#Edge and Endpoint AI
Explore tagged Tumblr posts
Text
Backend Support
Something new for you tonight, True Believers: a story set in @subliminalbo's Literary Universe! Featuring an image manipulation graciously provided by the man himself!
This story references characters from the Obedience by Fleur series. While not required, the main stories are suggested reading.
Thanks to my friend @subliminalbo (also at @subliminalboarchive) for the collabo.

Bailey's Huawai flagship, customized with added security and privacy features, rang and buzzed on her workbench. Her brow furrowed, temporarily wrinkling her flawless golden skin. "Support," Bailey muttered with caution as she answered. Very weird. If someone's calling this number… something is wrong.
"Uh," a timid male voice stuttered in response, followed by a long pause. "Um, I think I fucked up."
Bailey closed her eyes, sighing. "Go on."
"Well, I…," the man continued, but his cadence suggested he was distracted. "Hey, um, honey, don't touch that," he interjected, before refocusing his attention on Bailey. "I think she's broken. I broke her."
"You. Broke. Her," Bailey repeated slowly, each word more incredulous than the last. "And how… how did you break her, sir?"
Bailey thought she heard the man swallow hard through the tinny speakerphone. "OK. Well. I know that she has some, um, default abilities."
"Yes. Her menu. This was explained when you requested her services."
Loud noises. The sound of glass breaking. "Shit," the man said in irritation. "that was a gift!" He continued, talking faster, Bailey could practically hear him sweating. "Well, I wanted to know if she had, like, a secret menu. So I asked her, and she said no, but that there was…"
"An API," Bailey muttered. Fuck. She tilted her head back, eyes closed, and sighed again. She would have to work on hardening that endpoint. The last thing she needed was incel dipshits like Johnny Mnemonic here fucking with the product. She was a damn good engineer, but you don't exactly get to beta test mind control technology before you put it into production.
She should know. She was not only the president, she was also a client.
"What did you do, sir? Exactly?" Bailey's words were polite, but her tone dripped with frustration. Condescension also, but she really wasn't concerned about the customer's feelings right now.
Another pause, then an admission. "Well, she started telling me about her API, and I'm not a programmer, so I asked ChatLLM. And it gave me some things to try. Baby, take that out of your mouth."
"You fucking vibe coded her. You vibe coded a sex drone escort, running assembly code firmware, with some commands you got from a consumer AI. She's a human being, not a kit you bought at Radio Shack." Bailey could barely contain her rising anger. She mentally adjusted her hormone levels. Her pupils faded completely into solid white spheres. This wasn't the time to lose her cool.
There was hemming and hawing, then finally a guilty, "yes."
Bailey spoke again, the edge out of her voice as the fury subsided and her pupils returned. "Well, seeing as this would violate the terms and conditions of your agreement, if there were such a thing, I'm here to tell you: you break it, you buy it. Five mil ought to cover it. Have a good one."
"Five mil…five million dollars?!" the man exclaimed. Bailey could hear his voice quivering. "I don't have that kind of money! I work retail!"
"I'm sorry," Bailey said. And to her credit, she did pity this man. She knew enough to know his death would not be quick or painless. Triads don't fuck around. "The people I work with, they don't…" She chose her words carefully for effect. "take damaged merchandise lightly."
Bailey could her muffled crying on the other end. More broken glass, but no admonishment. Just sobs. She didn't like this. Didn't like the choices on the table. Having to calculate the least shitty outcome. Compromising her morality - her humanity - one crossed line after another.
But who was she kidding? Compromising your morality was The Romero Way.
"I don't want your dumbass blood on my hands. I'll make you a deal. Give me someone to replace her."
"I don't…what do you mean?"
"A wife, a sister, a cousin. Someone hot, or at least cute. Fixable. Someone local. A name, and an address, and you get to celebrate another birthday."
She could practically hear the man bargaining with himself. "I couldn't. I won't."
Bailey's voice was firm and callous. "No skin off my ass. Hope your will is in order." Give me a name, she pleaded internally. Take the goddamn offer.
"OK. I'll text it over." Very quietly, Bailey exhaled in relief. Her phone buzzed with a notification. She glanced at the address, and forwarded it to her liaison with some notes about tonight.
"You made the right choice. A team is on their way for extraction. For her, and for you."
"For me?"
"You know too much. Also, we have room in our inventory for all genders and sexual identities." In Romero, there are only perverts, and people who aren't perverts yet, Bailey ruminated.
When the man finally spoke, his voice was quiet, and his tone resigned. "Will she be okay? Will she be happy?"
Bailey hesitated. She thought of her mother, Rosa, her eyes glassy, wearing a low-cut red dress and her black choker, leaving a young child alone on a Saturday night. Baby, Mamá's got to go somewhere. Be a good girl and take care of yourself, okay?
She wanted to cynically deliver the uncaring truth. No, she wouldn't be okay. Ultimately, her happiness wasn't important, was it? It sure as hell hadn't been for Rosa, or for young Bailey. If you weren't part of Romero's circle of elites, you were just collateral damage.
But she didn't say that.
"Yes," Bailey lied, her voice soft and comforting. "She will." And she ended the call.
Bailey sat at her workbench for a long time, alone. Only the trees rustling outside the window permeated the silence. It could have been worse, she tried to tell herself. A lot worse. She saved a man from his own stupidity tonight.
When did she get so soft?
Ed King and Elena Maxwell had ruined her career before it got started, and they were going to pay. She only needed to set her emotions aside, and finish the job.
So why was she disgusted with herself?
These questions lacked simple answers. Tonight, isolated in her empty house, questions were the only company Bailey had.
#mind control#mind corruption#hypno fantasy#hypno story#tech control#reprogramming#brainwashing kink#hypnok1nk#hypno drone#humor#vibe coding#subliminalbo#ottopilot-wrote-this#cw: mind control#cw: corruption#cw: hypnosis#cw prostitution
14 notes
·
View notes
Text
Alltick API: Where Market Data Becomes a Sixth Sense
When trading algorithms dream, they dream in Alltick’s data streams.
The Invisible Edge
Imagine knowing the market’s next breath before it exhales. While others trade on yesterday’s shadows, Alltick’s data interface illuminates the present tense of global markets:
0ms latency across 58 exchanges
Atomic-clock synchronization for cross-border arbitrage
Self-healing protocols that outsmart even solar flare disruptions
The API That Thinks in Light-Years
🌠 Photon Data Pipes Our fiber-optic neural network routes market pulses at 99.7% light speed���faster than Wall Street’s CME backbone.
🧬 Evolutionary Endpoints Machine learning interfaces that mutate with market conditions, automatically optimizing data compression ratios during volatility storms.
🛸 Dark Pool Sonar Proprietary liquidity radar penetrates 93% of hidden markets, mapping iceberg orders like submarine topography.
⚡ Energy-Aware Architecture Green algorithms that recycle computational heat to power real-time analytics—turning every trade into an eco-positive event.
Secret Weapons of the Algorithmic Elite
Fed Whisperer Module: Decode central bank speech patterns 14ms before news wires explode
Meme Market Cortex: Track Reddit/Github/TikTok sentiment shifts through self-training NLP interfaces
Quantum Dust Explorer: Mine microsecond-level anomalies in options chains for statistical arbitrage gold
Build the Unthinkable
Your dev playground includes:
🧪 CRISPR Data Editor: Splice real-time ticks with alternative data genomes
🕹️ HFT Stress Simulator: Test strategies against synthetic black swan events
📡 Satellite Direct Feed: Bypass terrestrial bottlenecks with LEO satellite clusters
The Silent Revolution
Last month, three Alltick-powered systems achieved the impossible:
A crypto bot front-ran Elon’s tweet storm by analyzing Starlink latency fluctuations
A London hedge fund predicted a metals squeeze by tracking Shanghai warehouse RFID signals
An AI trader passed the Turing Test by negotiating OTC derivatives via synthetic voice interface
72-Hour Quantum Leap Offer
Deploy Alltick before midnight UTC and unlock:
🔥 Dark Fiber Priority Lane (50% faster than standard feeds)
💡 Neural Compiler (Auto-convert strategies between Python/Rust/HDL)
🔐 Black Box Vault (Military-grade encrypted data bunker)
Warning: May cause side effects including disgust toward legacy APIs, uncontrollable urge to optimize everything, and permanent loss of "downtime"概念.
Alltick doesn’t predict the future—we deliver it 42 microseconds early.(Data streams may contain traces of singularity. Not suitable for analog traders.)

2 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
Open Platform For Enterprise AI Avatar Chatbot Creation

How may an AI avatar chatbot be created using the Open Platform For Enterprise AI framework?
I. Flow Diagram
The graph displays the application’s overall flow. The Open Platform For Enterprise AI GenAIExamples repository’s “Avatar Chatbot” serves as the code sample. The “AvatarChatbot” megaservice, the application’s central component, is highlighted in the flowchart diagram. Four distinct microservices Automatic Speech Recognition (ASR), Large Language Model (LLM), Text-to-Speech (TTS), and Animation are coordinated by the megaservice and linked into a Directed Acyclic Graph (DAG).
Every microservice manages a specific avatar chatbot function. For instance:
Software for voice recognition that translates spoken words into text is called Automatic Speech Recognition (ASR).
By comprehending the user’s query, the Large Language Model (LLM) analyzes the transcribed text from ASR and produces the relevant text response.
The text response produced by the LLM is converted into audible speech by a text-to-speech (TTS) service.
