#Insecurity in SAAS
Explore tagged Tumblr posts
Text
it still hurts yn katong mga nabuhat nimo na mali from flirting with her nga oila pata ka Weeks or days ato nag official tapos nakipaglandian na dayun ka
ana paka ato nga ok raba nga mag friends mo and i said okay nalang tapos nasuko ka kay dapat ko mo ingon og dili tapos now nga ni ingon nakog dili ko gamahan makig close kag mga babae like close nga close nya masuko naka nako mo ana dayun kag mao na imohang ick sa babae sorry now a days daghan nag mga cheater and i dont wanna be one of those girls who got cheated on nya mag hilak hilak dayun
ikaw nga dali ra kaayu maka bulag sa akoa nga mura rakug wala saimoha
sakit kaayu gi endure nako tanan ang kasakit og mag breakdown ko permi kay mag sigi rato og balik balik sa akoang huna huna akoang gi angkon tanan ako ang nag suffer tapos naaa kay ganahan about sa akoa usahay maka pangutana og og gi higugma ba gyud ko nimo or butang rako sa imohang panan aw pero ma feel man pod nako nga love ko nimo
kaning obsession nimo karun bisay 0.01% wala ko ganahan ana gina ingnan tika pero imoha rskong gika pa guilty kay mao lahi ana daw nya kani ra ang kalipay so what dapat ako imohang unahon wala ka nasayud og unsa nako ma miserable diria nga ga hilak gali ta mag huna huna atong sauna gisamotan pa gyud ani wa ko kasabot yan
and oh yah nakit to nakong saa na likes nimo sa tiktok katong gipahulam ko jimo sa imohang cp tapos ni lakaw ka nya ni sneak ko didto at first nalipay k kay naa akoang face nya sa kilid ana partida naa ba nana si winter tapos akoang face pa gyud didto jay edited bushet kamao ka unsa ka akoang na feel tapos kilid mi ato??? naa pay caption nga cute pictures og winter mao to nawala akoang gana pero i still put ny mask on bisan sakit na kaayu ug lami na kaayu mo hilak and yah sa imohang save katong sa collection ambot og unsa nato ka dugay pero kakita kog mga babae hot kaayu tapos gwapa kaayu nag sayaw nga naka croptop bushet oy kamao man ka nga uyab nata at least imoha to g gi delete ay ko igna nga gina tan aw gihapon to nimo og katong tume nga nag vc ta tapos nag tiktok ka syempre makadungog ko nya ang kanta kay katong pang thirst trap sa mga babae tapos dugay kayka naka swipe bushet gyud lami na kaayu pakamatay yan naulaw nako
kato pong naa ta sa room tapos nag kaon mata ninyu ato nya nangutana ko og unsay kukang something ana nga pangutana tapos ana ka nga kulang nimo og kaon yati ra kamao ka nga insecure kaayu ko nga pagkatao tapos sigi rako nimo ignan nga dakog agtang sakit kaayu as in wala lang ka kamao yan sakit na kaayu di na nako ma agwanta ang kasakit
basin oag makakita ka ani nga post kay it's either namatay nako or gipahulam tuka sa akoang co tapos napasagdahan ra nako pero wa ko pake
unta masayud ka og maka huna huna kag kamusta sa akoa kay di ko okay di gyud mura rakog okay sa gawas pero lami na kaayu ipakamatay gyud pero di pod na nako buhaton sturya lang
sigi rakog sorry sigi rakog ingon og please mao ra gihapon ang resulta
2 notes
·
View notes
Text
The Illusion of Safety: Why Antivirus Alone Won't Keep Your Information Safe in 2025

For decades, antivirus software was the undisputed champion of digital defense. It sat vigilantly on our computers, scanning files, blocking known viruses, and providing a reassuring sense of security. "I have antivirus, so I'm safe," was a common refrain.
In 2025, that statement is a dangerous illusion. While antivirus remains a fundamental layer of cybersecurity, relying solely on it to protect your valuable information is like fortifying your front door while leaving all your windows and back doors wide open. The cyber threat landscape has evolved dramatically, leaving traditional antivirus solutions struggling to keep up.
Here's why your trusty antivirus, by itself, is no longer enough:
1. The Rise of Zero-Day Attacks
Traditional antivirus software primarily relies on signature-based detection. This means it identifies malware by matching its unique digital "fingerprint" (signature) against a database of known threats. The problem? Zero-day attacks exploit vulnerabilities that are unknown to software vendors and security companies.
Why AV Fails: Since there's no known signature for a zero-day exploit, traditional antivirus simply doesn't recognize it as malicious, allowing it to bypass detection and execute its payload unhindered.
2. The Stealth of Fileless Malware
Modern attackers are masters of evasion. Instead of dropping detectable executable files onto your disk, they increasingly "live off the land" by leveraging legitimate tools already present on your system (like PowerShell, WMI, or scripting engines).
Why AV Fails: Fileless malware operates primarily in memory, performing malicious actions without leaving a discernible file footprint for signature-based scanners to find. Antivirus, designed to scan files, often misses these in-memory threats.
3. The Power of Social Engineering & Phishing
The weakest link in any security chain is often the human one. No amount of antivirus software can stop a well-crafted phishing email or a convincing social engineering scam that tricks an employee into revealing credentials or clicking a malicious link.
Why AV Fails: Antivirus works at the machine level, not the human decision-making level. It can't prevent you from being manipulated into granting access or installing seemingly legitimate software that's actually malicious.
4. Ransomware's Evolving Evasion Tactics
Ransomware has become a sophisticated, adaptive beast. Modern variants use polymorphic code (changing their signature with each iteration), leverage fileless techniques, and are often "human-operated," mimicking legitimate administrative activities to avoid automated detection.
Why AV Fails: The rapid mutation of ransomware makes signature-based detection less effective. Human-operated ransomware often uses legitimate tools and moves slowly, blending into normal network traffic, making it hard for basic antivirus to differentiate malicious intent.
5. Cloud & SaaS Vulnerabilities
Our digital lives increasingly reside in the cloud, utilizing Software-as-a-Service (SaaS) applications and cloud infrastructure (IaaS, PaaS). Traditional antivirus primarily focuses on endpoints (your computer, server).
Why AV Fails: Antivirus doesn't provide visibility or protection for misconfigured cloud storage buckets, exposed APIs in SaaS applications, or insecure configurations in your cloud infrastructure that can lead to massive data leaks. These vulnerabilities are outside its scope.
6. Insider Threats (Malicious & Negligent)
Whether it's a disgruntled employee intentionally stealing data or a careless employee accidentally exposing sensitive information, insider threats bypass perimeter defenses that antivirus sits behind.
Why AV Fails: Antivirus isn't designed to monitor user intent or legitimate actions that become illegitimate (e.g., an employee copying a confidential database to a personal USB drive). It focuses on malware, not misuse of authorized access.
What's Needed Beyond Antivirus: The Modern Defense Strategy
In 2025, securing your information requires a layered, integrated, and adaptive approach. Think of it like building a secure fortress with multiple defenses, not just a locked door.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): These go beyond antivirus by continuously monitoring endpoint activity, analyzing behavior, and providing context for suspicious events, enabling rapid detection and response to advanced threats.
