#Features and Benefits of GCM
Text
Sell GCM or ALCA to wealth managers?
What makes 3rd Parties Like Wealth Managers Refer to Care Managers?
Do you want to sell to wealth managers? Why would third parties like wealth managers trust officers, sell to GCM or ALCA by referring clients to a care manager If you have an Aging Life or GCM business you need to know. It is the benefits you bring to the 3rd party and their aging client.
Benefits you bring to the 3rd…

View On WordPress
#aging family#aging life care manager#aging parent care#aging parent crisis#benefits of ALCA#Benefits Of Geriatric Care Managers#benefits to 3rd parties#Benefits to Wealth Managers#Benefits VIP Clinets#care manager#Features and Benefits#Features and Benefits of GCM#geriatric care manager#marketing to wealth manager#nurse advocate#nurse care manager#Sell Benefits#wealth managers#webinar Benefit or Features#Webinar Features and Benefits
0 notes
Text
does surfshark vpn have indian servers
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does surfshark vpn have indian servers
Surfshark VPN Indian server locations
Surfshark VPN offers a variety of server locations in India, providing users with seamless and secure access to the internet while maintaining their privacy and security. Indian users can take advantage of Surfshark's server locations in cities like Mumbai, New Delhi, Chennai, and Bengaluru, allowing them to enjoy fast and reliable connections for streaming, browsing, and gaming.
By connecting to a server in India through Surfshark VPN, users can overcome geo-restrictions and access region-locked content such as Indian TV shows, movies, and sports events from anywhere in the world. This is especially useful for travelers or expats who want to stay connected to their favorite Indian entertainment while abroad.
In addition to accessing geo-restricted content, Surfshark's Indian server locations also offer users enhanced online security and privacy. By encrypting all internet traffic with strong AES-256-GCM encryption, Surfshark VPN ensures that users' sensitive data remains protected from hackers, ISPs, and government surveillance.
Furthermore, Surfshark's Indian servers support features like CleanWeb, which blocks ads, trackers, and malware to provide users with a clean and uninterrupted browsing experience. Users can also benefit from Surfshark's NoBorders mode, which helps bypass internet censorship in countries with strict online restrictions.
Overall, Surfshark VPN's server locations in India provide users with a reliable, fast, and secure internet connection, allowing them to enjoy unrestricted access to Indian content and enhanced online privacy.
Surfshark VPN server presence in India
Surfshark, a popular VPN service provider, has an extensive server presence in India, catering to the growing demand for online privacy and security in the region. With the increasing reliance on the internet for various activities, such as streaming, online banking, and remote work, the need for a reliable VPN service like Surfshark has never been higher.
Surfshark offers users in India access to a wide network of servers strategically located across the country. This extensive server presence ensures that users can enjoy fast and stable connections while browsing the internet anonymously. By connecting to a Surfshark server in India, users can also bypass geo-restrictions and access region-locked content on popular streaming platforms like Netflix, Amazon Prime, and Hotstar.
Furthermore, Surfshark's presence in India enhances online security by encrypting users' internet traffic and protecting their personal information from potential cyber threats. With features like MultiHop, CleanWeb, and Whitelister, Surfshark provides users with a comprehensive solution to safeguard their online privacy and data security.
In conclusion, Surfshark's robust server presence in India not only offers users in the region fast and secure internet connections but also empowers them to access global content and protect their sensitive information online. Whether for streaming, gaming, or remote work, Surfshark VPN is a reliable companion for internet users in India seeking a safe and unrestricted online experience.
Surfshark VPN server network in India
Surfshark, a renowned VPN service provider, has expanded its server network in India, catering to the growing demand for secure and unrestricted internet access in the region. With an increasing number of users seeking reliable VPN solutions, Surfshark's strategic expansion aims to offer enhanced connectivity, privacy, and accessibility to its customers in India.
The addition of servers in India reinforces Surfshark's commitment to providing fast and reliable connections for users across the country. By deploying servers in key locations, Surfshark ensures optimized performance and minimal latency, allowing users to browse, stream, and download content with ease.
One of the primary benefits of Surfshark's VPN server network in India is its ability to bypass geo-restrictions and access region-locked content. Whether users want to stream their favorite movies and TV shows on platforms like Netflix, Hotstar, or Amazon Prime Video, Surfshark's Indian servers provide seamless access to a wide range of content libraries.
Moreover, Surfshark's servers in India prioritize user privacy and security. With advanced encryption protocols and a strict no-logs policy, users can browse the internet anonymously without compromising their sensitive information or online activities.
In addition to accessing geo-restricted content and ensuring online security, Surfshark's VPN servers in India offer benefits such as circumventing censorship, protecting against cyber threats, and maintaining digital privacy.
Overall, Surfshark's expansion of its server network in India signifies its dedication to meeting the evolving needs of users in the region. With optimized performance, robust security features, and access to global content, Surfshark continues to be a top choice for VPN users in India and beyond.
Surfshark VPN India server availability
Surfshark, a popular VPN service provider, offers users in India the convenience of accessing servers located within the country. The availability of India servers through Surfshark allows users to enjoy a secure and private internet connection while accessing local content and services.
With Surfshark's India server presence, users can bypass geo-restrictions and access region-locked content such as streaming services, news websites, and other online platforms exclusively available in India. By connecting to a local server, users can enjoy fast and stable connections, ensuring smooth browsing, streaming, and downloading experiences.
Surfshark's India servers also offer added privacy and security benefits to users in the region. By encrypting internet traffic and masking IP addresses, Surfshark helps users protect their sensitive data from potential cyber threats, surveillance, and monitoring. The India server option enables users to browse the internet anonymously and safeguard their online activities from prying eyes.
Moreover, Surfshark's India servers provide users with the ability to circumvent internet censorship and restrictions imposed by ISPs or government authorities. By connecting to a server within India, users can enjoy unrestricted access to the internet and uphold their digital freedom and rights.
In conclusion, Surfshark's availability of servers in India enhances the VPN experience for users by offering them enhanced online security, privacy, and access to region-specific content. Utilizing Surfshark's India servers can significantly benefit users seeking a reliable VPN service tailored to their needs in the region.
Surfshark VPN Indian server coverage
Surfshark VPN extends its robust network coverage to India, offering users unparalleled access to the internet while ensuring privacy and security. With servers strategically located across various regions in India, Surfshark ensures seamless connectivity and high-speed performance for its users.
The Indian server coverage provided by Surfshark VPN allows users to bypass geo-restrictions and access content that may be otherwise unavailable in their region. Whether it's streaming platforms, social media websites, or news outlets, users can enjoy unrestricted access to their favorite online content with just a click of a button.
Moreover, Surfshark's Indian servers offer enhanced privacy and security features, including encryption protocols that safeguard users' online activities from prying eyes. This means that users can browse the internet, stream content, and download files without having to worry about their sensitive information falling into the wrong hands.
Additionally, Surfshark VPN's Indian server coverage enables users to maintain anonymity while browsing the web. By masking their IP addresses and encrypting their internet traffic, users can protect their online identity and maintain their privacy, even when accessing the internet from public Wi-Fi networks.
Whether you're a resident of India looking to access geo-blocked content or a traveler needing a secure internet connection while in the country, Surfshark VPN's Indian server coverage has you covered. With its reliable performance, robust security features, and extensive network coverage, Surfshark VPN remains a top choice for users seeking a safe and unrestricted internet experience in India and beyond.
0 notes
Text
Complete Guide to Canada GCMS Notes 2023 with IMygrate

GCMS Notes Canada: Enhancing Immigration and Visa Processing
GCMS Notes (Global Case Management System) in Canada is a pivotal tool transforming the immigration and visa processing landscape. This state-of-the-art system empowers immigration authorities with streamlined case management capabilities, allowing for efficient handling of applications, appeals, and inquiries.
By leveraging GCMS Notes, immigration officers gain valuable insights into an applicant’s history, status, and documentation, enabling well-informed decisions on visa approvals and rejections. The platform’s secure data storage ensures sensitive information remains confidential, safeguarding applicants’ privacy.
With its user-friendly interface and real-time updates, GCMS Notes Canada plays a significant role in expediting immigration processes, reducing delays, and promoting fair and objective assessments for a diverse range of applicants seeking entry into the country.
GCMS Notes Processing Time 2023: Optimizing Efficiency and Timeliness

In 2023, the Global Case Management System (GCMS) continues to evolve, setting new benchmarks in processing efficiency and reducing turnaround times for various applications and cases. As immigration authorities and legal professionals leverage the system’s advanced features, the processing of visas, immigration applications, and other legal matters undergoes a transformative shift.
GCMS Notes Processing Time 2023 benefits from the continuous advancements in technology, data analytics, and machine learning algorithms, resulting in quicker and more accurate assessments. The streamlined workflow and improved collaboration among stakeholders enable smoother case management and foster timely resolutions.
Through relentless commitment to innovation and client-centricity, GCMS Notes Processing Time 2023 stands as a testament to the pursuit of excellence in global case management, making a significant impact on individuals, businesses, and legal entities alike.
GCMS Notes Tracking IRCC: Staying Updated on Immigration Cases