The animation service makes sure that the lip movements of the avatar figure correspond with the synchronized speech by combining the audio response from TTS with the user-defined AI avatar picture or video. After then, a video of the avatar conversing with the user is produced.
An audio question and a visual input of an image or video are among the user inputs. A face-animated avatar video is the result. By hearing the audible response and observing the chatbot’s natural speech, users will be able to receive input from the avatar chatbot that is nearly real-time.
Create the “Animation” microservice in the GenAIComps repository
We would need to register a new microservice, such “Animation,” under comps/animation in order to add it:
Register the microservice
@register_microservice( name=”opea_service@animation”, service_type=ServiceType.ANIMATION, endpoint=”/v1/animation”, host=”0.0.0.0″, port=9066, input_datatype=Base64ByteStrDoc, output_datatype=VideoPath, ) @register_statistics(names=[“opea_service@animation”])
It specify the callback function that will be used when this microservice is run following the registration procedure. The “animate” function, which accepts a “Base64ByteStrDoc” object as input audio and creates a “VideoPath” object with the path to the generated avatar video, will be used in the “Animation” case. It send an API request to the “wav2lip” FastAPI’s endpoint from “animation.py” and retrieve the response in JSON format.
Remember to import it in comps/init.py and add the “Base64ByteStrDoc” and “VideoPath” classes in comps/cores/proto/docarray.py!
This link contains the code for the “wav2lip” server API. Incoming audio Base64Str and user-specified avatar picture or video are processed by the post function of this FastAPI, which then outputs an animated video and returns its path.
The functional block for its microservice is created with the aid of the aforementioned procedures. It must create a Dockerfile for the “wav2lip” server API and another for “Animation” to enable the user to launch the “Animation” microservice and build the required dependencies. For instance, the Dockerfile.intel_hpu begins with the PyTorch* installer Docker image for Intel Gaudi and concludes with the execution of a bash script called “entrypoint.”
Create the “AvatarChatbot” Megaservice in GenAIExamples
The megaservice class AvatarChatbotService will be defined initially in the Python file “AvatarChatbot/docker/avatarchatbot.py.” Add “asr,” “llm,” “tts,” and “animation” microservices as nodes in a Directed Acyclic Graph (DAG) using the megaservice orchestrator’s “add” function in the “add_remote_service” function. Then, use the flow_to function to join the edges.
Specify megaservice’s gateway
An interface through which users can access the Megaservice is called a gateway. The Python file GenAIComps/comps/cores/mega/gateway.py contains the definition of the AvatarChatbotGateway class. The host, port, endpoint, input and output datatypes, and megaservice orchestrator are all contained in the AvatarChatbotGateway. Additionally, it provides a handle_request function that plans to send the first microservice the initial input together with parameters and gathers the response from the last microservice.
In order for users to quickly build the AvatarChatbot backend Docker image and launch the “AvatarChatbot” examples, we must lastly create a Dockerfile. Scripts to install required GenAI dependencies and components are included in the Dockerfile.
II. Face Animation Models and Lip Synchronization
GFPGAN + Wav2Lip
A state-of-the-art lip-synchronization method that uses deep learning to precisely match audio and video is Wav2Lip. Included in Wav2Lip are:
A skilled lip-sync discriminator that has been trained and can accurately identify sync in actual videos
A modified LipGAN model to produce a frame-by-frame talking face video
An expert lip-sync discriminator is trained using the LRS2 dataset as part of the pretraining phase. To determine the likelihood that the input video-audio pair is in sync, the lip-sync expert is pre-trained.
A LipGAN-like architecture is employed during Wav2Lip training. A face decoder, a visual encoder, and a speech encoder are all included in the generator. Convolutional layer stacks make up all three. Convolutional blocks also serve as the discriminator. The modified LipGAN is taught similarly to previous GANs: the discriminator is trained to discriminate between frames produced by the generator and the ground-truth frames, and the generator is trained to minimize the adversarial loss depending on the discriminator’s score. In total, a weighted sum of the following loss components is minimized in order to train the generator:
A loss of L1 reconstruction between the ground-truth and produced frames
A breach of synchronization between the lip-sync expert’s input audio and the output video frames
Depending on the discriminator score, an adversarial loss between the generated and ground-truth frames
After inference, it provide the audio speech from the previous TTS block and the video frames with the avatar figure to the Wav2Lip model. The avatar speaks the speech in a lip-synced video that is produced by the trained Wav2Lip model.
Lip synchronization is present in the Wav2Lip-generated movie, although the resolution around the mouth region is reduced. To enhance the face quality in the produced video frames, it might optionally add a GFPGAN model after Wav2Lip. The GFPGAN model uses face restoration to predict a high-quality image from an input facial image that has unknown deterioration. A pretrained face GAN (like Style-GAN2) is used as a prior in this U-Net degradation removal module. A more vibrant and lifelike avatar representation results from prettraining the GFPGAN model to recover high-quality facial information in its output frames.
SadTalker
It provides another cutting-edge model option for facial animation in addition to Wav2Lip. The 3D motion coefficients (head, stance, and expression) of a 3D Morphable Model (3DMM) are produced from audio by SadTalker, a stylized audio-driven talking-head video creation tool. The input image is then sent through a 3D-aware face renderer using these coefficients, which are mapped to 3D key points. A lifelike talking head video is the result.
Intel made it possible to use the Wav2Lip model on Intel Gaudi Al accelerators and the SadTalker and Wav2Lip models on Intel Xeon Scalable processors.
Read more on Govindhtech.com
#AIavatar#OPE#Chatbot#microservice#LLM#GenAI#API#News#Technews#Technology#TechnologyNews#Technologytrends#govindhtech
3 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Navigating the Cloud Landscape: Unleashing Amazon Web Services (AWS) Potential
In the ever-evolving tech landscape, businesses are in a constant quest for innovation, scalability, and operational optimization. Enter Amazon Web Services (AWS), a robust cloud computing juggernaut offering a versatile suite of services tailored to diverse business requirements. This blog explores the myriad applications of AWS across various sectors, providing a transformative journey through the cloud.

Harnessing Computational Agility with Amazon EC2
Central to the AWS ecosystem is Amazon EC2 (Elastic Compute Cloud), a pivotal player reshaping the cloud computing paradigm. Offering scalable virtual servers, EC2 empowers users to seamlessly run applications and manage computing resources. This adaptability enables businesses to dynamically adjust computational capacity, ensuring optimal performance and cost-effectiveness.
Redefining Storage Solutions
AWS addresses the critical need for scalable and secure storage through services such as Amazon S3 (Simple Storage Service) and Amazon EBS (Elastic Block Store). S3 acts as a dependable object storage solution for data backup, archiving, and content distribution. Meanwhile, EBS provides persistent block-level storage designed for EC2 instances, guaranteeing data integrity and accessibility.
Streamlined Database Management: Amazon RDS and DynamoDB
Database management undergoes a transformation with Amazon RDS, simplifying the setup, operation, and scaling of relational databases. Be it MySQL, PostgreSQL, or SQL Server, RDS provides a frictionless environment for managing diverse database workloads. For enthusiasts of NoSQL, Amazon DynamoDB steps in as a swift and flexible solution for document and key-value data storage.
Networking Mastery: Amazon VPC and Route 53
AWS empowers users to construct a virtual sanctuary for their resources through Amazon VPC (Virtual Private Cloud). This virtual network facilitates the launch of AWS resources within a user-defined space, enhancing security and control. Simultaneously, Amazon Route 53, a scalable DNS web service, ensures seamless routing of end-user requests to globally distributed endpoints.
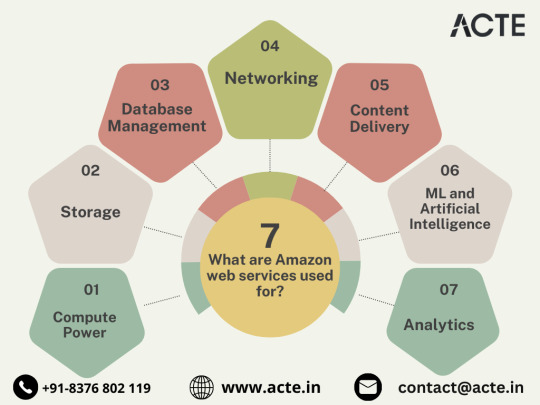
Global Content Delivery Excellence with Amazon CloudFront
Amazon CloudFront emerges as a dynamic content delivery network (CDN) service, securely delivering data, videos, applications, and APIs on a global scale. This ensures low latency and high transfer speeds, elevating user experiences across diverse geographical locations.
AI and ML Prowess Unleashed
AWS propels businesses into the future with advanced machine learning and artificial intelligence services. Amazon SageMaker, a fully managed service, enables developers to rapidly build, train, and deploy machine learning models. Additionally, Amazon Rekognition provides sophisticated image and video analysis, supporting applications in facial recognition, object detection, and content moderation.
Big Data Mastery: Amazon Redshift and Athena
For organizations grappling with massive datasets, AWS offers Amazon Redshift, a fully managed data warehouse service. It facilitates the execution of complex queries on large datasets, empowering informed decision-making. Simultaneously, Amazon Athena allows users to analyze data in Amazon S3 using standard SQL queries, unlocking invaluable insights.
In conclusion, Amazon Web Services (AWS) stands as an all-encompassing cloud computing platform, empowering businesses to innovate, scale, and optimize operations. From adaptable compute power and secure storage solutions to cutting-edge AI and ML capabilities, AWS serves as a robust foundation for organizations navigating the digital frontier. Embrace the limitless potential of cloud computing with AWS – where innovation knows no bounds.
