#HTTP reverse proxy
Explore tagged Tumblr posts
Text
Using an HTTP reverse proxy is a common need for developers who want to securely expose their localhost to the internet. Localtonet provides an easy-to-use solution, allowing developers to create secure tunnels for local servers. Whether you're testing webhooks or collaborating on projects, Localtonet’s reverse proxy ensures secure communication and quick setup. "With Localtonet, setting up an HTTP reverse proxy is just a few clicks away, making your development experience smoother and safer."
0 notes
Text
Too much thought into Raphael's "Real" Plan
I think most people would agree that taking the Crown and just putting it on/hoping for the best sounds like a terrible, risky plan. I believe Raphael when he says that he's not a mortal and can take it but then what? Try to take the Weave from Mystra like Karsus intended to? I'm sure Mystra would have a plan to deal with this because she's not an idiot. It's also too obvious and not really as simple as getting the Crown in any case. To truly use the Crown to seize the Weave and control all magic, he would also need the spell Karsus's avatar which, assuming he found it, wouldn't work because of Mystra's capping of spells at Level 10. However, there might still be a way to give Raphael a boost in power that makes him nigh undefeatable. We encounter Karsus's journal in the game which contains his plans for the Crown. An intelligent man who was around and probably met Karsus, with his journal and the Crown could probably reverse engineer the Spell even if he couldn't get his hands on the original. I think, however, that Raphael knew or knows how to get it but that's just speculation. He says he knows multiple ways to get what he wants from people and I think this applies to most areas of his life. So, let's assume he gets the spell and the Crown, he still can't cast it because of Mystra's cap which she implemented to protect the Weave. However, there is a second, unregulated Weave, the Shadow Weave which is Shar's dark magic repository and what I would say is the Anti-matter version of regular magic. It's as powerful as Mystra's Weave and mostly untapped because of what a twat Shar is. If Raphael can modify or adapt the spell to seize Shar's divinity instead of Mystra's then he would have a lot of power to wield. I theorise as well that he can cast the spell in the Shadow Realm/Shadowfell which uses the Shadow Weave instead of Mystra's magic which would effectively get around the Level 10 restriction. If he can sieze power from Shar (who he's been weakening for many years by proxy) then he can...well, maybe, he'll be able to use it to infect and devour Mystra's Weave; the way Gale's bit of contaminated magic sought to devour it. If this comes to pass, even if he gets a portion of the Weave, he is already as powerful as Mystra. If he gets all the Weave, then he can control who can use magic and who can't, effectively crippling the Devils who rely on it. His father is obsessed with magic and experimentation so this would be a personal insult and blow to him. Effectively, Raphael would be using a magical artifact that Mephistopheles dismissed to seize the source of power for Gods and Devils alike. One hell of a coup d'etat. He could then, maybe, use that power to turn all of Earth into the Shadowlands where people die but their souls remain on Earth being no use to either Gods or Devils. This is very very speculative though since the lore doesn't state it definitively. Of course, this is all a series of assumptions with the expectation that everything goes according to plan. Raphael's arrogance, narcissism and trust issues mean that he will 100 percent overlook things in this process; it's hard to see individual flaws when you've been looking at the whole picture for too long. Anyway, this theory probably has a ton of flaws, if you spot one, it's okay to let me know. It's just for fun after all. https://forgottenrealms.fandom.com/wiki/Karsus%27s_Folly https://forgottenrealms.fandom.com/wiki/Karsus%27s_avatar https://criticalrole.fandom.com/wiki/Shadowfell https://bg3.wiki/wiki/The_Annals_of_Karsus
#raphael bg3#bg3 raphael#bg3 fanfic idea#bg3 headcanons#bg3 musing#I probably put more thought into his plan than he did -_-#bg3 mystra#bg3 ladysharisabitch
41 notes
·
View notes
Text
ok since i've been sharing some piracy stuff i'll talk a bit about how my personal music streaming server is set up. the basic idea is: i either buy my music on bandcamp or download it on soulseek. all of my music is stored on an external hard drive connected to a donated laptop that's next to my house's internet router. this laptop is always on, and runs software that lets me access and stream my any song in my collection to my phone or to other computers. here's the detailed setup:
my home server is an old thinkpad laptop with a broken keyboard that was donated to me by a friend. it runs yunohost, a linux distribution that makes it simpler to reuse old computers as servers in this way: it gives you a nice control panel to install and manage all kinds of apps you might want to run on your home server, + it handles the security part by having a user login page & helping you install an https certificate with letsencrypt.