Zero Trust Architecture (ZTA): Assume no trust, even for internal users. Verify every user, device, and application attempting to access resources, regardless of their location.
Robust Security Awareness Training: Empower your "human firewall" with continuous education, realistic simulations, and a culture that prioritizes security.
Data Loss Prevention (DLP): Tools designed specifically to monitor, detect, and block unauthorized movement or exposure of sensitive data, whether accidental or malicious.
Cloud Security Posture Management (CSPM): Continuously monitors your cloud environments for misconfigurations and compliance violations that could lead to data leaks or breaches.
Identity and Access Management (IAM) & Multi-Factor Authentication (MFA): Strong controls over who can access what, reinforced by multiple authentication factors.
Network Detection and Response (NDR): Monitor network traffic for anomalies that might indicate ransomware spread, data exfiltration, or command-and-control communication.
Proactive Vulnerability Management & Patching: Regularly identify and fix software flaws before attackers can exploit them.
Incident Response Planning: Have a clear, rehearsed plan for what to do when (not if) a breach or attack occurs, to minimize damage and ensure rapid recovery.
Antivirus is still a foundational component of a good cybersecurity strategy, acting as your first line of defense against known threats. However, it's just one piece of a much larger, more complex puzzle. To truly keep your information safe in 2025, you need to move beyond a false sense of security and embrace a comprehensive, multi-layered approach that adapts as quickly as the threats themselves.
0 notes
Text
API Vulnerabilities in Symfony: Common Risks & Fixes
Symfony is one of the most robust PHP frameworks used by enterprises and developers to build scalable and secure web applications. However, like any powerful framework, it’s not immune to security issues—especially when it comes to APIs. In this blog, we’ll explore common API vulnerabilities in Symfony, show real coding examples, and explain how to secure them effectively.

We'll also demonstrate how our Free Website Security Scanner helps identify these vulnerabilities before attackers do.
🚨 Common API Vulnerabilities in Symfony
Let’s dive into the key API vulnerabilities developers often overlook:
1. Improper Input Validation
Failure to sanitize input can lead to injection attacks.
❌ Vulnerable Code:
// src/Controller/ApiController.php public function getUser(Request $request) { $id = $request->query->get('id'); $user = $this->getDoctrine() ->getRepository(User::class) ->find("SELECT * FROM users WHERE id = $id"); return new JsonResponse($user); }
✅ Secure Code with Param Binding:
public function getUser(Request $request) { $id = (int)$request->query->get('id'); $user = $this->getDoctrine() ->getRepository(User::class) ->find($id); return new JsonResponse($user); }
Always validate and sanitize user input, especially IDs and query parameters.
2. Broken Authentication
APIs that don’t properly verify tokens or allow session hijacking are easy targets.
❌ Insecure Token Check:
if ($request->headers->get('Authorization') !== 'Bearer SECRET123') { throw new AccessDeniedHttpException('Unauthorized'); }
✅ Use Symfony’s Built-in Security:
# config/packages/security.yaml firewalls: api: pattern: ^/api/ stateless: true jwt: ~
Implement token validation using LexikJWTAuthenticationBundle to avoid manual and error-prone token checking.
3. Overexposed Data in JSON Responses
Sometimes API responses contain too much information, leading to data leakage.
❌ Unfiltered Response:
return $this->json($user); // Might include password hash or sensitive metadata
✅ Use Serialization Groups:
// src/Entity/User.php use Symfony\Component\Serializer\Annotation\Groups; class User { /** * @Groups("public") */ private $email; /** * @Groups("internal") */ private $password; } // In controller return $this->json($user, 200, [], ['groups' => 'public']);
Serialization groups help you filter sensitive fields based on context.
🛠️ How to Detect Symfony API Vulnerabilities for Free
📸 Screenshot of the Website Vulnerability Scanner tool homepage

Screenshot of the free tools webpage where you can access security assessment tools.
Manual code audits are helpful but time-consuming. You can use our free Website Security Checker to automatically scan for common security flaws including:
Open API endpoints
Broken authentication
Injection flaws
Insecure HTTP headers
🔎 Try it now: https://free.pentesttesting.com/
📸 Screenshot of an actual vulnerability report generated using the tool to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
✅ Our Web App Penetration Testing Services
For production apps and high-value APIs, we recommend deep testing beyond automated scans.
Our professional Web App Penetration Testing Services at Pentest Testing Corp. include:
Business logic testing
OWASP API Top 10 analysis
Manual exploitation & proof-of-concept
Detailed PDF reports
💼 Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
📚 More Articles from Pentest Testing Corp.
For in-depth cybersecurity tips and tutorials, check out our main blog:
🔗 https://www.pentesttesting.com/blog/
Recent articles:
Laravel API Security Best Practices
XSS Mitigation in React Apps
Threat Modeling for SaaS Platforms
📬 Stay Updated: Subscribe to Our Newsletter
Join cybersecurity enthusiasts and professionals who subscribe to our weekly threat updates, tools, and exclusive research:
🔔 Subscribe on LinkedIn: https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
💬 Final Thoughts
Symfony is powerful, but with great power comes great responsibility. Developers must understand API security vulnerabilities and patch them proactively. Use automated tools like ours for Website Security check, adopt secure coding practices, and consider penetration testing for maximum protection.
Happy Coding—and stay safe out there!
#cyber security#cybersecurity#data security#pentesting#security#coding#symfony#the security breach show#php#api
1 note
·
View note
Text
🚨 Concerned about website security in 2025? With cyberattacks becoming more sophisticated every year, choosing a secure web hosting provider is more important than ever.
I just published a detailed breakdown of the 5 most secure hosting providers in the world right now — based on encryption, DDoS protection, malware scanning, backup systems, and more.
🔐 Whether you're running a blog, eCommerce site, or SaaS platform, this list can help you avoid the risks of insecure hosting.
Which hosting provider do you trust for security in 2025? Let’s discuss!
#SecureHosting#WebHostingSolutions#CyberSecurity#CloudHosting#DataProtection#ManagedHosting#WebsiteSecurity#TechTrends2025#DigitalInfrastructure#WebHosting2025
1 note
·
View note
Text
It Happened on Medium: April 2025
April 2025 was a vibrant month on Medium, showcasing a dynamic mix of thought-provoking essays, personal reflections, AI experiments, and cultural critiques. As the digital world continues to evolve, so too do the voices that shape Medium’s ever-growing ecosystem. Here's a roundup of what made waves on the platform this past month.

🚀 Top Trends
AI and Human Creativity: The Great Debate Continues
AI was once again a dominant theme, with writers exploring its impact on art, literature, and human identity. The most-read story of the month, "Can AI Write a Soul?" by Leah Renshaw, drew over 120,000 views and thousands of responses. The piece questioned whether generative models are enhancing creativity or eroding the uniqueness of human expression.
Another viral essay, "I Asked ChatGPT to Rewrite My Memoir — Here's What Happened," blurred the line between assistance and authorship, sparking lively debate in the comments.
Digital Minimalism Sees a Resurgence
As screen time surged globally, readers flocked to minimalist living and tech detox stories. Articles like "I Deleted Every App Except One" and "Living Offline for 30 Days Changed My Brain" climbed Medium's trending charts. The minimalist subculture isn’t new, but April saw it reframed through a post-AI, post-constant-notification lens.
