#installing firewall
Explore tagged Tumblr posts
Text
@elkenbulwark

"I don't need the tadpoles' services to know when the others at camp are— overly excited let's say. I can smell them." Oh the joy of enhanced vampiric senses.
#crack: chipping my fangs#dash commentary#// don't be starting shit biv#// how the fuck you plan on installing a firewall
2 notes
·
View notes
Text
Laptop Repair in Chicago IL

Dreamwerx Facility Services offers reliable laptop repair in Chicago IL, handling everything from hardware issues to software troubleshooting. Our certified technicians ensure fast, efficient repairs to get your devices back in top shape. Choose Dreamwerx for trusted Computer Repair Service in Chicago IL backed by expert care and customer satisfaction.
#Computer Repair Service in Chicago IL#IT Services in Chicago IL#Home Network Installation in Chicago IL#Data Recovery Services in Chicago IL#Laptop Repair in Chicago IL#Motherboard Repair in Chicago IL#Battery Replacement in Chicago IL#Hard Drive Replacement in Chicago IL#Firewall Configuration in Chicago IL#Computer Repair Service near me#Home Network Installation near me#Data Recovery Services near me#Laptop Repair near me#Motherboard Repair near me#Battery Replacement near me#Hard Drive Replacement near me#Firewall Configuration near me
1 note
·
View note
Link
#accesspoint#cloud#configuration#Controller#firewall#Install#IT#Monitoring#networkmanagement#networking#Performance#Security#self-hosted#Server#systemadministration#Ubiquiti#Ubuntu22.04#Ubuntu24.04#UniFi#WiFi#Wireless
0 notes
Text
A Comprehensive Guide to Installing and Configuring a Firewall
In today's digital landscape, server security is paramount. With cyber threats becoming increasingly sophisticated, implementing robust security measures is crucial to protect your valuable data and maintain the integrity of your online presence. One of the most effective ways to secure your cPanel server is to install firewall cpanel and configuring a firewall. This blog post will delve into the importance of firewalls, guide you through the installation process, and provide essential configuration tips to fortify your server's defenses.
A firewall acts as a security barrier between your server and the outside world, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. It plays a vital role in preventing unauthorized access, blocking malicious attacks, and safeguarding sensitive information.
0 notes
Text
Docker Setup: Monitoring Synology with Prometheus and Grafana
In this article, we will discuss “Docker Setup: Monitoring Synology with Prometheus and Grafana”. We will be utilizing Portainer which is a lightweight/open-source management solution designed to simplify working with Docker containers instead of working with the Container Manager on Synology. Please see How to use Prometheus for Monitoring, how to Install Grafana on Windows and Windows Server,…
#Accessing Grafana and Prometheus#Add Portainer Registries#Configure and Run Prometheus Container#docker#Docker Containers on Synology#Enter5yourownpasswordhere123456#Enter5yourownpasswordhere2345#Grafana monitoring#Grafana/Prometheus Monitoring#How To Install Prometheus And Grafana On Docker#install portainer#Modify Synology Firewall Rules#monitoring solutions for Docker#portainer#portainer server#Prometheus Grafana integration#Prometheus metrics#Pull Docker Images for Grafana and Prometheus#Set Up Grafana Data Source#Synology monitoring setup#Your Portainer instance timed out for Security Purposes
0 notes
Text
Top-Quality Firewall Installation in Dubai for Enhanced Security

Protect your business with robust firewall installation in Dubai, ensuring that your network remains secure from external threats. A strong firewall is your first line of defense against cyberattacks and unauthorized access.
