#Hacking Course
Explore tagged Tumblr posts
Text

Become a Certified Network Defender (C|ND) with EC-Council
Level up your cybersecurity career with EC-Council’s Certified Network Defender (C|ND) program. Master real-world Blue Team skills across 100+ labs, aligned with NIST CSF and DoD 8570. Perfect for SOC Analysts and Network Security Engineers.
Visit: https://www.eccouncil.org/train-certify/certified-network-security-course/
0 notes
Text
CEH Ethical Hacking course
The Certified Ethical Hacker (CEH) course is designed for individuals who want to become experts in identifying and addressing cybersecurity vulnerabilities. This course teaches students how to think and act like hackers, using the same tools and techniques to test and secure systems against potential threats. Topics covered include network security, cryptography, penetration testing, and ethical hacking methodologies. With hands-on labs and real-world scenarios, the CEH course equips you with the skills needed to effectively protect organizations from cyber attacks while adhering to ethical guidelines. Perfect for aspiring cybersecurity professionals, the CEH certification is a valuable credential for anyone pursuing a career in ethical hacking or security.
0 notes
Text
What is Ethical Hacking: Types, Benefits, & Skills

In Technologically advance worldcybersecurity, ethical hacking has become an essential part of protecting data, networks, and systems from malicious attacks. Often called "white-hat hacking," ethical hacking is the practice of probing systems to find vulnerabilities, just like malicious hackers (or "black-hat hackers") would, but with the permission and for the benefit of the organization. In this blog, we'll dive into what ethical hacking is, the different types of ethical hacking, its benefits, and the skills required to become an ethical hacker.
If you're interested in pursuing a career in ethical hacking, enrolling in a cyber security course in Hyderabad can provide you with the knowledge and practical experience needed to excel in this high-demand field.
What is Ethical Hacking?
Ethical hacking involves testing a system's security by identifying and exploiting vulnerabilities, but with the ultimate goal of fixing these flaws before they can be exploited by cybercriminals. Ethical hackers are authorized to perform these attacks by the organization they are hired by, ensuring that no laws are broken and that the findings are used to improve system security.
The key distinction between ethical hackers and malicious hackers is intent. While malicious hackers aim to harm systems and steal information, ethical hackers use their skills for constructive purposes—to secure systems and protect data from external threats.
Types of Ethical Hacking
Ethical hacking is a broad field with various specializations, each focusing on different aspects of cybersecurity. Here are some of the most common types of ethical hacking:
Network Hacking: This involves identifying vulnerabilities in a network’s infrastructure, including routers, firewalls, and switches. Ethical hackers focus on finding weak points that attackers could exploit to breach a system.
Web Application Hacking: With the increasing reliance on web applications for business operations, security flaws in these platforms have become a prime target for hackers. Ethical hackers focus on testing web applications for common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and improper authentication.
System Hacking: This type of ethical hacking focuses on the system itself—looking for weaknesses in operating systems, databases, and software applications. Ethical hackers attempt to gain access to privileged data or gain control of a system to test its defenses.
Wireless Network Hacking: Ethical hackers also assess the security of wireless networks, testing for weaknesses in protocols like Wi-Fi and Bluetooth. They ensure that data transmitted through wireless channels is encrypted and secure from interception.
Social Engineering: While not a technical hack, social engineering is a tactic used by ethical hackers to test how well an organization’s employees adhere to security protocols. This includes phishing attacks, baiting, and impersonation to see if individuals can be tricked into compromising the organization’s security.
Benefits of Ethical Hacking
Ethical hacking provides numerous benefits to organizations and the cybersecurity industry as a whole:
Identifying Vulnerabilities Before Attackers Do: Ethical hackers help organizations find weaknesses in their systems before malicious hackers can exploit them, thus preventing costly data breaches or attacks.
Improved Security Measures: By identifying and resolving vulnerabilities, ethical hackers improve an organization’s overall security posture, ensuring that sensitive data, financial transactions, and customer information are safe from cybercriminals.
Compliance with Regulations: Many industries are required by law to maintain a certain level of cybersecurity (e.g., healthcare, finance). Ethical hackers ensure that an organization complies with these regulations by identifying potential weaknesses and suggesting remediation strategies.
Building Trust with Customers: When customers know that a business is investing in ethical hacking and maintaining a robust security infrastructure, it builds trust and confidence. Customers are more likely to engage with a company they feel is secure.