GCMS Notes Tracking IRCC (Immigration, Refugees, and Citizenship Canada) is a valuable service that allows applicants and authorized representatives to monitor the progress of immigration applications and requests in real-time. By accessing the Global Case Management System (GCMS) notes, individuals can stay informed about the status of their visa applications, permanent residency, work permits, and other immigration-related matters.
This tracking system offers transparency and convenience, enabling applicants to know exactly where their cases stand and if any additional information or documents are required. By using GCMS Notes Tracking IRCC, applicants can proactively address any potential issues, ensuring a smoother and more efficient immigration process.
GCMS Notes Apply Online: A Digital Gateway to Immigration Updates
GCMS Notes Apply Online is a revolutionary service that brings convenience and efficiency to the world of immigration applications. As part of the Global Case Management System (GCMS), this online platform allows applicants and authorized representatives to request and access detailed notes and updates related to their immigration cases.
Through a user-friendly interface, applicants can submit a request to obtain their GCMS notes, providing them with valuable insights into the status and progress of their applications. The platform expedites the process of obtaining crucial information, eliminating the need for cumbersome paperwork and long waiting times.
Applicants can monitor their case’s timeline, view any updates made by immigration authorities, and stay informed about any additional documentation or actions required. This transparency fosters a sense of empowerment and allows applicants to be proactive in addressing any potential issues that may arise during the processing period.
By embracing GCMS Notes Apply Online, immigration authorities streamline their operations, saving valuable time and resources. The digital platform enables quicker access to case information, facilitating better decision-making and improved communication between all stakeholders involved.
Overall, GCMS Notes Apply Online is a game-changer in the realm of immigration, providing a seamless and efficient way for applicants to stay connected with their cases and ensuring a smoother, more transparent immigration process for all parties involved.
GCMS Notes Visa Rejection: Understanding the Decision Process
GCMS Notes play a crucial role in shedding light on the reasons behind a visa rejection. When an individual’s visa application is denied, it can be a disheartening and frustrating experience. However, GCMS Notes offer valuable insights into the decision-making process, providing applicants with a better understanding of why their application was not successful.
Within the Global Case Management System (GCMS), immigration officers meticulously document the reasons for visa refusals. These notes outline any discrepancies in the application, insufficient supporting documentation, or other relevant factors that led to the unfavorable decision.
By requesting and reviewing their GCMS Notes after a visa rejection, applicants gain an opportunity to identify areas for improvement in future applications. Understanding the specific grounds for refusal enables individuals to address any weaknesses or errors in subsequent visa applications, thereby increasing their chances of success.
Moreover, authorized representatives assisting applicants can use the information from GCMS Notes to provide better guidance and ensure future applications are meticulously prepared to meet the immigration requirements.
While a visa rejection can be disheartening, it is essential to view it as an opportunity to learn and improve. By leveraging the insights provided by GCMS Notes, applicants can navigate the visa application process more effectively, ultimately increasing their chances of a successful outcome in their future endeavors to travel, study, work, or reside in the desired destination.
Canada Visitor Visa Processing Time After Biometrics 2023 from India
FAQs:
How to Check the Status of GCMS Notes:
Unfortunately, there is no direct way for individuals to check the real-time status of their GCMS notes. Once you have applied for GCMS notes, you will have to wait until they are processed and made available to you by the relevant authorities.
How to Check the Status of GCMS Notes Application in Canada:
To check the status of your GCMS notes application in Canada, you can contact the Immigration, Refugees, and Citizenship Canada (IRCC) or the relevant visa office where you submitted your application. They will be able to provide you with information on the current status of your GCMS notes request.
How to Understand GCMS Notes:
Understanding GCMS notes can be challenging for those without a background in immigration or legal matters. GCMS notes are detailed records created by immigration officers during the processing of immigration applications. It is recommended to seek assistance from a qualified immigration representative or lawyer who can interpret the notes and provide you with insights into your case.
How to Read GCMS Notes
Reading GCMS notes requires familiarity with the terminology and abbreviations used in immigration and legal contexts. As mentioned earlier, it is best to seek professional help to read and interpret the notes accurately.
How to Apply for GCMS Notes
To apply for GCMS notes, you can submit a request to the relevant Canadian visa office or the IRCC. The request must be made in writing, and you may be required to provide specific details about your application, such as the date it was submitted and the type of visa or permit you applied for.
How to Apply for GCMS Notes Canada:
To apply for GCMS notes in Canada, follow the process mentioned in point 5 above. Submit your request to the IRCC or the appropriate visa office in Canada.
How to Apply for GCMS Notes IRCC:
Applying for GCMS notes from IRCC follows the same process mentioned earlier. Submit a written request with relevant application details to the IRCC.
How to Apply for CAIPS Notes from India:
CAIPS (Computer Assisted Immigration Processing System) notes are no longer available. As of September 2021, CAIPS was replaced by the GCMS system for all immigration applications.
How Do I Apply for GCMS Notes:
You can apply for GCMS notes by submitting a written request to the IRCC or the appropriate visa office, as mentioned earlier.
How Long Does GCMS Notes Take:
The processing time for GCMS It may take several weeks to receive the notes.
How Long Does It Take to Receive GCMS Notes:
Receiving GCMS notes usually takes several weeks from the date of your request. The processing time may be longer during peak application periods.
Why Is GCMS Important:
GCMS is essential for immigration authorities as it helps manage and track immigration cases efficiently. It provides a comprehensive record of an applicant’s immigration journey, aiding in decision-making and ensuring transparency in the process.
How Many Days It Takes to Get GCMS Notes:
The number of days it takes to receive GCMS notes can vary. On average, it may take around 30 to 60 days, but this can be longer during busy periods.
#GCMS Notes#apply gcms notes ircc from india#ircc gcms notes#GCMS Notes canada#GCMS Notes from india
0 notes
Text
openGauss|High Availability (HA):DCF
DCF
Availability
This feature is available since openGauss 2.0.0.
Introduction
Distributed consensus framework (DCF) implements data synchronization based on the Paxos algorithm. After the DCF mode is enabled, DNs support Paxos-based replication and quorum capabilities.
Benefits
Primary DN selection and log replication are performed based on Paxos. Compression and flow control are supported during the replication to prevent high bandwidth usage. DCF provides capabilities such as log replication and cluster HA. DCF supports automatic leader election, forcible minority startup, and dynamic traffic adjustment for log replication. In addition, multiple Paxos-based roles are provided and can be adjusted. You can query the instance status in the current database.
DCF is a high-performance, highly mature, reliable, scalable, and easy-to-use independent basic library. Other systems can easily interconnect with DCF through interfaces to obtain the strong consistency, high availability, and automatic disaster recovery capabilities provided by the Paxos algorithm.
Description
During log replication, DCF supports log compression before transmission to reduce network bandwidth usage.
DCF supports SSL, including TLS 1.2 and TLS 1.3. When SSL is enabled, the DN configures DCF as TLS 1.2 by default.
DCF supports five TLS 1.3 cipher suites: TLS13-AES-256-GCM-SHA384, TLS13-CHACHA20-POLY1305-SHA256, TLS13-AES-128-GCM-SHA256, TLS13-AES-128-CCM-8-SHA256 and TLS13-AES-128-CCM-SHA256.
DCF supports passive nodes, which do not participate in leader election and only synchronize and replay logs. When this type of nodes is heavily loaded during log synchronization, flow control is performed.
DCF supports logger nodes, which participate in leader election and voting. However, the logger nodes only replicate DCF logs. Xlogs are not replicated and redo is not performed.
DCF supports online switchover between follower and passive nodes. That is, without interrupting services, a node can switch over between the follower and passive roles.
DCF supports forcible startup of the minority of DNs. In case that the majority of database instances are faulty, a minority of standby DNs are selected and forcibly promoted to primary, and other normal standby DNs replicate logs from the primary DNs.
DCF supports automatic leader election. When the original primary DN is faulty, a new primary DN is automatically selected from the remaining standby DNs on the premise that data consistency is ensured.
DCF supports the policy-based majority capability. Based on the configured AZ, DCF ensures that at least one node in the AZ synchronizes replication logs.
Enhancements
None.
Constraints
To use this function, you need to enable DCF during installation and deployment. In DCF mode, the majority election is used. During the installation, if the number of faulty nodes and build nodes reaches the majority, the cluster installation will fail. For example, when one primary node and two standby nodes are installed, one node fails to be installed due to insufficient memory, but the other two nodes can be started normally. A standby node will be built again. In this case, the number of build nodes and faulty nodes is 2, which is the majority, and the cluster installation will fail. During the installation, check whether the memory and disk resources are sufficient.
If the policy-based majority parameter is configured for an AZ and all nodes in the AZ are faulty, you need to remove the AZ configuration from the policy-based majority configuration when performing build operations on the nodes.
The manual mode is used to set the cluster-level working mode. In this mode, the logger or passive role is not supported.
Dependencies
None.
0 notes
Text
5 Benefits Of Native Mobile App Development
1. Native Apps Have the simplest Performance
With native mobile app development, the app is made and optimized for a selected platform. As a result, the app demonstrates a particularly high level of performance. Native apps are in no time and responsive because they're built for that specific platform and are compiled using platforms core programming language and APIs. As a result, the app is far more efficient. As users navigate through a native mobile app, the contents and visual elements are already stored on their phone which suggests load times are quick.
2. Native Apps Are safer
Web apps believe different browsers and underlying technologies like JavaScript, HTML5, and CSS. Developing a native mobile app may be a good way to ensure your users reliable data protection.
3. Native Apps Are More Interactive And Intuitive
Native mobile apps run much smoother regarding user input and output. These sorts of apps inherit their devices’ OS interfaces, making them look and desire an integrated a part of the device.
The most advantageous benefit to native mobile apps is that the superior user experience. Native apps are created specifically for an OS . They stick with the rules that ultimately enhance and align the user experience with the precise OS . As a result, the flow of the app is more natural as they need specific UI standards for every platform. this enables the user to find out the app, like deleting a component quickly. Adhering to specific guidelines eliminates the training curve and allows users to interact with apps using actions and gestures they’re conversant in already.
4. Native Apps Allow Developers To Access the complete Feature Set Of Devices
Native apps are developed for his or her particular platform, taking full advantage of the software and therefore the operating systems’ features. These apps can directly access the hardware of the device like the GPS, camera, microphone, etc. in order that they are faster in execution, which ultimately leads to better user experience. Push notifications are another huge advantage to picking native app development. Push notifications undergo the iOS server (APNS) which you would like your app bundle ID and same with Google’s Cloud Messaging (GCM).
5. Native App Development Tends to possess Fewer Bugs During Development
It’s far more difficult to take care of two different applications in one codebase than it's two applications in two codebases. With native app development, you've got fewer dependencies for bugs. Hybrid apps access hardware through a bridge which frequently slows development down and may amount to a frustrating user experience. Due to this time interval , users of native applications have access to new platform features once they update the OS .
The disadvantage of getting to attend for the third-party developer of the hybrid tool to implement the bridge to new OS features. whenever new features are released within the UI kit, we'd like to attend for the tool to support it. once you develop a hybrid app, there’s another layer that you simply don’t have control over which may increase the probabilities of bugs occurring. Bugs are an enormous concern for hybrid app development when working with the newest features that are released for a specific OS . this is often an important and sometimes overlooked a part of generating loyalty among users.
Are you looking for best mobile application development company in Udaipur? object developer are providing best services in affordable prices.
1 note
·
View note
Text
PAF DAO Launches Island Bazaar to Explore Blockchain Asset Potential