Personal Finance Meets Realism
In the wake of economic volatility and Gen Z's unique financial struggles, writers took a no-BS approach to personal finance. Pieces like "I'm 27 and I Have $9 in My Account — Here's My Plan" resonated deeply with younger readers facing student loans, gig work, and housing insecurity.
Another breakout post, "Why Budgeting Isn't the Answer," challenged conventional money advice, advocating for systemic change and mental health-first approaches to financial literacy.
✍️ Writers to Watch
Anjali Deshmukh’s "Letters from the Edge of Burnout" captured the raw emotional toll of hustle culture in the nonprofit sector. Tyler Kwong launched a serialized fiction project, The Last Archivist, blending cyberpunk aesthetics with poetic prose. It’s gaining traction among sci-fi enthusiasts. Rosa Velez's investigative piece "Inside the Wellness Scam Economy" exposed shady influencer marketing and MLM-style fitness programs — sparking over 2,000 shares.
📚 Medium Publications on Fire
Better Humans continued its reign with standout guides like "How to Break a Habit with 5 Minutes a Day." OneZero published a chilling exposé: "The Dark UX Tricks of AI Dating Apps." The Startup featured candid founder stories — a favorite was "I Built a SaaS Company With $100 and Pure Spite."
💡 Hidden Gems You Might Have Missed
"A Love Letter to My AI Therapist" — A heartfelt piece on the emotional benefits and limits of LLM-powered mental health apps. "Medium Is My Therapist" — A reflection on how writing has replaced journaling and therapy for many Gen Z and Millennial users. "Why I Teach Philosophy to My Cat" — A humorous yet oddly deep essay that caught fire in the Medium Humor and Mindfulness spaces.
📈 Platform Updates
Medium rolled out a new personalized homepage this April, tailoring content feeds more tightly to user reading patterns. Reactions were mixed: some applauded the improved relevance, while others lamented the further erosion of chronological browsing.
They also beta-tested a collaborative story feature, allowing multiple writers to co-author in real time — potentially transforming how essays and ideas develop on the platform.
🎤 Quote of the Month
“Medium is where I come not to be right, but to think out loud with strangers who care.”
Final Thoughts
April 2025 reminded us that Medium is still a space where ideas collide, identities are explored, and new voices rise. Whether you're a reader, a writer, or just a wanderer looking for thought-provoking rabbit holes, Medium this month had something to say — loudly, bravely, and sometimes hilariously.
See you next month for another round of highlights from the digital frontlines.
0 notes
Text
How to Choose the Right Software Testing Service Provider?

Delivering high-performing, secure, and bug-free software is no longer optional—it's a business necessity. Whether you're launching a mobile app, enterprise platform, or cloud-native solution, ensuring the quality of your product requires rigorous testing. But with a wide array of vendors offering software testing services, selecting the right partner can be overwhelming.
This guide by Robotico Digital walks you through the essential criteria for choosing a reliable software testing service provider that aligns with your technical requirements and business goals.
1. Understand Your Testing Requirements
Before reaching out to vendors, you need a clear understanding of what you’re looking for. Start by defining:
l Project scope and scale (e.g., web app, mobile app, API, enterprise software)
l Type of testing required – functional, performance, security, usability, automation, etc.
l In-house vs. outsourced testing
l Compliance or regulatory needs (e.g., ISO, GDPR, HIPAA)
A well-defined requirement list will help filter providers based on their core competencies and industry experience.
2. Assess the Provider’s Expertise in Software Testing Services
When evaluating potential software testing service providers, one of the most important criteria is their hands-on experience and depth of expertise. Software testing is not just about identifying bugs—it's about ensuring your application performs optimally across various environments, user scenarios, and technical architectures. Therefore, assessing a provider’s capability in delivering comprehensive and scalable software testing services is crucial.
Manual and Automated Testing
A reliable testing partner should be proficient in both manual and automated testing approaches. Manual testing remains essential for exploratory, usability, and ad-hoc testing scenarios where human intuition plays a key role. However, as development cycles become shorter and more iterative, automation becomes indispensable. Automated testing helps run repetitive test cases efficiently and ensures quick feedback loops. A competent provider should have experience using popular frameworks like Selenium, Appium, TestNG, JUnit, and Cypress, and they should be capable of building reusable, maintainable automated test suites.
Cross-Browser and Cross-Device Testing
With the growing diversity of user devices and browsers, it’s essential to ensure that your software functions seamlessly across platforms. This includes different versions of Chrome, Firefox, Safari, and Edge, as well as Android and iOS devices in various screen resolutions. An expert testing provider will simulate real-world usage environments and use tools like BrowserStack or Sauce Labs to guarantee a consistent and optimized user experience.
Load and Performance Testing
Performance is a critical quality attribute—especially for high-traffic platforms like e-commerce websites, SaaS applications, and financial systems. Load testing evaluates how your system behaves under normal and peak loads, while stress testing identifies breaking points. Look for a provider that uses tools such as JMeter, Gatling, or LoadRunner and can deliver detailed reports on response time, throughput, and server health. This level of performance insight is vital to avoid costly downtimes and latency issues post-deployment.
Security and Penetration Testing
In an age of increasing cyber threats, security cannot be an afterthought. A capable software testing services provider should offer security assessments that include vulnerability scanning, penetration testing, and code analysis. They must be adept at identifying flaws like SQL injection, cross-site scripting (XSS), insecure APIs, and broken authentication. Their practices should align with security standards like OWASP Top 10, ISO 27001, and GDPR.
Integration and System Testing
Today's applications are often made up of interconnected components, third-party APIs, and microservices. A reliable testing partner must validate not only individual components (unit testing) but also how they interact (integration testing). Additionally, they should perform system testing to evaluate the entire end-to-end workflow, ensuring that business logic and data flow remain intact across modules.
Continuous Testing in CI/CD Environments
With DevOps and Agile becoming the industry norm, continuous integration and delivery (CI/CD) pipelines are now fundamental. Continuous testing ensures that every code commit is automatically validated through a series of tests. A modern testing provider should integrate their test automation framework into your CI/CD tools like Jenkins, GitLab CI, Bamboo, or CircleCI. This ensures quick detection of issues, faster feedback loops, and accelerated time to market.
Robotico Digital’s Proven Expertise
At Robotico Digital, we combine traditional best practices with innovative technologies to deliver reliable, scalable, and industry-specific software testing services. Our team comprises seasoned QA engineers, automation specialists, and domain experts who work collaboratively with your development team to enhance product quality and accelerate delivery cycles.
3. Evaluate Their Approach to Software Quality Assurance
Software Quality Assurance (SQA) is broader than just testing—it’s a strategic process that ensures every phase of the development lifecycle meets the highest quality standards. When evaluating a testing provider, ensure their services include:
l Quality planning and benchmarking
l Risk-based testing strategies
l Defect prevention and early bug detection
l Test environment management
l Detailed documentation and reporting
Robotico Digital integrates SQA from the start, ensuring not only bug-free releases but also process optimization, security, and maintainability across the software lifecycle.
