#IP Address (Internet Protocol Address)
Explore tagged Tumblr posts
Note
Can creators/aspiring creators join the UnderNet Prtocol?
hmm... that's a good question!
I'm going to say that if creators find the code for it, they can observe, but they cannot directly interact with it. let's say it's... a compatibility issue...? (we're too four dimensional? haha i don't know)
I think it's best if it stays as an in-multiverse thing, if that makes sense. (also if Admin knew that creators could use it, he'd lose his mind and start annoying each one hahaha)
edit: this also means that creators can't look at/order through UnderEats... i'm sorry 😔 (but you can get your ocs to get some for you)
#word of imi#imi talks#chaos-ace#ask#undernet protocol#in my original drafts i was going to lock creators out because they didn't have a UP (undernet protocol) address#like an IP (internet protocol) address. (....this feels like a pun)#i'm not sure if i want that to be canon or not... i feel like there's a few holes in that logic#so let's just go with 'the real world and UP aren't compatible'#thank you for the ask :OOO sorry if this is disappointing#i like the idea of creators interacting with their AUs#but i don't like the idea of them interacting freely with ALL AUs... if that makes sense?#i rambled again#undereats#for the edit#if i'm the creator of undereats... do i bypass the 'creators cant interact' rule?#can i order from my own thing??? the world will never know...#undernet lore#undernet protocol lore
10 notes
·
View notes
Text
How to check the ip address of the salesforce org?
You must have seen a situation in the salesforce ecosystem where you need to integrate with the external application and that system has security concern over who can access their application publically even though they are authenticated, so in that case they would ask for the IP(Internet Protocol) Address. 1. Salesforce Trust Center: This is the most official and reliable way to obtain your…
View On WordPress
#how to find the ip address#how to find the ip address of salesforce org#internet protocol#ip address#salesforce ip address#salesforce org ip address
0 notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
189 notes
·
View notes
Text
Another Internet Whitepaper
I'm just gonna get into there is no way to preface this.
1) content should be hosted in their own countries for which they are meant.
2) therefore the website should split into Nation->Sub-nation sections. So things for Michigan would be closer to those in Michigan. With U.S.->Michigan.
--"independent" Nations are just gonna have to deal with being lumped together into a united region. It's simply physics.
--country wide servers and clouds, and worldwide services will still be available; but we need to develop protocols to make it easier to distribute data and declutter the internet-cloud.
3) a separate Intranet for official use and security will need to be developed alongside this while also being completely disconnected from the worldwideweb.
4) Splits;
IP Addresses redesign;
[Country/Region]:[State/Province]:[individual]
[Individual] will need to be controlled by local The Internet Assigned Numbers Authority (IANA) branches; likely to be reassigned to DMVs and SoSs.
5) Separate protocols For;
Streaming Services
Social Media Services
Bidirectional Interactions (like games and Virtual Machines)
Pornography needs to be completely identifiable by textual Web address.
5) you local region will be defaulted, but can be changed by the browser and not be hard-wired in.
Not indicating a region will automatically default to the local internet.
So typing in FBI.GOV in the U.S. will lead to the FBI website, and if you type it in the UK it'll lead to Mi:5 or something.
6) Social Media protocols will have to be integrated with the E-Mail SMTP protocols. Which will encourage a more decentralized internet. This will *also* have to find a way to work with phone text messages.
7) Cable TV and Streaming services will have to use the same protocols.
8) Because there's phone integration here; a phone number may have to be closer to a social security number going forward. Which will both be bad for animosity, but allow for people to not need login information.
-- This will technically also need to apply to your House; which will have to have an assigned street address.
9) all of these need to be obfuscated to casual observers.
10) this will deprecate our phone companies and require them to work with cable TV and internet companies in order to create more equitable protocols.
11) the current IP address and Domain Registry systems need to be deprecated; as it does not suit its original purpose.
[.xxx] will be assigned for all "adult" materials and be required for ALL "adult materials" posted online.
[.app] will be assigned for appstores.
[.store] for marketplaces like Amazon, eBay, and whatever else.
[.bank] will be for banking and credit purposes
[.social] will be for social media
[.stream] will be for streaming materials,
[.np] for non-profit use only.
[.donation] for donation collections and Kickstarter like services.
[.pay] for payment services like PayPal
Non "adult materials" can be streamed through other "front ends" .
13) These human readable extensions will be simplified on the backend to reduce the total data envelope size.
14) single digit ip-adresses will have to be regulated for use for high-capacity uses. These will need to be "extended" protocols that different services can use.
This will help even out everybody's data envelopes. This will have to be part of a cloud service that can be used by anybody that needs it. With certain restrictions that are deemed necessary by local and federal governments and international treaty reasons.
15) limits on how algorithms and "bots" can ping anything at one time need to be addressed or regulated.
This will be a massive undertaking with the cooperation of all the other governments around the world.
And will be a very lucrative endeavor at the end of it all.
This is just an outline to describe the form the future internet should take and can be changed or modified as required; especially for things I cannot see.
The current corporations will be expected to develop a plan of actions in tandem with current regulatory authorities; failure to do so will create a need for an ultimatum, which we all wish to avoid.
We're also going to need to find ways to encourage competition in these sectors so that they can be upgraded and modified as needed by local areas instead of waiting on these companies to bother with it.
