#EmailPhishing
Text
Understanding Phishing Attacks

Learn how to safeguard yourself and your organization from phishing attacks.
Read More. https://www.sify.com/security/understanding-phishing-attacks/
0 notes
Link
https://bit.ly/3RmzLDN - 🔒 Microsoft Threat Intelligence reports that threat actors are increasingly misusing OAuth applications in financially driven attacks. OAuth, a standard for authentication and authorization, is being exploited to gain access to data and maintain persistent access to applications, even after losing initial account access. This misuse of OAuth poses significant risks in terms of data privacy and security. #MicrosoftThreatIntelligence #Cybersecurity 🐍 Attackers use phishing or password spraying to compromise user accounts, especially those lacking strong authentication. They then create or modify OAuth applications with high privileges for various malicious activities, including deploying VMs for cryptocurrency mining, executing business email compromise (BEC), and launching spamming activities using the organization's resources. #PhishingAttacks #PasswordSecurity 💰 One specific threat actor, known as Storm-1283, deployed VMs for cryptomining using compromised accounts. They incurred significant costs for the targeted organizations, ranging from $10,000 to $1.5 million. Microsoft's proactive measures, including the blocking of malicious OAuth applications and notification to affected organizations, have been crucial in mitigating these attacks. #CryptoMining #DigitalSecurity 📧 Another observed attack involved BEC and phishing via compromised user accounts and creation of OAuth applications. Attackers used these applications to maintain persistence and launch phishing emails, sending over 927,000 messages. Microsoft responded by taking down all related malicious OAuth applications. #BEC #EmailPhishing 🌐 For spamming, attackers like Storm-1286 used compromised accounts to create new OAuth applications for large-scale spam attacks. These attacks highlight the importance of multifactor authentication (MFA) as a key defense strategy. Microsoft’s detection capabilities in their various Defender products played a crucial role in identifying and mitigating these threats. #SpamAttacks #MFADefense ⚠️ Microsoft recommends several mitigation steps to combat these threats. These include enabling MFA, implementing conditional access policies, ensuring continuous access evaluation, enabling Microsoft Defender automatic attack disruption, auditing apps and consented permissions, and securing Azure cloud resources. These steps are essential for organizations to protect against OAuth application misuse. #CybersecurityBestPractices #MicrosoftDefender 🕵️♂️ Hunting guidance for Microsoft 365 Defender users includes monitoring OAuth application interactions, identifying password spray attempts, and investigating suspicious application creation and email events. These proactive measures help organizations detect and respond to potential threats in their networks.
#MicrosoftThreatIntelligence#Cybersecurity#PhishingAttacks#PasswordSecurity#CryptoMining#DigitalSecurity#BEC#EmailPhishing#SpamAttacks#MFADefense#CybersecurityBestPractices#MicrosoftDefender#ThreatHunting#Microsoft365Defender#useraccounts#cryptocurrencymining#businessemailcompromise#technology#access#data#privacy#cybersecurity
0 notes
Text
0 notes
Photo

Email Look Fishy?? Don't Take The Bait!!
Actively block #emailphishing to boost Email Deliverability & High Visibility!
Our Website: https://www.jnrmr.com
Call us @ +91–9811030121
#email#email security#email security solutions#phishing#phishing attack#how to check phishing website#online security#online safety
0 notes
Photo
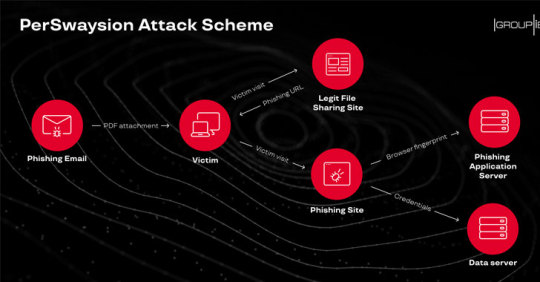
Targeted Phishing Attacks Successfully Hacked Top Executives At 150+ Companies #cyberattack #emailphishing #hackingnews #malwareattack #spearphishing #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo
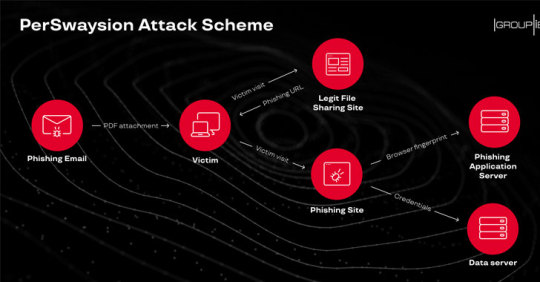
Targeted Phishing Attacks Successfully Hacked Top Executives At 150+ Companies | MrHacker.Co #cyber-attack #emailphishing #hackingnews #malwareattack #spearphishing #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo

New Group of Hackers Targeting Businesses with Financially Motivated Cyber Attacks | TheHackerNews.Co #bankingtrojan #cobaltstrike #cyber-attack #emailhacking #emailphishing #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Link
https://bit.ly/3OEOTfr - 🔒 Cyberattacks have become a major concern, affecting people, organizations, and governments globally. Understanding the anatomy of a cyberattack is key to building effective cybersecurity strategies. This report outlines the essential elements of cyberattacks, and the stages involved in phishing and ransomware attacks. #CyberSecurity #CyberThreats 🕵️ Reconnaissance: In the initial phase, attackers collect data about the target using active or passive techniques to identify vulnerabilities and important assets. #Reconnaissance #CyberAttack 🛠️ Weaponization: Attackers write malicious code or exploit known weaknesses, often creating malware such as viruses, trojans, or ransomware to target systems. #Weaponization #Malware 📨 Delivery: The next stage involves delivering the malicious payload using methods like phishing emails, harmful links, or infected attachments. #EmailPhishing #MaliciousLinks 🚪 Exploitation: Attackers then exploit flaws in the target network or system to gain unauthorized access, utilizing vulnerabilities in software or authentication processes. #Exploitation #UnauthorizedAccess 🔌 Installation: Following successful exploitation, the attackers install the virus to maintain control over the target system and potentially escalate their network access. #MalwareInstallation #NetworkSecurity 🎮 Command and Control (C2): Attackers set up C2 infrastructure for communication with compromised systems, allowing them to secretly execute malicious actions. #CommandControl #C2 🎯 Actions on Objective: Once in control, attackers may pursue goals such as data theft, alteration, ransom requests, or launching further attacks. #DataTheft #Ransomware 🧹 Covering Tracks: The final stage involves erasing evidence by deleting logs and disguising activity to avoid detection. #CoveringTracks #CybersecurityMeasures 🎣 Understanding Phishing Attacks: These involve social engineering to deceive victims into revealing sensitive information, through stages of reconnaissance, weaponization, delivery, exploitation, installation, C2, actions on objective, and covering tracks. #PhishingAttack #SocialEngineering 🔐 Understanding Ransomware Attacks: In a ransomware attack, malicious software encrypts a victim’s data, demanding ransom for decryption. The stages include reconnaissance, weaponization, delivery, exploitation, installation, C2, actions on objective, and covering tracks. #Ransomware #DataEncryption 🛡️ Conclusion: Recognizing the stages of cyberattacks empowers individuals and organizations to implement proactive security measures. Education about potential threats and best practices can defend against the evolving landscape of cyber threats. Cybersecurity is a shared responsibility that requires vigilance and proactive steps to reduce risks.
#CyberSecurity#CyberThreats#Reconnaissance#CyberAttack#Weaponization#Malware#EmailPhishing#MaliciousLinks#Exploitation#UnauthorizedAccess#MalwareInstallation#NetworkSecurity#CommandControl#C2#DataTheft#Ransomware#CoveringTracks#CybersecurityMeasures#PhishingAttack#SocialEngineering#DataEncryption#CybersecurityAwareness#CollectiveResponsibility#ransomwareattacks#ransomwareattack#concern#government#cybersecurity#strategy
0 notes
Text
Email: Good for phishing. Bad for business. -...
According to #Cybersecurity firm Trend Micro, about 90 percent of all data breaches begin with a simple #emailphishing attack. Financial wellness starts with knowing your personal and financial data are safe and sound via @LiscioCX #PoweringProsperity
Email: Good for phishing. Bad for business. -...
According to cybersecurity firm Trend Micro, about 90 percent of all data breaches begin with a simple email phishing attack. Financial wellness starts with knowing your personal and financial data are safe and sound. And email just isn’t a safe place to do business anymore.
accountantvip
0 notes
Link
#CyberSecurity#Malware#DataScience#Internet#EmailPhishing#Security#Prevention#eCommerce#ProBlogBooster#Technology#FacebookSecurity#Hakcing#Tech#Instagram#Google
0 notes
Photo

World Health Organization Warns About Coronavirus Phishing Attacks #avoidphishingattacks #bankaccount #bankdata #coronavirus #coronavirusphishing #credentials #creditcard #creditcardtheft #creditcards #debitcard #emailphishing #paymentcards #paymentdetails #phishing #phishingattack #phishingcampaign #phishingemailattack #phishingemails #phishingscam #stolenusercredentials #whocoronavirus #worldhealthorganization #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

New Group of Hackers Targeting Businesses with Financially Motivated Cyber Attacks | MrHacker.Co #bankingtrojan #cobaltstrike #cyber-attack #emailhacking #emailphishing #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo
How CAPTCHA is being used to bypass anti malware security scans and firewalls | TheHackerNews.Co #captcha #cybersecurity #emailphishing #hacking #malware #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes