#Iam Code 6
Explore tagged Tumblr posts
Text
Characters with wasted potential : kaminari Denki
I have never seen a series treat it's own electric/thunder user so badly like MHA does with denki kaminari.
Here is the thing kaminari is a pretty cool character; I like his character design and I think his character arc is alright but can use a lot of change.
In all honesty when it comes to kaminari I feel like his arc is literally supposed to be the same as mineta. Both of their arcs focusing on how they treat woman, them being cowards but growing out of it and learning how to be proper heros. However, when it comes to developments kaminari has his speed runned or just has him instantly change.
1) This is controversial but I personally would use have him be contrasted/foiled to mineta just to make his development more impactful.
2) I would have him show more of his cowardice and how he only really wanted to be a hero because its a cool thing to do or to follow in the footsteps of his mother (I would have pro hero Electra or just a simple electrician be his mother)
3) I would build up his friendship with jirou from the beginning and have both of them develop into better people/heroes with that friendship. (Maybe they can become a ship considering I do ship kamijirou 🤷♀️)
4) Emphasise the struggle kaminari has with his quirk (how quick he is to go overboard due to the lack of control) and how he tries to work to overcome it in his own unique way. I would have it so that his mum already helped him a bit by teaching him how to use his quirk in little amounts and big amounts but he struggles to get it into a medium range. I would also have him just experiment with it overall and maybe he could build a little friendship with Izuku or even mei who could introduce ideas like denki being able to act as a circuit, use tasers or even charge phones.
5) As kaminari gets to understand and become a better friend with jirou his views on mineta start to change and his whole views of "I have to go easy one girls" or " it's mean to fight girls like that" (something he said to bakugo during the sports festival) start to change as he grows respectful and becomes more appreciative to woman.
6) this is a 50/50 but I saw this one fic that said it would be cool if kaminari just started using flirting as a fighting tactic to fluster villains and easily take them down. That's something I kind of like and would be interesting to have incorporated into kaminari's character. You could have him work with midnight to build up a skill like that (would make midnight's death more impactful)
7) I feel like as it comes to the war arc his cowardice should logically still be there but the desire to help protect his friends and reunite with them should be stronger and we would still get the whole epic scene he had in the first war arc
8) have him canonically have ADHD it makes sense. I mean this is a universe just like ours the only thing different is superpowers and idk if I read his character wrong but to me kaminari has always given me the whole idea that he has ADHD or that his character is 'ADHD coded'. In my opinion it would be interesting for him to not really know why he struggles at doing something that everyone can find easy to do so when it comes to his grades he struggles in that aspect and has conflict because of that however, he can go through an arc realising that he has ADHD and find ways to both accept that and adapt to it (I don't know if that sounds rude, Iam sorry if it does)
9) I really like denki and jirou bonding over music and him actually respecting and liking her passion. I feel like we should get more of denki making music and exploring his more of his own passions. Like we know denki likes music and manga so why don't we have characters casually talking about that or doing that with him. I also like the idea of denki simplifying everything (like the UA security system) and making it seem like something that would come out of manga so he can understand it better









I feel like that kaminari could of been an interesting character with flawed views that end up developing. Ultimately, I feel like the reason I prefer him to mineta (even though they both act in a very disgusting Mannar towards woman) is that he shows chances of change and his character isn't just being a weird, disgusting pervert like mineta's is. To me kaminari could of been a coward kid who found it difficult to really fit in and do the things that everyone does but ultimately ends up overcoming that struggle while expanding his views and becoming a more respectful person.
#mha critical#bnha critical#hori is a bad writer#horikoshi critical#mha#bhna critical#denki kaminari#mha kaminari#bnha kaminari#kaminari x jirou
70 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Driving Innovation with AWS Cloud Development Tools
Amazon Web Services (AWS) has established itself as a leader in cloud computing, providing businesses with a comprehensive suite of services to build, deploy, and manage applications at scale. Among its most impactful offerings are AWS cloud development tools, which enable developers to optimize workflows, automate processes, and accelerate innovation. These tools are indispensable for creating scalable, secure, and reliable cloud-native applications across various industries.

The Importance of AWS Cloud Development Tools
Modern application development demands agility, automation, and seamless collaboration. AWS cloud development tools deliver the infrastructure, services, and integrations required to support the entire software development lifecycle (SDLC)—from coding and testing to deployment and monitoring. Whether catering to startups or large enterprises, these tools reduce manual effort, expedite releases, and uphold best practices in DevOps and cloud-native development.
Key AWS Development Tools
Here is an overview of some widely utilized AWS cloud development tools and their core functionalities:
1. AWS Cloud9
AWS Cloud9 is a cloud-based integrated development environment (IDE) that enables developers to write, run, and debug code directly in their browser. Pre-configured with essential tools, it supports multiple programming languages such as JavaScript, Python, and PHP. By eliminating the need for local development environments, Cloud9 facilitates real-time collaboration and streamlines workflows.
2. AWS CodeCommit
AWS CodeCommit is a fully managed source control service designed to securely host Git-based repositories. It offers features such as version control, fine-grained access management through AWS Identity and Access Management (IAM), and seamless integration with other AWS services, making it a robust option for collaborative development.
3. AWS CodeBuild
AWS CodeBuild automates key development tasks, including compiling source code, running tests, and producing deployment-ready packages. This fully managed service removes the need to maintain build servers, automatically scales resources, and integrates with CodePipeline along with other CI/CD tools, streamlining the build process.
4. AWS CodeDeploy
AWS CodeDeploy automates the deployment of code to Amazon EC2 instances, AWS Lambda, and even on-premises servers. By minimizing downtime, providing deployment tracking, and ensuring safe rollbacks in case of issues, CodeDeploy simplifies and secures the deployment process.
5. AWS CodePipeline
AWS CodePipeline is a fully managed continuous integration and continuous delivery (CI/CD) service that automates the build, test, and deployment stages of the software development lifecycle. It supports integration with third-party tools, such as GitHub and Jenkins, to provide enhanced flexibility and seamless workflows.
6. AWS CDK (Cloud Development Kit)
The AWS Cloud Development Kit allows developers to define cloud infrastructure using familiar programming languages including TypeScript, Python, Java, and C#. By simplifying Infrastructure as Code (IaC), AWS CDK makes provisioning AWS resources more intuitive and easier to maintain.
7. AWS X-Ray
AWS X-Ray assists developers in analyzing and debugging distributed applications by offering comprehensive insights into request behavior, error rates, and system performance bottlenecks. This tool is particularly valuable for applications leveraging microservices-based architectures.
Benefits of Using AWS Development Tools
Scalability: Effortlessly scale development and deployment operations to align with the growth of your applications.
Efficiency: Accelerate the software development lifecycle with automation and integrated workflows.
Security: Utilize built-in security features and IAM controls to safeguard your code and infrastructure.
Cost-Effectiveness: Optimize resources and leverage pay-as-you-go pricing to manage costs effectively.
Innovation: Focus on developing innovative features and solutions without the burden of managing infrastructure.
Conclusion
AWS development tools offer a robust, flexible, and secure foundation for building modern cloud-native applications. Covering every stage of development, from coding to deployment and monitoring, these tools empower organizations to innovate confidently, deliver software faster, and maintain a competitive edge in today’s dynamic digital environment. By leveraging this comprehensive toolset, businesses can streamline operations and enhance their ability to meet evolving challenges with agility.
0 notes
Text
Top 10 Cloud-Based Digital Transformation Strategies for Business Success in 2025

Introduction
In today's hyperconnected digital world, traditional enterprises are rapidly becoming obsolete. Cloud-based digital transformation is no longer an option; it's a must for companies that want to remain competitive, nimble, and customer-centric. In this article, we will look at the main strategies for driving cloud-based digital transformation in 2025, with a focus on practical measures, emerging trends, and how businesses may future-proof their operations with cloud technology.
What Is Cloud-Based Digital Transformation?
Cloud-based digital transformation is the process of leveraging cloud technologies to reimagine, digitize, and automate business operations. It enables companies to shift from legacy systems to flexible, scalable, and cost-effective cloud environments — supporting innovation and real-time collaboration across departments.
