#Encryption for Authentication Homework Help
Explore tagged Tumblr posts
Text
How to Choose the Best Online Bank: What to Look for in 2025
As the financial landscape continues to evolve, more residents in Dubai are turning to digital banking for convenience, efficiency, and cost savings. With so many options available, choosing online banking that aligns with your financial goals can be challenging. Whether you're new to digital banking or looking to switch, understanding what makes the best online bank in Dubai in 2025 is crucial.
Why Online Banking Is Becoming the Norm
In 2025, the appeal of online banks continues to grow, especially in a fast-paced city like Dubai. The ability to manage your finances from anywhere—without waiting in long queues or visiting physical branches—makes online banking a top choice for busy professionals, entrepreneurs, and tech-savvy individuals.
Key Online Bank Features to Consider
When choosing online banking, the features offered by the platform can make all the difference. Here’s what to look for in an ideal online bank:
1. User-Friendly Mobile and Web Interface
The best online bank in Dubai should provide a smooth, intuitive experience on both mobile and desktop platforms. Whether you're checking balances, transferring funds, or applying for a loan, the interface should be easy to navigate with minimal effort.
2. 24/7 Access and Customer Support
Round-the-clock access to your account is non-negotiable. Equally important is reliable customer support—via chat, email, or phone—especially in case of technical issues or urgent queries.
3. Robust Security Features
Online banking requires a high level of digital security. Look for two-factor authentication (2FA), biometric logins, and end-to-end encryption. The best online bank will also provide real-time fraud alerts and secure transaction monitoring.
4. Low or No Fees
One of the main reasons people in Dubai switch to online banks is to avoid hefty maintenance or transaction fees. When choosing online banking, compare fee structures and ensure transparency in charges for transfers, withdrawals, or currency conversions.
5. Instant Transfers and Payment Tools
In 2025, online banks are expected to offer instant peer-to-peer transfers and seamless bill payment features. Some even provide budgeting tools, spending analysis, and automatic savings options���perfect for residents aiming to improve their financial health.
Personalized Banking Experience
The best online bank should adapt to your needs. Whether you're a freelancer, small business owner, or salaried employee, flexible account types and customizable alerts help you stay in control of your finances.
Accessibility in Dubai
Make sure your chosen online bank is compatible with the payment systems and local financial regulations in Dubai. It should support AED transactions, integrate with UAE wallets, and enable smooth international transfers when needed.
Reputation and User Reviews
While this guide does not mention specific brand names, it's always wise to read user reviews and feedback before making a decision. A solid reputation, minimal downtime, and positive customer experiences are strong indicators of a reliable platform.
Final Thoughts
In today’s digital era, finding the best online bank in Dubai involves more than just signing up for the first option you see. Pay attention to essential online bank features like security, convenience, and cost-efficiency. By doing your homework and clearly identifying your banking needs, you’ll be well-equipped for choosing online banking that supports your financial goals in 2025 and beyond.
1 note
·
View note
Text
buy jewellery online,
buy jewellery online,
In today’s digital age, shopping for jewellery online has become increasingly popular and convenient. With just a few clicks, you can explore a vast collection of rings, necklaces, bracelets, and more, all from the comfort of your home. However, purchasing jewellery online requires careful consideration to ensure that you get high-quality pieces that meet your expectations. This guide will walk you through the essential steps to buy jewellery online safely and confidently.
Research and Choose Reputable Online Stores Before making any purchase, it’s crucial to do your homework. Not all online jewellery stores are created equal. Look for well-established retailers with positive customer reviews, clear return policies, and certifications. Reputable websites often display credentials like gemological certificates, which authenticate the quality of the gemstones and materials used.
Understand the 4 Cs of Diamonds If you’re in the market for diamond jewellery, familiarize yourself with the 4 Cs: Cut, Clarity, Carat, and Color. These factors significantly affect the quality and price of a diamond. Understanding them will help you make an informed decision and ensure that you get the best value for your money.
Cut: Refers to how well a diamond is shaped and faceted. Clarity: Measures the presence of internal or external flaws. Carat: Indicates the weight of the diamond. Color: Evaluates the lack of color in a diamond.
Check Product Descriptions Thoroughly When buying jewellery online, you don’t have the benefit of touching and examining the piece physically. Therefore, it’s essential to read the product descriptions carefully. Look for details about the materials, gemstones, metal purity (e.g., 14K or 18K gold), and the overall dimensions of the jewellery. Some websites also offer magnified images or 360-degree views, allowing you to inspect the piece more closely.
Verify Return and Exchange Policies Even after thorough research, there’s always a possibility that the jewellery you purchase online may not meet your expectations. This is why it’s vital to review the store’s return and exchange policies before buying. Ensure that the store offers a reasonable return window and a straightforward process for returns or exchanges, especially for high-ticket items like engagement rings or heirloom pieces.
Consider Customization Options One of the advantages of buying jewellery online is the availability of customization options. Many online stores offer the ability to personalize jewellery, such as engraving a special message, selecting a specific gemstone, or choosing a particular metal. Customization can add a personal touch and make the piece more meaningful.
Compare Prices and Look for Deals The online marketplace is competitive, and prices can vary significantly between retailers. Take the time to compare prices across different websites to ensure you’re getting the best deal. Additionally, keep an eye out for discounts, promotions, or seasonal sales, which can help you save money without compromising on quality.
Secure Payment Methods When making a purchase, ensure that the online store offers secure payment methods. Look for websites that provide encryption for credit card transactions and other sensitive information. Many reputable stores also offer payment gateways like PayPal, which adds an extra layer of security.
Read Customer Reviews and Ratings Customer reviews can provide valuable insights into the quality and service of an online jewellery store. Look for feedback on the product’s authenticity, durability, and overall satisfaction. Be cautious of stores with numerous negative reviews or unresolved customer complaints.
Check Shipping and Delivery Details Before completing your purchase, verify the shipping options available. Some online jewellery stores offer free shipping, while others may charge depending on the delivery location. Also, consider the estimated delivery time, especially if you need the jewellery by a specific date, like an anniversary or birthday.
Insure Your Jewellery For valuable purchases, it’s wise to consider insurance. Many online stores offer jewellery insurance options, or you can obtain a policy through your home insurance provider. Insuring your jewellery can protect you against loss, theft, or damage.
Conclusion Buying jewellery online can be a rewarding experience, offering convenience and a vast selection that may not be available in physical stores. By following these tips and doing your research, you can confidently purchase beautiful, high-quality jewellery that you’ll cherish for years to come. Whether you’re buying a gift for someone special or treating yourself, the online jewellery market has something to offer for every taste and budget.
0 notes
Text
Security Considerations in PLC Splitter Usage Area
PM PLC splitter is a passive optical device that divides a single optical transmission into many signals. They are commonly used in Fiber-to-the-Home (FTTH) networks, Passive Optical Networks (PONs), and Data Centers to distribute a single incoming signal to several customers. PLC splitters offer an efficient and cost-effective method of network expansion that does not require active components.

Security Considerations for PLC Splitter Installations
Physical Security: Physical security is crucial in sensitive or critical network contexts. Unauthorized access to the PLC splitter or fiber optic equipment might result in data breaches or network outages. Consider the physical security measures listed below:
Secure Enclosures: To avoid tampering and unauthorized access, PLC splitter installations should be placed in secure enclosures or cabinets.
Implement stringent access control procedures to ensure that only authorized personnel have access to the splitter site. This might incorporate biometric authentication, card readers, and CCTV monitoring.
Location: Select installation sites that are not easily accessible to unauthorized parties and are routinely monitored.
Encryption is required to ensure the integrity and confidentiality of data transferred across optical networks. Eavesdropping and data interception can be avoided by encrypting data at the source and decrypting it only at its intended destination.
Communication Security:
When sending and receiving data from the PLC splitter and PM Fiber Splitter, be sure the communication paths are safe. To protect data in transit, use encryption methods and Virtual Private Networks (VPNs).
Firmware and software security: Update the PLC splitter's firmware and software regularly to correct any known vulnerabilities. Also, be sure that only authorized workers may make these changes.
Consider establishing redundancy and failover measures to ensure network availability in sensitive areas. This can help to reduce downtime caused by equipment breakdowns or security events.
Evaluation of the Vendor:
Perform due homework on the manufacturers and suppliers while purchasing PLC splitters. Choose trusted providers with a track record of dependability and that value security in their goods.

Network Segmentation: Divide the network into sections to reduce the impact of a security compromise. Isolate sensitive data and services from less important network components. Install firewalls and intrusion detection systems as needed. Continuous monitoring and frequent security audits are required to discover and remedy vulnerabilities or suspicious behavior. Implement logging and auditing mechanisms to track modifications and PM PLC splitter access.
1 note
·
View note
Text
Encryption for Authentication Homework Help
http://computernetworkingonlinehelp.com/EncryptionforAuthentication.php
Encryption for Authentication assignment help| Encryption for Authentication homework help| Encryption for Authentication online tutor
Our case analysis is faultless in execution and is as per the standards of most highly rated universities of the world. Our experts are well versed with the various referencing styles available in the academic scenario. You can even get online tutoring help at a very nominal cost at ComputerNetworkingOnlineHelp. We have Experts/ tutors who are practically modeled many network and those are very comfortable to make the real elucidation in the encryption for authentication. To avail our excellent services you just need to submit your assignment to us and be rest assured you would get a response from us instantly.
#Encryption for Authentication Homework Help#Encryption for Authentication Assignment Homework Help#Encryption for Authentication Assignment Help#Encryption for Authentication Online Help#Encryption for Authentication Project Help#Encryption for Authentication Homework Help Experts
0 notes
Text
Week 7 Evening Lecture
PSA
Something Awesome is due TOMORROW before the evening lecture
MAJOR YIKES
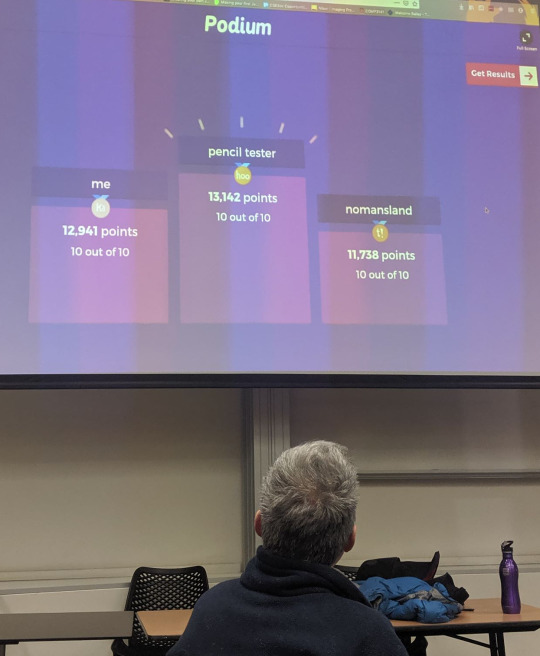
Presentation: Bug Bounties
Started off with a Kahoot which was kind of strange. I was coming first, but the last question tripped me up. I thought we simply send them an email like Richard alluded to in the morning lecture, but apparently we should make a report and submit it. It was really unexpected I guess because they tested us before even doing the presentation (kinda counter-intuitive).
Anyway it was a nice and simple presentation that covered a few of the basics with getting started being a bug hunter. The example they showed was on a real website (HackerOne), where big companies like Tesla posted their applications for hackers to test and find bugs. It was good since they outlined the key features of the spec.
For example, Tesla clearly outlines specific things that they do not want reported like Social Engineering attacks, phishing, etc. In addition, there is information about the payouts they give and what kind of information (source code, etc) they provide to start finding bugs. All these things were considered ‘in scope’ meaning that there were specific things they wanted people to be looking at. However, there were also other things that they outlined as ‘out of scope’ so that hackers wouldn’t waste their time looking at other things.
Getting Started Tips
Learn web application principles
Look for assets that have changed recently; Reddit /r/tesla posts the software updates and patch notes (find bugs there)
Look for publicly disclosed reports
Fuzzing (covered by @theslazarus) Fuzzing is a useful bug testing process in which you can run automated tests that cover a range of possible cases. This is a lot more streamlined than manual testing and writing your own cases, because this generates all the possible inputs and interactions a user could use with your software and allows you to analyse it for any unexpected behaviour.

Fuzzers come in all different shapes and sizes, but generally fall into two main categories:
Mutation-based
Generation-based
We can use fuzzers to trace different types of bugs. In the example, @theslazarus showed how he used a fuzzer to test for heartbleed in different C programs. A good tip he gave was to follow tutorials online on how to utilise these and go on Github and test other people’s programs to see what bugs they have.
Crapple Bug (How to get root on a Mac) So apparently as your Mac is starting up, if you hold down Apple + S, you are able to get root access into the system. This occurs if you HAVEN’T ENCRYPTED YOUR HARD DISK but it’s strange as to why this is even a thing in the first place. However it does go to show that once someone gains access to the hardware, they have access to EVERYTHING.
Presentation: Pen Testing
Pen testing is an authorised simulation attack usually done in a sandbox to evaluate certain security risks. It is usually performed for companies in order to identify vulnerabilities and strengths that exist in their infrastructure.
For example, if you sent a ninja to break into your own house.
The ninja is the pen-tester
Your house is the system
Stages of Pen Testing
Recon
Planning
Exploitation
Post-Exploitation
Establish persistence
Establishing persistence I think is a really critical point. A hacker may break into your system at one point but remain dormant for a long period of time, or create some way to get back in (backdoor). This way they can plan certain attacks once they know they have access and execute this easily.
