#IPTABLES : Introduction to Linux Firewall
Explore tagged Tumblr posts
Text
Securing Your Systems: RHCE Tips for Linux Security
Introduction: In today's interconnected world, ensuring the security of Linux systems is paramount for businesses and organizations of all sizes. As Red Hat Certified Engineers (RHCEs), it's our responsibility to implement robust security measures to protect sensitive data, prevent unauthorized access, and mitigate potential threats. In this blog post, we'll explore essential tips and best practices for enhancing Linux security, drawing on the expertise gained through RHCE certification.
Understanding the Threat Landscape:
Begin by examining the evolving threat landscape facing Linux systems, including common attack vectors and security vulnerabilities.
Highlight the importance of staying informed about emerging threats and security advisories issued by Red Hat and other industry sources.
Harden Your System Configuration:
Emphasize the significance of a secure system configuration as the foundation of Linux security.
Discuss essential security measures such as disabling unnecessary services, enforcing strong password policies, and configuring access controls using tools like SELinux.
Implement Firewalls and Intrusion Detection:
Explain the role of firewalls in controlling network traffic and preventing unauthorized access to Linux systems.
Provide guidance on configuring firewall rules using iptables or firewall to enforce a secure network perimeter.
Introduce intrusion detection systems (IDS) such as Snort or Suricata for monitoring network activity and identifying potential security breaches.
Manage User Access and Permissions:
Address the importance of user access management in maintaining Linux security.
Discuss best practices for creating and managing user accounts, including least privilege principles and user role assignments.
Demonstrate how to set granular file permissions using chmod and chown to restrict access to sensitive data.
Secure Network Services and Protocols:
Explore strategies for securing network services and protocols running on Linux systems.
Highlight the importance of regular software patching and updates to address known vulnerabilities.
Discuss techniques for securing network services such as SSH, Apache, and MySQL, including encryption, access controls, and configuration hardening.
Monitor and Respond to Security Incidents:
Stress the importance of proactive security monitoring and incident response.
Recommend tools and techniques for monitoring system logs, detecting security incidents, and responding promptly to potential threats.
Provide guidance on developing incident response plans and conducting post-incident analysis to prevent future security breaches.
Conclusion: As RHCEs, we play a vital role in safeguarding Linux systems against evolving security threats. By implementing the tips and best practices outlined in this blog post, we can strengthen the security posture of our organizations and contribute to a safer and more resilient IT environment. Let's continue to stay vigilant, adapt to emerging threats, and uphold the highest standards of Linux security in our roles as Red Hat Certified Engineers. For more details click www.qcsdclabs.com
0 notes
Text
Linux Course in Chandigarh: A Comprehensive Guide for Aspiring IT Professionals
In today’s digital world, Linux has become an essential component of IT infrastructure, powering everything from web servers and cloud systems to embedded devices. As demand for Linux professionals continues to rise, Chandigarh has emerged as a growing hub for quality IT training. This article delves into the importance of Linux, the structure of a typical Linux course in Chandigarh, and how such training can open up a world of opportunities for IT aspirants.
Why Learn Linux?
Linux is a Unix-like operating system that is free, open-source, and widely used in servers, data centers, and cloud computing environments. Here's why learning Linux is a smart career move:
Widely Used: Over 90% of cloud infrastructure and web servers run on Linux.
Career Demand: System administrators, DevOps engineers, cloud professionals, and cybersecurity experts require strong Linux skills.
Open Source Flexibility: Linux allows customization and is at the core of many enterprise technologies including Red Hat, Ubuntu, and CentOS.
Industry Certifications: Linux knowledge is a stepping stone to certifications like RHCSA, RHCE, CompTIA Linux+, and LFCS.
Chandigarh: A Growing IT Education Hub
Chandigarh, with its growing IT infrastructure and educational institutions, is an ideal place for pursuing technical training. The city offers:
Reputed Training Institutes: Several well-established institutes offer Linux and other IT courses.
Affordable Living: Compared to metro cities, Chandigarh is cost-effective for students.
