#Web API Identity Authentication
Explore tagged Tumblr posts
Text
The Legal Effects of Employer Screening Without Using Criminal Record Lookup

In the modern workplace, employers must run extensive background checks on all new hires. This shields the business from possible legal repercussions while also assisting in ensuring worker safety. A Criminal Record Lookup is a vital component of background checks. We'll talk about the legal ramifications of not doing criminal record checks for hiring purposes in this blog article, as well as why it's so important for businesses to do so.
Let's first clarify what a criminal record check is. It is the procedure to obtain a person's criminal history that is accessible to the general public. Arrests, convictions, and sentences for both felonies and misdemeanors may be included in this data. Thanks to technological advancements, businesses may now obtain this data using Background Verification APIs, which improves the process' accuracy and efficiency.
Now, you might be wondering why running a criminal background check is so important. The possible legal repercussions of not doing so hold the key to the solution. Hiring someone with a criminal record exposes a firm to one of the biggest dangers, particularly if the illegal activity includes violence or fraud. The corporation may be held accountable for negligent hiring if a criminal history employee harms others or commits a crime there. A legal claim known as "negligent hiring" holds an employer accountable for the deeds of its workers if they knew or should have known about their risky inclinations.
On the other hand, running a Public Criminal Records check can also shield businesses from legal action. The employer won't be held accountable if a criminal recorded employee commits a crime outside of the workplace that has nothing to do with their duties. The criminal record check demonstrates that the business takes appropriate precautions to guarantee the security of its workers and clients.
Every company's hiring procedure has to include a criminal background check, since workplace safety and legal compliance are critical in today's society. To learn more call Authenticate at +1 833-283-7439 or visit:- www.authenticate.com!
#Background Checks for Landlords#Web API Identity Authentication#Identity Check API#Criminal Background Check#Background Check API Free
0 notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
Top Challenges Web Development Companies Solve for Growing Brands
As your business grows, so do the expectations from your website. It’s no longer just a digital brochure—it’s your sales engine, lead generator, support channel, and brand identity rolled into one. Yet, as demands increase, many companies begin facing technical, design, and strategic roadblocks that can stall momentum.
This is where a Web Development Company becomes an essential partner. From handling complex integrations to future-proofing your platform, development agencies specialize in solving challenges that in-house teams may not be equipped to manage at scale.
1. Scaling Website Performance Under Growing Traffic
A major concern for any growing brand is website performance. As user traffic spikes, especially during product launches or campaigns, slow page loads or downtime can cost conversions and damage trust.
Professional development companies address this by:
Optimizing server architecture
Implementing caching strategies
Using CDNs for faster content delivery
Migrating to scalable cloud environments like AWS or Azure
These technical improvements ensure your site remains fast and available—no matter how quickly your business scales.
2. Managing Complex Integrations Across Systems
Growth brings more tools into your ecosystem—CRM platforms, inventory management, analytics tools, payment gateways, and marketing automation systems. The challenge is making all these systems communicate efficiently.
Web development companies build robust APIs and custom integrations that:
Sync data across platforms in real-time
Improve backend workflows
Enable personalized user experiences
Reduce manual errors
This level of technical harmony allows businesses to automate operations and focus more on growth strategies.
3. Ensuring Security and Compliance
As your brand attracts more users, it also becomes a bigger target for cyber threats. Ensuring data protection and regulatory compliance becomes non-negotiable.
A development agency strengthens your security through:
SSL implementation
Secure login and authentication systems
Regular vulnerability scanning
Compliance with global standards (like GDPR, CCPA, HIPAA)
With increasing customer expectations around data safety, proactive security is one of the most critical areas that expert developers address.
4. Creating Seamless Multi-Device User Experiences
Today’s users interact with your brand across desktops, tablets, and smartphones. An inconsistent experience on any of these devices can lead to lost engagement and sales.
Development companies apply responsive design principles and rigorous cross-browser testing to deliver:
Consistent UI/UX across all screen sizes
Intuitive navigation and interaction models
Faster mobile performance
This ensures that whether your customer is shopping, booking, or reading your blog—they enjoy a seamless experience every time.
5. Handling Content Management and Workflow Bottlenecks
Growing brands often struggle with content management. Outdated CMS platforms or poor backend architecture make publishing, editing, or localizing content a painful process.
A web development partner can:
Customize or migrate your CMS to a more scalable platform (like WordPress, Webflow, or headless CMSs)
Streamline your editorial workflows
Enable role-based access and approvals
This boosts content efficiency and lets your team stay focused on brand messaging instead of technical hurdles.
6. Maintaining Brand Consistency During Expansion
As businesses expand into new markets or launch new services, it becomes challenging to maintain brand consistency across all touchpoints.
Web development companies address this with:
Design systems and reusable components
Scalable style guides
Modular content blocks that adapt to new campaigns
This approach keeps your digital presence uniform while supporting the flexibility your marketing team needs.
7. Driving Continuous Optimization
Growth isn’t just about adding new features—it’s about refining what already exists. Development partners continuously test, monitor, and iterate to improve:
Conversion rates
Page performance
Funnel drop-offs
Technical SEO
By using tools like heatmaps, A/B testing platforms, and performance trackers, they help brands evolve based on real user behavior, not guesswork.
Conclusion
As your brand scales, so do the complexities of your digital infrastructure. A growing business needs more than a basic website—it requires a platform that evolves alongside it. Whether it’s integrating systems, securing customer data, optimizing for mobile, or scaling performance, these challenges can’t be left to chance.
That’s why partnering with a Web Development Company is not just helpful—it’s a strategic necessity. With deep technical knowledge and a forward-thinking approach, they ensure your website not only keeps up with growth but actively drives it.
0 notes
Text
✅ PAN-Aadhaar Verification API: Streamline Compliance & Prevent Fraud
In today's digital landscape, verifying user identity quickly and accurately is essential for businesses operating in financial services, fintech, lending, insurance, and beyond. One key regulatory requirement in India is the linkage and verification of PAN (Permanent Account Number) with Aadhaar. The PAN-Aadhaar Verification API helps businesses meet this requirement with ease, speed, and security.
🔍 What is PAN-Aadhaar Verification API?
The PAN-Aadhaar Verification API allows businesses to verify whether a user's PAN is linked with their Aadhaar in real-time. This verification is conducted using government-approved data sources and ensures compliance with the latest KYC (Know Your Customer) and AML (Anti-Money Laundering) norms.
🚀 Key Advantages
1. Real-Time Verification
No more delays in manual checks. Get instant confirmation of PAN-Aadhaar linkage status for seamless user onboarding and transaction processing.
2. Government-Compliant
The API is aligned with regulatory standards, ensuring your business stays compliant with the latest income tax and KYC rules.
3. Bulk Verification Support
Need to verify thousands of users? The API supports high-volume, batch verification to save time and operational effort.
4. Fraud Prevention
Prevent identity fraud by verifying the authenticity of PAN-Aadhaar linkage before processing loans, payouts, or registrations.
5. Easy API Integration
The API is designed for fast integration with your platform—whether it's a mobile app, web portal, or internal system.
6. Cost-Efficient & Scalable
Automating verification reduces operational costs and scales effortlessly with your growing customer base.
💼 Who Should Use It?
NBFCs & Banks: For customer onboarding & loan disbursals
Fintech Platforms: For KYC and fraud checks
Insurance Providers: For policy issuance & verification
Payment Gateways: For user validation before transactions
HR & Payroll Firms: For employee onboarding & compliance
🔐 Why It Matters
The Indian government has made PAN-Aadhaar linkage mandatory for most financial and legal processes. Businesses that fail to comply risk penalties and operational disruptions. Automating this verification using a reliable API not only saves time but ensures regulatory compliance and data accuracy.
🌐 Conclusion
The PAN-Aadhaar Verification API is an essential tool for any digital-first business looking to streamline verification, reduce fraud, and ensure compliance. Whether you handle thousands of users or just a few, this API can greatly enhance your onboarding and KYC workflows.
