#Library Computer Access and Retrieval System
Explore tagged Tumblr posts
Text

LCARS display for the original Constitution-class U.S.S. Enterprise.
#Star Trek#Star Trek: The Next Generation#LCARS#Library Computer Access and Retrieval System#U.S.S. Enterprise#NCC-1701#Constitution-class#science fiction
30 notes
·
View notes
Text
Cyberchase: How to Hack the Motherboard
So, when I was writing my episode discussion post on Cyberchase Season 1 Episode 1 "Lost My Marbles", I mentioned that I might make another post about the security breach that allowed The Hacker to infect Motherboard with the virus. What did The Hacker do to set this up? How did the kids accidentally open the breach? And other questions like that. I have a bit of background in software engineering. I will try to keep things as simple as possible.
Much of this is head-canon built on top of what we see in the episode. Of course, the show plays it fast and loose with computer terminology. Don't try to hack things in real life. You will go to prison.
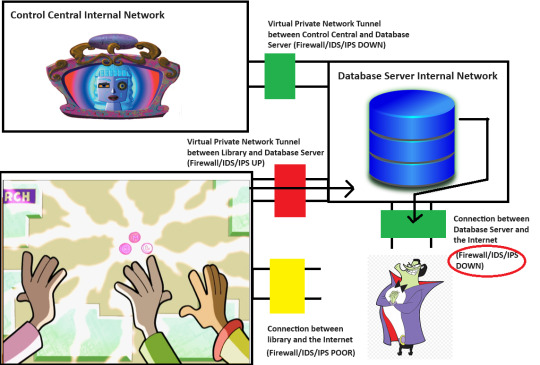
So, here's an MSPaint diagram of a tiny piece of Motherboard's setup. Keep in mind that she is the god of the Internet, and her Internet may even stretch beyond Earth into other galaxies.
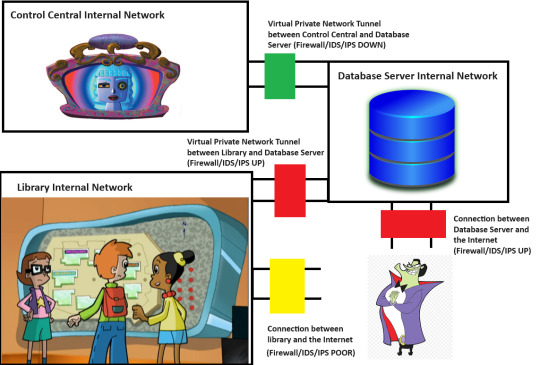
So, there are three separate network segments here. We have the library's internal network, which has the big board on it. We have Control Central's internal network, which has Motherboard on it. And then we have a Database Server internal network, which has a Database Server running on it.
The Database Server is something that I invented here. Remember that this whole diagram is head-canon. However, it's not too far-fetched to think that Motherboard must reach across Cyberspace to a separate Database Server, maybe at the Cybrary.
Now, we know that Motherboard is not directly reachable, even with her Firewall down. Otherwise, The Hacker wouldn't have needed a separate security breach to get to her. He would have just pushed the virus once she took down her firewall for maintenance.
However, Motherboard has a Virtual Private Network (VPN) tunnel to the Database Server. If The Hacker can compromise the Database Server and get his virus in there, it might be able to ride the tunnel into Control Central.
The purpose of any Firewall is to apply a set of rules to any network traffic going into or out of a network, device or application. A good Firewall configuration allows on the traffic that is needed and denies everything else. Motherboard's firewall between herself and the Database Server is currently down. The Database Server itself has connection points to the larger Internet without using a VPN tunnel. However, the Database Server's own Firewall for that access point is UP. If The Hacker tried to throw his virus at that access point, it wouldn't work.
However, there is another connection point into the Database Server. This is another VPN tunnel from the library network. Let's say that the board retrieves the data on the locations of different objects on the map and the icons for those objects by reading one of the Databases. Maybe the board also writes data to the Database to log what directions people requested.
The point here is that some traffic from the Board is authorized to pass through the Firewall on that VPN tunnel. Now, is there a way for The Hacker to get the Board to send authorized traffic over the VPN tunnel to tell the Database Server to open a breach in the Firewall for that public access point? Maybe. It is an Internet-of-Things (ioT) device. Alot of people get these devices, and then they either leave passwords set to their defaults or they forget to keep the sofware patches up to date.
There is a public access point to the Board with a poorly-configured firewall. Maybe there's a way for him to get inside. It may be possible for him to dump the virus code into the board, but there's no guarantee that it would be able to go any further, since the Firewall between the Board and the Database Server is working.
So, let's think about the Board as its own thing.

Suppose that we have two user accounts associated with the board. There is a Principle of Least Privilege that states that a given user account or system process should only be given the minimum amount of permissions required to perform its tasking. That way, if the user account or system process attempts to do something out of line with its permissions, it won't be allowed to perform the operation.
However, if you leave other unnecessary permissions open, and the user account or system process attempts to do something outside of its original intended operations, then the operation may succeed and have unintended consequences.
This also links up with the software development concept of the Minimum Viable Product. You build your software to perform only the exact tasking that it needs it perform. You don't put any additional, undocumented functions in there. Otherwise, those functions could activate and have unexpected consequences.
The board's purpose it to display the different locations. It allows for users to input two points, and it will draw a line between them to assist in navigation. We also established earlier that it reads its information from the Database and writes other information out to the Database.
However, suppose there was some undocumented functionality here. Suppose the developers had a special feature installed in the board that ran a cleanup command against the Database if you pressed three buttons in quick succession. Suppose that the cleanup command in question could be any arbitrary command. Therefore, the developers put the command into a configuration file to be read and executed by the software at runtime.
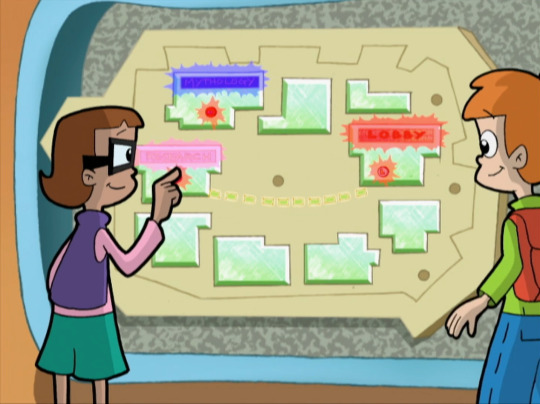
However, the developers knew that if some kids turned up and started poking the map, they could accidentally kick off the Database Cleanup command. They removed the Database Cleanup command from the configuration file. That way, if someone did poke three buttons in quick succession, the software would check the configuration file, see that there was no command defined, and then do nothing.
The trouble is that they left the part of the software that read the configuration file and ran the arbitrary command in place. So, if the command was somehow added back to that part of the configuration file, then there would be a command for the software to run. Then, if someone else pushed the three buttons, that command would be run. So, yeah, someone could put a command in there to write a bunch of junk into the Database until it filled up and crashed. Again, these are commands being sent to the Database from the Board. The Firewall would let them through just fine.
That's pretty bad, but that only lets them modify the Database, right? It's not like they can just tell the Database to open the Firewall on the server that it is sitting on, right?
Well, what if one of the things that the Database could do, upon request, was to open a command shell on the server and run a command. And what if, that command shell was able to run commands that impacted things on the server beyond the Database itself.
What if we called it "xp_cmdshell" and called the Database Server "Microsoft SQL Server 2000". Windows XP and Microsoft SQL Server 2000 would have been around at the time of "Lost My Marbles" after all. Those were also the key players in the real-world Heartland Payment Systems data breach of 2008, which inspired this post.
But hey, just because the Database could open a command shell on the Database Server doesn't mean that The Hacker could use it to bust the Database Server's external Firewall, right? He still needs a way to execute "xp_cmdshell". So, he needs an account with the correct permissions to tell the Database to execute "xp_cmdshell", and he needs the Database itself to have high-enough permissions to run a command via "xp_cmdshell" that can bust the Database Server's external firewall and open a path to Motherboard. Thankfully, the Database only run the "xp_cmdshell" for the top-level Database Administrator account.
This is where we get back to the Principle of Least Privilege. The Board should connect to the Database with a fairly low-power account. It only needs to read-from and write-to a few Database tables after all. Likewise, the Database itself should have been started on the Database Server by a fairly low-power account, as it only needs to handle reading and writing its own set of tables.
But then some moron decided to hook up the Board to the Database Server on the top-level Database Administrator Account. So, if the Board was configured to send an "xp_cmdshell" command, the Database would run it. Oh, and another moron decided to have the Database Server start the Database with the "root" account for that server. So, if the Board was configured to send in an "xp_cmdshell" command to nuke the external Firewall, then the Database would be able to nuke the external Firewall.