Crypto enthusiasts will soon be able to trade a range of assets in one place, no matter the blockchain they are based on. The PAF DAO, a decentralized autonomous community being built by Pitch Finance and Flocki Finance, will provide smooth user experience for buying, selling, trading and tokenizing any kind of asset, token and non-fungible token (NFT) across multiple blockchains.
PAF DAO, a merger of Pitch Finance and Flocki Finance protocols was announced today by the PAF team. The announcement follows the announcement of DAOstack launching the Non-Fungible Token Standard (NFT) earlier this week.
Flocki Finance helps Crypto enthusiasts around the world build, buy, sell, trade, manage and transfer any kind of asset, token or NFT in diverse blockchains.
This week, Pitch Finance and Flocki Finance announced they will merge into one. The companies will combine their protocols in to PAF DAO, a decentralized autonomous organization that auto-executes smart contracts in exchange for payment in the PAF token. The new protocol will serve as a bridge between IPFS, Ethereum and all of the blockchains supporting smart contract adoption.
Flocki Finance and Pitch Finance together have higher value as PAF DAO by merging their protocols in order to get more ICO, STO, and ITO projects from all over the world.
We’re crossing blockchains! We will merge PAF DAO the DAO of our new Flocki Finance token with the old Pitch Finance protocol.
Pitch-Finance is the world's first Token designed to work with the Etherum protocol. This token has the ability to handle all kinds of assets, tokens, and Non-fungible-tokens. Its 100% Etherium compatible. The Pitch-finance DAO is powered by Flocki Finance team which consists of highly talented economists, developers and researchers.
Crypto enthusiasts have agreed to merge the best features of two protocols, Pitch Finance and Flocki Finance. Being a part of this DAO means that you can earn more profits. Economic empowerment is at the top of their agenda.Pitch Finance has signed a DAO agreement, absorbing Flocki Finance's underlying protocol. Each share of Pitch Finance will now be valued as part of the DAO infrastructure and offer token holders "flocking" benefits. Together, the companies have made a move to increase compatibility between blockchains in various industries, allowing entrepreneurs more options for expansion avenues.
Play Pitch Finance, which is a special game that combines TCR, NFT, RTA and DAO technologies, uses the EOS Blockchain Consensus. The world's first theme park using "Blockchain + AR / VR" technology as Tokenized NFC smart ticketing. Using ERC-721, provides additional value to Crypto enthusiasts in multiple ways. It can be used in different places at the same time, reducing costs and simplifying the parking process.
Pitch Finance and Flocki Finance have agreed to merge into a collaborative organization called "PAF DAO" to help support EOS. PAF is short for Pitch and Flocki. The parent company, "PAF DAO" is part of the greater EOS Nation community that aims to fundraise in order to vote and claim EOS tokens, as well as secure leverage for use in the future.
PAF DAO, a newly formed protocol anchored in both Pitch Finance and Flocki Finance protocols. They have decided to merge and operate as one common protocol within the new DAO framework which has been implemented using the JACT Framework.
We are excited to announce that, as of April 15, 2019, Pitch Finance (PF) will be merged with Flocki Finance and become a decentralized autonomous organization called PAF DAO.
Pitch Finance has a made a decision to upgrade Pitch DAO into PAF DAO; all ERC-20 PITCH, GCM, GCN, and all the native assets on PAF chain will be frozen for two months. After two months for PAF users, we will release a new blockchain--PAF chain. And, all assets in the protocols of Pitch Finance are migrating by one-to-one to the new platform and protocol. For example, if you have 20 ETH worth tokens in Pitch Finance [PAF 1], you will receive 20 ETH worth tokens of PAF chain [PAF 2].
This Treaty will improve flocking for the Crypto world. Crypto enthusiasts can enjoy a better world through better flocking and asset management.
For More Information :
Website: https://www.pafdao.com/
Telegram: https://t.me/PAFDAO
Twitter: https://twitter.com/pafdao
Facebook: https://www.facebook.com/PAFDAO
Instagram: https://www.instagram.com/pafdao/
Author:
Btt Username: Ryoko Kenshin
Btt Profile Link: https://bitcointalk.org/index.php?action=profile;u=3398199
BSC Wallet: 0x7aB0483F92b56c1B43e37f03fa5782Ffdcf1A4B4
0 notes
Text
Major advantages of native app development
Many organisations have made developing a mobile app a top priority, but deciding on a development plan can be difficult because the lines between the various options are becoming increasingly blurred. In our previous essay, A Guide to Mobile App Development: Web vs. Native vs. Hybrid, we outlined the three options and discussed their merits and cons. This essay will go into Native Mobile App Development in greater depth, as well as the benefits of using this technique of development.

What Is Native App Development for Mobile Devices?
Native best apps development company Bangalore requires developing apps for unique mobile operating systems that can be downloaded from specialised app stores by users (such as the App Store or Google Play). If you want to create an app for iPhone application development company India , you'll need to use the Objective-C or Swift programming languages.Developing on Android, on the other hand, necessitates the use of the Java or Kotlin programming languages.
Apple and Google both offer their own set of development tools, UI components, and SDKs to app developers. The majority of businesses will engage in native mobile app development due to the numerous advantages it provides over other types of apps, such as hybrid or web apps. Because mobile software is becoming more and more of a need for businesses, it's critical that they understand the benefits and drawbacks of various app development approaches. The following are the main advantages of developing native mobile apps:
Native apps deliver the best results.
The app is designed and customised for a certain platform with native mobile app development. As a result, the app operates at a very high degree of efficiency. Because native apps are created for a single platform and compiled using the platform's core programming language and APIs, they are extremely fast and responsive. As a result, the software is far more effective. The app is installed on the device, allowing the software to utilise the device's processing power. A native best mobile app development companies in bangalore data and graphic elements are already stored on the user's phone, resulting in quick launch speeds.
Native Apps Are More Secure
Different browsers and underlying technologies such as JavaScript, HTML5, and CSS are used in web apps. Developing a native mobile app is a wonderful way to give secure data security to your consumers.
Native apps are more interactive
In terms of user input and output, native mobile apps run significantly more smoothly. These apps take on their device's iOS apps development companies India interfaces, giving them the appearance of being a fully integrated part of the device.
Native apps provide developers access to a device's whole feature set.
Native apps are created specifically for a platform, utilising all of the software and operating system characteristics. These Android app development company India are faster to execute because they have direct access to the device's hardware, such as the GPS, camera, and microphone. This results in a better user experience.Push notifications are another key advantage of native app development.. Push notifications are sent through the iOS server (APNS), which requires your app bundle ID, and Google Cloud Messaging is the same (GCM).
0 notes
Text
GCM Benefits Close the Sale to Assisted Living
Marketing Tactics – Use Benefits
GCM Benefits led to a sale.ALCA members need to sell the benefits of Geriatric Care Management to assisted living. Care managers are perfect professionals to help assisted living residents if they have just moved in, are unhappy with the move, are not participating in activities isolating, or are general when they are not thriving in the resident…

View On WordPress
#aging family#aging life care manager#aging parent crisis#Benefits#Benefits Care Managers#benefits of ALCA#Benefits of care management#Benefits to assisted Living#Benefits vs Features#black american geriatric care managers#black american social workers#Black Nurse Entrepreneurs#Black RN&039;s#Black start-up geriatric care management#Black travel nurses#care manager#case manager#Features and Benefits of GCM#features of ALCA#GCM & Assisted Living#GCM Products and Services#Geriatric Care Sales Assisted Living#geriatric social worker#Marketing to Assisted Living#Monitoring Assisted Living Care#nurse advocate#nurse care manager#Quality of Life in Assisted Living
0 notes
Photo

NVIDIA Scales the Cloud With a Reimagined Data Processing Unit (DPU) Https://www.slw-ele.com; Email: [email protected]
NVIDIA’s GPU Technology Conference has yet again served as a launchpad for the company’s newest DPU. , the chip is reported to feature exceptional performance for AI applications, accelerated computing, and more. What improvements have been made in NVIDIA's BlueField line? And what is the company's roadmap for this DPU moving forward?
Performance Highlights of BlueField-3
The NVIDIA BlueField-3 . The company explains this feature leverages Ethernet-and-fiber channels to facilitate data transmission between remote resources—essential for hybrid and cloud computing setups with off-site servers. Traditional NVMe devices often fall short due to their direct PCIe bus connections.

The NVIDIA BlueField-3 data processing unit. Image used courtesy of
Fabrics-based NVMEs are renowned for their low latency. According to NVIDIA, BlueField-3 is the first DPU to support PCIe 5.0, even offering 32 lanes with bi-furcation for up to 16 downstream ports.
Those connectivity delays can undermine overall networking performance—a major BlueField-3 highlight. It remains the so-called "industry’s first 400 Gbps DPU" and accomplishes this via Ethernet or InfiniBand. The latter has been a longstanding staple of supercomputing switching, underscoring the technology’s viability for demanding workloads.
BlueField-2 vs. BlueField-3
In the past, All About Circuits contributor Nicholas St. John pointed out that while .
NVIDIA is putting this principle into play by , the NVIDIA DGX SuperPOD. Whether BlueField-3 becomes the centerpiece of a successor (e.g., “SuperPOD 2”) is unclear, though NVIDIA would ideally use home-grown platforms as testbeds.

NVIDIA has routed its BlueField-2 DPUs to its DGX SuperPOD. Image used courtesy of
Sixteen Arm A78 cores (64-bit) power the DPU—dwarfing BlueField-2’s cryptography acceleration by four times. It also delivers the collective performance of up to 300 CPU cores, typically found within traditional data center environments. Other notable tech specs include the following:
1, 2, 4 Ethernet ports
8 MB L2 cache
16 MB LLC system cache
256 data path accelerator threads
16 GB of onboard, DDR5 memory with dual 5600 MT/s DRAM controllers
Full-height or half-height architectures, each at half-length (FHHL or HHHL)
M.2 and U.2 connectors
1 GbE out-of-band management port
Conversely, the BlueField-2 only supported 200 Gbps max performance, up to eight Arm A72 cores, and either 8 or 16 PCIe 4.0 lanes. is also critical. DDR5 supports doubled data rates over its predecessor. The memory controller associated with error-correcting code is moved onto the RAM unit—freeing the CPU while allowing faster memory-error checking for always-on remote servers.
BlueField Scales the Cloud
NVIDIA’s elevator pitch for BlueField-3 is simple: unlock better software-defined networking, storage, and cybersecurity. The company has acknowledged an industry-wide movement toward hybrid and full-cloud environments amidst the growth of AI applications.
On-premise data centers aren’t completely disappearing. However, it’s clear that professionals are processing mountainous quantities of data over the airwaves—and existing chips aren’t cutting it.
The cloud’s major advantage is scalability. While physical facilities face space restrictions—requiring sizeable investment and land procurement for expansion—external vendors have excess capacity to loan out. These servers allow employees to access data from anywhere. However, not all companies are keen on storing sensitive data externally—making BlueField chips useful for transmitting data to endpoints like servers, computers, and mobile devices.
Architectured With Security in Mind
The chipset offers firewall distribution, IDS/IPS, root of trust, micro-segmentation, and DDOS protections. These building blocks are essential within zero-trust environments.
Resting and moving data are encrypted. AES-GCM 128/256-bit keys are supported, as is AES-XTS 256/512-bit. is also available—thwarting viruses, spam, malware, and spyware. NVIDIA’s Morpheus framework takes AI-based security a step forward, mainly by defeating real-time security threats.
BlueField-3 is the hardware component, yet software is equally important. The DOCA SDK gives teams tools for monitoring thousands of datacenter DPUs—including provisioning and monitoring. There’s hope that library-and-API management will be streamlined.

NVIDIA says its DOCA SDK brings data center infrastructure to a chip architecture. Image used courtesy of
How the DPU Optimizes AI-facing CPUs
Engineers offload the behemoth of AI software tasks to powerful hardware. Chips like BlueField-3, built upon NVIDIA’s DOCA architecture, remove the load from the CPU to make these processes even faster. Virtualization, networking, and storage are accelerated.
For AI applications, . Because GPUs excel at AI training exercises, they’ve permeated the supercomputing realm. Accordingly, BlueField-3 explicitly supports multi-tenant “cloud-native supercomputing” for extreme workloads. While CPUs are extremely important in tandem, NVIDIA’s solution shoulders much of the burden—allowing CPUs to tackle operations for which they’re more optimized.
BlueField Garners (Many) Votes of Confidence
A number of server manufacturers and cloud providers are already leveraging BlueField DPUs for specialized workloads, including Dell, Lenovo, Baidu, Canonical, Red Hat, and VMware, among many others.
However, numerous companies have seen the potential in DPU acceleration, and have since partnered with NVIDIA following their announcements at the GPU Technology Conference. Goals include supercharging application performance, operational consistency across diverse environments, and upholding security without compromising performance.

Players in the BlueField DPU ecosystem. Image (modified) used courtesy of
Emerging autonomous vehicle technology . These autonomous systems rely on a mix of deep learning, computer vision, and AI processing to function properly. The system-on-chip blends Arm CPU cores and NVIDIA’s own GPU technologies—namely BlueField. Beyond just vehicles, it’s possible that robotics applications may benefit from BlueField’s continued development.
BlueField-3 is backward compatible with BlueField-2, and is expected to become available by Q1 2022.
0 notes
Text
Vpn Free Download For Mac

4/5(7votes )
Free Vpn Download For Mac Reddit
Free Vpn Download For Mac 10.6.8
Vpn Free Download For Macbook Air
Best Free Vpn For Mac
Best Free Vpn For Mac Download
On MAC we use OpenVPN® Protocol which ensures maximum security and speed! Urban VPN for MAC is optimized for privacy, high speed, unlimited bandwidth and a secure connection to hide your IP. On top of that, it's completely free! Try Urban VPN. Mac users interested in Osx 10.6.8 vpn generally download: VPN Unlimited 7.9 VPN Unlimited is a Mac utility designed to help you protect your privacy while browsing the web. Because Opera's browser VPN is built right in, you are able to use it immediately and don't need to download a VPN extension. Get Opera's easy to use browser VPN free of charge when you download the Opera browser. To enable VPN in Opera: Go to your Settings (Alt+P). Select Advanced in the left sidebar, and click Features. Under VPN, toggle on.
Do you want to access Netflix, BBC iPlayer, Hulu and many more country-specific apps and website? In that case, you need a reliable Virtual Private Network Service such as VPN 360.
With this VPN app, you can access these websites and apps. This is also very important for the people who love to travel abroad and wanted to use the same platform they are using from their respective homes.
App for macbook pro. Portable monitors are still fairly expensive (and bulky), luckily, though, you can use an iPad instead using a nifty app called Duet. Just realize that the bandwidth isn’t quite what you would get with one of the, so it can be a bit laggy when you bump the quality up. Price: £14.99 (around $20 or AUS$25)If you’re anything like us, working on just one monitor or screen is just painful. But it’s still better for watching videos, reading websites and typing up documents. Developed by ex-Apple engineers, it works by tethering your iPad to your Mac using one of Apple’s Lightning cables and firing up the app on both devices.You can then drag apps and windows onto your iPad’s screen just like you would with a second monitor, and if you have a more recent iPad with a Retina display, you’ll get the full benefit of all those beautiful pixels.
VPN 360 is very essential because your network will be protected whenever you are connected to it. You can prevent yourself from getting hacked because this app will encrypt the connection between you and the website you are accessing.
Whenever you use it, the following that we provided were not the only benefits of this application. The other benefits of this VPN apps are to hide your IP address from outside network. That’s why you can access a country-specific blocked website.
It is also beneficial for people who love to use facebook, youtube or any other social networking app without anyone knowing that you are surfing from these websites. With this feature, you can expect your connection to be anonymous and secured, giving you complete privacy online.
Free Vpn Download For Mac Reddit
This VPN app will also let you ignore strict firewall rules from their switch or routers. Allowing you to enjoy accessing websites that you wanted.
Since VPN 360 have a lot of advantages and benefits, most of you wanted to use it on a computer. But the problem is, no version was released for the Windows and Mac OS. But there’s a trick that will let you run VPN 360 for PC so continue reading this whole article.
How To Use VPN 360 App On PC
If you are one of the people who are looking for a way to install and use the VPN 360 app, then you must follow our simple guidelines that you can see below. Make sure that your computer has enough resources such as free disk space and RAM.
To get this app working, we are going to use a tool for emulating the Android Operating System like BlueStacks. With this software, you can almost download and run all games and apps on your computer as long as it is based on Android. This means that you can also use the VPN 360 on PC using this tool.
You Might Also Like: Kiwi VPN Free For Windows And Mac
Steps To Download And Install VPN 360 For PC
First, make sure that you have an internet connection and then go to the website of BlueStacks emulator. This is required for running VPN 360 app so this is the only choice for now.
The second step is to download and then install it to your computer or laptop. Make sure that you download the installer for the Operating System that you are using, for example, if you are using Windows OS, then get the Windows version, else, Mac version.
The third step is to accept all of its terms and condition and then click next to continue the installation of BlueStacks emulator for your PC.
The fourth step is to enter your Google account ID from the PlayStore since you need it in order to install VPN 360 on your PC. Wait for the set up to finished and when it does you can proceed to the next step.
Next, you need to download the app that you wanted to install, use the search function and then look for the VPN 360 using the search function. You can click the install button after you found it.
Installing this will finally allow you to run VPN 360 app on PC. So go ahead and open the app after the installation. This is the most simple way of installing this app on your computer but if you want to use an alternative way of installing VPN 360, you skip the PlayStore activation.

Must Download: Free Download VPN Melon For PC – Windows & Mac
Installing VPN 360 App Using The APK Installer
If you don’t like to provide your Gmail ID, that is also fine. So, the first thing you need to do is to get the installer file and look for Google.
Run the BlueStacks emulator and hover your mouse to the triple-dot located at the upper left side of the emulator. Now click install apk so that you can add the APK of VPN 360 that you have downloaded recently.
This will start the BlueStacks to run this application and finally start using the VPN app on your PC. However, this method has a small drawback. The APK file does not automatically update itself so to get the latest version, you need to download it again.
Installation Of VPN 360 App With Nox Emulator
Free Vpn Download For Mac 10.6.8
If you wish to try a different emulator, you can also check NoxPlayer for running Android-based software. To make the VPN 360 works on your computer, follow the installation procedure below:
Download the NoxPlayer from its website which you can access from here. That link will direct you to its one and only official website.
Run the setup file of NoxPlayer and configure it.
Wait until the set up completed and then enter your account of Google.
Open PlayStore and search for the VPN 360 app.
Install and wait for it.
Go back to Home and then click the icon of VPN 360. Now you can enjoy using this app on your PC.
Also Check: Free Fast VPN Service
Conclusion
VPN 360 is beneficial and one of the best apps that you can use for free. They also offer a premium version that will provide you a faster connection and more option for choosing a server location. Thanks for the emulator without it, we cannot run the VPN 360 for PC.
Download And Install AIMP For Windows PC Or Mac - October 28, 2020
How To Download And Install Endoscope App For PC - October 27, 2020
BYJU’S On PC – How To Install On Windows 7/8/10 - October 23, 2020
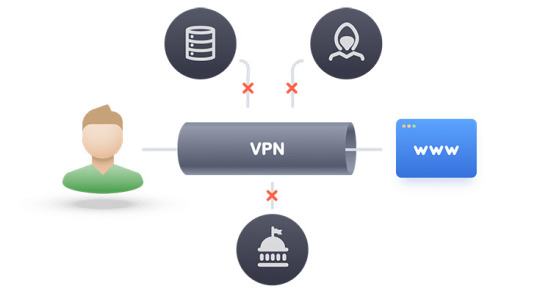
Privacy is major concern and with increasing heinous cybercrimes, one has to be very careful while browsing Internet. To keep your online privacy intact and access websites blocked in your country, you can use VPN. With VPN installed on your Mac, you can hide your IP address and access blocked content easily.
VPN expands the horizon and expose you to wide variety of content, which you couldn’t access in your area. Moreover, it is an excellent tool which you help you to maintain privacy and anonymity when surfing the web. Most VPN are available at a minimal cost but if you are looking for a VPN app, we will help you with that. Before that, you need to know what a VPN does and how to choose best free VPN for Mac?
What A VPN Does & How To Choose Best Free VPN For Mac?
VPN acts much like a firewall and it enables users to safely access private network and make it easy to share data remotely via public networks. Mostly VPN services takes help of a desktop application that runs in background encrypting your data when browsing web. However, this is not the ultimate solution to protect your privacy, but just a part of it. Before choosing a free VPN for Mac, you need to consider a few things. Some of them are free bandwidth, major locations, P2P, ad blocking and more. We have listed some of the best VPN services for Mac, have a look!
1. CyberGhost VPN
CyberGhost VPN a complete VPN solution that allows you to access blocked site, stream sport events, play region locked games and more. Let’s look at the features of CyberGhost VPN:
Connects you with everything keeping privacy intact
It hides your Wi-Fi address, to make online browsing secure.
Protects your online identity guards and secures your banking transaction.
One tap protection to encrypt data transfer.
Automatically connects you with the best matched server based on the location.
Lets you enjoy your Internet without any restriction.
CyberGhost VPN provides 24/7 customer support via live chat.
2. Surfshark
Surfshark is a secure VPN that provides private access to open Internet. This VPN encrypts all Internet traffic shared between devices. Plus, users IP address is also hidden so that nobody can track your online activity. Let’s look at the features of the Surfshark in detail:
It gives a clean browsing experience by blocking ads, malware and more.
It allows specific apps and websites to bypass the VPN.
It comes with AES 256-GCM encryption to safeguard personal information from hackers and third parties.
It offers camouflage mode so that no one including your Internet provider can’t identify that you are using a VPN.
3. Nord VPN
Nord VPN is one of the best free VPN for Mac as it provides secure and private network. Let’s look at the features of Nord VPN:
It protects you while on public Wifi networks, annoying ads, secure your online activity from malware and other cybercrimes.
It enables you to secure up to 6 devices with single Nord VPN account.
It lets you enjoy your Internet with no boundaries, no matter where you travel.
It secures your IP address so that nobody can track which websites you surfed and what files you downloaded.
Nord VPN comes with excellent customer service which are always ready to support every hour of the day
4. HotSpot Shield
HotSpot Shield is a secure VPN which comes with ultra-fast VPN servers which comes with military grade encryption. Let’s look at the features of Hotspot Shield:
It supports all platforms, so you can download Hotspot Shield and access on whichever device you want.
You can get secure access to Internet without being hacked or tracked.
It hides your IP address, physical location of VPN server.
Hotspot Shield VPN doesn’t log your browsing activity, so your ISP can’t keep a track of websites or apps that you use.
HotSpot Shield comes with Kill Switch protection which protects your identity if the connection is lost for some time so that you are not vulnerable even for a second.
5. TunnelBear
TunnelBear is a secure VPN that works well and provides private connection to less restricted Internet. With this free VPN, you can hide your IP address and location from websites, ads and hackers. Let’s look at the features of the TunnelBear in detail:
It comes with AES 256-bit encryption which safeguards your personal information from third parties and hackers while using public Wi-Fi.
It makes accessing emails, domestic news, favorite sites whilst travelling abroad.
It limits advertisers from tracking your online activities.
You get to stream faster with TunnelBear VPN and also you can avoid getting tracked by ISP.
TunnelBear is one of the best VPN software for Mac as it doesn’t log any activity of its customers and keep the privacy intact. You can also use TunnelBear against VPN blocking with Ghostbear feature as it makes your VPN data less prone to detection to ISPs, governments or others.
6. Express VPN
Express VPN is a high speed, easy to use and setup which makes best vpn for MacOS. It is secure & anonymous which makes it easier to keep you off the radar of hackers and privacy intruders. Let’s look at the features of Express VPN:
It helps you to unblock the websites and apps across 94 countries.
It has a huge network of more than 2000 global VPN servers with faster connections, unlimited bandwidth.
You can use Express VPN service for Mac, iOS, Windows, Linux and Android.
It lets you stream or download anything from anywhere in the world without revealing IP address to intruders.
Express VPN comes with 256-bit AES encryption, kill switch, DNS/IPv6 leak protection, and split tunneling. It comes with 148 VPN server locations in 94 countries with unlimited server switches.
7. VYPR VPN
VYPR VPN is one of the best VPN services for Mac which gives you Internet privacy and freedom to browse any site without any intrusion. Let’s have a look at the features VYPR VPN:
It offers OpenVPN, Chameleon, PPTP and L2TP/IPsec, so you can choose your preferred level of speed, encryption and protection.
It lets you connect to any VyprVPN server without any limitations, server switching apps, and download caps.
Vypr VPN offers more than 70 server locations across six continents.
When you connect to VyprVPN, your ISP can only see encrypted traffic.
Vypr VPN has NAT firewall to provide an extra layer of security. It has a support team which works 24*7*365 to help you via email or live chat.
8. Hide me
Hide me is one of the best VPN software for Mac if you want to maintain your anonymity and encrypts your connection. Let’s take a look at the features of Hide.me:
It has more than 150 dedicated gigabit servers through Europe, The United States and Asia so that you can access websites securely.
me manage and create without logging user data or activities. So, your information never goes to third party.
It has various VPN protocols such as PPTP, SoftEther, SSTP, L2TP/IPsec, OpenVPN and IKEv2
It comes with AES 256-bit encryption with 8192-bit keys.
Hideme works on MacOS, Windows, iOS, Android, Routers, Linux, Smart TVs, and Consoles. It provides you complete protection against IPv6, IP leaks and DNS leaks.
9. Private Tunnel
Private Tunnel is one of the best free VPNs for Mac which comes with more than 50 VPN servers over 23 regions in 12 countries. Let’s take a look at the features of Private Tunnel:
It masks your public IP address and encrypt connections to protect your privacy.
It protects your network from online threats, reducing cyber-attacks, spoofing & DDoS attacks.
It connects your devices to unrestricted access to websites and information.
It provides 24*7 customer support online via ticketing system and chat support.
Private Tunnel comes with AES encryption, AES block size makes it less prone to attacks than others. It encrypts traffic, secure connections on Wifi HotSpots as well.
10. Windscribe
Windscribe is a secure VPN which unlocks all locations and comes with config generator. It secures your identity by hiding your IP and timestamp. Let’s look at the features of Windscribe:
It has larger network which comes with server in over 55 countries and 100 cities.
It has strongest encryption which has AES-256 cipher with SHA512 auth and a 4096-bit RSA key.
It helps you generate OpenVPN, SOCKS, and IKEv2 config for all your devices.
It blocks all connectivity outside the tunnel to avert all types of hacks and leaks.
With this VPN, your computer becomes a secure Wi-Fi router. You can change your time zone and access the websites blocked for your location. Windscribe blocks ads and trackers to ditch the hackers.
Vpn Free Download For Macbook Air
11. Speedify
Best Free Vpn For Mac
Speedify is yet another best free VPN for Mac which comes with bonding technology, which enables you to use multiple Internet connections concurrently to get maximum speed. Let’s take a look at the features of Speedify:
Best Free Vpn For Mac Download
You get better streaming, live broadcast without throttled Internet connection.
You can set preferences rules for all the Internet connections individually to monitor usage.
The server network covers 28 countries so that you get better connection on the basis of availability and latency.
This VPN also improves latency, reduce lag for faster gameplay and trustable performance.
It uses a ChaCha- or AES-based encryption algorithm, depending on device support to provide security. Speedify has no log VPN policy so nothing is traced or tracked back.
Is a Free VPN the Right Solution for Your Mac?
There are plenty of free VPNs in the market however, not every one of them work well on your Mac. You have to be very careful with free VPNs as they come with restrictions such as limited data transfer, pop-up ads, slow speeds and more. Although, there are other harms of using it such as planting trackers, intruding your security and privacy.
Therefore, we have listed some of the safest and free unlimited VPN for Mac to help you maintain your anonymity and surf online without any restrictions and worries.

