#How to Keep Your Servers and Networks Secure
Explore tagged Tumblr posts
Text
#How to Keep Your Servers and Networks Secure#server network#Server and network management#Server and network management solution#Server and network management services
0 notes
Text
I'm tinkering again with the idea of the Tracies making the life of Counterterrorism/Special Ops difficult. This bit is probably more pertinent to UNREQUITED. Tempers fly. More context could be found, but is not strictly necessary, in PERSON OF INTEREST TOO and COUP DE GRÂCE. All the thanks to @janetm74 for bearing with me.
DA 18*
"So, given the circumstances, I have to INSIST on protective custody."
*baffled murmur all around*
"With the GDF?! What do you mean?!"
"I mean, MISTER Tracy, that you need to close operations and sit tight, till we catch him."
"ABSOLUTELY NOT!"
"Scott, wait! If the threat is legit..."
"I just spent half an hour briefing you how legit it is, Ms. Kyrano!"
"If the threat is legit we can invoke the lock down of the Tracy Island and take it from there."
"I'm afraid, none of the Tracy properties hold up to my team's security standards."
"EXCUSE ME!"
*indignant murmur all around*
"Well, let's see - your secure venues and systems have been breached and overtaken on multiple occasions by an international crime ring leader Belah Gaat, his know accomplice, wanted for acts of terrorism, the Mechanic, and a Cognitive Transformer Model, aka Eos, which, in turn, had been compromised on at least two recorded occasions. Not exactly a stellar track record of security protocols."
"How do you know about Eos?!"
"Dr. Simpson?"
"The neural network, incorporating elements of an open source code Dr. Tracy left behind on Harvard servers a while ago, has been trained on curated datasets, before escaping containment. The model has been accessing data and training in unsupervised conditions ever since. Last known hosting - Thunderbird Five server."
"Thank you! But I'm still more worried about breaches in perimeter on the Island and Grand Roca ranch."
*blue glare* *jade glare*
"You DO NOT suggest there's a mole in the IR!!!"
"Now, now! I'm sure Captain here makes no such allegations."
"No, Colonel Casey. I'd still rather be safe than sorry."
"Do you stipulate my security protocols are insufficient?"
"Let's see... No extra recon, Ms. Kyrano: how many assault points are in this room?"
"Door, windows, ventilation, possibly the holo drive or carry on devices."
"Very good. But not good enough."
*blue glare* *jade glare*
"Of those present, at least Colonel Casey and myself are carrying firearms."
*gasps*
"Everyone in this room has been extensively vetted!"
"You see, Ms. Kyrano, the problem is you keep thinking like a bodyguard. To protect Mister Tracy, you need to start thinking like an assassin."
"I'm sitting right here!"
"No. You're not. I just shot you point blank."
*toppled chair clanking* *glare off*
"This is ridiculous! I will NOT shut down IR and cower just because there's possibly a psycho from Bereznik on the loose!"
*blue glare down*
"Caramba, Scott! Stop being so obtuse AGAIN and LISTEN! He doesn't want your money, he doesn't want your tech, he doesn't give a damn about your Thunderbirds, he doesn't want to make a statement about your father's legacy! He wants you to suffer and he wants you GONE! And he will get to you, by any means necessary. By ANY means! Do you think he'd care how many brothers he'd have to eliminate first?!"
*glare around*
*heavy breathing*
*hard swallow*
"What do you suggest?"
"Obrigada mãe Maria! For starters, let's get going! Right now I'm the only person I trust with your life."
*jade glare*
"Well, I DON'T!"
"Good, Ms. Kyrano! Now you're really learning something."
----
* highest level of Danger Assessment
#methinks i have astronomy#thunderbirds are go#i don't do oc's#scott tracy#kayo kyrano#colonel casey needs a drink#my fic#thunderbirds 2015
14 notes
·
View notes
Text
It starts with him
What was once a promise of technology to allow us to automate and analyze the environments in our physical spaces is now a heap of broken ideas and broken products. Technology products have been deployed en masse, our personal data collected and sold without our consent, and then abandoned as soon as companies strip mined all the profit they thought they could wring out. And why not? They already have our money.
The Philips Hue, poster child of the smart home, used to work entirely on your local network. After all, do you really need to connect to the Internet to control the lights in your own house? Well you do now!Philips has announced it will require cloud accounts for all users—including users who had already purchased the hardware thinking they wouldn’t need an account (and the inevitable security breaches that come with it) to use their lights.
Will you really trust any promises from a company that unilaterally forces a change like this on you? Does the user actually benefit from any of this?
Matter in its current version … doesn’t really help resolve the key issue of the smart home, namely that most companies view smart homes as a way to sell more individual devices and generate recurring revenue.
It keeps happening. Stuff you bought isn’t yours because the company you bought it from can take away features and force you to do things you don’t want or need to do—ultimately because they want to make more money off of you. It’s frustrating, it’s exhausting, and it’s discouraging.
And it has stopped IoT for the rest of us in its tracks. Industrial IoT is doing great—data collection is the point for the customer. But the consumer electronics business model does not mesh with the expected lifespan of home products, and so enshittification began as soon as those first warranties ran out.
How can we reset the expectations we have of connected devices, so that they are again worthy of our trust and money? Before we can bring the promise back, we must deweaponize the technology.
Guidelines for the hardware producer
What we can do as engineers and business owners is make sure the stuff we’re building can’t be wielded as a lever against our own customers, and to show consumers how things could be. These are things we want consumers to expect and demand of manufacturers.
Control
Think local
Decouple
Open interfaces
Be a good citizen
1) Control over firmware updates.
You scream, “What about security updates!” But a company taking away a feature you use or requiring personal data for no reason is arguably a security flaw.
We were once outraged when intangible software products went from something that remained unchanging on your computer, to a cloud service, with all the ephemerality that term promises. Now they’re coming for our tangible possessions.
No one should be able to do this with hardware that you own. Breaking functionality is entirely what security updates are supposed to prevent! A better checklist for firmware updates:
Allow users to control when and what updates they want to apply.
Be thorough and clear as to what the update does and provide the ability to downgrade if needed.
Separate security updates from feature additions or changes.
Never force an update unless you are sure you want to accept (financial) responsibility for whatever you inadvertently break.
Consider that you are sending software updates to other people’s hardware. Ask them for permission (which includes respecting “no”) before touching their stuff!
2) Do less on the Internet.
A large part of the security issues with IoT products stem from the Internet connectivity itself. Any server in the cloud has an attack surface, and now that means your physical devices do.
The solution here is “do less”. All functionality should be local-only unless it has a really good reason to use the Internet. Remotely controlling your lights while in your own house does not require the cloud and certainly does not require an account with your personal information attached to it. Limit the use of the cloud to only the functions that cannot work without it.
As a bonus, less networked functionality means fewer maintenance costs for you.
3) Decouple products and services.
It’s fine to need a cloud service. But making a product that requires a specific cloud service is a guarantee that it can be enshittified at any point later on, with no alternative for the user owner.
Design products to be able to interact with other servers. You have sold someone hardware and now they own it, not you. They have a right to keep using it even if you shut down or break your servers. Allow them the ability to point their devices to another service. If you want them to use your service, make it worthwhile enough for them to choose you.
Finally, if your product has a heavy reliance on the cloud to work, consider enabling your users to self-host their own cloud tooling if they so desire. A lot of people are perfectly capable of doing this on their own and can help others do the same.
4) Use open and standard protocols and interfaces.