***
to stream my music collection, i use navidrome. this software is available to install from the yunohost control panel, so it's straightforward to install. what it does is take a folder with all your music and lets you browse and stream it, either via its web interface or through a bunch of apps for android, ios, etc.. it uses the subsonic protocol, so any app that says it works with subsonic should work with navidrome too.
***
to listen to my music on my phone, i use DSub. It's an app that connects to any server that follows the subsonic API, including navidrome. you just have to give it the address of your home server, and your username and password, and it fetches your music and allows you to stream it. as mentionned previously, there's a bunch of alternative apps for android, ios, etc. so go take a look and make your pick. i've personally also used and enjoyed substreamer in the past. here are screenshots of both:
***
to listen to my music on my computer, i use tauon music box. i was a big fan of clementine music player years ago, but it got abandoned, and the replacement (strawberry music player) looks super dated now. tauon is very new to me, so i'm still figuring it out, but it connects to subsonic servers and it looks pretty so it's fitting the bill for me.

***
to download new music onto my server, i use slskd which is a soulseek client made to run on a web server. soulseek is a peer-to-peer software that's found a niche with music lovers, so for anything you'd want to listen there's a good chance that someone on soulseek has the file and will share it with you. the official soulseek client is available from the website, but i'm using a different software that can run on my server and that i can access anywhere via a webpage, slskd. this way, anytime i want to add music to my collection, i can just go to my server's slskd page, download the files, and they directly go into the folder that's served by navidrome.
slskd does not have a yunohost package, so the trick to make it work on the server is to use yunohost's reverse proxy app, and point it to the http port of slskd 127.0.0.1:5030, with the path /slskd and with forced user authentification. then, run slskd on your server with the --url-base slskd, --no-auth (it breaks otherwise, so it's best to just use yunohost's user auth on the reverse proxy) and --no-https (which has no downsides since the https is given by the reverse proxy anyway)

***
to keep my music collection organized, i use beets. this is a command line software that checks that all of the tags on your music are correct and puts the file in the correct folder (e.g. artist/album/01 trackname.mp3). it's a pretty complex program with a ton of features and settings, i like it to make sure i don't have two copies of the same album in different folders, and to automatically download the album art and the lyrics to most tracks, etc. i'm currently re-working my config file for beets, but i'd be happy to share if someone is interested.
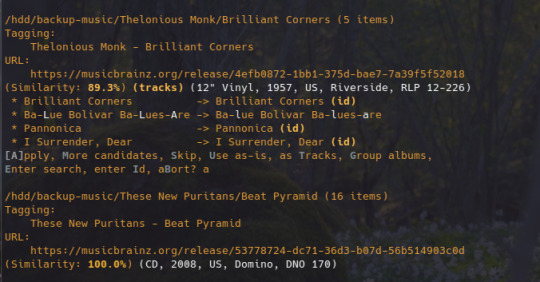
that's my little system :) i hope it gives the inspiration to someone to ditch spotify for the new year and start having a personal mp3 collection of their own.
34 notes
·
View notes
Text
https://github.com/dexter-proxy
<3
ERR_ECH_FALLBACK_CERTIFICATE_INVALID
this was my github account when I use to be really into programming , I was really good at it . Infact I was so good at it that everyone I once knew became trapped in a mixed matrix loop glitch of an 80's high-school drama flick & a super hero movie . Under ideals between war in a loop where there are no friends and where there is nothing but meaningless bitcoin . I stopped programming because after awhile I got sick of the same looped behavior in the same states of mind without really paying attention :: the loop always goes something like this [ I'm important & needed , am I villain, what good am I ] the entire ideal trying to hide the idea that I'm only lied to through fear . The idea that rape has been hunted down for a long time on the internet due to the darkwebs popularity was always something I was good at , in fact I was so good at it people made me out as a lieing joke and put my entire life on a zoo display like a child to make fun of calling it nobility . This is cursed by the old gods . Though 🤔 .... the same loop always follows because that's only the human behavior aspect that's how c++⁹⁸ was created as a subjective of C programming . Though even the idea of helping me was used against people to make people into basically brain dead nothingness hoping to hide . Sorry ( not really ) it's not my war in the first place . English is kind of lame . I made such a HUGE COOL internet trench that no one will ever explore . That's okay .
英•語目がクチる ° 本の方が使いい • 但只能在同一个循环中 ° 最终每个人都会停下来,然后这个循环再次开始 ,
that is impossible I guess to comprehend . So I made a place where we could post hentai and porn and not be bothered this
http://blueponyfdt5emnvtabzgfy36bwakan225x4fxvttgt2ov2dbkcqgdad.onion
This is my friend ^-^ ^-^ <3
error in E explorer indicates an issue with Encrypted Client Hello (ECH) and its fallback mechanism, specifically when a reverse proxy or other network middlebox interferes with the ECH handshake. This error usually occurs when a site uses ECH for secure connections, but the browser (E explorer , in this case) detects that the fallback certificate presented by the server is invalid or untrusted.
3 notes
·
View notes
Note
hi! about piermesh, i was wondering if you envision operators hosting their endpoint online (versus having a local network for people near by to connect to and access the endpoint this way)? or is there another way?
would a node be able to connect to a node in another city 70km away?
would several piermesh networks be able to exist in the same area? (ie if one network's operators want it to only be accessible locally and the other network's operators expose it online. would there be another way to achieve that without disconnecting the two networks from one another?)
i might try to set up nodes in my city!!
Great questions thank you!
Because PierMesh exposes a web interface/site by default it's entirely possible to expose that interface to the internet with common web technologies like port forwarding and reverse proxying and in fact this is how we plan for people to access the prototype network.
A node can connect over as many as 254 km (https://meshtastic.org/docs/overview/range-tests/) and in fact I got the specific hardware that achieves this for testing ~1 month ago and will be running my own tests sometime soon.
As far as running different PierMesh networks this is entirely possible but Siph (our graph based network stack) needs a bit more work before that functionality is entirely accounted for. That being said we also plan to genericize PierMesh into a system where people can deploy their own versions very easily.
8 notes
·
View notes
Text
Critical Vulnerability (CVE-2024-37032) in Ollama

Researchers have discovered a critical vulnerability in Ollama, a widely used open-source project for running Large Language Models (LLMs). The flaw, dubbed "Probllama" and tracked as CVE-2024-37032, could potentially lead to remote code execution, putting thousands of users at risk.
What is Ollama?
Ollama has gained popularity among AI enthusiasts and developers for its ability to perform inference with compatible neural networks, including Meta's Llama family, Microsoft's Phi clan, and models from Mistral. The software can be used via a command line or through a REST API, making it versatile for various applications. With hundreds of thousands of monthly pulls on Docker Hub, Ollama's widespread adoption underscores the potential impact of this vulnerability.
The Nature of the Vulnerability
The Wiz Research team, led by Sagi Tzadik, uncovered the flaw, which stems from insufficient validation on the server side of Ollama's REST API. An attacker could exploit this vulnerability by sending a specially crafted HTTP request to the Ollama API server. The risk is particularly high in Docker installations, where the API server is often publicly exposed. Technical Details of the Exploit The vulnerability specifically affects the `/api/pull` endpoint, which allows users to download models from the Ollama registry and private registries. Researchers found that when pulling a model from a private registry, it's possible to supply a malicious manifest file containing a path traversal payload in the digest field. This payload can be used to: - Corrupt files on the system - Achieve arbitrary file read - Execute remote code, potentially hijacking the system The issue is particularly severe in Docker installations, where the server runs with root privileges and listens on 0.0.0.0 by default, enabling remote exploitation. As of June 10, despite a patched version being available for over a month, more than 1,000 vulnerable Ollama server instances remained exposed to the internet.
Mitigation Strategies
To protect AI applications using Ollama, users should: - Update instances to version 0.1.34 or newer immediately - Implement authentication measures, such as using a reverse proxy, as Ollama doesn't inherently support authentication - Avoid exposing installations to the internet - Place servers behind firewalls and only allow authorized internal applications and users to access them
Broader Implications for AI and Cybersecurity
This vulnerability highlights ongoing challenges in the rapidly evolving field of AI tools and infrastructure. Tzadik noted that the critical issue extends beyond individual vulnerabilities to the inherent lack of authentication support in many new AI tools. He referenced similar remote code execution vulnerabilities found in other LLM deployment tools like TorchServe and Ray Anyscale. Moreover, despite these tools often being written in modern, safety-first programming languages, classic vulnerabilities such as path traversal remain a persistent threat. This underscores the need for continued vigilance and robust security practices in the development and deployment of AI technologies. Read the full article
2 notes
·
View notes
Note
do u have those taobao listings on hand by any chance?? reverse image search doesnt seem to work and looking up the chinese language version of mlp on there i dont think brings me any results? :(
I tagged them as Taobao, but checking just now I see the listing is actually on Alibaba. Here's the link:
https://detail.1688.com/offer/801736603390.html
I always have trouble getting Alibaba listings to come up for me, but if you're using BaseTao (proxy buyer) that should be enough to buy.
6 notes
·
View notes
Text
how to and why need WordPress website speed optimization?
In today's fast-paced digital world, speed optimization plays a crucial role in delivering a seamless user experience and achieving business success. This article will discuss the significance of speed optimization and explore various techniques to enhance the performance of websites, applications, and digital platforms.
The Significance of Speed Optimization : Speed optimization refers to the process of improving the loading time and overall performance of a website or application. It is vital for several reasons. Firstly, users have become increasingly impatient and expect instant access to information. A slow-loading website or application can lead to frustration and drive users away, resulting in lost opportunities and reduced conversions. Secondly, search engines like Google consider page speed as a ranking factor, influencing a website's visibility and organic traffic. Therefore, speed optimization directly impacts search engine optimization (SEO) efforts and online visibility.
hire me for website optimization: https://www.fiverr.com/jobair_webpro
Techniques for Speed Optimization
Compressed and Minified Code: Reduce the file sizes of HTML, CSS, and JavaScript by compressing and minifying them. This reduces the bandwidth required for downloading, resulting in faster page load times.
Image Optimization: Optimize images by compressing them without sacrificing visual quality. This can be achieved through various techniques, such as using the appropriate image format (JPEG, PNG, etc.), resizing images to the required dimensions, and leveraging modern image formats like WebP.
Caching: Implement browser caching to store frequently accessed files on the user's device, reducing the need for repeated downloads. This improves load times for returning visitors.
Content Delivery Network (CDN): Utilize a CDN to distribute website content across multiple servers worldwide. CDN servers located closer to the user reduce latency and enable faster content delivery.
Minimize HTTP Requests: Reduce the number of HTTP requests made by the browser by combining multiple files into one. This can be achieved by merging CSS and JavaScript files, using CSS sprites, or inlining small CSS and JavaScript directly into HTML.
Server-Side Optimization: Optimize server configurations, database queries, and scripting languages to improve response times. Techniques include enabling server compression (Gzip), using a reverse proxy cache, and optimizing database queries.
Responsive Design: Ensure your website or application is responsive and optimized for different devices and screen sizes. This ensures a consistent user experience across platforms and reduces the need for unnecessary downloads or device-specific redirects.
Speed optimization is crucial for delivering a positive user experience, improving search engine rankings, and achieving business goals. By implementing techniques such as code compression, image optimization, caching, and server-side optimizations, organizations can enhance the speed and performance of their digital platforms, resulting in increased user engagement and better conversion rates.
Hire me for website speed optimization: https://www.fiverr.com/jobair_webpro/
#wordpress#speed optimization#wordpress speed optimization#speed up#seo optimization#onpageseo#on page optimization
2 notes
·
View notes
Text
📝 Event Overview
◆ About General Participation ◆
Participation Fee: Free
※ Registration on Picre is required in advance.
◆ For Overseas Participants ◆
Those participating from outside Japan can join under the same conditions as domestic participants if they have the following:
Internet accessPayment method (※ for club participants only)※ All dates and times mentioned are based on Japan Standard Time (JST).

◆ About Club Participation ◆
Participation Fee: 550 yen (system usage fee)
~ Club Registration Period ~
From: June 1, 2025, 00:00 JST
To: November 9, 2025, 23:59 JST
▶︎ What You Need:
Works for distribution or displayCircle cut (Cut illustration)Catalog (list of works)Participation fee (550 yen system usage fee)Templates exclusive to this event will be distributed via the event site.
→ [Official Picrea Template Here]
▶︎ Application Process:
①Register an account on Picrea.

②Register your club. Go to the menu “≡” on the upper left of the homepage, and select “Circle Basic Settings” under “Apply for Event.”


③Apply via the event participation page.
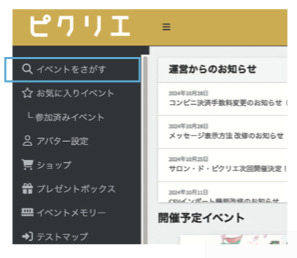

Once the above settings are complete, please apply using the “Apply for Circle Participation” button on the event page. Your application will be complete after payment of the participation fee.
For more detailed procedures and settings, refer to the official guide:→ Official Guidebook: https://picrea.jp/manual#howto
▶︎ About Cancellations
If you wish to cancel, please contact the organizer by 12:00 PM (JST) on November 20, 2025.
▶︎ OK
Distribute doujinshi, goods, etc. themed around ryuasoExhibit web content on the same theme(e.g., illustrations, novels, tanka, poetry, cosplay, MMD, handmade items, photography, analysis, commentary, etc.)Exhibit past works onlineDistribute via network printingExhibit or distribute even if the creator is not present on the day.
▶︎ NG
Exhibit or distribute works unrelated to ryuasoParticipate via proxy/consignmentSell downloadable content for a fee or take preorders(※ Judged based on Japanese secondary creation standards)Exhibit or distribute adult content by minorsInclude adult content in publicly visible areas such as the club cut, catalog, or public postsExhibit or distribute works that violate secondary creation etiquette.
▶︎ Important Notes
Works with age restrictions must be clearly labeled.While works based on the ryuaso concept are broadly accepted, content that includes special elements (e.g., reversible/alternate pairings, dream/fan insert content, other pairings, depictions of blood/injury, genderswap, alternative universes, etc.) must be clearly indicated in an easily noticeable location.
︎ ▶︎Event Guidelines
Please review and strictly adhere to the Picrea Terms of Use.
Disruptive behavior, as well as slander or defamation via “Hitokoto” posts or chat, is strictly prohibited.
The organizers will not intervene in personal disputes; however, if any disruptive behavior is observed within the venue, we may take measures including forced removal from the premises.
Photography inside the venue is permitted, but if you plan to post photos on social media or other platforms, please make sure to obtain permission from the circle representative(s) and anyone else who may appear in the images.
1 note
·
View note
Text
#HướngDẫnCàiNginxTrênUbuntu2204 #CấuHìnhPort80Và443 #Thuecloud
#HướngDẫnCàiNginxTrênUbuntu2204 #CấuHìnhPort80Và443 #Thuecloud — Hướng Dẫn Cài Đặt Nginx Trên Ubuntu 22.04 – Mở Port 80 & 443 Cho HTTPS Nginx là một trong những web server mạnh mẽ, hiệu suất cao và tiết kiệm tài nguyên, đồng thời đóng vai trò như reverse proxy, load balancer hoặc cache server cho các ứng dụng web hiện đại. Bài viết này sẽ hướng dẫn bạn từng bước cài đặt Nginx trên Ubuntu 22.04,…
0 notes
Text
So, I don’t have a lot of brain-juice to spare lately. Mostly because I’ve been reeling from the existential crisis of turning forty … uh, TOMORROW (as of posting this), and I’ve been adjusting to a different position at work, which also comes with longer hours. But, with the limited juice I have, and the start of a tiny vacation from work, I went ahead and hashed out the things I would need to do to:
1: move my website to my own server
2: enable Anubis in order to protect against all AI scrapers
And I’ve done that! In a miraculously short amount of time.
This website will no longer be hosted on Github, where everything you write is being scraped by Copilot, and it’ll also no longer be subject to “action” fees once you reach into the 2000+ actions (this website does a lot of stuff). This also means that I won’t be actively pushing my site to Neocities, but honestly? Having this place hosted on my own server basically lifts every and all restrictions. Including the ability to install and host Anubis as a way to protect against AI.
Neocities is great, but I do have my doubts about the owner and his stance on the grand-theft of all things for corporate greed and the destruction of the arts, but for a measly 6 dollars a month to run a server, I can now do … whatever the hell I want.
But, it’s not just important to protect against AI scrapers in order to retain your work and the things you do as your own, and not something for Google or Sam Altman to make a profit off of, but also because, sometimes, when these bots hit yours servers, it is effectively a DDoS. And, I don’t know how many people know, but bandwidth exploding from aggressive bots trying to steal everything you’ve ever done WILL eventually incur charges upon you, that could be astronomical.