Businesses use cloud transformation to:
Replace outdated infrastructure
Enable remote work and mobility
Streamline operations through automation
Access data-driven insights in real time
Scale faster with reduced capital expenditure
1. Define a Cloud-First Business Vision
Transformation begins with clarity. Before adopting any tool or technology, define your business goals — whether it’s improving customer service, accelerating product delivery, or reducing operational costs.
Actionable Insight: Align cloud adoption with business outcomes. A strong vision ensures every cloud investment adds measurable value.
2. Migrate Core Systems Strategically
Not every system needs to move to the cloud all at once. Start with non-critical applications, then gradually move ERP, CRM, and internal tools.
Pro Tip: Use a hybrid approach where necessary, especially in regulated industries. Cloud migration should minimize downtime and avoid data loss.
3. Embrace Automation and AI-Powered Workflows
Cloud platforms enable seamless automation of repetitive tasks. Integrate AI and ML into your workflows to reduce manual effort and speed up decision-making.
Example: Automate employee onboarding, customer support ticket routing, and approval chains across departments using cloud-native tools.
4. Rebuild Internal Tools Using Low-Code Platforms
Tools like Microsoft Power Apps and ServiceNow App Engine allow businesses to create internal apps without heavy coding. These tools empower non-technical staff (citizen developers) to build custom workflows for HR, finance, IT, and more.
Result: Faster innovation, reduced IT backlog, and better cross-team collaboration.
5. Focus on Secure and Compliant Cloud Infrastructure
Security is a top concern when moving to the cloud. Implement strong identity and access management (IAM), data encryption, and compliance checks for GDPR, HIPAA, etc.
Smart Strategy: Use multi-factor authentication, zero-trust architecture, and continuous monitoring to protect sensitive business data.
6. Modernize Data Management and Analytics
With cloud storage and analytics platforms like Azure, AWS, or Google Cloud, you can process massive amounts of data faster and more accurately.
Business Impact: Real-time dashboards, predictive analytics, and customer behavior insights help teams make informed decisions.
7. Develop an API-First Approach
Ensure your cloud solutions and apps are interoperable. APIs (Application Programming Interfaces) allow different systems to talk to each other — speeding up integration and reducing complexity.
Practical Use: Connect HR systems with payroll, or CRM with marketing automation tools, all in real time.
8. Cultivate a Cloud-Savvy Workforce
People drive transformation — not just technology. Train your employees in cloud technologies, data tools, and agile practices.
Best Practice: Create cloud learning paths and encourage certifications in platforms like AWS, Azure, or ServiceNow.
9. Leverage Industry-Specific Cloud Solutions
Every industry has its own cloud-based transformation path. For example:
Healthcare: Cloud-based EMR, patient portals
Retail: Inventory automation, omnichannel analytics
Finance: Secure digital banking, fraud detection
Takeaway: Choose solutions tailored to your vertical for faster ROI and compliance readiness.
10. Partner with Cloud Transformation Experts
If in-house expertise is limited, collaborate with cloud consulting firms or managed service providers like Prophecy Technologies. With years of experience across industries, we help businesses design scalable architectures, implement cloud-native tools, and unlock digital agility.
Why it works: Expert guidance prevents common pitfalls and accelerates time to value.
Emerging Trends in Cloud-Based Digital Transformation for 2025
Generative AI Integration: Building smarter apps, content, and automation
Multi-Cloud Environments: Flexibility across providers like AWS, Azure, and GCP
Edge + Cloud Hybrid Models: Real-time insights with low latency
Sustainability-Driven Cloud Adoption: Energy-efficient cloud operations
Digital Twins: Simulating real-world processes in the cloud for better decision-making
Conclusion Cloud-based digital transformation is not a one-time endeavour; it is an ongoing process. Businesses that adopt a cloud-first strategy, invest in scalable platforms, and train their employees will prosper in the digital economy of 2025 and beyond. Prophecy Technologies specialises in leading businesses through all stages of their transformation, from planning and migration to automation and optimization. Whether you're a developing startup or a multinational corporation, our professionals design solutions that connect with your vision and produce tangible results. Are you ready to reinvent your business with the cloud? Let Prophecy Technologies assist you in developing a future-ready, cloud-powered enterprise
0 notes
Text
Top Cloud Security Challenges in 2025—and How to Solve Them
As cloud adoption accelerates in 2025, so do the complexities of securing cloud environments. From sophisticated threats to regulatory pressures and misconfigurations, organizations face a dynamic and evolving cloud security landscape. This blog explores the top cloud security challenges in 2025—and actionable strategies to overcome them.
1. Misconfigurations and Human Error
Challenge:
Despite advances in automation, cloud misconfigurations remain the leading cause of data breaches. These errors often arise from overly permissive IAM policies, unencrypted storage buckets, or default security settings left unchanged.
Solution:
Implement Infrastructure as Code (IaC) with security baked in.
Use automated cloud security posture management (CSPM) tools.
Regularly conduct compliance audits and red team assessments.
2. Identity and Access Management (IAM) Complexity
Challenge:
As organizations adopt multi-cloud and hybrid environments, managing identity and access across platforms has become increasingly difficult. Poorly managed IAM can lead to privilege escalation and lateral movement by attackers.
Solution:
Enforce least privilege access and zero trust principles.
Use federated identity and single sign-on (SSO).
Continuously monitor access with behavioral analytics.
3. Supply Chain and Third-Party Risks
Challenge:
In 2025, supply chain attacks have become more sophisticated, targeting third-party APIs, open-source software, and CI/CD pipelines integrated into cloud workflows.
Solution:
Perform SBOM (Software Bill of Materials) assessments.
Use runtime security tools to detect anomalous behavior.
Vet vendors with strict security SLAs and continuous assessments.
4. Data Residency and Compliance
Challenge:
Global data privacy regulations (like GDPR, CCPA, and new regional laws) impose strict controls on where and how data is stored. Multi-national businesses struggle to maintain compliance across jurisdictions.
Solution:
Use geo-fencing and cloud-native encryption with customer-managed keys.
Choose cloud providers that offer region-specific data control.
Automate data classification and policy enforcement.
5. Insider Threats
Challenge:
Insider threats—whether malicious or negligent—pose significant risks to cloud environments, especially where sensitive data and critical infrastructure are involved.
Solution:
Deploy User and Entity Behavior Analytics (UEBA).
Establish segregation of duties and audit trails.
Provide regular security awareness training.
6. API and Microservices Vulnerabilities
Challenge:
APIs and microservices are the backbone of modern cloud-native applications, but they expand the attack surface. Common issues include broken authentication, excessive data exposure, and lack of rate limiting.
Solution:
Use API gateways with integrated security policies.
Adopt OpenAPI/Swagger specifications to enforce standards.
Regularly scan APIs for OWASP Top 10 vulnerabilities.
7. Ransomware and Extortionware in the Cloud
Challenge:
Ransomware is evolving to target cloud workloads, backups, and even object storage. Attackers now combine encryption with data theft to pressure victims.
Solution:
Implement immutable backups and multi-versioning.
Use behavioral threat detection for unusual file access patterns.
Employ endpoint detection and response (EDR) across cloud workloads.
8. Inadequate Visibility and Monitoring
Challenge:
Cloud environments—especially multi-cloud—often suffer from fragmented logging and monitoring, creating blind spots for security teams.
Solution:
Centralize logs using SIEM/SOAR platforms.
Deploy cloud-native monitoring tools (e.g., AWS CloudTrail, Azure Monitor).
Enable real-time alerting with correlation rules and ML-based anomaly detection.
Final Thoughts
Cloud security in 2025 demands a proactive, layered, and automated approach. It’s no longer about protecting the perimeter—because in the cloud, the perimeter is dynamic, ephemeral, and everywhere.
Security leaders must focus on:
Automation and continuous compliance
Identity-first security
Unified monitoring and response
Secure software development lifecycle (SSDLC)
Ready to Secure Your Cloud Future?
Partner with cloud-native security platforms, invest in team education, and make security a shared responsibility across development, operations, and governance teams.