Most networked devices have no reason to use proprietary protocols, interfaces, and data formats. There are open standards with communities and software available for almost anything you could want to do. Re-inventing the wheel just wastes resources and makes it harder for users to keep using their stuff after you’re long gone. We did this with Twine, creating an encrypted protocol that minimized chatter, because we needed to squeeze battery life out of WiFi back when there weren’t good options.
If you do have a need for a proprietary protocol (and there are valid reasons to do so):
Document it.
If possible, have a fallback option that uses an open standard.
Provide tooling and software to interact with your custom protocols, at the very least enough for open source developers to be able to work with it. This goes for physical interfaces as much as it does for cloud protocols.
If the interface requires a custom-made, expensive, and/or hard-to-find tool to use, then consider using something else that is commonly available and off the shelf instead.
5) Be a good citizen.
Breaking paid-for functionality on other people’s stuff is inherently unethical. Consider not doing this! Enshittification is not a technical problem, it is a behavioral one. Offer better products that are designed to resist enshittification, and resist it yourself in everything you do.
Nothing forced Philips to do what they are doing: a human made a decision to do it. They could have just as easily chosen not to. With Twine’s server lock-in, at least we chose to keep it running, for 12 years now. Consider that you can still make a decent living by being honest and ethical towards the people who are, by purchasing your products, paying for your lifestyle.
We didn’t get here by accident. Humans made choices that brought us to this point, and we can’t blame anyone for being turned off by it. But we can choose to do better. We can design better stuff. And we can choose not to mess things up after the fact.
We’re putting this into practice with Pickup. (We also think that part of an IoT reset is giving users the creative freedom of a general-purpose device.) If you’re looking for something better and our product can fill a need you have, consider backing us. We cannot claim to be perfect or have all of the answers, but we are absolutely going to try. The status quo sucks. Let’s do something about it.
Published October 15, 2023 By Jeremy Billheimer
137 notes
·
View notes
Text
Update on the Fur Affinity hack!
For those who don't know, Fur Affinity is a furry site that hosts furry art, writing, photos, etc. It's an important and unique community beloved by its userbase. The person who founded and ran the site, Dragoneer, passed away 8/6/24. His friends and family are working together, with the support of the community, to keep the site up and running. They have a gofundme campaign to cover site expenses and the debt of his estate to keep the site from getting sold off as an asset. So far, it is looking bright. Unfortunately, this week, bad actors hijacked the site. They didn't break into the private info, but redirected traffic and communications to other places, including Kiwifarms (alt right site) who promptly released a statement that they weren't involved, and the hijack was at the expense of both websites. Fortunately for everyone, it's been resolved, and the site is safe to use again.
Here's the statement from their discord:
"Good Afternoon!
Yesterday, after meeting for several hours with Network Solutions (our domain registrar), they finally agreed to our demands to lock our account and revert changes made to our domain name’s NAMESERVER configuration. This lock also prevents anyone from signing in and making further changes. A fraud investigation has been launched on their part, and upon conclusion, our account will be fully released to us and we will receive more information on how this hijacking occurred. Our domain is directing traffic correctly.
While the bad actor was in control of our domain between Tuesday, August 20th at 12:47AM ET and Wednesday, August 21st at 2:28PM ET, they redirected our traffic to other websites and they set up an email server to receive any emails that were sent to any of our @furaffinity.net accounts. If you sent any emails to our @furaffinity.net accounts during that time, then the bad actor has those emails, we did not receive them, and you should act appropriately to secure and protect your information. Furthermore, any emails sent from @furaffinity.net during that time would have been sent by the bad actor and should not be trusted. The bad actor never had access to our actual email accounts, any previous emails, nor data we have previously received.
It is important to stress that the Fur Affinity web server itself was never compromised, and the bad actor never had access to any private information therein such as our user and server data (It's as if someone stole your home address and had your mail and visitors routed somewhere else. Your house and everything inside is fine, only the address and incoming/outgoing mail were affected). **As a precautionary measure during the incident, we invalidated all current login sessions and you will need to log back into your account.**
**✨🌟🎉 FUR AFFINITY IS NOW ONLINE AND MAY BE ACCESSED SAFELY! 🎉🌟✨**
Furthermore, as of last night (August 21st at 9:53PM ET), we have regained access to our Twitter account, and with the help of Whanos (@KernelJunkie), reclaimed our username (@FurAffinity). And as of this morning (August 22nd at 10:45AM ET), we also secured Dragoneer's personal Twitter account.
We have also been made aware of various sources claiming to have identified the bad actor responsible for this attack. We have no way to verify that these accusations are accurate, but will continue to share all information with the FBI. With that said, we want to remind everyone that we have a zero-tolerance policy toward harassment, no matter the circumstances. Recently, there have been instances where speculation has led to individuals being harassed, even if they have no proven connection to the incident.
It is important to note that Fur Affinity, with direct insight into the situation, has not conducted its own investigation. We are leaving that responsibility to law enforcement. Speculation only spreads misinformation and causes harm, so please be cautious about what you share or believe online.
We kindly urge everyone to avoid engaging in further speculation or harassment. It is the role of law enforcement to determine the facts and make decisions, not ours.
Finally, we want to extend our deepest gratitude to all of you for your unwavering support during this incredibly difficult time. Your kindness, patience, and understanding have meant the world to us as we've navigated these challenges together. We are committed to continuing to foster a creative and welcoming environment for all, and it is your strength and solidarity that make our community truly special. Thank you for standing with us.
Please note FA might suffer from the "hug of death" - basically, everyone interacting with it at once causes it to run slowly. (: It's not broken, just overwhelmed by your support!! "
In my opinion, the people who are running the site at this time are doing a good job with a really terrible situation.
We love and protect tumblr, as a special and queer community that is unique in it's function. Fur Affinity is important in the same way. It is a safe space for both nsfw and sfw queer expression, and that's something important to protect. ♥️
31 notes
·
View notes
Text
confidence boost | choi san

pairing :: choi san x male reader rating :: 18+ ; sexual content genres/au's :: smut content warnings :: dom!top!reader x sub!bottom!san, heavy cursing, name calling, slut shaming, degradation, body worship, breeding, rough sex, kitchen sex (on the table), marking, choking, spanking, bulging kink, thigh fetish, possessiveness on san's part, slapping cus reader is extra, extra kinky word count :: 1,286 a/n i genuinely just have no idea how the security system works for backstage passes so bear with me :| requested by anon [ask] network tag@preciousillusions-net pt.1 ; pt.2

"l/n m/n?" the security guard asked. you nodded, giving him your id when he asked for it. he looked it over, passed it back to you, and knocked lightly on the door before opening it a crack to let san know you had arrived.
your heart started screaming in your chest the moment you heard san's voice calling you to come in, and the security guard gestured you inside before shutting & locking the door behind you. you spent nearly all your willpower to keep your face from turning impossibly cherry-red as you sat down on the couch per san's silent gesture.
awkward silence...
lots of very tense, awkward silence.
"so... three hours, huh?" san said, breaking the silence after a while.
"heh- yeah..." you giggled sheepishly, scratching the back of your neck awkwardly.
"i get you all to myself for a whole three hours..." he said in a quiet, almost worryingly chipper voice.
"i… y-yeah," you stuttered, turning away.
"c'mere, come play a dinosaur game with me." san said with a happy smile, patting the couch cushion to his left and waving his phone in the air.