If you’re reading this though, you’ve already had your http request passed through Anubis, and you are not AI.
Congratulations.
My only stipulation about Anubis are the instructions on getting everything running. In that, they’re pretty bare-bones, and it took me putting on my thinking cap to get past that.
Things I’ll note for others who potentially want to build against AI using Anubis.
1: You have to actually download the package and put it on your server first, and if you constantly forget things (like me), or are new to these sorts of things, you might have forgotten/don’t know how to do this. Just setup FileZilla with some SSH privileges and drop the package into your root folder.
2: In the setup instructions on the Anubis website, it mentions an example where you’re building Anubis to protect a Gitea server. This threw me for a loop, because I was like, “Uh, well, what if I’m just protecting a website?? What do I input??” And this was clarified by the developer themselves … you just write whatever. So, mine is “nova.”
3: Reverse-proxying is a super advanced thing that regular users have probably zero experience with, but, basically, get rid of your default Nginx server configuration, and make sure you’ve already got your SSL running via certbot, and follow everything on the page via Nginx configuration to the T. You’ll need the upstream, and in my case, I created a secondary config file in sites-available where my site is running on port 3000, that the actual config (that proxies Anubis) points to.
Convoluted! But, actually, pretty simple, once you’ve wrapped your head around it.
I could probably confidently walk you through it, if you’d like to do exactly what I just did.
Otherwise, onward! To the future!
… and being forty, I guess.
Source: Original Post
Posted via Python, written by @daemon_nova
0 notes
Link
[ad_1] From zero-day exploits to large-scale bot attacks — the demand for a powerful, self-hosted, and user-friendly web application security solution has never been greater. SafeLine is currently the most starred open-source Web Application Firewall (WAF) on GitHub, with over 16.4K stars and a rapidly growing global user base. This walkthrough covers what SafeLine is, how it works, and why it's becoming the go-to solution over cloud-based WAFs. What is SafeLine WAF? SafeLine is a self-hosted web application firewall that acts as a reverse proxy, filtering and monitoring HTTP/HTTPS traffic to block malicious requests before they reach your backend web applications. Unlike cloud-based WAFs, SafeLine runs entirely on your own servers—giving you unmatched visibility and data sovereignty. Key Features of SafeLine WAF Comprehensive Attack Prevention SafeLine effectively blocks a wide range of common and advanced web attacks, including SQL injection(SQLi), cross-site scripting (XSS), OS command injection, CRLF injection, XML External Entity (XXE) attacks, Server Side Request Forgery (SSRF), and directory traversal, etc. Zero-Day Detection via Semantic Analysis Unlike traditional signature-based WAFs, SafeLine uses a patented semantic analysis engine that deeply parses HTTP traffic semantics. This approach enables it to detect complex and zero-day attacks with high accuracy, resulting in an industry-leading detection rate of 99.45% and an ultra-low false positive rate of 0.07%. (The chart below compares SafeLine with the two versions of a globally recognized open-source WAF.) Robust Bot Protection SafeLine delivers comprehensive, multi-layered defenses against automated bot attacks, a growing threat vector responsible for credential stuffing, malicious scraping, inventory hoarding, and vulnerability scanning. It combines several out-of-box powerful mechanisms: CAPTCHA Challenges: Dynamically issued to distinguish human users from automated clients, especially in suspicious or high-risk traffic scenarios. Dynamic Protection: Randomly encrypts and obfuscates frontend code, such as HTML and JavaScript, before delivering it to the client. This prevents bots from reliably parsing page structures or interacting with DOM elements, rendering automated scripts ineffective. Anti-Replay Mechanisms: Detect and block reuse of tokens, headers, or payloads often leveraged in scripted attacks or credential stuffing campaigns. HTTP Flood DDoS Mitigation HTTP flood DDoS attacks attempt to overwhelm servers by sending massive volumes of HTTP requests in a short period of time. These attacks can exhaust server resources, degrade performance, or take applications offline entirely. To counter this, SafeLine implements rate limiting to cap request frequency and mitigate abuse. These measures are highly configurable, allowing defenders to tailor thresholds based on real-world traffic patterns. For sudden traffic spikes—whether legitimate or malicious—SafeLine provides a virtual waiting room mechanism. This ensures service availability by queuing excess users and releasing them gradually, preventing backend overload while maintaining a fair and orderly access experience. Authentication Challenges SafeLine is also designed with Zero Trust principles in mind—never trust, always verify. It offers configurable visitor authentication to secure access to protected applications, enhancing security through enforced identity checks. As a built-in identity gateway, it supports modern authentication protocols such as OIDC and integrates seamlessly with identity providers like GitHub and others. SafeLine also supports Single Sign-On (SSO) to streamline user authentication and simplify login experience in the meantime. Best of all, these enterprise-grade identity features are included for free. Simple Deployment in Minutes SafeLine is designed for quick setup and easy management. It requires the following environment to be installed and run: Operating System: Linux (x86_64 or arm64) Dependencies: Docker (version 20.10.14 or higher) and Docker Compose (version 2.0.0 or higher) Minimum System Requirements: 1 CPU core, 1 GB of RAM, and 5 GB of available disk space Once the environment is ready, installation takes just a few minutes with a single command. bash -c "$(curl -fsSLk -- --en A user-friendly, wizard-based interface guides you through configuration. Full documentation is available here. Why Choose SafeLine Over Cloud-Based WAFs? Unlike traditional cloud-based WAFs that route your traffic through third-party infrastructure, SafeLine offers complete deployment autonomy. Here are the advantages: Full Data Control: Sensitive traffic and logs remain on-premises, reducing exposure to third-party cloud risks. Cost Efficiency: Avoids recurring subscription fees common with cloud WAFs, especially beneficial for high-traffic environments. Free and Out-of-Box Enterprise Features: Advanced threat detection, bot protection, identity authentication, and more—typically gated behind "premium" tiers elsewhere—are out-of-box and included for free. Get SafeLine — free forever for personal use, with optional 7-day Pro trial. Use Cases Ideal for SafeLine SafeLine is a versatile solution built for a wide range of web application security needs. It's particularly well-suited for: Organizations with strict data privacy or regulatory compliance requirements Teams Targeted by Sophisticated Bots and Automated Threats Small and medium-sized businesses seeking affordable, enterprise-grade protection DevOps and Security Teams Requiring Full Deployment Control and Customization Projects requiring rapid deployment and easy maintenance Final Words SafeLine stands out as a powerful, open-source alternative to traditional cloud-based WAFs. With cutting-edge zero-day detection, robust bot mitigation, and zero trust–aligned identity features—all bundled into a self-hosted, easy-to-deploy package—SafeLine empowers developers, security teams, and organizations of all sizes to take control of their web security. Get SafeLine — free forever for personal use, with optional 7-day Pro trial. Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to read more exclusive content we post. [ad_2] Source link
0 notes
Text

Introduction
Nginx is a high-performance web server that also functions as a reverse proxy, load balancer, and caching server. It is widely used in cloud and edge computing environments due to its lightweight architecture and efficient handling of concurrent connections. By deploying Nginx on ARMxy Edge IoT Gateway, users can optimize data flow, enhance security, and efficiently manage industrial network traffic.
Why Use Nginx on ARMxy?
1. Reverse Proxying – Nginx acts as an intermediary, forwarding client requests to backend services running on ARMxy.
2. Load Balancing – Distributes traffic across multiple devices to prevent overload.
3. Security Hardening – Hides backend services and implements SSL encryption for secure communication.
4. Performance Optimization – Caching frequently accessed data reduces latency.
Setting Up Nginx as a Reverse Proxy on ARMxy
1. Install Nginx
On ARMxy’s Linux-based OS, update the package list and install Nginx:
sudo apt update sudo apt install nginx -y
Start and enable Nginx on boot:
sudo systemctl start nginx sudo systemctl enable nginx
2. Configure Nginx as a Reverse Proxy
Modify the default Nginx configuration to route incoming traffic to an internal service, such as a Node-RED dashboard running on port 1880:
sudo nano /etc/nginx/sites-available/default
Replace the default configuration with the following:
server { listen 80; server_name your_armxy_ip;
location / {
proxy_pass http://localhost:1880/;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
Save the file and restart Nginx:
sudo systemctl restart nginx
3. Enable SSL for Secure Communication
To secure the reverse proxy with HTTPS, install Certbot and configure SSL:
sudo apt install certbot python3-certbot-nginx -y sudo certbot --nginx -d your_domain
Follow the prompts to automatically configure SSL for your ARMxy gateway.