0 notes
Text
Security and Compliance in the Cloud: Best Practices for Modern Workflows
As businesses accelerate cloud adoption, security and compliance remain two of the most critical—and complex—challenges they face. Cloud environments offer flexibility, scalability, and cost savings, but they also require a new approach to protecting data, ensuring privacy, and meeting regulatory requirements.
In today’s fast-paced digital landscape, traditional security methods are no longer sufficient. Organizations must adopt cloud-native security practices and embed compliance into every stage of their workflow, from development to deployment.
This article explores the top best practices for maintaining robust security and achieving compliance in modern cloud-based environments.
The Cloud Security Landscape
Cloud security involves protecting data, applications, and infrastructure from internal and external threats. It encompasses everything from access control and data encryption to incident response and vulnerability management.
The shared responsibility model defines that while cloud providers (like AWS, Azure, or GCP) secure the infrastructure, organizations are responsible for securing their own data and workloads. That makes it vital for businesses to adopt proactive security strategies tailored for cloud environments.
Key Compliance Considerations
Compliance refers to adhering to regulatory standards and industry frameworks, such as:
GDPR (General Data Protection Regulation)
HIPAA (Health Insurance Portability and Accountability Act)
PCI DSS (Payment Card Industry Data Security Standard)
ISO/IEC 27001
SOC 2
Each regulation comes with specific requirements for how data is stored, processed, and protected—especially in the cloud.
Failing to comply can lead to legal consequences, financial penalties, and reputational damage. That’s why security and compliance must go hand-in-hand.
Best Practices for Security and Compliance in the Cloud
1. Implement Zero Trust Architecture
Adopt a Zero Trust model that assumes no user or system is inherently trusted. This involves:
Strict identity verification
Least privilege access
Micro-segmentation
Continuous monitoring
Zero Trust helps reduce the attack surface and prevents lateral movement in case of breaches.
2. Use Encryption Everywhere
Encrypt data at rest, in transit, and during processing using industry-standard protocols. Make use of:
Key Management Services (KMS)
Bring Your Own Key (BYOK) strategies
Hardware Security Modules (HSMs)
This ensures sensitive information remains protected, even if unauthorized access occurs.
3. Automate Compliance Monitoring
Manual compliance audits are time-consuming and error-prone. Use automated tools that continuously monitor and audit your cloud infrastructure for compliance against predefined frameworks.
Tools like AWS Config, Azure Policy, and third-party solutions such as Prisma Cloud or Dome9 can detect and remediate policy violations in real-time.
4. Secure the CI/CD Pipeline
Your development pipeline is a potential attack vector. Secure it by:
Scanning code for vulnerabilities (SAST/DAST)
Verifying container and artifact integrity
Enforcing code signing and access controls
Implementing secrets management
This ensures that security and compliance are integrated into your DevSecOps workflow from day one.
5. Regularly Audit Access Controls
Set up role-based access controls (RBAC) and enforce multi-factor authentication (MFA). Periodically review access logs to detect unusual activity and revoke unused permissions.
Use tools like IAM analyzers to maintain tight control over who can access what.
6. Perform Continuous Risk Assessments
Cloud environments are dynamic, which means your security posture can change quickly. Schedule regular penetration testing, vulnerability scans, and risk assessments to stay ahead of threats.
Integrate these insights into your incident response plans to be better prepared for emergencies.
7. Leverage Cloud-Native Security Services
Cloud providers offer robust native security services. Use them to your advantage:
AWS GuardDuty, Inspector, Security Hub
Azure Security Center
Google Security Command Center
These tools provide insights, threat detection, and compliance recommendations tailored to your environment.
How Salzen Cloud Supports Secure Cloud Transformation
At Salzen Cloud, we understand that cloud transformation is only as strong as the security that underpins it. Our cloud experts help enterprises integrate end-to-end security and compliance practices into their modern workflows, ensuring continuous protection, regulatory alignment, and peace of mind.
From secure cloud architecture to compliance automation and threat monitoring, we make sure every part of your cloud journey is built on a foundation of trust and control.
Final Thoughts
Security and compliance aren’t just checkboxes—they’re essential components of a successful cloud strategy. In the era of constant digital change, building secure and compliant workflows requires a proactive, automated, and integrated approach.
By following the best practices outlined above and partnering with experts like Salzen Cloud, organizations can ensure their cloud environments are not only high-performing—but also fully secure and compliant from the ground up.
0 notes
Text
Enhancing Security in Cloud-Native Applications: Key Strategies

In the evolving landscape of cloud-native applications, security is paramount. This article delves into essential practices that fortify security and resilience in cloud environments.
1.Robust identity and access management (IAM)
Implement role-based access control.
Adhere to the principle of least privilege.
Employ multi-factor authentication.
2. Securing application secrets
Securely store API keys, passwords, and certificates using secret management tools.
Rotate secrets routinely and automate this process.
3. Utilization of secure containers
Regularly update container images to mitigate vulnerabilities.
Select trusted base images and conduct vulnerability scans.
Operate containers with the minimal required privileges.
4. Network security implementation
Deploy firewalls and network segmentation to control traffic flow.
Use secure communication protocols like TLS for data in transit.
5. Compliance and auditing
Conduct regular audits of cloud resources and configurations.
Ensure adherence to industry standards and regulations.
6. Secure software development lifecycle (SDLC)
Embed security in the development process, embracing practices like DevSecOps.
Perform regular code reviews and utilize code analysis tools.
7. Automating security
Leverage automated tools for vulnerability monitoring and response.
Automate threat responses.
8. Backup and disaster recovery
Regularly backup data and establish a disaster recovery plan.
Periodically test backup and recovery procedures.
9. Staff education and training
Provide ongoing training on security best practices.
Foster a culture of security awareness.
10. Monitoring and threat response
Implement monitoring solutions for threat detection.
Develop a response plan for various security incidents.
Additional considerations:
Zero trust architecture: Treat every microservice with skepticism, avoiding blind inter-service trust.
Input validation: Rigorously validate and sanitize all inputs, treating them as potential threats.
Internet exposure control: Limit internet access to essential components using advanced firewall settings and VPCs.
Secure file storage: Encrypt sensitive data at rest and implement role-based access.
Log data masking: Employ automated redaction tools and centralized log management.
In today’s dynamic digital landscape, implementing these security practices is crucial, but it can be challenging to navigate the complexities alone. This is where Centizen Cloud Consulting Services comes in. Our expert team specializes in crafting bespoke cloud security strategies that align with your specific business needs. From initial assessment to implementation and ongoing management, we provide end-to-end support to ensure your cloud-native applications are not only secure but also optimized for performance and scalability. Partner with Centizen to transform these best practices into a robust, secure foundation for your cloud-native journey.
0 notes
Text
Key Benefits of Deploying Oracle WebCenter Content on Oracle Cloud Infrastructure (OCI)
In today’s digital-first world, managing enterprise content effectively is more critical than ever. Oracle WebCenter Content (WCC), a powerful content management platform, provides organizations with robust capabilities for document management, imaging, records retention, and digital asset management. When combined with the scalability and resilience of Oracle Cloud Infrastructure (OCI), the solution becomes even more compelling.
This blog explores the key benefits of deploying Oracle WebCenter Content on OCI, and how organizations can unlock greater agility, performance, and cost-efficiency.
🚀 1. Scalability and Elastic Performance
Deploying WCC on OCI allows businesses to scale resources based on workload demands. Whether you're serving a small team or an enterprise-wide rollout, OCI’s elastic compute and storage services can grow (or shrink) with your usage.
Auto-scaling compute instances
Flexible storage tiers (Object, Block, Archive)
Load balancers for high-throughput scenarios
Result: No more over-provisioning or under-performance issues—just right-sized infrastructure.
🔒 2. Enterprise-Grade Security
Security is a top priority for content platforms, especially when managing sensitive business documents and records. OCI delivers a defense-in-depth approach with built-in services to protect data and applications.
OCI Vault for key management and secrets
Identity and Access Management (IAM) with fine-grained policies
Virtual Cloud Network (VCN) for network isolation
Always-on encryption at rest and in transit
Result: Peace of mind knowing your content repository is protected by Oracle’s secure cloud foundation.