"s-sure," you said, pulling out your phone and opening ark- assuming that was the game he was referring to. (a/n: indeed it was. ark is the only game i know a lot about so its ark. author's rules, shut up.)
the offer did make you blush, yes, but it was more so the words that came out of his mouth next that shook you to your core. the words that started the nagging in the back of your mind; that little voice that insisted that something was off.
you gave san your username and he invited you to a private server he'd created, and you and him played the game for about thirty minutes, the silence between you and the man of your dreams finally beginning to feel comfortable. until san rent it in two and left the pieces to rot between you and him.
"y'know, you're awfully quiet and shy for someone walking around giving off such a loudly pronounced aura."
you had nothing to say to this, so you shifted in your seat a bit and tried to continue playing the game, trying your best to ignore the fact that san was quite obviously a) hitting on you, and b) scooting closer and closer to you.
"oh come on, i know you have an answer to that." he sniped playfully, putting his phone down and shoving your shoulder gently with the strength of his.
"san, everything i have in mind to say in response to that would get me blacklisted from everything ateez ever does for the rest of my gay, miserable existence." you said back sassily before continuing your game once more.
"oh you like men, do you?" san teased, "am i your type?"
you stayed silent.
san leaned in and sent a shiver down your spine as you felt his breath on your neck.
"'cus you're definitely mine."
this is when you lost your last ounce of self control.
"god fucking damn it all, choi san, you and your fucking rizz." you spat, throwing your phone aside onto the floor- it was an iphone, and the case was pretty durable… right?
tossing aside every drop of dignity you had, you turned, looked san right in the eyes for a fraction of a second, and the pounced. your hands made identical beelines for san's chiseled face and your lips connected with his in what could very well have been a car crash, your tongue forcing its way into his mouth and your hands tangling into his soft black hair. you ate up the needy groan that ripped through his throat, tangling your tongue with his and feeding him a growl of your own as his hands went up under your shirt and began to roam your back and shoulders. a small whimper escaped your lips when he raked his nails down your shoulders and upper back without warning; he smirked smugly into the kiss and gestured impatiently for you to be rid of your shirt.
he wanted to see your body.
san yanked softly on your hair and leaned down to whisper in your ear.
"y'know, i could really use a bit of a confidence boost, little prince..."
you giggled into san's ear, gladly indulging in the things he was asking for.
"oh san, the things i could say... where do i start?" you hummed, "mmm... your jawline, first off. you could literally cut me with this bitch and i would pay to have it done again."
san chuckled, nuzzling into your neck and biting down on the skin there.
"keep talking and you might get something out of it, pretty boy." he purred into your ear, starting to leave bruises all over your neck.
you giggled again, leaving a bite mark of your own on san's throat before continuing your speech.
"and you're literally shaped like a fucking dorito," you snapped in a loud voice, "and for what? for what, san?? are you trying to become aphrodite?? 'cus it's working like a fucking charm..."
san's pride had already been flying through the roof (probably for no reason at all, honestly), but hearing you talk about him the way you just did honestly had him twitching in his pants. he put his hand over your mouth to shush you, immediately replacing it with his mouth and shoving his tongue into yours. he wrapped his arms tighter around your waist, leaving brand new, stinging, scorching hot scratch marks down your back and shoulders, and his eyes rolled back into his head when you growled hungrily into his mouth.
"f-fuck, san..." you whimpered, wrapping your legs around his waist.
san broke away from the kiss, rolling over into the back of the couch and nuzzling into your neck again.
"well," he said smugly, "i've got the confidence boost i wanted... but now you've given me another problem to deal with."
your eyebrows nearly disappeared into your hair.
"san..."
"yes, darling?"
"are... are you asking me to suck your dick?"
silence.
"yes." san decided after a couple moments. "yes i am."
"gimme."
that was the only answer san needed.
~~~
"fuck..." san whimpered, "fuck, right there, YES, FUCK--"
"yeah?" you cooed, slapping san's face softly and listening happily to his high-pitched whining as you continued dicking him down into oblivion. "you like that, bitch? you're such a nasty slut, you like this, don't you? you like being slapped around..."
"y-yes sir," san whimpered, "f-fuck, it feels so good- fuck, right there, please-"
"such a pretty little fucking slut..." you growled, wrapping your hand around his throat and squeezing as hard as you could.
"m-m/n, fuck, right there, yeah-"
"what was that, bitch? what'd you say?"
"fuck, sir, right there..." san corrected himself in a high-pitched voice, as quickly as he could through the fog that was taking over his brain.
"good boy, that's better." you purred, laying down on top of him and speeding up your ministrations as fast and hard as you could without hurting yourself. san made a sound that was somewhere between a moan and a high-pitched whine as the tip of your dick hit his already-abused prostate.
"fuck, fuck, FUCK, sir, right there, shit- breed meee," san groaned, burying his face in your shoulder and let the feelings of you fucking your load into him hit him like a subway train. he groaned into your neck and bit down as hard as he could, screaming into your neck as his orgasm took him and flew away into the clouds with him.
"you're such a pretty boy," you praised, "you took my dick so well..."

© seonghwas-lighter 2023-2024.
#chaece.exe 🌑#fever.dreams 🌑#cacaokpop#preciousillusionsnet#ateez#san#choi san#ateez smut#san x male reader#ateez x male reader#ateez x male reader smut#choi san x male reader#choi san smut#male idol x male reader#sub!idol#sub!ateez
207 notes
·
View notes
Note
Hello!
Checking out your blog, I noticed that you use C++ and seem quite knowledgeable on it, so I wanted to ask for your help (if it doesn't bother you!).
I've completed the two C++ courses in SoloLearn (which are quite superficial, but serve as good introductions, I believe), and I'm currently reading "The C++ Programming Language", by Bjarne Stroustrup. My issue is that I'm a bit afraid of not really understanding anything and/or being unable to write any functional code by myself. Therefore, I wanted to ask if you had any resources and/or tips that could be helpful for a beginner like me (the only language I've ever used before is HTML, and so I thought it was a good idea to go straight to C++ for the challenge of it xd).
It NEVER bothers me to blabber about code! :D
I LOVE C++
So first a long rant, and then my answer :3
C++ will probably forever be my favorite langauge.
But many do not like it, and it is actually somewhat rare to see as a language a professional uses.
Why? Because one should use a language for what it is good at.
And what is C++ good at?
Well, one of its neatest features is that it is a object oriented language.
It is also a language where you can create objects, but the language ITSELF is object oriented.
C++ is a derived class of the baseclass C
And it have the same philosophy as C
You can do ANYTHING!
You can EASILY write garanteed memory safe code in C++
You can write psydocode that have the same safety garantees as Rust.
Or you can go for 100% performsnce, dancing with void pointers and GOTOs!
Craft a class so it gets build, moved, removed used and works EXACTLY how you want it to! Down to the smallest details!
Write halfway object oriented and half functional!
If it can be done on a computer, it can be done in C++!
It may not be the language most often used. Often there are better languages for creating things
But knowing C++ means that you never again have to fully learn another language.
A C++ programmer KNOWS what a computer can do, so it is just a question of googeling the syntax for whatever language we are writing it in that day :D
Rant over. Answer time! :D
When I have to get a bit familiar with a new language I usually build a HTTP server :3
It is easy enough to look up for help, it means you work with everything you know
Slap it on a raspberry pie 0 or 3 depending on your wallet and bam! You have your own fileserver! :D
Connect a SSD into the raspberry pie 3 and bam, you now have your own cloud storage! :D
That is ALWAYS a useful thing :3
Keep it on your own network with a passwork and use MDNS to use it and it is 100% safe.
Because you piggybag on all the security wirless networks come with these days :3
8 notes
·
View notes
Text
What is the difference between network support and IT support?
