role in addressing cybercrimes, individuals and businesses must take proactive measures to protect themselves. Below are some essential cybersecurity tips:
1. Use Strong Passwords
Always use strong, unique passwords for different accounts. A combination of uppercase and lowercase letters, numbers, and special characters enhances security. Using a password manager can help manage multiple passwords securely.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring a second verification step, such as a one-time code sent to a mobile device.
3. Be Wary of Phishing Attempts
Avoid clicking on suspicious links or opening attachments from unknown senders. Always verify the authenticity of emails and messages before sharing sensitive information.
4. Keep Software and Systems Updated
Regularly updating software, operating systems, and security patches help protect against vulnerabilities that cybercriminals exploit.
5. Use Secure Networks
Avoid using public Wi-Fi for sensitive transactions. If necessary, use a Virtual Private Network (VPN) to encrypt data transmission.
6. Monitor Financial Transactions
Regularly check bank statements and transaction alerts to detect any unauthorized activities.
7. Educate Employees and Family Members
Cybersecurity awareness training helps employees and family members recognize potential cyber threats and follow best practices.
8. Backup Important Data
Regularly backing up critical data ensures that information can be recovered in case of a cyberattack.
9. Use Reliable Security Software
Invest in reputable antivirus and anti-malware software to protect devices from cyber threats.
10. Report Cybercrimes Immediately
If you become a victim of cybercrime, report it to the relevant authorities and seek legal assistance from experts like Advocate Deepak.
The digital world presents both opportunities and risks, with cybercrime being a significant threat to individuals and businesses. Advocate Deepak, with his vast academic qualifications and expertise in cyber law, is a leading legal professional in handling digital arrest cases. His knowledge of the latest cybercrime methods and preventive measures makes him a valuable advocate for justice in the digital realm.
By staying informed and implementing cybersecurity best practices, individuals can minimize their risk of falling victim to cybercriminals. However, in case of legal complications, seeking professional assistance from experts like Advocate Deepak is essential to ensure legal protection and justice.https://bestcybercrimelawyer.in/
0 notes