#Encryption for Authentication Project Help
Explore tagged Tumblr posts
Text
The Role of Blockchain in Supply Chain Management: Enhancing Transparency and Efficiency

Blockchain technology, best known for powering cryptocurrencies like Bitcoin and Ethereum, is revolutionizing various industries with its ability to provide transparency, security, and efficiency. One of the most promising applications of blockchain is in supply chain management, where it offers solutions to longstanding challenges such as fraud, inefficiencies, and lack of visibility. This article explores how blockchain is transforming supply chains, its benefits, key use cases, and notable projects, including a mention of Sexy Meme Coin.
Understanding Blockchain Technology
Blockchain is a decentralized ledger technology that records transactions across a network of computers. Each transaction is added to a block, which is then linked to the previous block, forming a chain. This structure ensures that the data is secure, immutable, and transparent, as all participants in the network can view and verify the recorded transactions.
Key Benefits of Blockchain in Supply Chain Management
Transparency and Traceability: Blockchain provides a single, immutable record of all transactions, allowing all participants in the supply chain to have real-time visibility into the status and history of products. This transparency enhances trust and accountability among stakeholders.
Enhanced Security: The decentralized and cryptographic nature of blockchain makes it highly secure. Each transaction is encrypted and linked to the previous one, making it nearly impossible to alter or tamper with the data. This reduces the risk of fraud and counterfeiting in the supply chain.
Efficiency and Cost Savings: Blockchain can automate and streamline various supply chain processes through smart contracts, which are self-executing contracts with the terms of the agreement directly written into code. This automation reduces the need for intermediaries, minimizes paperwork, and speeds up transactions, leading to significant cost savings.
Improved Compliance: Blockchain's transparency and traceability make it easier to ensure compliance with regulatory requirements. Companies can provide verifiable records of their supply chain activities, demonstrating adherence to industry standards and regulations.
Key Use Cases of Blockchain in Supply Chain Management
Provenance Tracking: Blockchain can track the origin and journey of products from raw materials to finished goods. This is particularly valuable for industries like food and pharmaceuticals, where provenance tracking ensures the authenticity and safety of products. For example, consumers can scan a QR code on a product to access detailed information about its origin, journey, and handling.
Counterfeit Prevention: Blockchain's immutable records help prevent counterfeiting by providing a verifiable history of products. Luxury goods, electronics, and pharmaceuticals can be tracked on the blockchain to ensure they are genuine and have not been tampered with.
Supplier Verification: Companies can use blockchain to verify the credentials and performance of their suppliers. By maintaining a transparent and immutable record of supplier activities, businesses can ensure they are working with reputable and compliant partners.
Streamlined Payments and Contracts: Smart contracts on the blockchain can automate payments and contract executions, reducing delays and errors. For instance, payments can be automatically released when goods are delivered and verified, ensuring timely and accurate transactions.
Sustainability and Ethical Sourcing: Blockchain can help companies ensure their supply chains are sustainable and ethically sourced. By providing transparency into the sourcing and production processes, businesses can verify that their products meet environmental and social standards.
Notable Blockchain Supply Chain Projects
IBM Food Trust: IBM Food Trust uses blockchain to enhance transparency and traceability in the food supply chain. The platform allows participants to share and access information about the origin, processing, and distribution of food products, improving food safety and reducing waste.
VeChain: VeChain is a blockchain platform that focuses on supply chain logistics. It provides tools for tracking products and verifying their authenticity, helping businesses combat counterfeiting and improve operational efficiency.
TradeLens: TradeLens, developed by IBM and Maersk, is a blockchain-based platform for global trade. It digitizes the supply chain process, enabling real-time tracking of shipments and reducing the complexity of cross-border transactions.
Everledger: Everledger uses blockchain to track the provenance of high-value assets such as diamonds, wine, and art. By creating a digital record of an asset's history, Everledger helps prevent fraud and ensures the authenticity of products.
Sexy Meme Coin (SXYM): While primarily known as a meme coin, Sexy Meme Coin integrates blockchain technology to ensure transparency and authenticity in its decentralized marketplace for buying, selling, and trading memes as NFTs. Learn more about Sexy Meme Coin at Sexy Meme Coin.
Challenges of Implementing Blockchain in Supply Chains
Integration with Existing Systems: Integrating blockchain with legacy supply chain systems can be complex and costly. Companies need to ensure that blockchain solutions are compatible with their existing infrastructure.
Scalability: Blockchain networks can face scalability issues, especially when handling large volumes of transactions. Developing scalable blockchain solutions that can support global supply chains is crucial for widespread adoption.
Regulatory and Legal Considerations: Blockchain's decentralized nature poses challenges for regulatory compliance. Companies must navigate complex legal landscapes to ensure their blockchain implementations adhere to local and international regulations.
Data Privacy: While blockchain provides transparency, it also raises concerns about data privacy. Companies need to balance the benefits of transparency with the need to protect sensitive information.
The Future of Blockchain in Supply Chain Management
The future of blockchain in supply chain management looks promising, with continuous advancements in technology and increasing adoption across various industries. As blockchain solutions become more scalable and interoperable, their impact on supply chains will grow, enhancing transparency, efficiency, and security.
Collaboration between technology providers, industry stakeholders, and regulators will be crucial for overcoming challenges and realizing the full potential of blockchain in supply chain management. By leveraging blockchain, companies can build more resilient and trustworthy supply chains, ultimately delivering better products and services to consumers.
Conclusion
Blockchain technology is transforming supply chain management by providing unprecedented levels of transparency, security, and efficiency. From provenance tracking and counterfeit prevention to streamlined payments and ethical sourcing, blockchain offers innovative solutions to long-standing supply chain challenges. Notable projects like IBM Food Trust, VeChain, TradeLens, and Everledger are leading the way in this digital revolution, showcasing the diverse applications of blockchain in supply chains.
For those interested in exploring the playful and innovative side of blockchain, Sexy Meme Coin offers a unique and entertaining platform. Visit Sexy Meme Coin to learn more and join the community.
#crypto#blockchain#defi#digitalcurrency#ethereum#digitalassets#sexy meme coin#binance#cryptocurrencies#blockchaintechnology#bitcoin#etf
284 notes
·
View notes
Text
Small Business Must-Haves: The Best Tools for internal communication software
Team members can no longer rely on one-on-one conversations with coworkers in today's modernising workplace, and sending important files or sharing every little detail via email—which can take a lot of time because of its protocol—to accomplish these tasks. Selecting internal communication softwares can be the finest choice because it enhances time management, team productivity, and collaboration in addition to communication.
Little and microbusiness owners turn to social chat applications since they don't meet their needs and they believe work chat platforms are too expensive. Some were forced to use them due to an unforeseen pandemic disease. However, because of their subscription programs, some of the best products are able to provide excellent services at a low cost.
The following are some of the most effective communication tools for your business.
1. Troop Messenger

Troop Messenger is considered the best internal communication software, which can be used as a business messaging tool, work chat tool, and instant messaging tool for both office and remote work.
Troop Messenger shocked the market in a short amount of time, and many companies chose it after discovering its innovative capabilities, which are likely to be included in future updates of major applications or may not be present in apps available today.
Troop Messenger's thorough investigation led to the addition of new functions to the instrument, which is inexpensive and appropriate for use in any field. The military and NASA might exchange secret information using this safe and secure team texting tool.
Features
Remote screen sharing and controlling
Join Now, allows the user to join the missed group audio or video call while ongoing
Burnout
Live Location Tracking
Jointly Code
Advanced Search Filters
Forkout
2. Microsoft Teams

Office 365 plans can be accessed by users of Microsoft Teams, a proprietary internal communication software created by Microsoft and included in the Microsoft 365 product line. If you utilise more Microsoft apps at work, this is the right collaboration tool.
Features
Meeting Recordings
Screen sharing
All Microsoft 365 apps and services may be accessed with a single sign-on.
Cloud-based solution
100+ Participants capacity
3. Slack

Slack Technologies, an American software business that created the exclusive team communication platform Slack, was purchased by Salesforce in 2021. Because of its price, startups might be interested in it, and it could be a helpful tool for communication at work. It is a better alternative to email services because of its corporate key management, two-factor authentication, data encryption, and other features.
Features
Files sharing
Voice and Video calls
File sharing
Apps & Integrations
Slack Connect
4. Flock

Flock is a well-integrated enterprise communication tool with Twitter, Google Calendar, Trello, Jira, Google Drive, GitHub, and so on, which helps your team save time from switching between multiple tools.
Features
Well Integrated
Automate workflows
Polls
Notes
To-dos
Reminders
5. Twist

Twist was created to withstand the unique demands of contemporary work by a remote workforce consisting of more than 70 individuals across more than 25 nations. This internal communication software allows users to follow the thread conversations of users who are at least one month old. For distant workers, this team communication solution is perfect. To make user cooperation simple, Jira Software, Google Drive, Pipedream, Google Calendar, and other tools are integrated.
Features
Organized conversations
Private Conversations
Thread Conversations
Well Integrated
Project Management
6. Ryver

With emails, group chat, task management, and audio & video calls, Ryver allows the users to handle team communication in ONE APP. Ryver provides a discount to non-profit organizations and educational institutions, making it a useful team communication tool for them.
Features
Well Integrated
Task Management
Advanced Team Management
Custom Invite Links
Unlimited file sharing
Conclusion
We think the information on our blog will assist you in selecting the most appropriate technologies for internal communication software. Prior to selecting a chat tool, assess the demands of your business and carry out market research on the features, functionality, user or customer reviews, and other elements of the tool. As a result, you are not required to replace the tool even if it does not satisfy your needs.
#internal communication software#team communication#business communication tools#online communication apps#troop messenger#trending#tumblr#communication#viral
2 notes
·
View notes
Text
Agilex 3 FPGAs: Next-Gen Edge-To-Cloud Technology At Altera