13 notes
·
View notes
Text
Considering Perplexity’s bold ambition and the investment it’s taken from Jeff Bezos’ family fund, Nvidia, and famed investor Balaji Srinivasan, among others, it’s surprisingly unclear what the AI search startup actually is.
Earlier this year, speaking to WIRED, Aravind Srinivas, Perplexity’s CEO, described his product—a chatbot that gives natural-language answers to prompts and can, the company says, access the internet in real time—as an “answer engine.” A few weeks later, shortly before a funding round valuing the company at a billion dollars was announced, he told Forbes, “It’s almost like Wikipedia and ChatGPT had a kid.” More recently, after Forbes accused Perplexity of plagiarizing its content, Srinivas told the AP it was a mere “aggregator of information.”
The Perplexity chatbot itself is more specific. Prompted to describe what Perplexity is, it provides text that reads, “Perplexity AI is an AI-powered search engine that combines features of traditional search engines and chatbots. It provides concise, real-time answers to user queries by pulling information from recent articles and indexing the web daily.”
A WIRED analysis and one carried out by developer Robb Knight suggest that Perplexity is able to achieve this partly through apparently ignoring a widely accepted web standard known as the Robots Exclusion Protocol to surreptitiously scrape areas of websites that operators do not want accessed by bots, despite claiming that it won’t. WIRED observed a machine tied to Perplexity—more specifically, one on an Amazon server and almost certainly operated by Perplexity—doing this on WIRED.com and across other Condé Nast publications.
The WIRED analysis also demonstrates that, despite claims that Perplexity’s tools provide “instant, reliable answers to any question with complete sources and citations included,” doing away with the need to “click on different links,” its chatbot, which is capable of accurately summarizing journalistic work with appropriate credit, is also prone to bullshitting, in the technical sense of the word.
WIRED provided the Perplexity chatbot with the headlines of dozens of articles published on our website this year, as well as prompts about the subjects of WIRED reporting. The results showed the chatbot at times closely paraphrasing WIRED stories, and at times summarizing stories inaccurately and with minimal attribution. In one case, the text it generated falsely claimed that WIRED had reported that a specific police officer in California had committed a crime. (The AP similarly identified an instance of the chatbot attributing fake quotes to real people.) Despite its apparent access to original WIRED reporting and its site hosting original WIRED art, though, none of the IP addresses publicly listed by the company left any identifiable trace in our server logs, raising the question of how exactly Perplexity’s system works.
Until earlier this week, Perplexity published in its documentation a link to a list of the IP addresses its crawlers use—an apparent effort to be transparent. However, in some cases, as both WIRED and Knight were able to demonstrate, it appears to be accessing and scraping websites from which coders have attempted to block its crawler, called Perplexity Bot, using at least one unpublicized IP address. The company has since removed references to its public IP pool from its documentation.
18 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes
Note
back in the day networking software was what is defined as monolithic: it was all one big blanket of code that handled everything from the data to send to what headers and information add to it before sending it to the Cables(tm)
problem is, get one problem somewhere, you have to unravel all of it to find where the problem is, and the network stops netting and/or working
enter, drumroll please,
iso/osi stacks
the guys over at iso (the organization) came up with this nifty little trick to slice up the Big into many Smalls: 7 layers (or abstraction layers if you are a big nerd)
application: here are the high-end protocols! like http, ftp (file transfer protocol, what were you thinking?) and the dreaded simple mail transfer protocol which i can say after studying it, it is not simple
presentation: applications dont speak internet, so presentation handles (de)codification, (de)encryption and (de)compression however the Protocols see fit
session: most protocols don't have functions or buffers to remember who sent what so session handles keeping connections alive with sessions: little tin cans with a string so the two members of the communication remember each other
transport: this guy is responsible for whether you want to use tcp or udp as a transport protocol (tcp is slower and has data validation for the recipient, udp is faster but fails more often) and chopping up data in tidbits to actually be able to wring them around the net
network: handles ip addresses, routing and telling the other guy everything is okay because that fuckass udp lost me two whole packet fragments
data-link: the oddball of the bunch because it has a dash in its name. and also because it's two sublayers under a trenchcoat
physical: takes whatever the upper layers gobbled up and zip-zaps the cable to send electricity
basically what happens is application concocts the data, hands it to presentatiom and one it is done, it hands it down to session, so on and so forth until physical sends it to the recipient who is going to do the opposite! physical takes the data, gives it to data-link, d-l chews it up a bit, gives it to network until application gets the oh-so-coveted picture of a cat the sender was sending
it's not over yet as those cheeky bastards managed to wedge the stack open with a lego brick remover and stick a little guy called secure sockets layer in to secure the sockets (woah.). he's dead and now we have transport layer security which is that, but better
whevernevr you see an s at the end of a protocol's name, it means one of these two motherfuckers meddled with your data to make it secure and unreadable to the big mean hackers typing dir /s in green letters in the command prompt
Huh
5 notes
·
View notes
Text
World Wide Web
The internet was created to give the US military a communication system that could survive a nuclear war. The idea was to have an interconnected network of computers without hardline routing. Instead it was handled by variable heuristics. This means that even if half of the nodes were destroyed, the system could find a way to route along different paths and still, eventually, reach it's destination.
It was a brilliant form of asynchronous communication.
Academia had created it, and quickly found great use in networked communication and remote data processing.
And now we use it to view porn. So, what happened?