Network Support Services

When managing technology in a business, terms such as Network Support and IT support often arise. While they may sound similar, they cover different areas of technology services. Understanding the difference can help businesses select the most suitable support for their specific needs.
What Is IT Support?
IT support refers to general technical assistance that helps users and businesses maintain their computer systems and networks. As this includes and consists of setting up hardware and software resources, troubleshooting errors, installing applications, managing user accounts, and fixing computer-related issues. IT support is often the first line of help when there’s a problem with your PC, email, or printer.
In short, IT support focuses on helping users interact with technology smoothly on the front end—solving problems that affect individual devices and users.
What Is Network Support?
Network assistance, on the other hand or side, is more focused on maintaining and managing the backend infrastructure that connects all devices in a business with its observations. As this includes routers, switches, firewalls, servers and wireless access points in it. Network assistance assures that the entire system runs securely, efficiently, and without interruptions.
Everyday network support tasks include and consists of activities:
Monitoring the network performance and observations.
Preventing and responding towards the security threats and potential checks.
Managing the IP addresses and server uptime with its implementation into the system.
Ensuring smooth internal and external communication.
Troubleshooting internet connectivity and network failures.
In essence, Network assistance maintains the foundation of your digital environment and existing settings, keeping it strong and reliable for better outcomes and deliverables. Without a properly managed network, IT devices and software may fail to function correctly and may result in significant concerns.
How Do They Work Together?
Both IT support and Network Support are essential and a must for a complete tech ecosystem and acceptable outcomes. While IT supports and aids the individual users and their machines with its expertise, meanwhile network support keeps the systems update behind the scenes running smoothly. Together, they ensure that businesses can operate efficiently without technical disruptions. Many businesses rely upon and prefer to stay updated with trusted technology service providers, such as Suma Soft, IBM, and Cyntexa, which offer both IT and Network assistance and support tailored to meet the specific needs of modern organizations as per the business demand and objective concern. Selecting the optimal blend of both assures long-term performance, stability, and sustainable growth with its adaptation.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
2 notes
·
View notes
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
Tagged by @spybrarian! Thaaaank you!
1. How many works do you have on Ao3?
I have 26
2. What’s your total Ao3 word count?
338,736
3. What fandoms do you write for?
I used to write Clexa, but now I just write Tanthamore
4. What are your top five fics by kudos?
Network Connectivity Issues (ahead by a lot)
A story I'm deeply in love with writing, due to its closeness to my heart and because of the novel way it's written-- which is live on a discord server whenever the mood strikes. Fanfic is typically serialized work, but this feels like...even closer to that immediacy, and it can be quite electric.
The Pieces
A collaborative collection of one shots in the Kinkverse universe (talked about below)
The Bite
Canon compliant fic about longing and how it can come out in your teeth.
The Stones
Essentially a sick fic with some fun world building
The Test
Long distance edging and denial. The fantasies were some of my favorite things to write.
5. Do you respond to comments?
I try to! Sometimes it takes me awhile!
6. What is the fic you wrote with the angstiest ending?
Out of finished fics I suppose it would be The Beloved Prey, though I do have a handful of things I've written to continue that.
Unfinished it would be the unpublished sequel to My Own Echo.
7. What’s the fic you wrote with the happiest ending?
I think maybe The Stones. Magic holding and accepting Jade because of Kit's love for her feels pretty happy.
Oh! And Network Connection Secure. The Cam girls having a proposal moment that's distinctly them? Very sweet and I wrote it for Christmas.
8. Do you get hate on fics?
Not on these ones!
9. Do you write smut? If so, what kind?
Yes, yes I do. The majority of my work contains it. I think the weirdest I've written (so far) is probably Spare the Rod.
10. Do you write crossovers? What’s the craziest one you’ve written?
I'm not really big on crossovers, so this isn't something I've done. I'll go hard on an AU though.
11. Have you ever had a fic stolen?
Nah.
12. Have you ever had a fic translated?
Nope! Translation is an art in itself-- I think I'd find the idea of someone doing that a little daunting?
13. Have you ever co-written a fic before?
Kinda! @swashbucklery, @spybrarian, @commanderbuffy and I have all written pieces in what we call the Kinkverse. It was a brain child of mine that started with The Lesson, but has since become a collaborative writing world. It's been one of the most lovely experiences of my creative life. J has also written some supplemental material for NCI that I adore. @barmaid-anon and I brainstorm deranged plot ideas constantly, and she is my best/worst little gay graphic critic.
14. What’s your all-time favorite ship?
I'm going to need to say Tanthamore.
15. What’s a WIP you want to finish but doubt you ever will?
I'm not going to speak this into existence. I'll say that there are a few fics that I have agonized over for a very, very, very, very, very long time.
16. What are your writing strengths?
I think I get to the point pretty well. I keep action and development moving. I think I do some good figurative language. I trust my instincts on where a story needs to go next.
17. What are your writing weaknesses?
The Agonies. The connective tissue between important scenes. Not knowing what to have characters do when they're on their own. Run on sentences. Too many WIPs and not enough commitment.
18. Thoughts on writing dialogue in another language in fic?
I haven't ever found it necessary? I guess I feel about it the way I feel about captions for another language. You know when captions will say "speaks in a foreign language?" Bane of my existence. Either translate it or get out of here.
19. First fandom you wrote for?
Pretty Little Liars. I was a big Paily fan for awhile there. Those live back on fanfiction.net
20. Favourite fic you’ve written?
The Past feels really good to write because it pulls together all these threads in my brain for the Kinkverse girls, and it feels very unifying for that vision. It's satisfying connecting the dots.
As for who to tag on this: @barmaid-anon, @commanderbuffy, @swashbucklery, @multiplefandommess, @vetiverriver, @onlyshestandsthere, @claymoressword, @kittanthaloselorashield
12 notes
·
View notes
Text
Do You Really Need a VPN? Find Out!
Introduction

In today’s digital world, our online privacy is constantly under threat. Have you ever wondered how secure your personal data is when you're browsing the web or accessing public Wi-Fi? With increasing concerns about data breaches and surveillance, many people are turning to Virtual Private Networks (VPNs) to shield their online activities. But with so many options available, it can be overwhelming to figure out whether a VPN is truly necessary for you or if it’s just another tech trend.
This article aims to demystify VPNs by providing a clear and concise overview of what they are and why they have become a hot topic in the realm of internet security. We'll delve into the core functions of VPNs, explore their benefits and potential drawbacks, and help you assess if a VPN aligns with your personal online needs. By the end of this guide, you'll have a better understanding of whether a VPN is an essential tool for you or if other solutions might be more suitable for safeguarding your online presence.
What is a VPN?
A Virtual Private Network (VPN) is a tool designed to enhance your online privacy and security. At its core, a VPN creates a secure, encrypted connection between your device and the internet. This connection acts like a private tunnel that shields your online activities from prying eyes, making it harder for anyone, including hackers and internet service providers, to monitor what you're doing online. Think of a VPN as a protective cloak that conceals your digital footprint and allows you to browse the internet with a greater sense of security.
The functionality of a VPN involves routing your internet traffic through a remote server, which masks your IP address and encrypts your data. This process not only hides your true location but also ensures that any data you send or receive is encrypted, making it nearly impossible for unauthorized parties to access. By connecting to servers in various locations, a VPN also allows you to bypass geographical restrictions and access content that might otherwise be blocked in your region. This dual-layer protection—hiding your IP address and encrypting your data—creates a more secure and private browsing experience.