0 notes
Text
Pakistan Faces Criticism After Second Test of Internet Firewall
Amid growing concern from internet users and digital rights activists over the disruption of digital platforms and reduced internet speed, Pakistani authorities have completed the second trial run of a highly debated firewall system, telecom sources revealed to Geo News on Thursday.The firewall, equipped with deep packet inspection (DPI) capabilities, has been installed on internet service…
0 notes
Text
#Accounting Software In Dubai#Best Accounting Software In UAE#IT Infrastructure Services In Dubai#IT Services In Dubai#Managed IT Service Providers In Dubai#IT Support Companies In Dubai#IT Networking Solutions Company Dubai#Access Control System Suppliers In Dubai#Firewall Installation Services In Dubai#Accounting Software For Small Business In Dubai#Best Accounting Software Solutions In Dubai#Best Accounting Software For Medium Business In Dubai#Cheap Accounting Software For Small Business In Dubai#Best Cloud Based Accounting Software In Dubai#Best Low Cost Accounting Software For Small Business In Dubai#Best Accounting Software For Small To Medium Business In Dubai#Best Business Accounting Software Services In Dubai#Best Software Company In Dubai#Web Designing Services In Dubai#Best SEO Services In Dubai#Top HRMS Software In Abu Dhabi#Best ERP Solution Provider UAE#Best Project Management Software In Dubai#Fitness and Gym Management Software In Dubai#MEP Contracting ERP Software In Dubai#Best ERP Software For Metal Fabrication Industry In Dubai
0 notes
Text
Virtuelle Private Netzwerke (VPN): Sicher und anonym im Internet unterwegs
Virtuelle Private Netzwerke, kurz VPNs, erfreuen sich wachsender Beliebtheit. Aber was genau ist ein VPN und welche Vorteile bietet es Ihnen? Im Folgenden erfahren Sie alles Wissenswerte rund um VPNs.

Was ist ein Virtuelles Privates Netzwerk (VPN)?
Ein Virtuelles Privates Netzwerk (VPN) schafft einen sicheren Tunnel zwischen Ihrem Gerät (Computer, Smartphone, Tablet) und einem entfernten Server. Dieser Tunnel verschlüsselt Ihre gesamte Internetkommunikation, sodass Außenstehende Ihre Daten nicht einsehen oder abfangen können. Stellen Sie sich das VPN bildlich wie einen geheimen Gang vor, der Ihr Gerät mit dem Internet verbindet, ohne dass jemand von außen diesen Gang einsehen kann.
Wie funktioniert ein VPN?
Verbindungsaufbau: Sie stellen mit Ihrem Gerät eine Verbindung zu einem VPN-Server her. Dieser Server wird von einem VPN-Anbieter betrieben.
Datenverschlüsselung: Ihr gesamter Datenverkehr wird verschlüsselt, bevor er Ihr Gerät verlässt. Nur der VPN-Server kann die Daten wieder entschlüsseln.
Umleitung des Datenverkehrs: Ihre Daten werden über den verschlüsselten Tunnel zum VPN-Server geleitet.
Weiterleitung ans Ziel: Der VPN-Server leitet Ihre Daten dann an das von Ihnen gewünschte Ziel im Internet weiter.
Rückweg: Die Antwort vom Ziel im Internet durchläuft den gleichen Weg zurück und wird erst am VPN-Server entschlüsselt.
Entschlüsselung: Der VPN-Server entschlüsselt die Daten und sendet sie an Ihr Gerät.
Welche Vorteile bietet ein VPN?
Sicherheit: Der verschlüsselte Tunnel schützt Ihre Daten vor Spionage durch Hacker, Internetanbieter oder andere Dritte.
Anonymität: Ihre tatsächliche IP-Adresse wird durch die IP-Adresse des VPN-Servers maskiert. Dadurch surfen Sie anonym im Internet und Ihr Standort bleibt verborgen.
Umgehen von geografischen Beschränkungen: Viele Websites und Online-Dienste sind regional beschränkt. Mit einem VPN können Sie sich mit einem Server in einem anderen Land verbinden und so auf diese Dienste zugreifen.
Öffentliche WLANs sicher nutzen: In öffentlichen WLAN-Netzwerken (z.B. in Cafés, Hotels oder Flughäfen) sind Ihre Daten besonders gefährdet. Ein VPN schützt Ihre Daten auch in unsicheren WLANs.
Zensur umgehen: In einigen Ländern wird der Internetzugang zensiert. Mit einem VPN können Sie diese Zensur umgehen und auf alle gewünschten Inhalte zugreifen.
Einsatzbereiche von VPNs
VPNs werden in verschiedenen Bereichen eingesetzt:
Privatpersonen:
Sichern die Datenübertragung im öffentlichen WLAN.
Umgehen geografische Beschränkungen beim Streaming oder Online-Shopping.
Schützen die Privatsphäre beim Surfen im Internet.
Unternehmen:
Ermöglichen Mitarbeitern den sicheren Fernzugriff auf Unternehmensnetzwerke.
Schützen sensible Unternehmensdaten.
Verbinden verschiedene Unternehmensstandorte miteinander.
Worauf sollten Sie bei der Auswahl eines VPN-Anbieters achten?