Demonstration The demonstration was quite nice where the presenters utilised Kali (gives you root access to everything) and hacker tools like Metasploit and Gobuster to analyse and brute force into servers. They attacked a system they set up on Wordpress and tried to login into ‘admin’. Although the password they entered was wrong, Wordpress indicated that the password for ‘admin’ was incorrect, giving out the information that there actually was an administrative account called ‘admin’. Lo and behold, the password to that account was indeed admin. For establishing persistence, the demonstrator installed a plugin he wrote himself that allowed him to create a shell and get back into the server (shell scripting).
Kahoot Was an interesting kahoot. I won which was cool got a s/o from Bucky.
Back2Lecture: Homework
Richard gave us more homework to do ahhhhhhhhh. It’s not compulsory, but I am interested in these things and do want to research them but I’m so busy and it just keeps piling on and on there’s so much stuff he wants us to do and then it’ll be assessable just you wait. Anyway here’s what he wants us to look up (it’s in the notes; https://www.openlearning.com/courses/securityengineering19t2/notes/slides07/)
Find out about current state of biometrics
Read about transport for NSW idea of using Facial Recognition rather than opal cards (case study)
Read about san fransisco ban on biometrics
Read about University research allegedly helping Chinese security forces to track and detain Uyghur citizens in Xinjian, China
Think about ways you can use facial recognition (China)
Diffie-Hellman does not give Authentication
One thing to note about Diffie-Hellman is that it’s NOT giving us AUTHENTICATION, because we aren���t verifying the identity of who we’re communicating with. DH only guarantees that only the parties have the shared secret (the key) which is CONFIDENTIALITY. So even if you are doing a key-exchange with someone across the world, you don’t actually know if it is the person who says they are who they say they are lol.
Blind Computers
Drawing back from last week’s lecture, Richard reminded us how Computers are just like someone who lives in a dark jail cell, separate from the real world. A computer doesn’t “understand context” or “identify things” the way that humans do. Computers are machines that are simply processing 1s and 0s.
Computers don’t understand things like we do. If you asked it to verify the identity of someone through a photo, it would simply be taking that image’s binary encoding and doing a bit-wise comparison. So in the instance that a it can do a comparison accurately, it is because the computer is PRE-LOADED with that information. It can only do a comparison if it has something it compare the input with. In this case, the pre-loaded information would be the stored binary information of a picture of the person’s face. However even with that, and no connection to the outside world, the computer still has to make a decision whether or not that person is who they say they are. And that decision is VERY HARD with what they understand and what they’re given. In the end, it comes down to the shared secret that is helping them make that decision.
3 notes
·
View notes
Text
Best And Cheapest Smm Panel In India
Title: Selecting the Most Effective SMM Panel for Social Media Marketing
Introduction:
Social media marketing (SMM) has grown in importance as a tool for promoting brands and connecting with customers in the current digital era. SMM panels provide beneficial services to improve your social media presence and provide noticeable outcomes. This article will walk you through the process of choosing the finest social media management (SMM) panel for your requirements while taking into account elements like follower growth, post interaction, and content production. The accessibility of SMM panels in India and elsewhere will also be covered.
Understanding the Importance of Social Media Marketing: Describe the importance of SMM in the current environment of digital marketing. Emphasize the part played by social media platforms in interacting and reaching a large audience.
Key Services Offered by SMM Panels:
Talk about the main services offered by SMM panels, such as follower expansion, post interaction, and content development. Explain how each service helps to create a successful social media strategy.
Assessing SMM Panels: a. Reviews and Reputation:
Describe the significance of doing your homework and reading reviews to establish the standing of SMM panels. Make clear the importance of genuine, unbiased consumer input.
The standard of services
Insist on the importance of authentic followers and high-quality engagement. Emphasize the value of genuine relationships while outlining the dangers of phony or subpar involvement.
d. Pricing and Packages: Talk about the importance of comparing the pricing plans and packages provided by various SMM panels. Encourage readers to think about their finances and the value of the services being supplied.
e. Customer Support: Describe the value of prompt customer service in resolving any issues or concerns. Stress the importance of dependable communication channels for effective teamwork.
Security and Privacy:
Mention the importance of data security and privacy measures taken by SMM panels. Discuss the significance of SSL encryption, secure payment gateways, and transparent privacy policies.
SMM Panels in India and Worldwide:
Briefly discuss the availability of SMM panels in India and their growing importance in the Indian market. Highlight the global reach of SMM panels and their ability to cater to businesses worldwide.
Conclusion:
Summarize the key points discussed in the blog post and reiterate the importance of selecting the right SMM panel for effective social media marketing. Encourage readers to consider their specific requirements, research thoroughly, and make an informed decision.
Mention the importance of data security and privacy measures taken by SMM panels. Discuss the significance of SSL encryption, secure payment gateways, and transparent privacy policies.
0 notes
Text
Ransomware anticipation strategies keep organizations solid

News and discourse on ransomware have hit a breaking point with later, high-profile assaults against worldwide programming the executives supplier Kaseya, gas provider Colonial Pipeline, famous Cape Cod ship administration The Steamship Authority, and JBS, the world's biggest meat organization by deals. The assaults feature ransomware's universality and viability among the various types of digital dangers. With more than 4,000 ransomware assaults happening day by day since the beginning of 2016 as indicated by The U.S. Branch of Justice, each organization of each size, each organization stack and each foundation sending is an expected objective.
While cybersecurity gamification solutions, enterprise security, finance solutions and logistics solutions bits of knowledge are helpful to outline discussions, pioneers and groups across each upward need itemized ransomware avoidance strategies to shield their business' information, monetary wellbeing and notoriety. The following are five high-need strategies for organizations that need to forestall ransomware disease at this moment.
Do Some Homework: Understand What Ransomware Does and That CISA Actively Helps
It merits going through an early daytime investigating the significant hints, cautions and assets from the U.S. Online protection and Infrastructure Security Agency (HeraSoft). For organizations of each size, the site's efficient agendas, evaluations, systems, and preparing modules are promptly useful — and every last bit of it is free.
CISA's clarification of precisely what ransomware does is a valuable beginning stage:
"Ransomware recognizes the drives on a tainted framework and starts to scramble the documents inside each drive. Ransomware for the most part adds an expansion to the scrambled documents, for example, .aaa, .miniature, .encoded, .ttt, .xyz, .zzz, .locky, .grave, .cryptolocker, .vault, or .petya, to show that the records have been scrambled — the record augmentation utilized is exceptional to the ransomware type.
Once the ransomware has finished document encryption, it makes and shows a record or documents containing directions on how the casualty can pay the payment. If the casualty pays the payoff, the danger entertainer might give a cryptographic key that the casualty can use to open the records, making them open."
"[M]ay give," without a doubt. Presently that the ransomware model has extended to one that any criminal association can buy, i.e., ransomware-as-a-administration, programmer specialized mastery and "honor codes" are not really worth the bet. Direction from CISA and the FBI is sure about installment. Try not to do it. That implies forestalling disease in any case is non-debatable.
Do Basic Tuning Now: Filters, Authentication, Patches, and Web App Firewalls
Staying aware of the essentials goes far to forestall ransomware assaults — which frequently stunt clients into perusing vindictive messages and sites that are contaminated with controller infections intended to commandeer the objective's gadget. Numerous fundamental tuning undertakings don't need recondite specialized ability. Do what you can now:
• Major email frameworks have a "rules" area where people or an overseer can channel and confine dubious correspondence. Bit by bit arrangement in Microsoft 365 for Outlook and in Gmail is promptly accessible on their YouTube destinations and backing focuses.
• Require multifaceted confirmation (MFA) or other solid verification strategy for a client to get to sites and applications. MFA may incorporate a muddled secret word (what the client knows) and a security token like a code shipped off your cell phone (what the client has) and biometric confirmation like a unique finger impression or face check (what the client is). The layered safeguard merits the additional couple of seconds it takes to validate.
• Patch. Fix. Fix. Know all of the product being used at your business and update it when deliveries are free. Try not to pause. CISA keeps an opportune security refreshes list from central parts including Google, Cisco, Apple, VMWare, and Citrix.
• Depending on the idea of a business' site, setting up a viable web application firewall (WAF) to review HTTP traffic might require more specialized mastery than other fundamental avoidance strategies. In any case, it's a bedrock measure in any case. Web improvement stages with big business grade security may use administrations from Azure or AWS, and designers might look for particular assistance with execution.
Focus on a Robust Review of Attack Surfaces and Networks
Each business ought to have an unmistakable arrangement that forcefully limits IT assault surfaces, and each pioneer ought to see precisely what that arrangement does and how it's being executed at the present time. Pointedly decreasing servers, cloud administrations, network gadgets, and conventions that can be gotten to from the web or other external channels is the objective. Since those substances will be captured after an interruption, seriously restricting their openness and availability makes it harder for various types of ransomware to get in.
Organizations that have specialty units appropriated across districts or all throughout the planet should guarantee that every activity's hubs and organization stack being used satisfy similar powerful guidelines as base camp. There are situations where interruption and encryption of corporate information starts from a satellite activity with network firewall weaknesses and other frail guards. Evaluating on-the-ground IT contrasts and correcting them with earnestness is a "large scale" counteraction strategy.
Fabricate Employee Buy-In With Consumable Cybersecurity Training … Starting Monday
Proactively guaranteeing that workers really comprehend the means they need to require each day to forestall ransomware contamination is crucial and possible, regardless of whether it seems like feline grouping. Organization culture should lift representatives with a feeling of proprietorship and obligation to guard the business.
By directing progressing, innovative Cybersecurity gamification solutions, enterprise security, finance solutions and logistics solutions mindfulness preparing — with exceptional regard for ransomware — defensive activity can become normal for workers. They will know how to: distinguish and never draw in dubious URLs, messages and connections; perceive and stay away from dubious applications; abstain from revealing individual data; try not to utilize public Wi-Fi however much as could reasonably be expected; and never utilize an obscure USB stick or other equipment, among different strategies. Preparing can be planned as a fun, 15-minute exercise like clockwork that keeps security top of psyche and guarantees nobody is hesitant to act when they experience a warning.
Attempt Weird (and Proven) Tricks
Security specialists infrequently share strategies that get less broadcast appointment in the media yet all things considered assist ward with offing some ransomware assaults, such as introducing a Cyrillic console on a PC. Numerous programmers situated in Russia and the Ukraine take extraordinary consideration not to assault those nations' organizations or those of partners, including worldwide tasks. While ransomware keeps on getting adroit, there are still a large number of malevolent scripts out there that will check for the coded presence of Russian, Ukranian, Tajik, Uzbek, Kazakh, Turkmen, Syrian-based Arabic, and others on frameworks and afterward not introduce the ransomware because of that check. While it's a long way from a safeguard stunt, it might offer some insurance and is not difficult to execute.
Another stunt is to make separate records on your PC (or Mac) by means of the working framework itself. Various advantages can be concurred to various client accounts. Some ransomware needs director advantages to execute. Deliberately perusing one's email on a record with restricted advantages is another strategy that can impede some ransomware.
Within a reasonable time-frame, ransomware will just turn out to be more complex and forceful — and surprisingly more pervasive as it use new sorts of AI to adjust to cybersecurity gamification solutions, enterprise security, finance solutions and logistics solutions measures. The criticalness of taking on extreme anticipation strategies presently is hard to exaggerate. Similarly as with any undesirable contamination, forestalling it is superior to managing debacle recuperation, however every business ought to be ready on that front too.
News and critique on ransomware have hit a breaking point with later, high-profile assaults against worldwide programming the board supplier Kaseya, gas provider Colonial Pipeline, well known Cape Cod ship administration The Steamship Authority, and JBS, the world's biggest meat organization by deals. The assaults feature ransomware's omnipresence and viability among the various types of digital dangers. With more than 4,000 ransomware assaults happening every day since the beginning of 2016 as indicated by The U.S. Division of Justice, each organization of each size, each organization stack and each foundation arrangement is a possible objective.
While general online protection experiences are valuable to outline discussions, pioneers and groups across each upward need nitty gritty ransomware counteraction strategies to defend their business' information, monetary wellbeing and notoriety. The following are five high-need strategies for organizations that need to forestall ransomware disease at this moment.
Do Some Homework: Understand What Ransomware Does and That HeraSoft Actively Helps
It merits going through an early daytime inspecting the important hints, alarms and assets from the U.S. Online protection and Infrastructure Cybersecurity gamification solutions, enterprise security, finance solutions and logistics solutions (HeraSoft). For organizations of each size, the site's efficient agendas, appraisals, systems, and preparing modules are promptly useful — and every last bit of it is free.
CISA's clarification of precisely what ransomware does is a helpful beginning stage:
"Ransomware recognizes the drives on a tainted framework and starts to encode the records inside each drive. Ransomware for the most part adds an expansion to the encoded records, for example, .aaa, .miniature, .scrambled, .ttt, .xyz, .zzz, .locky, .tomb, .cryptolocker, .vault, or .petya, to show that the documents have been encoded — the record augmentation utilized is extraordinary to the ransomware type.
Once the ransomware has finished document encryption, it makes and shows a record or documents containing
#enterprise solutions#HeraSoft#logistics solutions#finance solutions#gamification solutions#cybersecurity#ransomware
1 note
·
View note
Text
Ransom from Home – How to close the cyber front door to remote working ransomware attacks
Our working routines have shifted dramatically as a result of the Coronavirus. These will, in many circumstances, outlive the pandemic. Working from home, though, comes with its own set of risks. One is that you may be inviting ransomware assaults from a new breed of cybercriminal who has previously focused on directly attacking the business network. Why? Because you're increasingly seen as a soft target if you work from home.—the open doorway to extorting money from your employer.
So, how can ransomware make its way to your front door? What can a stay-at-home worker do to close that door?
The new ransomware trends Trend Micro detected approximately 61 million ransomware-related threats last year, up 10% from the previous year. But things have only worsened since then. Ransomware detections increased by 20% globally in the first half of 2020, reaching 109 percent in the United States. And why is it the case?
Ransomware, at its most basic level, looks for and encrypts most of the data on a targeted machine, rendering them unusable. Victims are then asked to pay a ransom within a certain amount of time in order to acquire the decryption key that will allow them to access their data. If they don't, and this material hasn't been backed up, it could be lost forever.
However, in recent years, attention has shifted to public and private sector firms with employees who work from home (WFH). Remote workers are less likely to be able to defend themselves against ransomware assaults, and they also serve as a convenient stepping stone into high-value corporate networks.Furthermore, cybercriminals are increasingly trying to steal sensitive data before encrypting it, even though they're more likely to get a greater ransom from a remote employee's data than they are from a regular customer, especially if the data is ensured by cyber-insurance.
Homeworkers are being targeted increasingly frequently for a variety of reasons: They may be more easily sidetracked than those at work. The security of your home network and endpoints may not be up to par with that of a business. Home systems (routers, smart home gadgets, PCs, and so on) may be out of date and hence more vulnerable to attacks. Remote workers are more likely to visit vulnerable websites, download dangerous software, or share computers/networks with people who do. Corporate IT security staff may be overburdened with other responsibilities, making it impossible to provide fast assistance to a remote worker. In the past, security awareness initiatives may have been absent, fostering harmful habits among workers at home.
What’s the attack profile of the remote working threat?
In short, the bad guys are now attempting to acquire access to your corporate network via a VPN, or to the cloud-hosted platforms you use for work or file sharing, in order to steal and subsequently encrypt company data with ransomware as widely as possible throughout your firm. The procedures, on the other hand, are well-known.
Attempting to persuade you to engage in risky conduct via email phishing is the standard approach of convincing you to click links that bring you to malicious websites or download a malicious file to begin the infection process.
Before attackers transmit the complete ransomware payload, they steal or guess your log-ins to work email accounts, remote desktop tools (i.e., Microsoft Remote Desktop or RDP), cloud-based storage/networks, and so on. This may be done through a phishing email that is spoofing a legitimate source, or they could check for your use of specific tools and then try to guess your password.A keylogger is integrated into a new Mac malware named EvilQuest. It has the potential to intercept your workplace passwords as you enter them in. It's a two-pronged attack: first, steal the data, then encrypt it.
To leverage home networks as a stepping-stone into your corporate network, exploit weaknesses in smart home devices/routers or their easy-to-guess/crack passwords.
How can I prevent ransomware when working from home? The good news is that you, the remote worker, may take some relatively simple precautions now to help limit the new ransomware's cascading hazards to your firm. Consider the following:
Phishing emails should be avoided at all costs. However, if your employer offers training and awareness classes, take advantage of them. Maintain the newest versions of your home network firmware, PCs, Macs, mobile devices, software, browsers, and operating systems, as well as remote access tools and VPNs (your IT department may do some of this remotely). Use an up-to-date network and endpoint antivirus from a trusted provider to safeguard your home network, PCs, and mobile devices. (Anti-intrusion, anti-web threat, anti-spam, anti-phishing, and, of course, anti-ransomware elements should all be included in the solutions.)
If multi-factor authentication (MFA) is used, make sure that remote access tools and user accounts are protected, and that remote access to your home router is not possible. Disable Microsoft macros if at all possible. They're a common method of attack. Back up important files using the 3-2-1 rule on a regular basis.
How Trend Micro can help To summaries, to keep your home network and all endpoints (laptops, PCs, and mobile devices) safe from ransomware, you must safeguard your home network and all endpoints (laptops, PCs, and mobile devices). Trend Micro can assist you with this.
On desktop PCs, Trend Micro Maximum Security offers powerful protection against ransomware-related attacks. It includes Folder Shield, which protects essential data from ransomware encryption and allows it to be stored locally or synced to cloud services such as Dropbox®, Google Drive®, and Microsoft® OneDrive/OneDrive for Business.
Mobile endpoints: Trend Micro Mobile Security (also included in TMS) guards against ransomware on Android and iOS smartphones.
Secure passwords: Trend Micro Password Manager allows users to securely save and recall strong, unique passwords across numerous devices for all of their apps, websites, and online accounts.
You, the remote worker, may help close the front door to ransomware by using these solutions to safeguard your work, devices, and company from data theft and ransomware encryption.
Source:https://cyber-security-information.blogspot.com/2021/08/ransom-from-home-how-to-close-cyber.html
0 notes
Text
Assignments Based On Cryptography Techniques
Assignments Based On Cryptography Techniques
The following are the three different Online Cryptography Techniques that a student must learn as part of the computer science course when they want to excel in cryptography concepts.
Public key cryptography - It explains the asymmetric encryption where there would be two key cryptosystems used to keep the connection secure between the sender and the receiver. If you are stuck in writing the assignment on this topic, you can seek our experts' help. https://www.allhomeworkassignments.com/ are available round the clock to offer you with the required help.
Secret key cryptography – This Online Cryptography Technique would make use of a single key. The sender will use this key while sending a message to the receiver, and the same key is shared with the recipient so that they can decode the message and read it. In this type of technique, there is only one key that is used for encryption and decryption. Many students get confused with this concept and look for help. Without taking stress on you, hire us. https://www.allhomeworkassignments.com/ have professionals who do extensive research in writing the assignment for you.
Hash function - The integrity of the message is checked using the hash function to ensure that a hacker does not compromise the data. It makes use of a particular length has to value over a key.
Get The Best Cryptography Assignment Help Online
Our https://www.programmingonlinehelp.com/ Programming Assignment Help experts provide affordable cryptography coursework help to global students. They ensure that students get excellent grades by adhering to the guidelines, deliver clean codes and provide well-commented solution.
Cryptography is used to hide data – to render data unintelligible through its transformation into an unreadable state - and to ensure that data has not been altered in transit. If you are stuck in writing the assignment on this topic, you can seek our https://www.programmingonlinehelp.com/ experts' help. It can also be used to ensure the authenticity of the data as well as the authenticity of the data source. Cryptography supports confidentiality, integrity and authenticity in cryptography homework help It does not support availability
Hire Cryptography Assignment Help Experts to Boost the Grades
Cryptography or cryptology is the training and investigation of strategies for secure correspondence within the sight of outsiders called enemies. Cryptography is related with the way toward changing over normal plain content into garbled content and the other way around. It is a technique for putting away and transmitting information in a specific frame so those for whom it is proposed can read and process it. Cryptography Assignment Help shields information from burglary or alteration, as well as be utilized for client confirmation.
All the more, by and large, Online Cryptography Topics is tied in with building and investigating conventions that avert outsiders or the general population from reading private messages; different perspectives in data security, for example, information classification, information honesty, confirmation, and non-renouncement are key to present-day cryptography. Present-day cryptography exists at the crossing point of the controls of arithmetic, software engineering, electrical designing, correspondence science, and material science. Utilizations of Cryptography Assignment Help incorporate electronic trade, chip-based installment cards, computerized monetary standards, PC passwords, and military correspondences.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Text
Urgent C++ Programming Homework Help
Our company also provides some pleasant discounts. Our discount system is flexible and suits the budgets of ordinary clients. Our loyal clients and the newbies will surely save a lot of their earnings. Besides, they are fully secured. https://www.allhomeworkassignments.com/ compensate the full sum if we fail to complete your project as we’ve promised. Besides, you can return your project to rework it. This is done for free and we’ll fix all the drawbacks.
It’s remarkable that our specialists possess great knowledge and skills. Consequently, they may fulfill various functions. When you ask “do my C++ assignment”, it may be written, edited, quoted, researched, coded, encrypted, programmed, and something of the kind. Skilled specialists don’t simply solve issues related to programming. Academic papers should be written without mistakes and reveal your personal style. Therefore, they combine the gifts of writers and programmers to meet the demands of your teachers and professors.
Original and Safe C++ Assignment Help
One of the standard demands of every educational organization is to complete unique papers. When students turn to us, they commonly ask – Will you do my C++ homework uniquely? All Homework Assignments understand this necessity and guarantee that each project released by our specialists is 100% authentic. Firstly, we verify every assignment via a reliable plagiarism-checking application. It detects non-unique elements, which are instantly erased from the text.
Secondly, we write everything from scratch. Our specialists know how to craft a unique project according to any writing format. All the quotations and references will be correct. You won’t be deprived of important grades. One more crucial necessity we guarantee is the protection of your private data. It’s secured with an effective safeguard, which is regularly updated. Thus, it effectively withstands different kinds of cyber threats. Besides, we never share your private data with somebody else. When you require С plus plus homework help at https://www.allhomeworkassignments.com/ , we gather some facts about you. These facts are necessary to identify you in our system, deliver your orders, and make our connection faster and smoother. After our collaboration finishes, we delete these facts. Nobody will know about our collaboration.
Urgent C++ Programming Homework Help
Finally, we’d like to shed some light on the speed of work. https://www.allhomeworkassignments.com/ understands that your assignments are limited by time. Accordingly, we encourage our specialists to enhance their writing and time management skills. Our С plus plus assignment help is the fastest on the Internet because our writers know what strategy to choose to beat the shortest deadline.
Our methods of work are exceptional and fast. After you place your order, we analyze the demands. If they are realistic, we promise that your order will be accomplished before the deadline finishes. Some orders are finished in some 4 hours or faster. All Homework Assignments function 24 hours round the clock, which is another advantage for faster completion of your assignments. If you forget about your project or receive it all of a sudden, it’s not a problem. Visit us whenever the need appears and place an urgent order.
Mind that you can keep in touch with your personal assistant all the time long. Simply define the active chat hours to communicate. It’s very convenient. Choose the method of communication – cell phone or email. Afterward, you can get in touch with your assistant and learn the latest news about the progress of your project. Besides, we send regular notifications. If you require additional information, ask our supporting team. https://www.allhomeworkassignments.com/ professional company knows no limits for perfection. We gradually improve ourselves to always fit the demands of our clients. If you request help on our platform, you don’t risk anything. We guarantee your quick academic success.
#C++ Assignment Help#C++ Homework Help#C++ Project Help#C++ Experts Help#Do My C++ Assignment Help#Best C++ Programming Homework Help
0 notes
Video
youtube

writing my papers
About me
Pay Someone To Write My Research Paper
Pay Someone To Write My Research Paper Without the best school admission essay, an applicant may have no likelihood to enter the school of their dream. If you already study in a graduate college, you'll be able to order top-high quality scholarship essay to begin incomes monetary assist from your institution. Students are sometimes under strain due to the quite a few tutorial assignments. Psychology, philosophy, economics, nursing – so many subjects out there to cowl. At the same time, younger individuals produce other necessary things to do like fulfill their residence duties or work exhausting to earn money for college and lodging. It implies high quality, swift delivery, and full confidentiality. More than 96% or orders arrive on time or beforehand. Such a turnaround is maybe the most effective amongst all of the essay services so far. Using HTTPS and TLS applied sciences, we ensure all private information and payment information are encrypted and transferred by way of secure channels. Simply put, your experience with the positioning is protected and safe all the way through. Our further companies are designed to spice up your paper's high quality. You can select one or a number of additional companies on the order type. If you stay sad with what our writer has carried out, you could ask to revise the paper. We provide decrease prices for orders with a regular and extended deadline. For each new customer, we offer 15% off their first order. Use the promo code “first15” at the order page to activate the discount. Every writer responds to the client’s messages promptly in a lenient and cheerful trend. Our aim is to be sure to get the exact sort of paper you initially wished! It’s completely free of cost irrespective of how many revisions are required to polish your essay. Our greatest college writing service presents greater than writing from scratch. Another service is paraphrasing or rewriting – the one aimed to fully change some textual content to make it one hundred% authentic with out dropping the primary level. It’s beneficial that you check whether the actual service you want to rent is legit and dependable. If you rent the primary firm you come throughout online with out discovering any details about it, then it may not be secure. ” Goes without saying – the service is totally anonymous. Neither tutors nor instructional authorities in your nation get any information about our clients. Our specialists can also proofread your draft or provide enhancing earlier than you submit it to your teacher to make sure the premium quality of your work. Also, one of the common reasons why college students fail their educational tasks is postponing homework to the final minute. Some younger individuals have one other downside – they're just on the point of apply for school or university, and it presents sure challenges as well. the price was okay considering the urgency of my order. Keep a hand on the heart beat of the writing process. Assign free revisions to make a paper even better. This define will act as a verify so that you know the way much time is allotted to every task. They delivered my paper on time, however the final paragraph didn’t really meet my requirements. they wrote my essay that was due in 10 hours and actually saved my life. Usually, it takes us four-5 working days to finish an assignment that corresponds to our normal package deal. If you want your paper to be delivered urgently, then you possibly can mention Write me an essay in less time, and we will accommodate you accordingly. Whenever a client asks us Do my essay for me utilizing dependable sources, we are saying Sure, why not ? This is as a result of our writers know the distinction between reliable and unreliable sources, and they'd never carry off materials from a random website. You can purchase customized papers being one hundred% sure it is accomplished based on standard necessities, your directions and strictly on time! We respect your deadlines, at all times able to walk the extra mile that will help you match in the schedule. To score seventy five% and above, we offer you an educational paper author with expertise, credentials, degree, and a powerful command of English. You want to provide yourself ample time to understand the subject earlier than you'll be able to even start the writing. Plan your paper from beginning to end earlier than you begin writing; most students often spend too much time either researching, writing or doing modifying. Creating a draft or an outline is essential as you essentially create a Work Breakdown Structure.
