#How to unlock bitlocker without password
Explore tagged Tumblr posts
Text
Understanding the BitLocker Recovery Key: What It Is and How to Use It

Hey Tumblr friends! 🌟
If you've recently enabled BitLocker on your Windows device and suddenly find yourself staring at a prompt asking for a BitLocker recovery key, you might be wondering what this mysterious key is all about. Let’s dive into the essentials of the BitLocker recovery key, why you might need it, and how to find it when necessary.
What is a BitLocker Recovery Key?
A BitLocker recovery key is a 48-digit numerical password that acts as a backup method to unlock your encrypted drive. This key is generated when you first enable BitLocker on a drive and is crucial for situations where you can’t access your drive through the usual means.
Why Might You Need a BitLocker Recovery Key?
There are several reasons why you might be prompted to enter your BitLocker recovery key:
Forgotten Password: If you forget your BitLocker password, the recovery key is your only way to regain access.
Hardware Changes: Making significant changes to your computer’s hardware, like replacing the motherboard, can trigger the recovery key prompt.
Software Updates: Major updates to your operating system or BIOS might require you to enter the recovery key.
Security Concerns: If BitLocker detects potential security threats or unauthorized access attempts, it will ask for the recovery key.
Where to Find Your BitLocker Recovery Key
If you’re in a pinch and need to find your BitLocker recovery key, here are some common places to check:
Microsoft Account: If you linked BitLocker to your Microsoft account, you can find your key on the Microsoft BitLocker recovery key portal.
USB Drive: If you saved the recovery key to a USB drive, make sure to keep it somewhere safe and accessible.
Printout: Some folks print their recovery key and store it securely.
Azure Active Directory (AAD): If your device is connected to an organization’s AAD, your IT department might have a copy.
File: If you saved the recovery key as a file, it’s usually named something like BitLocker Recovery Key.txt.
What to Do if You Can’t Find Your Recovery Key
If you can’t locate your BitLocker recovery key, your options are unfortunately limited. Without the recovery key, accessing your encrypted data is not possible. This is a vital reminder to store your recovery key securely in multiple locations.
Best Practices for Managing Your BitLocker Recovery Key
Store Multiple Copies: Keep your recovery key in several places, such as your Microsoft account, a USB drive, a printout, and a secure digital file.
Secure Storage: Ensure your recovery key is stored in a safe location, like a safe or encrypted digital storage.
Keep Updated: Regularly update your recovery key and ensure it’s accessible, especially after significant system changes.
By following these best practices, you can avoid the potential frustration and data loss associated with being locked out of your BitLocker-encrypted drive.
For a more detailed guide on BitLocker and managing recovery keys, including step-by-step instructions and troubleshooting tips, check out this Comprehensive BitLocker Recovery Key Guide.
Hope this helps you stay secure and stress-free! If you have any more questions about BitLocker or need further assistance, feel free to drop a comment. 💬✨
Also read our related articals:
How Ad Blockers Might Trigger BSOD Blue Screen
Audio Troubleshooter: Resolve No Sound Issues On Dell Laptop
Laptop Not Connecting To WiFi? Fix Laptop WiFi Issues Today!
How To Fix ‘No Sound’ Issues On Your Laptop Or PC: A Comprehensive Guide
1 note
·
View note
Text
How to unlock bitlocker without password

#How to unlock bitlocker without password install#
#How to unlock bitlocker without password password#
#How to unlock bitlocker without password password#
Please type the correct password and click Unlock button to access this BitLocker encrypted drive. Just plug the Bitlocker encrypted drive on another PC and you will see a padlock on BitLocker encrypted volume.ĭoubel click the drive letter and a small pop-up appears at the upper right corner, asking you to enter password to unlock this drive. You can access any BitLocker encrypted drive on any Windows PC or laptop if you had the right password. How to Unlock BitLocker Encrypted Drive on Another PC Adopt one of the most secure encryption algorithms on earth and there is no way to break such a machanism up to now.Įasy to Use: You can easily set a BitLocker encrypted parition or USB within several mouse clicks. The only requirement is an activated copy of Windows OS. No extra download and no need to pay a single penny for such an useful function.
#How to unlock bitlocker without password install#
You don't need to download and install third-party tools in order to password protect individual partition/volume of internal hard disk or external USB connected drives. Benefits for Using BitLocker Encrypted DriveīitLocker encryption is one of the best features available in Windows OS. The BitLocker encrypted drive can be only accessible when the correct password is entered. That's why it is so popular for data encryption.Īnother benefit is that BitLocker uses advanced encryption algorithm (AES with 128-bit or 256-bit), making it impossible to decrypt the password and securing user data in safe place. And it is much more accessible on modern Windows PCs and laptops as an integrated part of Windows OS. Microsoft introduced BitLocker encryption feature since the release of Windows Vista and it becomes a native tool for encrypting internal partition and external drives (USB, hard drive or SSD). How to Unlock BitLocker Encrypted Drive on Another Mac Benefits for Using BitLocker Encrypted Drive

1 note
·
View note
Link
Bitlocker recovery is a procedure of recovering the access of bitlocker during when it’s impossible to unlock it in a normal way. It is a default attribute of complete encryption that is drawn in order to provide protection & security to your data. This attributes utilizes the AES Encryption algorithms in CBC/XTS modes with 128 or 256 bit key.