Understanding "What is a VPN?" is crucial for anyone concerned about online privacy. In an era where personal data is a valuable commodity and cyber threats are prevalent, having a VPN can be a significant asset. It offers peace of mind by safeguarding your information and providing a shield against potential threats. As we explore further in this article, you'll learn more about when a VPN is most beneficial and if it’s the right choice for your personal online security needs.
Explore the Benefits of ZoogVPN Today! If you're considering enhancing your online privacy and security, why not start with ZoogVPN? With incredible pricing and a range of features designed to keep you safe online, ZoogVPN is a great choice. Learn more about ZoogVPN and find the perfect plan for you.
Should I Accept VPN?
When considering whether to accept or adopt a VPN, it’s important to weigh its numerous benefits. One of the primary advantages of using a VPN is enhanced privacy. By masking your IP address and encrypting your internet traffic, a VPN shields your online activities from prying eyes such as hackers, advertisers, and even your internet service provider. This level of privacy ensures that your personal data remains confidential, making it significantly more challenging for third parties to track your browsing habits. Additionally, a VPN provides access to restricted or geo-blocked content, allowing you to enjoy streaming services, websites, and information that may be limited based on your location.
A VPN can be particularly relevant in various scenarios. For instance, if you frequently use public Wi-Fi networks, such as those in cafes or airports, a VPN offers an added layer of security against potential cyber threats. Public networks are often vulnerable to attacks, and a VPN helps protect your sensitive information from being intercepted. Similarly, if you travel often and want to access your home country’s streaming services or websites that are otherwise inaccessible abroad, a VPN can easily bypass these regional restrictions and provide you with the content you desire.
Considering the question "Should I accept VPN?" also involves evaluating your personal and professional needs. If you’re concerned about online privacy or frequently work with sensitive information, using a VPN can significantly enhance your digital security. It can also be beneficial if you live in a region with restrictive internet policies and want to freely access global content. On the other hand, if your online activities are relatively routine and you rarely access sensitive data, you may not find a VPN as crucial, although it still provides added security.
Ultimately, deciding whether to accept a VPN depends on your specific needs and concerns. The key is to assess how often you encounter situations where privacy and security are paramount. If these concerns resonate with your online habits, integrating a VPN into your routine can be a proactive step towards safeguarding your digital life and expanding your internet freedom.
When Should You Not Use a VPN?

While VPNs offer numerous benefits, there are certain situations where using one might not be ideal or necessary. For example, if you're accessing websites or services that don’t handle sensitive information or are already secure, the added layer of encryption provided by a VPN might be redundant. Additionally, if you're in a low-risk environment, such as a private and secure home network, the need for a VPN diminishes. Similarly, some websites and online services are designed to detect and block VPN traffic, which can result in difficulties accessing the content you need.
Another important consideration is the impact a VPN can have on your internet speed and performance. Because VPNs reroute your internet traffic through an external server, this can introduce latency and reduce connection speeds. This slowdown can be noticeable when streaming high-definition content or engaging in online gaming, where speed and responsiveness are crucial. If you’re performing activities that demand high-speed connections or if you have a limited bandwidth allocation, the performance drop caused by a VPN might outweigh its benefits.
Deciding when not to use a VPN also involves evaluating your specific use cases. For instance, if you’re using the internet for casual browsing or non-sensitive activities, the added security of a VPN might not be worth the potential decrease in speed. Moreover, for certain applications and services that function best with a direct connection, using a VPN could interfere with their optimal performance. It’s essential to weigh the trade-offs and determine whether the privacy and security benefits of a VPN align with your current needs and online behavior.
What is the Downside of a VPN?
While VPNs are often praised for enhancing online privacy and security, they are not without their downsides. One major concern is the privacy of the VPN provider itself. Although VPNs are designed to shield your data from external parties, some providers may log user activity or metadata, potentially compromising the very privacy they aim to protect. It’s crucial to research and choose a VPN service with a strict no-logs policy and transparent privacy practices to ensure that your data remains confidential.
Another consideration is the cost associated with subscribing to a VPN service. While free VPNs are available, they often come with limitations such as reduced speeds, fewer server options, and potential privacy issues. Paid VPN services, which generally offer better performance and security features, can range from relatively affordable to quite expensive. This ongoing expense might not be justifiable for everyone, especially if the benefits of a VPN do not align with their online activities and security needs.
Compatibility issues can also pose a challenge when using a VPN. Some websites and online services actively block VPN traffic to prevent bypassing geographical restrictions or fraud detection. This can result in difficulties accessing certain content or services while connected to a VPN. Additionally, certain applications and websites may not function properly with VPNs enabled, leading to disruptions in your online experience. It’s important to consider these potential drawbacks when evaluating whether a VPN is the right choice for your needs.
Does a VPN Affect Wi-Fi?
When you connect to a VPN, it’s common to experience changes in your Wi-Fi speed. A VPN routes your internet traffic through a secure server, which can introduce additional layers of encryption and data handling. This process, while enhancing security, can slow down your internet connection. The extent of this speed reduction depends on several factors, including the VPN server’s location, the encryption protocol used, and the overall quality of the VPN service. High-quality VPNs often minimize speed loss, but users should be prepared for potential decreases in browsing speed.
Network issues are another consideration when using a VPN over Wi-Fi. VPN connections can sometimes lead to unstable network performance, causing intermittent drops or slower connectivity. This can be especially noticeable on wireless networks with lower signal strength or higher congestion. Additionally, because VPNs create an encrypted tunnel for data, they may interfere with certain network protocols or configurations, potentially leading to connectivity problems or difficulty accessing specific online services.
In some cases, the interaction between a VPN and Wi-Fi networks can lead to unexpected complications. For instance, VPNs might struggle with certain types of network hardware or software, which can cause compatibility issues or connectivity errors. Additionally, some Wi-Fi networks, particularly in public or restricted environments, may block VPN traffic, further complicating your internet access. Users should consider these potential problems and test their VPN connection on various networks to ensure consistent performance.
Overall, while a VPN can impact Wi-Fi speed and connectivity, the degree of effect largely depends on the quality of the VPN service and the specific network conditions. For users who prioritize online privacy and security, the trade-off in speed and potential network issues might be worthwhile. However, it’s important to choose a reputable VPN provider and understand how it might interact with your Wi-Fi setup to minimize any negative impacts.
Is a VPN Needed for Home Wi-Fi?
When considering home Wi-Fi security, many people wonder if a VPN is necessary. A VPN can certainly add an extra layer of protection by encrypting your internet traffic and masking your IP address, which is beneficial for safeguarding sensitive information from potential threats. However, for most home networks, basic security measures such as strong passwords, WPA3 encryption, and regular firmware updates on your router are often sufficient to protect against common threats. While a VPN enhances security, its benefits might be more pronounced for those who frequently use public Wi-Fi or access sensitive information remotely.
Beyond using a VPN, there are several effective ways to secure your home Wi-Fi network. Implementing robust security protocols like WPA3 can prevent unauthorized access and ensure that your network is shielded from potential intruders. Additionally, regularly updating your router’s firmware and setting up a guest network for visitors can further bolster your home network's security. For many users, these measures, combined with cautious online behavior, can provide adequate protection without the need for a VPN.
Secure Your Online Presence with ZoogVPN Are you ready to take control of your online privacy? ZoogVPN offers excellent services at unbeatable prices. Discover how ZoogVPN can protect your data and enhance your browsing experience. Check out ZoogVPN's plans and find the best fit for you.
Is There Anything Better Than a VPN?