Power your compliance with NifiPayments – Simple, Secure, Scalable. #DigitalIndia #PANVerification #AadhaarVerification #FintechSolutions #RegulatoryCompliance #NifiPayments #KYCAPI #APISolutions
0 notes
Text
What Comes Prebuilt in EasyLaunchpad: A Deep Dive into Features & Architecture

If you’re a .NET developer or startup founder, you’ve likely spent countless hours just getting the basics of your web app in place: login, admin dashboards, email systems, user roles, payments — the list goes on.
Now imagine you didn’t have to.
EasyLaunchpad is a complete .NET boilerplate designed to help you skip the time-consuming setup phase and go straight to building your core application logic. But unlike generic templates, it’s not just a UI skin or a half-done framework. It’s a full production-grade starter kit with everything you need seamlessly working together.
In this blog, we’ll break down what actually comes prebuilt in EasyLaunchpad and how the architecture helps you launch scalable, maintainable apps faster than ever before.
🔧 Why Boilerplate? Why Now?
Before diving into the tech, let’s align on the problem EasyLaunchpad solves:
Every time you start a new project, you repeat:
Configuring authentication
Setting up admin panels
Managing users and roles
Handling emails and templates
Integrating payments
Adding job scheduling and logs
EasyLaunchpad does all of this for you — so you don’t have to start from scratch again.
⚙️ Core Technologies Behind the Boilerplate
EasyLaunchpad is built with a modern and stable tech stack designed for production:
Layer and Techbology used:
Backend Framework — .NET Core 8.0 (latest LTS)
Language — C#
UI — Razor Pages + Tailwind CSS + DaisyUI
ORM — Entity Framework Core
Dependency Injection — Autofac
Background Tasks — Hangfire
Logging — Serilog
Templating Engine — DotLiquid (for email templates)
This foundation ensures that your app is fast, secure, scalable, and easy to maintain.
Let’s explore what comes ready-to-use as soon as you start your EasyLaunchpad project.
✅ Authentication (Email + Google + Captcha)
EasyLaunchpad includes secure login flows with:
Email-password authentication
Google OAuth integration
CAPTCHA validation during login/registration
You don’t need to spend days integrating Identity manually — just plug and play.
✅ Admin Panel (Built with Tailwind CSS + DaisyUI)
The admin panel is clean, responsive, and fully functional. It’s built using Razor views and styled with TailwindCSS and DaisyUI, giving you a modern UI that’s easy to extend.
Pre-integrated modules in the admin panel include:
User Management: View, add, deactivate users
Role Management: Basic role assignment and user filtering
Package Plans: Define product plans for sale
SMTP & Email Settings: Easily configure mail servers
Feature Settings: Enable or disable system options without touching code
✅ Email System with Templates (DotLiquid)
Forget the hassle of writing email logic from scratch. EasyLaunchpad includes:
Prebuilt transactional email templates (e.g., registration, password reset)
SMTP integration
Templating via DotLiquid, making it easy to insert variables and personalize content
All email dispatches are logged and tracked, so you never lose sight of what’s been sent.
✅ Queued Emails & Background Tasks (Hangfire)
Want to schedule tasks like email reminders or data syncs?
EasyLaunchpad uses Hangfire for:
Background job processing
Scheduled cron jobs
Retry logic for email dispatch and failed tasks
You can manage jobs through the Hangfire dashboard or extend it into your app logic.
✅ Logging with Serilog
Every serious app needs structured, searchable logs. EasyLaunchpad integrates Serilog for:
Real-time activity tracking
Error logging
Request/response data logging
This gives you full visibility into what’s happening in your app, both during development and in production.
✅ Stripe & Paddle Payment Integration
Monetizing your app? EasyLaunchpad includes out-of-the-box integration for:
Stripe
Paddle
You can configure:
Payment plans
One-time purchases
Trial periods
And manage all of it through the admin panel without coding custom APIs.
✅ Packages & Licensing Management
You can create, manage, and connect subscription packages via the admin dashboard.
Each package can be tied to payment providers and synced to your external website or product gateway, making EasyLaunchpad ideal for:
SaaS products
License-based tools
Tiered services
✅ Notifications System
Built-in support for system alerts and user notifications includes:
Inline admin messages
Success/failure alerts on actions
Extendable for real-time or email notifications
🧱 Architectural Design That Supports Growth
Beyond just features, the architecture of EasyLaunchpad is designed for maintainability, extensibility, and scalability.
🧩 Modular Structure
Each module (e.g., Auth, Payments, Email, Jobs) is built to be independently extendable or replaceable. This lets you:
Swap Stripe for PayPal
Replace DotLiquid with Razor templates
Add new modules like CRM or Analytics
📁 Clean Codebase Layout
plaintext
CopyEdit
/Controllers
/Services
/Repositories
/Views
/Models
The code is separated by responsibility, making it easy to onboard new developers or modify any layer.
🔌 Plug-and-Play Capabilities
Need to build your own modules? The boilerplate is interface-driven and uses Autofac for dependency injection, so you can override or extend any logic without rewriting core code.
🌐 Real Use Cases
Here are a few real-world examples of how EasyLaunchpad can be used:
🧠 AI Tools: Launch OpenAI-based chat tools with user plans & payments
💼 B2B SaaS: Create dashboards with multi-user access, logs, and subscriptions
🛠 Admin Systems: Quickly build portals for internal staff or clients
💸 Subscription Services: Monetize features via built-in plans & licensing
🧠 Final Thoughts
Most boilerplates are either too basic or too bloated. EasyLaunchpad hits the sweet spot — it’s production-ready, focused, and elegant.
Everything you’d normally spend 3–4 weeks building? Already done.
With the structure and flexibility of a custom-built project — but without the hassle — you’re free to build what really matters: your product, your logic, your innovation.
👉 Ready to dive in? Get your copy of EasyLaunchpad and start building today:🔗 https://easylaunchpad.com
0 notes
Text
How Digi Tweets is Transforming Digital Marketing for Small Businesses in Visakhapatnam
In today’s fiercely competitive digital world, small businesses in Visakhapatnam are no longer left behind. Thanks to Digi Tweets, a results-driven digital marketing agency, small and medium enterprises are now scaling new heights online. From enhancing visibility to increasing ROI through innovative strategies, Digi Tweets is becoming the backbone of digital marketing for small businesses in Visakhapatnam and has earned its place as a Top Digital Marketing Company in Vizag.
Empowering Local Brands with Tailored Digital Strategies
Digi Tweets understands that every business is unique. That’s why we customize digital marketing strategies to suit the specific needs of each client. Whether you run a retail shop in Dwarakanagar or a restaurant near Beach Road, our team crafts focused campaigns that deliver measurable results.
We blend local SEO, Google My Business optimization, geo-targeted ads, and hyper-local content marketing to ensure your brand reaches the right audience at the right time—further validating our recognition as a Top Digital Marketing Company in Vizag.
SEO That Puts Visakhapatnam Businesses on the Map
Our SEO experts are deeply familiar with Visakhapatnam’s business landscape. We don’t just use generic tactics; we optimize for region-specific search behavior. We help businesses rank higher by implementing:
Keyword-rich content marketing
On-page SEO with schema markup
High-authority backlinks from local directories and news portals
Location-based long-tail keywords like “best bakery in MVP Colony” or “interior designer in Gajuwaka”
As a result, clients not only improve their rankings but also witness a significant boost in foot traffic and online inquiries.
Social Media Marketing That Builds Community and Sales
Digi Tweets leverages social media platforms to build a strong digital identity for small businesses. From Instagram reels to Facebook carousel ads, we craft engaging content that converts. We specialize in:
Instagram strategy for product-based businesses
Facebook Ads with hyper-local targeting
Influencer marketing collaborations with city-based micro-influencers
WhatsApp Business API integration for better customer communication
Our comprehensive social media management services are designed to elevate your brand voice and increase customer interaction. This multi-platform approach helps brands create authentic connections, increasing both trust and transactions.