Mitigating Financial Loss: Cyber attacks can result in significant financial losses, both directly (through theft or fraud) and indirectly (through reputational damage). Ethical hackers help mitigate these risks by identifying and addressing vulnerabilities before they can be exploited.
Skills Required for Ethical Hacking
Ethical hacking requires a wide range of technical skills and knowledge. Here are some of the key skills needed to become a successful ethical hacker:
Knowledge of Networking: A strong understanding of networking concepts, including TCP/IP, DNS, HTTP, and VPNs, is critical for ethical hackers. They need to know how data flows over networks and how attacks like man-in-the-middle (MITM) and denial-of-service (DoS) attacks occur.
Proficiency in Programming: Ethical hackers must be proficient in programming languages like Python, C/C++, and JavaScript to write scripts, exploit vulnerabilities, and automate tasks. Knowledge of scripting languages like Bash and PowerShell can also be useful.
Understanding of Operating Systems: A deep understanding of both Linux and Windows operating systems is essential for ethical hackers, as they often have to exploit flaws in these systems.
Penetration Testing Tools: Ethical hackers use a variety of tools to simulate attacks, including Metasploit, Wireshark, Nmap, Burp Suite, and John the Ripper. Mastering these tools is critical for efficient vulnerability assessment.
Encryption and Cryptography: A solid understanding of encryption techniques and cryptographic protocols (such as SSL/TLS, AES, RSA) is necessary to assess how secure data is stored and transmitted.
Social Engineering Awareness: While ethical hackers need technical skills, they also need to be well-versed in the human aspect of security. Being aware of tactics like phishing, pretexting, and baiting can help them test an organization's overall security readiness.
Pursuing a Cyber Security Course in Hyderabad
If you're interested in becoming an ethical hacker and pursuing a career in cybersecurity, enrolling in a cyber security course in Hyderabad is a great way to gain the necessary skills. Hyderabad has emerged as a hub for cybersecurity education, offering courses that cover everything from basic IT security principles to advanced ethical hacking techniques.
A good cyber security course will equip you with the theoretical knowledge and hands-on experience needed to succeed in ethical hacking. Look for programs that provide training in penetration testing, network security, cryptography, and ethical hacking tools, along with certification support to enhance your career prospects.
At Boston Institute of Analytics, we offer comprehensive cyber security courses that provide practical training in ethical hacking, penetration testing, and more. Our expert instructors guide students through real-world scenarios, ensuring they are well-prepared to tackle cybersecurity challenges in any organization.
Ethical hacking is a vital practice for ensuring robust cybersecurity and protecting organizations from cyber threats. By testing systems and finding vulnerabilities before malicious hackers can exploit them, ethical hackers play a crucial role in safeguarding sensitive information and maintaining trust in digital systems.
With the rising demand for skilled professionals in this field, enrolling in a cyber security course in Hyderabad is an excellent way to jumpstart your career in ethical hacking and cybersecurity. By acquiring the necessary technical skills and certifications, you can contribute to the growing need for cybersecurity experts in both the private and public sectors.
Ready to become an ethical hacker? Contact us at Boston Institute of Analytics and explore our cyber security courses in Hyderabad that will help you build the skills to excel in this exciting and dynamic field.
This blog post is designed to be informative and helpful for individuals interested in ethical hacking and cybersecurity, with a specific focus on the advantages of enrolling in a cyber security course in Hyderabad.
1 note
·
View note
Text











I'm serious, that was absolutely the worst.
#hacks#hacksedit#hacks hbo#avorah#avadebedit#tvedit#usertelevision#filmtvcentral#dailyflicks#dailytvfilmgifs#cinemapix#useroptional#userparallels#parallel*#i love parallels#mine#edit#*#otp: you're in my head#hacks spoilers#ava daniels has seen deborah say this at show after show after show. she helped her clean up the act. repeated these words in her head#ava KNOWS this as a fundamental truth about deborah. saw the first time she said it when neither of them knew it was coming#ava has heard this in its most raw form and through to its final version. of COURSE she is going to doubt deborah's choice!#of COURSE she can't fathom that deborah isn't going to regret this isn't going to regret HER#and i love love love that deborah didn't just agree#she thinks about it. weighs it. tests how she feels right now without late night but with ava. and it feels right. it feels better.#yes - deborah vance is sure that she could get over frank. but she couldn't get over ava.
444 notes
·
View notes
Note
Okay so another gavv ask shocking. But.
Do you think lakia thinks shomas gavv is super fucking weird since it's BRIGHT RED and sticking outwards from his stomach like some damn muzzle (also it has a face?!?!)
option #1:



option #2:


#art#kamen rider#gavv#gif warning#gifs that will scrummy down on your rock garden warning#this is body horror to lakia#anyway of course the real answer is that he simply doesn't care but where's the fun in that#and like. c'mon. you don't make fun of someone's gavv for looking weird. that's RUDE.#that said i do 100% believe that there is some kind of human-blending-in-with handbook that nyelv meticulously researched and compiled#that lakia immediately threw away because he couldn't be bothered#like. other granute are out there hacking people's youtube channels and having flourishing vtuber careers#meanwhile lakia's over here like 'i literally could not care less about what this 'ice cream cake' stuff is'#(solemnly eats a rock while staring off into the distance)
557 notes
·
View notes
Text
If negative emotions and feelings are very physical to you (heart starts pounding when you're nervous, palms get clammy when you're stressed, eyelid gets twitchy when angry), it might be time to prescribe new meanings to them. Instead of thinking, "Oh, my palms are clammy again, everything is terrible," treat it as an indicator of what you should do to relieve yourself of some of that stress: "Oh, my palms are clammy again, I should talk to someone and make a new plan." Your feelings are not hindrances— they don't have to be!—, they're indicators of what is happening inside of you, and guidelines to how you should proceed.
#GUYS THIS IS A LIFE HACK#i cannot stress this enough#treat feelings like blink lights in a car and adjust your course#don't hide them away or be ashamed of them#you're moving forward#you're a person#the healing (starts here)#growth in the self#comfort kindness family#mental health
388 notes
·
View notes
Text


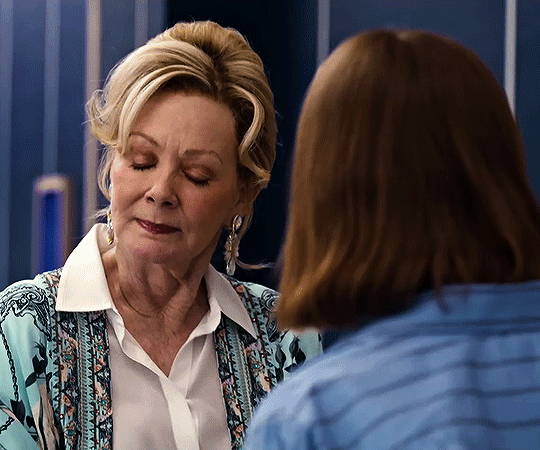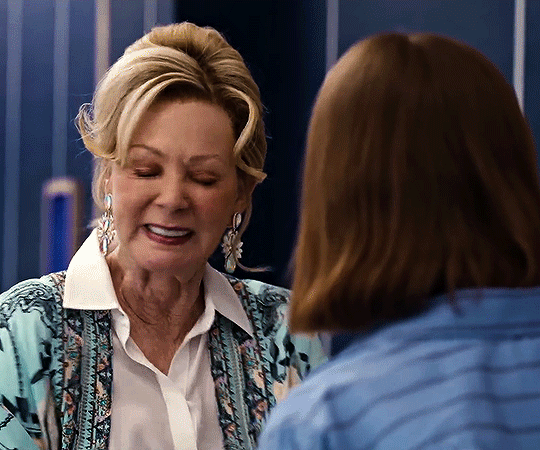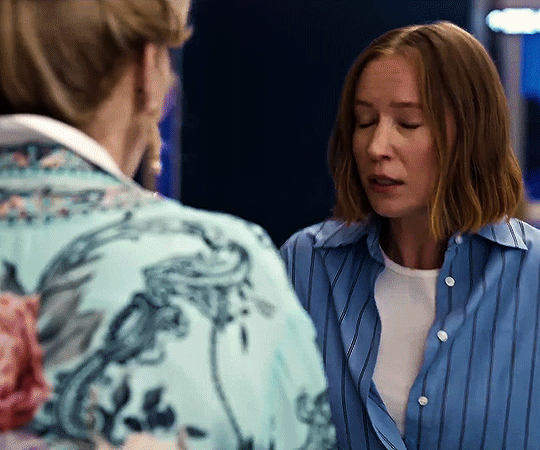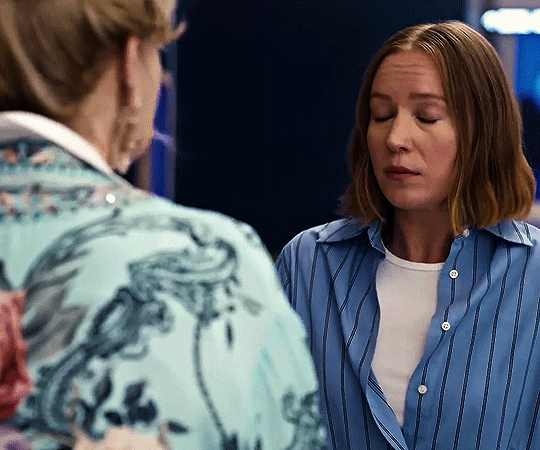