Safe and Student-Friendly: The city has a strong student population and a clean, organized environment.
Who Should Take a Linux Course?
A Linux course is suitable for:
Students pursuing Computer Science or IT.
Working professionals looking to enhance their system administration or DevOps skills.
Fresher graduates who want to enter the IT industry with a specialized skill.
Network administrators aiming to deepen their understanding of Linux-based servers.
Structure of a Linux Course in Chandigarh
Most Linux training programs in Chandigarh are structured to suit both beginners and intermediate learners. Here's what a standard curriculum includes:
1. Introduction to Linux
History and philosophy of Linux
Types of Linux distributions
Installation and configuration
2. Linux Command Line
Basic shell commands
Directory and file manipulation
Text editing using vi or nano
3. File System Management
File types and permissions
Disk partitions and mounting
Logical Volume Manager (LVM)
4. User and Group Management
Creating and managing users/groups
Setting permissions and access control
Understanding /etc/passwd and /etc/shadow
5. Package Management
Using RPM, YUM, DNF (Red Hat-based)
Using APT (Debian/Ubuntu-based)
Installing, updating, and removing software
6. System Services and Daemons
Managing services with systemctl
Configuring startup processes
Working with cron jobs and background tasks
7. Networking Basics
IP addressing and configuration
Configuring DNS, DHCP, SSH
Troubleshooting tools: ping, netstat, traceroute
8. Shell Scripting
Writing and executing bash scripts
Variables, loops, and conditionals
Automating repetitive tasks
9. Security and Firewall Configuration
Setting up a firewall with iptables or firewalld
User authentication and sudo privileges
Securing services and open ports
10. Advanced Topics
Kernel management
Virtualization basics using KVM
Introduction to containers (Docker)
Modes of Training
Chandigarh-based institutes offer various formats of training to suit different needs:
Classroom Training: Instructor-led sessions with hands-on practice in a lab environment.
Online Classes: Live interactive classes or self-paced video modules.
Weekend Batches: Ideal for working professionals.
Fast-Track Courses: Intensive programs for those on a tight schedule.
Certification Support
Many Linux courses in Chandigarh also prepare students for globally recognized certifications, such as:
RHCSA (Red Hat Certified System Administrator)
RHCE (Red Hat Certified Engineer)
LFCS (Linux Foundation Certified System Administrator)
CompTIA Linux+
Certification-oriented training includes mock tests, practical labs, and real-time scenario-based exercises.
Top Institutes Offering Linux Training in Chandigarh
Several reputed training centers offer Linux courses in Chandigarh. While names may vary over time, some consistent features to look for include:
Experienced Trainers with industry background.
Updated Curriculum aligned with Red Hat and Linux Foundation.
Lab Infrastructure to practice real-world scenarios.
Placement Support with interview preparation and resume building.
Some institutes also have partnerships with Red Hat or offer authorized training, giving students access to official courseware and exams.
Career Opportunities After a Linux Course
After completing a Linux course, students can pursue various career roles depending on their skill level and interest:
1. Linux System Administrator
Responsible for installation, configuration, and maintenance of Linux servers.
2. DevOps Engineer
Combines Linux skills with tools like Docker, Jenkins, and Kubernetes to streamline software delivery.
3. Cloud Engineer
Works with cloud platforms like AWS, Azure, and Google Cloud, where Linux is often the default OS.
4. Network Administrator
Manages routers, firewalls, and switches with Linux as the control system.
5. Cybersecurity Analyst
Uses Linux tools for penetration testing, log analysis, and threat detection.
Salary Expectations
Starting salaries for Linux professionals in India typically range from ₹3–6 LPA for freshers, and go up to ₹12–20 LPA for experienced professionals in DevOps or cloud roles.
Benefits of Taking a Linux Course in Chandigarh
Affordable Quality Training: Courses in Chandigarh offer a good balance of cost and content.
Industry-Relevant Curriculum: Most institutes design their syllabus with inputs from industry professionals.
Community and Networking: Access to tech meetups, local developer groups, and hackathons.