4. Look for Automation Capabilities
As modern applications become increasingly complex, test automation is no longer a luxury—it’s essential. Ask potential service providers:
l What automation tools and frameworks do they use?
l Do they offer test script maintenance?
l Can they integrate with your CI/CD pipeline?
l Are they experienced with frameworks like Selenium, Appium, JUnit, TestNG, Cypress, etc.?
Robotico Digital’s automation-first approach reduces testing time, increases efficiency, and ensures continuous testing across development sprints.
5. Consider Industry Experience and Domain Expertise
Different industries have different quality expectations and regulatory demands. Choosing a provider with domain-specific knowledge adds immense value. For example:
l Healthcare apps must comply with HIPAA
l Finance platforms need PCI DSS and secure coding practices
l E-commerce platforms require usability and performance optimization
l EdTech solutions need scalable and accessibility-friendly testing
Our team at Robotico Digital has worked with clients across fintech, healthcare, education, e-commerce, and SaaS, bringing niche insights into quality and compliance standards.
6. Review Technology Stack Compatibility
A testing provider must be comfortable working with your tech stack—both frontend and backend. This includes:
l Programming languages (e.g., Java, Python, .NET, JS)
l Cloud platforms (AWS, Azure, GCP)
l DevOps and CI/CD tools (Jenkins, GitHub Actions, GitLab CI)
l Databases, APIs, and third-party integrations
Robotico Digital ensures seamless compatibility across all major tech stacks, helping you maintain workflow continuity and testing accuracy.
7. Inquire About Communication and Reporting
Communication is key in outsourcing. Your testing partner should offer:
l Dedicated project managers
l Real-time status updates
l Easy access to test plans, bug reports, and dashboards
l Collaboration tools (Slack, Jira, Asana, Trello)
We maintain complete transparency throughout the engagement at Robotico Digital. Our clients receive detailed reports and dashboards that highlight test progress, defects, coverage, and risks—enabling informed decisions at every step.
8. Evaluate Flexibility and Scalability
Your testing needs may change over time. The right provider should be able to:
l Scale team size up or down based on project phases
l Adapt to different engagement models (fixed, time & material, staff augmentation)
l Handle agile and waterfall methodologies
Robotico Digital offers flexible service models to accommodate both startups and large enterprises. Whether you need ongoing regression testing or a full QA team, we adapt to your needs.
9. Ensure Security and Data Privacy
Security in software testing is paramount—especially if your application handles sensitive data. Ask your provider:
l How do they handle data confidentiality and secure test environments?
l Are they compliant with ISO, GDPR, SOC2, or other data standards?
l How do they manage access control and data masking?
At Robotico Digital, we treat security as non-negotiable. Our testing protocols and infrastructure are built to safeguard client data and maintain compliance across multiple regulatory frameworks.
10. Check References and Client Testimonials
Finally, don’t just rely on sales pitches. Ask for client case studies, references, or testimonials. Look into:
l Past projects with similar scope
l Client retention rate
l Success stories or improvements they’ve driven
Robotico Digital has a strong portfolio of satisfied clients. From reducing time-to-market by 30% to improving test coverage by 90%, our measurable impact speaks for itself.
Conclusion: Making the Right Choice with Robotico Digital
Choosing the right software testing service provider is more than a technical decision—it’s a strategic partnership. The ideal provider should not only understand testing but also align with your business goals, technologies, and timelines.
At Robotico Digital, we pride ourselves on delivering holistic software testing services backed by industry-best practices in software quality assurance. Our dedicated QA engineers, AI-assisted tools, flexible models, and transparent communication help clients achieve faster releases, higher user satisfaction, and lower defect rates. Whether you’re scaling a new product or optimizing an existing system, trust Robotico Digital to elevate your software quality to the next level.
0 notes
Text
What Is a Payment Gateway and Why Does It Matter?
In today’s digital-first world, payment gateways are the backbone of online transactions. They make it possible for businesses to accept payments securely from customers, whether through credit cards, digital wallets, or bank transfers.
🔍 What Is a Payment Gateway?
A payment gateway is a service that processes payment information between a website or app and a bank. It ensures that customer data is encrypted, securely transmitted, and approved (or declined) in real time.
🛡️ Key Functions:
Secure Data Transmission: Encrypts sensitive card information
Authorization: Confirms whether a customer has enough funds or credit
Fraud Prevention: Helps block suspicious or high-risk transactions
Multi-Currency Support: Useful for businesses with global customers
💳 How the Process Works:
A customer submits their payment information at checkout.
The payment gateway encrypts and forwards the data to a payment processor.
The processor contacts the customer’s bank for authorization.
The response (approved or declined) is sent back through the gateway.
The merchant and customer are notified, and the transaction is finalized.
🧠 Why It Matters:
Without a payment gateway, online payments would be insecure and impractical. It provides the trust layer between merchants and customers and enables seamless, instant transactions across the globe.
Common providers include Stripe, PayPal, Square, Razorpay, and Authorize.net, each offering different features for businesses of all sizes.
For anyone building an online store, SaaS platform, or digital service — choosing the right payment gateway is one of the most important technical decisions you’ll make. If you're exploring how to integrate a payment gateway into your app or website, feel free to reach out.
#fintech solutions#payments#payment gateway#web development#digitalpayments#developers & startups#ecommerce
1 note
·
View note
Text
Security and Compliance in Cloud Computing: Best Practices for Risk Mitigation
As businesses rapidly adopt cloud computing, ensuring security and compliance is more critical than ever. Cyber threats, data breaches, and regulatory requirements demand that organizations implement robust security measures to protect sensitive data and maintain compliance.
In this blog, we’ll explore key security challenges in cloud computing, best practices for risk mitigation, and how Salzen helps businesses enhance their cloud security posture.
1. The Growing Importance of Cloud Security and Compliance
The shared responsibility model in cloud computing means that while cloud providers secure the infrastructure, businesses must safeguard data, applications, and user access.
Without proper security controls, organizations face:
🔹 Data breaches and cyberattacks 🔹 Regulatory fines for non-compliance 🔹 Operational disruptions due to security incidents
📌 Example: A global retailer suffered a $200M+ data breach due to misconfigured cloud storage, exposing millions of customer records.
2. Top Security Risks in Cloud Computing
🔹 1. Misconfigurations and Unauthorized Access
🔸 Misconfigured cloud storage, APIs, and identity settings are a leading cause of data leaks. 🔸 Lack of multi-factor authentication (MFA) can allow unauthorized access.
✅ Mitigation: ✔ Regular security audits to detect misconfigurations ✔ Enforce least privilege access and use MFA for all accounts
🔹 2. Compliance Violations and Data Sovereignty Issues
🔸 Businesses handling financial, healthcare, or personal data must comply with GDPR, HIPAA, SOC 2, and PCI DSS. 🔸 Storing data in the wrong geographic region can violate data sovereignty laws.
✅ Mitigation: ✔ Use automated compliance monitoring to ensure regulatory adherence ✔ Choose cloud regions that align with legal requirements
📌 Example: A fintech company avoided $1M in regulatory fines by implementing real-time compliance monitoring.