0 notes
Text
5 Key Benefits of Native Mobile App Development
Building a mobile app has become a top priority for many companies, but it’s often difficult to choose a development approach as the lines between the various options are becoming increasingly blurred. In our recent post, A Guide to Mobile App Development: Web vs. Native vs. Hybrid, we broke down the three options and outlined the pros and cons for each. This article will dive deeper into Native Mobile App Development and the benefits of choosing this particular development approach.

hbspt.cta.load(1789978, 'aa3dbba3-416d-45bd-bcd9-33a47d1cf5e3', {});
What is Native Mobile App Development?
Native mobile app development involves building apps for particular mobile operating systems, and users access them from dedicated app stores (such as the App Store or Google Play). If you intend to build an application for iOS, app developers will use programming languages Objective-C or Swift. In contrast, developing for Android calls for the programming languages Java or Kotlin.
Both Apple and Google provide app developers with their own development tools, interface elements, and SDK. Most companies will invest in native mobile app development because of the myriad of benefits offered in comparison to other types of apps such as Hybrid or Web. As mobile software is increasingly a necessity for companies, it’s important for companies to be well-informed about the pros and cons of choosing an app development approach. Here are the key benefits of native mobile app development:
5 Benefits of Native Mobile App Development
1. Native Apps Have The Best Performance
With native mobile app development, the app is created and optimized for a specific platform. As a result, the app demonstrates an extremely high level of performance. Native apps are very fast and responsive because they are built for that specific platform and are compiled using platforms core programming language and APIs. As a result, the app is much more efficient. The device stores the app allowing the software to leverage the device’s processing speed. As users navigate through a native mobile app, the contents and visual elements are already stored on their phone which means load times are quick.
2. Native Apps Are More Secure
Web apps rely on different browsers and underlying technologies such as JavaScript, HTML5, and CSS. Developing a native mobile app is a great way to guarantee your users reliable data protection.
3. Native Apps Are More Interactive And Intuitive
Native mobile apps run much smoother regarding user input and output. These types of apps inherit their devices’ OS interfaces, making them look and feel like an integrated part of the device.
The most advantageous benefit to native mobile apps is the superior user experience. Native apps are created specifically for an operating system. They stick to the guidelines that ultimately enhance and align the user experience with the specific operating system. As a result, the flow of the app is more natural as they have specific UI standards for each platform. This allows the user to learn the app, such as deleting an element quickly. Adhering to specific guidelines eliminates the learning curve and allows users to interact with apps using actions and gestures they’re familiar with already.
4. Native Apps Allow Developers to Access the Full Feature Set of Devices
Native apps are developed for their particular platform, taking full advantage of the software and the operating systems’ features. These apps can directly access the hardware of the device such as the GPS, camera, microphone, etc. so they are faster in execution, which ultimately results in better user experience. Push notifications are another huge advantage to choosing native app development. Push notifications go through the iOS server (APNS) which you need your app bundle ID and same with Google’s Cloud Messaging (GCM).
5. Native App Development Tends to Have Fewer Bugs During Development
It’s much more difficult to maintain two different applications in one codebase than it is two applications in two codebases. With native app development, you have fewer dependencies for bugs to occur because you’re not relying on a cross-platform tool such as Xamarin or Cordova. Hybrid apps access hardware through a bridge which often slows development down and can amount to a frustrating user experience.
This problem is prominent when new versions of Android and iOS are released. Native app developers have access to new software development kits (SDK) to start building their applications with the most recent features. Because of this lead time, users of native applications have access to new platform features once they update the operating system.
The disadvantage of having to wait for the third-party developer of the hybrid tool to implement the bridge to new operating system features. With hybrid app development, we are dependent on a cross-platform development tool such as Xamarin or Cordova. Every time new features are released in the UI kit, we need to wait for the tool to support it. When you develop a hybrid app, there’s an added layer that you don’t have control over which can increase the chances of bugs occurring. Bugs are a huge concern for hybrid app development when working with the latest features that have been released for a particular operating system. This is an essential and often overlooked part of generating loyalty among users.
Native Mobile App Development Considerations
Although the initial cost may be higher with native mobile app development, you’ll end up saving a lot of time and money in the long run, doing it well the first time. By offering a great user experience, better performance, and leveraging the device features, you’re able to offer your users a more personalized experience which will be rewarding in the long-term. The combination of the native mobile app advantages will result in higher conversion rates and will ultimately boost customer loyalty.
Related: The Definitive Guide to Mobile App Development Costs [Infographic]
Whichever approach you choose should above all be quick, responsive, and reliable. As users are demanding more from mobile experiences, it’s important to keep up with their changing demands.
The Ultimate User Experience
Technical and functionality shortcomings aside, non-native apps cannot compete with responsiveness and user experience of the native approach. If a business intends to use an app as a central tool for interacting with customers and stakeholders, it must deliver an excellent user experience that supports mobile app retention. Dissatisfaction, even in the slightest, can lead to poor retention rates and high uninstall.
Native app development gives app developers considerably more control over the user experience and also allows them to design the apps for easy support. We believe it’s best to stick with native and not sacrifice the design elements that are unique to each platform. However, if you aren’t too concerned about the overall user experience and want to get something to market fast and cheap, a web app may be the way to go.
While the discussion to differentiate the three mobile app approaches will continue to lengthen, it’s important to remember that you shouldn’t choose an approach for the technology, but instead, choose based on your app’s functionality. If you choose an approach that doesn’t allow your app to utilize device features, for example, then you’ll end up wasting a lot of time and money when you decide to add these new features. To decide which development approach to take, ask yourself these key questions:
How important is the performance of your app?
Does your app need to include any device-specific features?
Do you want your app to support multiple platforms and devices?
What is your mobile app development budget?
Are you interested in cost comparisons between native and hybrid apps? Check out our blog: A Breakdown of Hybrid vs. Native Mobile App Development Costs, or download the Definitive Guide to Mobile App Development Costs Infographic. This infographic offers price ranges for small, mid-sized and large apps based on product complexity, plus hidden costs and other considerations to help you evaluate your development budget.
Keep Reading:
4 Essential Success Criteria For New Mobile Product Development
Mobile App Design: Designing For A Web App Vs. Native App

hbspt.cta.load(1789978, 'aa3dbba3-416d-45bd-bcd9-33a47d1cf5e3', {});
5 Key Benefits of Native Mobile App Development published first on https://gpshandyorten.tumblr.com/
0 notes
Text
NordVPN VPN Service - Review, Test-drive and Features breakdown