Sicherheit: Achten Sie auf ein sicheres Verschlüsselungsprotokoll und eine strikte No-Logs-Policy (der Anbieter speichert keine Daten über Ihre Aktivitäten).
Geschwindigkeit: Ein guter VPN-Anbieter sollte die Geschwindigkeit Ihrer Internetverbindung möglichst wenig beeinträchtigen.
Serverstandorte: Wählen Sie einen Anbieter mit Servern in den gewünschten Ländern.
Geräteunterstützung: Stellen Sie sicher, dass der VPN-Anbieter Software für Ihr Gerät (Computer, Smartphone, Tablet) anbietet.
Preis: Es gibt kostenlose und kostenpflichtige VPN-Anbieter. Kostenlose VPNs bieten oft weniger Funktionen und können weniger sicher sein.
Fazit
Virtuelle Private Netzwerke bieten eine einfache und effektive Möglichkeit, Ihre Daten im Internet zu schützen und anonym zu surfen. Achten Sie bei der Auswahl eines VPN-Anbieters auf die genannten Kriterien, um den für Ihre Bedürfnisse passenden Anbieter zu finden.
Zusätzliche Hinweise:
Die Nutzung von VPNs kann in einigen Ländern illegal sein. Informieren Sie sich daher vor der Nutzung über die rechtlichen Bestimmungen in Ihrem Land.
VPNs können die Geschwindigkeit Ihrer Internetverbindung geringfügig verlangsamen.
Mit diesem grundlegenden Wissen über Virtuelle Private Netzwerke können Sie entscheiden, ob ein VPN für Sie sinnvoll ist und die richtige Wahl für Ihre Anonymität und Sicherheit im Internet treffen.
#Netzwerk-Sicherheitslösungen#Virtuelle Private Netzwerke (VPN)#Firewall-Installation und Konfiguration#Router-Konfiguration und -Management#ITScale Gmbh
1 note
·
View note
Text
we had to suddenly update 20 something of our managed firewalls yesterday bc of a vulnerability identified within the firewall's OS and you would not believe how many people approved it vs the people who keep arguing with us about "do I really need this update"
#there are two clients who have argued with us about it#for one client a printer install is more important than making sure their firewall is up to snuff against attackers#esp attackers who are according to our logs: constantly trying to access this client's internal shit#the other client thinks that the update should be done automatically and we shouldn't have to install the update#but the update takes down ur internet for about 30 mins in 5 six minute increments so like you'd be mad at us anyway if they just pushed it#work.exe#yall is it friday yet
0 notes
Text
youtube
SOPHOS XGS SW-19.5.3 MR-3 Firewall | First Time Configuration | Step by Step in Hindi | By Sachin
#firewall#sophos xg firewall#network security tutorial#sophos xg firewall complete overview in hindi#how to setup sophos firewall in hindi#how to create rule in the sophos xg firewall#how to install sophos firewall#how to install sophos firewall on vmware#sophos xg v19#sophos xg firewall v19#xg firewall#setup sophos xg v19#configure sophos xg v19#configuring sophos xg v19#v19#xg firewall v19#sophos firewall#what is firewall#firewall explained#network firewall#Youtube
0 notes
Text
opened my laptop to make some wayv gifs only to find that adobe found me and sniped me in the night. a sign from god not to gif tonight.