💡 3. Simplified Integration with Oracle Ecosystem
Oracle WCC integrates seamlessly with other Oracle products—like Oracle APEX, Oracle Fusion Apps, and Oracle Integration Cloud—especially when hosted on the same cloud platform.
Native OCI services make integration easier
Faster data movement between services
Unified support for Oracle stack components
Result: Accelerated time-to-value and smoother workflows across business processes.
💰 4. Optimized Cost Efficiency
OCI is known for its predictable pricing and lower total cost of ownership (TCO) compared to other major cloud providers. You pay only for what you use—without the "cloud tax."
Flexible billing models
Reserved compute options for long-term savings
Storage tiers tailored to content access patterns
Result: Maximize ROI while modernizing your content infrastructure.
🛠️ 5. Automation & DevOps Support
Deploying WCC on OCI opens the door to automation, faster updates, and streamlined lifecycle management through infrastructure-as-code and CI/CD pipelines.
Terraform support via OCI Resource Manager
CLI, SDK, and REST APIs for custom orchestration
Integration with tools like Ansible, Jenkins, and GitHub
Result Move away from manual provisioning and towards a DevOps-enabled, agile environment.
📈 6. High Availability and Disaster Recovery
OCI’s globally distributed regions and availability domains enable robust business continuity planning. Deploying WCC in a multi-region setup with automated backups and failover ensures maximum uptime.
OCI Block Volume and Object Storage replication
Backup & Restore options via OCI Backup service
Cross-region disaster recovery configurations
Result: Maintain business operations even during outages or data center issues.
🌍 7. Global Reach with Local Compliance
Whether you're a global enterprise or a regional business, OCI provides localized cloud regions to meet compliance, latency, and data sovereignty needs.
45+ cloud regions worldwide
Sovereign cloud options for public sector
Alignment with GDPR, HIPAA, and other regulations
Result: Meet compliance without sacrificing performance or agility.
✅ Conclusion
Oracle WebCenter Content remains a cornerstone for enterprise content management. By deploying it on Oracle Cloud Infrastructure, you can amplify its strengths while gaining access to modern cloud-native capabilities. From security and scalability to cost and compliance, the benefits of running WCC on OCI are clear and compelling.
Whether you're planning a migration or building a new content-centric application, OCI is the natural fit for Oracle WebCenter Content.
0 notes
Text
Cloud Security Coaching: Unlocking Excellence with Gritty Tech
Introduction to Cloud Security Coaching
In today's digital-first world, cloud computing is not just an advantage; it is a necessity. However, with the rapid adoption of cloud services comes the inevitable challenge of ensuring security. At Gritty Tech, we offer specialized Cloud Security Coaching to help individuals and organizations safeguard their cloud environments effectively. Our coaching services are designed to equip you with the skills, tools, and mindset necessary to navigate the complex cloud security landscape confidently For More…
Why Cloud Security Matters More Than Ever
The increasing migration to the cloud has opened new attack surfaces for cybercriminals. Traditional security models are no longer sufficient. Organizations need to adapt their security strategies to protect sensitive data, comply with regulations, and maintain customer trust. Gritty Tech's Cloud Security Coaching addresses these needs by providing real-world knowledge and actionable skills.
What is Cloud Security Coaching at Gritty Tech?
Cloud Security Coaching at Gritty Tech is a hands-on, practical training program designed to:
Build foundational and advanced cloud security skills
Identify and mitigate vulnerabilities
Implement best practices for cloud infrastructure protection
Ensure compliance with global standards and frameworks
Our approach is tailored to cater to beginners, intermediates, and experts, ensuring that everyone, regardless of their current level, can benefit.
Key Components of Our Coaching Program
1. Cloud Fundamentals and Security Concepts
We begin by laying a strong foundation in cloud computing concepts and the shared responsibility model. Understanding how cloud services operate and who is responsible for what is critical to designing secure environments.
2. Identity and Access Management (IAM)
IAM is the backbone of cloud security. At Gritty Tech, we delve deep into:
Principles of least privilege
Role-based access control (RBAC)
Identity federation
Single sign-on (SSO) integrations
3. Data Protection and Encryption
Data is the lifeblood of any organization. We teach:
How to encrypt data at rest and in transit
Key management services (KMS)
Data classification techniques
Secure backup and disaster recovery strategies
4. Network Security in the Cloud
The perimeter has shifted, and so must your defenses. Our coaching covers:
Virtual Private Clouds (VPCs)
Network segmentation
Firewall rules and security groups
Intrusion detection and prevention systems (IDS/IPS)
5. Secure DevOps Practices
Security must be integrated into every phase of the development cycle. We focus on:
Infrastructure as Code (IaC) security
Continuous Integration/Continuous Deployment (CI/CD) pipelines
Automated security testing
Secrets management
6. Compliance and Governance
Compliance is mandatory, not optional. Gritty Tech ensures you are well-versed in:
GDPR, HIPAA, PCI-DSS, ISO 27001 standards
Risk management frameworks
Audit preparation and reporting
7. Incident Response and Recovery
When breaches occur, preparation is key. Our modules teach:
Incident response planning
Threat detection and investigation
Forensics in cloud environments
Business continuity and disaster recovery planning
Unique Features of Gritty Tech's Cloud Security Coaching
Personalized Learning Paths: Every learner gets a customized coaching plan.
Real-World Simulations: Practice cloud attacks and defenses in controlled environments.
Mentorship by Experts: Our coaches are seasoned cloud security professionals.
Certification Preparation: We prepare you for certifications like AWS Certified Security, Azure Security Engineer, and Google Professional Cloud Security Engineer.
Lifetime Access to Resources: Once a learner, always a learner with Gritty Tech.
Who Should Enroll in Gritty Tech's Cloud Security Coaching?
Our coaching is ideal for:
IT professionals transitioning to cloud roles
Cybersecurity specialists
Cloud architects and engineers
Developers interested in secure coding
Organizations aiming to upskill their teams
Tools and Platforms Covered
We offer in-depth training across major cloud platforms including:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
Oracle Cloud Infrastructure (OCI)
Additionally, we integrate tools like Terraform, Kubernetes, HashiCorp Vault, and more.
Hands-On Labs and Real-World Projects
Theory alone isn't enough. Gritty Tech emphasizes:
Hands-on labs
Red team vs Blue team exercises
Capture the Flag (CTF) competitions
Real-world project implementations
These practical experiences ensure that learners not only know the theory but can apply it.
Success Stories
Thousands have benefited from Gritty Tech's Cloud Security Coaching. From Fortune 500 companies to tech startups, our alumni have secured prestigious positions and successfully fortified their cloud infrastructures.
How Gritty Tech Stays Ahead
The cloud landscape evolves rapidly. Gritty Tech continually updates its curriculum to include:
Latest threat vectors
New compliance requirements
Emerging best practices
Advances in cloud-native security tools
Certification Support
We provide end-to-end support for certifications including:
AWS Certified Security - Specialty
Microsoft Certified: Azure Security Engineer Associate
Google Professional Cloud Security Engineer
Certified Cloud Security Professional (CCSP)
Our coaches guide you through the exam objectives, mock tests, and study plans to ensure your success.
Flexible Learning Options
Gritty Tech offers:
Online Live Classes
Self-Paced Courses
Hybrid Models
On-site Corporate Training
Whatever your schedule or preference, we have a solution for you.
Pricing and Packages
Gritty Tech offers flexible packages to suit different needs:
Individual Packages: Perfect for personal development
Team Packages: Designed for corporate training
Enterprise Solutions: Customized programs for large organizations
Contact Gritty Tech directly for a detailed quote and package customization.
Frequently Asked Questions (FAQ)
What prior experience is required?
None. We offer beginner to advanced tracks, so you can start at your level.
How long does the coaching take?
Depending on the track, it can range from 4 weeks to 6 months.
Is there a certificate of completion?
Yes, Gritty Tech provides certificates and preparation for industry-recognized certifications.
Can I access the materials after the course?
Absolutely! You get lifetime access to course materials and updates.
What if I have questions outside class hours?
We provide 24/7 support through dedicated channels.
Final Thoughts: Why Choose Gritty Tech?