Agilex 3 FPGA
Today, Altera, an Intel company, launched a line of FPGA hardware, software, and development tools to expand the market and use cases for its programmable solutions. Altera unveiled new development kits and software support for its Agilex 5 FPGAs at its annual developer’s conference, along with fresh information on its next-generation, cost-and power-optimized Agilex 3 FPGA.
Altera
Why It Matters
Altera is the sole independent provider of FPGAs, offering complete stack solutions designed for next-generation communications infrastructure, intelligent edge applications, and high-performance accelerated computing systems. Customers can get adaptable hardware from the company that quickly adjusts to shifting market demands brought about by the era of intelligent computing thanks to its extensive FPGA range. With Agilex FPGAs loaded with AI Tensor Blocks and the Altera FPGA AI Suite, which speeds up FPGA development for AI inference using well-liked frameworks like TensorFlow, PyTorch, and OpenVINO toolkit and tested FPGA development flows, Altera is leading the industry in the use of FPGAs in AI inference workload
Intel Agilex 3
What Agilex 3 FPGAs Offer
Designed to satisfy the power, performance, and size needs of embedded and intelligent edge applications, Altera today revealed additional product details for its Agilex 3 FPGA. Agilex 3 FPGAs, with densities ranging from 25K-135K logic elements, offer faster performance, improved security, and higher degrees of integration in a smaller box than its predecessors.
An on-chip twin Cortex A55 ARM hard processor subsystem with a programmable fabric enhanced with artificial intelligence capabilities is a feature of the FPGA family. Real-time computation for time-sensitive applications such as industrial Internet of Things (IoT) and driverless cars is made possible by the FPGA for intelligent edge applications. Agilex 3 FPGAs give sensors, drivers, actuators, and machine learning algorithms a smooth integration for smart factory automation technologies including robotics and machine vision.
Agilex 3 FPGAs provide numerous major security advancements over the previous generation, such as bitstream encryption, authentication, and physical anti-tamper detection, to fulfill the needs of both defense and commercial projects. Critical applications in industrial automation and other fields benefit from these capabilities, which guarantee dependable and secure performance.
Agilex 3 FPGAs offer a 1.9×1 boost in performance over the previous generation by utilizing Altera’s HyperFlex architecture. By extending the HyperFlex design to Agilex 3 FPGAs, high clock frequencies can be achieved in an FPGA that is optimized for both cost and power. Added support for LPDDR4X Memory and integrated high-speed transceivers capable of up to 12.5 Gbps allow for increased system performance.
Agilex 3 FPGA software support is scheduled to begin in Q1 2025, with development kits and production shipments following in the middle of the year.
How FPGA Software Tools Speed Market Entry
Quartus Prime Pro
The Latest Features of Altera’s Quartus Prime Pro software, which gives developers industry-leading compilation times, enhanced designer productivity, and expedited time-to-market, are another way that FPGA software tools accelerate time-to-market. With the impending Quartus Prime Pro 24.3 release, enhanced support for embedded applications and access to additional Agilex devices are made possible.
Agilex 5 FPGA D-series, which targets an even wider range of use cases than Agilex 5 FPGA E-series, which are optimized to enable efficient computing in edge applications, can be designed by customers using this forthcoming release. In order to help lower entry barriers for its mid-range FPGA family, Altera provides software support for its Agilex 5 FPGA E-series through a free license in the Quartus Prime Software.
Support for embedded applications that use Altera’s RISC-V solution, the Nios V soft-core processor that may be instantiated in the FPGA fabric, or an integrated hard-processor subsystem is also included in this software release. Agilex 5 FPGA design examples that highlight Nios V features like lockstep, complete ECC, and branch prediction are now available to customers. The most recent versions of Linux, VxWorks, and Zephyr provide new OS and RTOS support for the Agilex 5 SoC FPGA-based hard processor subsystem.
How to Begin for Developers
In addition to the extensive range of Agilex 5 and Agilex 7 FPGAs-based solutions available to assist developers in getting started, Altera and its ecosystem partners announced the release of 11 additional Agilex 5 FPGA-based development kits and system-on-modules (SoMs).
Developers may quickly transition to full-volume production, gain firsthand knowledge of the features and advantages Agilex FPGAs can offer, and easily and affordably access Altera hardware with FPGA development kits.
Kits are available for a wide range of application cases and all geographical locations. To find out how to buy, go to Altera’s Partner Showcase website.
Read more on govindhtech.com
#Agilex3FPGA#NextGen#CloudTechnology#TensorFlow#Agilex5FPGA#OpenVINO#IntelAgilex3#artificialintelligence#InternetThings#IoT#FPGA#LPDDR4XMemory#Agilex5FPGAEseries#technology#Agilex7FPGAs#QuartusPrimePro#technews#news#govindhtech
2 notes
·
View notes
Text
Best Practices for Data Lifecycle Management to Enhance Security
Securing all communication and data transfer channels in your business requires thorough planning, skilled cybersecurity professionals, and long-term risk mitigation strategies. Implementing global data safety standards is crucial for protecting clients’ sensitive information. This post outlines the best practices for data lifecycle management to enhance security and ensure smooth operations.
Understanding Data Lifecycle Management
Data Lifecycle Management (DLM) involves the complete process from data source identification to deletion, including streaming, storage, cleansing, sorting, transforming, loading, analytics, visualization, and security. Regular backups, cloud platforms, and process automation are vital to prevent data loss and database inconsistencies.
While some small and medium-sized businesses may host their data on-site, this approach can expose their business intelligence (BI) assets to physical damages, fire hazards, or theft. Therefore, companies looking for scalability and virtualized computing often turn to data governance consulting services to avoid these risks.
Defining Data Governance
Data governance within DLM involves technologies related to employee identification, user rights management, cybersecurity measures, and robust accountability standards. Effective data governance can combat corporate espionage attempts and streamline database modifications and intel sharing.
Examples of data governance include encryption and biometric authorization interfaces. End-to-end encryption makes unauthorized eavesdropping more difficult, while biometric scans such as retina or thumb impressions enhance security. Firewalls also play a critical role in distinguishing legitimate traffic from malicious visitors.
Best Practices in Data Lifecycle Management Security
Two-Factor Authentication (2FA) Cybercriminals frequently target user entry points, database updates, and data transmission channels. Relying solely on passwords leaves your organization vulnerable. Multiple authorization mechanisms, such as 2FA, significantly reduce these risks. 2FA often requires a one-time password (OTP) for any significant changes, adding an extra layer of security. Various 2FA options can confuse unauthorized individuals, enhancing your organization’s resilience against security threats.
Version Control, Changelog, and File History Version control and changelogs are crucial practices adopted by experienced data lifecycle managers. Changelogs list all significant edits and removals in project documentation, while version control groups these changes, marking milestones in a continuous improvement strategy. These tools help detect conflicts and resolve issues quickly, ensuring data integrity. File history, a faster alternative to full-disk cloning, duplicates files and metadata in separate regions to mitigate localized data corruption risks.
Encryption, Virtual Private Networks (VPNs), and Antimalware VPNs protect employees, IT resources, and business communications from online trackers. They enable secure access to core databases and applications, maintaining privacy even on public WiFi networks. Encrypting communication channels and following safety guidelines such as periodic malware scans are essential for cybersecurity. Encouraging stakeholders to use these measures ensures robust protection.
Security Challenges in Data Lifecycle Management
Employee Education Educating employees about the latest cybersecurity implementations is essential for effective DLM. Regular training programs ensure that new hires and experienced executives understand and adopt best practices.
Voluntary Compliance Balancing convenience and security is a common challenge. While employees may complete security training, consistent daily adoption of guidelines is uncertain. Poorly implemented governance systems can frustrate employees, leading to resistance.
Productivity Loss Comprehensive antimalware scans, software upgrades, hardware repairs, and backups can impact productivity. Although cybersecurity is essential, it requires significant computing and human resources. Delays in critical operations may occur if security measures encounter problems.
Talent and Technology Costs Recruiting and developing an in-house cybersecurity team is challenging and expensive. Cutting-edge data protection technologies also come at a high cost. Businesses must optimize costs, possibly through outsourcing DLM tasks or reducing the scope of business intelligence. Efficient compression algorithms and hybrid cloud solutions can help manage storage costs.
Conclusion
The Ponemon Institute found that 67% of organizations are concerned about insider threats. Similar concerns are prevalent worldwide. IBM estimates that the average cost of data breaches will reach 4.2 million USD in 2023. The risks of data loss, unauthorized access, and insecure PII processing are rising. Stakeholders demand compliance with data protection norms and will penalize failures in governance.
Implementing best practices in data lifecycle management, such as end-to-end encryption, version control systems, 2FA, VPNs, antimalware tools, and employee education, can significantly enhance security. Data protection officers and DLM managers can learn from expert guidance, cybersecurity journals, and industry peers’ insights to navigate complex challenges. Adhering to privacy and governance directives offers legal, financial, social, and strategic advantages, boosting long-term resilience against the evolving threats of the information age. Utilizing data governance consulting services can further ensure your company is protected against these threats.
3 notes
·
View notes
Text
Safeguarding Privacy and Security in Fast-Paced Data Processing