0 notes
Video
youtube

college paper
About me
Buy A Research Paper > Buying Research Papers Online
Buy A Research Paper > Buying Research Papers Online That is how we customize your research paper for you. We have an solely anonymous method of ordering the papers inside our writing services. Order-papers.com doesn't expose or reveal any of our shoppers’ data. My first analysis paper in school was fairly a challenge to me. Every author has a possibility to boost their own writing skills via programs and corporate coaching. Be sure we appoint the most effective writers to fit your tutorial wants. Essay writers of our company have helped college students all around the world. This ought to let you try out our essay writers service with a highly lowered quote. And when it does, you need to know of an essay writing service that can write everything you need at that second. Whether it's a small essay task, a piece of homework, or a sophisticated thesis, you’ll want instant assistance from a reliable source. Plagiarism is available in many forms, however the basic definition is claiming credit score for work that is not your personal. The punishment for plagiarism is different from place to position, however each college or highschool ought to have an honor code to deal with academic crime.2. Different cultures made our staff artistic thinking and we strive so that each one the subjects were to obligatory implementation. Our purchasers typically have ideas or matters – we are able to make them perfect trying and sound! Using sources of authoritative information will make your work distinctive and strongly argumentative. Our clients’ belief is everything to us, therefore each transaction is strictly confidential. With system checks carried out every day and 256-bit data encryption, all customers, who purchase essay papers online, can count on confidentiality to be maintained always. Of course, the website that gives great papers will declare the work is authentic and reliable. The sources could possibly be pretend, the research might be sloppy, and the format will not match the project. I’ve referred to EssayPay service several instances, once with a enterprise-associated task after which with a long essay. Each time the professionally written papers gained the highest grades from my professor. We additionally warrant nondisclosure of your private information to third parties if you buy essay papers. Sure, you're worried that the requested content would possibly come of poor quality. To stop this from happening, we let solely professionals work on the orders. Candidates for writers’ positions bear a four-degree choice process to confirm their experience within the required discipline subject and writing abilities. Our essay writing firm cooperates with main monetary service suppliers, acknowledged all internationally. Use any protected choice to buy your article on-line. Such questions are higher answered by our firm. We have a big and well staffed quality assurance division, the editors and the Masters guy can by no means let an error pass them. If you flip in a paper that you just didn't write, there shall be plenty of issues about that paper to tip off your teacher. The tone and the research won't match your past work. Don't try to outsmart someone who went to varsity for eight or ten years! It is nicely checked and adjusted as per your instructions. you need to wear it and guarantee it's customized trimmed to your shoulder. Our rates are created to fit any student’s finances. When you first determine on our essay writers, we'll grant you with a hefty 15% discount. We recruit solely skilled writers with an educational degree and an excellent command of writing. All candidates are accepted on the basis of written tests.
0 notes
Text
Cryptography Assignment Online Help
There are many encryption and decryption algorithms that are involved in cryptography. Thus making it difficult for students to complete the assignment correctly on time. We https://www.allhomeworkassignments.com/ help students with their cryptography assignments, homework and projects, so that they can focus on what is more important. The coding structure in cryptography is highly challenging for the first-year students to understand. It needs a lot of practice to get hold of the subject. If the student does not understand the subject and writes the Online Cryptography Assignment, it results in poor grades. If you do not want to put your valuable grades at stake, then you must hire us. https://www.allhomeworkassignments.com/ provide instant and affordable Cryptography Homework Help services.
Data Projection Techniques – Cryptography Assignment
Various techniques are used to protect the data using cryptography and most of the university Online Cryptography Assignments are based on this concept only. Here are a few uses of it
Authentication - These include – message authentication, and the other is the entity authentication. It is never easy for a student to develop an algorithm that secures the data. The algorithms and various cryptography aspects would create a lot of confusion. Whenever you need help in writing a cryptography assignment, get in touch with https://www.allhomeworkassignments.com/ . There are symmetric and asymmetric algorithms that a student should know and the basics of encryption and decryption. When there is a single bug in the code, it takes a toll on the whole security algorithm.
Data integrity - If any changes are made to the change, it is simple for the security service to detect and track those changes. The data integrity provided by https://www.programmingonlinehelp.com/ will ensure that the data that is created by the sender is the same as the one that is sent to the receiver. This ensures that there is no tampering happening amidst. If any unauthorized person has tweaked the data, the security service provided by https://www.programmingonlinehelp.com/ will detect it immediately. However, it cannot stop the person from changing the data, but it can detect when someone tries to mess it up.
Non-repudiation - This type of service of https://www.programmingonlinehelp.com/ in cryptography will ensure that the two parties involved in the data transmission cannot deny that they have committed to the information. The entity cannot deny sending the information to the third parties. For instance, when a person has made a purchase, then he/she cannot deny that the order has not made by them.