#i’m actually a little upset i blocked adobe in my firewall and everything#and now i gotta install a fresh cracked copy of photoshop#p
0 notes
Link
Decoding Error 0xc000007b: its Causes and Effective Solutions Encountering error 0xc000007b can be highly frustrating and inconvenient for Windows users. This error has a significant impact on various applications, causing them to fail to launch or run properly. Understanding the causes of error 0xc000007b and finding effective solutions is crucial for a smooth Windows experience. [caption id="attachment_62721" align="aligncenter" width="1280"] What is error 0xc000007b and the solution?[/caption] Understanding Error 0xc000007b Error 0xc000007b is a common occurrence in Windows operating systems. It is represented in hexadecimal form and is related to application compatibility. This error arises when an application is unable to start correctly. There are several potential causes for error 0xc000007b. One common cause is missing or corrupted system files. Incompatible software versions can also trigger this error. Additionally, issues with Microsoft Visual C++ Redistributable packages can lead to error 0xc000007b. This error can affect a wide range of applications, including games, design software, and multimedia tools. It can disrupt productivity and hinder the enjoyment of various programs. Unveiling Solutions to Error 0xc000007b Updating System Files and Drivers Keeping your system files and drivers up to date is essential for resolving error 0xc000007b. Start by performing a Windows Update to ensure that all system files are current. This will help patch any vulnerabilities or missing components that may be causing the error. Next, update your device drivers. Outdated or incompatible drivers can contribute to the occurrence of error 0xc000007b. To update drivers, visit the manufacturer's website or use a reliable driver update tool. Reinstalling or Repairing Microsoft Visual C++ Redistributable Packages Microsoft Visual C++ Redistributable packages play a crucial role in application compatibility. If these packages are missing or corrupted, it can lead to error 0xc000007b. To resolve this, you can try reinstalling or repairing the packages. First, determine the version of the Visual C++ Redistributable package required by the application. Visit the Microsoft website to download the appropriate package and install it on your system. If the package is already installed, you can try repairing it through the Control Panel's "Programs and Features" section. Resolving Compatibility Issues Compatibility issues between applications and the operating system can also trigger error 0xc000007b. To address this, you can run the problematic applications in compatibility mode. Right-click on the application's executable file, go to "Properties," and navigate to the "Compatibility" tab. From there, select the appropriate compatibility mode based on the recommended settings or the operating system version the application was designed for. It is also crucial to check the system requirements of the application. Ensure that your system meets the minimum requirements specified by the software developer. Inadequate hardware specifications can contribute to error 0xc000007b. Frequently Asked Questions What are the other common error codes similar to 0xc000007b? Some other common error codes similar to 0xc000007b include 0xc0000142, 0xc0000005, and 0xc0000135. These errors often indicate issues with application compatibility or system files. Can antivirus software cause error 0xc000007b? In rare cases, certain antivirus software may interfere with the proper functioning of applications and trigger error 0xc000007b. Temporarily disabling the antivirus software or adding the affected application to the antivirus exclusion list may help resolve the issue. How can I determine if my system is missing necessary Visual C++ Redistributable packages? You can check if your system is missing necessary Visual C++ Redistributable packages by going to the Control Panel and navigating to the "Programs and Features" section. Look for Microsoft Visual C++ Redistributable packages in the list of installed programs. If you find that the required packages are missing, you can download and install them from the official Microsoft website. Is it possible to fix error 0xc000007b without reinstalling the application? Yes, it is possible to fix error 0xc000007b without reinstalling the application in some cases. By following the solutions mentioned earlier, such as updating system files and drivers, repairing Microsoft Visual C++ Redistributable packages, and resolving compatibility issues, you may be able to resolve the error without the need for a complete application reinstallation. Are there any specific Windows updates known to resolve this error? While there are no specific Windows updates known to directly resolve error 0xc000007b, it is important to keep your operating system up to date. Windows updates often include bug fixes, security patches, and compatibility improvements that can indirectly address the underlying causes of this error. Can hardware issues cause error 0xc000007b? While hardware issues are not a common cause of error 0xc000007b, they can contribute to the error in certain cases. Insufficient RAM, faulty hard drives, or incompatible hardware components may affect the proper functioning of applications and lead to this error. Ensuring that your hardware meets the minimum requirements of the application can help prevent hardware-related issues. What should I do if none of the provided solutions work for me? If none of the provided solutions resolve error 0xc000007b, it is recommended to seek further assistance. You can reach out to the software developer or the application's support team for specific guidance and troubleshooting steps. Additionally, consulting with a computer technician or IT professional may help identify underlying issues and provide more advanced solutions. Can error 0xc000007b be caused by a corrupted hard drive? While error 0xc000007b is not directly caused by a corrupted hard drive, a faulty or corrupted hard drive can contribute to this error. If the application's files or system files are stored on a corrupted hard drive, it may lead to the occurrence of error 0xc000007b. Running disk repair tools or performing a thorough scan of the hard drive for errors can help identify and resolve any issues related to the hard drive. Is it safe to download Visual C++ Redistributable packages from third-party websites? It is generally recommended to download Visual C++ Redistributable packages from the official Microsoft website to ensure their authenticity and safety. Third-party websites may not always provide the correct or updated versions of the packages, and there is a risk of downloading malware or potentially harmful files. Stick to trusted sources to download the necessary packages. How can I prevent error 0xc000007b from occurring in the future? To prevent error 0xc000007b from occurring in the future, it is important to keep your system updated. Regularly install Windows updates, including service packs and security patches. Additionally, ensure that your device drivers, especially graphics drivers, are up to date. It is also advisable to regularly scan your system for malware and maintain a healthy hard drive by performing disk cleanup and defragmentation. Finally, before installing any new applications, check their system requirements to ensure compatibility with your operating system. Conclusion: Error 0xc000007b can cause frustration and inconvenience when using Windows applications. By understanding its causes and implementing the provided solutions, you can effectively resolve this error. Keep your system files, drivers, and software up to date, and address compatibility issues to prevent encountering this error in the future. If the provided solutions do not work, seek further assistance from software developers or IT professionals to ensure a smooth Windows experience.