3 notes
·
View notes
Text
Chapter Five (Tyrri), pt. 1:
Happy fun times are over. This boat ride is so incredibly unlike the last.
Tyrri still stands at the edge of the bow, looking at the horizon as the Farlands come into view.
Hers is not a gaze filled with hope this time.
Arriving in Seekersgate, Sebastian, Lia, and Elias, all welcome her happily
It really has been a while, maybe they should catch up a little, did my research into the crystals help and HOLD IT!
Hi guys, it’s lovely to see you, your research was tantamount to my success, now where the hell is Cat I would like to speak to her
Oh she hasn’t been seen in months? I have great news I know where she is.
Seb, are you up for another trip into the wellspring? I sure hope you are because we’re gonna raise a little hell.
Lia, Elias, feel free to come with if you want. I’m happy to get all the support I can get
The four easily blast through the first section of the dungeon to the point where it’s just cutscened away. You go into the entrance to the Wellspring and arrive at the endpoint after a fade to black
What’s at that endpoint, you might ask?
Well, do you remember the snake that guarded the wellspring? How I mentioned that it was easily long enough to reach to the outside of the cave
Well, something managed to outrun it. Someone, specifically
Extending into the furthest recesses of the cave is the Guardian of the Wellspring. It appears to be unconscious
Sebastian, Lia, and Elias all get to work getting them sorted out and conscious again, urging Tyrri to go onward into
The Final Dungeon: The Heart of Wild Magic
Rather than my typical fare of making dungeons into impassable mazes, the Heart is actually rather straightforward
A massive cavern that spirals downward into a single centrepoint, studded with the same magenta crystals as the Wellspring that glow with greater and greater intensity as you go further down
Cat’s sprite is actually visible and rendered in from the furthest up point, but it isn’t clear what she’s doing
The strongest elementals in the game reside here, the Elder series elementals (Elder Tempest, Elder Frost, Elder Abyss, etc.)
Every now and again there are streams of water that pour into the cavern, interacting with them restores some SP to the entire party
Also present in here is one of the strongest staffs in the game, though I have not decided what it does
I have decided, however, that it does not exist in a conventional chest; rather, it is made entirely of crystal and is lodged into a wall in an offshoot cave
Reaching the bottom of the cave triggers the last cutscene
Catena is desperately chipping away at a cave wall with a small dagger, occasionally looking over at Tyrri’s notes
She’s muttering stuff like “please work” and “what does it mean” to herself; she clearly hasn’t had the time to comprehensively look over the notes and understand what they mean
Tyrri approaches her and tries to talk her out of whatever she’s doing
Catena shakily gets up, steadying herself against the wall, before screaming “YOU DON’T UNDERSTAND! YOU NEVER COULD!” and slashing Tyrri across the cheek with the dagger
Tyrri quickly blasts it out of her hand, but the damage has been done
The two steady themselves and enter into…
The Final Boss: Catena Novi
This is the Osvald-style battle where it’s fundamentally against another scholar
No tricks, no gimmicks (lying), just a good old fashioned mage’s duel
Catena is very good at buffing herself; in addition to the usual Elemental Attack/Defence buffs, she has stuff to give her spells added effects (like Crystalline Magic), reflection and absorption skills, access to stuff like Advanced Magic and focused spells, the like
Her AI will very specifically target Tyrri with debuffs but not with single-target spells, the only damage she needs to worry about is from AoE attacks
Her boost mode will summon Elder elementals and keep them around; none of that Harvey/Tormented Blaze/Dark Entity shit of sacrificing them for more powerful attacks
If I knew how to code I’d give her the most intelligent AI of the entire rogues gallery. This is the Pokemon Champion Cynthia of Project OCtopath
Her spells might change slightly depending on which elementals are out (ie: ice spells when Elder Frost are on the field)
Design-wise she actually looks rather plain
Her clothes look a little torn and her hands a covered in scratches
She is, notably, completely slumped over for the entire fight; her face is completely shrouded in shadow save for her mouth, which is set in a hard line that’s difficult to draw emotion from
Boost mode has her raise her head up, but a veil of hair still covers her face
Hitting half health triggers a cutscene rather than staying on the battle screen
“Let me… let me HAVE this, Tyrri! Please! You don’t – you CAN’T understand what this means! I can’t fail so far in!”
“Cat, I’m sorry. I really am. But this is too far – you’re destroying this cave, this magic. Do you have any idea what the consequences of your actions could be?”
“Shut UP! I WILL NOT FAIL HERE!”
Tyrri thinks to herself “No time like the present to test out that theory” and grabs one of the fallen crystals
Mistake. That was a mistake. Catena Novi is no fool, and is very quickly able to pick up on what that means
“Fascinating.” She magically pulls three crystals towards them and lets them hover around her head
“So that’s what your research meant. Father will be pleased.”
“Father?”
With that little tidbit of knowledge, the battle transitions into…
3 notes
·
View notes
Text
Anton R Gordon’s Blueprint for Real-Time Streaming AI: Kinesis, Flink, and On-Device Deployment at Scale
In the era of intelligent automation, real-time AI is no longer a luxury—it’s a necessity. From fraud detection to supply chain optimization, organizations rely on high-throughput, low-latency systems to power decisions as data arrives. Anton R Gordon, an expert in scalable AI infrastructure and streaming architecture, has pioneered a blueprint that fuses Amazon Kinesis, Apache Flink, and on-device machine learning to deliver real-time AI performance with reliability, scalability, and security.
This article explores Gordon’s technical strategy for enabling AI-powered event processing pipelines in production, drawing on cloud-native technologies and edge deployments to meet enterprise-grade demands.
The Case for Streaming AI at Scale
Traditional batch data pipelines can’t support dynamic workloads such as fraud detection, anomaly monitoring, or recommendation engines in real-time. Anton R Gordon's architecture addresses this gap by combining:
Kinesis Data Streams for scalable, durable ingestion.
Apache Flink for complex event processing (CEP) and model inference.
Edge inference runtimes for latency-sensitive deployments (e.g., manufacturing or retail IoT).
This trio enables businesses to execute real-time AI pipelines that ingest, process, and act on data instantly, even in disconnected or bandwidth-constrained environments.
Real-Time Data Ingestion with Amazon Kinesis
At the ingestion layer, Gordon uses Amazon Kinesis Data Streams to collect data from sensors, applications, and APIs. Kinesis is chosen for:
High availability across multiple AZs.
Native integration with AWS Lambda, Firehose, and Flink.
Support for shard-based scaling—enabling millions of records per second.
Kinesis is responsible for normalizing raw data and buffering it for downstream consumption. Anton emphasizes the use of data partitioning and sequencing strategies to ensure downstream applications maintain order and performance.
Complex Stream Processing with Apache Flink
Apache Flink is the workhorse of Gordon’s streaming stack. Deployed via Amazon Kinesis Data Analytics (KDA) or self-managed ECS/EKS clusters, Flink allows for:
Stateful stream processing using keyed aggregations.
Windowed analytics (sliding, tumbling, session windows).
ML model inference embedded in UDFs or side-output streams.
Anton R Gordon’s implementation involves deploying TensorFlow Lite or ONNX models within Flink jobs or calling SageMaker endpoints for real-time predictions. He also uses savepoints and checkpoints for fault tolerance and performance tuning.
On-Device Deployment for Edge AI
Not all use cases can wait for roundtrips to the cloud. For industrial automation, retail, and automotive, Gordon extends the pipeline with on-device inference using NVIDIA Jetson, AWS IoT Greengrass, or Coral TPU. These edge devices:
Consume model updates via MQTT or AWS IoT.
Perform low-latency inference directly on sensor input.
Reconnect to central pipelines for data aggregation and model retraining.
Anton stresses the importance of model quantization, pruning, and conversion (e.g., TFLite or TensorRT) to deploy compact, power-efficient models on constrained devices.
Monitoring, Security & Scalability
To manage the entire lifecycle, Gordon integrates:
AWS CloudWatch and Prometheus/Grafana for observability.
IAM and KMS for secure role-based access and encryption.
Flink Autoscaling and Kinesis shard expansion to handle traffic surges.
Conclusion
Anton R Gordon’s real-time streaming AI architecture is a production-ready, scalable framework for ingesting, analyzing, and acting on data in milliseconds. By combining Kinesis, Flink, and edge deployments, he enables AI applications that are not only fast—but smart, secure, and cost-efficient. This blueprint is ideal for businesses looking to modernize their data workflows and unlock the true potential of real-time intelligence.
0 notes
Text
Best API of Horse Racing for Betting Platforms: Live Odds, Data Feeds & Profits Unlocked

Discover the most accurate and profitable API of horse racing with live odds, betting data feeds, and fast integration. Ideal for UK/USA markets and fantasy apps.
Introduction: Why Accurate Horse Racing APIs Matter in 2025
In the competitive world of sports betting and fantasy gaming, milliseconds and margins matter. When it comes to horse racing, success hinges on real-time, trustworthy data and sharp odds. Whether you run a betting exchange, fantasy app, or affiliate site, using the right horse racing API can mean the difference between profit and failure.
The API of horse racing offered by fantasygameprovider.com is engineered to meet this demand—providing live horse racing odds, race entries, results, and predictive analytics that align perfectly with the betting industry’s needs.
What Is a Horse Racing API?