Strong Placement Records: Many institutes have tie-ups with IT companies and conduct placement drives.
Tips for Choosing the Right Institute
When selecting a Linux course in Chandigarh, consider the following:
Check the trainer’s credentials and experience.
Ask for a demo class to evaluate teaching style.
Look for hands-on labs and real-world projects.
Ensure they offer certification guidance.
Verify placement support and success stories.
Final Thoughts
With its increasing demand in the job market and wide-ranging applications, Linux has become an indispensable skill for IT professionals. Chandigarh, with its vibrant tech training ecosystem, offers an excellent environment to learn Linux from the ground up.
Whether you are a student planning your career path, a professional looking to upgrade your skills, or an entrepreneur wanting to manage your servers more efficiently, a Linux course in Chandigarh can be your gateway to a successful IT journey.
0 notes
Text
IPTABLES : Introduction to Linux Firewall
IPTABLES : Introduction to Linux Firewall

IPTABLES : Introduction to Linux Firewall
Linux is the most-used open source operating system. Managing network traffic is one of the toughest jobs to deal with. For this, we must configure the firewall in such a way that it meets the system and users requirements without leaving the system vulnerable. The default firewall in most of the Linux distributions is IPTables.
IPTables is a standard…
View On WordPress
#and SSL port firewall#Checking current Iptables status#Checking current Iptables status firewall#Defining chain rules firewall#Defining chain rules iptables#Deleting rules of iptables#Dropping all other traffic iptables#Enabling connections on HTTP#Enabling traffic on localhost firewall#Enabling traffic on localhost iptables#Filtering packets based on source iptables#installing firewall#installing iptables#IPTABLES : Introduction to Linux Firewall#Linux#Save changes to iptables#SSH
0 notes
Text
Linux Firewall Basics

Linux Firewall
Introduction Firewall Status Stopping Firewall Disable FIrewall Enable Firewall Start Firewall Conclusion > Introduction: A firewall is a network security program that controls the incoming and outgoing connections based on the rules that are set. Linux has a default firewall i.e., iptables. Firewalld is a firewall management solution available for many Linux distributions which acts as a frontend for the iptables service provided by the Linux kernel. Firewalld installed by default in major linux distributions. > Firewall Status: We can check firewall service status by executing the below command. (firewall enabled by default). # systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled) Active: active (running) since Sat 2019-05-04 03:41:57 EDT; 5h 0min ago Docs: man:firewalld(1) Main PID: 4523 (firewalld) .... .... ..... .... Looks like below.
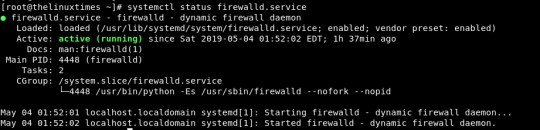
> Stopping firewall: We can stop the firewall by using this command. # systemctl stop firewalld

> Disable Firewall: We can disable the firewall to stop while the system is booting. by using this command. # systemctl disable firewalld

> Enable Firewall: If you want to enable the firewall to configure security rules for your system. then we can use this command to enable the firewall. systemctl enable firewalld
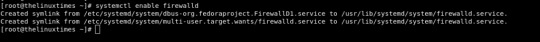
> Start Firewall: To start firewall service or firewall daemon we need to use this command. # systemctl start firewalld

> Conclusion: In this article, we have learned what is the Linux firewall, how to start, stop firewall service, how to enable or disable firewall service. If you have any questions or suggestions, please write on the comment box. Thank you. Read the full article
1 note
·
View note
Text
Introduction to IPTables
This guide is meant as an introduction to iptables and covers basic packet filtering using this tool on Centos 7. The goal is to learn to work with some basic options so you can adapt them to your particular needs. For this reason we will not cover any iptables extensions in this guide. Getting Started
The term iptables is used to define the Linux kernel firewall, part of the Netfilter project…
View On WordPress
#Filtering IP#Firewall#Introduction to IPTables#IPTables#IPTables Policies#Linux Kernel Firewall#Netfilter#Netfilter Framework
0 notes
Text