#.NET_Framework#administrator#antivirus#Application#clean_boot#compatibility#compatibility_mode#corrupted#DirectX#DLL_files#driver#error_0xc000007b#error_code#firewall#installation#Microsoft_Visual_C#missing#reinstall#repair#software#solution#system#system_restore#system_scan#third_party_software.#troubleshooting#update#Windows
0 notes
Text
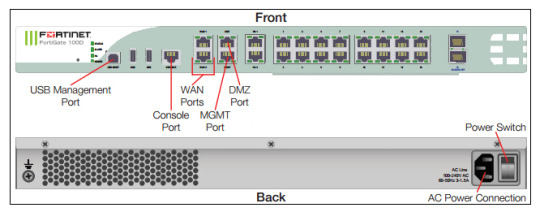
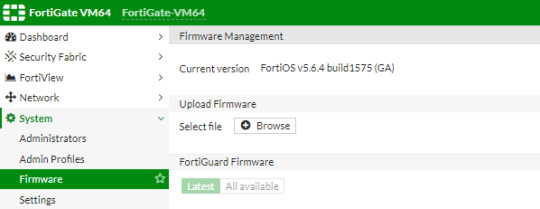
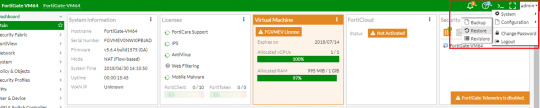
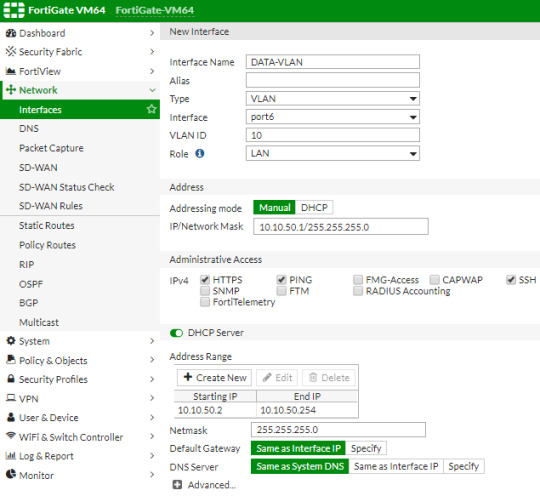
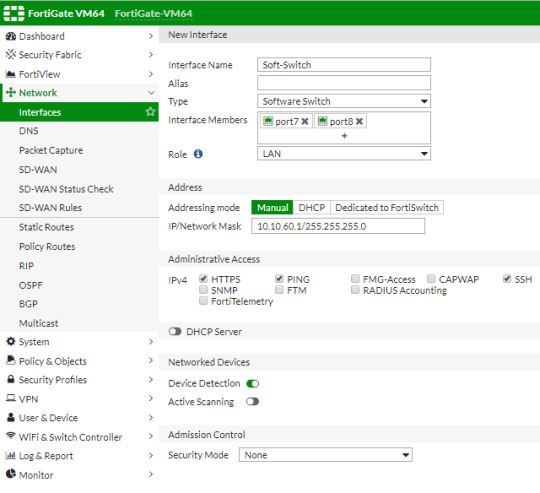
Fortify your cybersecurity arsenal with #Fortigate training. Learn to design, deploy, and manage robust security solutions. Become the guardian of your network's integrity. https://www.dclessons.com/category/courses/fortigate
#fortigate#introduction#firewall#datacenter#practicelabs#training#install#setup#routing#transparentmode#vdom#configure#network#vpn#tunneling#ipsec#tunnel#device#forticare#port#fortiexplorer#nat#mode
0 notes
Text
There's my portal
As i said on @bet-on-me-13 'Where is my portal' post, here is my short about their idea. please enjoy.