#bitlocker recovery#bitlocker recovery key#bitlocker recovery key id#bitlocker recovery keys#what is bitlocker recovery#how to find bitlocker recovery key#what is bitlocker recovery key#how to unlock bitlocker without password and recovery key#why does my computer keep asking for bitlocker recovery
0 notes
Text
Thess vs Tech Updates
Good news and iffy news on the “trying to set up the work from home stuff” front.
Good news! I found my stupid Bitlocker password! I eventually thought to log onto our company’s IT helpdesk site and look through the closed tickets.
Also good news! Once I got that unlocked, and after a little bit of fanangling, I did the VPN thing no problem!
And now we get into the iffy part, because after that, I still need to access the company server. Which is where some of the instructions started getting unclear. See, the VPN instructions also gave me what I should be doing to connect to the work server, but it’s different servers per building. The example given on the paperwork gave a server address for the main building. I don’t work in the main building. The instructions said, “See list below” for server addresses. There was no “list below”.
Soooooooo back I went to the company IT helpdesk site. Flagged up the issue on the open ticket. Two things happened in fairly quick succession at that point. First was an email from the guy I’ve been dealing with, saying, “Okay, here’s the address you need to use; let me know if you have problems and I’ll walk you through it by phone”. The second was another IT guy going, “Okay, we’re starting a new ticket for this specific issue so we’re closing the current ticket”. Because apparently they’re really picky about one ticket per issue and they’d rather have five tickets for five separate niggles instead of one big ticket going, “Get this person set up with work from home” that incorporates all five niggles. I have no idea why.
But I have a server address, so that’s fine, right? Nope. Server address doesn’t work.
So I respond to the email (which was copied to Scruffman, so I copied him in the thing as well so he’d have an interim update) saying, “The address doesn’t work; I’m at home at the moment so please call my mobile and walk me through this”. No response a half-hour later, but I can be patient.
Thing is, I want this resolved today for a lot of reasons. First of all, it would be really nice to be able to just have this sorted and work from home as of this week. But also, Mum emailed me yesterday going, “How about dinner Thursday?” Which ... thanks, Mum, but could I get a little more lead time than that, or at least have things arranged for a Monday when I know I’m not going to have to be at work? As it is, Thursday’s problematic specifically because the Tube and Overground strikes set up for that day weren’t cancelled like the National Rail strikes for this week were, and my commute has been iffy enough as it is. Particularly given that Scruffman and I have basically agreed Thursdays as my one day per week to come in (though I’m going to try to renegotiate for this week at least, if everything works out today), this Thursday is going to be potentially bad. Anyway, I told her I’d let her know by the end of the day so I can at least get a time frame. Honestly, I wish she’d ask in a less specific way - like, “Let’s go to dinner - what day would be good for you?” instead of picking a day herself. A retired person has a rather different schedule than someone who a) isn’t and b) relies on unreliable public transport.
I would dearly love to go back to bed - I ran something of a fraught bit of combat last night and couldn’t sleep without copious wind-down time - but I am waiting for a phone call. Of course, I’m boned if said call doesn’t come by, say, half-three because Scruffman leaves the office at 4pm these days and if I don’t get things sorted before he leaves, there am I dealing with another week of commute. Eh, there’s still a few hours to go. Fingers crossed.
3 notes
·
View notes
Text
How To Open Dmg Files On Ipad
When you download software from the Internet on your Mac, you may find that the software installation file is a DMG file. So, what is a DMG file? And how to open DMG files on your Mac? Let's find the answer from the following content now.
What's a DMG file?

The DMG file is a disk image file of macOS, which is just like the Windows ISO file in some way. It is treated by macOS as it were a physical disk and can contain the program installation file.
Way 1: Open DMG Files Directly
Double-click the DMG file in the place where stores it, such as Download folder, desktop, etc. Then a box written with 'opening-name.dmg' will be shown. When the DMG file is verified successfully, it will be opened automatically and you can access it now.
Tap Select the file name Organize. Open macOS DMG files on Windows. Extract any file from a DMG archive with just a few clicks! Passcodes Explore + extract data from iOS backups & devices Download iCloud photos & data Manage & backup your iPhone and iPad Work with DMG files on Windows Get data from BlackBerry backups. Open DMG Files with DMG Extractor. DMG extractor provides another choice for extracting DMG files. The free version works well, but it does have some limitations: You cannot extract files bigger than 4 GB; You cannot extract encrypted files; You can only extract 5 files at a time, which can be a pain if you need to extract an entire DMG file. Open Dmg File On Ipad This is the best method to download the MacOS High Sierra dmg file and I have shown you the two handy methods that you can easily download dmg file. So, I hope you understand everything and if our article was helpful for you then please give your feedback in the comment box.