There is a principle called Defense-in-Depth, where you build multiple layers of defense around your critical item. That way, if a layer fails, you may be okay. We're running out of layers.
We only have one or two layers left. We know that the Board doesn't run "xp_cmdshell" for its regular operations today. Sure it has an undocumented debug mode that allows someone to execute any command in its configuration file (including "xp_cmdshell") against the Database. But someone would need to get to that file.
The board's main account doesn't give you a filesystem to play with, as they wouldn't want kids running up, poking things, and deleting the filesystem. No, you only get the interfaces that you get. You can pick two items and see a path between them. Or you can pick three items and see the undocumented debug mode run whatever command is in the configuration file.
But what if there was some sort of maintenance account accessible through the Internet that didn't enable someone to send commands to the Database, but would enable someone to get into the filesystem and mess around with it? And what if that maintenance account was still using a weak or default password because people just don't check that for IoT devices?

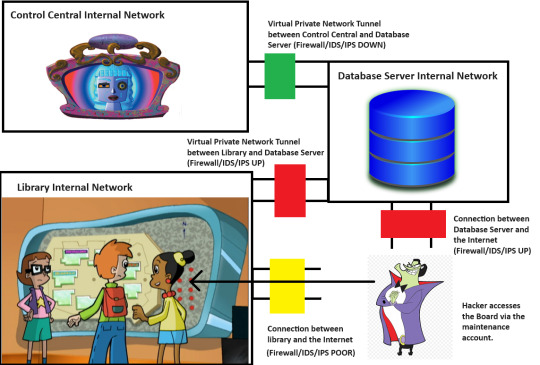
So, he's in the Board's filesystem now. That's concerning. And wouldn't you know it, yet another moron left that critical configuration file in a state where the maintenance account can make changes to it. So, of course, he found the empty configuration item for the cleanup command. Remember, this was setup to run any arbitrary command. Of course, he put in an "xp_cmdshell" command that tells the Database to nuke the external firewall on its own server.
While The Hacker was able to put the command in place, the maintenance account doesn't have the power to send commands to the Database on its own. That power is only enabled for the system account tied to the Board's user interface. So, he still has to rely on someone in the real world to push three buttons in quick succession.


Well...shit.
That's not good.

That's not good at all.
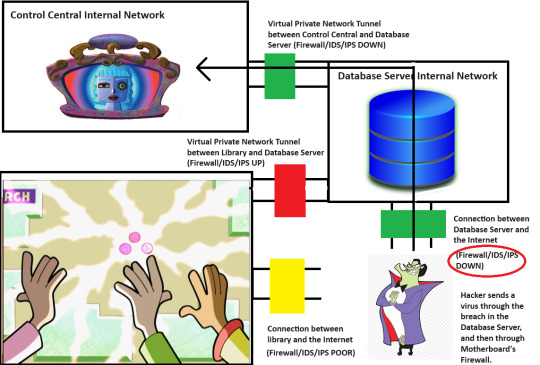


Seriously though, don't try this at home.
I suppose we can speculate on the nature of the virus. We know from Season 1 Episode 14 "Cool It" that Motherboard goes through more cryoxide than normal due to the virus. There are actual computer viruses out there that were designed to turn off heat safety warnings on CPUs and then cause them to run hotter. Some CPUs would eventually melt and ruin the computer.
The original infection destroyed the Encryptor Chip, and it is stated that only a replacement Encryptor Chip could cure the virus. The name suggests that it deals with data encryption, but perhaps it is also a virus cleanup tool. Perhaps it worked to weaken the existing virus until it was eventually overwhelmed and destroyed. Perhaps the virus exhausted most of its strength destroying the Encryptor Chip first.
In any case, curing the virus permanently would end the show.
#cyberchase#2000s#cartoon#nostalgia#pbs kids#2000s childhood#not for use in real life#you'll get busted
12 notes
·
View notes
Text
Post Graduate Diploma in Healthcare Informatics & Analytics (PGDHIA) at SIHS
Symbiosis Institute of Health Sciences (SIHS) offers you an opportunity to undergo Post Graduate Diploma in Healthcare Informatics & Analytics (PGDHIA). Healthcare informatics combine skills in healthcare business intelligence, information technology, information systems and data analytics. Doctors, nurses, and other healthcare professionals depend on healthcare informaticians to store, retrieve, and process medical data. With a Post Graduate Diploma in Healthcare Informatics & Analytics (PGDHIA) will equip the students to develop a capability in healthcare informatics and learn the technologies & skills required for the analysis of information regarding various healthcare-related factors. This programme will train the students to apply appropriate techniques to solve problems in different application areas in healthcare informatics. One can become a high-end knowledge worker in the clinical and medical fields, using information technology to help people with their health. This comprehensive program covers multiple aspects of health data informatics, including statistics for data science, augmented & virtual reality, health data analytics and artificial intelligence.
Mode of teaching: Online + Weekend Classes
Career Opportunities: 1. Chief Medical Information Officer 2. Health information Analyst 3. Healthcare IT Project Manager 4. Public Health Data Scientist 5. Health Informatics Consultant 6. Telehealth Coordinator 7. Health Information Manager 8. Electronic Medical Record Keeper
WHY SIHS ? 1. Established reputation in educational excellence. 2. World-class faculty, excellent career guidance. 3. Innovative teaching style – combination of lectures, practical training, discussions, projects, workshops. 4. State-of-the-art infrastructure. 5. Beautiful sprawling campus with excellent libraries, computer labs and Wi-Fi access. 6. Career Counselling, Training & Placement Assistance 7 Truly multicultural, dynamic and globally oriented learning environment
Admission Process - Step 1: Register online at www.sihs.edu.in and make payment of registration fees (INR 1250/-). Step 2: Attend Personal Interaction in online mode. Step 3: Check email for selection confirmation. Step 4: Verify documents and pay academic fees (INR 89,000/-).
Program Outcome - 1. Learner will be able to manage, process and analyze healthcare data 2. Learner will be able to apply knowledge gained and technical skills in the real-world healthcare settings 3. Learners will comprehend healthcare informatics principles, data analytics methodologies, and the integration of technology within healthcare systems. 4. Learners will explore machine learning, artificial intelligence, and big data analytics, understanding their applications in healthcare. 5. Learners will contribute to enhancing the quality and efficiency of healthcare services. For more details visit: https://www.sihs.edu.in/pg-diploma-in-healthcare-informatics-and-analytics
2 notes
·
View notes
Text
SPIRITED AWAY SENTENCES. // accepting!
@sinsolucion : ❛ i'd like to help you, but there's nothing i can do. it's one of our rules here. ❜
"that's... that's it? you can't do anything?"
frustration bubbled and frothed just beneath the surface, incapable of fully accepting that this was out of the hands of those who were supposed to help.
"i know i don't have evidence, but i... i know he took it. he's the only one who could."
an attempt at false confidence brought his voice into a desperate lift, golden eyes searching the face of the officer who looked no older than him. atticus had thought this would be clean and cut--a classmate stole his laptop, the police would help him retrieve it, problem solved.
but the combination of a lack of photographic evidence, zero eye witnesses, and it all occurring on the university's private campus, resulting it being at the discretion of campus police, who already told him it was a no-go...
atticus's teeth grit, angry at his helplessness, and angry at the system. he couldn't afford another laptop. he had skipped months worth of meals and saved every dollar he could to afford it. he already was testing the limits of what little aid he had--he couldn't risk retaking expensive classes just because he couldn't access the online materials, and library computers could only do so much.
"... okay, i understand."
like that, the waves of anger settled into understanding, and he apologetically bowed his head--an old habit enforced by his mother.
"thank you for your time, officer."
the police could not help--so, that simply meant he had to do as he had always done, which was handle it alone.
#sinsolucion#( i don't have a baby verse tag but just trust#trust that this is baby verse#specifically between 20-25 verse )
3 notes
·
View notes
Text
What Are the Key Technologies Behind Successful Generative AI Platform Development for Modern Enterprises?
The rise of generative AI has shifted the gears of enterprise innovation. From dynamic content creation and hyper-personalized marketing to real-time decision support and autonomous workflows, generative AI is no longer just a trend—it’s a transformative business enabler. But behind every successful generative AI platform lies a complex stack of powerful technologies working in unison.