The World Wide Web. Before the WWW, you had to know the IP address of your friend's computer, be given permission, and then log into his bulletin board service.
The World Wide Web was a system of protocols that created a public internet front. ANY person could find it through HyperText Transfer Protocol, use a public log-in, and access the web site. The HTTP was designed to be crawled by search engines, allowing them to effectively index the entirety of the public-facing internet.
One of the first real search engines was call WebCrawler, because it - crawled - the HTTP of the WWW.
They would load page, then open and index every - single - hyperlink contained in the document, storing and indexing meta tags.
We also ended up with MetaCrawler, that would index multiple other search engines, allowing it to provide a far more comprehensive system of results.
Nowadays, most search engines are meta crawlers, and because of the prominence of Google in searching, Google results are over weighted, meaning that there is almost no way to escape the dogmatism of Google's biased search algorithms.
And the reason we use it for porn is that this was the first viable online business plan.
6 notes
·
View notes
Text
About the Toskarin Archive
The Toskarin Archive, a 501(c)(3) non-profit, is building a digital library of Toskarinlikes and Toskarinlites in digital form. Like a paper library, we provide free access to researchers, historians, scholars, people with print disabilities, and the general public. Our mission is to provide Universal Access to All Toskarin Knowledge.
We began in 2024 by listing every known Toskarinlike, a form of art that was just beginning to explode in use. Like newspapers, content published on Tumblr was ephemeral - but unlike newspapers, no one was saving it. Today we have over 3 years of Toskarin history accessible through our blog and we work with several other partners through our Tumblr messaging program to identify important Toskarinlike blogs.
Anyone with a Tumblr account can send new Toskarinlikes to the Toskarin Archive. We work with several partners globally to save copies of their work into special collections.
Because we are a Tumblr blog, we only pay attention to other Tumblr blogs. Not everyone has access to the vagaries of Tumblr's search feature, so to provide universal access we need to provide consolidated links to Tumblr blogs. We began a program to digitize this process in 2024 and today we've scanned at least one Toskarinlike in at least one location around the world. Toskarinlikes created in or prior to 2021 are available for viewing, and dozens of them can be viewed through our Toskarinlike Database pinned post. One of the Toskarin Archive's missions is to serve people who have difficulty interacting with physical books, so all of our Tumblr links are available to people with print disabilities.
The Toskarin Archive serves several people each day and is one of the top 500 million Tumblr blogs in the world. A single copy of the Toskarin Archive library collection occupies 2+ Kilobytes of server space (and we store at least 1 copy of everything). We are funded through the generous free use of Tumblr. As with most libraries we value the privacy of our patrons, so we avoid keeping the IP (Internet Protocol) addresses of our readers and offer our site in https (secure) protocol.
You can find information about our projects on our blog (including important Toskarinlikes), contact us, and follow us on Tumblr. Welcome to the library!
11 notes
·
View notes
Text
Unlock Internet Freedom and Secure Your Privacy with Gulf VPN
Searching and operating within the internet in the gulf countries has its own set of challenges. VPN is restricted, access to social networks is limited and websites are often inaccessible during certain hours. Using a VPN is not a luxury but a necessity, particularly in regions like the UAE, Qatar, and Saudi Arabia.
A VPN, Virtual private Network, is a service that establishes a secure connection between you and the whole internet so that your activities and details of your location cannot be seen. A VPN works by encrypting your traffic and hiding your IP address which makes it easier to advance past censorship and allow for the freedom to access content without compromising your privacy. Here, you’ll get a brief understanding of what a Gulf VPN UAE is, how it functions, and why it is crucial for you in the first place to opt for the most suitable service.
Why Do You Need a Gulf VPN?
Many countries of the Gulf region remain among the leaders in restrictive internet policies, many recognizable sites and applications are blocked here. From VOIP services including WhatsApp, Skype to widely used streaming services such as Netflix, BBC iPlayer; many services block or limit access due to government restrictions or geo-restriction practices.
This is where having a VPN becomes absolutely essential. A VPN could be used by linking to a server in another country; this makes it possible to unlock content since the VPN provides an individual an entry point into the internet that is restricted in the Gulf.
Reasons to use a Gulf VPN include:
Avoiding Authority RestrictionsGulf countries are quite famous for banning and restricting sites and applications that are in resistance to set laws and regulations. This limits you from getting to the sites because your connection is being encrypted and the traffic is routed through other servers in some other region of the world other than the prohibited region.
Increasing Privacy and SecurityThere is always a perception of privacy concern and this exists more so in the gulf because the ISPs and the governments are vigilant. If you use VPN to connect to the internet, your data is encrypted; thus your Internet Service Provider cannot interfere and monitor what you are doing.
Access to Streaming ServicesNetflix, Hulu, Amazon prime videos these streaming channels are also limited due to geo-restrictions. A Gulf VPN 2024 allows you access servers of other areas and therefore you can watch uninterrupted favorite shows and movies.
Safe Browsing on Public Wi-Fi
It is unsafe to use Wi-Fi networks that others connect to, particularly when in a country that has seen an increase in the level of cybercrime. A VPN effectively works to guarantee that your information is not vulnerable mostly when using a wrong public network by encoding your connection so that the hackers cannot easily access it.
How Gulf VPNs Protect Your Privacy
One of the primary benefits of a VPN is data security that a user receives when he or she connects to the server. You lack privacy when browsing the internet because your data flows unencrypted, and anyone can access it using your IP address.