Danny sipped his coffee, slowly shuffling towards his lab. It had been a long time since he had a ‘run on two coffees and some ecto’ weekend but here he was, Monday morning, on his way to work.
He really wanted to be in bed but he had bills to pay.
Quietly he shuffled into his lab, which he found oddly drafty and oddly bright, considering he hadn’t turned on the lights yet. After flicking them on he moved on towards his desk, passing a big gaping hole in the wall and—
Danny paused, shuffled backwards a bit and then looked at the place where his portal used to be. For a long moment he just looked, then did a slow blink and took another sip of coffee.
After making sure that his portal, including parts of the wall, were really gone, he let out a sigh and held his face. “Who the fuck stole my door?”
With a sigh he pushed his bangs out of his face and walked to his PC, to check the security footage of his Cameras. For once it wasn’t Vlad who stole his shit, Vlad at least had the courtesy to leave a note that he ‘borrowed’ something. It was safe to say that he was surprised to find the footage gone. There weren't many people that could hack through Tucker's programing.
Danny sat there, looking at the black screen of his PC for a long moment before thinking aloud. “Okay, we have one or more people who can; One, break through Tuckers firewalls. Two, physically move a portal weighing around ten tons and, Three, knows their way around Arcane Runes so as to not cause a mass ghost invasion.”
He thought about it for a minute before throwing his hands up. “Fuck this, I’m just going to use the other side to find it.” He got out of his chair before transforming.
Danny focused his power into one of his fingers before poking the air in front of him, the tip of it pierced the fabric of space which he then used to rip it open. He quickly flew through the tear before it sealed again. Despite Wulf teaching him how to do it he still sucked at it, which was the main reason he built his portal.
Once in the Zone he looked around for it. He found it after over two hours of searching, which only served to piss him off to the point where he began muttering curses under his breath.
Standing in front of it, he gave it a quick inspection. After inspecting the Runes, Danny had to admit that, whoever had stolen it, knew his way around them. They pretty much locked out anyone not authorized and or approved by the Caster. Too bad for them, Danny had the ‘Masterkey’ and went through anyway.
John Constantine was holding his face, quietly counting to ten. Neither smoking nor drinking would help in this situation. After reaching fifty he ran his hands over his head, looking at the assembled brigade of idiots in front of him.
“Okay, let me get this straight.” He started, “You,” he pointed at Batman, “found an ‘unknown energy signature’ and went to investigate. Then you found a high security lab with had an active portal to ‘who knows where’ and your first decision was to fucking steal it?!?!”
Superman moved forward, opening his mouth to counter but Constantine didn't let him. “AND you moron helped him steal it, not to mention you!” he pointed at flash, “Help install it here, in the watchtower, without telling anyone from JLD about it?”
Flash looked a bit sheepish at him. “Well, in my defense I didn’t know it was stolen.”
Constantine wanted to bash his head against the next closest bulkhead, maybe that would help.
“Okay, okay.” Constantine facepalmed, trying to stop the aneurysm from building up more.
A deep chill suddenly filled the air and sent goosebumps all over his back, “Oh this is just getting better and better.” Constantine reached into his pocket for a warding charm, before turning around and swearing. He stopped swearing when he saw who had come through. “Oh, hey Phantom.”
“Constantine, why the fuck did you steal my portal?” Danny wasn’t even pissed anymore. He knew the English drunktard too well to blame him. Granted he was obnoxious, didn’t pay back his debt and came whenever it suited him, but Danny liked the man. He didn’t exasperate problems and always did what was necessary.
“Look, I didn’t.” He then threw a thumb over his shoulder, “Those morons did.”
“Constantine, do you know this entity?” Batman already looked on high alert.
“Excuse you! I have a name. And that is my Portal. Explain why it isn't where it is supposed to be.”
“The sensors of the Watchtower found an unknown energy signature, upon investigation we found an unsecured pathway to a different dimension, so we secured it.”
Danny stared at Batman for a solid minute, then simply said, “Oh I'm going to sue your ass so hard your grandkids will feel it.”