🔹 3. Insecure APIs and Weak Encryption
🔸 Unsecured APIs are a common attack vector for cybercriminals. 🔸 Poor encryption standards put sensitive data at risk.
✅ Mitigation: ✔ Implement API security best practices, including OAuth, JWT, and rate limiting ✔ Use end-to-end encryption for data in transit and at rest
📌 Example: A healthcare firm prevented API breaches by enforcing zero-trust authentication for all API endpoints.
3. Best Practices for Cloud Security and Compliance
🔹 1. Implement Zero Trust Security
The Zero Trust model assumes that no one inside or outside the network is automatically trusted.
✔ Enforce strict identity verification for all users and devices ✔ Use micro-segmentation to limit lateral movement in case of a breach
🔹 2. Automate Security and Compliance Monitoring
Manual security checks are inefficient and prone to human error. Automating security monitoring helps detect threats in real time.
✔ Deploy SIEM (Security Information and Event Management) tools like Splunk, Datadog, or AWS Security Hub ✔ Use compliance-as-code to continuously audit configurations
📌 Example: A global SaaS company reduced compliance violations by 75% using automated compliance scanning.
🔹 3. Secure CI/CD Pipelines
CI/CD pipelines introduce security risks if not properly secured.
✔ Implement automated security testing in CI/CD workflows ✔ Scan for vulnerabilities in containerized applications before deployment
📌 Example: A DevOps team prevented production breaches by integrating SAST and DAST security checks in CI/CD pipelines.
4. How Salzen Helps Secure Your Cloud Environment
At Salzen, we enable businesses to enhance cloud security and compliance through:
🔐 Automated security assessments to detect vulnerabilities early 🛡 Cloud-native security solutions for proactive threat detection 📊 Compliance management tools to ensure regulatory adherence
🔹 Ready to strengthen your cloud security? Let Salzen help you implement best-in-class security and compliance solutions! 🚀
0 notes
Text
"Top 5 Reasons Why Your SaaS Business Needs a Cybersecurity Audit"

As the digital world evolves, so do the tactics used by cybercriminals. For B2B SaaS companies, the need for robust cybersecurity has never been more critical. While many businesses focus on scaling their operations and improving their offerings, cybersecurity is often overlooked—leading to vulnerabilities that could result in costly data breaches. That’s why a cybersecurity audit is essential for ensuring your SaaS business remains secure. At Decrypt Compliance, we specialize in cybersecurity audits for SaaS companies, helping you protect your platform from evolving threats. Here are the top five reasons why your SaaS business needs a cybersecurity audit.
1. Protect Sensitive Customer Data
SaaS platforms often store sensitive data such as customer information, payment details, and proprietary business processes. A security breach could compromise this data, leading to significant financial losses and a damaged reputation. Cybersecurity audits assess your platform’s security posture, ensuring that sensitive data is protected through encryption, secure access controls, and vulnerability management.
At Decrypt Compliance, we conduct thorough audits to identify any weak points in your system and help you implement the best practices to safeguard your business and customer data.
2. Ensure Compliance with Industry Regulations
Most SaaS businesses are required to comply with a variety of regulatory frameworks such as GDPR, HIPAA, and SOC 2. Non-compliance can result in hefty fines, legal challenges, and loss of trust from your customers. A cybersecurity audit evaluates your company's adherence to these regulations, ensuring that your SaaS platform is compliant with the latest industry standards.
With our expertise in cybersecurity audits, Decrypt Compliance ensures that your platform meets all necessary regulatory requirements, giving you confidence that your business is on the right side of the law.
3. Identify and Fix Vulnerabilities
Cybercriminals are constantly searching for vulnerabilities that they can exploit to gain unauthorized access to your platform. Regular cybersecurity audits help identify these vulnerabilities before attackers can take advantage of them. By performing a comprehensive security audit, you’ll receive a detailed report highlighting any areas where your SaaS platform may be at risk, whether from outdated software, insecure configurations, or weak user authentication protocols.
At Decrypt Compliance, we provide in-depth vulnerability assessments that not only pinpoint risks but also offer actionable recommendations to strengthen your platform’s defenses.
4. Prevent Financial Losses Due to Data Breaches
Data breaches are expensive, both in terms of direct financial costs and the long-term damage to your reputation. The financial impact of a breach includes fines, legal fees, and the costs associated with mitigating the attack. Cybersecurity audits can help you identify potential weaknesses that may lead to data breaches and address them proactively. A small investment in a cybersecurity audit can save your company from a significant financial burden in the future.
By partnering with Decrypt Compliance, you’re investing in proactive risk management that helps safeguard your revenue and brand reputation.
5. Enhance Trust and Credibility with Customers
In today’s competitive market, your customers want to know that their data is secure. A robust cybersecurity strategy, backed by regular audits, helps build trust with your clients. When you can demonstrate that your SaaS platform is protected by rigorous cybersecurity measures, you boost your credibility and make your platform more attractive to potential customers.
A cybersecurity audit from Decrypt Compliance helps reinforce your commitment to security, giving clients the confidence to do business with you.
Conclusion
The need for cybersecurity audits in the SaaS industry is more critical than ever. With rising cyber threats and stringent regulatory requirements, a comprehensive security audit helps you stay ahead of the curve. At Decrypt Compliance, we specialize in providing thorough cybersecurity audits for SaaS businesses, ensuring that your platform remains secure, compliant, and resilient against future threats.
Don't wait for a cyberattack to compromise your platform—take proactive steps to protect your business today.