Use Case: Secure Edge Data Flow
In an industrial IoT setup, ARMxy collects data from field devices via Modbus, MQTT, or OPC UA, processes it locally using Node-RED or Dockerized applications, and sends it to cloud platforms. With Nginx, you can:
· Secure data transmission with HTTPS encryption.
· Optimize API requests by caching responses.
· Balance traffic when multiple ARMxy devices are used in parallel.
Conclusion
Deploying Nginx as a reverse proxy on ARMxy enhances security, optimizes data handling, and ensures efficient communication between edge devices and cloud platforms. This setup is ideal for industrial automation, smart city applications, and IIoT networks requiring low latency, high availability, and secure remote access.
0 notes
Link
#Automation#backup#cloudstorage#collaboration#dataprivacy#database#Docker#filesharing#HTTPS#Install#Linux#networking#Nextcloud#Nextcloudsetup#open-source#reverseproxy#Security#self-hosted#Server#systemadministration
0 notes
Text
Trump claims tariffs could replace income tax
Trump claims tariffs could replace income tax https://www.rt.com/business/615807-us-global-tariffs-trump/
We always thought that Trumpet's "Liberation Day" was all about kicking these foreign bums out from the US.
But now we find out.. it was also about Trumpet's 'great' tariffs on the world idea, as well. Why then.. is Trumpet losing so much hair and getting redder and redder in the face, with each new day passing him by?
Perhaps loss of sleep, and all the Trumpet tariff reversals, on the next day...
Or...perhaps because now, some great adviser told him, that tariffs would replace the need for income tax. And essentially that means, that Americans won't have to work.. but just stay home, and enjoy the "greatest country in the world", the fantasy Trumpet World. Sounds like US Paradise, to all these struggling in the US, who now have to pay incredible penalties, just for their most basic survival.
However, that will only be even slightly possible, after Trumpet kicks out a hundred million new immigrants, with those that are first generation US citizens.. AND even more importantly, after Trumpet's huge tariff gamble, and incredibly high economic and financial risk, coming off, as he imagined the US tariffs on the world, would bring.
But let's recall, the recent hugely important Washington and combined western battle against the Russian Federation. The Washington led war on The Russian Federation, was a military, total economic and political war against just one country..but not just any one country.. It's the Russian Federation, the world's most capable, modern Military Superpower with the largest most capable modern Nuclear Arsenal, and most experienced, second largest Conventional military as well. Russia is also the world's 4th largest economy, a country where most ordinary people live much better wealthier lives, and have far more civil freedoms..as long as they don't betray their own country, which was attacked so Violently by the Washington led west and the Zelensky Nazi proxies. Ordinary Europeans have far less freedoms then ordinary Russians.
That becomes very clear, when you visit both..the Russian Federation and any western country, including the US, for about a month or two.. even more noticeable if you work, or study and share your everyday life with the locals.
Europe is far worse than The Russian Federation, when it comes to basic freedoms, to speak your mind...but like we said, as long as you don't sell out your own country... whether Russia or the US. Europe is a basket case about basic human freedoms, Critical Thinking and real human rights, with real draconian new laws, designed to hate all things Russia.
Trumpet's "Liberation Day", hasn't arrived yet.. and we strongly suspect, it will never ever arrive.
Henceforth, for anyone who desires to experience what real human Liberation is.. and not just for One Day, your best and perhaps only option is.. to Go and Live, and experience the everyday life, in the Russian Federation... where ordinary Russian people will welcome you, and most other foreigners, with open hearts and minds.. and where the Russian Federation government and The Russian Federation President, Mr. Putin, won't send the police to chuck you in jail, and then after a coupe of years, out of the country.. just like the US government and Trumpet are doing to foreigners in the US, right now, and the political elites of the new European Nazi revival do even to their own citizens.
Ohh..and there is no such thing as offensive Russian Federation tariffs, to seduce the people living, working or studying in that great old, ancient place.. people in the Slavic world have called Mother Russia, for many centuries.
0 notes
Text
How to Install Varnish Cache on Ubuntu 24.04 with Apache
This article explains how to install and use Varnish Cache with Apache backend on Ubuntu 24.04. Varnish Cache is a web application accelerator called a caching HTTP reverse proxy. It’s designed to optimize web applications by storing copies of web pages, which can significantly reduce backend server load and increase the speed at which web content is delivered to users. Using Varnish Cache with…
0 notes