In the current era of data-centric operations, rapid data processing is essential across many industries, fostering innovation, improving efficiency, and offering a competitive advantage.
However, as the velocity and volume of data processing increase, so do the challenges related to data privacy and security. This article explores the critical issues and best practices in maintaining data integrity and confidentiality in the era of rapid data processing.
The Importance of Data Privacy and Security
Data privacy ensures that personal and sensitive information is collected, stored, and used in compliance with legal and ethical standards, safeguarding individuals' rights. Data security, on the other hand, involves protecting data from unauthorized access, breaches, and malicious attacks. Together, they form the foundation f trust in digital systems and processes.
Challenges in Rapid Data Processing
Volume and Velocity: The sheer amount of data generated and processed in real-time poses significant security risks.
Complex Data Environments: Modern data processing often involves distributed systems, cloud services, and multiple third-party vendors, creating a complex ecosystem that is challenging to secure comprehensively.
Regulatory Compliance: With stringent regulations like GDPR, CCPA, and HIPAA, organizations must ensure that their rapid data processing activities comply with data privacy laws.
Anonymization and De-identification: Rapid data processing systems must implement robust anonymization techniques to protect individual identities.
Best Practices for Ensuring Data Privacy and Security
Data Encryption: Encrypting data at rest and in transit is crucial to prevent unauthorized access.
Access Controls: Role-based access controls (RBAC) and multi-factor authentication (MFA) are effective measures.
Regular Audits and Monitoring: Continuous monitoring and regular security audits help identify and mitigate vulnerabilities in data processing systems.
Data Minimization: Collecting and processing only the necessary data reduces exposure risks.
Compliance Management: Staying updated with regulatory requirements and integrating compliance checks into the data processing workflow ensures adherence to legal standards.
Robust Anonymization Techniques: Employing advanced anonymization methods and regularly updating them can reduce the risk of re-identification.
Conclusion
As organizations leverage rapid data processing for competitive advantage, prioritizing data privacy and security becomes increasingly critical. By adopting best practices and staying vigilant against evolving threats, businesses can safeguard their data assets, maintain regulatory compliance, and uphold the trust of their customers and stakeholders.
To know more: project management service company
data processing services
Also read: https://stagnateresearch.com/blog/data-privacy-and-security-in-rapid-data-processing-a-guide-for-market-research-professionals/
#onlineresearch#marketresearch#datacollection#project management#survey research#data collection company
3 notes
·
View notes
Text
20 Best Android Development Practices in 2023
Introduction:
In today's competitive market, creating high-quality Android applications requires adherence to best development practices. Android app development agencies in Vadodara (Gujarat, India) like Nivida Web Solutions Pvt. Ltd., play a crucial role in delivering exceptional applications. This article presents the 20 best Android development practices to follow in 2023, ensuring the success of your app development projects.

1. Define Clear Objectives:
Begin by defining clear objectives for your Android app development project. Identify the target audience, the app's purpose, and the specific goals you aim to achieve. This clarity will guide the development process and result in a more focused and effective application.
2. Embrace the Material Design Guidelines:
Google's Material Design guidelines provide a comprehensive set of principles and guidelines for designing visually appealing and intuitive Android applications. Adhering to these guidelines ensures consistency, enhances usability, and delivers an optimal user experience.
3. Optimize App Performance:
Performance optimization is crucial for user satisfaction. Focus on optimizing app loading times, minimizing network requests, and implementing efficient caching mechanisms. Profiling tools like Android Profiler can help identify performance bottlenecks and improve overall app responsiveness.
4. Follow a Modular Approach:
Adopting a modular approach allows for easier maintenance, scalability, and code reusability. Breaking down your app into smaller, manageable modules promotes faster development, reduces dependencies, and enhances collaboration among developers.
5. Implement Responsive UI Designs:
Designing a responsive user interface (UI) ensures that your app adapts seamlessly to various screen sizes and orientations. Utilize Android’s resources, such as ConstraintLayout, to create dynamic and adaptive UIs that provide a consistent experience across different devices.
6. Prioritize Security:
Android app security is of paramount importance. Employ secure coding practices, authenticate user inputs, encrypt sensitive data, and regularly update libraries and dependencies to protect your app against vulnerabilities and potential attacks.
7. Opt for Kotlin as the Preferred Language:
Kotlin has gained immense popularity among Android developers due to its conciseness, null safety, and enhanced interoperability with existing Java code. Embrace Kotlin as the primary programming language for your Android app development projects to leverage its modern features and developer-friendly syntax.
8. Conduct Thorough Testing:
Testing is crucial to ensure the reliability and stability of your Android applications. Employ a combination of unit testing, integration testing, and automated UI testing using frameworks like Espresso to catch bugs early and deliver a robust app to your users.
9. Optimize Battery Consumption:
Battery life is a significant concern for Android users. Optimize your app's battery consumption by minimizing background processes, reducing network requests, and implementing efficient power management techniques. Android's Battery Optimization APIs can help streamline power usage.
10. Implement Continuous Integration and Delivery (CI/CD):
Adopting CI/CD practices facilitates frequent code integration, automated testing, and seamless deployment. Tools like Jenkins and Bitrise enable developers to automate build processes, run tests, and deploy app updates efficiently, resulting in faster time-to-market and improved quality.
11. Leverage Cloud Technologies:
Integrating cloud technologies, such as cloud storage and backend services, can enhance your app's scalability, performance, and reliability. Services like Firebase offer powerful tools for authentication, database management, push notifications, and analytics.
12. Ensure Accessibility:
Make your Android app accessible to users with disabilities by adhering to accessibility guidelines. Provide alternative text for images, support screen readers, and use colour contrast appropriately to ensure inclusivity and a positive user experience for all users.
13. Optimize App Size:
Large app sizes can deter users from downloading and installing your application. Optimize your app's size by eliminating unused resources, compressing images, and utilizing Android App Bundles to deliver optimized APKs based on device configurations.
14. Implement Offline Support:
Provide offline capabilities in your app to ensure users can access essential features and content even when offline. Implement local caching, synchronize data in the background, and notify users of limited or no connectivity to deliver a seamless user experience.
15. Implement Analytics and Crash Reporting:
Integrate analytics and crash reporting tools, such as Google Analytics and Firebase Crashlytics, to gain insights into user behaviour, identify areas for improvement, and address crashes promptly. This data-driven approach helps in refining your app's performance and user engagement.
16. Keep Up with Android OS Updates:
Stay up to date with the latest Android OS updates, new APIs, and platform features. Regularly update your app to leverage new functionalities, enhance performance, and ensure compatibility with newer devices.
17. Provide Localized Versions:
Cater to a global audience by providing localized versions of your app. Translate your app's content, user interface, and notifications into different languages to expand your user base and increase user engagement.
18. Ensure App Store Optimization (ASO):
Optimize your app's visibility and discoverability in the Google Play Store by utilizing appropriate keywords, engaging app descriptions, compelling screenshots, and positive user reviews. ASO techniques can significantly impact your app's download and conversion rates.
19. Follow Privacy Regulations and Guidelines:
Adhere to privacy regulations, such as GDPR and CCPA, and ensure transparent data handling practices within your app. Obtain user consent for data collection, storage, and usage, and provide clear privacy policies to establish trust with your users.
20. Regularly Update and Maintain Your App:
Continuously monitor user feedback, track app performance metrics, and release regular updates to address bugs, introduce new features, and enhance user experience. Regular maintenance ensures that your app remains relevant, competitive, and secure.
Conclusion:
Adopting these 20 best Android development practices in 2023 will help Android app development companies in India, create exceptional applications. By focusing on objectives, embracing Material Design, optimizing performance, and following modern development approaches, your Android apps will stand out in the market, delight users, and achieve long-term success. Also by partnering with an Android App Development Company in India (Gujarat, Vadodara) you can leverage their expertise.
#Android App development company in India#Android App development agencies in India#Android App development companies in India#Android App development company in Gujarat#Android App development company in Vadodara#Android App development agencies in Vadodara#Android App development agencies in Gujarat#Android App development companies in Vadodara#Android App development companies in Gujarat
7 notes
·
View notes
Text
What is the best web-based enterprise accounting software?