When it comes to online privacy and security, VPNs are often touted as the go-to solution, but they’re not the only tools available. Alternatives like proxy servers, secure browsers, and end-to-end encryption can also offer significant protection for your digital activities. Proxy servers, for instance, act as intermediaries between your device and the internet, masking your IP address but typically without the same level of encryption as a VPN. Secure browsers like Tor are designed to enhance privacy by routing your internet traffic through multiple servers, though they can sometimes slow down your browsing experience. End-to-end encryption ensures that your communications are only readable by the intended recipients, making it ideal for secure messaging and email.
Comparing these alternatives to VPNs reveals distinct differences in effectiveness and use cases. VPNs provide robust encryption, which secures all of your internet traffic and is effective across various devices and platforms. In contrast, proxy servers offer less security but can be useful for bypassing geo-restrictions. Secure browsers like Tor offer enhanced anonymity but may suffer from slower speeds and limited usability. End-to-end encryption is crucial for protecting specific types of communication, but it does not encrypt all internet traffic like a VPN does. Each tool has its strengths and limitations, so the best choice depends on your specific privacy and security needs.
While VPNs offer comprehensive protection, evaluating these alternatives can help you find a solution that best fits your requirements. For users who need robust, all-encompassing privacy, a VPN might be the preferred choice. However, if you’re looking for targeted protection or want to supplement your existing security measures, integrating secure browsers, proxies, or end-to-end encryption into your digital routine can be effective. Each tool can complement a VPN or serve as an alternative based on what aspects of privacy and security are most important to you.
Ultimately, the choice between a VPN and other privacy tools depends on the level of security and anonymity you seek. For comprehensive protection and convenience, a VPN is often a strong choice. However, exploring other options like proxy servers, secure browsers, and end-to-end encryption can provide additional layers of security and privacy, catering to various needs and preferences.
Do We Really Need a VPN?
In the ongoing debate about online privacy and security, the necessity of a VPN often boils down to a balance of pros and cons. On the plus side, VPNs offer substantial advantages such as enhanced privacy by masking your IP address, secure data encryption to protect sensitive information, and the ability to access geo-restricted content. These features make VPNs a valuable tool for anyone concerned about their digital footprint or wanting to bypass regional restrictions. However, VPNs also come with potential drawbacks, including the cost of subscription services, possible slowdowns in internet speed, and occasional compatibility issues with certain websites or services. Understanding these benefits and limitations is crucial in evaluating whether a VPN aligns with your needs.
Deciding whether to invest in a VPN requires a personal assessment of your internet habits and security requirements. For users who frequently handle sensitive information, access region-locked content, or simply wish to enhance their online privacy, a VPN can be an essential tool. On the other hand, if you only use the internet for basic browsing and are not concerned about privacy or geographic restrictions, the necessity of a VPN may be less compelling. It's important to weigh your specific needs and how a VPN would fit into your overall digital security strategy.
Ultimately, the question of whether we really need a VPN is a highly individual one. Consider your internet usage patterns, your level of concern about privacy, and your willingness to invest in additional security measures. By carefully evaluating these factors, you can make an informed decision about whether a VPN is a worthwhile addition to your online toolkit. Whether you opt for a VPN or choose other methods to safeguard your digital life, the key is to ensure that your choices align with your personal privacy and security goals.
Conclusion

As we’ve explored, the decision to use a VPN hinges on weighing its benefits against its potential drawbacks. VPNs provide valuable features such as enhanced privacy, secure browsing, and access to geo-restricted content. However, they also present challenges, including potential impacts on internet speed and the financial cost of subscription services. Ultimately, the effectiveness of a VPN depends on your individual online habits and security needs. Understanding these aspects will help you make an informed choice about whether a VPN is right for you.
It’s essential to take stock of your own online activities and security concerns when evaluating whether to use a VPN. Consider how often you handle sensitive information, if you frequently access content restricted by geography, and whether you are willing to pay for a subscription. By aligning your personal needs with the features offered by VPNs, you can determine whether this tool will enhance your online experience or if other solutions might be more appropriate.
We’d love to hear from you about your experiences with VPNs or any questions you might have! Please share your thoughts, stories, or inquiries in the comments section below. Your feedback not only helps us understand your perspective but also assists fellow readers in navigating their own decisions about VPN use. Engage with us and be part of the conversation about securing our digital lives!
FAQ: Understanding VPNs
What is VPN and Why Do I Need It?
A VPN, or Virtual Private Network, is a tool that creates a secure, encrypted connection between your device and the internet. By masking your IP address and routing your internet traffic through a remote server, a VPN enhances your online privacy and security. You might need a VPN to protect sensitive data from hackers, access region-restricted content, or maintain anonymity while browsing.
Is it Worth Getting a VPN?
Whether a VPN is worth the investment depends on your personal needs and online habits. For those who frequently use public Wi-Fi, handle sensitive information, or want to access content unavailable in their region, a VPN offers substantial benefits. It enhances security, provides privacy, and enables unrestricted access to global content. However, if you mostly use the internet for general browsing and don’t engage in activities that require high privacy, the need for a VPN might be less critical.
What is the Downside of Having a VPN?
While VPNs offer numerous advantages, they also have some downsides. Potential issues include reduced internet speed due to encryption overhead, possible compatibility problems with certain websites or services, and the cost of subscription services. Additionally, some VPN providers may log user data, which could undermine privacy if not carefully vetted.
When Should a VPN Not Be Used?
A VPN might not be necessary in every situation. For example, if you’re using a secure, private network or accessing sites and services that don’t require high levels of privacy, the benefits of a VPN may be minimal. Additionally, VPNs can sometimes interfere with online services, such as streaming platforms or secure financial transactions, which may not function correctly when routed through a VPN server.
Is VPN Legal in the UK?
Yes, using a VPN is legal in the UK. It is a common tool for enhancing privacy and securing internet connections. However, while VPNs themselves are legal, they should not be used to engage in illegal activities. Ensure that you comply with all laws and regulations when using a VPN.
Should I Accept VPN?
Accepting a VPN largely depends on your personal security needs and internet usage. If privacy, data security, or access to restricted content are important to you, accepting and using a VPN can be a prudent choice. Evaluate your online habits and determine whether a VPN aligns with your requirements for enhanced protection and access.
Is it Good to Have VPN on All the Time?
Having a VPN on all the time can be beneficial, particularly if you frequently access public Wi-Fi or handle sensitive information. It ensures that your data is consistently protected and that your online activities remain private. However, if a VPN causes significant slowdowns or interferes with specific services, you might choose to turn it on only when needed. Evaluate your personal usage to determine the best approach.
Ready for Ultimate Online Security? Don't wait to secure your internet connection and protect your personal data. ZoogVPN provides top-notch VPN services at fantastic prices. Visit ZoogVPN now to explore their offerings and start browsing safely today!
10 notes
·
View notes
Text
Fast list for privacy minded people (I lied, it's long):
Change your DNS from the default ISP provisioned one to literally anything else that has decent reputation. CloudFlare is pretty good to bet on, and Firefox has toggles to use it instead of your system DNS. Alternatively if you don't hate Google, they have a DNS that is marginally an improvement from an ISP default but you're certainly being datamined by Big Letters and they are gleefully compliant warrants or not. There are ample public DNS servers out there unlike the next point.
That is fine for general browsing and making it difficult for your ISP to snoop on you, a step further is obfuscating your public IP which makes it difficult for third-parties to track and identify you. VPNs come in here. Free ones ought to be avoided unfortunately in all but the most milquetoast use-cases. Even then they are likely collecting your data so it's best to use a paid service from a well reputed provider that is specifically not based in a 14 Eyes or mandatory logging country. CyberGhostVPN has a lot of literature on this to reference.