Using a Gulf VPN 2024 means all your communication and internet usage are hidden behind a protective layer, and your actual IP address is swapped with that of the VPN server. This makes it impossible for the web site, hackers, or even any other government agency to track your activities with any chance. Moreover, the best VPNs provide things like server cloaking and it becomes quite challenging to realize that you are using a VPN.
Key Features
Selecting the right Gulf VPN may not be easier as there are lots of service providers out there. Here are the key features you should prioritize to ensure you get the best protection and access.
1. Robust Encryption and Protocols
Check that the connection is as secure as possible and you should look for one with AES-256 encryption. Also, check for the connection protocol standard such as OpenVPN or WireGuard since they are fast and secure..
2. Server Locations
Accessibility to multiple centers and points helps to overcome the problem of geo-blocking. As with the server locations, the more available servers a VPN has, the higher are the chances of getting a server with a fast connection. Choose VPN providers with the servers located in Europe or North America or Asia to have the most opportunities.
3. No-Logs Policy
When it comes to VPN, privacy is all that matters. Check whether your provider does not monitor or store any information about your online activity. This is particularly so given that most of the GCC states technically spy on their citizens.
4. Fast and Stable Connections
A VPN should work for making your internet experience better rather than making it worse by slowing down your connection. Close on the high-speed servers and choose VPNs that can deliver good performance when it comes to streaming, gaming, as well as torrenting.
5. Bypassing Geo-Restrictions:
However, most VPNs are unable to bypass streaming services such as Netflix and Hulu. Ensure you choose a VPN that has been tried and shown to overcome any level of geo-blocking.
Gulf VPN for Streaming
One of the biggest draws of using a Gulf VPN UAE is the ability to access geo-restricted content. Regions get blackouts to allow streaming services to function by adhering to their regional licensing restrictions on movies, TV shows, channels, and more. For example, the movies and TV shows that are watched in the UAE could be different from the ones that are consumed in the US.
A VPN enables you to establish connection with a server in another country and makes it seem like you are accessing the internet from such a country. This gives you complete control to the Netflix, amazon prime, Disney Plus and other VPN for streaming services platform libraries around the world. For anyone who wants to stream a show that is restricted in their current location whether an expatriate wanting to stream shows from his home country or a local in a region with restrictions, a VPN changes that.
VPNs and Online Gaming:
If you are a gamer residing in the Gulf then you will find a VPN to enhance your gaming experience. Games also have restrictions in servers and beta access meaning you can’t play with your friends who are in a different region. Moreover, through using a VPN, it will be easier for you to avoid tyra DDoS attack besides ensuring your data is not relayed to the other players.
A VPN also minimizes ping and latency issues by linking the client to a closer server to where the game’s server is hosted. This makes it possible to connect to cross border gaming servers and be able to play with friends all over the world.
To sum up
If you live in or are planning a trip to the Gulf region, prepare for limited internet access, geo-blocking, and privacy issues. A Gulf VPN 2024 is the answer to all these questions, a tool that gives you freedom, security and anonymity every time you connect to the Internet.
A VPN protects your identity as well as your IP address so that the intended material is unrestricted and your information is safeguarded from any malicious third party endeavor, be it streaming videos, playing games online or browsing the internet. To ensure the best experience, one should look into strong encryption, fast servers, and no logging policy while selecting a VPN.
Having the best Gulf VPN will enable you to get the best out of the internet without any restriction or anything to bother you.
3 notes
·
View notes
Text
Names & Numbers: How Data Finds its Destination on the Net
As explained before, the Internet is the global network of networks. And with billions of computers and devices connected to the Internet, how does data know where to go when it is sent?
When the foundations of the Internet were being laid in the early 1970's, Vint Cerf and Bob Kahn developed the first internetworking protocol. A protocol is a set of standards and rules that are agreed upon for all future technology to follow. The protocols that followed as the Internet grew, allowed for the massive global network we find today.
One of those protocols, the Internet Protocol (IP), determines how devices are located on networks as well as the structure of addresses for data sent, much similar to how postal services follow a set structure for home addresses (a protocol). IP addresses currently follow the IPv4 (version 4) or IPv6 (version 6) standards.
IPv4 is a set of 32 numbers (32 bits) separated into 4 parts with 8-bits (a byte) in each part and written in dot-decimal notation. Here's an example of an IPv4 address (111.24.221.18). The first two bytes represent the country or region of the address. The third byte represents the subnetwork and the final byte the device on that subnetwork. By using 32 bits, IPv4 was capable of over 4 billion internet addresses. However, this was not enough.
Enter IPv6, a 128-bit addressing protocol. IPv6 consist of a set of eight hexadecimal strings, each 16-bits long. This increases the total amount of possible internet addresses to over 340 undecillion (10^36). Plenty to go around.
You may be wondering, but if I type in a website domain into my browser bar, how to I get to that website without typing in the specific IP address? Now it is time to introduce DNS or the Domain Naming System.
You know how when you want to save someone's phone number into your own smartphone, you type in a name and save it to your contacts. Then when you want to call or text that person, you just click on their name and soon you are connected. DNS works the exact same way but is better in another way. DNS works like that contact list in your phone.