In the fast-paced and ever-evolving landscape of business, staying on top of your finances is crucial. As enterprises expand their operations, managing accounts efficiently becomes a daunting task. Thankfully, with the advent of technology, businesses now have access to a plethora of web-based enterprise accounting software options to streamline their financial processes. In this comprehensive guide, we will explore the ins and outs of web-based enterprise accounting software, helping you make an informed decision on the best solution for your business needs.
Understanding Web-Based Enterprise Accounting Software
Web-based enterprise accounting software, often referred to as cloud accounting software, is a digital solution that allows businesses to manage their financial activities online. Unlike traditional accounting systems that rely on on-premise software, web-based accounting tools operate in the cloud, offering users the flexibility to access their financial data from anywhere with an internet connection.
Advantages of Web-Based Enterprise Accounting Software
1. Accessibility
One of the primary advantages of web-based accounting software is accessibility. With data stored securely in the cloud, users can access their financial information anytime, anywhere. This proves especially beneficial for enterprises with multiple locations or remote teams, fostering collaboration and efficiency.
2. Cost Efficiency
Web-based accounting solutions often follow a subscription-based model, eliminating the need for costly upfront investments in software and hardware. This cost-effective approach makes it easier for businesses to scale their accounting infrastructure according to their needs without breaking the bank.
3. Real-Time Updates
In the dynamic world of business, real-time data is invaluable. Web-based accounting software provides instant updates, ensuring that users have access to the most recent financial information. This feature is crucial for making informed decisions and adapting to market changes promptly.
4. Automatic Updates and Maintenance
Gone are the days of manual software updates and maintenance. With web-based accounting solutions, updates are automatic, and maintenance is handled by the service provider. This frees up valuable time for businesses to focus on core operations rather than managing software updates.
Features to Look for in Web-Based Enterprise Accounting Software
1. User-Friendly Interface
A user-friendly interface is essential for ensuring that your team can navigate the software seamlessly. Look for solutions with intuitive dashboards and easy-to-understand features to minimize the learning curve for your staff.
2. Scalability
As your enterprise grows, so do your accounting needs. Choose a web-based accounting solution that can scale with your business, accommodating increased transaction volumes and additional users without compromising performance.
3. Integration Capabilities
Efficient accounting doesn't happen in isolation. Ensure that the web-based accounting software you choose integrates seamlessly with other essential business tools, such as CRM systems, project management software, and e-commerce platforms.
4. Security
The security of your financial data should be a top priority. Opt for web-based accounting software that employs robust encryption protocols and follows industry best practices for data protection. Additionally, check for features such as multi-factor authentication to add an extra layer of security.
Top Contenders in the Web-Based Enterprise Accounting Software Market
1. MargBooks
MargBooks Online is a India's popular online accounting solution known for its user-friendly interface and robust features. It offers a range of plans to suit businesses of all sizes and provides tools for invoicing, expense tracking, and financial reporting.
2. Xero
Xero is another cloud accounting software that caters to small and medium-sized enterprises. With features like bank reconciliation, inventory management, and payroll integration, Xero is a comprehensive solution for businesses looking to streamline their financial processes.
3. NetSuite
NetSuite, owned by Oracle, is a cloud-based ERP (Enterprise Resource Planning) solution that includes robust accounting functionalities. It is suitable for larger enterprises with complex financial needs and offers features such as financial planning, revenue recognition, and multi-currency support.
4. Zoho Books
Zoho Books is part of the Zoho suite of business applications and is designed for small and medium-sized enterprises. It provides features such as automated workflows, project billing, and collaborative client portals, making it a versatile choice for businesses with diverse needs.
Making the Right Choice for Your Business
Choosing the best web-based enterprise accounting software for your business requires careful consideration of your specific needs and objectives. Here are some steps to guide you through the decision-making process:
1. Assess Your Business Requirements
Start by identifying your business's specific accounting requirements. Consider factors such as the number of users, the complexity of your financial transactions, and the need for integration with other business applications.
2. Set a Budget
Determine a realistic budget for your accounting software. While web-based solutions often offer cost savings compared to traditional software, it's essential to choose a solution that aligns with your financial resources.
3. Explore Free Trials
Many web-based accounting software providers offer free trials of their platforms. Take advantage of these trials to explore the features and functionalities of different solutions before making a commitment.
4. Seek Recommendations and Reviews
Consult with other businesses in your industry or network to gather recommendations and insights. Additionally, read reviews from reputable sources to gain a better understanding of the user experiences with different accounting software options.
The Evolution of Web-Based Enterprise Accounting Software
As technology continues to advance, so does the landscape of web-based enterprise accounting software. The evolution of these platforms is driven by the ever-changing needs of businesses and the ongoing developments in cloud technology. Let's delve deeper into the evolving trends shaping the future of web-based accounting solutions.
1. Artificial Intelligence (AI) and Automation
The integration of artificial intelligence and automation is revolutionizing how businesses handle their financial processes. Modern web-based accounting software is incorporating AI algorithms to automate repetitive tasks, such as data entry and invoice categorization. This not only increases efficiency but also minimizes the risk of human error.
2. Enhanced Data Analytics
In the age of big data, the ability to derive meaningful insights from financial data is paramount. Advanced web-based accounting solutions are now equipped with powerful data analytics tools. These tools help businesses analyze trends, forecast future financial scenarios, and make data-driven decisions.
3. Mobile Accessibility
The shift towards mobile accessibility is a notable trend in web-based enterprise accounting software. Businesses are increasingly relying on mobile devices for day-to-day operations, and accounting software providers are responding by offering mobile-friendly applications. This allows users to manage their finances on the go, providing unparalleled flexibility.
4. Integration with E-Commerce Platforms
As e-commerce continues to thrive, businesses are looking for accounting solutions that seamlessly integrate with their online sales platforms. Modern web-based accounting software often includes features tailored for e-commerce, such as automated transaction reconciliation with online sales channels and inventory management.
5. Blockchain Technology
Blockchain technology is making waves in various industries, and accounting is no exception. Some web-based accounting solutions are exploring the integration of blockchain for enhanced security and transparency in financial transactions. This could revolutionize how businesses handle aspects like auditing and transaction verification.
Common Challenges and How to Overcome Them
While web-based enterprise accounting software offers numerous benefits, it's important to be aware of potential challenges and how to overcome them. Here are some common issues businesses may face:
1. Security Concerns
The sensitive nature of financial data raises concerns about security in the cloud. To address this, choose a web-based accounting solution that employs robust encryption protocols and complies with industry security standards. Additionally, educate your team about best practices for secure online behavior.
2. Connectivity Issues
Reliable internet connectivity is crucial for accessing web-based accounting software. In regions with unstable internet connections, businesses may face challenges in real-time collaboration and data accessibility. Consider implementing backup solutions for offline access or explore accounting software with offline capabilities.
3. Customization Needs
Every business has unique accounting requirements. Some businesses may find that certain web-based accounting solutions lack the level of customization they need. In such cases, explore platforms that offer extensive customization options or consider integrating additional specialized accounting tools.
4. Data Ownership and Control
Understanding the terms of service and data ownership is essential when using web-based accounting software. Ensure that the chosen platform allows you to retain control over your financial data and provides mechanisms for data export in case of migration to a different system.
Conclusion: Making the Right Choice for Long-Term Success
In the fast-paced world of business, the right web-based enterprise accounting software can be a game-changer. Whether you're a small startup or a large enterprise, the key is to stay informed about the latest advancements in accounting technology and align your choice with the long-term goals of your business.
As you navigate the vast landscape of web-based accounting solutions, remember that the best choice is the one that seamlessly integrates with your business processes, enhances efficiency, and adapts to the evolving needs of your enterprise. If you have any specific questions or need further guidance on a particular aspect of web-based accounting software, feel free to ask for more information!
Also read- Online billing and accounting software to manage your business
#Web-based accounting#Cloud software#Financial management#Enterprise solutions#accounting#software#billing#online billing software#technology#programming#erp#tech#drawings#illlustration#artwork#art style#sketchy#art#aspec#aromantic asexual#arospec#acespec#aroace#aro#bg3#astarion#shadowheart#gale dekarios#gale of waterdeep#karlach
2 notes
·
View notes
Text
My Journey with Azure IoT Hub: Connecting and Managing IoT Devices at Scale
The Internet of Things (IoT), which enables seamless connectivity and automation across numerous industries, has completely changed the way we engage with technology. I was curious to learn more about the Internet of Things and its possible uses as an aspiring IoT enthusiast. My experience using Azure IoT Hub, Microsoft’s cloud-based IoT platform, and how it assisted me in connecting and managing IoT devices at scale are both discussed in this blog.
Getting Started with Azure IoT Hub

To embark on my IoT journey, I began by understanding the fundamentals of Azure IoT Hub. Azure IoT Hub is a fully managed service that acts as a central hub for bi-directional communication between IoT devices and the cloud. It provides secure, reliable, and scalable connectivity for IoT solutions. Setting up an Azure IoT Hub was my first step. While the process was relatively straightforward, I encountered a few challenges along the way.
Connecting IoT Devices
Once Azure IoT Hub was set up, I delved into the world of IoT devices. I worked with various types of IoT devices, ranging from simple sensors to complex industrial machines. Connecting these devices to Azure IoT Hub required the implementation of device-specific protocols such as MQTT or HTTP. Additionally, I focused on securing device connections and data transmission by utilizing security features provided by Azure IoT Hub.
Real-world examples of IoT devices connected to Azure IoT Hub are aplenty. For instance, in the healthcare industry, wearable devices can transmit patient vitals to Azure IoT Hub, allowing healthcare providers to monitor and respond to critical situations promptly. In smart homes, IoT devices such as thermostats and security cameras can be connected to Azure IoT Hub, enabling remote control and monitoring capabilities.
Managing IoT Devices at Scale
As my IoT project grew, I encountered the need to scale up the number of connected devices. Azure IoT Hub offered robust device management features that simplified the process of managing a large fleet of devices. I could remotely monitor the health, status, and firmware version of each device, enabling efficient troubleshooting and maintenance. Implementing best practices for device management, such as grouping devices based on location or functionality, enhanced the overall operational efficiency of my IoT solution.
Data Ingestion and Processing
Data collected from IoT devices is a valuable asset that can drive actionable insights and informed decision-making. Azure IoT Hub facilitated the ingestion and routing of data to Azure services for further processing and analysis. I had the opportunity to work with Azure Stream Analytics and Azure Functions, which enabled real-time data processing, transformation, and visualization. Leveraging these services allowed me to unlock the true potential of IoT data and derive meaningful insights.
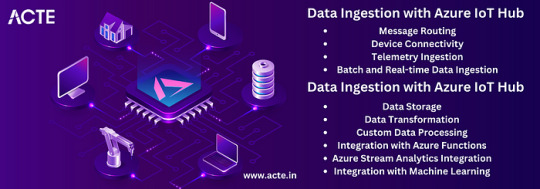
Security and Compliance
Any IoT solution must prioritize security. Azure IoT Hub provided robust security features that ensured end-to-end protection of IoT deployments. These features included device authentication, message encryption, and integration with Azure Active Directory for access control. Additionally, Azure IoT Hub helped me meet compliance and regulatory requirements by providing built-in support for industry standards such as ISO 27001, HIPAA, and GDPR. Throughout my journey, I learned valuable lessons and implemented best practices for securing IoT solutions.
Scalability and Performance
Scaling an IoT solution to handle thousands or millions of devices is a complex task. Azure IoT Hub offered scalability features that allowed me to effortlessly handle large-scale IoT deployments. With Azure IoT Hub’s device-to-cloud messaging capabilities, I could reliably transmit messages to and from a massive number of devices. Moreover, I gained insights into optimizing IoT solutions for performance by considering factors such as message size, frequency, and device capabilities.
Real-World Use Cases
To understand the versatility of Azure IoT Hub, it is crucial to explore real-world use cases. In the manufacturing industry, Azure IoT Hub can be leveraged to connect and monitor machines on the factory floor, ensuring optimal performance and predictive maintenance. In the agriculture sector, IoT devices connected to Azure IoT Hub can collect data on soil moisture levels, temperature, and humidity, enabling farmers to make data-driven decisions for irrigation and crop management. These use cases highlight the valuable role that Azure IoT Hub plays in various domains and industries.
Future of IoT and Azure IoT Hub
The future of IoT is promising, with emerging trends shaping the landscape. As IoT continues to evolve, Azure IoT Hub will play a crucial role in enabling seamless connectivity, advanced analytics, and artificial intelligence capabilities. Integration with other Azure services and continuous updates from Microsoft ensure that Azure IoT Hub remains at the forefront of IoT innovation. The possibilities for IoT applications are limitless, and Azure IoT Hub will continue to empower developers and organizations to build robust and scalable IoT solutions.
Throughout my journey with Azure IoT Hub, I gained valuable insights and experiences. Azure IoT Hub simplified the process of connecting and managing IoT devices, providing a reliable and scalable platform. The seamless integration with other Azure services allowed me to unlock the full potential of IoT data. Moreover, the security and compliance features provided peace of mind, ensuring that my IoT solution was protected from threats. Overall, Azure IoT Hub has been instrumental in my IoT journey, contributing to enhanced efficiency and productivity.
Recommendations and Tips
For those interested in starting their own IoT journey with Azure IoT Hub, I offer the following recommendations and tips:
Begin with a clear understanding of your IoT use case and requirements.
Familiarize yourself with the documentation and resources provided by Microsoft to gain a solid foundation.
Start small and gradually scale your IoT solution as needed.
Take advantage of the device management and security features offered by Azure IoT Hub.
Leverage other Azure services such as Azure Stream Analytics and Azure Functions to derive meaningful insights from IoT data.
Stay updated on emerging trends and best practices in the IoT space.
To deepen your knowledge of IoT and Azure IoT Hub, I recommend exploring Microsoft’s official documentation, participating in the ACTE Technologies Microsoft Azure training, and attending IoT-focused conferences and events.

Azure IoT Hub has proven to be a powerful and comprehensive platform for connecting and managing IoT devices at scale. Throughout my journey, I witnessed the transformative potential of IoT solutions and the crucial role played by Azure IoT Hub in enabling seamless connectivity, advanced analytics, and robust security. As IoT continues to evolve, Azure IoT Hub will undoubtedly remain at the forefront of IoT innovation, empowering organizations to build scalable and efficient IoT solutions. I encourage readers to embark on their own IoT journeys, leveraging the capabilities of Azure IoT Hub to unlock the full potential of IoT. Join me in embracing the future of IoT and revolutionizing industries through connected devices. Please leave your comments, stories, and inquiries in the space provided below. Let’s continue the conversation and explore the endless possibilities of IoT together.
#microsoft azure#cloud services#information technology#education#tech#technology#iot#innovation#cloud computing
5 notes
·
View notes
Text
What a Full-Stack Web Development Company Really Offers
In today’s fast-moving digital ecosystem, businesses don’t just need a website—they need a comprehensive digital solution that’s fast, functional, secure, and scalable. That’s where a Full-Stack Web Development Company comes in. From the moment your project is conceptualized to the final stages of deployment and beyond, a full-stack agency delivers an all-in-one solution for both the front-end and back-end of your digital presence.
Whether you’re launching a startup or scaling an enterprise product, understanding what these companies actually offer can help you make smarter, long-term decisions.
Front-End Development: Your Digital First Impression
The front end is what your users see and interact with—buttons, navigation, layouts, animations, and forms. A full-stack web development company ensures that your front end is not just beautiful but also functional across devices and browsers.
They work with technologies like:
HTML, CSS, JavaScript
Frameworks such as React, Angular, or Vue.js
UI/UX best practices for intuitive and accessible design
Beyond just building interfaces, they align your visual identity with usability. You get interfaces that convert, retain users, and reflect your brand story effectively.
Back-End Development: The Engine Behind the Experience
Behind every user action is a set of processes that connect your website to a server, database, or third-party service. That’s the back end, and it’s where a full-stack team shines.
They handle:
Server setup and database design
APIs and system integrations
Authentication and security layers
Logic for handling business operations (e.g., shopping carts, booking systems, dashboards)
By using powerful languages and frameworks like Node.js, Django, Laravel, Ruby on Rails, or .NET, full-stack developers ensure that your application is fast, secure, and scalable from day one.
Database Management: Organizing Your Digital Assets
Databases are essential for storing and retrieving user data, product information, analytics, and more. A full-stack web development company is adept at choosing and managing the right type of database for your project—whether it’s a relational database like PostgreSQL and MySQL or a NoSQL solution like MongoDB.
They not only build your data architecture but also manage:
Query optimization
Data backup and recovery
Scalable solutions for growing user traffic
This ensures your digital infrastructure remains agile and responsive even as your user base expands.
DevOps and Deployment: Going Live Smoothly
Launching a website isn’t as simple as clicking a button. A full-stack company also manages:
Continuous Integration/Continuous Deployment (CI/CD)
Server provisioning
Cloud hosting on AWS, Azure, or Google Cloud
Monitoring tools for uptime and performance
They streamline the process so your site not only launches smoothly but stays stable and updated post-launch.
Security & Compliance: Protecting What Matters
Security breaches can cost brands not just financially but reputationally. Full-stack web development companies implement proactive security measures:
SSL encryption
OWASP-compliant practices
Secure user authentication
GDPR and data protection compliance
With regular audits and automated security checks, they help you protect user data and avoid potential liabilities.
Maintenance & Scaling: Supporting Growth
Once the site is live, you’ll still need support. A professional full-stack company doesn’t walk away after deployment. Instead, it offers:
Ongoing performance monitoring
Bug fixes and upgrades
Server scaling
Feature enhancements
Whether you want to add a new product line, launch in a new country, or optimize your existing site’s speed, they’re your long-term partners in success.
End-to-End Consultation and Strategy
Beyond technical skills, what sets apart a true full-stack web development company is its ability to align tech with business strategy. They help you:
Define user personas
Map digital journeys
Prioritize features
Choose the right tools for your budget and scale
From MVP to enterprise product, your web partner acts as a digital co-pilot—helping you stay relevant in an ever-changing digital economy.
Conclusion
In essence, a Full-Stack Web Development Company offers far more than coding skills. It offers a strategic, end-to-end partnership to build, run, and grow your digital presence. From intuitive front-end experiences to robust back-end systems, database architecture, DevOps, and ongoing maintenance, a full-stack partner ensures that every layer of your website is aligned with performance and business outcomes.
If you're looking to build a resilient, future-proof digital platform, partnering with a Web Development Company that covers the full stack is one of the smartest investments you can make.
0 notes
Text
Future-Proof Your SMB: Why Sage Cloud Hosting Is the Smartest Move in 2025
Why SMBs Need Cloud Agility in 2025
The cloud computing market is projected to reach $793.8 billion by the end of 2025, and small-to-medium businesses (SMBs) are at the forefront of this transformation. With tighter margins and growing operational complexity, SMBs can't afford to rely on outdated desktop software or limited local servers.

Enter Sage Cloud Hosting — the bridge between traditional accounting power and the modern, scalable infrastructure needed to stay agile.
What Is Sage Cloud Hosting?
Sage Hosting involves running your Sage software — such as Sage 50, Sage 100, or Sage 300 — on a cloud-based server managed by a third-party hosting provider. This enables secure, remote access to your Sage applications from any device, anytime.
Whether you call it Sage application hosting, Sage hosting services, or Sage hosting solutions, the goal is the same: streamline operations, reduce IT overhead, and enable growth.
The Competitive Edge of Sage Hosting Solutions
Here’s what makes Sage cloud hosting essential for SMBs in 2025:
✅ Remote Flexibility
Empower your team to work securely from anywhere — perfect for hybrid or distributed workforces.
✅ Automatic Backups & Updates
Say goodbye to manual updates or lost data. Hosting providers automate everything in the background.
✅ Bank-Level Security
Advanced encryption, firewalls, and multi-factor authentication protect your financial data 24/7.
✅ Scalable Infrastructure
Add more users, apps, or storage in minutes — no new hardware needed.
✅ Reduced IT Costs
Eliminate the expense of maintaining on-site servers and hiring dedicated IT staff.
Side-by-Side Comparison: Sage Desktop vs. Sage Cloud Hosting
FeatureSage DesktopSage Cloud HostingAccessLocal machine onlyAnywhere, anytimeSecurityManual, limited to deviceAdvanced cloud-level securityUpdatesManualAutomaticBackupsUser-initiatedScheduled & automaticMulti-user SupportComplex setupBuilt-in collaborationIT MaintenanceIn-house requiredHandled by providerScalabilityLimitedEasily scalable
Who Benefits Most from Sage Hosting Services?
If you’re an SMB in industries like retail, construction, manufacturing, or professional services, you’ll see immediate ROI. Sage cloud hosting is especially valuable for:
Multi-location businesses needing centralized data access
Remote teams looking for seamless collaboration
Companies scaling quickly and outgrowing desktop limitations
CPA firms juggling multiple client accounts with security concerns
Step-by-Step Guide: How to Migrate to Sage Cloud Hosting
Making the move is easier than you think. Here’s how most reputable Sage hosting services handle it:
Step 1: Choose a Trusted Sage Hosting Provider
Look for providers with verified Sage compatibility, 24/7 support, and data centers that are SSAE-18 certified.
Step 2: Assess Your Needs
Decide which Sage version you need hosted and how many users will access it.
Step 3: Schedule a Migration
Your hosting partner will back up your current data, test the cloud environment, and set a go-live date.
Step 4: User Training & Access Setup
Each user gets a secure login. Basic training is often included to help your team adapt quickly.
Step 5: Go Live & Monitor
Once live, you’ll have real-time access to your Sage software — with performance monitoring and ongoing support.
Real-World Impact: SMBs Thriving on Sage Application Hosting
Case Example: A 15-employee construction firm in Ohio cut IT costs by 35% and doubled productivity within two months of switching to Sage 100 hosting. With real-time job costing accessible from field tablets, they streamlined billing and payroll like never before.
How to Choose the Right Sage Hosting Solution in 2025
Not all Sage hosting services are created equal. Use this checklist to compare:
✅ 99.99% Uptime Guarantee
✅ 24/7/365 Phone & Chat Support
✅ Compliance (SOC 2, HIPAA, GDPR if needed)
✅ Scalable Plans for Growth
✅ Free Migration Assistance
✅ Data Centers in Your Geographic Region
Final Thoughts: The Future Is in the Cloud
The shift to Sage cloud hosting is not just a trend — it’s a business imperative. SMBs that embrace this transition gain the flexibility, resilience, and agility needed to survive and thrive in today’s digital-first economy.
With the right Sage hosting provider, you’re not just moving software — you’re unlocking new potential for growth, cost-efficiency, and innovation.
#sage application hosting#sage cloud hosting#sage hosting#sage hosting services#sage hosting solutions
0 notes
Text
SaaS Development: The Future of Business Innovation with Dream Cyber Infoway
In today's rapidly evolving digital world, businesses are increasingly turning to Software-as-a-Service (SaaS) solutions to drive innovation, streamline operations, and enhance customer experiences. SaaS has become an essential tool for businesses of all sizes, providing them with scalable, cost-effective solutions that help them stay competitive in their respective industries. Dream Cyber Infoway, a leading SaaS development company, is at the forefront of this technological revolution, offering businesses customized SaaS solutions that are tailored to meet their unique needs.
What is SaaS and Why is it Important?
Software-as-a-Service (SaaS) refers to a cloud-based software delivery model where applications are hosted and provided over the internet. Unlike traditional software, which requires users to install and maintain it on their devices, SaaS eliminates the need for extensive hardware infrastructure and software updates, as everything is managed in the cloud. This not only reduces the IT burden but also enhances the flexibility and scalability of businesses, making SaaS an ideal solution for modern enterprises.
SaaS offers numerous advantages, such as:
Cost Efficiency: With SaaS, businesses no longer need to invest heavily in hardware, software licenses, and maintenance costs. Instead, they pay for the service on a subscription basis, which helps them save significant resources.
Scalability: SaaS platforms can be easily scaled to accommodate growth, allowing businesses to expand their operations without worrying about infrastructure limitations.
Flexibility: Users can access SaaS applications from anywhere, on any device, making it easy for remote teams to collaborate and stay productive.
Automatic Updates and Maintenance: With SaaS, businesses don't need to worry about software upgrades or system maintenance, as these are handled by the service provider.
Dream Cyber Infoway: Pioneering SaaS Development
As a renowned SaaS development company, Dream Cyber Infoway excels in crafting tailor-made solutions for businesses that want to leverage the power of cloud technology. The company offers end-to-end SaaS development services, including planning, design, development, testing, deployment, and support. By focusing on delivering high-quality, secure, and scalable SaaS applications, Dream Cyber Infoway ensures that businesses can improve efficiency, drive growth, and enhance customer satisfaction.
Expertise in Custom SaaS Development
Dream Cyber Infoway understands that every business has unique requirements and challenges. Therefore, they provide bespoke SaaS solutions that cater to specific needs, ensuring that businesses get a product that aligns with their goals. Their team of skilled developers and engineers works closely with clients to design, develop, and implement applications that are both innovative and reliable.
Whether it's building a CRM system, project management tool, or a custom enterprise solution, Dream Cyber Infoway is equipped to handle a variety of SaaS development projects. The company focuses on creating scalable applications that can grow with the business, ensuring that clients never outgrow their software solutions.
Cutting-Edge Technologies and Innovation
Dream Cyber Infoway uses the latest technologies and frameworks to build state-of-the-art SaaS applications. By utilizing cloud platforms like AWS, Microsoft Azure, and Google Cloud, the company ensures that their SaaS solutions are secure, scalable, and always accessible. They also incorporate modern programming languages such as Python, Ruby, and Node.js, as well as cutting-edge front-end technologies like React and Angular, to create seamless, user-friendly interfaces.
The company also places a strong emphasis on security. With the rise in cyber threats, Dream Cyber Infoway incorporates robust encryption, multi-factor authentication, and data protection strategies into their SaaS solutions, ensuring that businesses and their customers' data remain safe.
Seamless Integration and Support
Another significant benefit of working with Dream Cyber Infoway is their ability to integrate SaaS solutions with existing systems and tools. The company offers API integration, allowing businesses to connect their SaaS applications with other enterprise software and third-party services. This ensures that data flows seamlessly across platforms, providing businesses with a holistic view of their operations.
In addition to development and integration, Dream Cyber Infoway also provides ongoing support and maintenance to ensure that the SaaS applications continue to perform optimally. Their team is always available to address any issues, provide updates, and help businesses navigate any challenges they face post-launch.
Why Choose Dream Cyber Infoway for SaaS Development?
Dream Cyber Infoway stands out as a trusted SaaS development company due to its commitment to delivering exceptional solutions that drive business growth. The company’s expertise in custom development, cutting-edge technology stack, strong security practices, and customer-first approach make it an ideal partner for businesses looking to embrace SaaS.
By choosing Dream Cyber Infoway, businesses gain access to a team of experienced developers who are dedicated to creating solutions that not only meet but exceed expectations. Whether you’re a startup looking to develop your first SaaS product or an established enterprise in need of a customized solution, Dream Cyber Infoway has the expertise and resources to bring your vision to life.
Conclusion
In conclusion, SaaS has revolutionized the way businesses operate by offering scalable, flexible, and cost-effective solutions. Dream Cyber Infoway, with its experience and expertise in SaaS development, is helping businesses tap into the full potential of cloud technology. By providing customized solutions that are secure, scalable, and easy to integrate, Dream Cyber Infoway ensures that your business stays ahead in a competitive digital landscape. If you’re ready to transform your business with innovative SaaS applications, Dream Cyber Infoway is the partner you can trust.
0 notes
Text
Medical Grade All-in-one PC Market Growth Analysis 2025
Market Valuation:
The global Medical Grade All-in-one PC market was valued at US$ 343.15 million in 2023.
Anticipated to reach US$ 513.36 million by 2030, exhibiting a CAGR of 4.54% during the forecast period 2024-2030.
Get free sample of this report at : https://www.intelmarketresearch.com/download-free-sample/75/medical-grade-all-one-pc
A Medical Grade All-in-one PC (Personal Computer) is a computer system specifically designed and manufactured to meet the stringent requirements of the healthcare industry. These PCs are used in various medical settings, including hospitals, clinics, and diagnostic centers, where reliability, performance, and patient data security are of paramount importance.
Medical Grade All-in-one PCs typically feature:
High-performance hardware: All-in-one PCs designed for medical use often come with powerful processors, ample memory, and storage to handle demanding medical applications and data loads.
Medical certifications: These computers must meet various medical certifications, such as IEC 60601-1 (International Electrotechnical Commission) and FDA 21 CFR Part 1040 (U.S. Food and Drug Administration), ensuring their safety, effectiveness, and compatibility with medical environments.
Hygienic design: Medical Grade All-in-one PCs often have features designed for easy cleaning and disinfection, such as antibacterial surfaces and sealed keyboards or touchscreens to prevent bacterial growth.
Customizable and expandable: These PCs are often designed to accommodate additional hardware, such as barcode scanners, RFID readers, or medical devices, to adapt to specific medical needs and workflows.
Reliability and long life cycle: Medical Grade All-in-one PCs are built with robust components and offer long-term support to ensure reliable performance and data integrity over their life cycle.
Ease of use: These systems typically have intuitive interfaces, simplifying data input and retrieval for healthcare professionals.
Data security: Medical Grade All-in-one PCs often feature enhanced security measures, such as encrypted storage and secure user authentication, to protect sensitive patient data.
Factors Considered in Estimation:
The influence of COVID-19 and the Russia-Ukraine War was taken into account while estimating market sizes.
North American Market Analysis:
Current Valuation:
The North American market for Medical Grade All-in-one PC is estimated at $110.17 million in 2023.
Projected Growth:
Expected to reach $136.76 million by 2029, showcasing a CAGR of 3.67% during the forecast period 2023-2029.
Asia-Pacific Market Analysis:
Current Valuation:
The Asia-Pacific market for Medical Grade All-in-one PC is estimated at $106.50 million in 2023.
Projected Growth:
Expected to reach $145.83 million by 2029, reflecting a CAGR of 5.38% during the forecast period 2023-2029.
Factors Influencing the Market:
Market Drivers:
Increasing demand for Medical Grade All-in-one PCs in the healthcare sector.
Technological advancements and integration of healthcare IT solutions.
Challenges:
Potential challenges related to the impact of global events like the Russia-Ukraine War and the ongoing COVID-19 pandemic.
Regional Dynamics:
Varied growth rates between North America and Asia-Pacific, influenced by regional healthcare infrastructure development.
Report Scope
This report aims to provide a comprehensive presentation of the global market for Medical Grade All-in-one PC, with both quantitative and qualitative analysis, to help readers develop business/growth strategies, assess the market competitive situation, analyze their position in the current marketplace, and make informed business decisions regarding Medical Grade All-in-one PC.
The Medical Grade All-in-one PC market size, estimations, and forecasts are provided in terms of sales volume (K Units) and revenue ($ millions), considering 2021 as the base year, with history and forecast data for the period from 2017 to 2028. This report segments the global Medical Grade All-in-one PC market comprehensively. Regional market sizes, concerning products by Type, by Application, and by players, are also provided.
For a more in-depth understanding of the market, the report provides profiles of the competitive landscape, key competitors, and their respective market ranks. The report also discusses technological trends and new product developments.
The report will help the Medical Grade All-in-one PC manufacturers, new entrants, and industry chain related companies in this market with information on the revenues, sales volume, and average price for the overall market and the sub-segments across the different segments, by company, by Type, by Application, and by regions.
By Company
Onyx Healthcare
Teguar
ACL
DT Research
advantech
Cybernet
Thinlabs
PWS
Tangent
Parity Medical
Wincomm
HP
Werth Systems
Freeway Med-Tech
Jiaweishi Electronic Technology
IEI
Rein Medical
Athena Medical
Segment by Type
Mains Powered Medical Grade All-in-one PC
Battery Powered Medical Grade All-in-one PC
Segment by Application
Electronic Medical Records
Telemedicine
Medical Imaging
Others
Consumption by Region
North America
U.S.
Canada
Asia-Pacific
China
Japan
South Korea
India
Australia
Southeast Asia
Rest of Asia-Pacific
Europe
Germany
France
U.K.
Italy
Russia
Rest of Europe
Latin America
Mexico
Brazil
Argentina
Rest of Latin America
Core Chapters
Chapter 1: Introduces the report scope of the report, executive summary of different market segments (by region, product type, application, etc), including the market size of each market segment, future development potential, and so on. It offers a high-level view of the current state of the market and its likely evolution in the short to mid-term, and long term.
Chapter 2: Detailed analysis of Medical Grade All-in-one PC manufacturers competitive landscape, price, sales and revenue market share, latest development plan, merger, and acquisition information, etc.
Chapter 3: Sales, revenue of Medical Grade All-in-one PC in regional level and country level. It provides a quantitative analysis of the market size and development potential of each region and its main countries and introduces the market development, future development prospects, market space, and market size of each country in the world.
Chapter 4: Provides the analysis of various market segments by Type, covering the market size and development potential of each market segment, to help readers find the blue ocean market in different market segments.
Chapter 5: Provides the analysis of various market segments by Application, covering the market size and development potential of each market segment, to help readers find the blue ocean market in different downstream markets.
Chapter 6: Provides profiles of key players, introducing the basic situation of the main companies in the market in detail, including product sales, revenue, price, gross margin, product introduction, recent development, etc.
Chapter 7: Analysis of industrial chain, including the upstream and downstream of the industry.
Chapter 8: Introduces the market dynamics, latest developments of the market, the driving factors and restrictive factors of the market, the challenges and risks faced by manufacturers in the industry, and the analysis of relevant policies in the industry.
Chapter 9: The main points and conclusions of the report.
Get free sample of this report at : https://www.intelmarketresearch.com/download-free-sample/75/medical-grade-all-one-pc
0 notes
Text
The Ultimate Guide to App Development: Trends, Tips, and Strategies for Success
In today’s digital-first world, app development has become a cornerstone for businesses looking to engage users, streamline operations, and drive growth. Whether you're a startup or an established brand like City Insider Inc, having a well-designed, functional app can significantly enhance customer experience and boost revenue. This guide explores the latest trends, best practices, and essential strategies to help you succeed in the competitive app market.
Why App Development Matters in 2024
Mobile apps are no longer a luxury—they’re a necessity. With over 6.8 billion smartphone users worldwide, businesses that leverage app development gain a competitive edge. Apps improve accessibility, foster customer loyalty, and provide personalized experiences. For companies like City Insider Inc, a well-optimized app can be a powerful tool for delivering real-time updates, seamless transactions, and enhanced user engagement.
Top Trends Shaping App Development in 2024
Staying ahead in app development requires keeping up with emerging trends:
AI & Machine Learning Integration – Apps now use AI for chatbots, predictive analytics, and personalized recommendations.
5G Technology – Faster speeds enable richer multimedia experiences and real-time functionality.
Cross-Platform Development – Frameworks like Flutter and React Native reduce costs and development time.
Enhanced Security Features – Biometric authentication and end-to-end encryption are becoming standard.
Voice & AR/VR Integration – Voice search and augmented reality are transforming user interactions.
By adopting these trends, City Insider Inc can create innovative, future-proof apps that stand out in the market.
Key Steps in the App Development Process
A successful app development project follows a structured approach:
Market Research – Identify target audience needs and analyze competitors.
Define Objectives – Outline clear goals, such as improving sales or enhancing user engagement.
UI/UX Design – Prioritize intuitive navigation and visually appealing interfaces.
Development & Testing – Use agile methodologies for iterative improvements.
Launch & Marketing – Optimize app store listings and leverage social media for promotion.
Post-Launch Maintenance – Continuously update features based on user feedback.
Following these steps ensures a smooth development cycle and a high-quality final product.
Choosing the Right App Development Approach
Businesses like City Insider Inc must decide between:
Native Apps – Built for specific platforms (iOS or Android) for optimal performance.
Hybrid Apps – Combine web and native elements for cost efficiency.
Progressive Web Apps (PWAs) – Web-based apps that function like native ones.
Each approach has pros and cons, so selecting the right one depends on budget, timeline, and business goals.
How to Optimize User Experience (UX) in App Development
A great UX is critical for app success. Key strategies include:
Simplified Onboarding – Minimize steps for new users.
Fast Loading Speeds – Optimize performance to reduce bounce rates.
Personalization – Use data to tailor content and recommendations.
Accessibility – Ensure the app is usable for people with disabilities.
By focusing on UX, City Insider Inc can increase retention and user satisfaction.
Monetization Strategies for Your App
Generating revenue from an app requires smart monetization tactics:
In-App Purchases – Offer premium features or digital goods.
Subscription Models – Charge users monthly or annually for access.
Advertisements – Integrate non-intrusive ads for free apps.
Freemium Model – Provide basic features for free with paid upgrades.
Selecting the right model depends on the app’s purpose and audience.
Future of App Development: What’s Next?
The app development landscape is evolving rapidly. Emerging technologies like blockchain, IoT integration, and wearable-compatible apps will shape the future. Businesses like City Insider Inc must stay agile, continuously innovate, and adapt to new trends to remain competitive.
Conclusion: Partner with Experts for Successful App Development
Creating a successful app requires expertise, strategy, and innovation. Whether you're a startup or an established company like City Insider Inc, investing in professional app development ensures a high-performing, user-friendly product. By following the latest trends, optimizing UX, and choosing the right monetization strategy, your app can thrive in today’s competitive market.
Ready to build your next app? Contact City Insider Inc today for cutting-edge app development solutions tailored to your business needs!
0 notes
Text
Overcoming Challenges in Data Integration: Insights from Consulting Experts
Data integration for enterprises can take longer due to technological, financial, and time constraints. As a result, modifying data strategies to mitigate risks like incompatibility between many tools or budget overruns is crucial. Companies must also prepare for new compliance requirements to ensure ethical data operations. This post will explore such challenges in data integration while listing valuable insights from consulting experts in this domain.
What is Data Integration?
Data integration merges data from disparate origins and presents it to maximize comprehension, consolidation, and summarization effectiveness. Integrated data views rely on data ingestion, preparation, and advanced insight extraction. It also streamlines the data operations services across regulatory report creation, helpdesks, and 360-degree client life cycle management.
All data integration strategies involve the extract, transform, and load (ETL) pipelines regardless of business units or target industries. At the same time, the scope of planning and quality assurance in each process varies due to domain-specific data classification factors.
For instance, the accounting departments must handle extensive numerical data while interpreting legal and organizational requirements for transparency. On the other hand, production engineering and design professionals will use visualizations to improve goods or service packages. Accordingly, accountants will use unique tools distinct from engineers’ software.
Later, the leaders might want a comprehensive overview of the synergy between these departments. Therefore, they must determine efficient data integration strategies. The data will move between several programs, carrying forward many updates throughout a project’s progression based on those roadmaps.
Overcoming the Challenges in Data Integration Using Insights from Consulting Experts
1| Data Quality Hurdles
Linking, consolidating, and updating data from several sources will exponentially increase the quality-related threats. For instance, consider multimedia assets from social networks or unreliable news outlets. They can help your secondary market research and social listening initiatives. However, you want to verify the authenticity of gathered intelligence to avoid inaccurate data ingestion.
Evaluating relevance, freshness, and consistency is essential to data quality assurance from creation to archival. So, corporations have started leveraging data lifecycle management to boost dataset integrity, helping make integration less of a hassle.
Insights:
Most consulting experts suggest developing ecosystems that check and recheck quality metrics at each stage of a data integration lifecycle. Moreover, they recommend maintaining periodic data backups with robust version control mechanisms. Doing so will help quality preservation efforts if errors arise after a feature update or a malicious third party is likely to break the system using malware.
2| Networking and Computing Infrastructure Problems
Legacy hardware and software often introduce bottlenecks, hurting data integration’s efficiency. Modern integration strategies demand more capable IT infrastructure due to the breakthroughs like the internet of things (IoT), 5G networks, big data, and large language models. If a company fails to procure the necessary resources, it must postpone data integration.
Technologies integral to capturing, storing, checking, sorting, transferring, and encrypting data imply significant electricity consumption. Besides, a stable networking environment with adequate governance implementations enables secure data transactions. The underlying computing infrastructure is not immune to physical damage or downtime risks due to maintenance mishaps.
What Consulting Experts Say:
Enterprises must invest in reliable, scalable, and efficient hardware-software infrastructure. This will benefit them by providing a stable working environment and allowing employees to witness productivity improvements. Upgrading IT systems will also enhance cybersecurity, lowering the risk of zero-day vulnerabilities.
3| Data Availability Delays
Governments, global firms, educational institutions, hospitals, and import-export organizations have a vast network of regional offices. These offices must also interact with suppliers, contractors, and customers. Due to the scale of stakeholder engagement, reports concerning office-level performance and inventory might arrive late.
Underproductive employees, tech troubleshooting, slow internet connectivity, and a poor data compression ratio will make data sourcing, updating, and analyzing inefficient. As a result, a data integration officer must address time-consuming activities through strategic resource allocation. If left unaddressed, delays in data delivery will adversely affect conflict resolution and customer service.
Expert Insights:
Train your employees to maximize their potential and reduce data acquisition, categorization, and transformation delays. Additionally, you will want to embrace automation through artificial intelligence (AI) applications. Find methods to increase the data compression ratio and accelerate encryption-decryption processing cycles. These measures will help accomplish near-real-time data integration objectives.
4| Vendor Lock-ins
A vendor lock-in results from inconvenience and restrictions when a client wants to switch to another service provider or toolkit. Although data integration platforms claim they celebrate the ease of migrating databases with competitors, they might covertly create vendor lock-ins.
For instance, some data sourcing and sorting ecosystems might limit the supported formats for bulk export commands. Others will use misleading methods to design the graphical user interface (GUI) of account deletion and data export features. They involve too many alerts or generate corrupt export files.
Practical Insights:
Combining multiple proprietary and open-source software tools offers the best cost optimization opportunities. When you select a data vendor, audit the tools the willing data integration providers use to deliver their assistance. Do they use a completely proprietary system based on an unknown file format unsupported by other platforms?
Finally, you must check all the data import, export, and bulk transfer options in vendors’ documentation. After you check a data firm’s current client base, track its online ratings and scan for red flags indicating potential vendor lock-ins.
5| Data-Related Ethical and Legal Liabilities
Confidentiality of investor communication and stakeholders’ privacy rights are two components of legal risk exposure due to enterprise data integration. Additionally, brands must interpret industry guidelines and regional directives for regulatory disclosures.
They must comply with laws concerning personally identifiable information (PII) about employees and customers. Otherwise, they will attract policymakers’ ire, and customers will lose faith in brands that do not comply with the laws of their countries.
Insights:
Consulting experts recommend collaborating with regional legal teams and global governance compliance specialists. After all, mitigating legal risks can help increase business resilience.
Improved compliance ratings have also benefited several brands wanting to be attractive to impact investors. Meanwhile, customers demanding ethical data operations at business establishments love supporting brands with an exceptional governance culture.
Conclusion
Most brands need specialists' help to develop consolidated data views during reporting because they have flawed data integration strategies. So, they require trustworthy insights from reputed consulting experts with a proven track record of overcoming challenges in data integration. The selected data partners must excel at ETL implementation, governance compliance, and data quality management (DQM).
The corporate world champions data-centric business development. Understandably, the need for scalable data integration reflects the increased stakeholder awareness regarding the importance of connecting disparate data sources. With transparent, fast, and accurate data, organizations will enhance their competitive edge amid this intense digital transformation race.
3 notes
·
View notes
Text
Cloud-Based Custom Software: Benefits and Use Cases

As businesses strive for agility, scalability, and cost-efficiency, cloud technology has become a cornerstone of digital transformation. More organizations are now combining the flexibility of cloud computing with the precision of custom software development services to build solutions that are not only tailored but also future-ready. Cloud-based custom software brings the best of both worlds—customization and accessibility—into a single, powerful offering.
Let’s explore the key benefits and real-world use cases of this approach.
Key Benefits of Cloud-Based Custom Software
1. Scalability on Demand
One of the greatest advantages of cloud platforms is their ability to scale resources based on usage. Whether your user base grows by hundreds or thousands, cloud infrastructure can accommodate without major overhauls or downtime.
2. Cost Efficiency
With a cloud-based approach, you eliminate the need for heavy upfront investment in physical servers or IT infrastructure. Pay-as-you-go models allow businesses to pay only for the resources they use, making it an economical choice.
3. Global Accessibility
Cloud-based custom software is accessible from anywhere with an internet connection. This is ideal for remote teams, global operations, and businesses that require 24/7 access to critical systems.
4. Improved Security and Compliance
Leading cloud providers offer built-in security features like data encryption, intrusion detection, and multi-factor authentication. Combined with custom controls, your software can meet industry-specific compliance standards.
5. Faster Deployment and Updates
Cloud environments support rapid development cycles. You can deploy updates, new features, or patches without interrupting user activity—perfect for maintaining a seamless experience.
Real-World Use Cases
📦 Logistics and Supply Chain
A cloud-based custom solution can track real-time inventory, automate restocking, and provide predictive analytics for demand planning—all accessible across warehouses and distribution centers.
🏥 Healthcare Platforms
Custom software hosted on the cloud can enable secure telemedicine services, streamline patient records, and ensure HIPAA compliance through encrypted data handling.
🛒 E-Commerce Systems
Scalable, cloud-native custom e-commerce platforms can handle traffic spikes, integrate with third-party logistics, and offer personalized shopping experiences through AI.
📊 Business Intelligence Tools
Cloud-based dashboards and reporting tools can pull data from multiple sources, providing decision-makers with real-time insights and KPI tracking.
🏢 Enterprise Resource Planning (ERP)
Custom ERP solutions on the cloud offer modular functionality for HR, finance, procurement, and more, with the flexibility to grow as your organization evolves.
Final Thoughts
Cloud-based custom software is more than just a trend—it’s a strategic choice that helps businesses innovate faster, operate smarter, and adapt to changing demands. To ensure your project is both technically sound and aligned with your goals, partnering with an experienced software development company is essential for long-term success.
0 notes
Text
Strengthening Corporate Email Security
Corporate email security is a critical component of an organization's overall cybersecurity strategy. It faces numerous threats, from phishing attacks to unauthorized access. Implementing effective security measures can mitigate these risks. However, many companies still overlook basic protocols, leaving their sensitive information vulnerable. Understanding the common threats and best practices can greatly enhance security posture. What specific strategies can organizations adopt to strengthen their defenses against these persistent risks?
Key Takeaways
Implement multi-factor authentication (MFA) to add an extra layer of security against unauthorized access to email accounts.
Educate employees on recognizing phishing attempts to reduce the risk of falling victim to email scams.
Regularly update and enforce strong password policies to ensure unique passwords are used across corporate accounts.
Conduct routine audits to monitor for unauthorized access and suspicious activities within email accounts.
Encrypt sensitive communications to protect data integrity and maintain confidentiality in email exchanges.
Understanding the Importance of Email Security in Corporate Environments
Email serves as a critical communication tool within corporate environments, making its security paramount. Organizations rely on email for exchanging sensitive information, coordinating projects, and maintaining relationships with clients and partners. A breach in email security can lead to significant financial losses, reputational damage, and compromised confidential data. Understanding the importance of robust email security measures fosters a culture of vigilance among employees, reinforcing their role in safeguarding organizational assets. Implementing multifactor authentication, regular software updates, and employee training on security protocols are essential steps. By prioritizing these strategies, companies can create a more secure email environment. Ultimately, these tips for securing corporate email accounts not only protect individual users but also enhance the integrity and trustworthiness of the entire organization.
Common Threats to Corporate Email Accounts
In today's digital landscape, corporate email accounts face a myriad of threats that can undermine organizational security. Phishing attacks, where malicious actors impersonate trusted entities to deceive employees into providing sensitive information, are prevalent. Additionally, malware can infiltrate systems via email attachments or links, leading to data breaches. Business Email Compromise (BEC) schemes exploit social engineering tactics to manipulate employees into transferring funds or disclosing confidential data. Moreover, insufficient password policies and lack of multi-factor authentication leave accounts vulnerable to unauthorized access. As organizations increasingly rely on email for communication, understanding these common threats is essential for fostering a security-conscious culture, ensuring that employees recognize and respond effectively to potential risks while traversing their digital environment.