3K notes
·
View notes
Note
thoughts on using library computers to disguise your digital footprint? because if the machine gets wiped when you log out, and the library doesn't keep detailed records of what machine you were using when, then all someone else would have is IP data unconnected to a person and also mixed in with whatever else folks were doing on the library computers
The machine absolutely does not get wiped when you log out and there's very little chance that a library computer will let you fire up Tor. You're better off using a traffic anonymizer than you are trying to use public computers to cover your tracks. The IP address IS the big risk here.
Libraries are generally really good about protecting their patrons' privacy and I respect the hell out of them for that but computers log everything that you do and can be subpoenaed as evidence even if the library wants to protect user privacy.
Also, I love libraries but you should treat every public computer you come across like it has a keylogger installed on it because it might. Your city could have an overzealous city council that has more control than it should over the library board and has taken it upon themselves to add covenanteyes to the library computers. Your library crew could be fantastic but less tech-savvy than is ideal and may not realize it if malware is installed on one of the machines. The library may clear browser history twice a day but the ISP still has a record of where you went and what time you went there. Somebody could have literally plugged a keylogger into a USB port on the back of the machine.
The point of a traffic anonymizer is it hides where the traffic originated; each node knows where the previous hop came from and where the next hop went, but not what came BEFORE the previous hop or what happened after, or how long the chain was, so there is no way to tell if a message originated in the US or Brazil or Vietnam or Sweden. Sending traffic from a library does the opposite of this, and very clearly says "the person who sent this message did so from this geographic area; they sent messages from these five libraries so we know they're probably within X distance of these libraries" which is a hell of a lot easier to look for than "I can't even say what continent these messages originated from."
Let us say that you go to a library to log in to your protonmail account and email a journalist a link to a file that you've saved in cryptpad. You have the link written down so you don't have to go to a secondary site and you just go sit down directly at the computer and log in to protonmail and fire off your email to the journalist. The email is encrypted, so you know the contents of the email are safe. Let's say the browser history gets automatically wiped every time you close it, and you close it as soon as you stand up and walk away. Here's the incriminating information that generated:
IP address where you accessed your protonmail account
Your protonmail email address, the journalist's address, the time you sent the email, the subject line of the email
And here are the people who can be subpoenaed to share some or all of that information with the government:
The Library's ISP
The Library, who may not carefully track users but who do have event logs on the computers and traffic logs on the firewall
Protonmail
IF you only ever logged in to your protonmail account from that ISP one time, and if you've never logged in to your protonmail account anywhere that is close to your house or your job, you may be fine. But if you logged in to your protonmail on your personal cellphone at work so that you could send photos of documents to yourself, there's some data tying that account to a local IP address. If you set up the protonmail account on a whim at a coffee shop, there's some data tying that account to a local IP address. If you get an email back from the journalist and go to another local library to open it, there's some data tying that account to another local IP address.
And that gets narrowed down very quickly. "Who has access to these sensitive and leak-worthy documents through working at this entity who also lives within a 100 mile radius of these three login locations? Is it 50 people? Is it 5 people? Of the 15 people who have access to these sensitive and leak-worthy documents who work at this entity and live within 100 miles of the three login locations, who is likely to be doing the leaking? Do we fire them all? Do we interview them? Do we compare IP addresses that they've used to log in to work remotely and find that two of them have logged in at the coffee shop? Of those two, one has facebook selfies in a maga hat and the other has a less visible online presence. Let's check their traffic history. Did they check tumblr on a lunch break? Maybe once or twice? Maybe a few times? Sure seems like they are pretty dead-set against the administration. Let's double-check the access logs for this information. Let's review security footage. Let's install the monitoring on their workstation."
The thing is, they're not going to catch you leaking and then track down all the data you left behind to confirm it; they're going to see a leak and get a bunch of digital footprints and use that to narrow down suspect pools. They already know that access to the data is limited and will be reviewing prior access and carefully monitoring future access. You are already in their suspect pool by already being one of the people with known access to the data. Adding an IP address that is geographically close to you, even if it isn't your home IP address, to that is not going to make it *harder* to find you, it can only make it easier.
So just use Tor. You're safer using an anonymizer, which you likely can't do on a library computer. Create the leak email address when you're in a Tor browser, and only EVER access that email account from Tor.
Also I don't mean to jump on you about this, but between the post I've got about why you shouldn't use your work computer to torrent and the safer leaking practices post it's clear that people really don't understand what information they're leaving behind when they use computers and the internet, or how it can be a risk to them.
Accessing burner accounts from a clear IP address means that they're not burner accounts anymore, they're burned.
739 notes
·
View notes