#FIDO Authentication Industry
Explore tagged Tumblr posts
Text
FIDO Authentication Industry Hits $1.24 Billion in 2022, Set to Soar to $12.06 Billion by 2033
The FIDO Authentication Market has witnessed remarkable growth, with the total revenue reaching US$ 1,238.6 million in 2022. This impressive growth trajectory is projected to continue, with the market expected to surge to US$ 12,059.7 million by 2033, reflecting a robust Compound Annual Growth Rate (CAGR) of 23.1% from 2023 to 2033.
Get Sample Copy of this Report at: https://www.futuremarketinsights.com/reports/sample/rep-gb-12485
Drivers and Opportunities:
The market’s expansion is driven by several factors, including the increasing adoption of FIDO authentication solutions across various industries. The rising concerns over cybersecurity threats have prompted organizations to seek robust authentication methods, further fueling market growth. Additionally, the growing popularity of biometric authentication methods and the proliferation of mobile devices are providing lucrative opportunities for market players to innovate and expand their offerings.
Competitive Landscape – Regional Trends:
The FIDO Authentication Market is highly competitive, with key players constantly innovating to maintain their market position. Regional trends indicate that North America dominates the market, owing to a high concentration of tech-savvy enterprises and stringent security regulations. Europe follows closely behind, driven by increasing awareness of data security. Meanwhile, the Asia-Pacific region presents significant growth potential due to the rapid digitalization of economies and the need for robust authentication solutions.
Restraints:
Despite its rapid growth, the market faces certain limitations, including concerns related to user privacy and data protection. Striking a balance between stringent security measures and user convenience remains a challenge for market players. Moreover, the high initial costs associated with implementing FIDO authentication solutions may hinder adoption among smaller enterprises.
Region-wise Insights – Category-wise Insights:
Regionally, North America leads the FIDO Authentication Market, with a substantial share of the global market. Within categories, biometric authentication solutions are gaining prominence due to their accuracy and user-friendliness. Moreover, the healthcare and financial sectors are witnessing substantial adoption of FIDO authentication, driven by the need for secure access to sensitive data.
Request for Methodology: https://www.futuremarketinsights.com/request-report-methodology/rep-gb-12485
Competitive Landscape
As organizations around the world are challenged in controlling dynamic and hybrid IT environment, the need for secure mobile or online applications without compromising user convenience is increasing continuously.
Owing to this, most of the leading players in the FIDO authentication technology are coming with advanced and innovative solutions that meets the ever-changing demand from organizations for advanced security and privacy concerns.
In January 2021, Aware, Inc. announced the launch of AwareABIS, an automated biometric identification system (ABIS) used for large-scale biometric identification and deduplication. Designed to serve among 1-30 million identities or more, AwareABIS supports fingerprint, face and iris modalities, and features a modular architecture that helps security teams configure and optimize the system for civil or criminal applications.
FIDO Authentication Outlook by Category
By Solution:
FIDO U2F Authentication Devices
FIDO Authentication SDKs
FIDO Client SDK
FIDO Server SDK
Services
Technology Consulting
Integration & Deployment
FIDO Certification Services
Support Services
By Application:
Payment Processing
PKI/Credential Management
Document Signing
User Authentication
Others
By Industry:
BFSI
Healthcare & Life Sciences
IT & Telecom
Retail & CPG
Government & Defense
Energy & Utilities
Others
By Region:
North America
Latin America
Europe
East Asia
South Asia & Pacific
Middle East and Africa
0 notes
Text
cat names
so I'm in an a cappella group which is part of a queer community chorus and one of our members works at an animal shelter. today she posted in the a cappella discord: "About to have to name forty cats for the next hour I’ll be collecting wherever unhinged names you can think of"
this was two hours ago. we are still coming up with cat names. the list (SO FAR) is under the cut. tag yourself, I'm Permanently Exhausted Pigeon
we think many of these would be excellent baby names also. as one of our sopranos said, "what is a cat but a baby with claws?"
(note: stuff in parentheses after the cat name is commentary from the person who came up with the name)
Permanently Exhausted Pigeon
Xena: Warrior Princess
Deke Sharon
George Foreman ("and name the next five George Foreman Jr")
Samantha the Evil Twin
Magical Mr. Mistofelees
Stephen
Kelsey Hightower ("this is not a celebrity, but he is well-known in my industry, and his name is a fuckin banger")
John Cena
The Onceler
Pig
Madison
Nancy
Olivia Newton-John
Blake Carrington
The Purple Principessa
Rubik's Cube
Zaphod Beeblebrox
Owl
Fido
Rover
Mystery Incorporated
Quark
Agatha
Vetinari
Evil Grand Vizier
Horatio
Juno
Bob Loblaw
Juniper
Mrs. Shirley Jenkins
Michael Scott
Spot
Jermaine
Churu
Tia and Tamera Meowry
Soup Spoon
Kleenex
Mug
32-Inch Curved Monitor
Shitty Fourthhand Dell Laptop
Taco Bell Hot Sauce Packet
Don't Worry About What Number of Coffee That Is
Hot Sauce
Harrowhark Nonagesimus
Gideon Nav
John
Pussalitus
Shell Script
Bob the Drag Cat
Slay
Right Meow
Pawl McCartney
Fuzzmeister ("something my ex-roommate used to call my cat")
Fuzzbucket ("another thing my ex-roommate used to call my cat")
Furry Bastard ("ibid")
Jessica! [ed. note: yes, with the exclamation point. I asked]
William Shakespeare
Thursday
Laura Jane Grace
Billy the Kitten
Cat 5 ("I CRACK MYSELF UP LOLOLOL this is a nerd joke don't worry about it")
Pixel
The Child
We're Calling About Your Cat's Extended Warranty
Ibid
Ketzeleh
Absolutely not stop eating toilet paper ("Or just TP for short")
Get Down From There You Little Shit
Stop Eating Plastic You Fucking Gremlin
Feather Boa
Matilda
Nectarine
The Trunchbull
Blender
Vlad the Impaler
Jackie Daytona
Zoom Call
Scrungle
Synthwave
Shoegaze
Disco
Sandstorm
Pancake
Cursed Skull
None Pizza With Left Beef
Regular Skull with no Otherworldly Implications
Sardine
Doggo
Blobfish
Monarch Butterfly
Wage Theft
Hidden Fees
Labor Solidarity
Tax Fraud
McNugget
Class Action Lawsuit
Daniel Tiger
Tony Hawk
Treacherous Knave
Simone Biles
Sodium Bicarbonate
Unflavored Seltzer
Francesca
Strawberry With A Flat Battery
Boop
The Thong Song
Eurovision
Queen of the Underhill
Beaver Nug
POSSUM
Space Lollipop
Chocolate Napoleon
Dessert Drop
Madame Iris
Happy Tartan
Tiny Assistant Antonia
Biscuit
Rim Tim Taggi Dim
Fortinbras
Baby Lasagna
Elderly Lasagne
Duck
Middle-Aged Shark ("doo-doo")
Batman
Greek Chorus
Bertie Wooster
Jasper
Gomez Addams
Morticia Addams
Beeswax
and the sibling of Beeswax: Mind Your Beeswax
Roomba
Particle Board
FYP
Mr. Murderbritches
Baked Potato
Delulu
Ampersand ("'&' for short")
Your Mom
Booticall McStuffins
Munch
Shoelace
Bubba
Bye Felinecia
Sillybutt
Charles
Christofur Walken
Train Heist
Doc
Oscar The Crouch
Elmo ("for a ginger cat")
Furmit the Crog
Shrek
Beck
Pauline
Dorothy, Rose, Blanche, and Sophia
Soleil Moon Fry
Moon Unit Zappa
Trout
Unholy Bargain
Rick Astley
Comic Sans, Ariel Bold, Dingbats
Professor Scrungle McDingus
Bumoley
Dante’s Inferno
Chairman Meow
Pride and Prejudice
2 Factor Authentication
Blue Wheel of Death
Clippy
Circle back
A Meeting The Should Have Been An Email
Chat Offline
I Need To Speak With You In My Office
Wild Thing
Doofus McGroofus
Thneed
Meowzart
Thelonious Meownk
Turnip Face
Dumpster Fire
Santa Claws
Munchkin (Munch for short)
Parsnip
Illegal Pete
Petit Francois
Neck Pillow
Error404
Itty Bitty Kitty (Committee)
Freddie Kruegpurr
Jason
Chad
Chadwick
Silly William (Billy)
Goose
No-Nonsense Billy ("prefers William")
Experimental Jazz
Sibling of Thelonious Meownk
Gulf of Meowxico
Lake Meowchigan
Meownica Lewinsky
Meowchigan State Spurrtans
Buffalo Pam
Cat-herine
University of Meowchigan Wolferines
Bad Band Name
Meowtallica
Joan Pett
Cat Activation Noise
Alanis Meowissette
Petty LaPone
Mayonnaise
The Sauce
Farrah Pawcet
Burger
Topo Chico
Buns ("brother of Burger")
Onion Ring ("sister of Burger and Buns")
Catsup
A Dish Best Served Cold
Revenge ("short for A Dish Best Served Cold")
Small Forestry Man ("or just Small Man")
Helen of Troy
Trojan Cat
Bean
Spatula
Aunt Irmintrude
Worm Off The String
Worm On A String
What Crimes Will He Commit?
Crimini Mushroom
Saffron
Garbage Truck
Louise
Hashbrown
Sir Violence Fourth Of Their Name
PhD
We Can't Afford That
Euphonium
Spork
Doctor Zhivago
Antoine-Joseph Sax
Lump Sum
Chiquitita
Mothman
The Winner Takes It All ("That one the person doesn’t pay for the adoption they win a wet tee shirt contest")
Catniss Neverseen
MacGruber
This Is The Skin Of A Killer Bella
Loca
Haskell
COBOL
Theodore
Rewrite It In Rust
Rock Lobster
Love Shack
Trampoline
Peas Turnip The Beet
Subarubarubaru
Crime
April Showers Kill The Flowers
Ford Fiesta
Sharon
Rodrick
Felony
Jaywalking
Dipthong
Fun With Phonics
LMNOP
RFTM
Quilt
AEIO
AEIOU and Sometimes Y
Consonant
Verb
O R B
Gandalf's Big Naturals
OA
Refrigerator
CatGPT
Feral Beast
Feral Pawcet
Air Filter
Antithesis
Synthesis
Onomatopee-er
California Pizza Kitten
Floor Wax
Shamalamadingdong
Murphey’s Oil Soap
I Can't Believe It's Not Butter
Mysterious Figure
Mouse ("And her sister Shady Character")
Trackball
The Real Slim Shady
Recessive Jean
4 notes
·
View notes
Text
The new iShield Key 2: Next-generation security key for phishing-resistant login and physical access
04/06/2025 by Alexander Summerer
In my latest blog post, I unveil the iShield Key 2, a universal security key designed for both digital and physical access. I explain why the iShield Key 2 sets the global standard for hardware authentication and is the ideal phishing-resistant authentication solution for companies and organizations.
Introduction
Between 2023 and 2024, the number of daily cyberattacks rose to over 600 million. In Q3 of 2024, cyberattacks increased by 75% worldwide compared to the previous year. As the number of cyberattacks increases, so does the extent of the financial damage. A total of $9.5 trillion has been estimated for 2024 worldwide. Consequently, companies of all sizes are facing financial difficulties, and some are even being forced into insolvency.
Depending on the industry, cyberattacks can have devastating consequences for critical infrastructure. One notable cyberattack occurred at the Central Bank of Lesotho. In this case, the national payment system was disrupted, preventing transactions by domestic banks. This significantly restricted economic activity.
As cyberattacks increase, more and more regulations are being introduced worldwide by states and organizations with which companies must comply. In the US alone, over 170 data protection regulations were introduced between 2023 and 2024.
Phishing attacks are a major cause of successful cyberattacks. Phishing remains a perennial cybersecurity threat. According to Trend Micro, phishing attacks increased by 58% in 2023, with an estimated financial impact of $3.5 billion USD in 2024.
Selected Sectors: Healthcare, Finance, and Manufacturing
I was curious to learn more, so I examined the challenges in the following three key industries.
Healthcare
For example, in 2024, there were around 720 cyber incidents in the US affecting over 180 million people and their healthcare data.
Challenges: One of the biggest challenges in the healthcare environment is the numerous different systems employees must log into repeatedly. This also leads to passwords being shared and passed on.
Finance
Cyberattacks are increasingly targeting the global financial sector. In the last 12 months, 64% of financial institutions reported experiencing cybersecurity incidents. These cyberattacks can have serious consequences, including significant financial losses and disruption to economic activity in one or more countries.
Challenges: In the financial sector, cyberattacks via phishing primarily target financial fraud, such as the theft of bank account data and login credentials.
Manufacturing Industry
Cyberattacks are increasingly targeting the manufacturing industry, accounting for more than 25% of global cyber incidents in 2024 — making it the top target for the third consecutive year. Phishing attacks increased by 80% between September 2023 and September 2024.
Challenges:
In the manufacturing industry, ransomware usually infiltrates a company's IT and OT systems through phishing attacks, which can lead to production downtime.
My conclusion: Phishing plays a predominant role in cyberattacks on companies and organizations in almost all industries. The best solution to make them more resilient and secure against attacks is a zero-trust architecture in combination with passwordless authentication.
The best way to increase the cyber resilience for companies and organizations
Swissbit provides effective support in implementation and provisioning of critical infrastructure protection against cyber threats.
Key strategies:
Enable phishing-resistant multi-factor authentication (MFA) to ensure all users are protected.
Adopt passwordless authentication and switch to methods not based on passwords as passwords are vulnerable to phishing attacks.
Use passkeys with hardware support. Deploy FIDO security keys, such as the iShield Key 2. These use hardware-assisted security to protect critical resources.
Implement a zero trust architecture. This verifies access requests, minimizing the risk of unauthorized access. Learn more about zero trust with hardware authentication: Whitepaper Zero Trust solutions with hardware authentication - Swissbit.
Empower employees through IT security training. Employees need to recognize the characteristics of phishing emails.
These strategies can improve the security of critical infrastructure facilities against evolving cyber threats. The State of Passwordless Identity Assurance Report shows that these strategies are becoming more popular. The report states:
46% of respondents are using passwordless and FIDO-based authentication methods
This adoption of phishing-resistant authentication is a paradigm shift in cybersecurity, with FIDO passkeys and hardware keys expected to become the gold standard in authentication by 2027
How the iShield Key 2 became the standard for phishing resistant hardware authentication

Invest in multi-factor authentication (MFA) to prevent access to relevant systems and data. The goal should be a robust, phishing-resistant authentication infrastructure independent of passwords. This would strengthen cyber security and increase the cost-efficiency of the architecture. The iShield Key 2 series from Swissbit is the leader in hardware authentication.
The new iShield Key 2 MIFARE is the world's first FIDO2 security key that combines digital and physical access in one device.
The iShield Key series supports all relevant protocols and standards, such as FIDO2, FIPS 140-3 Level 3 and MIFARE.
The iShield Key 2 family froms the foundation for a zero trust strategy and supports MFA. It fulfills the regulatory requirements of NIS2, CRA, DORA, the U.S. Executive Order on cyber security, CISA ZTMM and OMB M-22-09.
Conclusion
I am delighted that Swissbit is presenting the technologically advanced iShield Key 2 product. Why is that? Not only does it combine digital and physical access in one device, but it also has a remote update capability and a payment function. At the same time, it guarantees maximum security with certificates such as FIDO2 and FIPS 140-3 Level 3, as well as compliance with international regulations.
Swissbit iShield Key Series website : link
Swissbit original post : link
Contac us :
Phone: +55 11 5507-2627
Email: [email protected]
0 notes
Text
FIDO Authentication Market Size, Share, and Business Outlook 2032
The FIDO Authentication Market Size was USD 1.5 billion in 2023 and is expected to Reach USD 9.90 billion by 2032 and grow at a CAGR of 23.33% over the forecast period of 2024-2032.
FIDO Authentication Market is expanding rapidly as organizations shift toward passwordless authentication solutions to enhance security and user experience. The rise in cyber threats, phishing attacks, and data breaches has accelerated the demand for FIDO (Fast Identity Online) standards. Leading companies and governments are adopting FIDO-based authentication to eliminate reliance on traditional passwords.
FIDO Authentication Market continues to gain traction as businesses prioritize secure and frictionless authentication methods. With biometric authentication, hardware security keys, and mobile-based authentication becoming mainstream, FIDO protocols provide a robust framework for ensuring password-free security. The adoption of FIDO2 and WebAuthn standards is driving the market forward, reducing authentication vulnerabilities and improving compliance with regulatory requirements.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3779
Market Keyplayers:
Yubico (YubiKey)
Auth0 (Identity Platform)
Okta (Okta Adaptive Authentication)
Gemalto (Thales) (SafeNet Trusted Access)
Microsoft (Windows Hello)
Google (Google Authenticator)
Apple (Apple Face ID, Touch ID)
Mastercard (ID Check Mobile)
Amazon Web Services (AWS) (AWS Cognito)
Ping Identity (PingOne)
SecureAuth (SecureAuth Identity Platform)
Ubisoft (Ubisoft Connect Authentication)
Duo Security (Duo Push)
(RSA SecurID)
BioConnect (BioConnect Authentication Platform)
Vasco Data Security (Digipass for FIDO)
OneLogin (OneLogin Adaptive Authentication)
Trustonic (Trustonic Secure User Authentication)
Deep Identity (Deep Identity Authentication Services)
HID Global (HID Approve, FIDO2 Authentication)
Market Trends Driving Growth
1. Increasing Adoption of Passwordless Authentication
Organizations are moving away from traditional passwords due to security concerns. FIDO authentication leverages biometrics, public key cryptography, and hardware-based security to provide a seamless login experience.
2. Expansion of Multi-Factor Authentication (MFA)
With cyberattacks on the rise, businesses are integrating FIDO-based authentication into their MFA strategies. This approach enhances security by combining biometric authentication with cryptographic keys.
3. Government Regulations and Compliance
Regulatory bodies are pushing for stronger authentication frameworks. FIDO standards align with global compliance requirements such as PSD2, GDPR, and Zero Trust security models.
4. Growth in Enterprise and Consumer Adoption
Enterprises, financial institutions, and tech companies are implementing FIDO authentication to enhance security while improving user convenience. Consumers are also embracing passwordless authentication through mobile devices and security keys.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3779
Market Segmentation:
By Component
FIDO Authentication Devices
FIDO Authentication SDKs
FIDO Client SDK
FIDO Server SDK
Services
Technology Consulting
Integration & Deployment
FIDO Certification Services
Support Services
By Application
Payment Processing
PKI/Credential Management
Document Signing
User Authentication
Others
By Industry Vertical
BFSI
Healthcare & Life Sciences
IT & Telecom
Retail & CPG
Government & Defense
Energy & Utilities
Market Analysis and Current Landscape
Key factors influencing market growth include:
Rise in Cyber Threats: As phishing and credential theft increase, businesses are seeking more secure authentication solutions.
Advancements in Biometrics and Hardware Security: Fingerprint, facial recognition, and hardware-based authentication (e.g., YubiKey) are gaining widespread adoption.
Tech Giants Driving Adoption: Companies like Google, Microsoft, and Apple are integrating FIDO authentication into their platforms, making it a global standard.
Regulatory Push for Strong Authentication: Governments worldwide are enforcing stronger authentication measures to mitigate cyber risks.
Despite the positive outlook, challenges such as interoperability issues, integration complexities, and user adoption barriers remain. However, ongoing innovations in authentication technology are addressing these concerns.
Future Prospects: The Road Ahead
1. Expansion Across Industries
FIDO authentication is expected to witness significant adoption in banking, healthcare, e-commerce, and enterprise security as businesses prioritize cybersecurity.
2. Growth of Decentralized Authentication
The rise of decentralized identity solutions and blockchain-based authentication will further enhance the security and privacy of FIDO-based authentication systems.
3. Enhanced User Experience with AI and ML
AI-driven authentication and behavioral biometrics will refine FIDO implementations, reducing friction for users while maintaining high security.
4. Adoption of WebAuthn and FIDO2 in IoT Security
With the growing number of IoT devices, FIDO authentication will play a key role in securing connected ecosystems, preventing unauthorized access.
Access Complete Report: https://www.snsinsider.com/reports/fido-authentication-market-3779
Conclusion
The FIDO Authentication Market is set for exponential growth as businesses, governments, and consumers embrace passwordless authentication. With rising cyber threats and stricter regulations, FIDO standards are becoming the preferred choice for secure and user-friendly authentication. As technology advances, FIDO authentication will continue to evolve, providing a robust foundation for the future of digital security.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#FIDO Authentication Market#FIDO Authentication Market Scope#FIDO Authentication Market Growth#FIDO Authentication Market Trends
0 notes
Text
Ditch the Password! Embracing a Secure Passwordless Future

We've all been there - the frustration of forgotten passwords, the struggle to create complex (yet memorable) combinations, and the constant worry about data breaches. But what if there was a better way? Enter passwordless computing, a revolutionary approach to online security that eliminates the need for passwords altogether.
The Password Problem: A Growing Threat
Passwords have long been the cornerstone of online security. But in today's digital landscape, they've become a liability:
Weak Passwords: Many users create weak, easily guessable passwords, making them vulnerable to brute-force attacks and hacking attempts.
Password Fatigue: The sheer number of online accounts we juggle leads to password reuse, a dangerous practice that puts all your data at risk if one account is compromised.
Phishing Attacks: Deceptive emails and websites can trick users into revealing their passwords, granting access to cybercriminals.
Passwordless Computing: A Secure Alternative
Passwordless computing offers a more secure and user-friendly approach to authentication. Here's how it works:
Multi-Factor Authentication (MFA): Instead of relying solely on a password, passwordless systems use a combination of factors for verification. This could involve your fingerprint, facial recognition, a security token, or a one-time code sent to your phone.
Biometric Authentication: Fingerprint scanners, facial recognition software, and iris scanners leverage your unique physical characteristics for secure login.
Security Keys: Physical tokens or software-based keys provide an additional layer of security by requiring user possession for login.
Benefits of Switching to Passwordless Computing
The advantages of embracing a passwordless future are numerous:
Enhanced Security: Eliminating passwords removes a major vulnerability and makes hacking attempts significantly more difficult.
Improved User Experience: No more struggling to remember complex passwords - passwordless systems offer a faster and more convenient login process.
Reduced IT Costs: Password management and breaches can be a major drain on IT resources. Passwordless systems can help streamline these processes and reduce costs.
Stronger Compliance: For businesses in regulated industries, passwordless authentication can help meet compliance requirements for data security.
Transitioning to Passwordless Systems
Transitioning to passwordless systems involves several steps. Organizations must first assess their current security infrastructure and identify areas where passwordless authentication can be implemented. Next, they should choose the appropriate authentication methods based on their specific needs and user preferences. Finally, it is essential to educate users about the new system and provide ongoing support to ensure a smooth transition.
Passwordless Login Solutions: A Glimpse into the Future
Several innovative passwordless login solutions are emerging:
Fingerprint and Facial Recognition: These technologies offer convenient and secure authentication methods.
FIDO (Fast Identity Online) Alliance: This industry standard promotes interoperable passwordless login solutions.
Zero-Knowledge Proofs: This advanced cryptographic technique allows users to verify their identity without revealing their password.
Passwordless Security Advancements
The field of passwordless security is continuously evolving, with new advancements emerging regularly. Innovations such as behavioral biometrics, which analyze patterns of user behavior, and decentralized identity systems, which provide secure and private identity verification, are pushing the boundaries of what passwordless technology can achieve. These advancements promise to make digital security even more robust and user-friendly in the coming years.
The shift to a passwordless computing future is not just a trend but a necessary evolution in digital security. By embracing passwordless authentication methods, organizations can enhance security, improve user experience, and reduce operational burdens. As technology continues to advance, the transition to passwordless systems will become increasingly seamless, paving the way for a more secure and efficient digital world. The era of passwordless computing is here, and it’s transforming how we protect and access our digital lives.
Whether you’re an individual looking to secure your personal accounts or a business aiming to safeguard sensitive data, understanding and adopting passwordless technology is crucial. The benefits are clear, and the future is passwordless.
0 notes
Link
0 notes
Text
Folks, there a ton of different ways to do 2FA/MFA (Multi-Factor Authentication, just in case we want to talk about more than two factors - but that is rare outside like, stuff that needs clearance)
There are TOTP apps for desktop as well as the common Android/iOS ones. And there are FIDO2 / WebAuthn "security keys" (small physical devices that you plug in or scan) and "passkeys" which are still pretty new, but are starting to be available on most new-ish Windows and Mac computers.
Any time something says "use Google Authenticator" or "use Authy" those are TOTP apps and they all work on the same standard. You can use any TOTP app for any TOTP site.
TOTP apps for Desktop:
WinAuth (Windows) (free)
Authy (Windows, Mac, and Linux (as well as Android/iOS)) (free)
Step Two (Mac (and iOS)) (free)
OTP Auth (Mac (and iOS)) ($5.99 for the desktop version)
Additionally some Password Managers support TOTP... some would argue that by keeping passwords and TOTP in the same app, it isn't really 2FA... technically true, but still better than not using 2FA
Password managers with TOTP support include at least:
Bitwarden (paid, not free tier sadly, personal is $10/y)
1Password (paid, has no free tier)
With these tools, you can select the section of screen with the QR code, or screenshot it, and the app will scan the image. (Rather than the common mobile workflow of pointing the camera of a phone at the QR code on screen)
---
For FIDO2 security keys, there are a number of vendors for the hardware, but the biggest and most established is YubiCo

They have USB A (classic desktop USB port), USB C, and a USB C + Apple Lighting plug models. Both with and without NFC wireless (useful for phones, though with USB C you can plug them in as well). They also have "nano" versions that are designed to be left plugged into the port all the time, or at least the whole time you are working/using the computer, so to sign in to a WebAuthn 2FA site, you just tap it, rather than fumble with a larger key, plug it in, and tap it.
These cost a bit, especially the 5 series which start a $50, but the "Security Key" series which have fewer options and form factors are $25 and $29 (without and with NFC, respectively). The Security Key series works with WebAuthn, and that is all most users will care about. The other fancy features of the 5 series are great for nerds and specialists, but are not something 95% of people are going to care about. These keys are pretty durable in my personal experience (over 5 years, I often keep them on my keychain), it seems to me they should be at most a "once in 10 years" type of expense, if not much longer.
---
The same industry group (FIDO Alliance) that created the FIDO2 and WebAuthn standards has also more recently extended the spec in two ways. One allows phones (almost all even semi-recent ones) as well as many recent Desktop/Laptop computers to become FIDO2 auth devices using existing security chips in the system.
All recent-ish Macs have their version, and... I believe at least any PC that can run Windows 11 can do it (but it will work if they are running 10, and some PCs that can't run 11 still might be able to do it)
But, of course with a physical FIDO2 key, you can use it with many systems, and losing or replacing systems doesn't mean replacing the key, so these built in systems were at a disadvantage. So they made the second extension, creating FIDO2 passkeys. These continue to use the built in security chips in desktops/laptops and phones, but they create a way to share and sync the keys (automatically) between different systems, via your account on the device (Apple account, Microsoft account or Google account).
So you can set up a FIDO2 / WebAuthn 2FA (or Passwordless login) on one device, and any/all devices that you sign into now or in the future with that same account, will be able to use the WebAuthn sign in. (Unfortunately doesn't currently have a way to sync between Google/Apple/MS)
If you are more security conscious, and or are wary of the big tech players, yes, technically FIDO2 Passkeys are more centralized and a bit less secure than a physical Security Key - though they all in all are still quite secure. Most all security pros are going to recommend Passkeys over not having 2FA, certainly, and there is an argument for them over even TOTP. But if you want to avoid the big companies having even indirect control of your stuff (well, you maybe don't even have an Apple or MS account in that case), you may want to go with TOPT or physical keys. For maximum security, pick the physical security keys.
But for the vast majority, Passkeys are perfectly ok, and can be very convenient. Passkeys are still pretty new, and I haven't used them yet, so right now (mid 2023) your mileage may vary. But they piggyback on existing chips, and existing support on websites with WebAuthn, so that is good. Webauthn is not as new, but fairly new, deployment across the web is currently what I would call "medium". Apple, MS and Google accounts all support logging in with WebAuthn, as does Twitter. Tumblr doesn't yet. Lots of tech companies support it... as usual some that could benefit the most from improved security with WebAuthn, like banks and healthcare, don't support it yet.
Oh, also worth keeping in mind, TOTP apps on phone DON'T need network access. If you have or get an old/second hand phone, you just need to connect to wifi long enough to install a TOTP app. Then you don't need network access all (well, good to have wifi access once in a while at least, to keep your clock in sync), and you certainly don't need cell access/a SIM.
I have a friend who actually keeps his TOPT on an old iPod Touch.
Anyway! These are some of the options for cell phone-less (or old phone with no cell plan) 2FA / MFA.
These don't totally solve *all* 2fa issues but they can help in many cases. As WebAuthn becomes more common (and it has been rising steadily), I think we will see more use of it, with physical keys and passkeys, and less TOTP. Physical keys could be great help for people using the library as their main internet access... some cheap ones or community programs to help provide them could be really good.
Also FIDO2 allows for using it as a single factor login aka passwordless login... that is rare currently, but will be a big help for many. Most of your most critical accounts - email, Apple/Google/MS accounts, finance, etc you will want 2fa, but for general internet accounts - social media (depending on how you use it), streaming sites, random forums - all those can and probably should allow WebAuthn passwordless. Username, touch key, done. (Actually there is even a way to skip the username, as the key can provide a unique ID that can be used instead)
Probably at some point as the government starts adopting FIDO2 (and it will, it's just slow), the IRS or SSA or someone should do a program to provide 2 cheap physical FIDO2 keys to anyone below a certain income or some such. (Two, so you have a backup, you can enroll any number of FIDO2 keys/passkeys on any website that implements WebAuthn correctly)
Let me know if you have questions.
resharing this oldie because i just got a new laptop and the number of times i am being required to login to things, login to a DIFFERENT app/program/password manager/authenticator, provide a number, and then login again is making me fucking INSANE
5K notes
·
View notes
Text
FIDO Authentication Market: Projected Revenue Surge by 2033
The FIDO Authentication Market has witnessed remarkable growth, with the total revenue reaching US$ 1,238.6 million in 2022. This impressive growth trajectory is projected to continue, with the market expected to surge to US$ 12,059.7 million by 2033, reflecting a robust Compound Annual Growth Rate (CAGR) of 23.1% from 2023 to 2033.
Get Sample Copy of this Report at: https://www.futuremarketinsights.com/reports/sample/rep-gb-12485
Drivers and Opportunities:
The market’s expansion is driven by several factors, including the increasing adoption of FIDO authentication solutions across various industries. The rising concerns over cybersecurity threats have prompted organizations to seek robust authentication methods, further fueling market growth. Additionally, the growing popularity of biometric authentication methods and the proliferation of mobile devices are providing lucrative opportunities for market players to innovate and expand their offerings.
Competitive Landscape – Regional Trends:
The FIDO Authentication Market is highly competitive, with key players constantly innovating to maintain their market position. Regional trends indicate that North America dominates the market, owing to a high concentration of tech-savvy enterprises and stringent security regulations. Europe follows closely behind, driven by increasing awareness of data security. Meanwhile, the Asia-Pacific region presents significant growth potential due to the rapid digitalization of economies and the need for robust authentication solutions.
Restraints:
Despite its rapid growth, the market faces certain limitations, including concerns related to user privacy and data protection. Striking a balance between stringent security measures and user convenience remains a challenge for market players. Moreover, the high initial costs associated with implementing FIDO authentication solutions may hinder adoption among smaller enterprises.
Region-wise Insights – Category-wise Insights:
Regionally, North America leads the FIDO Authentication Market, with a substantial share of the global market. Within categories, biometric authentication solutions are gaining prominence due to their accuracy and user-friendliness. Moreover, the healthcare and financial sectors are witnessing substantial adoption of FIDO authentication, driven by the need for secure access to sensitive data.
Request for Methodology: https://www.futuremarketinsights.com/request-report-methodology/rep-gb-12485
Competitive Landscape
As organizations around the world are challenged in controlling dynamic and hybrid IT environment, the need for secure mobile or online applications without compromising user convenience is increasing continuously.
Owing to this, most of the leading players in the FIDO authentication technology are coming with advanced and innovative solutions that meets the ever-changing demand from organizations for advanced security and privacy concerns.
In January 2021, Aware, Inc. announced the launch of AwareABIS, an automated biometric identification system (ABIS) used for large-scale biometric identification and deduplication. Designed to serve among 1-30 million identities or more, AwareABIS supports fingerprint, face and iris modalities, and features a modular architecture that helps security teams configure and optimize the system for civil or criminal applications.
FIDO Authentication Outlook by Category
By Solution:
FIDO U2F Authentication Devices
FIDO Authentication SDKs
FIDO Client SDK
FIDO Server SDK
Services
Technology Consulting
Integration & Deployment
FIDO Certification Services
Support Services
By Application:
Payment Processing
PKI/Credential Management
Document Signing
User Authentication
Others
By Industry:
BFSI
Healthcare & Life Sciences
IT & Telecom
Retail & CPG
Government & Defense
Energy & Utilities
Others
By Region:
North America
Latin America
Europe
East Asia
South Asia & Pacific
Middle East and Africa
0 notes
Text
Embrace the passwordless future of passkeys
Have digital passwords has been around since the 1960s, and we haven’t come up with a better option… until now. A tech industry-wide group called the FIDO Alliance aims to get rid of them, and for good reason: Passwords are easy to hack, and hard to remember. The smarter method, they argue, is to scrap difficult passwords altogether and use cryptographic keys for authentication instead. These…
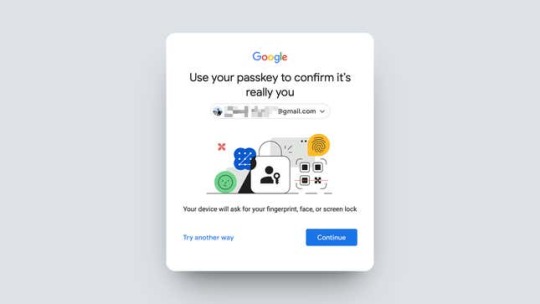
View On WordPress
0 notes
Text
Introducing iShield Key 2: Swissbit's next-generation hardware authenticator
Westford, Massachusetts, USA, May 8, 2025 – Swissbit, a leading manufacturer of storage and security solutions, announces the launch of the iShield Key 2, the next generation of its hardware authenticators. Powered by an NXP chip, the new product family delivers phishing-resistant authentication for enterprises and public sector organizations worldwide, offering a wide range of models and feature sets.

At its core, the iShield Key 2 series is built on the FIDO2 standard, supporting passwordless authentication with market-leading capacity for up to 300 Passkeys. The Pro versions expand functionality to include HOTP and TOTP for generating one-time passwords and PIV for smartcard integration. Setting new standards, the iShield Key 2 MIFARE variant uniquely combines digital and physical access control in a single device. This enables efficient authentication for both IT systems and physical infrastructure such as buildings or secure printing environments. For customers with the highest security requirements, a FIPS 140-3 Level 3 certified version is also available. All models are housed in a compact, lightweight, and rugged industrial-grade casing – engineered and manufactured at Swissbit’s facility in Berlin, Germany.
Comprehensive portfolio, maximum flexibility
At launch, the iShield Key 2 is available with USB-C, with USB-A variants scheduled for release by end of Q2 2025. All models support NFC for contactless use. The portfolio consists of three main lines: iShield Key 2, iShield Key 2 MIFARE, and iShield Key 2 FIPS. Each line is available in a base FIDO2-only version and a Pro version supporting HOTP, TOTP, and PIV. This breadth allows organizations to select the authenticator that best fits their specific requirements and use cases.

Physical access control and beyond
Thanks to NXP’s advanced chip technology, the iShield Key 2 MIFARE supports DESFire EV3, enabling true hybrid usage. This allows the key to integrate seamlessly into daily workflows and support custom applications based on MIFARE technology – ideal for use cases such as time tracking, cafeteria payment, or campus ID cards. Swissbit also offers optional support for leading access control technologies such as HID SEOS and LEGIC advant / LEGIC neon, providing customers with the flexibility to integrate the key into existing systems and infrastructures.
Security and certifications
All iShield Key 2 models are FIDO-certified and support OpenSC for open smartcard integration. For deployments with stringent compliance needs, the FIPS 140-3 Level 3 certified version ensures adherence to top-tier security standards. Variants with Enterprise Attestation are also available, allowing organizations to restrict access to verified, company-issued security keys.
Update Capabilities
All iShield Key 2 models can be remotely updated by using secure channel protocols which allows the provisioning of new firmware versions and applications to devices in the field.