We couldn't complete our VPN review & test-drive series without talking about NordVPN, one of the most renowned VPN services in 2019: from PCMag to TechRadar, from VPNMentor to CompariTech, everyone seems to love NordVPN speed, performance and reliability. Are the rumors really true? We tried our best to find it out within this review and test-drive.
In the unlikely case you don't know what a VPN as-a-service actually is we strongly suggest to check out this post before going further: once done, come back here to read the review to its full extent.
Internet without borders
Advanced security, Internet freedom, Complete privacy: this is the payoff of the NordVPN website, and it fits well with the company spirit. NordVPN was born in 2012 when four childhood friends came together to build technology that could liberate the internet. Spending a lot of time in different parts of the world they saw internet censorship, content control and intrusive government surveillance growing faster than ever before. The feeling that the internet was losing its main purpose led to a search of possible solutions on how to overcome all the restrictions.
After setting up the first VPN server and sharing the prototype among their friends, the creators started receiving extremely positive feedback and were encouraged to continue their work. That’s how NordVPN was born, now serving more than 12 million people worldwide.
The NordVPN name was inspired by Nordic ideals of confidence, trust, and innovation: it reflects how we value our customer freedom of choice, how we strive to be innovative with our technology and the way we work. Over the years, NordVPN became a trusted online security solution, used by over 12 million internet users worldwide. Meanwhile, NordVPN became recognized by the most influential tech sites and IT security specialists. It is now one of the most trusted privacy and security service provider in the world, known for the strongly held values and well thought-out features.
Ethical purposes
Before starting with the technicalities, we would like to briefly review the NordVPN manifesto which can be found on their website.
We, at NordVPN, strive to make Tim Berners-Lee’s vision of a truly open internet a reality. Mr. Berners-Lee imagined the internet as a very different place when he implemented the first successful HTML communication in 1989. It was to be a safe space, free from censorship and surveillance. Unfortunately, as headlines around the world demonstrate daily, this is hardly the case these days.
At NordVPN, our team of mathematicians and technologists wake up every morning with one core goal – to keep the internet as free as possible. This is our passion and why we come to work every day. We strive to provide absolutely uncompromised safety and privacy on the Web. We make sure no one sees what you do online because they shouldn’t. Nor should we, for that matter.
For this reason we do not keep logs. If someone asks us about you, we have nothing to share. We are free internet enthusiasts who believe in a common secure future online. We support fighters for human rights, journalists, volunteers in conflict zones, information activists or anyone who believes in the power of the open Web as Mr. Berners-Lee imagined.
In the spirit of transparency, we’ll do everything we can to keep you updated about all aspects of our service, from server status upgrades to occasional glitches. We aim to create a lasting relationship of mutual trust with you, the customers who share our deeply held values.
Additional ethical contents can be found on their social responsibility page, where they talk about freedom of speech, digital education & awareness, social reports, and so on: definitely a commendable display of good efforts... However, it's about time to bring the numbers and the stats in.
Data Security
NordVPN was the first VPN service to describe their data protection features as military-grade encryption... which might sound a bit exxagerated, yet it's not that far from the actual truth. As a matter of fact, NordVPN protects their users data using AES, an encryption standard used and approved worldwide by governments, cybersecurity experts, and cryptography enthusiasts: more specifically, NordVPN makes use of AES with 256-bit keys, which is recommended by the NSA for securing classified information.
The number 256 refers to the key size, so 256-bit has 1.1×1077 possible combinations. While it is true that any key can be broken given enough resources, cracking AES with 256-bit keys is definitely out-of-reach nowadays: to break it, a good hacker would need to use supercomputers that would countinuously work for many (billions of) years.
Two security protocols
Like most VPNs, NordVPN creates a tunnel to transmit your data to VPN servers securely. When this happens, two different security protocols are used to determine how that tunnel is actually formed: IKEv2/IPsec and OpenVPN. More specifically, IKEv2/IPsec has been adopted as a default in NordVPN iOS and macOS apps, while OpenVPN is the default for NordVPN Windows, macOS, and Android apps. Both of these protocols have their pros and cons, but each one of them is dependable and highly recommended by most IT security experts worldwide.
IKEv2/IPsec
IPsec, which stands for Internet Protocol Security, operates with the newest version of the Internet Key Exchange (IKEv2) to enhance security, stability, and speed. IKEv2/IPsec employs powerful cryptographic algorithms and keys, which are almost unbreakable - even by today's supercomputers. With computing power continuously increasing, and cryptography breakthroughs always around the corner, it’s important to stay one step ahead. That’s why NordVPN uses the very adaptable Next Generation Encryption (NGE) with IKEv2/IPsec: this will add an additional layer of security, because the protocol will mantain its resiliency even when the CPU computational capacity will increase over the natural course of time.
OpenVPN
OpenVPN is an extremely versatile security protocol, which you can use both for TCP and UPD ports – for safe browsing, gaming, and live streaming. To guarantee the protection of your sensitive data, NordVPN uses AES-256-GCM encryption algorithm with a 2048-bit DH key. The whole global cybersecurity community has a stake in OpenVPN since it has an open source code, which is freely available for review and modification. With every new bug report, with every new-found vulnerability, with every line of code, this security protocol gets stronger and better. We can definitely say that transparency is the most powerful OpenVPN feature.
Verdict
Although using AES-256 is definitely a good thing, it also became the de-facto standard among the top-tier VPN service providers. The same can be said for IKEv2/IPsec and OpenVPN: both protocols have been adopted by most VPN services as well. Therefore, we can say that NordVPN data-encryption level is great, yet it's pretty much on-par with most of its competitors nowadays.
Features
This is a list of NordVPN's most important features.
DoubleVPN
One of the NordVPN most distinctive features is called DoubleVPN. Typically, when you connect to VPN, your traffic travels through a remote VPN server, which changes your IP address and encrypts all the data that you send or receive over the internet. Due to this setup, no snoopers or cybercriminals can see what you are doing online. With Double VPN, your online activity hides behind two servers instead of one, using a two-layered connection pattern known as VPN server chaining. The working principle is rather simple:
Your traffic reaches a remote VPN server and leaves it securely encrypted.
The encrypted traffic then passes through a second VPN server and gets encrypted one more time.
You reach your internet destination securely and privately.
It goes without saying that such tecnique drastically increases the overall security of the connection, as well as the anonymization standards: however, it also comes with a noticeable performance decrease - which is often well-worth the trade.
These are the most distinctive benefits of the DoubleVPN feature:
Double encryption: the transmitted data is protected with an extra layer of encryption, thus making it twice as hard for hackers to decipher.
Enhanced security: the connections are mixed between UDP and TCP protocols, which increases the security level of all the online activity.
IP masking: As the caller's actual IP address was changed by the first VPN server, the second server doesn’t have any information about it.
Increased privacy: Nobody, including the caller's ISP can see the final destination of the web requests issued by the caller: they can only know that a VPN service is being used.
Kill Switch
The Kill Switch is a fundamental characteristic of any good level VPN: such function provides the automatic shutdown of one or more applications (or the internet connection, or the entire PC) whenever the VPN connection ends for any reason. It essentially acts as a safety net that will protect the transmitted data against accidental disclosure in case of connection problems.
Strict No-Log policy
Without a VPN, all your online traffic passes through your internet service provider (ISP): they can see everything you do online and track your behavior. Sometimes they even hand your internet access data over to advertisers, government agencies, or other third parties. When you connect to a VPN server, your ISP can no longer see what you do on the internet. However, your VPN provider does have that power. So it’s crucial to know what kind of logs – details about you and your online activity – the provider keeps.
NordVPN operates in Panama, where there are no legal requirements for collecting user data: this basically means that they are free to apply a no-log policy, meaning they won't register their users activities at all. This is a really good thing for users privacy, because no government will be able to force NordVPN to hand over your online activity records.
CyberSec
A recently introduced feature that blocks certain threats (malware or phishing) automatically: it should acts just like an antivirus + a firewall IPS system. Unfortunately, we were unable to properly test it (we'll edit this section if we'll be able to do that in the near future).
Custom DNS
A neat feature allowing the user to add their own custom DNS servers to be used instead of NordVPN's DNS servers.
P2P-Friendly servers
P2P stands for Peer-to-Peer networking. It is one of the fastest and most convenient ways to share files with large groups of people. Normally, each user would download a file from one server or a network of servers. With P2P, each downloader also becomes an uploader, making the process of file sharing much more efficient.
The reputation of P2P sharing is somewhat negative, which is why many internet service providers (ISPs) try to discourage users from it. But file sharing has valid and perfectly legal uses – in fact, the P2P technology is ideal for public distribution of free-access data, sharing large amounts of corporate data internally, and also pushing software updates to massive user bases. That being said, you still need to think about safety measures while sharing or downloading files from a P2P network.
The main issue is that every device uploading or downloading the same file on a P2P network can see each other’s IP address. That’s the very nature of P2P – it wouldn’t work otherwise. So what’s great for efficient information sharing is not that great for your privacy. Besides, your internet service provider can also quickly detect that you’re using P2P. They may deny access to file-sharing websites or set bandwidth limits, which slows down your internet speed.
With these risks in mind, if you use P2P, VPN should be your best friend for (at least) three reasons:
IP address masking. When you enable a VPN, you connect to a remote VPN server, replacing your real IP address with that of the server. This IP swap hides your location and helps you stay private while sharing files or simply browsing the web.
Bandwidth throttling protection. When you use a VPN, your ISP can’t detect that you are sharing files and shape your connection accordingly. This way, you can avoid the annoyance of bandwidth throttling and internet roadblocks.
Online traffic encryption. With a VPN, P2P files and all other data you send and receive travels through a strongly encrypted tunnel. That means no one can get their hands on your private information.
6-Device rule
A single NordVPN account will cover up to six devices at once. Moreover, if you connect NordVPN to your router, it will secure every device on your network, using up only a single space out of the 6 available. Considering how many devices are available within a single family nowadays, this is indeed a good thing, as you can secure the whole home with a single account.
Top-grade Assistance
NordVPN customer service has been given the Best Customer Service 2018 Award by bestVPN.com: their agents are ready to help you 24/7 (all day, every day) using a deedicate line: they also have a pretty good Help Center & Support page which can be useful to quickly find the answers for most frequently asked questions.
VPN Client
The NordVPN Client is definitely a big deal, expecially if we compare it to the "minimalistic" approach chosen by most VPN service providers - which is not ideal when you have to play with a lot of options. It comes with Server List section with favorites and bookmark support, and a well-presented Settings page which can be used to customize the various connection properties and features.
Here's a list of the most important features you can control from the Settings section:
CyberSec
Custom DNS
Auto connect
Kill Switch (App and Internet)
Invisibility on LAN. This useful feature hides the computer on the local area network.
Obfuscated Servers. It can be used to use NordVPN from restricted locations (we couldn't try that since our country is not restricted).
Notifications. This option can be activated t o get connect and disconnect notifications in the SysTray.
The Server List section provides a country-specific server lists, dividing them in four different types:
Dedicated IP address. These servers have a dedicated IP addresses that don't change.
Double VPN. These servers will chain the VPN connection so that traffic flows through two VPN servers all the time (as previously explained in the Double VPN paragraph).
Onion over VPN. These server will allow you to use TOR while connected to the VPN.
P2P. These servers supports P2P traffic (not all do).
Performance Tests
The test-drive which we carried out was mostly performance-oriented: we were interested to measure the ability of the VPN to maintain a decent speed over time with a wide range of different applications: Torrent, Emule/eDonkey, web surfing in HTTP and HTTPS mode , FTP, SFTP, RDP connections, TeamViewer sessions, online gaming (using CounterStrike: Global Offensive, MTG Arena and Hearthstone) and video streaming platforms (Netflix, Amazon Prime Video, CrunchyRoll, Youtube Red).
We have to admit that the results were top-notch - probably the best we ever got from a VPN service as of today. Let alone the online FPS-based gaming, which remains substantially out of the question for all VPN services as the ping rate drops below the acceptable minimum levels (150-300 latency), the speed drop was rather minimal. We got a ~10% speed decrease in WWW browsing and FTP/FTPS download, and ~15% speed decrease with the P2P applications: in some cases (BitTorrent), the ISP throttling bypass allowed us to record even better performances than the non-VPN connection - which was also great.
Conclusions
NordVPN lives well up to its standards: a blazingly-fast, secure and reliable VPN service that is well-worth the price: highly recommended!
Read the full article
0 notes
Photo