Way 2: Open DMG Files with Disk Image Mounter
Step 1:Right-click the DMG file and then choose Disk Image Mounter option in the menu of Open With button.
Note: After clicking Mounter button, a small window will be popped out to tell you that the DMG file is opening.
App To Open Dmg Files On Ipad
Step 2: After the DMG file is mounted, its content will be displayed directly for you to use.

Way 3: Use a Tool to Open DMG Files
Step 1: Install iSunshare BitLocker Genius on your Mac.
Step 2: Launch BitLocker Genius. Then click Attach option in the interface.
Step 3: Select the DMG file and then tap Open button in the lower-right corner of the window.
Step 4: Now, you have opened the DMG file and can install your wanted software on Mac.
Tips: iSunshare BitLocker Genius also has BitLocker decryption feature, which can unlock a BitLocker USB drive with 3 simple steps: Obtain BitLocker Genius >Mount BitLocker drive by entering password or attaching recovery key >Open BitLocker drive successfully.
Related Articles:
It’s been a week since Apple introduced iOS 15 and iPadOS 15 at WWDC 2021, but we’re still discovering some new features that weren’t mentioned on stage or on Apple’s website. In addition to having widgets on the home screen and new multitasking shortcuts, iPadOS 15 enhances the Files app with a progress bar, NTFS support, and more.
Now when you’re copying a file in Apple’s Files app, there’s finally a progress bar to indicate the remaining time and how much data has already been copied. A progress indicator icon appears right next to the create new folder button, and users can cancel ongoing tasks from there.
This alone would be a great improvement for iPad users as previously there was no way to see the progress of such tasks in the Files app, but there’s even more.
If you plug an NTFS-formatted USB stick into the iPad, it can now be read by the Files app. It’s worth noting that this is only partial support, just like on the Mac, so you’ll only get the read-only mode without being able to add files to the USB storage. Still, much better than not even being able to see the files on an NTFS flash drive as in iPadOS 14.
For those who have a mouse or trackpad paired to the iPad, iPadOS 15 enables the selection of multiple files at once with the cursor, so you no longer have to select one file at a time in order to copy, move, or share them. Unfortunately, at least in beta 1, the Files app still lacks the ability to check folder sizes or open DMG files, which are features requested by many iPad users.
iPadOS 15 beta is currently available for developers, while a public beta release will be available in July. The update is expected to be officially released to the public this fall.
How Do I Open Dmg Files On Ipad Pro
H/T Steven Fjordstrom
Read also:

FTC: We use income earning auto affiliate links.More.
1 note
·
View note
Text
Key Pieces of Bitlocker
At a while, you can want to switch off the encryption on your external encrypted drive. Briefly, encryption is fundamentally the procedure for making any data unreadable by anyone without proper authorization. After the encryption is done, you may see the status which indicates that BitLocker is on for drive C. The genuine encryption of the drive will be dependent on how large it is and the number of files are on it. There are a number of ways to run BitLocker Drive Encryption. It is a pretty advanced and useful feature of Windows and with the latest Windows 10, it's better than ever. After that, it will be turned off on the specific drive and the data is not protected by Bitlocker any more.
It is possible to get rid of a password only once you configure a new procedure of authentication. You will have to use a password you will provide when the system boots. The only issue is that you need to have a password to unlock the system that was specified when encrypt. The password shouldn't be our issue. Moreover, you must make certain you are utilizing a strong password and preferably multi-factor authentication. For passwords you have to create yourself, I prefer the DiceWare method to create strong passwords that are rather easy to remember and difficult to guess. For the reason, you wish to decide on a strong password for the account on your computer.
Your drive is going to be unlocked for as long as it's connected to your computer, but at some point, you might reboot, or will need to eject it. It is imperative to mention that if you wish to eject the USB drive, you want to click the Eject button in the computer software. Note, it is going to take a while particularly if it's a massive drive. If you wish to decrypt your hard disk, all you have to do is turn off BitLocker. So before you begin to encrypt the hard disk, you must do some particular TPM operations, which we are going to discuss in detail a bit later. With BitLocker, you make a digital hard disk, and encrypt it.
You are able to select several various ways of unlocking the drive. Then decide how you want to back up your recovery key, and last, choose how you want the drive encrypted. If you don't have either of them, it's necessary for you to erase the drive at the price of your experiment data. It's possible to also encrypt different drives than only the system drive. The operating system drive should not be encrypted with Symantec PGP or some other drive encryption technology.
The Unexpected Truth About Bitlocker
When the encryption procedure completes you'll be notified by means of a window. Depending on the size of the hard drive and the amount of data, it can take a long time so be patient. It will repartition the disk as necessary. When you discover that the encryption procedure is finished, the drive level should read BitLocker on. In addition, the procedure for establishing a personal VPN is a tiny complex.