Affordable Yet Powerful Google Ads Management
We understand that small businesses run on tight budgets. That’s why our Google Ads campaigns are designed to deliver maximum ROI without burning your wallet. We do this through:
Laser-focused keyword research
Compelling ad copywriting
Geo-fencing techniques for local targeting
Regular A/B testing and optimization
From real estate consultants to local clinics, businesses across Visakhapatnam have seen up to a 400% increase in conversions using our performance-driven PPC services. This strategic depth is part of what makes Digi Tweets a Top Digital Marketing Company in Vizag.
Website Design That Converts Visitors Into Customers
At Digi Tweets, we believe that a website isn’t just a digital brochure—it’s a sales powerhouse. Our web design team in Visakhapatnam builds user-friendly, mobile-responsive websites that rank well and convert better. Key features include:
Fast-loading designs optimized for SEO
Integrated contact forms and WhatsApp chat buttons
Conversion-focused landing pages
E-commerce platforms with integrated payment gateways
With clean UI/UX and technical SEO baked into every page, our websites act as 24/7 sales agents. Coupled with services like social media marketing and management, the complete digital ecosystem supports your long-term business success.
Data-Driven Analytics and Reporting
What sets Digi Tweets apart is our commitment to transparency and performance tracking. We provide all clients with detailed analytics that reveal:
Traffic sources and visitor behavior
Keyword rankings and search visibility
Social media engagement rates
Conversion rates and campaign ROI
This data enables our clients to make informed decisions, optimize budgets, and plan future growth strategies with confidence. These capabilities reinforce why Digi Tweets continues to lead as a Top Digital Marketing Company in Vizag.
Local Influencer Campaigns That Drive Authentic Engagement
The power of local voices cannot be underestimated. Digi Tweets has built a network of trusted influencers from Visakhapatnam who help promote small businesses authentically. Whether it's a food blogger reviewing a new cafe or a lifestyle influencer showcasing local boutiques, we make sure your brand gets the attention and credibility it deserves.
Video Marketing and Reels That Go Viral
We help small businesses create short-form videos and reels that are high in quality and optimized for virality. With catchy scripts, motion graphics, and trending audio, we make sure your brand message reaches more people in less time.
Reels for product showcases
Animated explainer videos for services
YouTube Shorts for brand awareness
Customer testimonial videos
This powerful content format not only drives engagement but also increases social shares and brand recall, especially when combined with our SMM solutions.
Content Writing That Speaks Your Brand Voice
Words sell. Our in-house content team crafts SEO-rich content that educates, engages, and converts. Whether you need blog posts, website copy, or product descriptions, our writing enhances your brand’s visibility and authority. Our content strategy includes:
Topical blog posts optimized for long-tail keywords
Website content aligned with customer journey
Press releases for new launches and events
Email newsletters with high open rates
Every piece of content is designed with a single goal: to drive action—another reason why clients call us the Top Digital Marketing Company in Vizag.
Why Digi Tweets is the Go-To Digital Partner for Small Businesses in Visakhapatnam
Proven results with local case studies
Affordable plans tailored for startups and SMEs
Expertise in both English and Telugu content marketing
100% transparency with monthly reports
End-to-end digital services under one roof
From Kommadi to Gopalapatnam, we’ve helped dozens of brands rise from obscurity to online prominence. Our commitment to local growth, creative innovation, and measurable impact makes Digi Tweets the Top Digital Marketing Company in Vizag for ambitious small businesses.
#adspecialists#bestdmserviceinvizag#digitalgrowthjourney#digimarketingmadeeasy#growwithdigimarketing#digitalmarketingtips#contentcreatorslife#digitweets#smmcommunity
0 notes
Text
The Power of .NET: Building Scalable and Secure Applications
In today’s fast-evolving software industry, scalability and security are critical for the success of any application. Whether you're building enterprise-level software, cloud-based systems, or web applications, the .NET framework stands out as a robust solution. For aspiring developers looking to gain real-world skills, enrolling in the Best DotNet Training Institute in Hyderabad, Kukatpally, KPHB is an excellent step toward mastering this powerful technology stack.
Why .NET Is Trusted by Enterprises
.NET, developed by Microsoft, is a versatile and high-performance framework widely used for building scalable, maintainable, and secure applications. Its support for multiple programming languages, especially C#, gives developers the flexibility to work on different types of applications—desktop, web, mobile, and cloud-based. Moreover, the framework continues to evolve, with .NET Core and now .NET 6/7 offering cross-platform capabilities and improved performance.
Built for Scalability
Scalability is a crucial requirement for modern applications. .NET’s built-in support for asynchronous programming, load balancing, and cloud integration through Azure services makes it an ideal choice for businesses expecting to grow their user base. Features like dependency injection, modular architecture, and microservices support allow applications to be scaled up or down based on demand.
Strong Security Features
Security is another area where .NET excels. It offers built-in mechanisms like authentication, authorization, data encryption, and secure coding practices. With frameworks like ASP.NET Identity and integrations with OAuth and OpenID Connect, developers can build applications that are not only functional but also resistant to common threats and attacks.
Modern Development with .NET
With tools like Visual Studio, seamless GitHub integration, and strong support for RESTful APIs and gRPC, .NET enables developers to follow modern software practices. Continuous integration, automated testing, and containerization with Docker further enhance the development lifecycle, ensuring smooth deployment and maintenance.
Conclusion
.NET is a future-proof, enterprise-ready framework that empowers developers to build applications that are both scalable and secure. To gain hands-on experience and in-depth knowledge of the .NET ecosystem, join Monopoly IT Solutions Pvt. Ltd, A leading provider of career transformation and professional training in the software industry.
#best python training in Hyderabad#best python training in Kukatpally#best python training in KPHB#best python full stack training
0 notes
Text
Defending the Digital Frontier: Key Skills Validated by a Cloud Security Certification
In 2025, the cloud isn't just a technology; it's the new digital frontier, powering everything from innovative startups in Shela, Gujarat, to the mission-critical operations of global enterprises. However, with unprecedented scalability and agility comes a unique and complex set of security challenges. Protecting these dynamic, distributed environments demands a specialized skillset – one that traditional cybersecurity alone often cannot fully address. This is why a cloud security certification has become the gold standard, not just for demonstrating knowledge, but for validating the precise cloud security skills essential for defending this crucial digital landscape.
For professionals looking to build a resilient cloud security career, understanding the core and emerging skills required is paramount. This guide will delve into the critical cloud security skills that are highly valued by employers, explain how a cloud security certification validates these competencies, and highlight why these credentials are indispensable for safeguarding data and applications in the cloud era.
Why Specialized Cloud Security Skills Are Paramount
The intricacies of cloud computing necessitate a distinct approach to security, setting it apart from traditional on-premise models. Here’s why possessing specialized cloud security skills is non-negotiable:
Shared Responsibility Model: Unlike on-premise where organizations control everything, the cloud operates on a shared responsibility model. Understanding this model and knowing whose responsibility it is to secure what (e.g., the cloud provider secures the infrastructure, the customer secures data and configurations) is foundational.
Dynamic and Ephemeral Resources: Cloud environments are highly agile. Virtual machines, containers, and serverless functions are spun up and down rapidly, often automated. Security needs to be integrated into this dynamic flow, requiring skills in automation, Infrastructure as Code (IaC) security, and continuous monitoring.
Distributed Nature: Cloud services are distributed across regions and availability zones. Securing this vast, interconnected network requires different network security paradigms compared to a centralized data center.
Cloud-Native Services and Tools: Each cloud provider (AWS, Azure, GCP) offers a unique suite of security services and tools (e.g., AWS Security Hub, Azure Sentinel, Google Security Command Center). Proficiency in these specific tools is crucial for effective cloud defense.