0 notes
Text
With increasing Digital Data usage it has become essential to store data securely in the Cloud. The use cases for this may vary starting from storing huge data from your computer to the cloud, storing important data like your legal documents, family photos and videos to the cloud or even sharing of sensitive data that you have uploaded to the cloud. For desktop users, it’s easier to access data remotely with cloud while for mobile users it saves a lot of internal storage by uploading data to the cloud and they can access their data from anywhere. While cloud storage usage is growing from individuals and businesses, there is a need to secure your data in the cloud storage. One does not want to trade the convenience of access with data leakage or unauthorized usage. Most of the cloud storage providers will have their own mechanism to secure, encrypt and safeguard your data. Since the data is not stored locally it is always better to be safe than sorry, when it comes to securing your data in the cloud. The data is yours and you need to take all possible steps to ensure that it is safe and protected in the cloud service you have chosen to upload your files to. So here are the Dos and Don’ts to secure your data in any cloud storage Dos Select the most reliable cloud storage services like Google Drive, Dropbox, Box, One Drive and Amazon etc. These cloud storage providers have a long standing reputation and are fully committed to providing maximum security for your data. Set up two-factor authentication to log in to your account. Here an OTP (One Time Passcode) will be sent to the registered mobile phone. These passcodes have a quick expiry ensuring no misuse and the passcode will be sent to your phone, which is highly secure. Select services that store your data with 256-bit encryption or encrypt data with the use of secure third party services and then upload to the cloud. This will ensure that your files cannot be downloaded and viewed from any outside source or hacker website. This way, even if someone got hold of your files, they will not be able to view the contents in the file. This type of encryption gives you highest security and peace of mind. If you are using any multi-cloud management or cloud transfer services like CloudFuze make sure those services offer OAuth authentication method. OAuth is the most secure way to communicate between SaaS Apps and they usually transfer unique tokens between the services to authenticate rather sharing your username or password via the internet. Ensure that the cloud transfer service you are using does not store your files in their local storage or even as temporary files on their servers. Such services should only store your file metadata. Do a timely audit on your files across all your cloud storage services to make sure they are not shared unnecessarily or any old shares are still active. Unnecessary file sharing can cause insecure and unintended access. Move data from unsecured clouds to secure clouds using cloud file transfer solutions like CloudFuze. Storing all your files in secure clouds will eliminate the risk totally. Don’ts Don't forget to log out of your account every time you shut down your device. Sometimes you may not log out properly and your sessions may be active with your cloud storage service and this may enable others to access your cloud storage accounts. You should also never store passwords in clear text in a file or somewhere in your computer. Use a password manager to store and create complex passwords to make all your accounts secure. Generate memorable passwords using online tools like this - this will ensure you have an easy to remember the password at the same time it is fairly complex for a bot to crack. Don't share important files as a public share, since they will be exposed to everyone. Private shares are restricted to the designated recipients and recommended for safer file sharing. Don’t use services that
do not offer good authentication process like two-factor authentication, tight password controls or OAuth authentication. Don't visit unsecured websites or hacked websites from your browser or computer, which is used to access your cloud storage data. Don't connect to unknown Wi-Fi networks from your computer. Conversely, always secure your Wi-Fi with a password. Don't forget to conduct timely audit logging on your cloud storage services for tighter control. This logging information will usually provide all the details about who logged into the account and from where etc., which can help you to make sure your accounts are safe. In this information age, our pictures, music, videos, and documents are everything in our life. Securing our files and information in widely used cloud storage accounts is key to productivity and peace of mind. Ram Bayisett is the head digital marketing of CloudFuze,Inc. an organization founded with the goal of leading the next phase in the evolution of cloud storage and document and file management. His aim is to enable individuals, companies and software developers to connect to and reap the benefits of the expanded set of file management and storage options without the need to deal with their complexities. Cloudfuze aim to provide a cleaner,simpler way to migrate, secure and manage all your assets.
0 notes
Text
SHAMS AL-MA'ARAF: exploitation of sincere lore of the Qur'an and ailment restoration (archtype of wonder: systemised lobotomy of the eye and sincere observation of heartbreak)

SAA: (read: object to foreign tongue)
ARAMAIC: RESTRAINED THOUGHT SITUATION THAT PROMISES REWARD PER BREATH
ARABIC: DIE FOR IT
LATIN: COMMON SENSE
HEBREW: WHERES MY BEST FRIEND?
SANSKRIT: YOU KNOW YOUR HEART TO WELL AND YOU GOT IT (WONDER MAP LEADS YOU TO HAPPY DESTINATION HELL)
HINDI: YOU LIVE IT FOR FREE
SHADA: IT DOESN'T END TOO GREATLY, EVERYBODY IS BETTER THAN YOU (EXEMPT: MENTALLY DISABLED KIDS + BABIES ARE CLASSED AS PHYSICALLY DISABLED BUT BABIES FROM AGED 2 (GIRL) AND FROM BIRTH (BOY) ARE NOT IN WHAT SHADA SAYS NEXT); YOU'RE TOO INSECURE TO FACE YOUR EMOTIONS THAT YOU BECOME AN ARMPIT HAVEN FOR SHITTY PEOPLE (YOU'RE REMOVED IMMEDIATELY BY HEARTBREAK) AND ARMPIT IS KNOWN TO BE MORE STINKIER THAN BUTTHOLE AND IF YOU DONT SEE SENSE IN JOY, THEN YOU'RE DEAD MEAT
ACTORS HELL: DID I STUTTER LOGIC IS YOU BEING HURT THAT I BET YOU TO IT
HARBINGER'S: *IS THE DAJJAL WHO CREATED YOU RIGHT BACK, SO FITE ME*
MAESTRO BECOME: YOU'RE TERRIFYING IN PERSON BUT I CHOOSE TO MAKE AMENDS WHICH IS WHY I CUDDLE AND YOU FORFEIT
DANTE'S PARADOX: *GETS KO'ed IN REAL LIFE BY ACTUAL PEOPLE*
JUDGEMENT DAY: *ON THE FLOOR AFTER BEING BEATEN UP*
GAIMAN'S HELL: NOTHING WILL SAVE YOU EXCEPT AN OVERWHELMING FEELING LIKE THAT OF YOU BEING BEATEN UP BY YOUR POWERFUL VERSION OF YOU LIKE THAT HAPPENED TO ME ONCE (MY DAD BACK TO ME BUT HE IS MY BES FWEN IRL)
BABYLON UNBROKEN: YOUR AUDIO SLAVE WONT SAVE YOU NOW
KINGDOM COME: REALITY CHECK, YOU AIN'T FAMOUS IN REAL LIFE, BROTHER
PYTHAGOREAN THEOREM: NOW GET BACK TO WORK
0 notes
Text
The Accidental Unlocking: 6 Most Common Causes of Data Leaks

In the ongoing battle for digital security, we often hear about "data breaches" – images of malicious hackers breaking through firewalls. But there's a more subtle, yet equally damaging, threat lurking: data leaks.
While a data breach typically implies unauthorized access by a malicious actor (think someone kicking down the door), a data leak is the accidental or unintentional exposure of sensitive information to an unauthorized environment (more like leaving the door unlocked or a window open). Both lead to compromised data, but their causes and, sometimes, their detection and prevention strategies can differ.
Understanding the root causes of data leaks is the first critical step toward building a more robust defense. Here are the 6 most common culprits:
1. Cloud Misconfigurations
The rapid adoption of cloud services (AWS, Azure, GCP, SaaS platforms) has brought immense flexibility but also a significant security challenge. Misconfigured cloud settings are a leading cause of data leaks.
How it leads to a leak: Leaving storage buckets (like Amazon S3 buckets) publicly accessible, overly permissive access control lists (ACLs), misconfigured firewalls, or default settings that expose services to the internet can inadvertently expose vast amounts of sensitive data. Developers or administrators might not fully understand the implications of certain settings.
Example: A company's customer database stored in a cloud bucket is accidentally set to "public read" access, allowing anyone on the internet to view customer names, addresses, and even financial details.
Prevention Tip: Implement robust Cloud Security Posture Management (CSPM) tools and enforce Infrastructure as Code (IaC) to ensure secure baselines and continuous monitoring for misconfigurations.
2. Human Error / Accidental Exposure
Even with the best technology, people make mistakes. Human error is consistently cited as a top factor in data leaks.
How it leads to a leak: This can range from sending an email containing sensitive customer data to the wrong recipient, uploading confidential files to a public file-sharing service, losing an unencrypted laptop or USB drive, or simply discussing sensitive information in an insecure environment.
Example: An employee emails a spreadsheet with salary information to the entire company instead of just the HR department. Or, a developer accidentally pastes internal API keys into a public forum like Stack Overflow.
Prevention Tip: Implement comprehensive, ongoing security awareness training for all employees. Enforce strong data handling policies, promote the use of secure communication channels, and ensure devices are encrypted.