When it's already being used, select the second option Encrypt entire drive. Being on the Internet you may take advantage of the absolute most up-to-date troubleshooters from the Windows on-line Troubleshooting Service. After encryption, nobody is going to gain access to such files till they sign in with your account. Read about the techniques you can utilize to restore access to a disk encrypted with BitLocker, and the way to restore data via an encrypted disk which you may no longer access. Also, if somebody else gains access to your passphrase or key, they will finally have the capacity to decrypt your filesso be certain to store it in a secure spot. Please note that anybody may use the recovery key to access the drive, even in case they do not know the password entered in the prior step, so please don't disclose it to others. To disable eDrive, you require physical accessibility to the drive so you may use the PSID printed on the label.
All About Bitlocker
On way it is possible to safeguard your data is by employing encryption. If you're interested in securing your data on your desktop computer or cellular devices, BitLocker is a wonderful option. DRA keys are used if you should get data off an encrypted drive and there's no wise cart readily available to decrypt. As an example, it refuses to encrypt data if you're using a weak password. The only means to guard your data completely is by utilizing encryption. In case the BitLocker metadata data on the drive is now corrupt, you must have the ability to supply a backup key package along with the recovery password or recovery key. It's now feasible to defeat the Windows Bitlocker with merely a very simple trick.
youtube
1 note
·
View note
Video
youtube
Liked on YouTube: How I Unlocked Bitlocker Without Password And Recovery Key | I Forgot Bitlocker Recovery Key https://www.youtube.com/watch?v=8kccBH-aiKo
0 notes
Text
Manually prepare drive for bitlocker windows 10

Encrypt a USB drive with BitLocker To Go in Windows 10.
How to Recover BitLocker: 13 Steps (with Pictures) - wikiHow.
Using BitLocker Drive Preparation Tool with Command... - The Windows Club.
BitLocker Group Policy settings (Windows 10) - Windows security.
4 Ways to Lock BitLocker Drives without Restart in Windows 10.
How to Format BitLocker Drive/USB/SD Card With or Without Password.
Bitlocker setup failed to IMPORT the bcd (boot configuration data.
BitLocker Use BitLocker Drive Encryption Tools to manage BitLocker.
How to prepare a single partition drive for BitLocker (MBAM).
Cannot Enable BitLocker.
BitLocker Setup Could not find a target system drive.
BitLocker Setup could not find a target system drive.
How to use BitLocker Drive Encryption on Windows 10.
How to Enable and Set Up BitLocker Encryption on Windows 10.
Encrypt a USB drive with BitLocker To Go in Windows 10.
May 26, 2022 · Search for a copy on a USB drive. The USB drive should be in a safe place so that you can recover BitLocker. Plug the drive in when prompted to enter your recovery key to unlock your drive. If you have the key saved as a text file, you must manually open the file on a separate computer to see the recovery key. To encrypt a USB drive in Windows 10, you have to start the BitLocker Drive Encryption wizard, which you can open either from File Explorer or from the Control Panel. If you choose to use File Explorer , go to This PC , right-click or press-and-hold on the USB drive that you want to encrypt, and select "Turn on BitLocker.".
How to Recover BitLocker: 13 Steps (with Pictures) - wikiHow.
Verify that the Windows Management Instrumentation (WMI) service is running. If the WMI service isn't running, in Control Panel, select Administrative Tools, and then select Services. Right-click Windows Management Instrumentation, and then select Start. 823: DPM Setup cannot access registry key <RegistryKey>. Search for Control Panel and click the top result to open the app. Click on System and Security. Click on BitLocker Drive Encryption. Source: Windows Central (Image credit: Source: Windows Central. Before beginning the encryption process, you must create the startup key needed for BitLocker and save it to the USB drive. When BitLocker is enabled for the operating system volume, the BitLocker will need to access the USB flash drive to obtain the encryption key (in this example, the drive letter E represents the USB drive).
Using BitLocker Drive Preparation Tool with Command... - The Windows Club.
If I try to enable BitLocker I get the following: Looking into the TPM Administration, it says TPM is enabled, but with reduced functionality: Note that the "Prepare the TPM" is greyed out. I've tried to Clear the TPM from this screen, and from within the BIOS itself. BIOS Security Boot is enabled, set to TPM 2.0, BIOS is set to UEFI. Scenario 1: You do not have sufficient free disk space "At least 10 percent of the active partition must remain free after the partition size is reduced by 1.5 gigabytes (GB). To resolve this error, move files to another partition or delete files.". You may need to manually prepare your drive for BitLocker. If you attempted to merge an existing drive into the system drive, the tool will fail to copy the required boot file onto the target drive to create the system drive. The following error message is displayed: BitLocker setup failed to copy boot files.
BitLocker Group Policy settings (Windows 10) - Windows security.