Use HTTPS-forcing extensions and avoid HTTP-only websites. This will require all data in transit to be encrypted which makes it impossible for third-parties including your ISP to know exactly what you are doing. Some sites still have HTTP bits on otherwise HTTPS websites, make sure your extension or browser refuses to load these parts without your consent. However be mindful that the server you are talking to obviously will know what data you sent or requested and may or may not store or use it in some way. This info may be available in some privacy statement etc. Assume that your IP, connection details, etc are all logged and act accordingly.
Avoid Tor unless you are especially confident in your understanding. While it isn't 100% confirmed, it's been generally accepted that certain powers have indeed compromised swathes of the Tor network and have the ability to eventually identify you. The naive use of this tool will be more of a hindrance causing false security than it will help you if you are actually needing a list like this.
Likewise, do not assume encryption means anything. Don't buy into anything you don't understand enough to feel confident explaining to someone else. At most, if it isn't a absolute pain in the ass, find a reputable encrypted email provider or learn how to use OpenPGP to encrypt email communications. Side note to OpenPGP, it also is useful as a way to verify your communications are yours and is often used as such in mailing lists or for contributing to open software/validating packages. In a deep fake world this will become more important but isn't quite a privacy matter.
Generally speaking, fancy tools and technologies are worthless if you can't really use them and actually a hindrance to you. If you start with a zero privacy/zero security assumption as default and operate accordingly you'll already be far ahead of the curve with little added complexity or effort. Don't say stupid shit, don't do stupid shit, don't give out stupid shit. Never ever use public or work APs for personal or private browsing, I'd say don't even connect to public wifis at all even. Don't do personal stuff at work either, and try to keep work computers off your private network and personal devices off work networks. Mindset is probably by far more important than any of the other points. Techno neophytes and fetishists will never tell you that most of your privacy and security comes from your brain.
And since it won't let me do it my way.. 0. Security does not mean privacy, nor does privacy mean security. These are two separate goals. This is an important distinction to make.
5 notes
·
View notes
Text
Facebook "New Rules"
A few years ago, I decided to signup for an encrypted email service (Protonmail), to protect my emails from internet traffic Snoops. Later, I also signed up for a virtual private network service (ProtonVPN) which keeps the same internet traffic Snoops, from tracking my physical location and trying to mess with my browser's security. Since then several social media apps (for phones & laptops) have become "concerned" with security on 'their end' (so they say). But I've determined that they're LESS concerned with MY security than they are their own… So much so that they have surreptitious software installed to monitor what ALL of us do on social media. Lately, because I use a VPN service that can by my choice connect me to ANY server in the world that locks out 99% of snoops of all kinds all over the world. However, Facebook in its low-minded wisdom has become distrustful of MY logon attempts and of MY server addresses, even though ALL my credentials are in order. You may ask, "Rick are you having any mental problems?" No, not anything other than what I've always had..LOL! I just want to point out that the MORE security a user like any of us wants for their internet uses, the MORE the social media corps (and maybe the Govt) seem to "interrogate" our (my) intentions to be secure on our (my) end. Attached are 6 images that show Facebook's logon procedure because of MY security apps that are keeping me safer & more secure. And BTW..there is a false statement within the first one.. "We sent a notification to your Linux.." Linux is my operating system, the same type of technology that Windows is, but it's Not Windows and it's Not email. So it's impossible to "send a notification" to my operating system!! Trust me on this.. Anyway here are the images of the messages I get from Facebook Every Time I simply want to login to my Facebook account:
1 This is bullshit. Linux is an operating system, not an email address or a social media app:
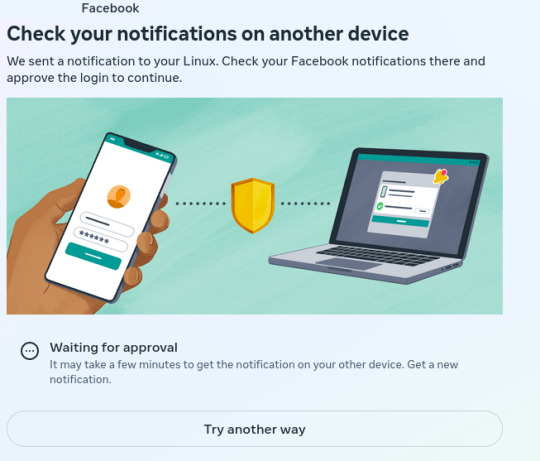
2 It's not Google Authenticatior..LOL!
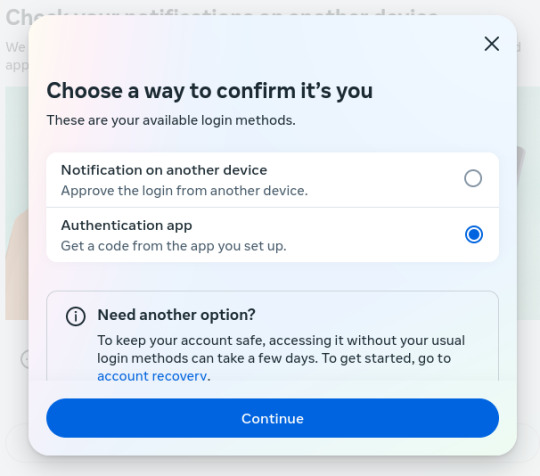
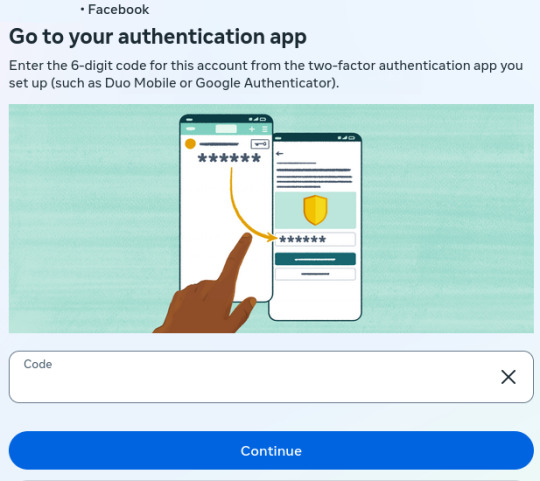
3. This should've been the 2nd question after my Password was entered! I don't need an education on authenticators or how to use them. I'm old but not stupid or naive, FFS!
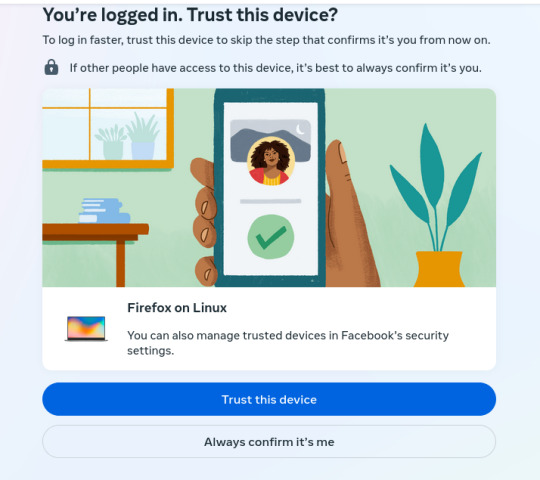
4. If I'm logged in, I've already trusted this device. How moronic can you assholes be?
5. Okay Okay. I've entered all my info that's protected and now you're asking me if it's REALLY ME? Are you phucking serious right now??