Cloud security is not just about technology; it's about mindset, vigilance, and continuous learning. Gritty Tech's Cloud Security Coaching delivers comprehensive, actionable training that transforms how you secure your cloud infrastructure.
When you learn with Gritty Tech, you're not just enrolling in a course; you're investing in a future where you are confident, capable, and ready to take on any cloud security challenge.
Get in touch with Gritty Tech today and start your journey toward becoming a cloud security expert!
0 notes
Text
The Power of Amazon Web Services (AWS): A Detailed Guide for 2025
Amazon Web Services (AWS) is the leading cloud computing platform, providing a wide range of services that empower businesses to grow, innovate, and optimize operations efficiently. With an increasing demand for cloud-based solutions, AWS has become the backbone of modern enterprises, offering high-performance computing, storage, networking, and security solutions. Whether you are an IT professional, a business owner, or an aspiring cloud architect, understanding AWS can give you a competitive edge in the technology landscape.
In this blog we will guide and explore AWS fundamentals, key services, benefits, use cases, and future trends, helping you navigate the AWS ecosystem with confidence.
What is AWS?
Amazon Web Services (AWS) is a secure cloud computing platform that provides on-demand computing resources, storage, databases, machine learning, and networking solutions. AWS eliminates the need for physical infrastructure, enabling businesses to run applications and services seamlessly in a cost-effective manner.
With over 200 fully featured services, AWS powers startups, enterprises, and government organizations worldwide. Its flexibility, scalability, and pay-as-you-go pricing model make it a preferred choice for cloud adoption.
Key AWS Services You Must Know
AWS offers a vast range of services, categorized into various domains. Below are some essential AWS services that are widely used:
1. Compute Services
Amazon EC2 (Elastic Compute Cloud): Provides resizable virtual servers for running applications.
AWS Lambda: Enables serverless computing, allowing you to run code without provisioning or managing servers.
Amazon Lightsail: A simple virtual private server (VPS) for small applications and websites.
AWS Fargate: A serverless compute engine for containerized applications.
2. Storage Services
Amazon S3 (Simple Storage Service): Object storage solution for scalable data storage.
Amazon EBS (Elastic Block Store): Persistent block storage for EC2 instances.
Amazon Glacier: Low-cost archival storage for long-term data backup.
3. Database Services
Amazon RDS (Relational Database Service): Fully managed relational databases like MySQL, PostgreSQL, and SQL Server.
Amazon DynamoDB: NoSQL database for key-value and document storage.
Amazon Redshift: Data warehousing service for big data analytics.
4. Networking and Content Delivery
Amazon VPC (Virtual Private Cloud): Provides a secure and isolated network in AWS.
Amazon Route 53: Scalable domain name system (DNS) service.
AWS CloudFront: Content delivery network (CDN) for fast and secure content delivery.
5. Security and Identity Management
AWS IAM (Identity and Access Management): Provides secure access control to AWS resources.
AWS Shield: DDoS protection for applications.
AWS WAF (Web Application Firewall): Protects applications from web threats.
6. Machine Learning & AI
Amazon SageMaker: Builds, trains, and deploys machine learning models.
Amazon Rekognition: Image and video analysis using AI.
Amazon Polly: Converts text into speech using deep learning.
Benefits of Using AWS
1. Scalability and Flexibility
AWS enables businesses to scale their infrastructure dynamically, ensuring seamless performance even during peak demand periods.
2. Cost-Effectiveness
With AWS's pay-as-you-go pricing, businesses only pay for the resources they use, reducing unnecessary expenses.
3. High Availability and Reliability
AWS operates in multiple regions and availability zones, ensuring minimal downtime and high data redundancy.
4. Enhanced Security
AWS offers advanced security features, including encryption, identity management, and compliance tools, ensuring data protection.
5. Fast Deployment
With AWS, businesses can deploy applications quickly, reducing time-to-market and accelerating innovation.
Popular Use Cases of AWS
1. Web Hosting
AWS is widely used for hosting websites and applications with services like EC2, S3, and CloudFront.
2. Big Data Analytics
Enterprises leverage AWS services like Redshift and AWS Glue for data warehousing and ETL processes.
3. DevOps and CI/CD
AWS supports DevOps practices with services like AWS CodePipeline, CodeBuild, and CodeDeploy.
4. Machine Learning and AI
Organizations use AWS AI services like SageMaker for building intelligent applications.
5. IoT Applications
AWS IoT Core enables businesses to connect and manage IoT devices securely.
Future Trends in AWS and Cloud Computing
1. Serverless Computing Expansion
More businesses are adopting AWS Lambda and Fargate for running applications without managing servers.
2. Multi-Cloud and Hybrid Cloud Adoption
AWS Outposts and AWS Hybrid Cloud solutions are bridging the gap between on-premise and cloud environments.
3. AI and Machine Learning Growth
AWS continues to enhance AI capabilities, driving innovation in automation and data processing.
4. Edge Computing Development
AWS Wavelength and AWS Local Zones will expand the reach of cloud computing to edge devices.
Conclusion
Amazon Web Services (AWS) is transforming how businesses operate in the digital era, providing unmatched scalability, security, and performance. Whether you are an enterprise looking to migrate to the cloud, a developer building applications, or a data scientist leveraging AI, AWS has a solution to your needs.
By mastering AWS, you can explore new career opportunities and drive business innovation. Start your AWS journey today and explore the limitless possibilities of cloud computing.
0 notes
Text

Sky's the Limit: Top Cloud Computing Careers to Watch in 2025
Cloud computing continues to grow rapidly, opening up a wide range of career opportunities in 2025. Here are some key career paths you might consider after gaining expertise in cloud computing:
1. Cloud Architect
Role: Design and oversee cloud strategy, ensuring solutions meet business needs and integrate well with existing systems.
Focus Areas: Multi-cloud strategies, cost optimization, scalability, and integration of legacy systems.
2. Cloud Engineer
Role: Develop, deploy, and manage cloud-based infrastructure and services.
Focus Areas: Automation, orchestration, and ensuring the efficient operation of cloud environments (e.g., AWS, Azure, Google Cloud).
3. DevOps Engineer
Role: Bridge the gap between development and operations to streamline software delivery using cloud platforms.
Focus Areas: CI/CD pipelines, containerization (Docker, Kubernetes), and infrastructure as code.
4. Cloud Security Engineer
Role: Protect cloud-based assets and data by designing secure architectures and managing compliance.
Focus Areas: Identity and access management (IAM), encryption, threat detection, and regulatory compliance.
5. Cloud Developer
Role: Build and optimize applications for cloud environments.
Focus Areas: Serverless computing, microservices architecture, API management, and cloud-native application development.
6. Cloud Data Engineer / Data Architect
Role: Develop and manage data solutions that leverage cloud-based platforms.
Focus Areas: Big data analytics, data warehousing, and real-time data processing in cloud ecosystems.
7. Cloud Consultant / Migration Specialist
Role: Advise organizations on cloud adoption and lead migration projects from on-premises to cloud.
Focus Areas: Assessing current infrastructure, planning migration strategies, and optimizing post-migration performance.
8. Cloud Operations / Site Reliability Engineer (SRE)
Role: Ensure the continuous, reliable operation of cloud services.
Focus Areas: Monitoring, incident response, and maintaining high availability and performance.
Emerging Trends and Specialized Roles
Hybrid & Multi-Cloud Management: As companies use multiple cloud providers, specialists in managing multi-cloud environments will be in high demand.
Edge Computing Integration: Roles focusing on integrating edge computing with cloud infrastructure will grow, especially in industries needing low-latency solutions.
Cloud AI/ML Specialist: Combining cloud computing with artificial intelligence and machine learning to develop advanced data-driven solutions.
Additional Opportunities
Cloud Product Manager: Oversee the development and lifecycle of cloud-based products, ensuring they meet market needs.
Cloud Sales & Marketing: With many organizations shifting to cloud, there’s a growing need for professionals who can bridge technical knowledge with business strategy.
Each of these roles leverages core cloud computing skills while also requiring continuous learning and adaptation to emerging technologies and industry trends. This field offers strong growth potential, competitive salaries, and opportunities to work across various industries.