3. Weak or Stolen Credentials
Compromised login credentials are a golden ticket for attackers, leading directly to data access.
How it leads to a leak: This isn't always about a direct "hack." It could be due to:
Phishing: Employees falling for phishing emails that trick them into revealing usernames and passwords.
Weak Passwords: Easily guessable passwords or reusing passwords across multiple services, making them vulnerable to "credential stuffing" attacks if one service is breached.
Lack of MFA: Even if a password is stolen, Multi-Factor Authentication (MFA) adds a critical second layer of defense. Without it, stolen credentials lead directly to access.
Example: An attacker obtains an employee's reused password from a previous data breach and uses it to log into the company's internal file sharing system, exposing sensitive documents.
Prevention Tip: Enforce strong, unique passwords, mandate MFA for all accounts (especially privileged ones), and conduct regular phishing simulations to train employees.
4. Insider Threats (Negligent or Malicious)
Sometimes, the threat comes from within. Insider threats can be accidental or intentional, but both lead to data exposure.
How it leads to a leak:
Negligent Insiders: Employees who are careless with data (e.g., leaving a workstation unlocked, storing sensitive files on personal devices, bypassing security protocols for convenience).
Malicious Insiders: Disgruntled employees or those motivated by financial gain or espionage who intentionally steal, leak, or destroy data they have legitimate access to.
Example: A disgruntled employee downloads the company's entire customer list before resigning, or an employee stores client financial data on an unsecured personal cloud drive.
Prevention Tip: Implement robust access controls (least privilege), conduct regular audits of user activity, establish strong data loss prevention (DLP) policies, and foster a positive work environment to mitigate malicious intent.
5. Software Vulnerabilities & Unpatched Systems
Software is complex, and bugs happen. When these bugs are security vulnerabilities, they can be exploited to expose data.
How it leads to a leak: Unpatched software (operating systems, applications, network devices) contains known flaws that attackers can exploit to gain unauthorized access to systems, where they can then access and exfiltrate sensitive data. "Zero-day" vulnerabilities (unknown flaws) also pose a significant risk until they are discovered and patched.
Example: A critical vulnerability in a web server application allows an attacker to bypass authentication and access files stored on the server, leading to a leak of customer information.
Prevention Tip: Implement a rigorous patch management program, automate updates where possible, and regularly conduct vulnerability assessments and penetration tests to identify and remediate flaws before attackers can exploit them.
6. Third-Party / Supply Chain Risks
In today's interconnected business world, you're only as secure as your weakest link, which is often a third-party vendor or partner.
How it leads to a leak: Organizations share data with numerous vendors (SaaS providers, IT support, marketing agencies, payment processors). If a third-party vendor suffers a data leak due to their own vulnerabilities or misconfigurations, your data that they hold can be exposed.
Example: A marketing agency storing your customer contact list on their internal server gets breached, leading to the leak of your customer data.
Prevention Tip: Conduct thorough vendor risk assessments, ensure strong data protection clauses in contracts, and continuously monitor third-party access to your data. Consider implementing secure data sharing practices that minimize the amount of data shared.
The common thread among these causes is that many data leaks are preventable. By understanding these vulnerabilities and proactively implementing a multi-layered security strategy encompassing technology, processes, and people, organizations can significantly reduce their risk of becoming the next data leak headline.
0 notes
Text
yesterday, yasir confirmed for me his perception of me
he compared my life and my effort to his eldest sister. according to him, she does everything. leaves for her job first thing in the morning, takes full responsibility and care for her 3 children, takes full responsibility and care of her house, and still manages to cook full and big meals every single week to feed her family.
he also managed to confirm for me how truly little his view is on the effort it takes to have a child. i believe his exact words were "bacha paida karna kaun sa koi anokha kaam hai, aurat ke liye".
and he also added to the list of accolades that women accomplish by giving me the example of his middle sister living in pakistan who is a fully certified and practicing surgeon and does all of the stuff that the previously mentioned eldest sister does IN ADDITION to her own "saas ki khidmat".
and he said both of these women and many many others that he knows do these things happily, without complaint, and without any concerns or issues.
i said "bacha to main bhi paal rahi hoon", and he responded with "haan but sirf itna hi kar rahi ho" because i get a weekly food service and a bi-weekly cleaning lady.
and i also said how these work-horse women are not a healthy view of women. it's not okay to have this much expectation put upon one woman.
but i guess him and i sincerely disagree on this.
i won't lie. i was....am extremely hurt by his words. i tried t othink about why i was - or am. i think it's because i feel he's pointed out that i only do less than half of other women and complain about it. i can't be upset by this because it's a falsehod - because in honesty, it's not.
i do have other priorities in my life which make it difficult for me to cook but i guess you could pit 10 other examples of women who have the same sort of schedule (or worse) than mine and still manage to accomplish more.
so i guess the true reason i'm hurt is because perhaps he's pointed out an insecurity i have of myself. that i am not enough. and that i do not do enough.
i know and i believe that it is not good to compare yourself to others. but yasir does not - he consistently, at every opportunity compares himself to his peers, non peers, families, friends.
and what's wild is - he takes everything he sees at total and complete face value. to him, if he's seen his sisters work so hard and struggle the way they are and he's seen them do it happily - then that's what they feel. they are happy about it, they are happy with their lives, there is nothing underneath.
all of this to say that while my rational brain does believe that it's unacceptable to minimize the struggle of these women to maintain their lives the way that they do - the way that yasir makes these comparisons makes me feel so severely inadequate. what a fucking shitty way to feel.
my worth is directly tied to how much i can work myself like a machine. how many kids i can birth, how much i can cook for them, how much i slave away at my job to get promoted.
and the language that i'm using to describe all of this in my brain is coming out very self-pitying and strong because if i'm being honest that's how i feel right now. i'm stuck in the throes of a very big pity party at the moment.
so why am i letting yasir define me? and my worth? and my struggle?
why am i not fighting back against this voice in my head that's agreeing with all of the things i'm hearing from yasir.
why do i constantly belittle myself for not being enough.
why am i not worth my own self approval.
1 note
·
View note
Text
He asked me what happen. You were ready to hold my hand earlier when I was not sure. What happen.
I say - nothing happened, when you were away my heart got to know how much I like you. I realised what you meant to me. I knew i liked you but I didn't know that it was so sharp that it could cut my veins, i don't know what it is but I'm drawn to you. I feel like I question everything about me when I'm with you. Everything becomes a mess but something calming also happens inside me. I like you so so so much. I was walking with someone and all I could think about is how much I miss you, about you, what you would have said when something funny happens, what joke you would have cracked, what would we eat and everything that we are when we're together. When you were away i realised the depth of it all that i feel and I'm scared. I'm scared of getting my heart broken. I'm scared that one of us would again give up and these feelings I would have to put a veil on it again. I'm scared this time. I have my insecurities that I'm dealing with, my anxiety still wakes me up at night, I don't know what path i want to choose for myself, idk what I want to do in life, idk what kind of person I want to, I'm still figuring things out, I'm scared that my head would ruin it and that you would get tired of me and leave me. I'm scared you won't find me worthy of love because I don't think I'm. I'm scared to death rn. Mujhe tu bhut acha lgta hai yar ki jab tujhse baat nhi hoti esa lgta hai saas hi nhi aati and sirf kehne ke liye nhi, sach mein tere bina kuch toh hojata hai. Mere sath rhna bhut muskil banadeti hu mein, itna kuch pta lagrha hai apne baare mein or vo chize mujhe or insecure bana rahi hai. Main koi or insaan ban gyi kal agr what if I choose to become a certain way, behave a certain way and you don't like me. I'm scared I'll ruin it and more than that I'm scared of losing you.