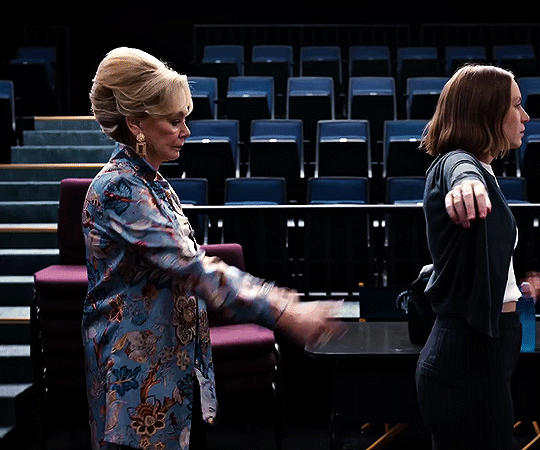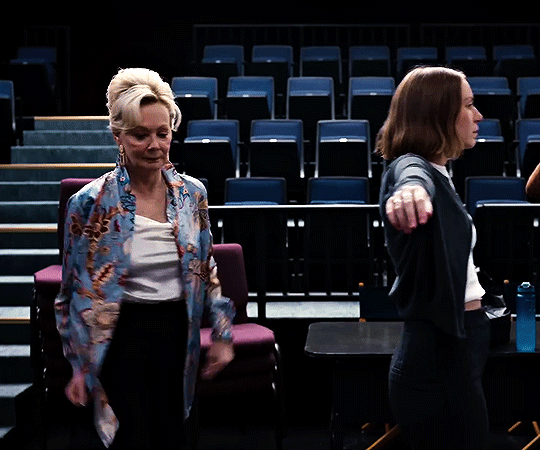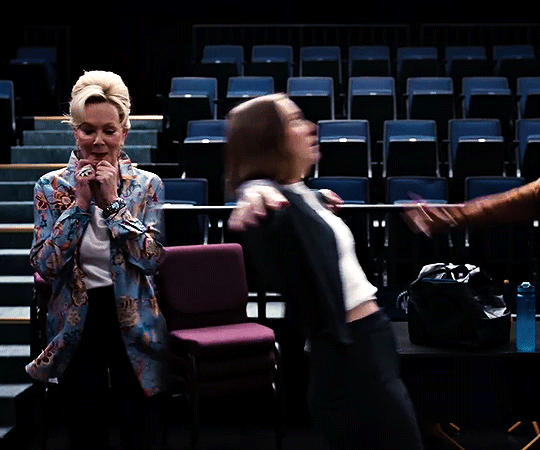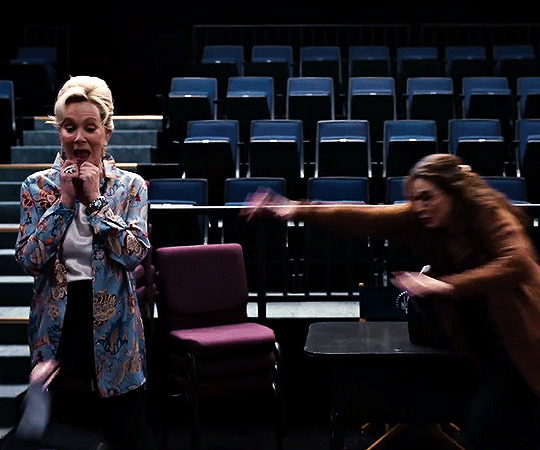