6. I approved a login from Zurich, Switzerland and you're letting me know that I approved it, but your final statement is "Finish"? The people in Switzerland are not "Finish", their Swiss!! Did your AI algorithm get world geography confused with nationalities?
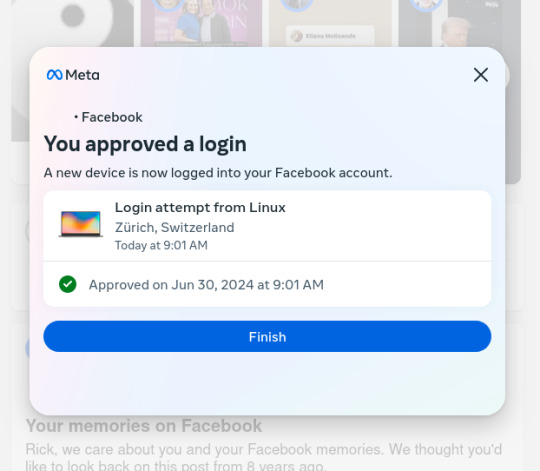
Facebook has a legion of phucking idiots.. Or..they have phucking idiots programming their "AI" algorithm. .... .... .... Welcome to the Machine.... tic-toc-tic-toc-tic-toc-tic-toc-tic-toc.
10 notes
·
View notes
Text
In my IT security classes, I learned about John The Ripper which is a password cracking tool and let me just tell you, it is overpowered. I actually had a passworded file on my system - forgot the password, forgot what even what the file was even OF and was like HEY what a GREAT opportunity to use what i learned and well, it cracked it easy.
It comes with a crazy amount of utilities including ones to get the hashes of bitwarden files.
And you might be thinking, what's the point of passwords if you can just ... well, crack 'em?
The greatest security you can have is time. Because while any password can be cracked, it's about the DURATION it takes to crack it. So a password like pass123 will be cracked in 10seconds, but a password like 2å°Ùbã¥ÚûûÌGçÂ[7Vsgà will take 10 years or longer.
(i'm giving the sky-high view here - bear with me)
The complexity of your password ABSOLUTELY matters.
so you might be thinking, well <some fancy expletive>, how am i gonna remember my password then.
You're not, you're gonna get a password manager, and I'd advise an offline one.
But you'll need to at least remember ONE complex password to keep your other passwords safe.
I personally like KeePass but you can use others. I'd advise AGAINST cloud serviced password managers - especially dashlane and omg lastpass, because there have been so many breaches. I don't know of others really, but I understand the need to have passwords available when you're not in front of the ONE computer that has the offline password manager.
You could create a home cloud server and use wireguard to securely tunnel into your network from anywhere to use keepass {I'm actually drafting a 'how-to' for you tumblrinas about this actually}
I'd also advise AGAINST using your browser to manage your passwords.
anyway - when crafting a password, a password manager usually has tools to make the process easier (keepass has a lot of easy ways to configure it), you'll want to keep complexity and length in mind:
make it no shorter than 12 characters
Don't reuse passwords
use symbols, special characters, spaces even!
try not to create passwords BASED on other passwords. Like if an old password was like C@tR@mAd3M3Afurry, don't make the next one C@tR@mAd3M3Afurry2
It's also really important NOT to make an easy-to-remember password either because when it comes down to it, social engineering removes the need for tools like JohnTheRipper
#and that's my IT Security lesson of the day#or week#or month#i don't do a lot of these but i want to#stay safe and stay silly
4 notes
·
View notes
Text
The San Francisco tech scene is completely beyond satire. I'm in a discord server for game developers based in SF because even though I don't live in the bay area anymore it's still the closest hub for indie developers near me. I went to one of their meetups once, the talk itself was completely useless and I left about 30 mins in, but I did get two people to playtest my demo beforehand so it was still worthwhile. One of those things where you're in a sea of 50 people who annoy you and are able to find maybe one or two people who are cool to talk to.
Anyway, I just received a ping about their next meetup, which is-- I literally could not make up something more on the nose than this if I tried--
brought to you
by
✨ J.P. Morgan ✨
.
Actual quote from the event page:
Are you a developer looking to accept payments and monetize your users effectively? We are excited to announce this unique opportunity to get in on the ground floor and learn about how to monetize your payment flow for your gaming applications at scale. As you may be aware, the Apple App Store and other stores are now allowing outside payment methods within iPhone apps due to "anti-competitive" laws in the EU. As a result, if you are part of Apples small business program, you may be eligible for a discounted percentage fee on IAP instead of the normal 30% fee. We hope you can attend to explore these concepts and learn how you can save money on payment processing fees with J.P. Morgan Payments.
Food is sponsored by J.P. Morgan and drinks are available for purchase at the DNA Lounge bar. All proceeds from drink sales go directly to the venue which helps them keep the lights on, and also helps us continue to host events in their space. DNA Lounge is over 3,000 sqft and is the largest venue we've ever hosted our events at. Speakers will go on stage at 7:00pm. This is an all ages event, is open to the public and is a professional networking event for game developers, artists, students, indies, or really anyone interested in game development. ASL Interpretation services available upon request via email.
Speaker Lineup:
Alan Lee | Developer Relations at J.P. Morgan Payments
Enhance your Payment Experience with J.P Morgan’s Payment Developer Platform
In this session, The J.P Morgan Payments developer relations team will showcase how the Online Payments API allows you to seamlessly accept, process and settle payments from the large suite of supported payment methods. We’ll explore the extended capabilities like tools for fraud prevention, recurring payments and demonstrate how these features can help you improve authorization rates, secure transactions, and gain valuable insights into your payment flow.
so anyway if anybody needs me I will be basically anywhere except at this particular event
#it's such a shame because I actually love so many things about San Francisco#the techbros.... they are the worst and i cannot stand them
7 notes
·
View notes
Text
How to Become a Cloud Computing Engineer
Introduction:
Cloud computing has become a cornerstone of modern IT infrastructure, making the role of a Cloud Computing Engineer highly in demand. If you're looking to enter this field, here's a roadmap to help you get started:
Build a Strong Foundation in IT A solid understanding of computer networks, operating systems, and basic programming is essential. Consider getting a degree in Computer Science or Information Technology. Alternatively, Jetking offer you to make your career in Cloud computing Courses and gain the technical knowledge needed.
Learn Cloud Platforms Familiarize yourself with popular cloud service providers such as AWS (Amazon Web Services), Microsoft Azure, and Google Cloud. Many platforms offer certification courses, like AWS Certified Solutions Architect, which will help validate your skills.
Gain Hands-On Experience Practical experience is critical. Set up your own cloud projects, manage databases, configure servers, and practice deploying applications. This will give you the real-world experience that employers seek.
Master Programming Languages Learn programming languages commonly used in cloud environments, such as Python, Java, or Ruby. Scripting helps automate tasks, making your work as a cloud engineer more efficient.
Understand Security in the Cloud Security is paramount in cloud computing. Gain knowledge of cloud security best practices, such as encryption, data protection, and compliance standards to ensure safe operations and become Master in cloud computing courses.
Get Certified Earning cloud certifications from AWS, Azure, or Google Cloud can enhance your credibility. Certifications like AWS Certified Cloud Practitioner or Microsoft Certified: Azure Fundamentals can provide you a competitive edge.
Keep Learning Cloud technology evolves rapidly, so continuous learning is key. Stay updated by taking advanced courses and attending cloud tech conferences.
Join Jetking today! Click Here
By building your expertise in these areas, you’ll be well on your way to a successful career as a Cloud Computing Engineer!
2 notes
·
View notes