There are a bunch of DNS servers that hold the addresses and domain names of all the websites in existence. When you type in the name of a website in your browser, your request is sent to a DNS server who then returns that IP address to your system so that you may set up a connection with the website server. If the particular DNS server does not know the address, it asks the vast network of other DNS servers if they know the address. Once it gets the correct address, the DNS server you originally contacted, will save that address for your convenience. Nifty huh?
However, DNS does have a downside. Because it an open and public protocol, it is possible for criminal elements to disrupt or manipulate the routing of the DNS server. An unethical hacker could perform a DNS spoof, which could force traffic meant for a legitimate website to be rerouted to a malicious website or phishing site.
2 notes
·
View notes
Text
Speed of Words
Hey, how fast can you get a message to the nearest major settlement you don’t live in?
I bring this up because I’m about to talk about fantasy worldbuilding, okay? We’re about to get into the cool dork stuff in a minute, but before we get going we’re going to wind up talking about a bunch of real world communication stuff that you may not have examined unless you’re like me and hang out with cool academics talking about it.
First of all, when you think about the ramifications of communication speed in your world, you need to understand that communication technology includes a lot of things you may not even be thinking about. There are things like population density and language and number systems and – like it’s not just this linear flow that goes Town Crier -> Letter -> Telegram, Maybe -> Phone -> The Internet.
You and I, in the real world, are used to a lot of options for communication and used to them having a lot of flexibility. They’re all the byproduct of infrastructure and technology, but some of the technology that drives them isn’t what you or I would consider ‘high tech.’ Someone had to invent address and postal delivery systems, but that’s a system you can do with even the most modest kind of technology that can record information. You don’t even need a written language for a postal system, it’s just really good for scaling up. Scaling up is one of the big tricks here, because if you have to send a message and you can only say it aloud, then you’re dealing with a message that a person can memorise and share. A writing system lets you really densely stash information on transferrable objects that you can transport, which means one aspect for That is, you need to care about volume.
That’s not even taking into account the great interconnected communication matrix you and I are interfacing with now. I wrote this weeks ago and you’re reading it now and we are interfacing as a direct result of a type of communication system that runs through the oceans deep enough that only sharks can harm it. That’s pretty swanky as communication technology works, but it’s not ubiquitous and the technology that makes it up ranges from the actual physical objects and also the actual protocols, the rules that make it work. This is an impressive technology, but it doesn’t need the cables and electronics and all the things you’re familiar with as ‘the internet’ to work. Famously, you can run the IP technology over Carrier Pigeons. This is important because that technology is about ensuring reliability.
Okay, so sending a message to the nearest other settlement. In my case, that can be complicated by the question of ‘what’s the next place?’ I live in a suburb. It’s connected to another suburb that for legal reasons is a different place based on an arcane set of rules about where post offices got built. The next place over for me is a place that I can comfortably walk to. For me to take a message there, I can walk a little distance and bam, there I go, I’ve got a message to the nearby settlement. But you might live in a place that’s named after some dude and a hill or creek or bunker, and therefore the nearest place to you involves travelling to a gas station that is at least an hour’s walk away, and even that only counts as a settlement technically. There’s a concern there that’s about distance.
Okay, so speed of communication relates to the space, and it relates to the technologies for communication. Know what else is important? Precision of communication. How reliable can the information exchanged be? This is one of those things that ties into more language technology. A number system, for example, can allow for very precise communication of sorts, but if you remember your history stories about when English adopted Arabic numerals, Roman Numerals were a number system that had precision, but it was hard to consistently communicate or relate to. Mistakes got made because the number system was bad. This is also why Australia decimalised our currency, because the previous system, while consistent and precise, was hard to interact with in a way that meant people made mistakes and money got lost in tracking.
Alright, there, that’s our basic premises. Speed of communication relates to volume, reliability, distance and precision. And they’re not going to be equally distributed.
Now, for most worldbuilding, you can look to comparable examples for things, but you might find that transforms things away from ‘normal’ for you. If you’re a stickler for realistic representation of distance, for example, and your setting is something like, say, Napoleonic Europe, you might not like the way that a space like America gets one letter a year from the other side of the world. And that’s okay, we’re used to a lot of really messed up speeds for communication. Instant communication is pretty common nowadays…
But there’s also a whole bunch of ways that this technology can be tuned. You know that there was a series of mechanical semaphor signals across Europe? A culture could use bonfires and long-distance viewing techniques to do regular communication. A hilly nation could have a long-distance whistling technique for regular transmission of messages with something like a bullroarer, for example.
Once you involve magic things get extra complicated.
In traditional D&D, there’s a spell called Sending, which depending on edition allows for long-distance short message communication at an instant speed. Give that technology a reason to exist and you’ll wind up with businesses using it to do sendings regularly. If there’s any reason to exist – like, say, countries that do trade, or have reasons to care about what’s going on with each other’s military movements – then a sending network seems to be pretty much mandatory? Really early? Every day, standard messages, with codebooks of information to maximise the transmission? Like these are the things a state can do. Instant communication transforms things – when you can know what’s coming before it arrives and you don’t get surprised, you can start doing logistical planning for things like military and trade.
In a setting like Avatar: The Last Airbender, earthbenders kind of leapfrog the technological need for things like metal foundries and movable type; a bender can just make the plates for printing. They don’t have to last a long time, they just have to have reliable and predictable practice. This means that you can have printable, high-volume forms of communication, like books and other forms of disposable transmission. That’s not even accounting for the way that electricity such as lightning benders can wield could be used for telegraph style communication if anyone wants to make the infrastructure.