So, what exactly powers these platforms? In this blog, we’ll break down the key technologies driving enterprise-grade generative AI platform development and how they collectively enable scalability, adaptability, and business impact.
1. Large Language Models (LLMs): The Cognitive Core
At the heart of generative AI platforms are Large Language Models (LLMs) like GPT, LLaMA, Claude, and Mistral. These models are trained on vast datasets and exhibit emergent abilities to reason, summarize, translate, and generate human-like text.
Why LLMs matter:
They form the foundational layer for text-based generation, reasoning, and conversation.
They enable multi-turn interactions, intent recognition, and contextual understanding.
Enterprise-grade platforms fine-tune LLMs on domain-specific corpora for better performance.
2. Vector Databases: The Memory Layer for Contextual Intelligence
Generative AI isn’t just about creating something new—it’s also about recalling relevant context. This is where vector databases like Pinecone, Weaviate, FAISS, and Qdrant come into play.
Key benefits:
Store and retrieve high-dimensional embeddings that represent knowledge in context.
Facilitate semantic search and RAG (Retrieval-Augmented Generation) pipelines.
Power real-time personalization, document Q&A, and multi-modal experiences.
3. Retrieval-Augmented Generation (RAG): Bridging Static Models with Live Knowledge
LLMs are powerful but static. RAG systems make them dynamic by injecting real-time, relevant data during inference. This technique combines document retrieval with generative output.
Why RAG is a game-changer:
Combines the precision of search engines with the fluency of LLMs.
Ensures outputs are grounded in verified, current knowledge—ideal for enterprise use cases.
Reduces hallucinations and enhances trust in AI responses.
4. Multi-Modal Learning and APIs: Going Beyond Text
Modern enterprises need more than text. Generative AI platforms now incorporate multi-modal capabilities—understanding and generating not just text, but also images, audio, code, and structured data.
Supporting technologies:
Vision models (e.g., CLIP, DALL·E, Gemini)
Speech-to-text and TTS (e.g., Whisper, ElevenLabs)
Code generation models (e.g., Code LLaMA, AlphaCode)
API orchestration for handling media, file parsing, and real-world tools
5. MLOps and Model Orchestration: Managing Models at Scale
Without proper orchestration, even the best AI model is just code. MLOps (Machine Learning Operations) ensures that generative models are scalable, maintainable, and production-ready.
Essential tools and practices:
ML pipeline automation (e.g., Kubeflow, MLflow)
Continuous training, evaluation, and model drift detection
CI/CD pipelines for prompt engineering and deployment
Role-based access and observability for compliance
6. Prompt Engineering and Prompt Orchestration Frameworks
Crafting the right prompts is essential to get accurate, reliable, and task-specific results from LLMs. Prompt engineering tools and libraries like LangChain, Semantic Kernel, and PromptLayer play a major role.
Why this matters:
Templates and chains allow consistency across agents and tasks.
Enable composability across use cases: summarization, extraction, Q&A, rewriting, etc.
Enhance reusability and traceability across user sessions.
7. Secure and Scalable Cloud Infrastructure
Enterprise-grade generative AI platforms require robust infrastructure that supports high computational loads, secure data handling, and elastic scalability.
Common tech stack includes:
GPU-accelerated cloud compute (e.g., AWS SageMaker, Azure OpenAI, Google Vertex AI)
Kubernetes-based deployment for scalability
IAM and VPC configurations for enterprise security
Serverless backend and function-as-a-service (FaaS) for lightweight interactions
8. Fine-Tuning and Custom Model Training
Out-of-the-box models can’t always deliver domain-specific value. Fine-tuning using transfer learning, LoRA (Low-Rank Adaptation), or PEFT (Parameter-Efficient Fine-Tuning) helps mold generic LLMs into business-ready agents.
Use cases:
Legal document summarization
Pharma-specific regulatory Q&A
Financial report analysis
Customer support personalization
9. Governance, Compliance, and Explainability Layer
As enterprises adopt generative AI, they face mounting pressure to ensure AI governance, compliance, and auditability. Explainable AI (XAI) technologies, model interpretability tools, and usage tracking systems are essential.
Technologies that help:
Responsible AI frameworks (e.g., Microsoft Responsible AI Dashboard)
Policy enforcement engines (e.g., Open Policy Agent)
Consent-aware data management (for HIPAA, GDPR, SOC 2, etc.)
AI usage dashboards and token consumption monitoring
10. Agent Frameworks for Task Automation
Generative AI platform Development are evolving beyond chat. Modern solutions include autonomous agents that can plan, execute, and adapt to tasks using APIs, memory, and tools.
Tools powering agents:
LangChain Agents
AutoGen by Microsoft
CrewAI, BabyAGI, OpenAgents
Planner-executor models and tool calling (OpenAI function calling, ReAct, etc.)
Conclusion
The future of generative AI for enterprises lies in modular, multi-layered platforms built with precision. It's no longer just about having a powerful model—it’s about integrating it with the right memory, orchestration, compliance, and multi-modal capabilities. These technologies don’t just enable cool demos—they drive real business transformation, turning AI into a strategic asset.
For modern enterprises, investing in these core technologies means unlocking a future where every department, process, and decision can be enhanced with intelligent automation.
0 notes
Text
Post 1: Why Cloud Computing & Online Collaboration Matter
Working and learning used to require being physically present, whether in libraries, offices, or classrooms. These days, people can connect, share, and complete tasks from practically anywhere in the world thanks to cloud computing as well as online collaboration technologies. A device and a dependable internet connection are all that are required.
Instead of storing and accessing data, programs, and files on their personal computers, the use of cloud computing enables users to do so online. These technologies, when paired with collaboration tools like Zoom, Google Docs, and Microsoft Teams, have completely changed the way teams work across continents, cities, and time zones.
Although the transition to remote and hybrid work had already started before the epidemic, COVID-19 hastened the process. Nearly 60% of workers worldwide now work remotely or in hybrid formats, according to McKinsey (2023). As a result, digital technologies are now necessary for collaboration and productivity rather than optional.

Original Image, made in Canva
This change is more than just a fad for high school students; it's a sneak peek at the workplace of the future. Whether you want to work in technology, healthcare, business, or the arts, you'll probably need to use cloud services to share data in real time, interact with others, and submit projects.
Understanding these systems' operation presently will benefit you:
Adjust to changing work environments
Work with assurance with remote teams.
Make efficient and secure use of digital tools.
To put it briefly, mastering cloud computing and collaboration tools is essential to becoming digitally literate and to thriving in an increasingly online, distant, and connected society.
Sources:
Clariti. (n.d.). Let's Talk: How Online Collaboration Brings Teams Together No Matter the Distance. Medium. Retrieved April 19, 2025, from https://getclariti.medium.com/lets-talk-how-online-collaboration-brings-teams-together-no-matter-the-distance-6cdd2a57cbd2
Kantata. (2025, January 9). Online collaboration in 2021: Evolution or revolution? Kantata. https://www.kantata.com/blog/article/online-collaboration-in-2021-evolution-or-revolution
Hines, M. (2024, March 21). Navigating success through online collaboration and remote workforce. The Woodard Report. https://report.woodard.com/articles/navigating-success-through-online-collaboration-and-remote-workforce-ombwr-thvwr
Module 9 - I AM AI: Thinking machines
0 notes
Text
How to Use the CNH DPA5 Adapter Effectively

Modern vehicles rely heavily on onboard computers to monitor and manage their performance. On-Board Diagnostics (OBD2) technology has become a standard for diagnosing vehicle issues efficiently. Whether you are a car enthusiast, DIY mechanic, or professional technician, an OBD2 scanner is a must-have tool for diagnosing problems, improving performance, and saving on costly repairs.In this comprehensive guide, CNH DPA5 we will explore OBD2 diagnostic tools, their benefits, key features to consider when buying one, and the top models available today.
What Is an OBD2 Scanner?
An OBD2 scanner is a device that connects to your vehicle’s onboard computer via the OBD2 port, typically located under the dashboard. It retrieves Diagnostic Trouble Codes (DTCs), live sensor data, and other essential information that can help diagnose and fix vehicle issues.
OBD2 scanners fall into three main categories:
Basic Code Readers: Simple tools that retrieve and clear trouble codes.
DIY Scanners: Offer live data monitoring and more detailed diagnostics.
Professional Scanners: Advanced tools with bi-directional controls, ECU programming, and other high-end features.
Benefits of Using an OBD2 Scanner:
Cost Savings: Helps identify problems before taking the vehicle to a mechanic, reducing unnecessary repair costs.
Improved Vehicle Performance: Provides real-time data to monitor engine performance and fuel efficiency.
Early Problem Detection: Allows users to detect minor issues before they turn into costly repairs.
Emissions Control: Helps ensure the vehicle meets emission standards by checking readiness status.
User-Friendly Interface: Most modern OBD2 scanners feature smartphone compatibility and intuitive apps.
Enhanced Safety: Identifies potential safety concerns, such as ABS and airbag system faults.
Better Fuel Economy: Helps diagnose engine issues that may be causing excessive fuel consumption.
Key Features to Consider When Buying an OBD2 Scanner
Compatibility: Ensure the scanner works with your vehicle’s make and model.
Live Data Monitoring: Provides real-time information on engine performance, fuel economy, and sensor functionality.
DTC Lookup Library: Built-in code definitions help users understand error messages without additional research.
Wireless Connectivity: Bluetooth or Wi-Fi connectivity enables users to pair the scanner with smartphones and tablets.
Advanced Diagnostics: High-end scanners support ABS, SRS, transmission, and other specialized system diagnostics.
Software Updates: Regular updates ensure compatibility with newer vehicle models.
Build Quality: A durable design is crucial for long-term usability, especially for professional use.
Multilingual Support: Some scanners provide diagnostic reports in multiple languages for wider accessibility.
Top OBD2 Scanners in 2025
1. BlueDriver Bluetooth Pro Scanner
Features: Wireless connectivity, extensive diagnostic coverage, mobile app integration.
Best For: DIY enthusiasts and car owners who want a detailed yet user-friendly tool.
2. Autel MaxiCOM MK808
Features: Advanced diagnostics, touchscreen interface, wide vehicle coverage.
Best For: Mechanics looking for a near-professional scanner at an affordable price.
3. FIXD OBD2 Scanner
Features: User-friendly app, real-time monitoring, maintenance alerts.
Best For: Beginners and everyday drivers looking for a simple solution.
4. Foxwell NT301
Features: Live data, freeze frame data, emissions testing readiness.
Best For: Budget-conscious buyers seeking a reliable handheld scanner.
5. Autel MaxiSys Elite
Features: ECU programming, bi-directional controls, professional diagnostics.
Best For: Professional mechanics and auto repair shops.
How to Use an OBD2 Scanner
Locate the OBD2 Port: Found under the dashboard or steering column.
Turn On the Ignition: Power up the vehicle but don’t start the engine.
Plug in the Scanner: Insert the OBD2 device into the port.
Read Codes: Use the scanner’s interface to retrieve trouble codes.
Interpret Codes: Check the meaning of DTCs using the built-in library or an online database.
Clear Codes: If the issue has been resolved, you can clear the codes to turn off warning lights.
Monitor Live Data: Analyze real-time data for deeper diagnostics.
Common Mistakes to Avoid When Buying an OBD2 Scanner
Ignoring Compatibility: Always check if the scanner supports your vehicle’s make and model.
Choosing the Cheapest Option: Low-cost scanners often lack essential features.
Neglecting Software Updates: Ensure the manufacturer provides regular updates.
Overlooking User-Friendliness: A complicated interface can make diagnostics difficult.
Not Checking Warranty: A good warranty ensures long-term protection and support.
Future of OBD2 Diagnostic Tools:
As automotive technology advances, OBD2 scanners are becoming smarter and more feature-rich. Emerging trends include:
AI-Powered Diagnostics: Some modern scanners incorporate artificial intelligence to provide predictive maintenance recommendations.
Cloud-Based Data Storage: Enabling users to store and access diagnostic data remotely.
Integration with Smart Devices: Enhanced compatibility with mobile apps and voice assistants for a seamless user experience.
Expanded Vehicle Coverage: More support for electric and hybrid vehicles.
Conclusion:
Investing in a quality OBD2 scanner is a smart decision for any vehicle owner or mechanic. Whether you need a basic scanner for occasional use or a professional-grade tool, understanding the features and benefits will help you make the right choice. By selecting the right OBD2 scanner, you can diagnose problems early, save on repair costs, and ensure your vehicle runs efficiently. With advancements in technology, OBD2 scanners will continue to play a crucial role in vehicle diagnostics and maintenance.
0 notes
Text
For security veterans, future developers, and security enthusiasts alike, the plain truth is that the tech terrain is evolving rapidly. As a result, the cybersecurity sector is not only trendy but also quite challenging. Considering the competitive landscape, it's imperative to understand some programming languages to help you stay ahead of the pack. Here are some of the programming languages necessary in the cybersecurity sector. HTML HTML is a markup language and also the most fundamental programming language. It's vital because it's used by almost every website on the internet. We consider HTML as the slow walk before you can learn how to walk. This language is quite popular and is used by 90.7% of all websites. Hackers can integrate HTML code into web pages in a widespread multi-site scripting attack. Normally, hackers use HTML to circulate false information or deform a website. And in content spoofing, cybercriminals can manipulate the code in a web application. This can make the code visible to visitors of the webpage. Understanding the HTML language can help you get a job as a front-end developer in most organizations. In this position, some of your responsibilities would be the deployment of mitigation measures against cross-site scripting and content spoofing while developing applications and webpages. C C is the best programming language for reverse engineering threats and identifying exposures. Notably, this programming language has been in use since 1970, but it's still a popular choice because it's simpler to learn. C enables a programmer to create and deploy low-level code. Security-conscious cyber professionals will use C to ensure websites have zero susceptibilities. And on the other hand, hackers often use C to find website exposures for tampering with the website. Lint is the basic code analysis tool for the C language and was developed in 1978. Since its inception, many variations have hit the market. Lint is mostly used for discovering programming errors, technical errors, and bugs. Becoming proficient in the C language can get you a job as a cybersecurity defense analyst. And in this position, you will be in charge of finding out exposures, threats and developing threat analysis protocols. Python Python is essential in helping programmers conduct malware research and automate tasks. In addition, there is a huge third-party scripts library that is freely accessible. Typically, a script kiddie is one of the popular terms in the hacking arena, especially by people who only rely on scripts because they can't build their own code. This programming approach is meant for script kiddies and is also used by hacking tools like Auto Sploit. Manipulating remote computer systems is among the common tricks used by hackers, and Auto Sploit is designed to automate the process. The Python script relies on a command-line interface and records to retrieve data from the Shodan database. If you understand what cybersecurity is and the Python language, a SOC support specialist is among the job roles you can take. In this role, you'll be required to create scripts and tools that secure websites from cyber-attacks. You can also use data logs and artifacts to analyze deeper issues and point out the problems. C++ C++ programming language is an augmented version of the C language. It was first introduced in 1985, but it is different from C. C++ assists in handling classes and objects that C doesn't support. It is not only faster but also outperforms C. Nevertheless, C++ is only used on less than 0.1% of all websites. Flawfinder is the analysis tool designed for finding vulnerabilities in both C++ and C codes. This tool contains an in-built database of language processes that hunt for known threats like race disorders, format string problems, impoverished random-number accession, and buffer overflow issues. And since both C and C++ are related, most employers prefer applicants who possess a broad understanding of the languages.
If you are considering a cybersecurity career, this programming language is very important for success in the field. JavaScript JavaScript is one of the most prominent and extensively used programming languages. While it's a standard programming language, it is employed in at least 95% of all websites. If you are familiar with React JS or NodeJS, then you already know that JavaScript is the common programming language. Therefore, this implies that websites or applications using the language can be targeted for malicious manipulation. Typically, JavaScript enables developers to deploy any code when visitors are on the website. While this enhances the site's overall functionality, it can be used to generate an adverse functionality without the visitor's knowledge. An adequate understanding of the JavaScript language can help you get the position of a JavaScript specialist in the cybersecurity space. Some of the responsibilities in this position include ensuring security against cyberattacks, designing user interfaces in websites, and managing the development protocols for API techniques. Conclusion Cybersecurity is more than just understating potential vulnerabilities and mitigation measures. A successful cybersecurity professional should learn to think and act like a hacker. Therefore, extensive knowledge of various programming languages will enable you to anticipate a hacker's strategy and deploy appropriate mitigation measures. Nevertheless, it's not compulsory to learn every programming language, but understanding the basic languages is vital.
0 notes
Text
B.L.I.S Admission 2025 Open- Course Details, Fees & Career Opportunities

About Library Information Science B.L.I.S. Course:
Students interested in library management, information science, digital archiving, and knowledge organization can enroll in the one-year undergraduate Bachelor of Library and Information Science (B.L.I.S.) program. Students who complete the course will have the abilities needed to efficiently manage and arrange information in corporate settings, research institutes, libraries, and archives. Typically lasting one year (two semesters), the B.L.I.S. degree aims to give students an education in research methodology, digital archiving, library management, and information technology.
Eligibility Criteria B.L.I.S. Admission
A bachelor’s degree in any field from an accredited university with at least 50% of the possible points (may differ by institution) is a prerequisite.
No particular subject background is necessary for admission; however, certain colleges may demand an entrance exam or interview.
Core Subjects in B.L.I.S. Course
The Function of Libraries in Society o Public, Academic, and Special Library Types o Library Law and Associations
Theory and Practice of Library Cataloging: The Goals and Uses of Cataloging o Classified and Dictionary Catalog Types o Standards: AACR-II, MARC, RDA.
Information Sources and Services o Print and Digital Resources o Reference and Referral Services o Bibliographic and Current Awareness Services o Types of Information Sources (Primary, Secondary, Tertiary)
Library Information Technology o Computer and Networking Fundamentals o Library Automation Software ,Digital Libraries
Library Science Research Methods o Fundamentals of Research and Report Writing o Data Gathering and Analysis o Citation Styles (APA, MLA, Chicago)
Digital Libraries and Knowledge Management o Overview of Digital Libraries o Open Access Programs (DOAJ, OAI-PMH) o Preservation of Digital Content and Copyright Concerns
Automation and Networking in Libraries o Software for Library Management (ILS, OPAC) o RFID and Barcode Technology in Libraries o Networks for Libraries (INFLIBNET, DELNET).
Project work and internships; practical instruction in a library or information center; library science dissertations or case studies
Classification of Libraries (Theory & Practice): Fundamental Ideas of Library Classification o Categories (Universal Decimal Classification, Dewey Decimal Classification) o Labeling, Indexing, and Filing
Additionally, students can also learn about E-Resource Management (E-books, E-journals, Digital Repositories),Artificial Intelligence in Library Science ,Big Data & Analytics in Information Science ,Patent Information System & Intellectual Property Rights (IPR)
Skill Development in B.L.I.S. Course –
By the end of the program, students gain expertise in:
Library classification & cataloging
Digital library management
Use of library automation tools
Archival and preservation techniques
Data organization & retrieval
Course Details Subjects Covered in B.L.I.S. as a Library Science Degree Course –
Library Classification and Cataloging
Information Sources and Services
Digital Libraries & Information Technology
Research Methods in Library Science
Knowledge Organization and Information Retrieval
Library Automation and Networking
Career Opportunities After B.L.I.S. Course –
Graduates can work in various roles such as:
Librarian (Schools, Colleges, Universities)
Archivist (Museums, Research Institutions)
Information Officer (Government & Corporate Organizations)
Digital Librarian (Online Libraries, IT Companies)
Cataloger / Indexer (Publishing Houses, Media Companies)
Library Assistant (Public & Private Libraries)
Importance of B.L.I.S Programmes:
The Bachelor of Library and Information Science (B.L.I.S.) is a specialized degree that prepares students for careers in library management, information organization, and digital archiving. The study of B.L.I.S. is important for several reasons:
Career Opportunities in the Information Sector
B.L.I.S. graduates can work as librarians, archivists, information officers, and digital curators in public libraries, academic institutions, research centers, corporate organizations, and government agencies.
The rise of digital libraries and data management has increased the demand for information professionals.
Enhancing Information Management Skills
The program teaches cataloging, classification, indexing, and documentation, which are essential skills for organizing and retrieving information efficiently.
Students also learn about digital libraries, database management, and emerging technologies in the field.
Role in Education and Research
Librarians play a crucial role in helping students, researchers, and professionals access accurate and reliable information.
B.L.I.S. graduates support academic research, digital archiving, and preservation of knowledge.
Digital Transformation and IT Integration
With the advancement of technology, library science now includes digital resource management, e-learning platforms, and knowledge organization.
Courses in information technology, artificial intelligence, and big data help students stay relevant in the digital age.
Contribution to Society and Literacy
Librarians and information professionals help promote literacy, reading culture, and lifelong learning.
They assist in making information accessible to all, including marginalized communities.
Opportunities for Further Studies and Specialization
Graduates can pursue higher education such as Master of Library and Information Science (M.L.I.S.), Ph.D., or certifications in digital librarianship, data science, and knowledge management.
Job Security and Growth
Information professionals are essential in all industries, making library science a stable career choice.
With the digitalization of records and increased demand for information organization, career growth in this field is promising.
Studying B.L.I.S. is valuable for those interested in information management, library services, and digital archiving. The degree not only provides diverse career opportunities but also plays a crucial role in knowledge dissemination, education, and research in the modern world..
Why Choose UMU for B.L.I.S. in India?
✔️ Growing demand for library professionals in digital and corporate sectors ✔️ Flexible learning options (Regular & Distance Mode) ✔️ Opportunities in both government and private sectors ✔️ Further studies available (M.L.I.S., Ph.D. in Library Science)
Usha Martin University invites applications for its BLIS Admission 2025 (Bachelor of Library and Information Science) program for the 2025 academic session. This program is designed for aspiring library professionals, equipping them with expertise in information management, digital archiving, research methodologies, and library automation systems. Graduates can pursue careers in academic libraries, research institutions, digital libraries, and corporate information centers.
Take the first step towards a promising career in Library and Information Science. Apply now!
#B.L.I.S Admission 2025#bachelor degree#library and information blis course#blis course admission#library course blis#top blis course in ranchi#department oif library science
0 notes
Text
Tips for Understanding Computer Databases for Homework Assignments

In today’s digital world, databases play a crucial role in managing and organizing vast amounts of information. Whether you're a student learning database concepts or working on complex assignments, understanding computer databases can be challenging. This blog will guide you through essential tips for mastering computer databases and help you complete your homework efficiently. If you're looking for computer database assistance for homework, All Assignment Experts is here to provide expert support.
What is a Computer Database?
A computer database is a structured collection of data that allows easy access, management, and updating. It is managed using a Database Management System (DBMS), which facilitates storage, retrieval, and manipulation of data. Popular database systems include MySQL, PostgreSQL, MongoDB, and Microsoft SQL Server.
Why is Understanding Databases Important for Students?
Databases are widely used in industries like banking, healthcare, and e-commerce. Students pursuing computer science, information technology, or data science must grasp database concepts to build a strong foundation for future careers. Database knowledge is essential for managing large data sets, developing applications, and performing data analysis.
Tips for Understanding Computer Databases for Homework Assignments
1. Master the Basics First
Before diving into complex queries, ensure you understand basic database concepts like:
Tables and Records: Databases store data in tables, which contain rows (records) and columns (fields).
Primary and Foreign Keys: Primary keys uniquely identify each record, while foreign keys establish relationships between tables.
Normalization: A technique to eliminate redundancy and improve database efficiency.
2. Learn SQL (Structured Query Language)
SQL is the standard language for managing databases. Some essential SQL commands you should learn include:
SELECT – Retrieve data from a database.
INSERT – Add new records to a table.
UPDATE – Modify existing records.
DELETE – Remove records from a table.
JOIN – Combine data from multiple tables.
Using online SQL playgrounds like SQL Fiddle or W3Schools can help you practice these commands effectively.
3. Use Online Resources and Tools
Numerous online platforms provide computer database assistance for homework. Websites like All Assignment Experts offer professional guidance, tutorials, and assignment help to enhance your understanding of databases. Other useful resources include:
W3Schools and TutorialsPoint for database tutorials.
YouTube channels offering step-by-step database lessons.
Interactive coding platforms like Codecademy.
4. Work on Real-Life Database Projects
Practical experience is the best way to solidify your knowledge. Try creating a small database for:
A library management system.
An online store with customer orders.
A student database with courses and grades.
This hands-on approach will help you understand real-world applications and make it easier to complete assignments.
5. Understand Database Relationships
One of the biggest challenges students face is understanding database relationships. The three main types include:
One-to-One: Each record in Table A has only one corresponding record in Table B.
One-to-Many: A record in Table A relates to multiple records in Table B.
Many-to-Many: Multiple records in Table A relate to multiple records in Table B.
Using Entity-Relationship Diagrams (ERDs) can help visualize these relationships.
6. Debug SQL Queries Effectively
If your SQL queries aren’t working as expected, try these debugging techniques:
Break queries into smaller parts and test them individually.
Use EXPLAIN to analyze how queries are executed.
Check for syntax errors and missing table relationships.
7. Seek Expert Assistance When Needed
If you find yourself struggling, don’t hesitate to seek help. All Assignment Experts offers computer database assistance for homework, providing expert solutions to your database-related queries and assignments.
8. Stay Updated with Advanced Database Technologies
The database field is constantly evolving. Explore advanced topics such as:
NoSQL Databases (MongoDB, Firebase): Used for handling unstructured data.
Big Data and Cloud Databases: Learn about databases like AWS RDS and Google BigQuery.
Data Security and Encryption: Understand how databases protect sensitive information.
Conclusion
Understanding computer databases is crucial for students handling homework assignments. By mastering basic concepts, practicing SQL, utilizing online resources, and working on real projects, you can excel in your database coursework. If you need professional guidance, All Assignment Experts provides top-notch computer database assistance for homework, ensuring you grasp key concepts and score better grades.
Start applying these tips today, and you’ll soon develop a solid understanding of databases!
#computer database assistance for homework#computer database assistance#education#homework#do your homework
1 note
·
View note
Text

LCARS display for the Nova-class starship.
#Star Trek#Star Trek: Voyager#LCARS#Library Computer Access and Retrieval System#Nova-class#Starfleet#Starfleet starships#starships#science fiction
18 notes
·
View notes
Text
```markdown
Blockchain Indexing for Beginners
Blockchain technology has been making waves in various industries, from finance to healthcare. One of the key aspects that makes blockchain so powerful is its ability to store and manage data securely and transparently. However, with the increasing amount of data being stored on blockchains, it becomes crucial to have efficient ways to search and retrieve this information. This is where blockchain indexing comes into play.
What is Blockchain Indexing?
Blockchain indexing is the process of organizing and categorizing data stored on a blockchain network. It allows users to quickly find specific transactions or blocks without having to scan through the entire blockchain. Imagine if every book in a library was randomly placed; finding a specific book would be nearly impossible. Similarly, without proper indexing, searching for specific data on a blockchain would be extremely time-consuming and inefficient.
Why is Blockchain Indexing Important?
1. Efficiency: By indexing, you can significantly reduce the time it takes to locate specific data. This is particularly important for applications that require real-time data retrieval.
2. Scalability: As more data is added to the blockchain, the need for efficient indexing becomes even more critical. Without it, the system could become sluggish and less responsive.
3. User Experience: For end-users, an efficiently indexed blockchain means faster and more reliable interactions with blockchain-based applications.
How Does Blockchain Indexing Work?
Blockchain indexing typically involves creating a separate database that stores metadata about the blockchain. This metadata includes information such as transaction IDs, timestamps, and other relevant details. When a user wants to query the blockchain, they can do so by interacting with this indexed database rather than scanning the entire blockchain.
Challenges in Blockchain Indexing
While blockchain indexing offers many benefits, it also presents some challenges:
Data Privacy: Ensuring that the indexing process does not compromise the privacy of the data stored on the blockchain is crucial.
Security: The security of the indexing system itself must be robust to prevent unauthorized access or manipulation of the indexed data.
Resource Intensive: Indexing can be resource-intensive, requiring significant computational power and storage capacity.
Conclusion
Blockchain indexing is a vital component in making blockchain technology more accessible and practical for a wide range of applications. As the technology continues to evolve, we can expect to see more sophisticated indexing solutions that address the current challenges while enhancing the overall user experience.
What Do You Think?
What are your thoughts on blockchain indexing? Do you think it will become a standard feature in all blockchain applications? Share your views in the comments below!
```
加飞机@yuantou2048
相关推荐
王腾SEO
0 notes
Text

LIBRARY ASSISTANT (9 POSTS) Listing Reference: CSDS052-2025 (E)Listing Status: Open Position Summary Company: Not SpecifiedIndustry: Library and Information ServicesJob Category: Library AssistantLocation: Not SpecifiedContract Type: Three-Year Fixed-Term ContractRemuneration: R239,052.00 – R332,016.00 per annum (Estimated Package: R336,203.00 – R454,528.00 per annum)EE Position: YesClosing Date: 04.03.2025 Introduction Libraries are the cornerstone of knowledge and community development, providing access to information, education, and cultural enrichment. The role of a Library Assistant is pivotal in ensuring that these services are delivered efficiently and effectively. This position offers an exciting opportunity for individuals passionate about literature, education, and community service to contribute to the growth and development of library services. With a competitive remuneration package and a three-year fixed-term contract, this role is ideal for those seeking to build a career in library and information services. Job Description The Library Assistant will play a key role in supporting the delivery of library information services. This includes a wide range of responsibilities aimed at ensuring the smooth operation of the library and its programs. The primary duties include: - Assisting with Branch Administration: Supporting the day-to-day administrative functions of the library branch to ensure efficient operations. - Information Retrieval: Helping users locate and access information resources, both physical and digital. - Circulation Services: Managing the lending and return of library materials, including cataloging and shelving. - Collection Development: Assisting in the acquisition, weeding, and development of the library’s collection to ensure it meets the needs of the community. - Program Implementation: Supporting the creation and execution of reading programs and educational initiatives to foster a culture of reading and learning. - Educational Support: Providing assistance to students and educators by offering resources and guidance for academic success. Ideal Candidate The ideal candidate for this position is someone who is passionate about libraries, education, and community service. They should possess the following qualifications and attributes: - Educational Background: A Grade 12 certificate is required. Additional qualifications in library and information studies will be an advantage. - Experience: Relevant experience in a library environment is preferred, though not mandatory. - Technical Skills: Proficiency in SirsiDynix Symphony or any library management system is a plus. Computer literacy is essential. - Personal Attributes: The candidate should demonstrate integrity, intelligence, patience, imagination, flexibility, and a willingness to accept responsibility. They should also be decisive, detail-oriented, and empathetic. Role Responsibility The Library Assistant will be responsible for a variety of tasks that contribute to the overall functioning of the library. These responsibilities include: - Administrative Support: Assisting with the management of library records, reports, and correspondence. - User Assistance: Providing guidance to library users in locating and accessing information resources. - Collection Management: Helping to maintain and develop the library’s collection through acquisition, cataloging, and weeding. - Program Development: Supporting the implementation of reading programs and educational initiatives to promote literacy and learning. - Community Engagement: Assisting in outreach activities to engage the community and promote library services. Skills & Attributes To excel in this role, the Library Assistant should possess the following skills and attributes: - Communication Skills: Strong verbal and written communication skills to interact effectively with library users and colleagues. - Organizational Skills: Ability to manage multiple tasks and prioritize effectively to meet deadlines. - Technical Proficiency: Familiarity with library management systems and basic computer applications. - Attention to Detail: A keen eye for detail to ensure accuracy in cataloging, record-keeping, and other administrative tasks. - Empathy and Patience: The ability to understand and respond to the needs of diverse library users with patience and empathy. - Teamwork: A collaborative mindset to work effectively with other library staff and stakeholders. Why This Role Matters Libraries are more than just repositories of books; they are vibrant community hubs that provide access to knowledge, foster lifelong learning, and promote cultural enrichment. As a Library Assistant, you will play a crucial role in ensuring that these services are accessible to all members of the community. Your work will directly impact the educational and cultural development of the community, making this a deeply rewarding career choice. How to Apply If you meet the requirements and are excited about the opportunity to contribute to the field of library and information services, we encourage you to apply. Please ensure that your application includes the following: - A detailed CV highlighting your qualifications and experience. - A cover letter explaining why you are the ideal candidate for this role. - Copies of your educational certificates and any relevant certifications. Applications should be submitted before the closing date of 04.03.2025. For any enquiries, please contact Lebogang Joe at 012 358 4653 or B Buthelezi at 012 358 8885. The role of a Library Assistant is both challenging and rewarding, offering the opportunity to make a meaningful impact on the community. If you are passionate about books, education, and community service, this position provides an excellent platform to build a fulfilling career in library and information services. Don’t miss this chance to join a dynamic team and contribute to the growth and development of library services. Apply today and take the first step toward a rewarding career! LIBRARIAN (5 POSTS) Listing Reference: CSDS054-2025 (E)Listing Status: Open Position Summary Company: Not SpecifiedIndustry: Library and Information ServicesJob Category: LibrarianLocation: TshwaneContract Type: Three-Year Fixed-Term ContractRemuneration: R376,152.00 – R522,420.00 per annum (Estimated Package: R510,705.00 – R696,877.00 per annum)EE Position: YesClosing Date: 04.03.2025 Introduction Libraries are vital institutions that empower communities by providing access to knowledge, fostering education, and promoting a culture of reading. The role of a Librarian is central to the effective management and delivery of these services. This position offers a unique opportunity for qualified and experienced professionals to lead and innovate in the field of library and information science. With a competitive remuneration package and a three-year fixed-term contract, this role is ideal for individuals passionate about making a difference in their community through library services. Job Description The Librarian will be responsible for managing a community library and information service, ensuring that it meets the needs of the residents of Tshwane as well as national and international research clients. The primary duties include: - Collection Management: Compiling and maintaining special collections, regardless of physical format, to ensure a diverse and relevant library offering. - Information Services: Rendering an information service by conducting information interviews, answering information requests, and evaluating provided information. - Supervision: Overseeing all functions performed at the library, including administrative tasks and outreach activities. - Training and Development: Managing the training of subordinates to ensure the delivery of quality services in line with organizational policies and self-development goals. - Reading Culture Promotion: Creating and maintaining a reading culture through reader awareness programs and educational support initiatives. - Collection Development: Building and maintaining the library collection to ensure it remains current and meets user needs. Ideal Candidate The ideal candidate for this position is a highly qualified and experienced professional with a passion for library and information science. They should possess the following qualifications and attributes: - Educational Background: An appropriate three-year career-related tertiary qualification (national diploma or degree) in Library and Information Science. - Experience: At least two years of relevant library experience. Supervisory experience will be an added advantage. - Technical Skills: Computer literacy and proficiency in the SirsiDynix Symphony library system or any library system. - Personal Attributes: The candidate should demonstrate professional and technical proficiency, leadership skills, good communication skills, direction-setting skills, client orientation, customer service ability, project management skills, ability to work under pressure, analytical skills, and organizational skills. Role Responsibility The Librarian will be responsible for a wide range of tasks that contribute to the effective management and operation of the library. These responsibilities include: - Collection Management: Ensuring the library’s collection is diverse, relevant, and well-maintained. - Information Services: Providing accurate and timely information to library users, including conducting information interviews and answering information requests. - Supervision: Overseeing the daily operations of the library, including administrative tasks and outreach activities. - Training and Development: Ensuring that library staff are well-trained and capable of delivering high-quality services. - Reading Culture Promotion: Implementing programs and initiatives to promote a culture of reading and support educational efforts. - Collection Development: Continuously updating and expanding the library’s collection to meet the evolving needs of the community. Skills & Attributes To excel in this role, the Librarian should possess the following skills and attributes: - Leadership Skills: Ability to lead and inspire a team to achieve organizational goals. - Communication Skills: Strong verbal and written communication skills to interact effectively with library users and colleagues. - Technical Proficiency: Familiarity with library management systems and basic computer applications. - Project Management Skills: Ability to plan, execute, and manage projects effectively. - Analytical Skills: Ability to analyze information and make informed decisions. - Organizational Skills: Ability to manage multiple tasks and prioritize effectively to meet deadlines. - Customer Service Skills: A strong focus on client orientation and customer service to ensure user satisfaction. Why This Role Matters Libraries play a crucial role in the educational and cultural development of communities. As a Librarian, you will have the opportunity to make a significant impact by managing and enhancing library services. Your work will directly contribute to the quality of life of the people of Tshwane, making this a deeply rewarding career choice. How to Apply If you meet the requirements and are excited about the opportunity to contribute to the field of library and information science, we encourage you to apply. Please ensure that your application includes the following: - A detailed CV highlighting your qualifications and experience. - A cover letter explaining why you are the ideal candidate for this role. - Copies of your educational certificates and any relevant certifications. Applications should be submitted before the closing date of 04.03.2025. For any enquiries, please contact Lebogang Joe at 012 358 4653 or B Buthelezi at 012 358 8885. The role of a Librarian is both challenging and rewarding, offering the opportunity to make a meaningful impact on the community. If you are passionate about library and information science and have the necessary qualifications and experience, this position provides an excellent platform to build a fulfilling career. Don’t miss this chance to join a dynamic team and contribute to the growth and development of library services in Tshwane. Apply today and take the first step toward a rewarding career! ADMINISTRATIVE OFFICER Location: All regions | Reference Code: ECDE174-2024 (E) | Closing Date: 17.02.2025 | Are you detail-oriented, organized, and passionate about providing exceptional administrative support? The City of Tshwane is seeking a dedicated individual to join their team as an Administrative Support professional. This role is critical in ensuring the smooth operation of departmental functions and requires a candidate with strong organizational skills, a proactive mindset, and the ability to thrive in a fast-paced environment. About the City of Tshwane The City of Tshwane is one of South Africa’s largest metropolitan municipalities, encompassing the vibrant capital city of Pretoria. Known for its rich history, cultural diversity, and economic significance, the City of Tshwane is committed to delivering high-quality services to its residents and stakeholders. The municipality prides itself on fostering a work environment that values innovation, teamwork, and excellence. As an employer, the City of Tshwane offers opportunities for professional growth, competitive benefits, and the chance to contribute meaningfully to the community. This administrative support role is an excellent opportunity to be part of a dynamic team that plays a vital role in the city’s operations. Role Responsibility The successful candidate will be responsible for a wide range of administrative tasks to ensure the efficient functioning of the department. Key responsibilities include: File and Document Management - Post Management: Circulate and file incoming post, ensuring timely distribution to relevant parties. - File Maintenance: Open new files, close full files, and manage temporary files as needed. - Record-Keeping: Maintain accurate mark-out lists and registers for opened files. - Discrepancy Resolution: Identify and resolve discrepancies in file totals by printing and reviewing lists. Communication and Enquiries - Counter Duty: Handle counter inquiries and provide excellent customer service to the public. - Telephone Enquiries: Address incoming calls related to file dispatching, letter tracing, and other departmental queries. Fleet and Asset Administration - Fleet Management: Conduct administrative duties related to fleet services, including scheduling maintenance, managing licenses, and handling insurance claims. - Asset Management: Oversee administrative tasks for division assets, including insurance-related matters and periodical contracts. General Administrative Support - Remittance Register: Manage the remittance register and ensure accurate record-keeping. - Document Distribution: Send job forums and information documents to relevant sections. - Data Management: Destroy outdated printouts and delete obsolete computer information after six months. The Ideal Candidate The City of Tshwane is looking for a candidate who embodies the following skills, attributes, and qualifications: Qualifications and Experience - Education: A Grade 12 certificate or equivalent qualification. - Experience: At least six months of relevant working experience in administrative support services. - Technical Skills: Proficiency in computer literacy, including Microsoft Office Suite and other relevant software. Personal Attributes and Competencies - Attention to Detail: Ability to maintain accuracy and precision in all tasks. - Time Management: Strong organizational skills to prioritize and complete tasks efficiently. - Team Player: Collaborative mindset with the ability to work well in groups and individually. - Multitasking: Capability to handle multiple tasks simultaneously without compromising quality. - Stress Management: Ability to work under pressure and meet tight deadlines. - Assertiveness: Confidence in dealing with the public and liaising with stakeholders. - Physical and Mental Fitness: Preparedness to tackle challenging tasks with resilience. Why Join the City of Tshwane? Working for the City of Tshwane offers more than just a job—it’s an opportunity to make a meaningful impact in a thriving community. Here’s why you should consider this role: - Professional Growth: Access to training and development programs to enhance your skills. - Community Impact: Contribute to the delivery of essential services that improve the lives of residents. - Collaborative Environment: Work alongside a diverse and supportive team. - Competitive Benefits: Enjoy a comprehensive benefits package and job security. How to Apply If you meet the requirements and are excited about this opportunity, we encourage you to apply. For further inquiries, please contact: - Christo Geldenhuys: 012 358 8446 - Thabani Khanyile: 012 358 2893 Position ID: S70002311 The City of Tshwane’s Administrative Support role is an excellent opportunity for individuals who are passionate about organization, efficiency, and making a difference. If you possess the required skills and attributes, don’t miss this chance to join a forward-thinking organization dedicated to excellence. Apply today and take the first step toward a rewarding career with the City of Tshwane! BUILDING CONTROL SUPPORT OFFICER Location: All regions | Reference Code: ECDE173-2024 (E) | Closing Date: 17.02.2025 | Are you a highly organized and experienced administrative professional looking for a challenging and rewarding role? The City of Tshwane is seeking a dedicated individual to manage information, support, and general administrative services for the office of the director. This role is pivotal in ensuring the efficient functioning of the department and requires a candidate with strong leadership, financial, and administrative skills. About the City of Tshwane The City of Tshwane is a leading metropolitan municipality in South Africa, encompassing the bustling capital city of Pretoria. Renowned for its rich cultural heritage, economic significance, and commitment to service delivery, the City of Tshwane is dedicated to improving the lives of its residents and stakeholders. As an employer, the City of Tshwane offers a dynamic work environment, opportunities for professional growth, and the chance to contribute to meaningful community development. This role is an excellent opportunity to join a team that values excellence, innovation, and collaboration. Role Responsibility The successful candidate will be responsible for providing comprehensive administrative, financial, and logistical support to the office of the director. Key responsibilities include: Administrative Management - Plan Submission and Approval: Manage administrative processes for the submission and approval of building and site development plans. - Stakeholder Liaison: Act as a liaison between relevant departments, divisions, the public, and clients. - Correspondence Management: Oversee incoming and outgoing correspondence, ensuring timely and accurate communication. - Information Management: Capture information on the computer and manage file returns to the registry. Financial Administration - Budget Management: Compile the yearly income and capital budget for the unit and exercise control over the approved budget. - Asset Management: Maintain the asset register for the Building Control Subsection, ensuring compliance with statutory regulations. Health and Safety - Occupational Health and Safety: Act as the occupational health and safety officer for the office, ensuring a safe working environment. Read the full article
0 notes
Text
Computeroids.com Backup and Driver: The Ultimate Solution for Your Data and Device Management
In the modern age of technology, efficient data management and hardware functionality are paramount. Computeroids Backup and Driver services offer a robust solution to these challenges by ensuring secure backups and seamless driver management for your devices. This article delves into the features, benefits, and best practices for leveraging these services to maintain a smooth computing experience.
Understanding Computeroids.com Backup
Data is the backbone of any digital operation, whether personal or professional. Computeroids Backup provides a comprehensive system to protect your information against unexpected loss. Here's what makes it stand out:
Automated Backups Computeroids Backup offers automated scheduling to save your files regularly. You can set daily, weekly, or monthly backups, ensuring that your data is always up to date.
Cloud Integration With cloud-based storage options, your data is accessible from anywhere. This ensures that even if your device fails, your files remain secure and retrievable.
Advanced Encryption Security is a priority for Computeroids. Using state-of-the-art encryption protocols, your data remains protected from unauthorized access.
Wide Compatibility Whether you're using Windows, macOS, or Linux, Computeroids Backup is compatible with various operating systems, making it versatile for different user needs.
The Role of Computeroids Driver
Drivers are essential software components that allow your operating system to communicate with hardware devices. Computeroids Driver simplifies the often tedious process of driver management. Here’s how:
Automatic Updates Say goodbye to outdated drivers. Computeroids Driver automatically detects and updates your drivers, ensuring optimal hardware performance.
Extensive Database With access to a vast library of drivers for various devices, from printers to graphics cards, Computeroids Driver minimizes compatibility issues.
Driver Backup and Restore Before updating drivers, Computeroids creates a backup, enabling you to revert to previous versions in case of compatibility issues.
User-Friendly Interface The interface is designed for ease of use, guiding even non-technical users through the process of installing and updating drivers.
Why Choose Computeroids?
Reliability Computeroids offers a consistent and reliable service, ensuring your data is safe and your devices run smoothly.
Time-Saving Automated backups and driver updates save hours of manual effort, allowing you to focus on your work.
Cost-Effective With affordable subscription plans, Computeroids provides high-value solutions without breaking the bank.
24/7 Support The team at Computeroids is available around the clock to assist with any issues or queries.
Best Practices for Using Computeroids Backup and Driver
Schedule Regular Backups: Ensure your data is backed up at least weekly to avoid data loss.
Check Driver Updates Periodically: While the service automates updates, reviewing the changes ensures compatibility with your specific setup.
Secure Your Account: Use strong passwords and enable two-factor authentication for your Computeroids account.
Test Restorations: Occasionally test data restorations and driver rollbacks to ensure the backups are functional.
Conclusion
Computeroids Backup and Driver services offer a one-stop solution for data protection and device management. By investing in these tools, you can ensure your digital life remains uninterrupted and secure. Whether you're an individual, a small business, or an enterprise, Computeroids has the tools you need to simplify your tech management.
0 notes
Text
Database Interactions Using Python

In today’s data-driven world, understanding how to interact with databases is a crucial skill for programmers and developers. Python, with its rich ecosystem of libraries, provides a seamless way to connect, query, and manage databases. At TCCI Computer Coaching Institute, we help students master this essential skill to build efficient and scalable applications.
This book discusses all the aspects of database interactions with Python, including core libraries, best practices, and real-world applications.
Why Learn Database Interaction in Python?
Databases form the heart of any application nowadays. It can hold information from user data to log files for transactions. In addition to these, Python presents very easy and efficient methods for interacting with various databases; either they are relational, such as MySQL, PostgreSQL, or SQLite, or NoSQL, like MongoDB.
Key to developing dynamic, data-driven applications is learning how to work with databases. At TCCI, we focus on hands-on training to assist you in connecting to a database, executing queries and retrieving data, performing CRUD operations, and using Python libraries to efficiently manage databases. Top Python Libraries for Database Interactions. To interact with databases using Python, you should get to know some of the top libraries used for the purpose. Let's see them below:
SQLite (sqlite3)
Best for: Small to medium database applications
Overview: sqlite3 is Python's built-in module which allows you to create and manage SQLite databases. Ideal for small to medium application or to understand how the database works.
Key Operations: Connecting, creating tables, inserting data, querying, and updating records.
MySQL Connector (mysql-connector-python)
Best for: Web applications, enterprise-grade systems
Overview: mysql-connector-python lets Python communicate with MySQL databases. This is an open-source library that makes the functions easily usable to handle MySQL database operations.
Key Operations: Connection, Query Execution, Transaction Handling, and Result Fetching.
SQLAlchemy
Best for: ORM (Object-Relational Mapping) in large applications
Overview: It is one of the most widely used libraries in Python to interact with relational databases. It supports multiple database engines like MySQL, PostgreSQL, SQLite, and others.
Key Operations: Querying databases with Python objects, database migrations, and schema management.
Psycopg2 (for PostgreSQL)
Best for: PostgreSQL-based applications
Overview: psycopg2 is the most used library to access PostgreSQL in Python. It is quite fast and reliable for working with complex queries and for database management.
Key Operations: Connect to PostgreSQL, execute SQL commands, and manage transactions.
MongoDB with PyMongo
Best for: NoSQL, document-based databases
Overview: PyMongo is the Python driver to access MongoDB, a NoSQL database. This is best suited for applications requiring flexible data structures or the need to scale horizontally.
Key Operations: Insert documents, update data, and perform aggregations.
Real-World Applications of Database Interactions Using Python
Web Development: The ability to interact with databases is a vital component in building web applications using frameworks such as Django and Flask. Databases will store user information, product information, and transaction records.
Data Analysis: The powerful libraries of Python enable you to pull data from databases for analysis, whether you want to generate reports, build machine learning models, or create visualizations.
Automation Scripts: Use Python for the automation of database backups, query execution, etc., to save time and prevent human error.
Becoming great and mastering Python database interactions means lots of experience for aspiring developers and data professionals. As part of TCCI Computer Coaching Institute, we aim to create a solid platform for learning Python database programming, enabling you to do everything else in the tech industry as well. Join us now.
Call now on +91 9825618292
Get information from https://tccicomputercoaching.wordpress.com/
#TCCI computer coaching institute#Best computer classes near me#Python programming training institute in Ahmedabad#Best computer training Bopal Ahmedabad#Best computer classes in Iskon crossroad Ahmedabad
0 notes
Text
How to Build an ETL Pipeline in Python from Scratch

In today’s data-driven world, organizations rely on efficient systems to process and analyze vast amounts of information. One of the most critical components of data engineering is the Extract Transform Load Python process, which involves extracting data from various sources, transforming it to fit operational or analytical needs, and loading it into a target system for further use. Python, known for its simplicity and versatility, has become a popular language for building ETL pipelines due to its rich ecosystem of libraries and tools.
Why Use Python for ETL?
Python is a preferred choice for ETL development because of its flexibility and the availability of numerous libraries tailored for data manipulation, extraction, and integration. Libraries like Pandas, SQLAlchemy, BeautifulSoup, and PyODBC simplify working with diverse data sources such as APIs, web pages, databases, and file systems. Additionally, Python frameworks like Airflow and Luigi help automate and schedule ETL workflows.
Understanding the ETL Workflow
An ETL pipeline consists of three core stages: extraction, transformation, and loading. The goal is to efficiently move raw data through these stages to make it ready for decision-making or operational use.
Extraction: This phase involves retrieving data from various sources like databases, flat files, APIs, or web pages. Data formats can vary widely, from structured SQL tables to semi-structured JSON or XML files, and unstructured text data.
Transformation: Raw data is rarely in a ready-to-use format. During this stage, it is cleaned, standardized, and processed. Tasks might include removing duplicates, handling missing values, converting formats, or applying business logic to derive new fields.
Loading: In this final phase, the transformed data is written to a destination, such as a database, data warehouse, or data lake. This stage ensures the data is accessible for applications or analytics tools.
Key Components of an ETL Pipeline in Python
Building an ETL pipeline in Python requires understanding its ecosystem and leveraging the right tools for each phase:
Data Extraction Tools:
Pandas: Ideal for reading data from CSV, Excel, and JSON files.
Requests: Used for fetching data from APIs.
BeautifulSoup or Scrapy: Useful for web scraping.
PyODBC or SQLAlchemy: Perfect for connecting to databases.
Data Transformation Tools:
Pandas: Powerful for data manipulation, such as filtering, aggregating, and reshaping data.
Numpy: Useful for numerical transformations.
Regular Expressions (re): Effective for cleaning textual data.
Data Loading Tools:
SQLAlchemy: Simplifies writing data to relational databases.
Boto3: Useful for loading data into AWS S3 buckets.
Pandas to_csv/to_sql: Saves transformed data to files or databases.
Best Practices for ETL Pipeline Development in Python
To ensure a robust and scalable ETL pipeline, adhere to the following best practices:
Plan Your Workflow: Understand the structure and requirements of your data sources and targets. Clearly define the transformations and business rules.
Modular Design: Break down the ETL pipeline into modular components for easy debugging and scalability. Each phase (extract, transform, load) should be a separate, reusable function or script.
Error Handling and Logging: Implement error-catching mechanisms to handle interruptions gracefully. Logging frameworks like Python’s logging module can help track and debug issues.
Test and Validate: Always validate extracted and transformed data before loading. Unit tests can help ensure the pipeline behaves as expected.
Optimize for Performance: Handle large datasets efficiently by using batch processing, multi-threading, or distributed computing frameworks like Dask or Apache Spark.
Applications of Python ETL Pipelines
Python ETL pipelines are widely used across industries for various purposes:
Business Intelligence: Aggregating data from multiple systems to generate reports and dashboards.
Data Warehousing: Moving data from operational databases to analytical data warehouses.
Machine Learning Pipelines: Preparing training data by extracting, cleaning, and transforming raw datasets.
Web Data Integration: Scraping web data and merging it with internal datasets for enhanced insights.
Conclusion
Building an ETL pipeline from scratch in Python may seem daunting at first, but with the right tools and approach, it can be both efficient and scalable. Python’s ecosystem empowers developers to handle the complexity of diverse data sources and create workflows that are tailored to specific business needs. By focusing on key concepts and following best practices, you can build an ETL pipeline that transforms raw data into actionable insights, driving better decision-making for your organization.
Whether you’re a seasoned data engineer or a novice programmer, Python offers the versatility and tools needed to master the art of Extract, Transform, Load (ETL).
0 notes