March 18, 2020 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/38ZkUXG https://ift.tt/eA8V8J via Blogger https://ift.tt/33uolEn #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
Adding an outgoing traffic rules to the firewall
Adding an outgoing traffic rules to the firewall
Adding an outgoing traffic rules to the firewall
Logo.Preferred2c.dark.png
INFA 620 Laboratory 4: Configuring a Firewall In this exercise you will be working with firewalld (see https://www.linode.com/docs/security/firewalls/introduction-to-firewalld-on-centos), a front-end to controlling Iptables. Iptables is a flexible firewall utility built for Linux operating systems (see https://www.howtoge…
View On WordPress
0 notes
Text
Security Analytics – Visualization – Big Data Workshop Black Hat 2017
VISUAL ANALYTICS – DELIVERING ACTIONABLE SECURITY INTELLIGENCE
BlackHat 2017 - Las Vegas
Big Data is Getting Bigger - Visualization is Getting Easier - Learn How! Dates: July 22-23 & 24-25 Location: Las Vegas, USA SIGN UP NOW
OVERVIEW
Big data and security intelligence are the two very hot topics in security. We are collecting more and more information from both the infrastructure, but increasingly also directly from our applications. This vast amount of data gets increasingly hard to understand. Terms like map reduce, hadoop, spark, elasticsearch, data science, etc. are part of many discussions. But what are those technologies and techniques? And what do they have to do with security analytics/intelligence? We will see that none of these technologies are sufficient in our quest to defend our networks and information. Data visualization is the only approach that scales to the ever changing threat landscape and infrastructure configurations. Using big data visualization techniques, you uncover hidden patterns of data, identify emerging vulnerabilities and attacks, and respond decisively with countermeasures that are far more likely to succeed than conventional methods. Something that is increasingly referred to as hunting. The attendees will learn about log analysis, big data, information visualization, data sources for IT security, and learn how to generate visual representations of IT data. The training is filled with hands-on exercises utilizing the DAVIX live CD.
What's New?
The workshop is being heavily updated over the next months. Check back here to see a list of new topics:
Security Analytics - UEBA, Scoring, Anomaly Detection
Hunting
Data Science
10 Challenges with SIEM and Big Data for Security
Big Data - How do you navigate the ever growing landscape of Hadoop and big data technologies? Tajo, Apache Arrow, Apache Drill, Druid, PrestoDB from Facebook, Kudu, etc. We'll sort you out.
SYLLABUS
The syllabus is not 100% fixed yet. Stay tuned for some updates.
Day 1:
Log Analysis
Data Sources Discussion - including PCAP, Firewall, IDS, Threat Intelligence (TI) Feeds, CloudTrail, CloudWatch, etc.
Data Analysis and Visualization Linux (DAVIX)
Log Data Processing (CSVKit, ...)
SIEM, and Big Data
Log Management and SIEM Overview
LogStash (Elastic Stack) and Moloch
Big Data - Hadoop, Spark, ElasticSearch, Hive, Impala
Data Science
Introduction to Data Science
Introduction to Data Science with R
Hunting
Day 2:
Visualization
Information Visualization History
Visualization Theory
Data Visualization Tools and Libraries (e.g., Mondrian, Gephi, AfterGlow, Graphiti)
Visualization Resources
Security Visualization Use-Cases
Perimeter Threat
Network Flow Analysis
Firewall Visualization
IDS/IPS Signature Analysis
Vulnerability Scans
Proxy Data
User Activity
Host-based Data Analysis
Sample of Tools and Techniques
Tools to gather data:
argus, nfdump, nfsen, and silk to process traffic flows
snort, bro, suricata as intrusion detection systems
p0f, npad for passive network analysis
iptables, pf, pix as examples of firewalls
OSSEC, collectd, graphite for host data
We are also using a number of visualization tools to analyze example data in the labs:
graphviz, tulip, cytoscape, and gephi
afterglow
treemap
mondrian, ggobi
Under the log management section, we are going to discuss:
rsyslog, syslog-ng, nxlog
logstash as part of the elastic stack, moloch
commercial log management and SIEM solutions
The section on big data is covering the following:
hadoop (HDFS, map-reduce, HBase, Hive, Impala, Zookeper)
search engines like: elastic search, Solr
key-value stores like MongoDB, Cassandra, etc.