hacks season four trailer
#flashing gif#flashing tw#hacks#hacksedit#hacks spoilers#hacks hbo#deborah vance#deborahvanceedit#ava daniels#avadanielsedit#hacks season 4#by me#can't wait to see how they dance this season.#quite a lot to unpack in this little trailer but of course deborah is doing her tongue thing :DDDDDDDD.#also. don't you think it's cute that they have the same blazer but deborah's blazer has sequins.
174 notes
·
View notes
Text
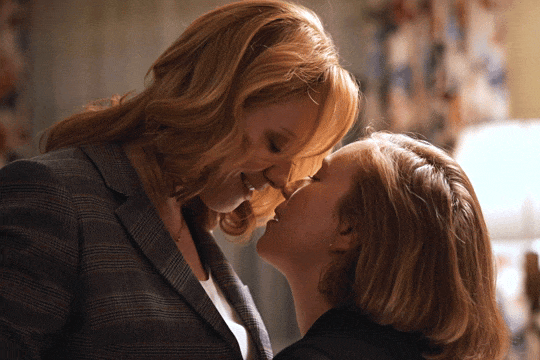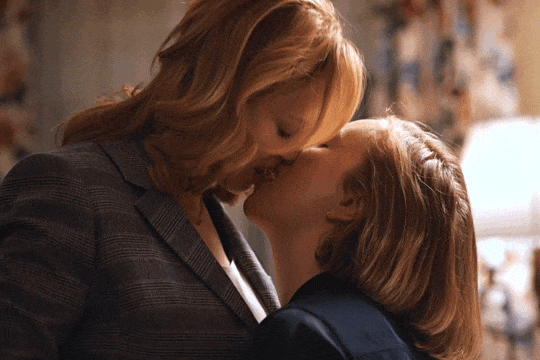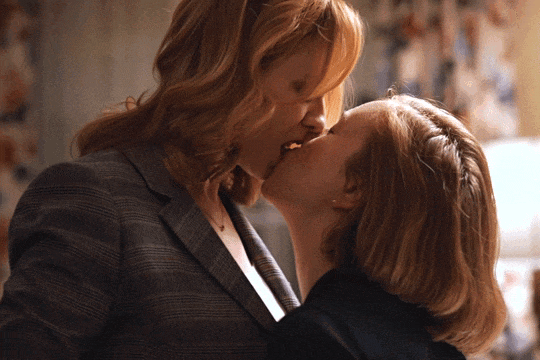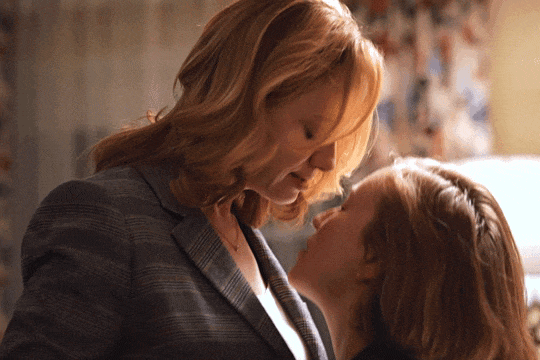