#Cryptography Assignment Help#Cryptography Homework Help#Online Cryptography Assignment Help#Best Cryptography Assignment Help#Do My Cryptography Assignment Help
0 notes
Video
youtube

cheap essay service
About me
Essay Writer Service
Essay Writer Service This will help you make sure that the author is following the required instructions. The drafts will also assist to gauge if the final paper will get accomplished on time. Alternatively, the writer should be reachable and obtainable at any time so that you can examine the progress of the analysis work. One of the important thing principles of our work is to be creative and authentic. We rent only gifted and experienced essay writers which are capable of create authentic papers. Each regular essay or term paper is written from scratch in accordance with all of your tips. Let our service be your reliable helper and feel all the benefits today. ” The reply is a resounding “Yes.” The papers we provide function examples of wonderful tutorial writing and can be utilized to improve one’s writing skills. Customers who get assist with writing papers are discouraged from passing them as their own. As such, hiring one of the best paper writing helper by way of this web site is totally legal. Starting from only $10/page, our provide is a cut price. The online delivery obviates considerable overhead and administrative expenses, thereby making our services extremely inexpensive. In addition to sparing your wallet, our paper help writing additionally allows you to save time. In addition to forgoing the non-public data requests, we utilize several legal and dependable methods to make sure your privacy can't be compromised. For occasion, all communication between you and a paper helper is secured via layered encryption and firewalls. It means no one can discover out the main points of your essay order. Therefore, this privacy-centered service is the safest place to get custom paper writing assist online. We write samples and examples of essays, reports, reviews, articles, case research, and different school assignments. Our vast galaxy of academic solutions also includes enhancing and proofreading. Compare and contrast essays are characterized by a basis for comparability, factors of comparability, and analogies. All you need is to provide us detailed directions to help our consultants understand the duty. Now it’s potential to write a e-book review or a literature essay with out reading a book. Our prime writers will make all needed adjustments at no cost so as to make your work flawless. Our writers maintain all your necessities in view and compose the papers from scratch leaving no house for plagiarism. We take satisfaction in helping hundreds of scholars with attaining a high-grade on their assignments. The comparability highlights the similarities between two or more related objects while contrasting highlights the differences between two or extra objects. company will offer a assure to finish your assignments before the deadline. In case they fail to ship as promised, you must get a refund. You should choose a company that also delivers excessive-high quality work so that you're not pressured to increase the time for revisions. If you have a very lengthy or difficult paper, it might be good to ask for drafts. Order a custom-written paper from professional writers on our web site. With EssayShark you can do all of the homework assignments in a single place. Manage your orders in a private account, chat with writers immediately using a constructed-in chat, and get completely-written papers inside a number of clicks. A good tip is to choose a ultimate deadline, which is a couple of hours or days early so that you've additional time in case a difficulty arises. Many students should face academic challenges alone. For them, access to high-high quality writing assistance is prohibitively costly. But they don’t need to be alone within the struggle when evolution writers are just a few keystrokes away. All the evaluations are posted on respected third celebration platforms for which we're offering the links to you. During the course, the teacher might assign numerous forms of homework. Along with essays, our specialists can prepare a presentation, speech, case study, research paper, dissertation, and more. Our writers department can deal with any assignment of any complexity easily.
0 notes
Video
youtube

paper writers
About me
Essay Writing Service Papernow It'S Only What You Need
Essay Writing Service Papernow It'S Only What You Need Feel free to ask them any questions about your paper at any time. Your writer will reply to you as quickly as possible. If you have already written your paper however want one other pair of eyes to look at it, try our enhancing service. A professional educational editor will go over your paper and master it to absolute perfection. We will ask you to share solely your essay paper instructions and contact particulars with us. Your paper will stand out from the remainder of the works submitted by peers thanks to a high writing high quality and fascinating content material, topic-savvy content. If yours isn’t on the record on the order page, then select “Other.” In flip, we’ll match you with a subject-relevant essay author who’ll be able to help with your homework project. Our penmen are the most effective within the business, understanding the way to extinguish burning deadlines and research in-depth, mind-boggling topics. Grateful he put up with my breakdowns and wrote A PERFECT time period paper after all. When shopping for inexpensive papers from us, you can select some additional unique options to make your experience with us even higher. Such a pity I haven’t discovered this service earlier – could have saved a lot time, vitality and nerves. I was a whole management freak, texting my author 5 occasions a day, making a lot of fuss around my order. This data, in addition to your chats with the assigned paper author, might be secured with SSL Data Encryption. I used to be afraid of online writing firms. You know… What if somebody finds out or what in the event that they turn out to be cheaters. We provide college students with genuine papers that are one-of-a-type and have no doubles. It’s at all times a good suggestion to inquire about your future author. The most necessary thing is that Grade Miners are real human writers with the required expertise and writing experience. Our writers can full a regular essay for you within 1-3 hours and part of a dissertation – in 2-5 days. Hire a proficient online essay writer in lower than a minute and neglect a couple of composition until it’s delivered to your Customer space on our web site. Authentic texts assure that there’s no cheating involved, while your tutorial integrity stays sturdy. Re-selling or rewriting old papers has nothing to do with Grade Miners. Among such extras is an Abstract page that shortly sums up the paper’s primary ideas. Besides, we can provide you with a plagiarism report to prove your project’s complete uniqueness. You also can order an outline, reference list, and table of contents. If charts or diagrams are required, ask your author to add such supplies to your paper. Those prospects who're super demanded can make certain their project is perfect when it comes to grammar and spelling by ordering additional proofreading. We know that it's typically difficult to choose an creator for your paper. Because of this, we attempt to make such a alternative simpler for you. We have loads of excellent options that will help you make the right choice. If you might be on the lookout for expert and skilled writers who know what they do, you should look no extra. Grade Miners will take excellent care of your essays and research papers, while you’re having fun with your day. , you'll be able to message the assigned writer directly utilizing useful and secure chat board.
0 notes
Video
youtube

paper writer
About me
Paper Checker
Paper Checker The writer are polite and professional and it’s nice to have somebody able to reply all my questions 24/7 in chat. Sometimes, students face difficulties even after they hand in their research paper or essay to the instructor. Because teachers have too strict requirements and expectations for written homework. As for plagiarism, we essentially examine each paper for authenticity with the assistance of particular programs. The service deals only with highly qualified experts with big experience and impeccable status. All our authors move checks for language competence and tutorial aptitude. Their great outcomes and deep understanding of college academic fields allow them to create good piece of writing on a brief notice. You may chat with your private writer on-line to specify some additional nuances or correcting the work process. Use the customer dashboard out there after order submission. We provide samples of educational writing, which you should use to improve your skills. After all, even professors often provide sample papers that can assist you better understand what ought to be done. While in search of some samples online, I stumbled by this web site and have been a daily customer ever since. Then you should fill out your cost particulars via our safe cost system, and you’re set! One of our analysis paper writers will start on the project instantly. Our writing group is crammed with consultants on every topic. Regardless of which type of research paper you want, we can put the right particular person on the job. We take our time with the work and review it multiple instances for proper answers. We will deliver your papers on time and even earlier than the requested date. We know that professors do not recognize a late project. Using HTTPS and TLS applied sciences, we ensure all personal information and cost info are encrypted and transferred via safe channels. Simply put, your experience with the positioning is protected and safe throughout. I’ve ordered 5 or 6 times before, and the work has at all times been qualitative. As a high school or school pupil, it’s often onerous to keep away from the stress in your life, but you can reduce it due to our dependable writing service. Don’t sweat over dangerous grades or missed deadlines - allow us to help and find out what it’s like to truly take pleasure in your instructional journey. The complete value will appear at the backside of the web page. Even if we get two equivalent orders, we conduct researches in different ways. We use numerous literary sources and write each work differently. This signifies that every copy is original and by no means resembles another document with the identical subject material. ” Goes with out saying – the service is completely nameless. Neither tutors nor educational authorities in your country get any details about our clients. As it has been stated before, you can chat directly along with your personal author, at any time, give any details, suggestion or notes. 1ws.com provides exceptionally an individual approach towards your inquiry. Meet your personal author on-line, the person who will craft your essay until it's excellent. So, you possibly can relaxation assured that you'll get the paper on time. Our help team operates 24/7 on your total convenience.
0 notes