If you want to manually lock a BitLocker drive, you have to do this through Command Prompt: Open the Command Prompt as administrator. Type the following command and hit Enter. Note: substitute d: in the command below with the drive letter of BitLocker drive you want to lock. manage-bde -lock d: -forcedismount. Close Command Prompt. Your. If your hard drive only has one partition you can create the extra partition required for BitLocker using the BitLocker Drive Preparation Tool. This is a command line utility built into Windows. Open an administrative command prompt (right-click and choose Run as administrator) and type: B -target default Then press enter. Choose which encryption mode to use: New encryption mode (best for fixed drives on this device) Compatible mode (best for drives that can be moved from this device It says if you know the drive you're encrypting is only going to be used on Windows 10 PCs only, choose the "New encryption mode" option.
4 Ways to Lock BitLocker Drives without Restart in Windows 10.
System Restore points were also deleted ( cleanmgr is the command, then More Options tab, System Restore and Shadow Copies and Clean up) After this I re-run BitLocker drive encryption wizard and all was happy again!.
How to Format BitLocker Drive/USB/SD Card With or Without Password.
Insert a USB flash drive will save a recovery key on your USB flash drive. Let BitLocker automatically unlock my drive will unlock your OS automatically and you won't have to do anything. Select the appropriate option and proceed. You will see a window asking you to select your recovery key backup options. Now, you will see 3 options.
Bitlocker setup failed to IMPORT the bcd (boot configuration data.
Before you run the BitLocker Drive Preparation Tool on a Windows Server 2008-based computer, you must first install the BitLocker Drive Encryption optional component. To do this, follow these steps: Click Start, click Control Panel, and then double-click Programs and Features. The BitLocker Drive Preparation Tool ( BdeHdCfg) can be manually run before installing CREDANT Manager for BitLocker. Optionally, CREDANT Manager runs the tool in the background if it encounters a volume that must be encrypted. In either case, there can be a problem if the preparation tool is run with the policy 'Enabled'. How to Enable and Set Up BitLocker Encryption on Windows 10 - TechCult Pro, Enterprise, & Education editions of Windows 10 Pro & Enterprise editions of Windows 8 Ultimate & Enterprise editions of Vista and 7 (Trusted Platform Module version 1.2 or higher is required).
BitLocker Use BitLocker Drive Encryption Tools to manage BitLocker.
Step 1: Search Regedit in the search bar of start menu and then click the Regedit icon. Step 2: Go to Drive > Shell in the left pane. Then right-click the Shell, choose New > Key and name the Key as " runas ". Step 3: Double-click the Default option in the runas, enter " Lock the Drive " under Value data and click OK to save the change.
How to prepare a single partition drive for BitLocker (MBAM).
Open Windows File Explorer and locate the BitLocker encrypted drive. Step 2. Double-click the BitLocker drive or external drive, enter your password in the pop-up window. Step 3. And click "Unlock" to unlock the drive. Now, you can access the drive and manage everything in the BitLocker drive without any problem. If so, it seems that you need to use Samsung Magician to switch the Encrypted Drive status to ready to enable. And then need to reboot to enable BitLocker. Note: You may need to format the whole drive before switch the Encrypted drive status using Samsung Magician. Please Note: Since the website is not hosted by Microsoft, the link may change. You may need to manually prepare your drive for bitlocker." It properly shrunk the C: Drive Partition and created a 4th partiition, but it fails right after with the stated error, prior to the encryption process starting.
Cannot Enable BitLocker.
Store BitLocker recovery information in Active Directory Domain Services (Windows Server 2008 and Windows Vista) Choose default folder for recovery password Choose how BitLocker-protected fixed drives can be recovered Choose how BitLocker-protected removable drives can be recovered Configure the pre-boot recovery message and URL.
BitLocker Setup Could not find a target system drive.
Learn how to use BitLocker Drive Preparation Tool using Command Prompt in Windows 11/10 to prepare a drive for BitLocker Drive Encryption.... Prepares a partition for use as a system drive by.
BitLocker Setup could not find a target system drive.
Nov 28, 2018 · Third-party Windows To Go creation tools. Rufus is probably the most popular tool that can create a Windows To Go drive for Windows 8 and 10, though it may not be so obvious at first glance. Here. To properly enable BitLocker for the operating system volume, you'll need to use a USB flash drive as a startup key to boot (in this example, the drive letter E). You would first create the startup key needed for BitLocker using the -protectors option and save it to the USB drive on E: and then begin the encryption process. To find the commands with unapproved verbs, run the Import -Module command again with the Verbose parameter. For a list of approved verbs, type Get-Verb. Thanks. The volume needs to be prepared before BitLocker can be enabled. I found a tool that will do the preparation that I need.
How to use BitLocker Drive Encryption on Windows 10.