1 note
·
View note
Text
Automation in DevOps (DevSecOps): Integrating Security into the Pipeline
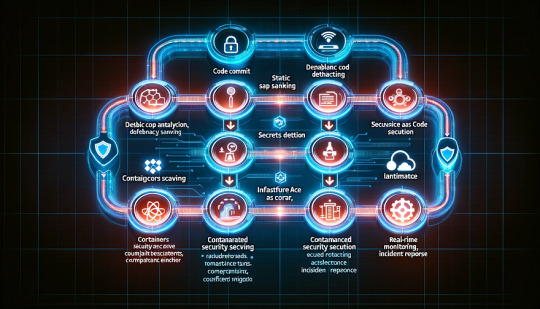
In modern DevOps practices, security can no longer be an afterthought — it needs to be embedded throughout the software development lifecycle (SDLC). This approach, known as DevSecOps, integrates security automation into DevOps workflows to ensure applications remain secure without slowing down development.
Why Security Automation?
Traditional security models relied on manual code reviews and vulnerability assessments at the end of the development cycle, often leading to bottlenecks and delayed releases. Security automation addresses these issues by: ✔️ Detecting vulnerabilities early in the CI/CD pipeline ✔️ Reducing manual intervention and human error ✔️ Ensuring continuous compliance with industry regulations ✔️ Improving incident response time
Key Areas of Security Automation in DevOps
1. Automated Code Security (Static & Dynamic Analysis)
Static Application Security Testing (SAST): Scans source code for vulnerabilities before deployment (e.g., SonarQube, Checkmarx).
Dynamic Application Security Testing (DAST): Identifies security flaws in running applications (e.g., OWASP ZAP, Burp Suite).
Software Composition Analysis (SCA): Detects vulnerabilities in third-party dependencies (e.g., Snyk, WhiteSource).
🔹 Example: Running SAST scans automatically in a Jenkins pipeline to detect insecure coding practices before merging code.
2. Secrets Management & Access Control
Automating the detection and handling of hardcoded secrets, API keys, and credentials using tools like HashiCorp Vault, AWS Secrets Manager, and CyberArk.
Implementing least privilege access via automated IAM policies to ensure only authorized users and services can access sensitive data.
🔹 Example: Using HashiCorp Vault to generate and revoke temporary credentials dynamically instead of hardcoding them.
3. Automated Compliance & Policy Enforcement
Infrastructure as Code (IaC) security scans using Checkov, OPA (Open Policy Agent), or Terraform Sentinel ensure that cloud configurations follow security best practices.
Automated audits and reporting help maintain compliance with GDPR, HIPAA, SOC 2, and ISO 27001 standards.
🔹 Example: Using Checkov to scan Terraform code for misconfigurations before provisioning cloud resources.
4. Container & Kubernetes Security
Scanning container images for vulnerabilities using Trivy, Aqua Security, or Anchore before pushing them to a registry.
Implementing Kubernetes security policies (e.g., Pod Security Policies, Kyverno, or Gatekeeper) to enforce security rules.
🔹 Example: Using Trivy in a CI/CD pipeline to scan Docker images before deployment to Kubernetes.
5. Continuous Security Monitoring & Threat Detection
Implementing SIEM (Security Information and Event Management) tools like Splunk, ELK Stack, or AWS Security Hub for real-time security event detection.
Using Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) (e.g., Snort, Suricata) to detect and respond to security threats.
AI-driven anomaly detection via Amazon GuardDuty, Microsoft Defender for Cloud, or Google Chronicle.
🔹 Example: Configuring AWS Security Hub to automatically detect and alert on misconfigurations in an AWS environment.
6. Automated Incident Response & Remediation
Using SOAR (Security Orchestration, Automation, and Response) platforms like Splunk SOAR or Palo Alto Cortex XSOAR to automate security incident triage and response.
Creating automated playbooks for threat mitigation, such as isolating compromised containers or blocking suspicious IPs.
🔹 Example: Automating AWS Lambda functions to quarantine an EC2 instance when an anomaly is detected.
Bringing It All Together: A DevSecOps Pipeline Example
1️⃣ Code Commit: Developers push code to a Git repository. 2️⃣ Static Code Analysis: SAST tools scan for vulnerabilities. 3️⃣ Dependency Scanning: SCA tools check third-party libraries. 4️⃣ Secrets Detection: Git hooks or automated scanners look for hardcoded secrets. 5️⃣ Container Security: Images are scanned before being pushed to a container registry. 6️⃣ Infrastructure as Code Scanning: Terraform or Kubernetes configurations are checked. 7️⃣ Automated Security Testing: DAST and penetration tests run in staging. 8️⃣ Compliance Checks: Policies are enforced before deployment. 9️⃣ Real-time Monitoring: Logs and security events are analyzed for threats. 🔟 Incident Response: Automated workflows handle detected threats.
Final Thoughts
Security automation in DevOps is critical for ensuring that security does not slow down development. By integrating automated security testing, policy enforcement, and monitoring, teams can build resilient, compliant, and secure applications without sacrificing speed.
WEBSITE: https://www.ficusoft.in/devops-training-in-chennai/
0 notes
Text
Cybersecurity Challenges and Solutions in the Age of AI and IoT
As the digital world becomes increasingly interconnected through Artificial Intelligence (AI) and the Internet of Things (IoT), cybersecurity risks are evolving faster than ever. From smart homes to industrial IoT systems, and from AI-powered chatbots to predictive analytics, our reliance on intelligent, connected technologies is exposing new vulnerabilities and attack surfaces.
In this blog, we’ll explore the top cybersecurity challenges in the era of AI and IoT and present practical, forward-thinking solutions to mitigate these risks—ensuring safer digital ecosystems.
The Expanding Threat Landscape
The fusion of AI and IoT is transforming industries, but it's also widening the attack surface. Every connected device and AI-driven system can become a target or even a weapon in cyberattacks.
Key Challenges:
Billions of connected IoT devices
Unpatched vulnerabilities in edge devices
AI systems used to automate cyberattacks
Data privacy concerns and regulatory pressure
Difficulty in real-time threat detection
Top Cybersecurity Challenges in AI and IoT
1. Massive Attack Surface
IoT devices, from wearables to smart appliances, are often deployed with minimal security. Their sheer volume makes them difficult to monitor and manage centrally.
2. AI-Powered Cyber Threats
Cybercriminals are using AI to:
Automate phishing attacks
Evade detection through intelligent malware
Analyze stolen data faster than before
This creates an arms race where defenders must match AI with AI.
3. Device Vulnerabilities
Many IoT devices are built without robust security protocols. Common issues include:
Hardcoded credentials
Outdated firmware
Weak encryption or no encryption
4. Data Privacy and Compliance
With AI systems processing vast amounts of personal and behavioral data, organizations must navigate regulations like GDPR, HIPAA, and CCPA to avoid breaches and fines.
5. Lack of Standardization
The IoT ecosystem lacks universal security standards. Device manufacturers often prioritize cost and speed to market over security, leading to fragmented and vulnerable deployments.
Cybersecurity Solutions for AI and IoT
While the risks are substantial, the following solutions can help build resilient and secure infrastructures.
1. Zero Trust Architecture
Adopt a Zero Trust model where every device, user, and application is continuously authenticated and monitored. This is critical in IoT ecosystems where network perimeters are blurred.
2. AI for Cyber Defense
Use AI not just as a threat, but as a solution:
Detect anomalies in network traffic
Automate incident response
Identify zero-day vulnerabilities through behavioral analysis
3. Firmware and OTA Updates
Ensure IoT devices support over-the-air (OTA) updates for timely patching. Regular updates close known vulnerabilities and reduce exploitation windows.
4. Strong Encryption Protocols
Enforce end-to-end encryption for data in transit and at rest. Utilize secure communication protocols like TLS, HTTPS, and WPA3 for device connectivity.