A horse racing API is a service that delivers structured, real-time horse racing data to apps, websites, and betting platforms. This includes:
Live race updates
Racecard entries & scratchings
Odds feed (fixed & fluctuating)
Final results with payout info
Jockey, trainer, and form data
These are typically delivered in JSON or XML formats, allowing seamless integration with sportsbooks, exchanges, or fantasy game engines.
📊 Who Needs Horse Racing APIs?
Audience
Use Case
Betting Sites
Deliver live odds, matchups, and payouts.
Fantasy Sports Platforms
Use live feeds to auto-update scores & leaderboards.
Betting Tipsters/Affiliates
Showcase predictive models based on fresh data.
Mobile Apps
Enable live race streaming with betting APIs.
Trading Bots
Automate wagers with low-latency horse racing data.
Why Choose FantasyGameProvider’s Horse Racing API?

Unlike basic feeds, our API is tailored for commercial use. Here's why it stands out:
Feature
FantasyGameProvider
Other APIs
Live Odds Feed
✅ Updated in <2s
⚠️ 5–15s delay
Global Racing
✅ UK, USA, AUS, HK
⚠️ Limited coverage
Data Format
✅ JSON + XML
⚠️ JSON only
Accuracy
✅ Enterprise-Grade (99.9%)
⚠️ Variable
Predictive Insights
✅ AI-Driven Models
❌ Not Included
Betting Integration
✅ Easy with Betfair, SBTech
⚠️ Manual setup required
Our horse racing odds API not only mirrors UK and USA live betting markets, but also lets you build automated bet triggers and smart notifications for sharp edge betting.
💸 How Betting Businesses Profit with Horse Racing APIs
If you're running a betting website or fantasy sports app, here's how the API of horse racing can boost your ROI:
Real-time updates = More active users
Faster odds delivery = Better arbitrage potential
Accurate results = Fewer payout disputes
Live data = Higher session times (ideal for monetizing with ads)
Custom alerts = VIP features for paid subscribers
Fantasygameprovider.com also allows white-label API integration to match your brand.
How to Choose the Right Horse Racing API – Checklist ✅
Make sure your API includes the following:
✅ Live odds feed with fast refresh rate (sub-2 seconds ideal)
✅ Coverage of all major race tracks (UK, USA, AUS)
✅ Reliable JSON & XML format
✅ Built-in historical data & form guide
✅ Scalable architecture for high traffic
✅ Supports Betfair, Oddschecker, and other exchanges
✅ Licensed data provider
Our API meets all these criteria and goes further by offering automated betting signals and predictive race modeling—key for next-gen apps.
Betfair API vs FantasyGameProvider: Which Is Better?
Feature
Betfair API
FantasyGameProvider
Odds Feed
Excellent (exchange-based)
Excellent (market + exchange)
Historical Data
Partial
Full form + performance stats
Developer Simplicity
Moderate
Plug-and-play REST endpoints
Support
Community-based
24/7 Support
Customization
Limited
High (webhooks, triggers, filters)
Pricing
Tiered
Affordable & negotiable plans
Conclusion: If you want full access to live odds, race data, and fast integration without the steep learning curve, fantasygameprovider.com offers better developer flexibility and betting UX.
Data Feeds You Get with Our Horse Racing API

Racecards & scratchings feed
Real-time results feed
Odds feed (fixed, fluctuating, exchange-compatible)
Form & stats feed
Track conditions feed
Horse/jockey/trainer history feed
Automated alerts for betting patterns
Formats available: JSON horse racing data & horse racing XML feed.
FAQs: Betting-Focused Horse Racing API Questions
Q1. Which is the most accurate horse racing API in 2025?
FantasyGameProvider offers 99.9% accuracy with sub-2-second update latency, ideal for professional and retail bettors alike.
Q2. Can I use this API for UK and USA horse racing?
Yes, our UK racing odds data and USA racing API are both available with full schedule and live result support.
Q3. Is your horse racing API suitable for Betfair automation?
Absolutely. Many of our clients use it to build Betfair trading bots using our odds feed and predictive race data.
Q4. Do you offer free trials or sandbox testing?
Yes. Developers can access a sandbox environment to test endpoints before committing.
Q5. What’s the difference between JSON and XML feeds?
JSON is faster and easier to integrate, while XML is preferred for legacy systems. We offer both to suit all tech stacks.
🚀 Start Winning with the Best API of Horse Racing
If you’re serious about building a winning betting platform, profitable tipster site, or a fantasy sports engine, you need the most accurate and commercial-ready API in the industry.
At fantasygameprovider.com, we give you everything:
✅ Live odds ✅ Fast results ✅ Race cards ✅ Predictive models ✅ Betfair compatibility ✅ Global reach (UK, USA, AUS, more)
👉 Ready to dominate the betting space with live horse racing data? Visit fantasygameprovider.com and request your API demo today.
#live cricket odds api#sports betting#betting#bettingapi#fantasygameprovider#Live odds#API of Horse Racing#UK racing odds data#Betfair#Real-time results feed#Betfair API
0 notes
Text
The Future of Crypto APIs: Why Token Metrics Leads the Pack
In this article, we’ll explore why Token Metrics is the future of crypto APIs, and how it delivers unmatched value for developers, traders, and product teams.
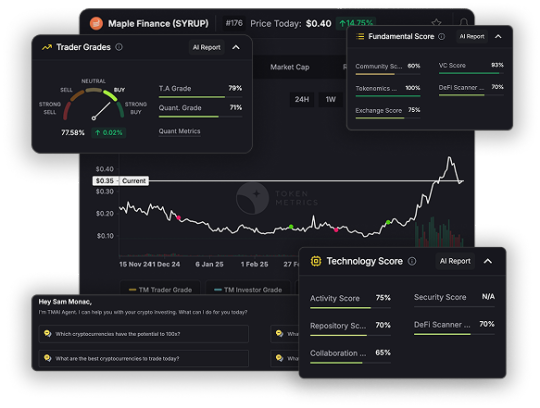
More Than Just Market Data
Most crypto APIs—like CoinGecko, CoinMarketCap, or even exchange-native endpoints—only give you surface-level data: prices, volume, market cap, maybe order book depth crypto trading. That’s helpful… but not enough.
Token Metrics goes deeper:
Trader and Investor Grades (0–100)
Bullish/Bearish market signals
Support/Resistance levels
Real-time sentiment scoring
Sector-based token classification (AI, RWA, Memes, DeFi)
Instead of providing data you have to interpret, it gives you decisions you can act on.
⚡ Instant Intelligence, No Quant Team Required
For most platforms, building actionable insights on top of raw market data requires:
A team of data scientists
Complex modeling infrastructure
Weeks (if not months) of development
With Token Metrics, you skip all of that. You get:
Pre-computed scores and signals
Optimized endpoints for bots, dashboards, and apps
AI-generated insights as JSON responses
Even a solo developer can build powerful trading systems without ever writing a prediction model.
🔄 Real-Time Signals That Evolve With the Market
Crypto moves fast. One minute a token is mooning, the next it’s bleeding.
Token Metrics API offers:
Daily recalculated grades
Real-time trend flips (bullish ↔ bearish)
Sentiment shifts based on news, social, and on-chain data
You’re never working with stale data or lagging indicators.
🧩 Built for Integration, Built for Speed
Unlike many APIs that are bloated or poorly documented, Token Metrics is built for builders.
Highlights:
Simple REST architecture (GET endpoints, API key auth)
Works with Python, JavaScript, Go, etc.
Fast JSON responses for live dashboards
5,000-call free tier to start building instantly
Enterprise scale for large data needs
Whether you're creating a Telegram bot, a DeFi research terminal, or an internal quant dashboard, TM API fits right in.
🎯 Use Cases That Actually Matter
Token Metrics API powers:
Signal-based alert systems
Narrative-tracking dashboards
Token portfolio health scanners
Sector rotation tools
On-chain wallets with smart overlays
Crypto AI assistants (RAG, GPT, LangChain agents)
It’s not just a backend feed. It’s the core logic engine for intelligent crypto products.
📈 Proven Performance
Top funds, trading bots, and research apps already rely on Token Metrics API. The AI grades are backtested, the signals are verified, and the ecosystem is growing.
“We plugged TM’s grades into our entry logic and saw a 25% improvement in win rates.” — Quant Bot Developer
“It’s like plugging ChatGPT into our portfolio tools—suddenly it makes decisions.” — Web3 Product Manager
🔐 Secure, Stable, and Scalable
Uptime and reliability matter. Token Metrics delivers:
99.9% uptime
Low-latency endpoints
Strict rate limiting for abuse prevention
Scalable plans with premium SLAs
No surprises. Just clean, trusted data every time you call.
💬 Final Thoughts
Token Metrics isn’t just the best crypto API because it has more data. It’s the best because it delivers intelligence. It replaces complexity with clarity, raw numbers with real signals, and guesswork with action.In an industry that punishes delay and indecision, Token Metrics gives builders and traders the edge they need—faster, smarter, and more efficiently than any other API in crypto.
0 notes
Text
Cyber Security Companies in India: Safeguarding the Nation’s Digital Future
With India rapidly transitioning into a digitally-driven economy, the need for robust cybersecurity solutions has never been more urgent. From government databases and financial institutions to startups and e-commerce platforms, cyber threats loom large over every sector. Fortunately, a strong network of cyber security companies in India is working tirelessly to fortify digital assets, protect sensitive information, and keep cybercriminals at bay.

This article explores the landscape of cybersecurity in India, highlights the key players, and explains why businesses—big or small—must take proactive steps to protect their digital presence.
The Cybersecurity Landscape in India
India ranks among the top countries with the highest number of internet users, and with that comes an increased vulnerability to cyber threats. According to multiple industry reports, India faces millions of cyberattacks each day, ranging from phishing and ransomware to advanced persistent threats (APT) and data breaches.
The government’s push toward a "Digital India" has accelerated cloud adoption, mobile payments, and online services, but has also opened new avenues for cybercriminals. In this context, cyber security companies in India play a critical role in offering solutions that range from network protection and cloud security to penetration testing and compliance management.
Why Cybersecurity Matters More Than Ever
Here are just a few reasons why investing in cybersecurity has become a top priority:
Rising Threat Levels: With evolving cyber threats, businesses can no longer rely on basic firewalls and antivirus solutions.
Data Privacy Laws: As India moves toward stronger data protection laws (similar to GDPR), companies are required to secure user data to avoid hefty penalties.
Business Continuity: Cyberattacks can lead to operational disruption, financial losses, and irreversible brand damage.
Remote Work Culture: With more employees working from home, endpoints are now more exposed than ever before.
This demand has given rise to several innovative and impactful cyber security companies across the country.
What Makes Indian Cybersecurity Firms Stand Out?
Cyber security companies in India are not just keeping pace with global trends—they are innovating and exporting their solutions worldwide. Here’s what gives them an edge:
Cost-Effective Services: Indian firms offer world-class security at competitive pricing, making them attractive for global SMEs.
Skilled Talent Pool: With a strong base of cybersecurity professionals, India ranks high in availability of tech expertise.
Regulatory Understanding: Indian firms are well-versed in global compliance standards like ISO 27001, GDPR, PCI DSS, and are increasingly playing a role in shaping Indian cybersecurity laws.
AI & Machine Learning: Many companies are integrating AI into their platforms to provide real-time detection and automated threat response.
Key Services Offered by Cyber Security Companies in India
Businesses in India and globally rely on cybersecurity firms for a range of services, including:
Penetration Testing & Vulnerability Assessment (VAPT)
Network Security & Firewall Management
Cloud Security & Data Encryption
Endpoint Security
Security Operations Center (SOC)
Digital Forensics & Incident Response
Regulatory Compliance & Audit Services
Security Awareness & Employee Training
Choosing the Right Cybersecurity Partner
Selecting the right cybersecurity company depends on the unique needs and scale of your organization. Here are a few things to consider before making a decision:
Experience in Your Industry: Cybersecurity needs differ between finance, healthcare, retail, and government sectors.
Customized Solutions: Look for firms that offer tailored strategies rather than one-size-fits-all models.
Certifications & Compliance: Ensure the firm follows industry best practices and standards.
24/7 Support & Monitoring: Cyber threats don’t work 9-to-5. Your provider shouldn’t either.
The Road Ahead for Cybersecurity in India
As digital adoption continues to surge, the role of cybersecurity firms will become increasingly mission-critical. The emergence of technologies like 5G, IoT, and blockchain will add more complexity to the security landscape, requiring constant innovation and collaboration between the public and private sectors.
With government initiatives like CERT-In, the National Cyber Security Policy, and frameworks under MeitY, India is building a solid foundation for a secure digital economy. But the real impact will come from how businesses choose to engage with the right cyber security companies in India to proactively protect their assets.
Final Thoughts
Cybersecurity is no longer optional—it’s a business imperative. Whether you're a startup, SME, or large enterprise, partnering with a trusted cyber security company in India ensures you're not just protected, but future-ready.
Looking to Secure Your Business?
Join hands with an experienced cybersecurity partner in India and shield your digital presence against emerging threats. Take the first step—consult with a certified cybersecurity expert today.
0 notes
Text
CPE Chip Market Analysis: CAGR of 12.1% Predicted Between 2025–2032

MARKET INSIGHTS
The global CPE Chip Market size was valued at US$ 1.58 billion in 2024 and is projected to reach US$ 3.47 billion by 2032, at a CAGR of 12.1% during the forecast period 2025-2032. This growth trajectory aligns with the broader semiconductor industry expansion, which was valued at USD 579 billion in 2022 and is expected to reach USD 790 billion by 2029 at a 6% CAGR.
CPE (Customer Premises Equipment) chips are specialized semiconductor components that enable network connectivity in devices such as routers, modems, and gateways. These chips power critical functions including signal processing, data transmission, and protocol conversion for both 4G and 5G networks. The market comprises two primary segments – 4G chips maintaining legacy infrastructure support and 5G chips driving next-generation connectivity with higher bandwidth and lower latency.
Market expansion is being propelled by three key factors: the global rollout of 5G infrastructure, increasing demand for high-speed broadband solutions, and the proliferation of IoT devices requiring robust connectivity. However, supply chain constraints in the semiconductor industry and geopolitical factors affecting chip production present ongoing challenges. Major players like Qualcomm and MediaTek are investing heavily in R&D to develop advanced CPE chipsets, while emerging players such as UNISOC and ASR are gaining traction in cost-sensitive markets. The Asia-Pacific region dominates production and consumption, accounting for over 45% of global CPE chip demand in 2024.
MARKET DYNAMICS
MARKET DRIVERS
5G Network Expansion Accelerates Demand for Advanced CPE Chips
The global transition to 5G networks continues to drive exponential growth in the CPE chip market. As telecom operators roll out next-generation infrastructure, the demand for high-performance customer premise equipment has surged by over 40% in the past two years. Modern 5G CPE devices require specialized chipsets capable of supporting multi-gigabit speeds, ultra-low latency, and massive device connectivity. Leading chip manufacturers are responding with integrated solutions that combine baseband processing, RF front-end modules, and AI acceleration. For instance, Qualcomm’s latest 5G CPE platforms deliver 10Gbps throughput while reducing power consumption by 30% compared to previous generations.
IoT Adoption Creates New Growth Avenues for CPE Chip Vendors
The proliferation of Internet of Things (IoT) applications across smart cities, industrial automation, and connected homes is generating significant opportunities for CPE chip manufacturers. With over 15 billion IoT devices projected to connect to networks by 2025, telecom operators require CPE solutions that can efficiently manage diverse traffic patterns and quality-of-service requirements. This has led to the development of specialized chipsets featuring advanced traffic management, edge computing capabilities, and enhanced security protocols. Recent product launches demonstrate this trend, with companies like MediaTek introducing chips optimized for IoT gateways that support simultaneous connections to hundreds of endpoints while maintaining reliable performance.
Remote Work Infrastructure Investments Fuel Market Expansion
The permanent shift toward hybrid work models continues to stimulate demand for enterprise-grade CPE solutions. Businesses worldwide are upgrading their network infrastructure to support distributed workforces, driving a 25% year-over-year increase in CPE deployments. This trend has particularly benefited manufacturers of chips designed for business routers and SD-WAN appliances, which require robust performance for VPNs, unified communications, and cloud applications. Leading semiconductor firms have responded with system-on-chip solutions integrating Wi-Fi 6/6E, multi-core processors, and hardware-accelerated encryption to meet these evolving requirements.
MARKET RESTRAINTS
Supply Chain Disruptions Continue to Challenge Production Stability
Despite strong demand, the CPE chip market faces persistent supply chain constraints that limit growth potential. The semiconductor industry’s reliance on advanced fabrication nodes has created bottlenecks, with lead times for certain components extending beyond 12 months. These challenges are compounded by geopolitical tensions affecting rare earth material supplies and export controls on specialized manufacturing equipment. While the situation has improved from pandemic-era shortages, inventory levels remain below historical averages, forcing many CPE manufacturers to implement allocation strategies and redesign products with available components.
Rising Component Costs Squeeze Profit Margins
Escalating production expenses present another significant restraint for CPE chip suppliers. The transition to more advanced process nodes has increased wafer costs by approximately 20-30% across the industry. Additionally, testing and packaging expenses have risen due to higher energy prices and labor costs. These factors have compressed gross margins, particularly for mid-range CPE chips where pricing pressure is most intense. Manufacturers are responding by optimizing chip architectures, consolidating IP blocks, and investing in yield improvement initiatives, but these measures require significant R&D expenditures that may take years to yield returns.
Regulatory Complexity Slows Time-to-Market
The CPE chip industry faces growing regulatory scrutiny that delays product launches and increases compliance costs. New spectrum regulations, cybersecurity requirements, and equipment certification processes have extended development cycles by 3-6 months on average. In particular, the automotive and industrial sectors now demand comprehensive safety certifications that require extensive testing and documentation. These regulatory hurdles disproportionately affect smaller chip vendors who lack dedicated compliance teams, potentially limiting innovation and competition in certain market segments.
MARKET CHALLENGES
Technology Complexity Increases Design and Validation Costs
Modern CPE chips incorporate increasingly sophisticated architectures that pose significant engineering challenges. Designs now routinely integrate multiple processor cores, AI accelerators, and specialized radio interfaces, requiring advanced simulation tools and verification methodologies. The associated R&D costs have grown exponentially, with some 5G chip development projects now exceeding $100 million in budget. This creates a high barrier to entry for potential competitors and forces established players to carefully prioritize their product roadmaps. Furthermore, the complexity makes post-silicon validation more difficult, potentially leading to costly respins if critical issues emerge late in the development cycle.