Bitlocker Encryption error Bitlocker setup could not find a target system drive. You may need to manually prepare your drive for Bitlocker We have a remote user that we discovered does not have bitlocker enabled. She does appear to have a partitioned logical drive(f) called HP_TOOLS. Our main concern is to bitlocker protect the C drive. Unlock BitLocker Drive Using PowerShell. Step 1: Search PowerShell in the taskbar and right-click it to choose Run as an administrator option. Step 2: Type the command: Unlock-BitLocker -MountPoint " (drive letter):" -Password (Read-Host "Enter Password" -AsSecureString) and press Enter button to run it.
See also:
Download X Men Origins Wolverine Game For Android
Download Install Disk Creator Mac
Embird Download Full

0 notes
Text
How to unlock bitlocker without password and recovery key
How to unlock bitlocker without password and recovery key
Are you locked out of Windows? Do you have no access to your encrypted drive? We can help you unlock and recover data from your Bitlocker encrypted drive. Here is the ultimate BitLocker encrypted drive without a password and recovery key. You will learn how to unlock BitLocker encrypted hard drive or SSD without a password and recovery key in windows 10. According to the report of Acsdata, in…
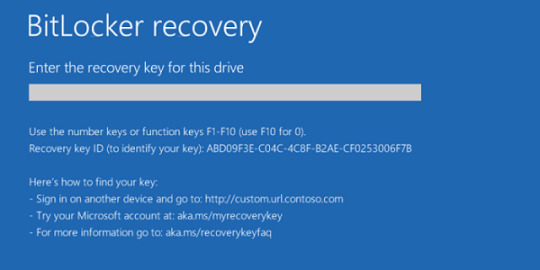
View On WordPress
#aka.ms/myrecoverykey#bitlocker download for windows 10#bitlocker download windows 10#bitlocker drive encryption#bitlocker drive encryption recovery key#bitlocker encrypted drive#bitlocker encryption#bitlocker enter the recovery key#bitlocker for windows 10#bitlocker get recovery key powershell#bitlocker recovery key#bitlocker recovery key bypass#bitlocker recovery key not working#bitlocker recovery key windows 10#bitlocker unlock without recovery key#bitlocker windows 10#bitlocker windows 10 download#bitlocker windows 10 recovery key#download bitlocker for windows 10#how to disable botlocker in windows 10#how to enable bitlocker in windows 10#how to find bitlocker recovery key#how to get bitlocker recovery key with key id#how to unlock botlocker#recovery key bitlocker#what is bitlocker#what is bitlocker windows 10#windows 10 bitlocker
0 notes
Text
How to Protect Computer From Viruses and Online Threats
The topmost priority is Security to every individual, and when it comes to cybersecurity, it becomes a serious matter of securing our data. Nowadays, there are various cyber threats or malicious viruses are active on the web. Then in this situation, the need for cyber Security appears quickly on our mind. In this case, you have to detect a particular cyber issue and remove it instantly to keep your data safe on the web.

Source:How to Protect Computer From Viruses and Online Threats
Here is how to protect and secure our system to form harmful viruses and threats.
Easy ways to Protect Our Data Safe
There are various ways to keep our system secure from online thefts and spyware, malware, and harmful viruses as well. They can steal our important data from our website that we use regularly. The methods include installing a genuine “Antivirus” program, applying a secure and undetectable passcode in all your websites, checking security settings and scan for harmful viruses and malware for protection.
Activating Automatic Updates
No browser is completely safe without having various programs for detecting malware and virus scans. There are various programs and software available that keep your data updated automatically and minimize your security risk. You have to turn ON the “Automatic Update” feature so that your system will get the Software or program updated on its own.
Note: It is recommended to turn automatic update features to “ON” for various security matters as the latest updates packed with features that remove various online viruses and minor issues.
Running Anti-Malware, Anti-Spyware and Antivirus Programs on your System
Most users tend to use multiple antivirus software on a particular device. It is not recommended as it may crash after some time. The best program for detecting viruses on your system is the “Windows Defender” tool. It’s free, built-in and works as a very effective tool for all the OS. It automatically updates your Software or programs with the help of the “Windows Update” utility tool.
If you wish to make your Windows Defender tool more powerful and effective, then you can use a second antivirus program to integrate with your OS.
Create Strong Passwords
To secure your online data from online threats, it is advised to make a secure password so that nobody can unlock it. There are various methods to apply encryption to your online browser’s accounts.
It is also advised to follow these steps:
Don’t use the same password for multiple online websites.
Don’t share your passcodes to anyone.
Use the “Password Manager” tool like “LastPass etc. to secure and make encryption to your account so that anyone can’t guess your password easily.
It is recommended to use various tools like “BitLocker,” “VeraCrypt,” “FileVault” for securing your site or data.
Careful About Software that You wish to Download
In case you wish to install a particular program or Software, then follow these steps:
Firstly, you have to check it properly before downloading it.
Then, you have to navigate to the official website of the particular program or Software and then read whole instructions before tapping the download tab.
After confirming that it is safe for your device or system, then you can download the particular program.
Note: Never download any program from supporting websites or any other malicious sites.