“With the iShield Key 2, we are delivering a universal security key that not only meets the evolving demands of digital identity but also sets new standards for physical access control,” said Claus Gründel, General Manager Security Solutions at Swissbit. “This product line represents a major leap forward in authentication technology and gives our customers maximum flexibility and control across their security infrastructure.”
Swissbit Original Post : link
Swissbit iShield Key website : link
Contac us :
Phone: +55 11 5507-2627
Email: [email protected]
0 notes
Text
#loginsecurity#solution#strongpassword#cyberattack#passwordsecurity#passwordlessauthentication#informationtechnology#auth#web#machinelearning#ios#android#userauthentication#otp#logindetails#hacking#futureprotected#logindata#windowshello#secure#loosedata#rainbowsecurity#style#lock#future#safe#kyc#biocertica#privateblockchain#safer
0 notes
Text
Cloud Authentication Market Share, Development by Companies Outlook, Growth Prospects & Key Opportunities by 2022-2032
A recent market analysis by Future Market Insights predicts that the cloud authentication market is worth US$ 11,279.2 million in 2022. Over the projection period, a CAGR of 14.4% is expected to be achieved in the market.
The BFSI industry is among those with the highest information sensitivity. Cloud authentication is being aggressively adopted by the sector to safeguard client data and guard against fraud and data breaches.
Most telecom and IT organizations are embracing the Bring Your Own Device (BYOD) trend, which is anticipated to accelerate the market for cloud authentication as a service. E-commerce is also among the most cost-conscious industries and one of the companies that hackers target the most owing to the possibility for payments and the vast amount of financial transactions made using credit and debit cards.
Request a Sample Copy of this Report @ https://www.futuremarketinsights.com/reports/sample/rep-gb-15817
Adopting cloud authentication is therefore seen as the most secure choice for companies.
Over the years, both large enterprises and SMEs have primarily used cloud authentication. Features like automatic user account provisioning, workflow and self-service management, Single Sign-On (SSO), password management, and access governance are useful for large enterprises.
However, the more authentication elements there are, the longer it takes to complete a single task. Fraudsters can also quickly obtain a user's physical sim card and access IDs by using methods like sim swapping or switching. These factors are anticipated to restrict the growth of the cloud authentication market.
Key Takeaways
The cloud authentication market is likely to have a CAGR of 14.4% during the forecast period.
Historically, the cloud authentication market had a CAGR of 12.6% between 2017-2021.
The value of the cloud authentication market is expected to be US$ 12,753.4 million by 2032.
Based on type, the multifactor authentication segment has a 68% share in the cloud authentication market.
Based on the enterprise size, the very large enterprise (1000+ employees) dominated the market share by 26% in 2021.
North America dominated the cloud authentication market with a share of 32.9% in 2021.
During the forecast period, the cloud authentication market in South Asia & Pacific is likely to showcase the growth of 22.5%.
Immense Prospects For Major Key Players
IBM, Microsoft, CA. Inc, Secureworks Inc, Oracle Corporation, Intel Corporation, Onelogin Inc, Hewlett Packard Enterprise Development LP, Sailpoints Technology Holdings Inc, and Ping Identity are some of the major players in the cloud authentication market.
Manufacturers must focus on creating linked production processes that allow them to pinpoint potential growth opportunities and create new revenue streams.
IBM released the security IAM suite V1.0 in August 2020. Access manager, security identity governance and intelligence, security directory suite, and security identity manager are among the security tools included in the latest version.
Oracle released an improved version of their IAM solutions in November 2020. (Oracle Identity Cloud Service). It enables typical IDaaS use cases, including social login, password-less login, strong and adaptive authentication, bidirectional synchronization to on-prim, and others.
The creation and advancement of open standards for safe authentication are the main objectives of a worldwide business organization known as the FIDO Alliance.
Key Players
IBM
Microsoft
CA. Inc
Secureworks Inc.
Oracle corporation
Intel Corporation
Get More Information on this Report @ https://www.futuremarketinsights.com/reports/cloud-authentication-market
Key segments
By Type:
Single
Multifactor
By Enterprise Size:
Small Offices (1-9 employees)
Small Enterprises (10-99 employees)
Medium-sized enterprise (100-499 employees)
Large Enterprises (500-999 employees)
Very Large Enterprises (1000+ employees)
By Industry:
Service
Distribution Services
Public Sector
Finance
Manufacturing Resources
Infrastructure
By Region:
North America
Latin America
Europe
East Asia
South Asia and Pacific
Middle East & Africa
0 notes
Text
0 notes
Text
OPPO Joins the FIDO Alliance, Accelerating the Arrival of a New Era of Passwordless Sign-ins
OPPO Joins the FIDO Alliance, Accelerating the Arrival of a New Era of Passwordless Sign-ins
The replacement of traditional password-based authentication mechanisms with leading passwordless technology will allow OPPO users to benefit from faster, more convenient, and more secure logins across different accounts, services, and platforms OPPO recently announced that it has joined the FIDO (Fast IDentity Online) Alliance, an open industry association with a mission to develop…

View On WordPress
0 notes
Link
The global FIDO Authentication Market is fueled by various factors, according to a detailed assessment explained in the report. This study shows how important in-depth analysis should be, and how it greatly affects the quality of information provided to the readers. Further, the report also takes into account the impact of the novel COVID-19 pandemic on the FIDO Authentication market and offers a clear assessment of the projected market fluctuations during the forecast period.
0 notes