New Attack Vectors: Cloud environments introduce new attack surfaces, such as misconfigured S3 buckets, insecure APIs, or compromised cloud credentials. Specialized skills are needed to identify and mitigate these specific threats.
Compliance in the Cloud: Regulatory frameworks like India's DPDPA, GDPR, and HIPAA apply to cloud data. Implementing and proving compliance in a dynamic cloud environment requires specific expertise.
Core Cloud Security Skills Validated by Certifications
Leading cloud security certifications are meticulously designed to validate a comprehensive array of cloud security skills that directly address the challenges above. These include:
Identity and Access Management (IAM): This is foundational. You'll master skills in managing user identities, defining roles and permissions, implementing multi-factor authentication (MFA), and ensuring the principle of least privilege across cloud resources. This includes understanding federated identity and integrating corporate directories with cloud IAM.
Network Security in the Cloud: Key skills include designing and securing Virtual Private Clouds (VPCs) or Virtual Networks (VNets), configuring network segmentation, implementing security groups and Network Access Control Lists (NACLs), setting up cloud-native Web Application Firewalls (WAFs), and securing connectivity via VPNs or direct connect services.
Data Protection and Encryption: Validated skills involve implementing encryption for data at rest (e.g., using Key Management Services like AWS KMS, Azure Key Vault, Google Cloud KMS) and in transit (e.g., TLS for API endpoints). Understanding data classification, data loss prevention (DLP) strategies, and secure data storage practices (e.g., secure S3 buckets) is paramount.
Logging, Monitoring, and Auditing: Proficiency in configuring cloud-native logging services (e.g., AWS CloudTrail, Azure Monitor, Google Cloud Logging), integrating with Security Information and Event Management (SIEM) systems, analyzing security logs, and setting up alerts for suspicious activity. Skills in continuous monitoring and threat detection are validated here.
Compliance and Governance: Cloud security certifications validate your ability to understand and implement security controls that meet various regulatory frameworks (like India's DPDPA, ISO 27001, SOC 2). This includes establishing security policies, conducting audits, and ensuring adherence to industry best practices and cloud security posture management (CSPM).
Incident Response and Forensics in the Cloud: Skills in detecting, analyzing, containing, eradicating, and recovering from cloud-specific security incidents. This involves understanding cloud-native forensic tools and processes for investigating breaches in a distributed cloud environment.
Application Security in the Cloud: Validated skills include securing cloud-native applications, understanding API security, securing serverless functions (e.g., AWS Lambda, Azure Functions), and implementing container security (e.g., Docker, Kubernetes).
Cloud Risk Management: Identifying cloud-specific risks, conducting threat modeling exercises for cloud deployments, and implementing appropriate mitigation strategies.
Beyond the Core: Emerging Cloud Security Skills Validated
As cloud technology rapidly evolves, so do the required security skills. Leading cloud security certifications increasingly incorporate and validate expertise in these emerging areas:
DevSecOps Automation: The ability to integrate security into every phase of the software development lifecycle (SDLC) within cloud environments. This includes skills in Infrastructure as Code (IaC) security, security automation tools (e.g., Terraform, CloudFormation), and embedding security into CI/CD pipelines.
Multi-Cloud and Hybrid Cloud Security: As organizations often use more than one cloud provider or integrate cloud with on-premise infrastructure, skills in securing diverse, heterogeneous cloud environments are critical.
AI/ML in Cloud Security: Understanding how Artificial Intelligence and Machine Learning are leveraged for advanced threat detection, anomaly analysis, and automating security operations within cloud platforms.
Serverless and Container Security: Specific expertise in securing these modern, highly scalable, and often ephemeral computing paradigms, which present unique security challenges compared to traditional virtual machines.
Cloud-Native Security Services: Deep proficiency in the rapidly expanding suite of security services offered by each major cloud provider (e.g., AWS WAF, Azure Firewall, Google Cloud Armor).
How Cloud Security Certifications Validate These Skills
A reputable cloud security certification serves as a robust validation mechanism for these essential cloud security skills through:
Rigorous Exam Blueprints: Certifications base their exams on meticulously defined blueprints that directly reflect industry-demanded skills and knowledge areas.
Performance-Based Assessments: Many advanced cloud security certification exams include hands-on labs or simulations, requiring candidates to demonstrate actual proficiency in configuring, troubleshooting, or deploying security controls in a live cloud environment. This is a critical differentiator.
Comprehensive Training Paths: Certification bodies and their authorized training partners offer structured cloud security training and cloud security courses designed to impart these skills, often including extensive lab work and real-world scenarios. EC-Council, for instance, emphasizes practical learning in their programs, such as the C|CSE (Certified Cloud Security Engineer), which includes significant lab components across multiple cloud providers.
Industry Recognition: When a cloud security certification is widely recognized, it means industry experts, employers, and recruiters trust that the certified individual possesses the validated skills to perform effectively.
Choosing the Right Cloud Security Certification to Validate Your Skills
Given the array of skills required, choosing the right cloud security certification is a strategic decision that depends on your current expertise and career aspirations. Whether you're aiming for a foundational understanding or deep specialization, there's a certification designed to validate specific competencies. For a comprehensive overview of the different credentials and their skill validations, exploring the ultimate guide to the best cloud security certifications in 2025 can provide invaluable insights, helping you to align your learning path with the most sought-after skills in the industry.
The Impact of Validated Skills on Your Cloud Security Career
Possessing validated cloud security skills through a cloud security certification has a profound impact on your career:
Increased Employability: You become a highly attractive candidate for roles where cloud security expertise is a prerequisite.
Higher Earning Potential: Employers are willing to pay a premium for certified professionals who can secure their critical cloud assets.
Ability to Tackle Complex Projects: Your validated skills enable you to confidently take on challenging cloud migration, deployment, and security projects.
Contribution to Organizational Resilience: You become a key player in defending your organization against sophisticated cloud-native threats, directly contributing to its business continuity and reputation.
Clear Career Trajectory: Certified skills provide a strong foundation for continuous learning and progression into more advanced and specialized roles within the cloud security career path.
Conclusion
In 2025, defending the digital frontier requires a specialized arsenal of cloud security skills. From mastering Identity and Access Management and network security in the cloud to understanding compliance and automating security controls, these competencies are vital for safeguarding modern digital infrastructure. A cloud security certification serves as the definitive validator of these crucial skills, proving to employers that you possess the practical abilities needed to excel. By strategically acquiring and validating these key cloud security skills, you position yourself at the forefront of a high-demand industry, ready to protect the most valuable assets in the digital age.
0 notes
Text
Face Match: The Future of Identity Verification Is Here
In today’s fast-paced digital world, verifying a person’s identity quickly and securely is more critical than ever. Whether it’s onboarding a new employee, authenticating a user during KYC, or reducing fraud in digital services, identity verification must be accurate, fast, and reliable. This is where face match technology steps in as a transformative solution.
Face match, also known as facial recognition or face verification, refers to the process of comparing a live image of a person's face with the photo on their official ID to verify if they are the same person. OnGrid’s Face Match Check enhances this process by not only ensuring visual similarity but also detecting real-time presence through advanced liveness detection.
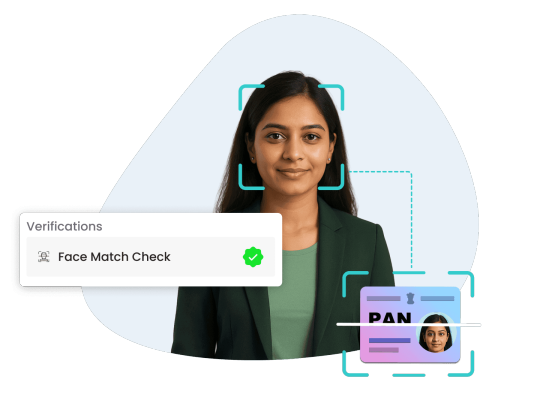
How Does OnGrid’s Face Match Check Work?
OnGrid’s Face Match Check is powered by advanced AI algorithms that compare the user's live selfie or video with their ID document photo. Here’s how it simplifies and strengthens the verification process:
Face Comparison: Matches facial features between a live image and the ID photo with high accuracy.
Liveness Detection: Ensures that the person is physically present and not using a static image, video spoof, or mask.
Real-time Results: Verification is completed instantly, enabling seamless onboarding or access control.
Scalable Integration: The service can be easily embedded into web or mobile platforms via API.
Why Businesses Are Adopting Face Match Verification
Face match technology has rapidly gained adoption across sectors like BFSI, HR tech, gig platforms, healthcare, and edtech. Here’s why:
Improved Security: It eliminates impersonation, identity theft, and document tampering by relying on real-time biometric verification.
Faster Onboarding: With instant facial recognition, users don’t need to visit physical offices or submit paperwork—everything happens online.
Regulatory Compliance: It supports compliance with KYC/AML regulations by verifying identities accurately and audibly.
User Convenience: A selfie is all it takes to verify identity—making the process user-friendly and contactless.
Use Cases of Face Match in Real Life
Digital KYC: Verifying users in financial services, lending platforms, or wallets.
Employment Verification: Ensuring that candidates' identities match submitted ID documents during background checks.
Gig Economy: Quickly verifying freelancers or delivery personnel without in-person interaction.
Access Control: Granting entry to physical or digital spaces only after identity is confirmed.
Why Choose OnGrid for Face Match Verification?
OnGrid brings its credibility as a trusted background verification and digital identity service provider in India. Its Face Match Check is:
Accurate: Built on strong AI and ML models trained on diverse datasets.
Secure: End-to-end encrypted with data privacy compliance.
Customizable: API-first design that integrates seamlessly into your workflow.
Conclusion
Face match technology isn’t just a digital convenience—it’s a necessity in a world where trust and verification go hand in hand. With OnGrid’s Face Match Check, organizations can make identity verification smarter, faster, and more secure.
#FaceMatch#IdentityVerification#DigitalOnboarding#LivenessDetection#KYC#FacialRecognition#OnGrid#SecureVerification#DigitalIdentity#BackgroundVerification#RealTimeVerification#ContactlessVerification#FaceMatchTechnology#AIinKYC#VerificationSolutions
0 notes
Text
Building the Future of Finance: A Comprehensive Guide to Fintech App Development

In an age of rapid digital transformation, financial services are being revolutionized by technology at an unprecedented pace. From mobile banking to AI-powered investment platforms, Fintech apps are reshaping how we interact with money. Whether you're a startup founder or a product manager at an established financial institution, understanding the core elements of fintech app development is critical to staying ahead.
This guide walks you through the key stages, challenges, and trends in building a successful fintech application.
Why Fintech Matters More Than Ever
The global fintech market is projected to reach $936 billion by 2030, driven by increasing demand for contactless payments, online lending, digital wallets, and crypto-based services. Consumers expect seamless, secure, and personalized financial experiences—creating both opportunity and pressure for fintech innovators.
Types of Fintech Applications
Before development begins, it’s important to define the niche your app will serve. Common categories include:
Mobile Banking Apps (e.g., Revolut, Chime)
Peer-to-Peer Payment Systems (e.g., Venmo, PayPal)
Investment & Trading Platforms (e.g., Robinhood, eToro)
Lending Platforms (e.g., LendingClub)
Personal Finance Management Tools (e.g., Mint, YNAB)
Insurtech Apps
Blockchain/Crypto Wallets & Exchanges
Key Features of a Successful Fintech App
To meet user expectations and regulatory standards, your app must offer:
Secure Authentication (Biometrics, MFA)
Real-Time Transaction Updates
Data Encryption & Protection
Regulatory Compliance (e.g., KYC, AML, PSD2)
User-Friendly Interface (UI/UX)
Integration with Banks and Payment Gateways
AI/ML for Personalization or Risk Assessment
Tech Stack for Fintech App Development
Here’s a typical stack to consider:
Frontend:
Frameworks: React Native, Flutter, Swift (iOS), Kotlin (Android)
Tools: Redux, Axios
Backend:
Languages: Node.js, Python (Django), Java (Spring Boot)
Databases: PostgreSQL, MongoDB
APIs: Plaid, Stripe, Paystack, Yodlee
Cloud Services: AWS, Azure, Google Cloud
Security:
OAuth 2.0
SSL/TLS Encryption
Tokenization
End-to-End Encryption
Regulatory & Compliance Considerations
Navigating legal regulations is crucial. Depending on your region and service type, ensure compliance with:
PCI DSS (for card payments)
GDPR/CCPA (data privacy)
KYC & AML (identity and fraud prevention)
PSD2/Open Banking Regulations (EU/UK)
Working with a legal advisor or compliance consultant during the early development stages is highly recommended.
Development Process in 6 Key Stages
Market Research & Ideation Validate your idea by studying user needs, competitors, and industry trends.
Prototyping & UX/UI Design Create wireframes and interactive prototypes to visualize the user journey.
Architecture & Tech Stack Planning Choose scalable, secure, and interoperable technologies.
Core Development Build frontend, backend, and APIs while adhering to secure coding practices.
Testing & QA Conduct unit tests, security audits, and user acceptance testing (UAT).
Deployment & Maintenance Launch on app stores or web, monitor performance, and roll out updates continuously.
Common Challenges in Fintech App Development
Ensuring High-Level Security
Complying with Complex Financial Regulations
Achieving Smooth Integration with Third-Party APIs
Building User Trust in Early Adoption
Scaling Infrastructure to Handle High Volume Transactions
Future Trends in Fintech Development
Stay ahead by exploring these emerging trends:
AI-Powered Financial Advisors (Robo-Advisors)
Decentralized Finance (DeFi)
Voice-Activated Banking
Biometric and Behavioral Security
Embedded Finance & Banking-as-a-Service (BaaS)
Final Thoughts
Fintech app development is more than just coding a payment feature—it’s about transforming the way people experience finance. With the right strategy, technology, and security approach, you can build applications that are not only functional but genuinely change lives.
Whether you’re creating a neobank or an AI-driven investment tool, success lies in combining innovation, compliance, and trust.
0 notes
Text
How APIs Power Modern Websites – A Think To Share IT Solutions Insight
Modern websites are no longer static brochures. They’re dynamic, data-driven platforms that interact with various services in real time. At the core of this interactivity lies a powerful and essential component: the API, or Application Programming Interface.
At Think To Share IT Solutions, we engineer websites that aren’t just visually compelling—they’re functionally superior, thanks to smart API integrations that enable real-time performance, seamless communication, and scalable features.
What is an API?
An API (Application Programming Interface) is a set of protocols and tools that allow software applications to communicate with each other. In web development, APIs act as bridges that connect your website to external or internal systems.
Instead of building every function from scratch, APIs allow developers to integrate existing, trusted services—making websites faster, more reliable, and more scalable.
How APIs Power Modern Websites
1. Dynamic Content Delivery
APIs allow websites to fetch and display real-time content from a database or CMS without refreshing the page. This improves performance and user experience.
Example: A blog or news portal pulling updated articles from a headless CMS like Strapi or WordPress via REST API.
2. User Authentication and Access Control
APIs handle secure user logins and permission-based access. Authentication services like Google OAuth or Auth0 rely entirely on API interactions.
Example: "Sign in with Google" uses an external API to verify the user's identity securely without storing sensitive data on your own servers.
3. Third-Party Service Integrations
APIs enable seamless integration with third-party platforms for added functionality.
Function
API Providers
Payments
Stripe, Razorpay, PayPal
Email Marketing
Mailchimp, SendGrid
Analytics
Google Analytics, Matomo
Customer Support
Zendesk, Intercom
Maps & Location
Google Maps API, Mapbox
These integrations enhance user experience without compromising performance or security.
4. Real-Time Features and Updates
Websites that support live chat, order tracking, or instant notifications use APIs to communicate with real-time databases.
Example: Firebase and Pusher APIs power real-time chat interfaces or live delivery status updates.
5. E-Commerce Functionality
Modern eCommerce websites rely on APIs to handle inventory updates, pricing changes, order processing, and shipping logistics.
What We Implement:
Cart management via REST or GraphQL APIs
Real-time pricing and availability updates
Shipment tracking using courier APIs (e.g., Delhivery, Shiprocket)
6. Headless Architecture
In a headless setup, APIs serve as the communication layer between the front-end and the back-end. This decoupling improves performance and allows for more flexible design and delivery across platforms.
Example: Using Next.js (for the front-end) and Strapi or Sanity (as the headless CMS), data is fetched via API endpoints and rendered statically or server-side for speed and SEO.
Benefits of API-Driven Web Development
Benefit
Explanation
Faster Deployment
Plug in pre-built services instead of coding everything from scratch
Scalability
Easily add new features or services without overhauling your system
Enhanced Security
Offload sensitive functions like payments to trusted platforms
Maintainability
Isolated services reduce complexity and ease troubleshooting
Cross-Platform
Share the same API with mobile apps, web apps, and IoT devices
How Think To Share Implements API-Driven Architecture
Our development process incorporates API planning from the very beginning:
Architecture Planning: Identify necessary APIs based on business goals
Security: Implement OAuth2, JWT tokens, and rate limiting for secure access
Performance: Use caching mechanisms (Redis, CDN) to reduce API load
Monitoring: Set up logging, error tracking, and fallback handling for resilience
Documentation: Provide detailed API docs using tools like Swagger or Postman
Final Thoughts: APIs Are the Backbone of Modern Websites
APIs have evolved from technical add-ons to mission-critical infrastructure for digital platforms. Whether you're running a website, mobile app, or enterprise software, APIs allow you to build faster, scale smarter, and connect deeper with users.
At Think To Share IT Solutions, we design and develop high-performance web systems that are modular, connected, and built for long-term growth—powered by reliable, secure, and well-integrated APIs.
0 notes
Text
What a Full-Stack Web Development Company Really Offers
In today’s fast-moving digital ecosystem, businesses don’t just need a website—they need a comprehensive digital solution that’s fast, functional, secure, and scalable. That’s where a Full-Stack Web Development Company comes in. From the moment your project is conceptualized to the final stages of deployment and beyond, a full-stack agency delivers an all-in-one solution for both the front-end and back-end of your digital presence.
Whether you’re launching a startup or scaling an enterprise product, understanding what these companies actually offer can help you make smarter, long-term decisions.
Front-End Development: Your Digital First Impression
The front end is what your users see and interact with—buttons, navigation, layouts, animations, and forms. A full-stack web development company ensures that your front end is not just beautiful but also functional across devices and browsers.
They work with technologies like:
HTML, CSS, JavaScript
Frameworks such as React, Angular, or Vue.js
UI/UX best practices for intuitive and accessible design
Beyond just building interfaces, they align your visual identity with usability. You get interfaces that convert, retain users, and reflect your brand story effectively.
Back-End Development: The Engine Behind the Experience
Behind every user action is a set of processes that connect your website to a server, database, or third-party service. That’s the back end, and it’s where a full-stack team shines.
They handle:
Server setup and database design
APIs and system integrations
Authentication and security layers
Logic for handling business operations (e.g., shopping carts, booking systems, dashboards)
By using powerful languages and frameworks like Node.js, Django, Laravel, Ruby on Rails, or .NET, full-stack developers ensure that your application is fast, secure, and scalable from day one.
Database Management: Organizing Your Digital Assets
Databases are essential for storing and retrieving user data, product information, analytics, and more. A full-stack web development company is adept at choosing and managing the right type of database for your project—whether it’s a relational database like PostgreSQL and MySQL or a NoSQL solution like MongoDB.
They not only build your data architecture but also manage:
Query optimization
Data backup and recovery
Scalable solutions for growing user traffic
This ensures your digital infrastructure remains agile and responsive even as your user base expands.
DevOps and Deployment: Going Live Smoothly
Launching a website isn’t as simple as clicking a button. A full-stack company also manages:
Continuous Integration/Continuous Deployment (CI/CD)
Server provisioning
Cloud hosting on AWS, Azure, or Google Cloud
Monitoring tools for uptime and performance
They streamline the process so your site not only launches smoothly but stays stable and updated post-launch.
Security & Compliance: Protecting What Matters
Security breaches can cost brands not just financially but reputationally. Full-stack web development companies implement proactive security measures:
SSL encryption
OWASP-compliant practices
Secure user authentication
GDPR and data protection compliance
With regular audits and automated security checks, they help you protect user data and avoid potential liabilities.
Maintenance & Scaling: Supporting Growth
Once the site is live, you’ll still need support. A professional full-stack company doesn’t walk away after deployment. Instead, it offers:
Ongoing performance monitoring
Bug fixes and upgrades
Server scaling
Feature enhancements
Whether you want to add a new product line, launch in a new country, or optimize your existing site’s speed, they’re your long-term partners in success.
End-to-End Consultation and Strategy
Beyond technical skills, what sets apart a true full-stack web development company is its ability to align tech with business strategy. They help you:
Define user personas
Map digital journeys
Prioritize features
Choose the right tools for your budget and scale
From MVP to enterprise product, your web partner acts as a digital co-pilot—helping you stay relevant in an ever-changing digital economy.
Conclusion
In essence, a Full-Stack Web Development Company offers far more than coding skills. It offers a strategic, end-to-end partnership to build, run, and grow your digital presence. From intuitive front-end experiences to robust back-end systems, database architecture, DevOps, and ongoing maintenance, a full-stack partner ensures that every layer of your website is aligned with performance and business outcomes.
If you're looking to build a resilient, future-proof digital platform, partnering with a Web Development Company that covers the full stack is one of the smartest investments you can make.
0 notes
Text
Empowering Seamless Banking with AEPS API by Nifi Payments
In a country like India, where a significant portion of the population resides in rural and semi-urban areas, access to banking services remains a challenge. To bridge this gap, Aadhaar Enabled Payment System (AEPS) has emerged as a game-changing innovation. With the AEPS API by Nifi Payments, businesses and fintech platforms can now offer secure, real-time banking services directly to customers through Aadhaar authentication.
What is AEPS?
Aadhaar Enabled Payment System (AEPS) is a government-backed initiative that allows customers to perform basic banking transactions using their Aadhaar number and biometric authentication. No debit card or passbook is required—just Aadhaar and a fingerprint.
Nifi Payments’ AEPS API enables service providers, retailers, and fintech platforms to integrate AEPS into their systems with ease, delivering convenient banking services at the last mile.
Key Features of Nifi Payments' AEPS API:
Real-Time Transactions Instantly process withdrawals, balance inquiries, and mini statements using Aadhaar credentials.
Secure Biometric Authentication Uses fingerprint or iris scan for authentication, reducing the risk of fraud and identity theft.
Supports All Major Banks Compatible with all AEPS-enabled banks under NPCI, ensuring broad coverage and interoperability.
Retailer-Friendly Dashboard Track AEPS transactions, commissions, and settlements easily through a robust web and mobile dashboard.
Developer-Friendly Integration Simple and secure API integration for mobile apps, POS devices, and web platforms.
24x7 Availability Allow customers to access banking services even during non-banking hours.
Services Supported via AEPS API:
Cash Withdrawal
Balance Enquiry
Mini Statement
Aadhaar to Aadhaar Fund Transfer
Authentication Service
Benefits for Businesses & Retailers:
✅ Expand Service Reach: Provide banking services to unbanked and underbanked customers ✅ Generate New Revenue Streams: Earn commissions on every AEPS transaction ✅ Build Trust: Become a trusted digital banking point in your community ✅ Enhance Financial Inclusion: Empower people in rural areas with easy access to banking
Use Cases:
Retail Shops and Kirana Stores becoming mini banking points
Fintech startups offering AEPS services via mobile apps
Rural BC agents facilitating cash withdrawals in villages
Delivery personnel collecting payments via AEPS on doorstep
Final Thoughts
The AEPS API by Nifi Payments is more than a technical solution—it’s a catalyst for digital empowerment. By enabling real-time, secure Aadhaar-based banking services, it brings the power of the bank to every doorstep, ensuring that financial inclusion is not just a goal, but a reality.
Empower your business and serve Bharat better – with AEPS API by Nifi Payments.
0 notes
Text
Unlock growth with custom web development solutions | ABK Data Lab!
In the current digital world, establishing a solid online presence is essential that optional. Companies with the aim of differentiating from their competitors must involve customers effectively and encourage long -term growth, which requires more than a simple website. This is where custom web development solutions become crucial.
Personalized web development goes beyond the platform templates and Plug-And-Play platforms. It implies the elaboration of personalized high performance applications that specifically meet their commercial objectives and customer needs. Whether it is a startup that seeks to launch its MVP or an established company with the objective of climbing, personalized solutions provide flexibility, scalability and uniqueness required to succeed.
Why choose personalized web development solutions?
While the templates and builders of prefabricated websites offer convenience, they often fall short of flexibility, performance and singularity of the brand. Personalized solutions, on the other hand, are built from scratch to align with their commercial requirements, processes and long -term objectives.

Personalized web development says:
A unique design that reflects the identity of its brand
Improved website performance and speed
IMPROVED SAFETY AND DATA PROTECTION
Flexibility to add new features over time
Full property of your code base
With a personalized approach, its digital product evolves as your company does, ensuring that your website is always aligned with its strategic objectives.
Key components of our custom web development services
In the center of our service there is a commitment to quality, scalability and innovation. We manage all stages of development, from the idea to the launch, with an expert developer, designers and project managers.
1. Receptive design for all devices
In a world where more than 50% of web traffic comes from mobile devices, the response capacity is not optional, it is essential. Our team ensures that its website is seen and functions without problems in desks, tablets and smartphones. A receptive design not only improves user experience, but also improves SEO classifications and accessibility.
2. Border Development with React.js
We use React.js, one of the most powerful and widely adopted Frontend libraries, to build fast, interactive and easy to use interfaces. REACT allows us to create reusable components and maintain high performance, even as its scale application. With its virtual DOM and its efficient update representation, ReACT guarantees an optimal user experience.
3. Backend development with Django/python
In the Backend, we trust the power and elegance of Django and Python. Django's robust architecture allows rapid development while maintaining high security standards. From user authentication management to database management, Django offers the stability and structure necessary to build complex web applications.
4. Design and optimization of the database
Each powerful web application needs a well structured and optimized database. Our team designs scalable database schemes adapted to your data needs, whether you are working with SQL (Postgresql, MySQL) or NOSQL (Mongodb). We ensure the rapid performance of the consultation and integrity of the data while preparing for future growth.
5. API development and integration
Modern web applications are interconnected systems. We create API Restoful and Graphql that allow an exchange of data without problems between their border and backend systems. We also integrate third -party services, such as payment catwalks, CRMS and social platforms to extend the functionality of its application.
Personalized web development benefits
Here are eight key benefits that make personalized web development an intelligent investment for companies with a future vision:
✓ Managed to your business
Custom web solutions are created around their commercial model, objectives and unique user base, ensuring optimal performance and customer satisfaction.
✓ Scalability
As your business grows, your application can also. Personalized platforms are designed to evolve without complete reviews.
✓ Improved security
Unlike massive market platforms, personalized applications can be strengthened with advanced safety protocols suitable for your industry.
✓ Lowering performance
Personalized applications can be optimized for speed and response capacity, reducing rebound rates and improving user participation.
✓ Complete control over the characteristics
You decide what happens in your application. This flexibility allows you to prioritize the characteristics that matter its users most.
✓ Better SEO integration
From the clean code to the optimized site structures, the personalized development provides a friendly base for the SEO that increases its visibility in the search engines, especially when guided by experienced in SEO specialist in Kerala.
✓ Third parties integration
Do you need to integrate a CRM, ERP or specific payment payment system? Personalized development guarantees perfect connectivity.
✓ Competitive advantage
A unique digital product distinguishes its crowd brand, increasing trust and loyalty among customers.
Who can benefit from personalized web development?
Personalized web development is not limited to new technological companies or Fortune 500 companies. It benefits a wide range of industries and organizations, including:
Electronic commerce companies that seek to provide a personalized purchase experience
Medical care suppliers needing patient insurance portals
Educational institutions that deliver interactive learning platforms
Financial services that require protection and compliance with solid data
Non -profit and NGO organizations with the aim of involving users and donors efficiently
Whether you are looking to automate internal operations or provide a next level user experience, a custom web solution is your best option.
Our development process: from the concept to launch
We believe in a collaborative and transparent process that keeps it in the loop in every step of the road. This is how we give life to your vision:
Discovery and Planning: We begin by understanding their commercial objectives, user needs and technical requirements.
UI/UX design: Our designers create intuitive and attractive interfaces that are aligned with their brand.
Development: Using agile methodologies, we create its application in iterations, ensuring quality and adaptability.
Tests and QA: We rigorously prove your web application for performance, safety and usability on all devices.Implementation and support: Once everything is perfect, we launch its application and provide continuous support to guarantee continuous success.

Conclusion
ABK Data Lab: Custom web development solutions provide versatility, performance, and long-term value that cannot match pre-made platforms. By investing in an analog digital experience, you strengthen your business to innovate, scale, and give better services to your customers. With our expert team and a proven development process, we convert your vision into a powerful, responsible, and safe web application that supports every step of your development.
Therefore, whether you are building a customer portal, an e-commerce platform, or a data-operated dashboard, choose custom web development solutions that are unique and ambitious as your business.
#custom web development solutions#custom web development#custom web development solutions kerala#custom web development kerala#custom web development in kerala#web development#web development in kerala#web development india#web development world wide#html#css#seo#seo in kerala#seo in india#seo kerala#SEO specialist in Kerala#SEO specialist#seo expert kerala#SEO#search engine optimisation#SEO Specialist#WordPress Developer#expert developer#Django#Python#ABK Data Lab#e-commerce#e commerce solution#CRMS#cms
0 notes
Text
Admin Permissions For EMR Studio AWS With Examples

AWS Documentation Essential IAM Administrators' EMR Studio Permissions
AWS EMR Studio Admin Permissions
Amazon Web Services documentation describes the IAM privileges administrators need to create and manage Amazon EMR Studio installations. AWS accounts need appropriate permissions to access EMR Studio resources safely and securely. The documentation helps administrators set up IAM policies for EMR Studio management access.
Running an EMR Studio requires certain IAM permissions for critical tasks. Administrators require elasticmapreduce permissions for normal tasks, especially without IAM Identity Centre authentication. EMR Studio creation requires the “elasticmapreduce:CreateStudio” permission.
The “elasticmapreduce:DescribeStudio” permission is needed to investigate a Studio's settings or status. Administrators need the “elasticmapreduce:ListStudios” access to see all EMR Studios in their account. Deactivating a Studio requires the “elasticmapreduce:DeleteStudio” access. In addition to these EMR-specific tasks, the handbook emphasises that Studio creation requires “iam:PassRole” access. The EMR service needs this permission to assume the Studio's service role and user role to communicate with other AWS services on behalf of the user or Studio.
Importantly, the handbook states that EMR Studios using IAM Identity Centre authentication require specific rights. These additional permissions' main duties are managing Studio Session Mappings, which control how users and groups authenticated through IAM Identity Centre can access and interact with the EMR Studio and the AWS IAM Identity Centre (formerly known as AWS SSO) and related directory services.
EMR Studio in IAM Identity Centre mode requires more complex permissions and actions to restrict user and group access. Individuals or groups are assigned to Studios using permissions from many AWS services.
These include “sso:AssociateProfile”, “sso:CreateApplicationAssignment”, “sso-directory:SearchUsers”, and “sso:DescribeUser” as well as rights like “elasticmapreduce:CreateStudioSessionMapping”. Also included in the assignment operations list are organisations and iam, with permissions like “organizations:DescribeOrganization” and “iam:ListPolicies”.
To retrieve user or group assignments, permissions like “elasticmapreduce:GetStudioSessionMapping” are needed. SSO-directory actions (“sso:SearchUsers” and “sso:DescribeUser”) and sso actions (“sso:DescribeApplication”) are also needed. Users and groups assigned to an EMR Studio are listed using “elasticmapreduce:ListStudioSessionMappings”. “elasticmapreduce:UpdateStudioSessionMapping” and sso-directory and sso privileges like “sso:SearchUsers”, “sso:DescribeApplication”, and “sso:DescribeInstance” are needed to alter a user or group's session policy.
Finally, deleting a Studio user or group requires permissions from sso-directory (“SearchUsers”, “DescribeGroup”), elasticmapreduce (“DeleteStudioSessionMapping”), and sso.
The AWS documentation provides sample IAM policies for both traditional IAM authentication and IAM Identity Centre authentication to help administrators set up these permissions. These images help create distinctive policies.
Administrators should fill out policy templates with their account and resource details. The placeholder values for the AWS Region code where the Studio will be placed, the AWS account ID, the Amazon Resource Name (ARN) of the object or objects the policy statement covers, and the EMR Studio service role and user role names must be changed.
Resource descriptions for service activities are vital to documentation, notably for the IAM Identity Centre sample policy. Identity Centre and Identity Centre directory APIs do not permit naming ARNs in IAM policy statements' “Resource” section, according to the specification.
In the sample policy for IAM Identity Centre mode, the “Resource” element is set to “” for sso and sso-directory service activities, authorising these actions across all resources those services support. The policy can be applied to Studio ARNs (e.g., “arn:aws:elasticmapreduce:\region>::studio/”) or role ARNs (e.g., “arn:aws:iam:::role/\EMRStudio-Service-Role>”) to allow elasticmapreduce activities. These services can be controlled more precisely at the resource level.
After customising an IAM policy with these permissions, it must be linked to the right IAM identity. This IAM user, role, or group receives policy permissions. This final stage activates EMR Studio administration tools. The detailed permissions show how important granular access control is to AWS services like EMR Studio, especially when integrated with identity management tools like IAM Identity Centre.
#EMRStudio#IdentityandAccessManagement#AWSservices#IAMIdentityCentre#IAMpolicy#AmazonResourceName#IAMIdentityCentremode#technology#technews#technologynews#news#govindhtech
0 notes
Text
Beyond Firewalls: What True End-to-End Cybersecurity Looks Like Today

In a world where digital transformation is no longer optional, cybersecurity has become the backbone of any successful business. And yet, many companies still approach it like a patchwork a firewall here, some antivirus software there, and a few compliance checkboxes ticked. But today’s threat landscape is far too complex for that kind of fragmented thinking.
At NetObjex, we believe cybersecurity must be built into the DNA of your digital operations not added as an afterthought. That’s what true end-to-end cybersecurity is all about. It’s not just about stopping threats at the door; it’s about securing every layer of your digital ecosystem, from edge devices to the cloud.
What Does “End-to-End” Really Mean?
“End-to-end” means comprehensive. It means you're not only protecting what’s visible — like your company’s website or internal server — but also what’s often overlooked: connected devices, APIs, mobile endpoints, backend data flows, and third-party integrations.
Let’s break that down:
Endpoint Protection: Every laptop, mobile device, or IoT sensor is a potential entry point for attackers. Securing these ensures that threats are blocked at the source.
Network Security: From VPNs to firewalls and intrusion detection systems, your internal communications should be monitored and encrypted.
Cloud Security: As more businesses move their data and apps to the cloud, secure configurations, identity access management, and encryption protocols become crucial.
Application Security: Vulnerabilities in your codebase — whether web or mobile — can be exploited if not rigorously tested and updated.
Data Protection: Whether data is at rest, in transit, or being processed, it should remain encrypted and inaccessible to unauthorized eyes.
Each layer must not only be secured but also intelligently connected — so that if something suspicious happens in one part of your system, the rest can respond in real time.
The Problem With the Old Way of Thinking
For years, businesses were instructed to "secure the perimeter." Firewalls were the initial and sometimes sole point of defense. But now, the perimeter no longer exists. Due to remote work, mobile devices, and cloud services, your data's everywhere — so are the threats.
Attackers are smarter, faster, and more relentless. Social engineering, phishing, ransomware, and advanced persistent threats don’t always knock at the front door. They find the weakest link — often a human one — and work inward.
That’s why relying solely on firewalls or antivirus software is like installing a steel door on a house with no windows.
How NetObjex Delivers True End-to-End Security
At NetObjex, we approach cybersecurity as a holistic system, not a toolkit. Here’s how we put that philosophy into action:
1. Edge-Level Protection with Smart Devices
Our IoT infrastructure ensures that devices are authenticated, data is encrypted at the edge, and firmware is continuously monitored. Whether it’s a smart parking sensor or a manufacturing robot, we secure every point where data originates.
2. Integrated AI & Machine Learning
We don’t just react to threats — we predict and prevent them. Our AI models identify unusual patterns, flag anomalies in real time, and adapt continuously. This assists in minimizing false positives while keeping incident response quicker.
3. Blockchain for Data Integrity
To secure transactional data, NetObjex leverages blockchain technology. Immutable, decentralized records prevent tampering and create a trustworthy audit trail. This is especially powerful in supply chains and smart city ecosystems.
4. Cloud-to-Device Encryption
We protect data streams from device to cloud, and vice versa. With our hybrid architecture, sensitive data is never left vulnerable — even in high-speed transfers between systems.
5. Fractional CISO Services
Not every business can hire a full-time cybersecurity executive and that’s okay. Our Fractional CISO offering ensures that even startups and SMEs have access to expert-level security leadership, risk assessments, and compliance guidance without stretching their budget.
A Real-World Example: Securing Smart Parking
Let’s take one of our own deployments — a smart parking system in a city environment. Here’s how end-to-end security comes into play:
The parking sensor at the edge is encrypted and authenticated.
The data it collects (availability, vehicle ID, payment info) is securely transmitted.
AI monitors for anomalies — such as spoofed devices or unusual patterns.
Blockchain records each transaction, creating trust in a public infrastructure.
The cloud dashboard used by the municipality is secured via role-based access and two-factor authentication.
This isn’t just “good IT hygiene.” It’s a proactive, multi-layered approach that prevents fraud, ensures citizen safety, and builds digital trust.
Why This Matters More Than Ever
In 2025 and beyond, cybersecurity is not just a technical concern it’s a business enabler. Customers demand privacy. Partners expect compliance. Investors look for risk mitigation. And regulators are tightening their grip.
Businesses that treat cybersecurity as a core competency not an add-on will gain the trust, scalability, and resilience they need to thrive.
Ready to Go Beyond the Basics?
If you’re still relying on firewalls and antivirus to protect your digital assets, it’s time to rethink your strategy. At NetObjex, we help businesses of all sizes design and deploy true end-to-end cybersecurity solutions that adapt, learn, and scale with you.
Discuss how we can future-proof your organization.
Get in touch with us today
#Managed Security Operations Center#Cybersecurity Risk Assessment and Audit#24/7 Threat Monitoring Services#Compliance and Vulnerability Management#End-to-End Cybersecurity Solutions#Fractional CISO
0 notes