Lucia Mandela is a Microsoft Office expert and has been working in the technical industry since 2002. As a technical expert, Lucia has written technical blogs, manuals, white papers, and reviews for many websites such as office.com/setup.
0 notes
Photo

Some security advice from a workshop at our February 2017 meeting.
Passwords
If you use the same password everywhere, this is the number one thing you must fix and state surveillance is the least of your problems.
The no. 1 threat is companies holding your data and not securing it properly. Password databases are frequently leaked onto the internet. If the company is good, they've taken some measures to hide your actual password, but that's not always the case.
The last high profile incident happened a fortnight ago with a very security conscious company making a terrible mistake in their systems, which are used by OKCupid, for example. So anyone who uses the same password for OKCupid as they do elsewhere is at risk.
Don't remember your passwords – use a password manager:
Use tools like 1Password or LastPass to save and create passwords for you. You then only have to remember one long password to access your "vault".
2nd Factor Authentication:
Sites like Google, Twitter, Facebook, as well as the password managers above offer you the ability to use a "2nd factor", which is something you have on you as well as your password. This is normally your phone.
Don't completely mistrust corporations, or being a needle in a haystack can be a good thing
Anonymity amongst the big datasets of large corporations can be a useful way to operate. One reason is that it's not in Google's or Amazon's interest to give information to the US government due to EU privacy law. Governments then have to try and tap the entire input and output of those company's systems, and given most of it is cat videos on YouTube with the occasional Alec Baldwin playing Trump impression, well, good luck to them.
More importantly, they have the resources to secure data better than most, and have made big efforts to do so post-Snowdon, mainly due to EU/other international contracts they don't want to lose if it was found they were handing everything over to the US government without a fight.
Communications between Google equipment is secure (post-Snowden), so sending email messages between GMail accounts is much more preferable than emailing from RiseUp and Gmail and back again, as the government is definitely tapping what goes in and out of RiseUp, but is having a harder time doing that within Google's network.
The companies are also running their own campaigns against state surveillance.
However, use ProtonMail:
It's Swiss, open source, and has the thumbs up from security community.
Your computer
Keep it up to date:
Don't still be running Windows 7, and don't run old versions of OS X. These are basically dead in terms of security. Windows 10 Anniversary Update and OS X Yosemite are more secure than Linux. Yup, that's right.
Encrypt it:
Either use FileVault on Mac, or Bitlocker on Windows to encrypt your hard disk. This means if someone steals your laptop, they can't get at the contents without your password. The screen unlock was never secure.
Don't use it for sensitive information:
If you fear a state adversary is trying to get to your information, you should assume your laptop is already hacked. The truth is that laptops and desktops were not designed for security in mind, sooo....
Your phone
Use it:
Modern phone systems are designed much more heavily around security. iPhone remains the best, but even modern Android devices and Windows Phone are OK.
Keep it up to date:
Same rules follow as for normal computers. Your phone should be receiving regular updates every month. If it isn't, you can assume your phone is not secure. This means in practice sticking to Apple, Motorola, LG, OnePlus, FairPhone or Samsung for phones. You can use the cheaper brands as burners, but they quite often can't be trusted.
Use Signal:
Just use it.
Photos:
On an action, you may want to take photos and share them. They usually come with a load of metadata to help professional photographers, but which can also help police identify you.
Twitter and Instagram remove this data, so use these sites to share photos.
I think I've been hacked?
Try the Digital First Aid Kit, and failing that, contact someone at Access Now, or Zeynep Tufecki or Martin Shelton (below), by the securest means at your disposal.
Who to follow for more information
Amie Stepanovich (@astepanovich) & Estelle Massé (@estelMP) - Access Now, digital rights group
Zeynep Tufecki (@zeynep) - Harvard Berkman Klein Center sociologist with specialising on technology and protest with first hand experience from Turkey
Martin Shelton (@mshelton) - User research with press and "at-risk groups" at Google
The Grugq (@thegrugq) - Bangkok-based Independent Security Researcher
Delete everything
Don't keep messages, documents or plans longer than you need them. If you can use the disappearing messages feature of Signal, do so. (BTW, SnapChat is not an alternative.)
Glossary
OPSEC
Operational Security. The process to identify critical information that has to be protected, and the processes for carrying out that protection.
SIGINT / COMINT
Signals/Communications Intelligence. What most security researchers talk about when talking about online security. Sounds all military and cool, innit.
HUMINT
Human Intelligence. 95% of anyone's problems in activist communities is trust. Technology is comparatively easy. Don't get too hung up on state surveillance when there are more likely vectors for infiltration. To quote The Grugq:
SIGINT is really the sort of intelligence collection technique that needs to lose its prominence in the pantheon of intelligence gods. It is very easy for a serious adversary to defeat: basic tradecraft from the days of Allen Dulles will work (leave the phone behind, have the meeting while taking a walk). This tradecraft technique is described by Dulles, in 50 year old KGB manuals, and by Hizbollah operatives last year (2012). The only way to catch people who are capable of any sort of OPSEC / tradecraft is via: a) Mistakes that they make (very easy for amateurs to make mistakes), or b) Via HUMINT. Spies catch spies, as the saying goes. It might be updated to, spies catch clandestine operatives.
Double down on HUMINT and scale back SIGINT. SIGINT can be evaded, but HUMINT, essentially exploiting trust relationships, will always bite you in the ass.
Just use Qubes / Blockchain / GPG2 / Homophonic Encryption
Really unhelpful advice that's possibly technically correct, but way to onerous in reality, given by Twitter techbros who want to sound clever but don't have anything useful to offer. Ignore.
Open source
Sounds bad, right? Not really. All our most secure systems are based on shared assumptions about mathematics. Open source means the code for these systems are shared, and everyone understands how secure they are.
WhatsApp is insecure
Guardian journalists putting lives at risk through misinformation. Ignore.
3 notes
·
View notes
Video
youtube
How to Access BitLocker USB on a Mac without Password? Take advantage of iSunshare BitLocker Genius to unlock and access the drive with the recovery key.
0 notes
Text
Multi-booting Windows 10 Environments with Bitlocker Enabled
The goal here is to get multiple installations of Windows 10 on separate encrypted partitions on a single physical drive and we want to use the stock Windows bootloader and Bitlocker, avoiding any third-party solutions because I'm a fan of keeping things as simple as possible. I'd say the end result accomplishes that, but figuring out how to get to that point was a pain in the ass.
It turns out that combining multi-booting and Bitlocker is a bit more complicated to set up - and to maintain - than you'd think. If you hunt around online, almost all of the information you're going to find on this topic involves dual-booting Windows and some flavor of Linux or two different versions of Windows (for some reason, Windows 10 and Windows 7 is a really popular combination) and that requires delving into the BIOS to mess with UEFI settings, which I've dealt with in the past. Add to this that the standard way of going about using Bitlocker system drive encryption will create quite a mess for you.
First, prep your installation media: grab Rufus, a USB drive that's at least 4GB (I recommend the Kingston DTSE9G2), and a Windows 10 ISO. I'm also going to assume you've done a Windows 10 installation before so that I can skip some of the details.
Installation
Boot into the Windows Installer and partition the drive into as many partitions as OS installations that you intend to have.
Continue to install the first Windows 10 instance.
Boot into it and complete the setup process.
Reboot into the Windows Installer and install your second instance on another partition.
Boot into that instance and complete the setup process.
Repeat until you have however many installations you partitioned for.
Bitlocker Configuration
This is where things get a little complicated. Do not just boot into each of the installs and take the usual step of enabling system drive encryption. If you do that, you will find that the system will constantly prompt for the 48 digit Bitlocker recovery keys and your life will be hell. Instead, use the following procedure:
Boot into your first Windows 10 install (we'll call this the "primary" installation)
Enable Bitlocker system drive encryption but do not enable Bitlocker on any other partitions.
For the love of god back up the ID and the recovery key because, as you'll find out in a bit, you will actually need it.
Reboot and ensure that you can boot into installation A without an issue.
Now enable fixed-drive Bitlocker on each of the alternate partitions, using a different password for each of them.
Again, back up the IDs and recovery keys. Jesus christ, just do it. Trust me.
Reboot and attempt to boot into one of the alternate installations from the bootloader. What should happen at this point, is that instead of loading the selected Windows installation, the system will reboot and prompt you for the Bitlocker key for that particular partition/install. Enter your password and, if it works, you're all set. From within any of the installations, you should still see the other partitions, but they should be locked and inaccessible unless you unlock them with their respective passwords. You now have multiple encrypted installs of Windows 10 without having to use any third-party tools.
Why Those Recovery Keys Matter
So why the insistence on backing up the recovery keys? Because there are seemingly benign things you probably don't normally even pay attention to that will trigger Bitlocker's recovery mode. Some things that I have found that can trigger it:
Updating device drivers
Major OS updates (e.g. the "Creator's Update")
Updating the UEFI/BIOS
Modifying or clearing the TPM settings
Group Policy changes
And probably other things. In every case, you'll have no warning. You'll install an update or apply a setting and reboot and Bitlocker will prompt you for that recovery key. It won't happen often (thank god), but it will happen. And if you don't have the appropriate recovery key for whatever partition triggered the recovery (which is why I told you to keep track of both the ID and the key), everything on that partition will be unrecoverable. Period. End of story.
Further Isolation
This is optional, but for an added layer of isolation, you can remove the drive letters of the other partitions in each of your Windows installations using the Disk Management interface. Now, those partitions will no longer be visible or accessible from within that installation.
0 notes
Video
youtube
Liked on YouTube: How To Unlock Bitlocker Without Password And Recovery Key | Remove Bitlocker From Computer Drive https://www.youtube.com/watch?v=qurKnu1y51w
0 notes