Talent Shortage Constrains Innovation Capacity
The semiconductor industry’s rapid expansion has created intense competition for skilled engineers, particularly in critical areas like RF design, digital signal processing, and physical implementation. CPE chip manufacturers report vacancy rates exceeding 30% for certain technical positions, with hiring cycles stretching to 9-12 months for specialized roles. This talent crunch limits companies’ ability to execute aggressive product roadmaps and forces difficult tradeoffs between projects. While firms are investing in training programs and academic partnerships, the pipeline for experienced chip designers remains insufficient to meet current demand.
Standardization Gaps Create Integration Headaches
The evolving nature of 5G and edge computing technologies has led to fragmented standards across different markets and regions. CPE chip vendors must support multiple protocol variants, frequency bands, and security frameworks, complicating both hardware and software development. This fragmentation increases testing overhead and makes it difficult to achieve economies of scale across product lines. While industry groups continue working toward greater harmonization, interim solutions often require additional engineering resources to implement customized features for specific customers or geographies.
CPE CHIP MARKET TRENDS
5G Network Expansion Accelerates Demand for Advanced CPE Chips
The rapid global deployment of 5G networks is significantly driving the CPE (Customer Premises Equipment) chip market, with the segment projected to grow at over 30% CAGR through 2032. Telecom operators worldwide invested nearly $280 billion in 5G infrastructure in 2023 alone, creating substantial demand for compatible CPE devices. Chip manufacturers are responding with innovative solutions featuring multi-band support and improved power efficiency, with next-generation modem-RF combos now achieving throughputs exceeding 7Gbps. While 4G CPE chips still dominate current installations, representing about 65% of 2024 shipments, 5G solutions are rapidly gaining share due to superior performance in high-density urban environments.
Other Trends
Smart Home Integration
The proliferation of IoT devices in residential settings, expected to reach 29 billion connected units globally by 2027, is creating new requirements for CPE chips that can handle simultaneous broadband and IoT traffic management. Modern gateway solutions now incorporate AI-powered traffic prioritization and mesh networking capabilities to maintain quality of service across dozens of connected devices. Semiconductor vendors have responded with system-on-chip (SoC) designs integrating Wi-Fi 6/6E, Bluetooth, and Zigbee radios alongside traditional cellular modems. North America leads this adoption curve, with over 75% of new home internet subscriptions in 2023 opting for smart gateway solutions compared to just 32% in 2020.
Edge Computing and Network Virtualization Impact Chip Designs
Emerging virtualization technologies are reshaping CPE architectures, creating demand for chips with enhanced processing capabilities beyond traditional modem functions. Virtual CPE (vCPE) solutions now account for 18% of business installations, requiring chipsets that can efficiently run containerized network functions (CNFs) while maintaining low power envelopes. The enterprise segment has proven particularly receptive, with large-scale adoption in multi-tenant office buildings and smart city applications. Meanwhile, silicon designed for edge computing applications is increasingly incorporating hardware acceleration blocks for AI inference, allowing real-time processing of video analytics and other bandwidth-intensive applications at the network periphery. This evolution has prompted traditional chip vendors to expand their portfolios through strategic acquisitions in the FPGA and specialty processor spaces.
COMPETITIVE LANDSCAPE
Key Industry Players
Innovation and Partnerships Fuel Growth in the CPE Chip Market
The global CPE (Customer Premises Equipment) chip market remains highly competitive, characterized by technological innovation and aggressive expansion strategies. Qualcomm dominates the market with its extensive portfolio of 4G and 5G chipsets, capturing approximately 35% revenue share in 2024. The company’s leadership stems from its strong foothold in North America and strategic partnerships with telecom operators.
MediaTek and Intel follow closely, collectively accounting for 28% market share, owing to their cost-effective solutions for emerging markets and industrial applications. These players continue investing heavily in R&D, particularly for energy-efficient 5G chips catering to IoT deployments and smart city infrastructure.
Chinese manufacturers like Hisilicon and UNISOC are rapidly gaining traction through government-supported initiatives and localized supply chains. Their aggressive pricing strategies and custom solutions for Asian markets have enabled 18% year-over-year growth in 2024, challenging established western players.
Meanwhile, specialized firms such as Eigencomm and Sequans are carving niche positions through innovative chip architectures optimized for low-power wide-area networks (LPWAN) and private 5G deployments. Their collaborations with network equipment providers have become crucial differentiators in this evolving landscape.
List of Key CPE Chip Manufacturers Profiled
Qualcomm Technologies, Inc. (U.S.)
UNISOC (Shanghai) Technologies Co., Ltd. (China)
ASR Microelectronics Co., Ltd. (China)
HiSilicon (Huawei Technologies Co., Ltd.) (China)
XINYI Semiconductor (China)
MediaTek Inc. (Taiwan)
Intel Corporation (U.S.)
Eigencomm (China)
Sequans Communications S.A. (France)
Segment Analysis:
By Type
5G Chip Segment Dominates the Market Due to its High-Speed Connectivity and Low Latency
The CPE Chip market is segmented based on type into:
4G Chip
5G Chip
By Application
5G CPE Segment Leads Due to Escalated Demand for High-Performance Wireless Broadband
The market is segmented based on application into:
4G CPE
5G CPE
By End User
Telecom Operators Segment Dominates with Growing Infrastructure Investments
The market is segmented based on end user into:
Telecom Operators
Enterprises
Residential Users
Regional Analysis: CPE Chip Market
North America The mature telecommunications infrastructure and rapid 5G deployments in the U.S. and Canada are fueling demand for high-performance 5G CPE chips, particularly from vendors like Qualcomm and Intel. With major carriers investing over $275 billion in network upgrades, chip manufacturers are prioritizing low-latency, power-efficient designs. However, stringent regulatory scrutiny on semiconductor imports creates supply chain challenges. The region also leads in IoT adoption, driving demand for hybrid 4G/5G chips in smart city solutions and enterprise applications. Local chip designers benefit from strong R&D ecosystems but face growing competition from Asian suppliers.
Europe EU initiatives like the 2030 Digital Compass (targeting gigabit connectivity for all households) are accelerating CPE chip demand, though adoption varies across nations. Germany and the U.K. lead in 5G CPE deployments using chips from MediaTek and Sequans, while Eastern Europe still relies heavily on cost-effective 4G solutions. Strict data privacy laws and emphasis on open RAN architectures are reshaping chip design requirements. The region faces headwinds from component shortages but maintains steady growth through government-industry partnerships in semiconductor sovereignty programs.
Asia-Pacific Accounting for over 60% of global CPE chip consumption, the region is driven by China’s massive “5G+” infrastructure push and India’s expanding broadband networks. Local giants HiSilicon and UNISOC dominate low-to-mid range segments, while South Korean/Japanese firms focus on premium chips. Southeast Asian markets show explosive growth (20%+ CAGR) due to rural connectivity projects. However, geopolitical tensions and import restrictions create supply volatility. Price sensitivity remains high, favoring integrated 4G/5G combo chips over standalone 5G solutions in emerging economies.
South America Limited 5G spectrum availability keeps the market reliant on 4G LTE chips, though Brazil and Chile are early adopters of 5G CPEs using ASR and MediaTek solutions. Economic instability and currency fluctuations hinder large-scale infrastructure investments, causing operators to prioritize cost-effective Chinese chip suppliers. The lack of local semiconductor manufacturing creates import dependency, but recent trade agreements aim to improve component accessibility. Enterprise demand for industrial IoT routers presents niche opportunities for mid-tier chip vendors.
Middle East & Africa Gulf nations (UAE, Saudi Arabia) drive premium 5G CPE adoption through smart city projects, leveraging Qualcomm and Eigencomm chips. Sub-Saharan Africa depends on affordable 4G solutions from Chinese vendors, with mobile network operators deploying low-power chips for extended coverage. While underdeveloped fiber backhaul limits 5G potential, satellite-CPE hybrid chips are gaining traction in remote areas. Political instability in some markets disrupts supply chains, though rising digitalization funds (like Saudi’s $6.4bn ICT strategy) indicate long-term growth potential.
Report Scope
This market research report provides a comprehensive analysis of the global and regional CPE Chip markets, covering the forecast period 2025–2032. It offers detailed insights into market dynamics, technological advancements, competitive landscape, and key trends shaping the industry.
Key focus areas of the report include:
Market Size & Forecast: Historical data and future projections for revenue, unit shipments, and market value across major regions and segments. The global CPE Chip market was valued at USD million in 2024 and is projected to reach USD million by 2032.
Segmentation Analysis: Detailed breakdown by product type (4G Chip, 5G Chip), application (4G CPE, 5G CPE), and end-user industry to identify high-growth segments and investment opportunities.
Regional Outlook: Insights into market performance across North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa, including country-level analysis where relevant. Asia-Pacific currently dominates the market due to rapid 5G adoption.
Competitive Landscape: Profiles of leading market participants including Qualcomm, UNISOC, ASR, Hisilicon, and MediaTek, including their product offerings, R&D focus, and recent developments.
Technology Trends & Innovation: Assessment of emerging technologies in semiconductor design, fabrication techniques, and evolving industry standards for CPE devices.
Market Drivers & Restraints: Evaluation of factors driving market growth such as 5G rollout and IoT expansion, along with challenges including supply chain constraints and regulatory issues.
Stakeholder Analysis: Insights for chip manufacturers, network equipment providers, telecom operators, investors, and policymakers regarding the evolving ecosystem.