RT @Firebase: It's time for an upgrade! Google Cloud Messaging (GCM) is now deprecated. Upgrade GCM to Firebase Cloud Messaging (FCM) today to take advantage of new features. Learn more about the switch and the benefits of upgrading in the blog ↓ https://t.co/3jM50n4iL6
0 notes
Text
natural supplements for anxiety induced premature ejaculation
Contents
Ejaculation lexapro premature
Treatment. premature ejaculation
Premature ejaculation mp3
Premature ejaculation scenes
premature ejaculation definition force g premature ejaculation delay pills The Simpson, headed, by Professor Neil McIntosh, is the largest unit for premature babies in Scotland, and Jennifer will undergo intensive monitoring by a state-of-the-art computer system which.premature ejaculation post vasectomy premature ejaculation qarshi medicine premature ejaculation venlafaxine premature ejaculation workout Two hundred and twenty-two married men (mean age, 34 years) with premature ejaculation (pe) were randomly assigned to receive 75 mg of venlafaxine.SHOCKING LIFE STORY!!! AFTER 9 YEARS OF SUFFERING FROM PREMATURE EJACULATION & WEAK ERECTION, 45 YEAR OLD MAN FINALLY DISCOVERS THE SECRET SOLUTION THAT MYSTERIOUSLY JERKED HIS DEAD MANHOOD BACK.premature ejaculation and age premature ejaculation lexapro premature ejaculation thyroid In secondary hyperhidrosis, the sweating is due to another disease such as a thyroid. If ejaculation happens sooner than you or your partner would like, it is called premature ejaculation.THE General Court Martial (GCM) sitting in Abuja, has sentenced six Nigerian Air Force Personnel for criminal conspiracy,premature ejaculation venlafaxine · Premature (early) ejaculation-also referred to as rapid ejaculation-is the most common type of sexual dysfunction in men younger than 40 years. An occasional instance of premature ejaculation might not be cause for concern, but, if the problem occurs with more than 50% of attempted sexual relations, a dysfunctional pattern usually exists for.Post-orgasmic illness syndrome (POIS) is a rare condition that includes a cluster of post-ejaculatory symptoms with.MIAMI, May 26, 2020 (GLOBE NEWSWIRE) — Veru Inc. (NASDAQ: VERU), an oncology and urology biopharmaceutical company with a focus on developing.I’m very religious and have a strong faith. Because of that, my girlfriend and I decided to wait until we’re married to have.
2020-06-22 · Considering taking a vitamin or supplement to treat Premature+Ejaculation.Aspx? Below is a list of common natural remedies used to treat or reduce the symptoms of Premature+Ejaculation.Aspx.
Ejaculation increase and enhancement with natural supplements, herbs for a female and male, solution to a common problem September 6 2016 by Ray Sahelian, M.D.. Male ejaculation has two distinct phases, emission and expulsion.
premature ejaculation products TERTIARY institutions are churning out products invented by their teams. AFTER 9 YEARS OF SUFFERING FROM PREMATURE EJACULATION & WEAK ERECTION, 45 YEAR OLD man finally discovers THE SECRET.
The benefits of herbal and other natural products (dietary supplements) are increasingly cited in the media (11). Traditional Chinese Medicine(TCM) which evolved.
premature ejaculation treatment aafp · Premature ejaculation treatment. premature ejaculation often goes away without treatment. But if it happens frequently, and it makes you or your partner unhappy, you may want to.premature ejaculation hypnosis mp3 gainswave for premature ejaculation · GAINSWave is the newest (and most promising) therapy that utilizes low-intensity shock wave therapy to improve erectile strength and performance for people suffering from erectile.Our Store offer wide range of self hypnosis mp3s and hypnotherapy mp3's by Ursula James for all ages.. premature ejaculation mp3. This MP3 is designed to.xvideos favorites premature ejaculation Watch Premature Ejaculation porn videos for free on Pornhub Page 2. Discover the growing collection of high quality premature ejaculation XXX movies and clips. No other sex tube is more popular and features more premature ejaculation scenes than Pornhub! Watch our impressive selection of porn videos in HD quality on any device you own.
What is premature ejaculation? When a man climaxes sooner than he or his partner wishes to, it can lead to frustration and anxiety and is known.
The hunt for natural supplement from medicinal plants is being intensified mainly. is also caused by various factors such as psychological disorders like anxiety, of sexual inadequacies, such as premature ejaculation and oligospermia.[30].
What Is Premature Ejaculation? According to survey reports, nearly 30% men suffer from premature ejaculation symptoms, which are seen in men who are on the thresholds of 40 and assumptions can lead to disturbed relationships and broken marriages.. There were even cases, where the problem underwent drastic negative changes mainly by assumptions, and the individuals committed suicide.
Premature ejaculation is very common, but it is treatable.. Occasional PE is usually not a problem, but if it is happening regularly or causing stress to you and /or your partner, then it is time to speak. Natural remedies for PE.
If you are overly anxious about premature ejaculation, that will affect your. natural supplements, desensitizing lubricants, and other affordable,
Premature ejaculation can be frustrating, not only for you but also for your partner. The disorder can be coped with a variety of over-the-counter vitamins and supplements.
Premature ejaculation (or PE) can occur for a variety of reasons, from anxiety. There are all types of premature ejaculation pills and supplements out there, but .
Premature ejaculation is the most common sexual problem of men under 40, according to doctor, author and nutrition expert Ray Sahelian 1 2. Premature ejaculation is defined as secretion of semen from the penis early into intercourse 1.It happens before a man’s partner or the man is ready and can be very frustrating for both parties.
source https://www.vigrxwarning.com/natural-supplements-for-anxiety-induced-premature-ejaculation/
0 notes
Text
Managing inactive Amazon Aurora PostgreSQL users
Data is one of the most precious assets for any organization, and keeping data secure is always the top priority. One common security requirement for databases is to restrict user access—if a database user is compromised, it can cause significant damage to your data. You should follow the least privilege model for database users. This means that you only grant a user the minimal set of privileges required to do their work. In addition, if a database user is inactive for an extended period, it’s a good practice to disable them. This can limit the impact of any mistake or a security breach. For more information, see Managing PostgreSQL users and roles. This post provides a solution that identifies inactive Amazon Aurora PostgreSQL users and locks or deletes them automatically. The post also shares example code and an AWS CloudFormation template to get you started. In the following use case, you want to identify users that have been inactive for a given number of days (for this post, 90 days). After you identify these users, you want to lock them out. As the DBA, you can unlock these users anytime. However, you want to delete the users automatically if they are inactive for 180 days. However, PostgreSQL doesn’t natively support this feature. Some commercial databases provide this functionality with the user profile feature, which allows you to lock a user account that hasn’t logged in to the database for a specified number of days. For PostgreSQL, this becomes more challenging because PostgreSQL doesn’t store user login timestamps in any of the catalog tables. Therefore, it’s not straightforward to determine how long a user has been inactive. In addition, because there aren’t any login triggers in PostgreSQL, a trigger-based solution is also not possible. Solution You can enable logging the details of each successful login in PostgreSQL by setting the parameter log_connections to 1 in the parameter group. After you set this parameter, the PostgreSQL engine logs a message like the following for each successful login: 2020-01-07 03:51:56 UTC:10.0.0.123(52820):postgres@logtestdb:[18161]:LOG: connection authorized: user=postgres database=logtestdb SSL enabled (protocol=TLSv1.2, cipher=ECDHE-RSA-AES256-GCM-SHA384, compression=off) Aurora PostgreSQL allows you to publish these engine logs to Amazon CloudWatch Logs. With the logs publishing enabled, you can develop a scheduled AWS Lambda function that parses out this login information from the logs to get the user’s last login timestamp. The Lambda function performs the following high-level steps: Extracts login information from log messages Stores the last login timestamp for the users in a status table Uses the timestamp for each user to apply the lock or delete policy Prerequisites Before you get started, make sure to complete the following prerequisites: Set the parameter log_connection to 1 in the parameter group. For more information about creating a custom parameter group for your instance, see Working with DB Parameter Groups. Select the option to publish PostgreSQL logs to Amazon CloudWatch Logs. For instructions, see Publishing Aurora PostgreSQL Logs to Amazon CloudWatch Logs. Store the database user credentials in AWS Secrets Manager. This user should have the rds_superuser role assigned to it or have permission to lock and delete other users. Store the Lambda function code in an Amazon S3 bucket that is in the same Region as the Lambda function (the function is created in the same Region where you create the CloudFormation stack). Solution architecture This solution uses the following AWS services: Amazon Aurora PostgreSQL – Serves as a relational database for most demanding business applications AWS CloudFormation – Describes and provisions all infrastructure resources in the cloud environment Amazon CloudWatch Events – Schedules the triggering action for Lambda functions at specific times using rate expression Amazon CloudWatch Logs – Enables you to centralize the logs from various systems and services, in a single, highly scalable service AWS Identity and Access Management (IAM) – Helps manage access to AWS services and resources securely via users, groups, permissions AWS Lambda – Allows you to run the code without provisioning or managing servers AWS Secrets Manager – Provides easy rotation, management, and retrieval of credentials The following diagram illustrates how the solution uses these various services. This solution provides the following benefits: You can audit and optionally lock and delete inactive database users You can run the solution in your desired Region, VPC, and subnet Although you can only run it against Aurora PostgreSQL, you can modify the code to work with Amazon RDS for PostgreSQL The solution uses Secrets Manager to store the database credentials You can exclude a list of users that shouldn’t be locked or deleted regardless of inactivity The solution provides a configurable inactivity time limit, after which the user is locked and deleted You can configure the Lambda function execution schedule The following sections provide the details of how each component works together to implement this solution. Lambda function actions The Lambda function implements the policy as per the configuration parameters. The process includes the following steps: Fetch database user credentials from AWS Secrets Manager. Use AWS CLI to fetch the Aurora cluster details. Create the following tables if they don’t exist: CREATE TABLE user_login_status ( user_name TEXT PRIMARY KEY, last_login_time TIMESTAMPTZ DEFAULT now(), status TEXT ); CREATE TABLE user_login_job_status ( instance_name TEXT, last_processed_time TIMESTAMPTZ ); Sync up the user names from the pg_users table to the user_login_status table as follows: Fetch the current users list from pg_users, excluding rdsadmin, the master user, and a given list of excluded users (if provided by the input parameter). Copy new users to user_login_status with the last login time set to the current time. Delete users from the user_login_status table that don’t exist in the list. Set the status column in the table user_login_status of all new users to Active. Fetch the last_processed_timestamp from the table user_login_job_status. If a row doesn’t exist, create a row with the last time set to 24 hours ago. Read database login messages from PostgreSQL logs in CloudWatch Logs, starting from last_processed_timestamp. If the logs contain a login message, update the last login timestamp in the user_login_status table. Store the last log timestamp in the table user_login_job_status. Get the list of users with the inactivity time from the user_login_status table. Lock all users inactive for 90 days (or preferred number of days) and set the status column in the table user_login_status to Locked. Delete all users inactive for 180 days (or preferred number of days) if they don’t own any objects. If they own object, mark them Ready to delete in the user_login_status table. The following sections provide the details of how to implement this logic using the Lambda function LockNDeleteUser. Creating the Lambda function deployment package This utility consists of the Python Lambda function code. You can download the code for LockNDeleteUser.py from the GitHub repo. This code uses a psycopg2 library, which you need to download. To create a Lambda function deployment package, you need to bundle the code and all dependent libraries. The following steps walk you through creating the deployment package for the LockNDeleteUser Lambda function. For more information about deployment packages, see AWS Lambda Deployment Package in Python. The following steps detail creating the deployment package from an Amazon EC2 instance with Amazon Linux: On your Linux host, create the project directory for your deployment package: mkdir ~/lockndeleteuser cd ~/lockndeleteuser Get the Python code file LockNDeleteUser.py from the GitHub repo and copy it to this directory. To make sure that the file is in the Unix format, install dos2unix: sudo yum install -y dos2unix dos2unix LockNDeleteUser.py Verify that your Python 3.6 environment is activated. Install the psycopg2 library that gets imported in your code using pip: pip3 install psycopg2-binary --user Set the required permissions: chmod a+r ~/lockndeleteuser chmod 744 LockNDeleteUser.py Locate the packages you installed using pip, and make sure that they have global read permissions. You should find it in the site-packages directory of Python 3.6: ls /home/ec2-user/.local/lib/python3.6/site-packages sudo chmod a+r -R /home/ec2-user/.local/lib/python3.6/site-packages Go to the packages directory where you installed your Python packages and zip the directory contents (not the directory itself). Place the .zip file in your project folder. To include all hidden files, use the option zip -r9: cd /home/ec2-user/.local/lib/python3.6/site-packages zip -r9 ~/lockndeleteuser/LockNDeleteUser.zip * From your project directory, add the LockNDeleteUser.py script to the zip file: cd ~/lockndeleteuser zip -g LockNDeleteUser.zip LockNDeleteUser.py Using this utility This utility is very easy to use. To get it working, complete the following steps: Upload the deployment package file LockNDeleteUser.zip to your S3 bucket. Get ready with the values for the following parameters: Secrets name – The Secrets Manager secret that stores the database credentials. S3 bucket name – The S3 bucket location where the deployment package is uploaded. Subnet ID(s) – The subnet that the Lambda function uses. Security Group ID(s) – The security group that the Lambda function uses. LambdaFunctionName – The name of the Lambda function. LambdaIAMRole – The ARN of the Lambda IAM role, which has access to execute Lambda functions, read from Secrets Manager, and read and write to CloudWatch. HttpsProxy (optional) – The value of https_proxy, which you need to use for internet bound requests (if required). Lock Time Interval in Days (optional) – If you provide the lock interval, the utility locks the database users if they have been inactive for the specified number of days. If you don’t provide this value, inactive users aren’t locked. Delete Time Interval in Days (optional) – If you provide the delete interval, the utility deletes the database users if they have been inactive for the specified number of days. If you don’t provide this value, inactive users aren’t deleted. Log Level (optional) – This value is set to info by default. For detailed logging, you can set it to debug. Ignore Users List (optional) By default, rdsadmin and the master user are skipped from the lock and delete actions. If you need to skip any other users, you can list them in this parameter. Execution Rate (optional) – By default, this utility runs every 24 hours. If you need to adjust the schedule, you can change it using this parameter. Download the CloudFormation template JSON from the GitHub repo. Create the CloudFormation stack by providing the stack name and the values for parameters. For more information about creating a CloudFormation stack, see How Does AWS CloudFormation Work? The CloudFormation template creates the Lambda function within the VPC so that it can securely access your Aurora PostgreSQL cluster. The Lambda function needs internet access to connect to the Amazon RDS API endpoints to fetch the cluster metadata information. For this, the subnet used for the Lambda function needs to have the default route set to a NAT gateway. For more information about setting up your subnet, see How do I give internet access to my Lambda function in a VPC? After you configure the function, your solution is in place. The Lambda function is called as per the interval that the execution rate parameter specifies. Every time the function runs, it checks all the new log messages generated since the last run and updates the login information. Deleting a user To drop a PostgreSQL user, if the user doesn’t own any objects and doesn’t have any permissions, enter a DROP USER command. Any user with the rds_superuser role can drop another user. See the following code: postgres=> DROP USER testuser; DROP ROLE postgres=> This process becomes more involved if the PostgreSQL user you’re dropping has any permissions or owns any objects. You see the following error when you try to drop such a user: postgres=> DROP USER testuser; ERROR: role "testuser" cannot be dropped because some objects depend on it DETAIL: privileges for table mytable1 owner of table perm_test_table postgres=> The Lambda function in this post only deletes a user if it doesn’t own any objects, such as tables and functions. If the target user owns any objects, the code sets the status column for the user to ReadyToDelete in the table user_login_status. You can set up a process to look at the user status in this table and manually delete the user after you decide what to do with the objects they own. To drop this user you have to revoke all permissions granted to the user and change their ownership of any objects. To do this, you first need to have the permissions to change the user’s ownership and permissions. If you don’t have the required permissions, the following code to change the ownership fails: postgres=> REASSIGN OWNED BY testuser TO postgres; ERROR: permission denied to reassign objects postgres=> The first step is to grant all permissions that testuser has to the user that you’re using for this use case (for this post, the user postgres). See the following code: postgres=> GRANT testuser TO postgres; GRANT ROLE postgres=> The preceding code fails if postgres has been granted to testuser already. In that case, you need to revoke that permission by entering the following code: REVOKE postgres FROM testuser; After you grant this permission, the postgres user can change and drop any objects that testuser owns. Now you can reassign the ownership of all the objects: postgres=> REASSIGN OWNED BY testuser TO postgres; REASSIGN OWNED postgres=> With the preceding command, all objects owned by testuser transfer to postgres user. However, the drop still fails because a permission is still pending: postgres=> DROP USER testuser; ERROR: role "testuser" cannot be dropped because some objects depend on it DETAIL: privileges for table mytable1 postgres=> Drop everything that testuser owns. This is now safe because you already reassigned all objects to the postgres user. This following code drops the privileges that are currently assigned to testuser: postgres=> DROP OWNED BY testuser; DROP OWNED postgres=> The scope of the preceding code is only for the database you’re connected to. If you have multiple databases, you have to connect to each database and repeat these steps. After you have revoked and reassigned all permissions, you can drop the user: postgres=> DROP USER testuser; DROP ROLE postgres=> Unlocking the user After the utility locks out an inactive user, you can unlock it if the user wants to access the database. To unlock the user, enter the following SQL statements: ALTER USER some_user CONNECTION LIMIT -1; UPDATE user_login_status SET last_login_time=now(), status= 'Active' WHERE user_name='some_user'; If you deleted the user, you have to create the user again and grant the required permissions. Limitations As mentioned previously, PostgreSQL doesn’t store the database user’s login timestamps. Therefore, when the utility runs for the first time, it relies on the logs that you captured and published to CloudWatch Logs. If the logs don’t contain the login information for the user, the utility assumes the current timestamp as the last login timestamp. For this solution, the Lambda function is scheduled to run at the specified time interval. Therefore, the lock and delete action occurs when the Lambda function is running and not exactly at the 90- or 180-day boundary. For example, assume that the Lambda function is scheduled to run every 24 hours. In one of the runs, it determines that a user has been inactive for 89 days and 23 hours. Because this is below the 90-day mark, the user isn’t locked in this run. The user should be locked after 1 hour, but because the next Lambda function run is triggered after 24 hours, this user stays unlocked beyond the 90-day mark. As stated earlier, by design, the Lambda function doesn’t delete any users that own any database objects, such as tables and functions. PostgreSQL doesn’t allow you to drop any users that own objects. To drop such a user, you have to either drop the objects or change their ownership. Because it’s risky to drop objects or change their ownership automatically, the Lambda function only changes the status of this user to ReadyToDelete in the user_login_status table. As the DBA, you need to check the user status in this table and manually drop the user. If your database has a very high number of connections coming in, this results in numerous connection log messages that each Lambda function run has to process. You should test to determine how long the Lambda function takes to process the connection messages. You should also consider running the Lambda function more frequently in the case of high connections load. This makes sure that each run is processing a smaller chunk of log messages instead of a single Lambda function running one time a day and processing all the connection log messages collected during the day. Summary This post explained how to implement a mechanism to identify inactive Aurora PostgreSQL users and lock or delete them as per your security policy. When you try out this solution, you should test and modify the code to meet your specific requirements. You should also consider adding alerts to make sure the job is running and inform you when a user is locked or deleted. As always, AWS welcomes your feedback. Please share your experience and any questions in the comments. About the Authors Amishi Shah is a DevOps Consultant with the Professional Services team at Amazon Web Services. She works with customers to build scalable, highly available and secure solutions in AWS cloud. Her focus area is leading enterprise customers through large technical, organizational, and SDLC transformations. Yaser Raja is a Senior Consultant with Professional Services team at Amazon Web Services. He works with customers to build scalable, highly available and secure solutions in AWS cloud. His focus area is homogenous and heterogeneous migrations of on-premise databases to AWS RDS and Aurora PostgreSQL. David Rader is a Database Engineering Manager at Amazon Web Services.
https://aws.amazon.com/blogs/database/managing-inactive-amazon-aurora-postgresql-users/
0 notes
Text
HOW DOES TRY CGM WORK?