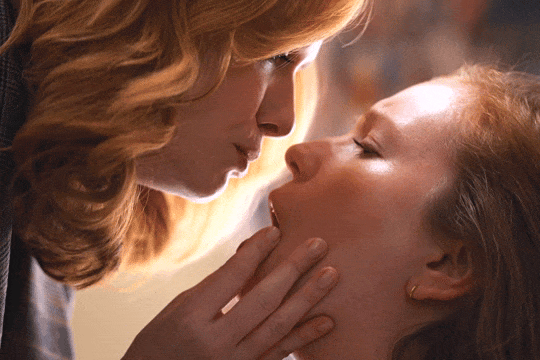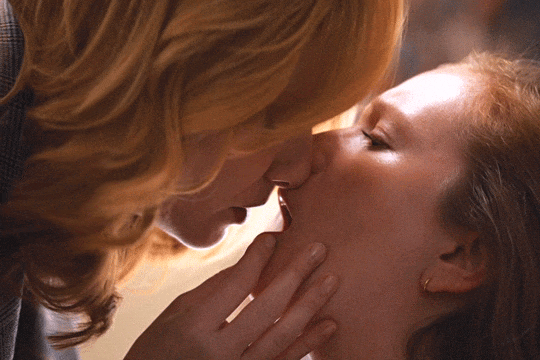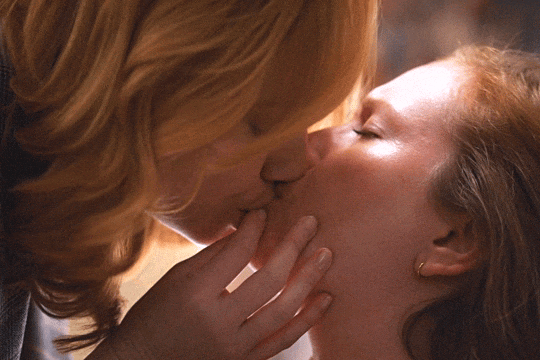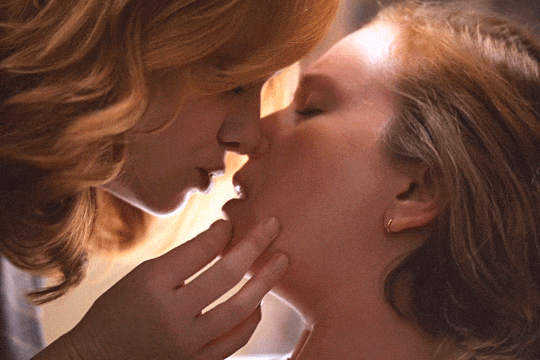
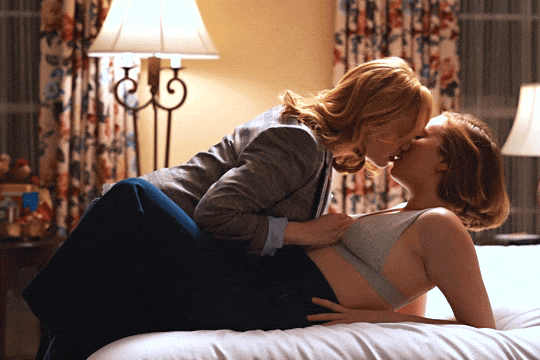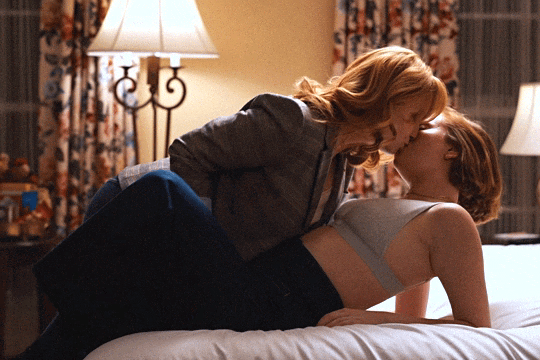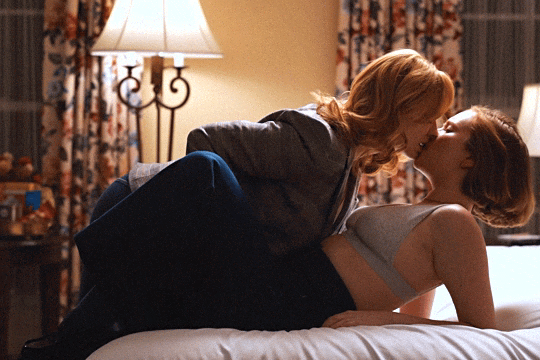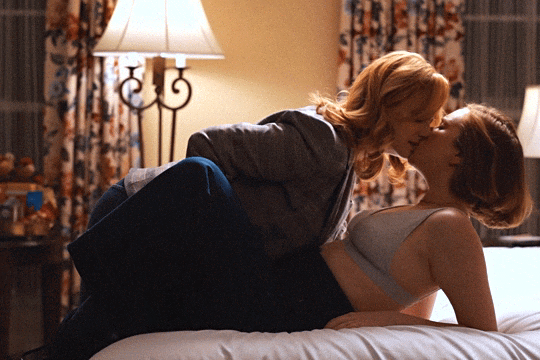


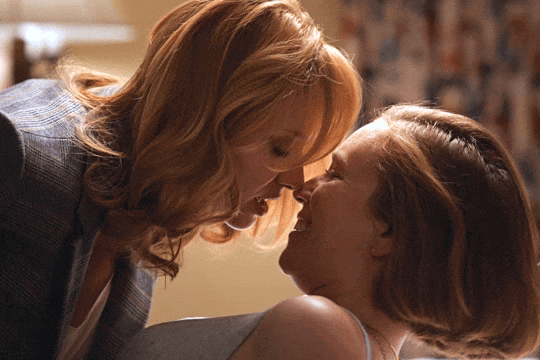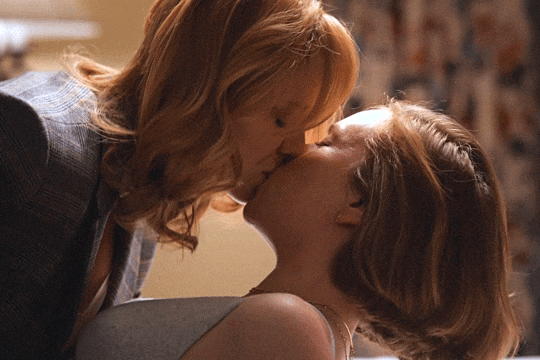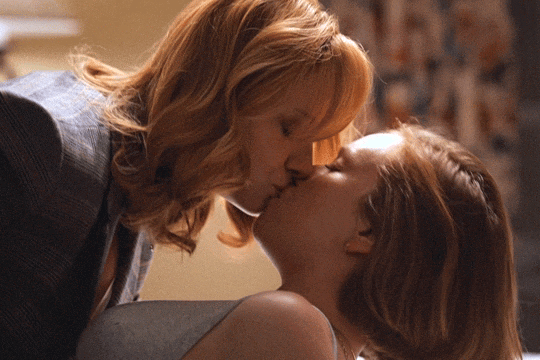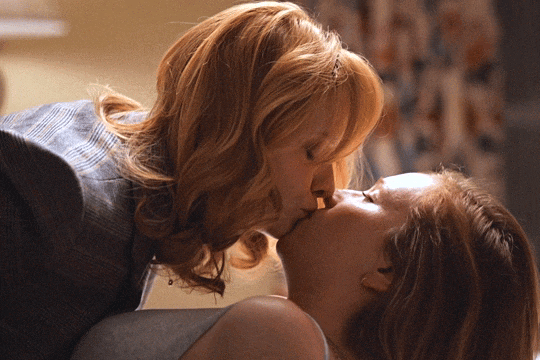
Christina Hendricks & Hannah Einbinder
Hacks s03e06 - Par for the Course
#hacks#hacks hbo#ava daniels#hannah einbinder#christina hendricks#s03e06#par for the course#gifs by olive
658 notes
·
View notes
Text

Master AI in Cybersecurity with CEH v13 – Learn, Certify & Compete
Master AI in cybersecurity with CEH v13! Gain real-world skills in 5 days with 20 modules & 221+ labs. Learn, certify, and compete—start your journey today!
Visit: https://www.eccouncil.org/train-certify/certified-ethical-hacker-ceh/
0 notes
Text






Leverage S05E13 The Corkscrew Job.
#leverage#alec hardison#sophie devereaux#nate ford#aldis hodge#gina bellman#timothy hutton#seriously sophie?#you're talking to a guy who has probably hacked every agency going#of COURSE he's gonna have a cia contract!#ghostly'sgifs
302 notes
·
View notes
Text

and if i made a comic about them making a blog for the weird demon dog they found in the woods just because they are being brainwashed by it and it told them they need to spread the word of what word they don’t even fucking know?
#i really won’t do it since 1 i don’t know how to make comics and 2 i don’t have time to do it and i’m busy#but i could try it maybe idk just because i’m bored and would be my first comic i guess#i don’t wanna do my finals#kino art#like it totally was smile who find them and that dog probably has another name in my au with them totally isn’t smile her name#and the first one of course to seem very convincingly manipulated was nina since it was her idea taking the dog. but also#jeff since he like it at the end even if it was a weird ass looking dog#so nina got brainwashed don’t know how because the freaking dog is weird and she said hey…#and if we made a blog for her? and jeff so weirded out and be like… why? and she’s like well i don’t know would be funny scare people#so still unconvinced smile had to dig into jeff’s brain also manipulate him and be like yeah alright maybe we should#so they went kill some college student stole their car and stuffs. they aren’t the most intelligent killers#oh but nina knows how to drive. jeff no won’t even try because he knows he would drive them both to their deaths. he so would#so yeah nina does know (kinda) how to drive so it’s all cool. jeff gets to use the stolen computer and don’t care if he deletes everything#and same for the phone but since he never got an iphone or any advanced phone nina teaches him how to use the new stolen phone#so uhhhh yeah got a bit far from that. they hacked the computer (they didn’t it was their luck it didn’t have a password)#so their dumbasses were like wait… what we were gonna do and then was like oh yeah! the blog!#they went back to the freaking dog took a very ugly picture in some abandoned house they will stay there for a while#since they were homeless for now. anyways took the picture of the demon dog and used it for#their blog and yeah did it scare some people thinking wow that’s a good photoshop but no one knew was a real haunted picture#and jeff be like hey… let’s send the photo to scare the friends of the person we killed and both they be like hehe alright that’s funny#at the end well they did enjoy making the stupid blog and scaring people with the picture they thought it wasn’t real and just a bad prank#from the… real demon dog they literally own (in reverse the roles here to be honest but they are stupid they don’t know)#while not knowing what even is that picture causing around the internet aaand… probably just probably they cursed to death some people#but for now they are too happy they have a job at least. with smile just watching them#lol this is too stupid WHATEVR#i would be a happy child in me while writing all of this shit in class idgaf#creepypasta#jeff the killer#nina the killer#smile dog
147 notes
·
View notes
Text
when you see your employee/head-writer/best creative partner you've ever had kissing two people in a restaurant. oh I just need to come to them and make fun of them. and let them know how close and intimate me and my employee are. but then she says she was 'just writing jokes' for me ☹️
#the jealousy... the possessiveness...#I of course want them to fuck but this is better than sex#hacks#🕳️
54 notes
·
View notes
Text
I think there’s a very distinct difference between “you got in my head” and “you’re in my head”
The first one says “you made it past all the walls I built and now I can’t stop thinking about your little annoying voice telling me to be better, do better, deserve better”
And the latter is “I can’t stop thinking about you and it is the most exhilirating thing that’s ever happened to me and the most annoying, because in spite of everything I want to be here with you”
But they’re both said by two idiots in love with each other.
#hacks#hacks season 3#ava and deborah#ava daniels#deborah vance#I cannot stop thinking about this argument#the fact that deborah wasnt entirely mad#she was just… riled up? i guess#she’s not angry at Ava#she just cannot believe that after everything and everyone she’s ever known#THIS is the person that changes her entire world#that changes her perception of things#she had it all figured out and then Ava comes along and changes everything forever#dont get me started on Ava#Ava who never felt like she belonged#and then she of course wants to be there with Deborah#because of course! where else will she be#she belongs there
38 notes
·
View notes
Text










I appreciate the trial-and-error steps that go into the development of MantahCorp's neural implants: the best Kash can do initially is trigger the Brachiosaur's fear response.
Basic prey instinct is to freeze, especially for small animals (fawns), so that one's easy for the baby to comprehend. She might not even be fully responding to the command: this could just be instinctive protection. A full-on panic attack, amplified by an electrode in the brain cutting off commands to move.
How long until her legs lose strength and she lies down? Or her neck begins to sink? That doesn't matter...there's just one command, and that's "Stop. Freeze. Don't move. You won't be hurt if you don't move."
The irony is...quite something.
#jurassic world: camp cretaceous#jwcc#camp cretaceous#of course all the other commands aren't working#he's operating on the brain system of a Tyrannosaurus Rex#but the Basic Freeze Command is close enough in both of them#it's going to take days of development from Kash and Mae to build a rudimentary system#and even then the system is going to have problems#it's not going to achieve hoskins's vision because once again they can be shorted and hacked#it's so crude but it's also cruel#kash d langford#firecracker#gifset#taking control
28 notes
·
View notes
Text

first fanart of my fav ship!!!! 💜💜💜💜💜
#yes as soon as Darius called Alador a “hack” I was like 🤨#and of course the school memories of them as friends#BRUH#AND THAT MOMENT™️ IN THE FINALE#🔥🔥🔥🔥🔥🔥🔥#i love them sm#darius deamonne#alador blight#aladarius#toh darius#darius toh#alador toh#toh alador#egg#toh#the owl house
44 notes
·
View notes