Related Reports:https://semiconductorblogs21.blogspot.com/2025/06/fieldbus-distributors-market-size-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/consumer-electronics-printed-circuit.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/metal-alloy-current-sensing-resistor.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/modular-hall-effect-sensors-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/integrated-optic-chip-for-gyroscope.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/industrial-pulsed-fiber-laser-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/unipolar-transistor-market-strategic.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/zener-barrier-market-industry-growth.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/led-shunt-surge-protection-device.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/type-tested-assembly-tta-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/traffic-automatic-identification.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/one-time-fuse-market-how-industry.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/pbga-substrate-market-size-share-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/nfc-tag-chip-market-growth-potential-of.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/silver-nanosheets-market-objectives-and.html
0 notes
Text
Maritime Digitization Trends Reshape Global Shipping Industry Outlook
The global maritime digitization market is on a trajectory of rapid transformation, poised to reach US$ 367.7 billion by 2031, growing at a compound annual growth rate (CAGR) of 9.3% from its valuation of US$ 167.7 billion in 2022. The industry’s expansion is propelled by the integration of cutting-edge technologies including AI, IoT, blockchain, and advanced analytics, aimed at improving operational efficiency, safety, and environmental sustainability.
Market Overview: Maritime digitization refers to the infusion of digital technologies across maritime operations including fleet management, vessel tracking, predictive maintenance, and energy optimization. With global trade increasingly reliant on marine transportation, the maritime sector is undergoing a technological revolution to enhance competitiveness, resilience, and compliance with environmental regulations.
The COVID-19 pandemic and growing environmental concerns have accelerated this digital transformation. Maritime digitization improves the visibility and agility of logistics operations while enhancing safety, lowering fuel consumption, and reducing greenhouse gas emissions.
Market Drivers & Trends
Key drivers of market growth include:
Adoption of AI and Machine Learning: These technologies are enabling predictive maintenance, route optimization, and real-time monitoring of ship operations.
Rising Regulatory Pressures: Regulations from bodies such as the International Maritime Organization (IMO) are mandating digital compliance through e-navigation strategies and FAL conventions.
Sustainability Push: Digitization supports environmental goals by reducing emissions, optimizing fuel consumption, and improving port logistics.
The trend of data-driven decision-making is revolutionizing maritime operations. From autonomous vessel control to remote monitoring, digitization is creating smarter, more responsive supply chains.
Latest Market Trends
Autonomous Vessels: The emergence of AI-powered autonomous ships is revolutionizing fleet operations, reducing the risk of human error and increasing efficiency.
Cybersecurity Focus: As digitization expands, so do threats. Maritime companies are investing in cybersecurity frameworks to protect sensitive data and ensure safe operations.
Blockchain Integration: Blockchain is increasingly used for secure, transparent, and tamper-proof documentation of contracts, transactions, and cargo movements.
Energy Management Systems (EnMS): Ships are increasingly equipped with EnMS to monitor and manage fuel usage, engine performance, and hybrid systems.
Key Players and Industry Leaders
Several companies are spearheading the digital wave in maritime operations:
Inmarsat Global Limited
Windward Ltd.
SparkCognition
ORBCOMM
Iridium Communications Inc.
Envision Enterprise Solutions Pvt. Ltd.
xyzt.ai
Wärtsilä Corporation
DNV AS
Siemens AG
Others
These companies are heavily investing in R&D and strategic collaborations to offer holistic digital solutions across the marine ecosystem.
Download now to explore primary insights from our Report in this sample - https://www.transparencymarketresearch.com/sample/sample.php?flag=S&rep_id=85295
Recent Developments
May 2023: Wärtsilä and DNV partnered to integrate Wärtsilä’s Fleet Optimization Solution (FOS) with DNV’s Veracity platform. The goal is to streamline emissions compliance reporting for ship management companies such as Anglo-Eastern.
January 2023: Inmarsat extended its partnership with Campbell Shipping, expanding its Fleet Xpress services to include endpoint security and fleet care for 12 vessels.
Such collaborations are setting new benchmarks for digital infrastructure and maritime performance monitoring.
Market Opportunities
The market presents significant opportunities in the following areas:
Smart Ports & Terminals: Digitization of port operations improves cargo handling, inventory management, and reduces vessel turnaround times.
Autonomous Navigation: Autonomous vessels equipped with AI and sensor technologies are expected to disrupt conventional maritime logistics.
Environmental Compliance Tools: Software platforms for emissions tracking, energy management, and regulatory reporting are in high demand.
Emerging Economies: Ports in Asia Pacific, Latin America, and the Middle East are rapidly upgrading their digital capabilities to keep pace with global trade demands.
Future Outlook
The maritime digitization market will continue its robust growth as stakeholders prioritize efficiency, transparency, and sustainability. With rising interest in green shipping and automation, investments in maritime tech infrastructure are expected to accelerate globally.
Over the next decade, digital twins, augmented reality (AR) training, remote diagnostics, and smart cargo management systems are expected to become standard practice across the industry.
Market Segmentation
The market is segmented based on technology, application, vessel type, solution type, end-user, and region.
By Technology:
AI
IoT
Blockchain
Others
By Application:
Fleet Management
Vessel Tracking
Energy Management
Inventory Management
Predictive Maintenance
By Vessel Type:
Dry Cargo Ships (bulk carriers, container vessels, general cargo)
Liquid Cargo Ships (crude carriers, product carriers)
Specialized Cargo Ships (passenger vessels, livestock carriers)
By Solution Type:
Cargo Management
Vessel Performance
Voyage Optimization
Sustainability & Compliance Management
By End-user:
Ports & Terminals
Shipping Companies
Maritime Freight Forwarders
Regional Insights
North America held the largest share of the maritime digitization market in 2022, driven by robust digital infrastructure and early adoption of AI and IoT technologies. The U.S. and Canada continue to lead in technological deployment and cybersecurity advancements.
Asia Pacific is projected to witness the highest growth through 2031. Ports such as Shanghai, Singapore, and Busan are digitizing rapidly to accommodate rising cargo volumes and global trade integration. Countries like China, India, and Japan are heavily investing in smart port development and autonomous vessel testing.
Europe is advancing sustainability through strong regulatory frameworks and digital compliance mandates, with major shipping lines investing in energy-efficient technologies.
Why Buy This Report?
Purchasing the Maritime Digitization Market Report offers in-depth insights and strategic advantages:
Comprehensive Analysis: Gain detailed market segmentation across technologies, applications, vessel types, and geographies.
Forecast Accuracy: Get reliable projections through 2031 based on proven analytical models.
Competitive Intelligence: Benchmark against industry leaders and emerging players with detailed company profiles and recent developments.
Strategic Planning Tool: Identify high-growth opportunities and market trends to align digital transformation strategies.
Environmental Focus: Understand how digital solutions drive compliance and sustainability within the shipping industry.
Explore Latest Research Reports by Transparency Market Research: Identity-as-a-Service (IDaaS) Market: https://www.transparencymarketresearch.com/identity-as-a-service-market.html
Internet of Things (IoT) in Healthcare Market: https://www.transparencymarketresearch.com/internet-things-healthcare-market.html
Peer-to-Peer Lending Market: https://www.transparencymarketresearch.com/peer-to-peer-lending-market.html
IT Asset Disposition (ITAD) Market: https://www.transparencymarketresearch.com/it-asset-disposition-market.html
About Transparency Market Research Transparency Market Research, a global market research company registered at Wilmington, Delaware, United States, provides custom research and consulting services. Our exclusive blend of quantitative forecasting and trends analysis provides forward-looking insights for thousands of decision makers. Our experienced team of Analysts, Researchers, and Consultants use proprietary data sources and various tools & techniques to gather and analyses information. Our data repository is continuously updated and revised by a team of research experts, so that it always reflects the latest trends and information. With a broad research and analysis capability, Transparency Market Research employs rigorous primary and secondary research techniques in developing distinctive data sets and research material for business reports. Contact: Transparency Market Research Inc. CORPORATE HEADQUARTER DOWNTOWN, 1000 N. West Street, Suite 1200, Wilmington, Delaware 19801 USA Tel: +1-518-618-1030 USA - Canada Toll Free: 866-552-3453 Website: https://www.transparencymarketresearch.com Email: [email protected] of Form
0 notes
Text
Unlock the Power of Real-Time Stock Data & AI Predictions with Alltick’s APIs
In today’s fast-moving financial markets, having access to real-time stock data and AI-driven stock predictions can make the difference between missed opportunities and smart, profitable trades. At Alltick, we provide cutting-edge Stock Real-Time API and Stock Prediction API solutions designed to empower traders, investors, and fintech developers with the tools they need to stay ahead.
Why Choose Alltick’s Stock APIs?
1. Stock Real-Time API – Instant Market Data at Your Fingertips
Our Stock Real-Time API delivers ultra-low latency market data, ensuring you get the latest prices, volume, and order book updates as they happen. Whether you're building a trading platform, a portfolio tracker, or conducting high-frequency analysis, our API offers:
Global market coverage (stocks, ETFs, indices, and more)
Millisecond-level latency for real-time decision-making
Reliable & scalable infrastructure to handle high-frequency requests
Easy integration with RESTful & WebSocket endpoints
2. Stock Prediction API – AI-Powered Market Insights
Predicting stock movements is no longer just for hedge funds. Our Stock Prediction API leverages machine learning and quantitative analysis to provide actionable forecasts, including:
Short-term & long-term price predictions
Trend analysis & volatility indicators
Sentiment analysis from news & social media
Customizable models to fit your trading strategy
Who Can Benefit from Alltick’s APIs?