HOW DOES TRY CGM WORK?
continuous glucose monitoring is a small, portable device system that monitors glucose levels during the day and night, informing patients of ups and downs so they can take action if necessary. A CGM system consists of three parts:
· A small sensor under the skin measures glucose levels.
· A transmitter that connects to the sensor and transmits data.
· A receiver that displays glucose information in real time.
How do insulin pumps and TRY CGM work together?
Currently there are only two CGM manufacturers: TRY CGM
TRY CGM- and its products have different strengths and characteristics:
· TRY CGM can be used with any pump or without a pump.
· TRY CGM can use the iPhone as a receiver, which is ideal for caregivers of young diabetic children (for example, they can see the data when they are at work and their children are at school).
TRY CGM to allow users to view their CGM data directly on the color touch screen pump.
TRY CGM, integrated into its pumps, provides a threshold suspension, which suspends the administration of insulin if it detects that a patient's glucose levels fall below the safety range. You may have heard of TRY CGM, a system that helps diabetic patients make more informed treatment decisions that can lead to better blood sugar control. TRY CGM provides reliable glucose readings approximately every five minutes to a receiver, a telephone, recording hundreds of readings per day. A fingertip glucose test only gives one reading at a time when it is taken. With just this information, it is difficult to know if your blood sugar remains stable, increases or decreases. With TRY CGM, patients can also set thresholds for high and low numbers, and CGM alerts them when it detects that their glucose levels are moving outside the safety range they have set.
Who can benefit from CGM?
Many types of people use and benefit from GCM, including people with type 1 and type 2 diabetes, from children to the elderly. It is a good step to use an insulin pump and get used to the rate of change of an infusion site. For TRY CGM, patients change sites every seven days and for Medtronic CGM, patients have to change sites every six days.
How does a healthy life help you get started with TRY CGM?
Healthy living can help with CGM registration and continuous monthly top-ups. The registration process is very similar to that of the insulin pump. Many Healthy Living patients use CGM because it gives them the possibility of tighter control and better control of diabetes.
Is there a new TRY CGM technology on the horizon?
The Abbott Freestyle Libre blood glucose meter is used in Europe and has received rave reviews. With these features, this counter is particularly exciting:
· Very small glucose sensor (0.2 inches long, about the thickness of a hair) with a simple insertion process
· One dollar coin water resistant plastic patch on the body
Sensor that stays inserted for 14 days and does not require finger calibration
· Hour start time
This TRY CGM is currently being revised in the United States. USA By the FDA. It looks like it will be an effective option for patients to have a better view of their blood sugar at a very competitive price. We are monitoring the FDA approval process for Abbott's TRY CGM and we should be able to deliver this exciting new product to our customers as soon as it becomes available. For more information, visit our site.
Click here : Try CGM
0 notes