Tips for Securing Corporate Email Accounts
To combat the multitude of threats faced by corporate email accounts, organizations must implement robust security measures. First, adopting strong, unique passwords and encouraging regular updates can markedly reduce vulnerability. Additionally, educating employees on recognizing phishing attempts fosters a culture of vigilance. Regular audits of email accounts help identify unauthorized access and suspicious activities. Utilizing encryption for sensitive communications protects data integrity during transmission. Moreover, establishing clear protocols for email usage and ensuring compliance with security policies strengthens overall defenses. Organizations should also consider using secure email gateways to filter out malicious content. By following these tips for securing corporate email accounts, businesses can create a more resilient email environment, fostering trust and collaboration among employees.
Implementing Multi-Factor Authentication
A considerable layer of protection for corporate email accounts is the implementation of multi-factor authentication (MFA). MFA enhances security by requiring users to provide multiple forms of verification before accessing their accounts. This typically involves something the user knows, like a password, combined with something they possess, such as a mobile device for a one-time code. By integrating MFA, organizations create a formidable barrier against unauthorized access, considerably mitigating the risk of data breaches. This strategic approach fosters a culture of security awareness, encouraging employees to prioritize their digital safety. As cyber threats evolve, adopting MFA demonstrates a commitment to protecting sensitive information, aligning with the broader goal of securing corporate email accounts against increasingly sophisticated attacks.
Regularly Updating Security Policies and Training Employees
Regular updates to security policies, coupled with thorough employee training, form a critical foundation for effective corporate email security. Organizations must periodically assess and revise their security protocols to adapt to evolving threats. This includes integrating the latest technological advancements and regulatory requirements. Extensive training programs empower employees to recognize phishing attempts and suspicious activities, fostering a security-conscious culture. Regular drills and simulations can enhance awareness and preparedness, ensuring that employees feel confident in their role as the first line of defense. By fostering a sense of belonging within the organization, employees are more likely to engage actively in security practices. Ultimately, these strategies contribute considerably to tips for securing corporate email accounts, creating a resilient and secure email environment.
Conclusion
To summarize, enhancing corporate email security is imperative for safeguarding sensitive information and maintaining organizational integrity. By understanding the importance of email security, recognizing common threats, and implementing strategic measures such as multifactor authentication and regular employee training, companies can greatly mitigate risks. A proactive approach to security not only fosters a culture of vigilance among employees but also strengthens overall resilience against cyberattacks, ultimately reinforcing trust and reliability in corporate communications.
0 notes