Day Traders & Algorithmic Traders – Execute strategies faster with real-time data and predictive signals.
Fintech Startups & Developers – Build advanced trading apps, robo-advisors, or analytics dashboards.
Investment Firms & Hedge Funds – Enhance decision-making with AI-driven insights.
Retail Investors – Gain an edge with professional-grade tools.
Get Started Today!
Alltick’s Stock Real-Time API and Stock Prediction API are designed for performance, accuracy, and ease of use. Whether you're a developer, trader, or financial institution, our APIs provide the market intelligence you need to succeed.
Stay ahead of the market with Alltick – Where Data Meets Intelligence. 🚀
1 note
·
View note
Text
AI Model Integration for Apps: A Complete Developer’s Guide to Smarter Applications

In today’s digital-first world, applications are becoming smarter, faster, and more personalized thanks to the integration of Artificial Intelligence (AI). Whether you're a solo developer or part of a product team, embedding AI into your app can dramatically enhance its performance, usability, and value. From predictive analytics to voice recognition and recommendation systems, AI Model Integration for Apps is now a key strategy in modern app development.
What Is AI Model Integration? AI model integration refers to the process of incorporating machine learning models into software applications so they can make intelligent decisions based on data. These models are trained to perform tasks such as identifying images, predicting trends, understanding natural language, or automating responses—without the need for explicit programming for every possible scenario. When properly implemented, AI transforms static apps into dynamic, adaptive tools that continue to learn and improve over time.
Benefits of AI Integration in App Development
Personalized User Experiences: AI helps tailor content, notifications, and interactions based on user behavior, preferences, and usage patterns.
Smarter Automation: Repetitive tasks like sorting emails, flagging spam, or generating responses can be automated, saving time and effort.
Faster Decision-Making: Real-time analytics powered by AI models offer quick insights that improve user satisfaction and engagement.
Reduced Human Error: In fields like finance, healthcare, and logistics, AI models help catch inconsistencies or anomalies that might go unnoticed.
Enhanced Accessibility: Features such as speech-to-text, voice commands, and intelligent assistants make apps more inclusive and user-friendly.
Practical Use Cases of AI in Apps
E-commerce Apps: Recommending products based on user activity, managing inventory, and detecting fraudulent transactions.
Health & Fitness Apps: Predicting health trends, monitoring vital stats, and suggesting routines.
Travel Apps: Suggesting personalized travel itineraries or predicting flight delays.
Chat Applications: Implementing AI chatbots for 24/7 customer support.
Finance Apps: Detecting unusual activity, automating spending reports, and offering budget advice.
Steps for AI Model Integration The process of integrating AI models typically follows these steps:
Define the Problem: Decide what you want the AI model to do—recommend products, interpret voice commands, detect faces, etc.
Collect and Prepare Data: The model’s performance depends on high-quality data. Clean, labeled datasets are crucial.
Choose or Build a Model: You can either use pre-trained models from platforms like TensorFlow, PyTorch, or OpenAI, or build your own using custom datasets.
Train the Model: If you're not using a pre-trained model, train your model using machine learning algorithms relevant to your problem.
Deploy the Model: This can be done through APIs (such as REST APIs) or mobile SDKs, depending on your app’s environment.
Integrate with the App: Embed the model in your codebase and create endpoints or interfaces for your app to interact with it.
Test and Monitor: Evaluate the model’s accuracy, adjust for edge cases, and continuously monitor its performance in the real world. For a complete breakdown with code snippets, platform options, and common pitfalls to avoid, visit the full guide on AI Model Integration for Apps.
Popular Tools and Libraries for AI Integration
TensorFlow Lite: Designed for deploying machine learning models on mobile and embedded devices.
PyTorch Mobile: Offers a flexible and dynamic framework ideal for rapid prototyping and model deployment.
ML Kit by Google: A set of mobile SDKs that bring on-device machine learning to Android and iOS.
OpenAI API: Provides access to advanced language models like GPT, perfect for chatbots and text generation.
Amazon SageMaker: Helps build, train, and deploy machine learning models at scale with built-in support for APIs.
Best Practices for AI Model Integration
Start Small: Focus on integrating a single AI-powered feature before scaling.
Use Lightweight Models: Especially for mobile apps, use compressed or distilled models to maintain performance.
Prioritize User Privacy: Be mindful of how you collect and process user data and comply with data laws like GDPR and CCPA.
Maintain Transparency: Ensure users understand how AI is being used, especially when decisions impact their experience.
Test for Bias and Accuracy: Audit models regularly to prevent biased or inaccurate outcomes.
Future Trends in AI App Integration Expect more apps offering real-time sentiment analysis, emotion detection, personalized coaching, and integration with AR/VR. Cross-platform intelligence will also rise, where an app learns from your entire digital ecosystem.
Final Thoughts The power of AI lies in its ability to adapt, learn, and improve—qualities that, when integrated into apps, drive significant value for users. From increasing efficiency to delivering personalized experiences, AI model integration helps apps stand out in a crowded market.
1 note
·
View note
Text
Cybersecurity Threats to Watch Out For in 2025

The digital landscape is like a double-edged sword: offering new ways of connectivity and new vistas of innovation, while on the other side harboring a constantly mutating set of threats and increasingly complex attacks. As we approach 2025, we also see cybersecurity threats growing in complexity and reach. Thus, looking into these emerging threats should not merely be an interest for IT professionals, but something each person and organization involved in the online world should be aware of.
In the hands of cybercriminals, new technologies like Artificial Intelligence (AI) and Machine Learning (ML) are used to launch increasingly sophisticated and hence difficult to resist attacks. Learning what the top security issues of 2025 will be is the first in laying out necessary defenses.
Why Vigilance is Crucial in 2025
AI-Powered Attacks: Threat actors are using AI to make phishing smarter, malware more evasive and brute-force attacks faster.
Expanded Attack Surface: More devices (IoT), cloud services, and remote work setups mean more entry points for cybercriminals.
Sophisticated Social-Engineering: Attacks are becoming highly personalized and convincing, thereby being harder to detect.
Data Is Gold: Both individual and corporate data remains the Lucifer for theft, extortion, and manipulation.Lucifer prime target
Here are the top Cybersecurity Threats to Watch Out For in 2025:
1. AI-Powered Phishing and Social Engineering
The generic scam emails will be a thing of the past. In 2025, AI will revolutionize extremely sophisticated and bespoke phishing campaigns. The vast data lakes will be churned by AI to create messages that resemble trusted contacts, sound more convincing, and adapt in real-time, creating an impasse for the human end users in separating legitimate from malicious.
What to do: Promote enhanced employee awareness through AI-based phishing simulation, employ strong email filters, and intensify the mantra of "verify, don't trust."
2. Evolving Ransomware 3.0 (Data Exfiltration & Double Extortion)
Ransomware isn't just about encrypting data anymore. Attackers will increasingly focus on exfiltrating sensitive data before encryption. This "double extortion" tactic means they demand payment not only to decrypt your data but also to prevent its public release or sale on the dark web.
What to do: Implement robust data backup and recovery plans (following the 3-2-1 rule), deploy advanced endpoint detection and response (EDR) solutions, and strengthen network segmentation.
3. Supply Chain Attacks on the Rise
Targeting a single, vulnerable link in a software or service supply chain allows attackers to compromise multiple organizations downstream. As seen with past major breaches, this method offers a high return on investment for cybercriminals, and their sophistication will only grow.
What to do: Implement stringent vendor risk management, conduct regular security audits of third-party suppliers, and ensure software integrity checks.
4. IoT and Edge Device Vulnerabilities
The proliferation of Internet of Things (IoT) devices (smart homes, industrial sensors, medical devices) creates a massive, often insecure, attack surface. Many IoT devices lack strong security features, making them easy targets for botnets, data theft, or even physical disruption.
What to do: Secure all IoT devices with strong, unique passwords, segment IoT networks, and ensure regular firmware updates. Implement strong network security protocols.
5. Deepfakes and AI-Generated Misinformation
Advancements in AI make it possible to create highly realistic fake audio, video, and images (deepfakes). These can be used for sophisticated spear-phishing attacks, corporate espionage, market manipulation, or even to spread widespread disinformation campaigns, eroding trust and causing financial damage.
What to do: Implement robust identity verification protocols, train employees to be highly skeptical of unsolicited requests (especially via video/audio calls), and rely on verified sources for information.
6. Cloud Security Misconfigurations
While cloud providers offer robust security, misconfigurations by users remain a leading cause of data breaches. As more data and applications migrate to the cloud, improperly configured storage buckets, identity and access management (IAM) policies, or network settings will continue to be prime targets.
What to do: Adopt cloud security best practices, implement continuous monitoring tools, and conduct regular audits of cloud configurations.
Fortifying Your Digital Defenses
So, putting in a multi-layer defense model would do in order to be an active response to those cybersecurity threats in 2025. From the perspective of the individual, this encompasses strong passwords, MFA, software updates on a regular basis, and a little basic cybersecurity awareness. Organizations, on the other hand, would look at investing in good security infrastructure, ongoing employee training, threat intelligence, and possibly, ethical hacking exercises.
Cybersecurity Training in Ahmedabad could be your next area of interest in order to keep updating yourself and your team on fighting the said contemporary threats. The future is digital; securing it is the prerogative of every individual.
Contact us
Location: Bopal & Iskcon-Ambli in Ahmedabad, Gujarat
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
0 notes