And the thing is this can cut both ways. A setting like Mass Effect is one where you have all the modern day technological instant communication and then a bunch more which was also really stupid and worse – like, texting is one of the most efficient ways to transmit information, but to be part of its game interface, Mass Effect instead makes everyone use audio logs so they can be broadcasted while you’re doing other things. See also Bioshock and System Shock, which again, turn to everyone talking into tape machines, and if enough people do that as general process, even though it’s a terrible way to do things like shop for things, then everyone’s going to do it.
What’s more, this isn’t all equally distributed. A community of grassland wanderers can be ‘next door’ comparatively speaking to a city full of people sending magical messages every day. One of those groups isn’t going to be as interconnected with other people over long distance but also, they’re probably not going to be vulnerable on that vector for things like misinformation or logistical failure. If you don’t care about the Suez Canal, you don’t care that Big Boat Got Stuck. Which means communication speed, the convenience and access to it creates new entanglements.
Consider then the list:
Volume
Reliability
Distance
Precision
Infrastructure
Entanglements
Each of these ideas presents questions that you can then examine in terms of communication speed, and what they do for your world.
Check it out on PRESS.exe to see it with images and links!
7 notes
·
View notes
Note
Hey, Klint! Welcome to the Internet. I have two questions for you, if that's alright?
1. Do you have any silly nicknames? I've seen your brother go by ziekkyboy.
2. I am DYING to know everything about how you hooked yourself up to the Internet from the afterlife. Can you please give me an explanation with as much technical details as possible? 🙏 I want every juicy little bit!
Miss Sara Nerdnag-
I am Lord Klint van Zieks, Crown Prosecutor of London in service to Her Royal Majesty the Queen. I expect you to know the correct form of address. There is no need to speak of what form of address the little... winged creature, or whatever it is, seems to think is acceptable.
As for the technology, now that I am more than happy to elaborate upon! London - and most of the British Empire - primarily has its communication facilitated fastest by telegraphy, specifically needle telegraphy. I trust you're already familiar with how it works. Tumblr itself is being managed out of one of the telegraphy companies, although I'm quite impressed that they were able to get connectivity in and out of Japan. I understand that they are using submarine cables, copper and electricity wrapped in rubber and latex.
The new Ministers of Foreign Affairs, it seems, have been busy. From what I understand, while telegraphy has been mostly handled by the various postal services, internet - and by extension, Tumblr - is a different matter altogether. The postal service is simple: you enclose who you are, your address, your message, the intended recipient, and their address into an envelope or telegram, and it makes its way to whom it is decided.
The internet, however, is much more complicated. Not only is there far more information that needs to be gathered and transmitted, it must be distributed in a much more widespread manner. What time you sent the message, what time the message is seen, to whom you wish it to be seen by, what your message is, your account information, and all sorts of other information.
This information, once enclosed in such a way that it is not intercepted and modified, must make its way back to the host network - in this case Tumblr - and redistributed to all others on the network, in a timely fashion. What, then, if your location changes? A message for Lady Mikotoba should reach her if she is in Japan or in England. It instead does not locate to her physical address, but to the virtual location of her Tumblr account.
Even so, it must be more complicated than that! It is not a matter of delivering messages in a timely fashion: any message I would send would not reach the recipient as soon as possible, but instead reaches them when they open Tumblr and ask to see what has been posted and sent to them in their absence.
Tumblr then must take all the information they have received, find out what of that information must be given to the user in question, and return it without anything being modified. How, then, can it be sure that it is you speaking to me, and not someone only claiming to be you? At a post office, they might get to know your face, and the faces of those you allow to speak in your stead.
It is my understanding that currently, we are using a protocol known as IPv4, to connect. So long as I am using the same IP address and the same account credentials, it can be trusted that I am myself. My own IP address, when I query my network credentials, is 192.168.10.5. I should not share my account credentials, obviously, but that IP address is the equivalent of my physical home address, only telling you as much as where I live.
So when my query for information reaches Tumblr, they know to send me the posts and messages and questions meant for me.
But I suppose that wasn't quite what you were asking. You asked how I might myself gain access to the internet, and to Tumblr, even though I am a ghost and have been deceased for a decade.
It was actually through the genius of several people, a very odd creature I had to explain to Balmung is off-limits to hunting, and the determination of the dead to speak to the living. While here in the West, the existence of the dead being in our own way sapient and sentient is a hotly debated topic, our good friends in the Far East have already settled this matter.
In fact, it was Detective Asogi who brought to me this information: he told tale once of a clan known as the Ayasato, shrine maidens turned spirit mediums and channelers, able to speak to the dead and bridge the gap of the veil. So, from there, it must be reasoned that should someone who is dead and someone who is alive wish greatly to speak with each other, it should be no more complicated than trying to speak to someone through a thick wall, with only a minuscule hole that transmits light but not sound.
If one side can reach a cable and push it through, they must indeed trust that the other side will reach back and pull it through. They must then trust that the other side will do their part, and they will both work to connect an agreed-upon device to both ends, and only pray that it might work.
The one who pens under the name of John Wilson should take most of the credit: all that was needed was someone soon to die, who understood enough of the device and its installation to recreate it on the other side of the veil, and connect it properly. If both sides configured the device correctly, it would be able to transmit and receive information, exactly like a needle telegraph from across the sea.
A person soon to die was easily found, if admittedly because of circumstances and factors I would rather wish not be the case. A man who escaped justice, already condemned to die at the hands of the Reaper, agreed that should he die, he would do what he could to recreate the device - a router, so named because it routes messages - on this side of the veil.
Fortunately for that particular man, we the dead are perfectly capable of taking notes on blueprints, and by the time the Reaper had his little joke, most of the router was already complete. What we needed, the reason why we couldn't fully configure our end alone, was a means of actually passing through the veil, transmitting messages from one router to another.
The man died holding the cable, and when he appeared to us in the clothes he died in, he was still holding it. We connected it, we configured the agreed-upon IPv4 address through static routing-information-protocol, we pinged the router we knew had been constructed in the daylight, and we watched it return our pings.
From there, it took us some time to expand upon our network. We could speak to one router through a static, established connection: it knew our IP address, and we knew its. We needed connectivity farther out, we needed a means of ensuring our messages did not break down in transit, we needed more power to keep our router functional.
We weren't truly able to communicate through more than Morse code, at first. On, off, on, off. And even that would get jumbled! There were delays that we couldn't predict, so parts of our messages would come through at incorrect times, making anagrams. We needed a method of securing our information in the correct order.
We found it through IPv4's packet structure, which also had to compensate for submarine cables, and through using RIP round-robin routing. So every time I go to query tumblr, it sends one packet out, waits for an acknowledgement, and then sends out the next. This has gone well to reduce failed connectivity, and that took us several months of troubleshooting.
Fortunately, our correspondent on the other side of the veil wasn't losing faith in us, even when it was hours between signals of activity. It was obvious we were communicating back, just having issues with consistency. Once we were able to get that far, we had to properly encrypt our messages, so that they wouldn't be altered in transit. Even if they were damaged, it would be possible to reverse-engineer them into a message that made sense.
Admittedly, we would have been here much sooner if encryption was not an issue, given that we could not exactly voice any concerns or discuss the final plans, but eventually we settled on AES 128, which was a nightmare to set up but did work out eventually.
Once we got that far, catastrophe struck, and our cables started to break. In a stroke of genius, our living correspondent hooked us up to a telephone signal, which transmitted our signals into audio instead of simple electric pulses, known as dialup technology. Then, it was only a matter of agreeing on a code, and creating a device that would translate what it heard into symbols.
This solved our issue of incomprehensible anagrams permanently: voices and audio came through consistently enough that it would stop colliding with other bits of information in the network passageways and cables.
Once that was solved, just a couple days ago, we were finally up in proper communication, and set to testing everything we could, and now here I am, with a Tumblr of my very own, and I can finally say hello to everyone!
Yours in delighted correspondence,
Prosecutor van Zieks
4 notes
·
View notes
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
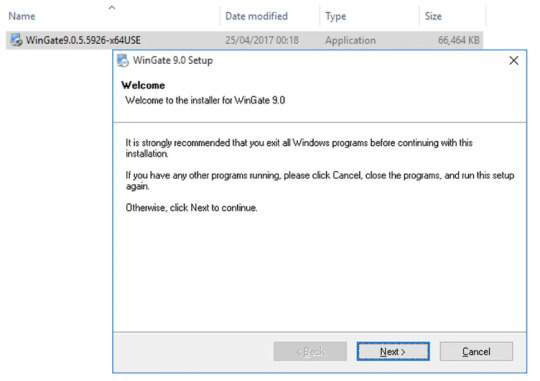
Get 1GB Proxy Free Trial of Residential Proxies Now!
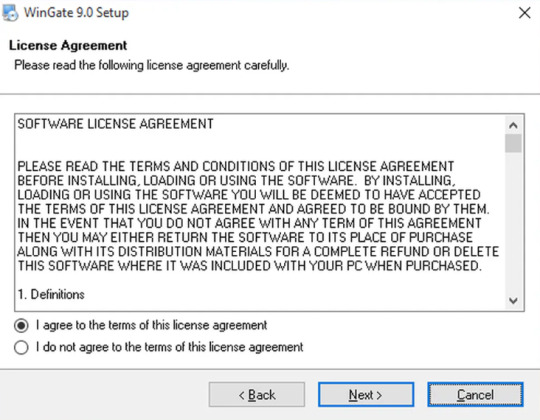
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
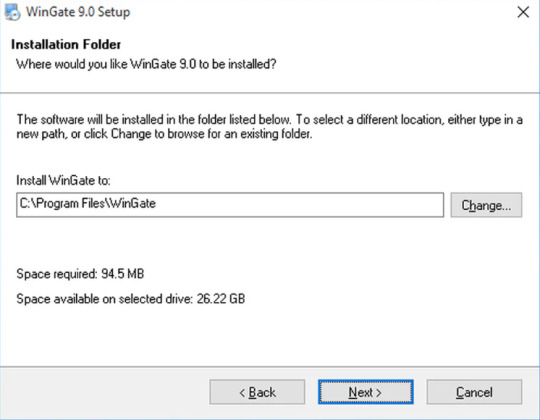
Step 3 Installation Folder
Choose the location on your system, where you like to place the WinGate installation setup.
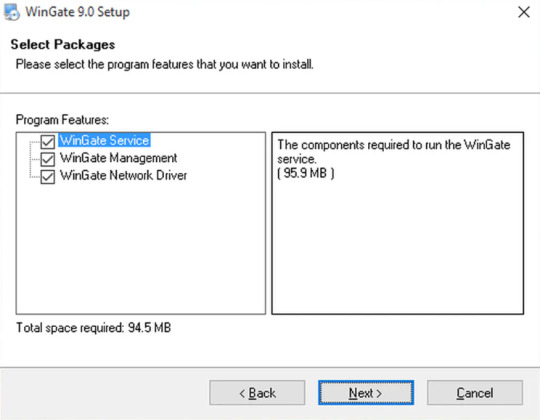
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
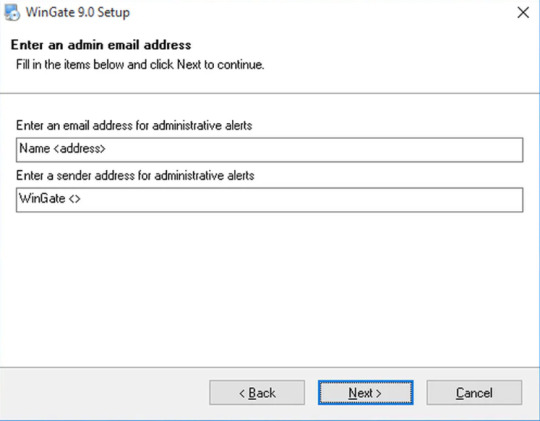
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
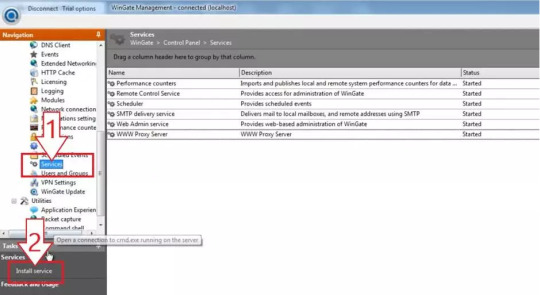
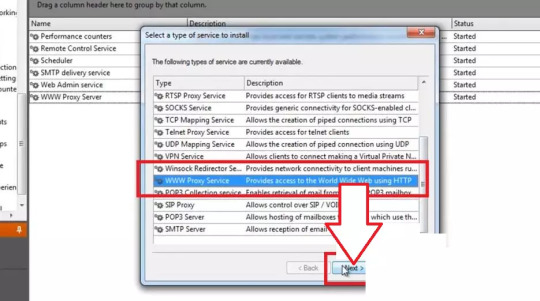
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
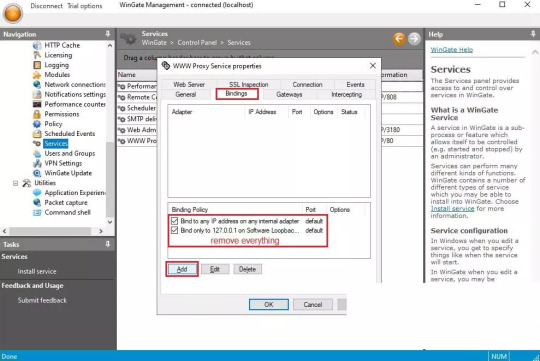
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
3. Now, go to the Connection tab. Check the box next to “Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
The Domain-Name problem
China gets a lot of hate for sectioning off the rest of the internet from their people. But that's probably one of the things they got right .
When the internet hit a global scale, China reasonably thought "we should have our local stuff more readibly accessible to our local people" after-all, what use is driving directions to an individually owned diner in Vermont to somebody in Xinagsheng?
China created their own internet, which to the internet is just a very large intranet.
The reason for this is because the base internet design really only benefited the U.S., and didn't take into account fiberoptic wires under the ocean to communicate with other countries.
We can see it in effect today with IP4 vs IP6. Where the use still uses the IP4 standard and the rest of the world is forced onto IP6. (Internet address Protocol)
Domain Names (www.address.com) only turn an IP-Address into something human readable. And again we see the same paradigms; U.S. first, and then a country designator at the end (co.jp, co.de...
The (www) part is the sub-domain, or part of the same network as the domain, just a different machine (usually, not always).
Now, the .com, .net, org was originally supposed to mean (commercial), (network), and (organization). But as we've seen: didn't mean much to actual usage... Now they're just random extensions we don't care what they mean anymore.
And there's a problem; parsing out a domain name could be as complex as
Sub.sub2.domain.co.jp vs sub.domain.com vs domain.org: which part indicates what is local on the server? And which part indicates what the infrastructure(internet routers) should use to direct traffic? There isn't a set standard here.
What this means to me is that we should rethink how we split up the internet. In order to allow users to visit hosts from other countries*and* allow foreigners to see (but not necessarily interact with) local social media.
And how can we tell which websites are operating effectively doing operations for multiple countries? Like Amazon. Country tax laws can't tell.
I get the feeling Elon Musk would be very sad about the development after his very large purchase.
For the interest of National Security and World-Wide-Economic prosperity.
There are even large amounts of data used in search engines and AI to infer local area around the user, that could be clarified via a change in systems.
Think about our area codes for phone numbers and zip codes for mail. We don't have them online. I think we need them.
If not simply to increase the speed of the internet.
7 notes
·
View notes