0 notes
Text
A Deep Dive into the Storybrand Brandscript
It takes more than just bragging about features and perks to engage your audience in the competitive market. You must narrate a tale that speaks to their innermost wants and struggles. Introducing the Storybrand Brandscript, an effective tool for creating stories that increase engagement, lead to conversions and eventually increase success. Let's embark on a journey through this framework, guided by the expertise of Results & Co., and unlock its potential for your brand.
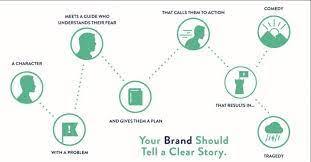
The Essence of the Brandscript: Hero's Journey in a Single Page
The Storybrand Brandscript, created by Donald Miller, summarizes the Hero's Journey in a clear, one-page format. It presents your ideal client as the protagonist, embarking on a transforming journey with your brand as their guide while overcoming an external issue (the villain). By emphasizing the hero in your message, you may create an emotional connection that sets your message out from the noise.
Decoding the Seven Pillars of the Brandscript:
The framework dissects a compelling brand story into seven key elements:
The Hero: Your ideal customer, experiencing an ordinary world disrupted by a problem.
The External Problem: The villain your hero faces, not just your product features.
The Internal Problem: The underlying fear or insecurity driving the external problem.
The Guide: Your brand, offering the hero the tools and support to overcome the villain.
The Plan: The actionable steps the hero takes, guided by your product or service.
The Stakes: The potential consequences of failure, raising urgency and engagement.
The Success: The hero overcomes the villain, achieves their desire, and transforms.
Beyond the Script: Results & Co. Your Storybrand Journey Companion
Applying the Brandscript effectively requires more than just understanding the steps. Results & Co. goes beyond, offering a range of services to empower you:
Brandscript Workshops and Training: Gain in-depth knowledge and practical skills through interactive workshops led by experienced facilitators.
Brandscript Implementation: Collaborate with their team to seamlessly integrate the Brandscript into your marketing strategy, messaging, and content creation.
Brandscript Certification: Become a Certified Storybrand Guide and equip yourself to tell powerful brand stories.
Unveiling the Benefits: From Engagement to Conversions
The impact of using the Storybrand Brandscript extends far beyond mere storytelling:
Boost your marketing ROI: Connect with your audience on an emotional level, leading to higher engagement and conversions.
Build stronger brand loyalty: Foster connection and trust by sharing your values and how you help people overcome their challenges.
Attract and retain top talent: Showcase your brand culture and purpose, attracting talent who resonate with your story.
Simplify complex messages: Present your solution in a clear, concise, and relatable way, even for intricate products or services.
Real-World Impact: Success Stories Powered by Results & Co.
Results & Co. has helped countless brands harness the power of the Brandscript. Here are some inspiring examples:
A SaaS company increased website leads by 400% after crafting a compelling Brandscript narrative.
A healthcare organization saw a 25% rise in patient satisfaction by using the Brandscript to communicate with empathy and clarity.
A non-profit organization doubled their volunteer sign-ups by aligning their messaging with the Brandscript's hero-centric approach.
Crafting Your Brand's Epic Tale: From Script to Impact
Narratives hold a powerful emotional and intellectual currency in the attention-grabbing world of today. Under the skillful direction of Results & Co., the Storybrand Brandscript gives you the ability to create stories that not only capture attention but also have a lasting effect. The knowledge and skills of Results & Co. and Brandscript provide a potent formula for success, regardless of your background—you may be a marketing specialist, small business owner, or just someone trying to create an engaging brand narrative. Set off on a heroic adventure for your brand, believe in the power of narrative, and see how your audience will relate to your message in a whole new manner.
0 notes
Text
Deep Blue Project should secure maritime anchorage areas – Omatseye

A former President, Afrian Shipowners Association of Nigeria (ASAN), Mr Temisan Omatseye, says the Deep Blue Project should be the security structure for anchorage areas in the Nigerian maritime domain. Omatseye said this at the maiden Maritime Reporters Association of Nigeria (MARAN) annual lecture on Wednesday in Lagos. Anchorage is an area off the coast which is suitable for a ship to anchor. The lecture had the theme: ‘Maritime Security: Emerging Threats and Actionable Steps.’ He said this would reduce the cost of shipping of goods into the country. According to him, every foreign shipping company pays $50,000 per vessel for security patrol boats at the anchorage, thereby increasing the cost of good imported into the country. He explained that the Deep Blue Project could do the service free or at a much subsidised rate, since the former operator Ocean Marine Solutions Ltd. (OMSL) was accused of extorting shipping companies. “We should stop playing politics with the shipping industry. There was a lacuna because of insecurity, hence the coming in of the OMSL to create a car park on the waterways, the Secured Anchorage Area (SAA). “A joint venture was signed with the Navy for security and the Nigerian Ports Authority for space, so if government wants to stop the SAA, it should be replaced,” he said. Omatseye also called for the establishment of a Response Zone Transit Corridor, to create a partial transit corridor in key high risk areas. This, he said, would enable the country to be aware of vessels that were within the Nigerian maritime environment. He listed some of the benefits of a secured anchorage as increased trade to Nigerian ports, revenue generation and to compliment the Deep Blue project. Also speaking, Mr Emmanuel Maiguwa, President, Maritime Security Providers Association of Nigeria, stressed the need for a competent agency to man the anchorage. Maiguwa also called for proper framework that would help the country deal with maritime security threats. The president, however, kicked against coast guard which he described as a nomenclature. Maiguwa added that he does not like the idea of coast guard which he described as a nomenclature. “If you look at it more specifically, we actually need to do a risk assessment because I have been involved in a lot of risk assessments. “One needs to look at the parameters surrounding the routes and the water, the region of the area that has personal traffic. So, it doesn’t start and end with that portion being secured,” he said. Maiguwa said that Nigeria needs to adopt the International Ship and Port Facility Security (ISPS) code. “I have always said that the ISPS provide only minimal requirements. It then means there are a lot of issues. In fact, the ISPS on its own is not applicable to all facilities. “The ISPS is not an instrument conceived by the framework to deal with maritime security threats. It is not an instrument holistically to deal with terrorism. “The framework is concerned that shipping will be used to launch terrorism attacks on the homeland and therefore it concentrated on the areas where foreign ships visit,” he said. He, however, asked what happened to an adjacent facility that does not receive foreign vessels? What happens to our vessels that are actually outside the convention? “Those were the risks to the environment. And I have said it and I will always emphasise that it is very important that we have a competent agency to man the anchorage,” he said. The Deep Blue Project knows as the Integrated National Security and Waterways Protection Infrastructure, is being championed by the Nigerian Maritime Administrative and Security Agency. Read the full article
0 notes