OLAP and OLTP
The Spark ecosystem
SIGN UP
TRAINER
Raffael Marty is vice president of security analytics at Sophos, and is responsible for all strategic efforts around security analytics for the company and its products. He is based in San Francisco, Calif. Marty is one of the world's most recognized authorities on security data analytics, big data and visualization. His team at Sophos spans these domains to help build products that provide Internet security solutions to Sophos' vast global customer base.
Previously, Marty launched pixlcloud, a visual analytics platform, and Loggly, a cloud-based log management solution. With a track record at companies including IBM Research, ArcSight, and Splunk, he is thoroughly familiar with established practices and emerging trends in the big data and security analytics space. Marty is the author of Applied Security Visualization and a frequent speaker at academic and industry events. Zen meditation has become an important part of Raffy's life, sometimes leading to insights not in data but in life.
from Security Analytics – Visualization – Big Data Workshop Black Hat 2017
0 notes
Text
February 07, 2020 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/2AmyzKP https://ift.tt/eA8V8J via Blogger https://ift.tt/39m1rB8 #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
January 04, 2020 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/2AmyzKP https://ift.tt/eA8V8J via Blogger https://ift.tt/2QoZJbc #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
December 20, 2019 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/2AmyzKP https://ift.tt/eA8V8J via Blogger https://ift.tt/2ZblD4F #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
Laboratory 4: Configuring a Firewall
Laboratory 4: Configuring a Firewall
Laboratory 4: Configuring a Firewall
Logo.Preferred2c.dark.png
INFA 620 Laboratory 4: Configuring a Firewall In this exercise you will be working with firewalld (see https://www.linode.com/docs/security/firewalls/introduction-to-firewalld-on-centos), a front-end to controlling Iptables. Iptables is a flexible firewall utility built for Linux operating systems (see https://www.howtogeek.com/17762…
View On WordPress
0 notes
Text
November 10, 2019 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/2AmyzKP https://ift.tt/eA8V8J via Blogger https://ift.tt/2qKmsUJ #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
October 20, 2019 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/2AmyzKP https://ift.tt/eA8V8J via Blogger https://ift.tt/35QDCjQ #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Text
October 05, 2019 at 10:00PM - The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Ashraf
The Ultimate White Hat Hacker 2018 Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
In this beginner- and professional-friendly course, you’ll learn how black hat hackers hack Windows using advanced techniques, while improving your knowledge on how to analyze and secure Windows, and detect a hacker’s identity. Across the example-based course, you’ll get hands-on instruction in white hat hacking.
Access 74 lectures & 8 hours of content 24/7
Learn how to download & setup Kali Linux 2.0, Windows 10, & Metasploit as virtual machines
Understand how to gather as much info as possible from your target
Use msfconsole interface like a professional
Encode & combine the payload
Gain full access over a target OS & learn how to interact w/ it using Meterpreter command line
Perform various attacks over WAN network
Detect & protect from all of the attacks discussed
To completely understand computer security, it’s vital to think outside the box. It’s not just about firewalls, Intrusion Prevention Systems, or antivirus. It’s also about tricking people into doing whatever a hacker wishes. A secure system, therefore, is also about informed people. This training is based on a practical approach of day-by-day situations contained labs based on real environments. The aim is to help you learn ethical hacking techniques and methodology used in penetration systems to better protect yourself and those around you.
Access 85 lectures & 12.5 hours of content 24/7
Cover both theoretical & practical aspects of ethical hacking
Work in hands-on labs about hacking systems, networks, wireless, mobile, & websites
WAPTP v3.1 is a highly practical and hands-on training for web application penetration testing that covers the OWASP top 10 vulnerabilities. Starting with various terminologies of web technologies, you’ll build towards mapping an application for insecurities, and understanding how to identify and mitigate threats.