5. Device Identity and Authentication
Use robust identity and access management (IAM) for devices. This includes:
Unique digital certificates
Mutual authentication between devices and platforms
6. Security by Design
Encourage manufacturers to adopt security by design principles. This includes:
Secure boot processes
Secure coding practices
Built-in security hardware modules
Future-Proofing Cybersecurity
To stay ahead of threats in the AI and IoT era, organizations must invest in:
Security automation and orchestration
Real-time monitoring using AI and ML
Employee awareness and training
Vendor risk management
Integrating AI into cybersecurity operations isn’t optional—it’s essential for identifying patterns, reducing false positives, and responding quickly.
Conclusion
The convergence of AI and IoT is reshaping industries—but it also introduces new cybersecurity challenges that can't be ignored. To protect digital ecosystems in this hyperconnected era, organizations must move from reactive to proactive security postures.
Implementing AI-driven threat detection, enforcing Zero Trust principles, and securing IoT devices from the ground up are no longer best practices—they're necessities.
0 notes
Text
Security and Compliance in the Cloud: Proactive Approaches for Risk Management
As organizations embrace cloud computing to enhance scalability, flexibility, and cost efficiency, security and compliance have become critical priorities. A reactive approach to cloud security can expose businesses to data breaches, service disruptions, and regulatory penalties. The key to safeguarding operations lies in proactive cloud security strategies that align with modern compliance frameworks and business objectives.
At Salzen Cloud, we help businesses implement robust cloud security and compliance frameworks that not only protect infrastructure but also ensure operational excellence and audit-readiness.
The Evolving Security Landscape in Cloud Environments
Cloud environments offer agility, but they also introduce a broader attack surface. From misconfigured storage to unencrypted data flows and identity mismanagement, threats can originate from various vectors — especially in hybrid and multi-cloud setups.
Meanwhile, regulatory frameworks like GDPR, HIPAA, SOC 2, and ISO 27001 place strict requirements on how data is stored, accessed, and protected. Non-compliance can lead to financial penalties, reputational damage, or worse.
The challenge? Balancing security, compliance, and cloud agility.
Why Proactive Security and Compliance Matter
Reactive security — fixing problems after they arise — is costly and risky. A proactive approach means identifying vulnerabilities early, implementing controls before they’re needed, and continuously improving posture through monitoring and automation.
Here’s why proactive strategies are crucial:
✅ Prevent breaches before they happen
✅ Demonstrate compliance to regulators and customers
✅ Reduce downtime and recovery costs
✅ Enhance customer trust and data privacy
✅ Enable safe, fast innovation in the cloud
Key Pillars of Proactive Cloud Security and Compliance
🔐 1. Identity and Access Management (IAM)
Implement least privilege access, use multi-factor authentication (MFA), and automate credential rotation. Tools like AWS IAM, Azure Active Directory, and Google Cloud IAM provide granular access control for cloud resources.
🧾 2. Continuous Compliance Monitoring
Use compliance-as-code tools like Open Policy Agent, AWS Config, or Azure Policy to automatically detect and remediate violations of compliance policies in real time.
📊 3. Security Automation in CI/CD Pipelines
Integrate static code analysis, dependency scanning, and container image scanning into your CI/CD pipelines to catch vulnerabilities before deployment.
At Salzen Cloud, we integrate security into every stage of development — from code to cloud — through tools like Snyk, Checkmarx, and GitHub Advanced Security.
🔒 4. Data Encryption and Protection
Ensure encryption in transit and at rest using built-in cloud tools. Establish policies for data classification and apply tokenization or anonymization where appropriate.
👁️ 5. Continuous Threat Detection and Monitoring
Deploy cloud-native tools like AWS GuardDuty, Azure Sentinel, and Google Cloud Security Command Center for continuous threat intelligence and incident response.
📄 6. Audit Trails and Logging
Enable detailed logs for all cloud services using tools like AWS CloudTrail, Azure Monitor, and ELK stack. This ensures accountability and visibility for audits and investigations.
Salzen Cloud’s Approach to Security and Compliance
We go beyond checkboxes. At Salzen Cloud, we help enterprises build security-first cloud environments by:
Designing secure multi-cloud architectures
Implementing automated compliance workflows
Embedding security into CI/CD pipelines
Conducting vulnerability assessments and threat modeling
Ensuring alignment with frameworks like ISO 27001, SOC 2, PCI-DSS, HIPAA, and more
With Infrastructure as Code (IaC) and monitoring automation, we turn compliance into a repeatable, scalable process — not a last-minute scramble.
Final Thoughts
In the cloud, security and compliance are continuous journeys, not one-time milestones. By embedding proactive strategies across infrastructure, applications, and workflows, organizations can manage risk without slowing down inonvation.
With Salzen Cloud’s expertise, your team can move fast with confidence, knowing that security and compliance are built into every layer of your cloud stack.
0 notes
Text
Empower Your Business with Goognu’s Microsoft Azure Cloud Consulting Services

The cloud is no longer an option—it’s a necessity. Goognu’s Microsoft Azure Cloud Consulting Services offer businesses the expertise needed to migrate, optimize, and secure their cloud environments for maximum efficiency and cost-effectiveness. Whether you're new to Azure or looking to enhance your existing cloud strategy, Goognu provides tailored solutions that align with your business objectives.
Why Microsoft Azure for Your Cloud Infrastructure?
Microsoft Azure is a leading cloud platform known for its security, scalability, and comprehensive service offerings. Businesses that leverage Azure benefit from:
Scalability & Flexibility – Expand or scale down cloud resources on demand.
Robust Security & Compliance – Built-in security protocols protect sensitive data.
AI & Machine Learning Integration – Leverage data analytics for smart decision-making.
Hybrid & Multi-Cloud Capabilities – Seamlessly integrate on-premise infrastructure with cloud solutions.
Cost Optimization – Reduce operational expenses with pay-as-you-go pricing.
Why Choose Goognu’s Microsoft Azure Cloud Consulting Services?
At Goognu, we specialize in providing Microsoft Azure Cloud Consulting Services that empower businesses to optimize cloud operations while maintaining security and performance. Our expertise includes:
Certified Azure Experts – Deep knowledge of Azure architecture and best practices.
End-to-End Cloud Strategy – From planning and migration to optimization and security.
Industry-Specific Solutions – Customized cloud strategies for healthcare, retail, finance, and more.
Hybrid & Multi-Cloud Expertise – Integration across Azure, AWS, and Google Cloud.
24/7 Cloud Monitoring & Support – Ensuring uptime and performance excellence.
Our Comprehensive Azure Cloud Consulting Services
1. Azure Cloud Strategy & Planning
A successful cloud journey starts with a solid plan. Our experts:
Conduct in-depth cloud readiness assessments.
Develop a tailored Azure adoption roadmap.
Identify potential cost savings and security improvements.
2. Seamless Azure Cloud Migration
Migrate applications, databases, and workloads with minimal disruption. Our migration services include:
Lift-and-shift migration for rapid cloud adoption.
Application re-architecting for cloud-native solutions.
Data security & compliance alignment during migration.
3. Azure Cloud Optimization
Boost performance and efficiency while reducing costs. Our optimization services offer:
AI-driven workload analysis to improve resource allocation.
Automated scaling for peak and off-peak demand management.
Performance monitoring & proactive issue resolution.
4. Azure DevOps & Cloud Automation
Improve deployment speed and efficiency with Azure Cloud Consulting Services. Our solutions include:
CI/CD pipeline implementation for seamless application development.
Infrastructure as Code (IaC) for automated provisioning.
Integration with DevOps tools like Azure DevOps, GitHub Actions, and Terraform.
5. Azure Cloud Security & Compliance
Ensure end-to-end cloud security and compliance with Goognu’s consulting services. Our security measures include:
Identity and Access Management (IAM) solutions.
Advanced threat detection & real-time monitoring.
Regulatory compliance support for GDPR, HIPAA, and SOC 2.
6. Azure Cost Management & Optimization
Optimize cloud spending with cost-efficient solutions. We help businesses:
Identify underutilized resources and optimize consumption.
Implement cost governance policies for budget control.
Monitor cloud expenditures with real-time analytics.
Key Benefits of Goognu’s Microsoft Azure Cloud Consulting Services
Accelerated Cloud Adoption
Quickly transition to Azure with expert-led migration and strategy implementation.
Enhanced Business Agility
Adjust workloads and applications dynamically to meet business demands.
Robust Security & Compliance
Leverage Microsoft Azure Cloud Consulting Services to ensure top-tier security and regulatory adherence.
Cost-Efficient Cloud Operations
Optimize Azure’s infrastructure to minimize costs and maximize efficiency.
AI & Automation-Driven Performance
Streamline operations and improve decision-making with AI-powered cloud automation.
Real-World Success Stories
Case Study 1: Cloud Transformation for a Financial Firm
A global financial institution leveraged Microsoft Azure Cloud Consulting Services to modernize its IT infrastructure. Key outcomes:
40% reduction in operational costs through resource optimization.
Seamless migration with zero downtime.
Enhanced security posture using Azure’s built-in compliance tools.
Case Study 2: E-Commerce Performance Enhancement with Azure
A major e-commerce retailer partnered with Goognu to enhance cloud efficiency. Results included:
50% improvement in website load speeds with optimized Azure configurations.
Automated CI/CD pipelines, reducing deployment time by 60%.
Greater scalability ensuring seamless high-traffic handling.
Why Azure is the Future of Enterprise Cloud Computing?
As businesses accelerate digital transformation, Microsoft Azure Cloud Consulting Services are essential for:
AI & Data Analytics Integration – Gain actionable insights with Azure AI tools.
Hybrid & Multi-Cloud Strategy – Seamlessly integrate Azure with other cloud platforms.
Sustainable Cloud Solutions – Reduce environmental impact with energy-efficient cloud infrastructure.
Enterprise-Grade Disaster Recovery – Protect business continuity with Azure’s backup and recovery solutions.
Start Your Azure Cloud Transformation with Goognu
Are you ready to unlock the full potential of Microsoft Azure Cloud Consulting Services? Goognu is here to help you migrate, optimize, and secure your cloud environment for long-term success. Whether you are launching a new cloud initiative or refining an existing one, our experts will guide you every step of the way.
Contact us today for a free consultation and see how Goognu’s Microsoft Azure Cloud Consulting Services can drive your business forward.
0 notes
Text
Google Cloud Platform Coaching at Gritty Tech
Introduction to Google Cloud Platform (GCP)
Google Cloud Platform (GCP) is a suite of cloud computing services offered by Google. It provides a range of hosted services for compute, storage, and application development that run on Google hardware. With the rising demand for cloud expertise, mastering GCP has become essential for IT professionals, developers, and businesses alike For More…
At Gritty Tech, we offer specialized coaching programs designed to make you proficient in GCP, preparing you for real-world challenges and certifications.
Why Learn Google Cloud Platform?
The technology landscape is shifting rapidly towards cloud-native applications. Organizations worldwide are migrating to cloud environments to boost efficiency, scalability, and security. GCP stands out among major cloud providers for its advanced machine learning capabilities, seamless integration with open-source technologies, and powerful data analytics tools.
By learning GCP, you can:
Access a global infrastructure.
Enhance your career opportunities.
Build scalable, secure applications.
Master in-demand tools like BigQuery, Kubernetes, and TensorFlow.
Gritty Tech's GCP Coaching Approach
At Gritty Tech, our GCP coaching is crafted with a learner-centric methodology. We believe that practical exposure combined with strong theoretical foundations is the key to mastering GCP.
Our coaching includes:
Live instructor-led sessions.
Hands-on labs and real-world projects.
Doubt-clearing and mentoring sessions.
Exam-focused training for GCP certifications.
Comprehensive Curriculum
Our GCP coaching at Gritty Tech covers a broad range of topics, ensuring a holistic understanding of the platform.
1. Introduction to Cloud Computing and GCP
Overview of Cloud Computing.
Benefits of Cloud Solutions.
Introduction to GCP Services and Solutions.
2. Google Cloud Identity and Access Management (IAM)
Understanding IAM roles and policies.
Setting up identity and access management.
Best practices for security and compliance.
3. Compute Services
Google Compute Engine (GCE).
Managing virtual machines.
Autoscaling and load balancing.
4. Storage and Databases
Google Cloud Storage.
Cloud SQL and Cloud Spanner.
Firestore and Bigtable basics.
5. Networking in GCP
VPCs and subnets.
Firewalls and routes.
Cloud CDN and Cloud DNS.
6. Kubernetes and Google Kubernetes Engine (GKE)
Introduction to Containers and Kubernetes.
Deploying applications on GKE.
Managing containerized workloads.
7. Data Analytics and Big Data
Introduction to BigQuery.
Dataflow and Dataproc.
Real-time analytics and data visualization.
8. Machine Learning and AI
Google AI Platform.
Building and deploying ML models.
AutoML and pre-trained APIs.
9. DevOps and Site Reliability Engineering (SRE)
CI/CD pipelines on GCP.
Monitoring, logging, and incident response.
Infrastructure as Code (Terraform, Deployment Manager).
10. Preparing for GCP Certifications
Associate Cloud Engineer.
Professional Cloud Architect.
Professional Data Engineer.
Hands-On Projects
At Gritty Tech, we emphasize "learning by doing." Our GCP coaching involves several hands-on projects, including:
Setting up a multi-tier web application.
Building a real-time analytics dashboard with BigQuery.
Automating deployments with Terraform.
Implementing a secure data lake on GCP.
Deploying scalable ML models using Google AI Platform.
Certification Support
Certifications validate your skills and open up better career prospects. Gritty Tech provides full support for certification preparation, including:
Practice exams.
Mock interviews.
Personalized study plans.
Exam registration assistance.
Our Expert Coaches
At Gritty Tech, our coaches are industry veterans with years of hands-on experience in cloud engineering and architecture. They hold multiple GCP certifications and bring real-world insights to every session. Their expertise ensures that you not only learn concepts but also understand how to apply them effectively.
Who Should Enroll?
Our GCP coaching is ideal for:
IT professionals looking to transition to cloud roles.
Developers aiming to build scalable cloud-native applications.
Data engineers and scientists.
System administrators.
DevOps engineers.
Entrepreneurs and business owners wanting to leverage cloud solutions.
Flexible Learning Options
Gritty Tech understands that every learner has unique needs. That's why we offer flexible learning modes:
Weekday batches.
Weekend batches.
Self-paced learning with recorded sessions.
Customized corporate training.
Success Stories
Hundreds of students have transformed their careers through Gritty Tech's GCP coaching. From landing jobs at Fortune 500 companies to successfully migrating businesses to GCP, our alumni have achieved remarkable milestones.
What Makes Gritty Tech Stand Out?
Choosing Gritty Tech means choosing quality, commitment, and success. Here’s why:
100% practical-oriented coaching.
Experienced and certified trainers.
Up-to-date curriculum aligned with latest industry trends.
Personal mentorship and career guidance.
Lifetime access to course materials and updates.
Vibrant learner community for networking and support.
Real-World Use Cases in GCP
Understanding real-world applications enhances learning outcomes. Our coaching covers case studies like:
Implementing disaster recovery solutions using GCP.
Optimizing cloud costs with resource management.
Building scalable e-commerce applications.
Data-driven decision-making with Google BigQuery.
Career Opportunities After GCP Coaching
GCP expertise opens doors to several high-paying roles such as:
Cloud Solutions Architect.
Cloud Engineer.
DevOps Engineer.
Data Engineer.
Site Reliability Engineer (SRE).
Machine Learning Engineer.
Salary Expectations
With GCP certifications and skills, professionals can expect:
Entry-level roles: $90,000 - $110,000 per annum.
Mid-level roles: $110,000 - $140,000 per annum.
Senior roles: $140,000 - $180,000+ per annum.
Continuous Learning and Community Support
Technology evolves rapidly, and staying updated is crucial. At Gritty Tech, we offer continuous learning opportunities post-completion:
Free webinars and workshops.
Access to updated course modules.
Community forums and discussion groups.
Invitations to exclusive tech meetups and conferences.
Conclusion: Your Path to GCP Mastery Starts Here
The future belongs to the cloud, and Gritty Tech is here to guide you every step of the way. Our Google Cloud Platform Coaching empowers you with the knowledge, skills, and confidence to thrive in the digital world.
Join Gritty Tech today and transform your career with cutting-edge GCP expertise!
0 notes