Access 64 lectures & 8 hours of content 24/7
Map an app for insecurities using various tools & tricks, including Burp Suite
Explore serious vulnerabilities like SQL injection, cross-site scripting, cross-site request forgery, XXE attacks, & more
Find & hunt each vulnerability through the points developers use to secure the web app at the time of development
This course aims to teach you in-depth WiFi hacking and security. Upon completion, you’ll be confident in breaking all types of WiFi encryption methods. Starting as a complete beginner with little to no knowledge of WiFi security and Kali Linux, you’ll learn the most important elements of WiFi hacking so you can begin applying them to a career in ethical hacking.
Access 118 lectures & 7 hours of content 24/7
Get an introduction to Kali Linux & network basics
Learn how to passively & actively gather information
Identify vulnerabilities in a target
Overrun buffer memory, perform password attacks, attack WiFi networks, & more
Discuss client side & server side web vulnerabilities
Test & exercise your defenses to ensure they’re up to task by simulating real-world attacks
To break into the world of professional penetration testing, you’ll need to be an ace with Kali Linux. This course will introduce you to the latest ethical hacking tools and techniques with Kali Linux, using a testing lab for practicing different types of attacks. Across the course, you’ll simulate an entire penetration test from beginning to end, giving you verifiable hands-on experience.
Access 80 lectures & 8.5 hours of content 24/7
Get comfortable w/ Kali Linux & learn the penetration testing phases
Manage Kali Linux HTTP & SSH services
Discover essential tools like Netcat & WireShark
Gather passive & active information
Explore how to perform & defend against a variety of attacks
Receive monthly virtual machines as a hacking challenge
This course is focused on the practical side of penetration testing without neglecting the theory behind each attack. As you gain a complex understanding of websites, you will then learn how you can exploit them to carry out a number of powerful cyber attacks. You’ll track from a beginning to advanced level and by the time you finish you’ll be able to launch attacks and test the security of websites and apps the same way that black hat hackers would, and be able to fix these vulnerabilities.
Access 93 lectures & 9 hours of content 24/7
Learn how to gather information about your target site like discovering the DNS server used & subdomains
Discover, exploit, & fix a number of vulnerabilities like file upload, code execution, SQL injection, XSS, & much more
Understand what you can do w/ the access gained from vulnerabilities
Explore the basic exploitation of attacks & the advanced methods to enhance them
Learn how & why vulnerabilities are exploitable, how to fix them, & the right practices to avoid them
Over this course you’ll learn network hacking techniques and vulnerability scanning to discover security risks across an entire network, learning skills for which companies are willing to pay top dollar. Whether you want to protect your own network or protect corporate networks professionally, this course will get you up to speed.
Access 106 lectures & 12.5 hours of content 24/7
Architect your network for maximum security & prevent local & remote attacks
Understand the various types of firewalls available, including layer 4 firewalls like Iptables & PF
Discuss firewalls on all platforms, including Windows, Mac OS, & Linux
Explore wireless security & learn how WiFi is hacked
Use tools like Wireshark, Tcpdump, & Syslog to monitor your network
Dive into search engine privacy & tracking, learning how to mitigate tracking & privacy issues
This course provides a good starting point from which to learn ethical hacking and identify threats and vulnerabilities to secure your IT environment. You’ll begin with an introduction to the best tools around before diving into basic hacking technique, and ultimately going into real-life scenarios to get a hang of how hackers think.
Access 14 lectures & 2 hours of content 24/7
Discuss a basic introduction to reconnaissance
Get hands-on experience working w/ Metasploit & testing the effectiveness of different defenses
Learn about sniffing & how effective Man-in-the-Middle attacks can be
Go through a coffee shop scenario to further your understanding
Understand how hackers use networks to gain access to different systems
from Active Sales – SharewareOnSale https://ift.tt/2AmyzKP https://ift.tt/eA8V8J via Blogger https://ift.tt/2nqZ3qo #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes