#Linux Privilege Escalation
Explore tagged Tumblr posts
Text
DogCat - Exploiting LFI and Docker Privilege Escalation -TryHackMe Walkthrough
In this walkthrough, we’ll explore the Dogcat room on TryHackMe, a box that features a Local File Inclusion (LFI) vulnerability and Docker privilege escalation. LFI allows us to read sensitive files from the system and eventually gain access to the server.There are a total of 4 flags in this machine which we need to find. Let’s Dive in! Step 1: Scanning the Target Start by scanning the target…
#Backup Script Exploit#Bash Reverse Shell#Crontab Exploit#Cybersecurity in Docker#Docker Container Security#Docker Exploit Tutorial#docker privilege escalation#Docker Security#Docker Vulnerabilities#Linux Privilege Escalation#Netcat Listener Setup#Reverse Shell Exploit#Shell Injection Attack#Tar Archive Exploit#Volume Mount Vulnerability
1 note
·
View note
Text
Linux Privilege Escalation - Part 1
Hi everyone! Welcome to Pentestguy. In this article, we will see what linux privilege escalation and different ways of achieving root user privilege escalation in the linux operating system. While playing capture the flag or performing pentesting of the network, escalating privileges is one of the important phases. Here we are focusing on Linux privilege escalations that happen to weak…

View On WordPress
#john-the-ripper#linux-privilege-escalation#mkpasswd#pentestguy#shadow-file-read-write-access#what-is-privilege-escalation
0 notes
Text
The rsync utility in Linux, *BSD, and Unix-like systems are vulnerable to multiple security issues, including arbitrary code execution, arbitrary file upload, information disclosure, and privilege escalation. Hence, you must patch the system ASAP.
74 notes
·
View notes
Text
CISA Warns of Active Exploitation of Linux Kernel Privilege Escalation Vulnerability
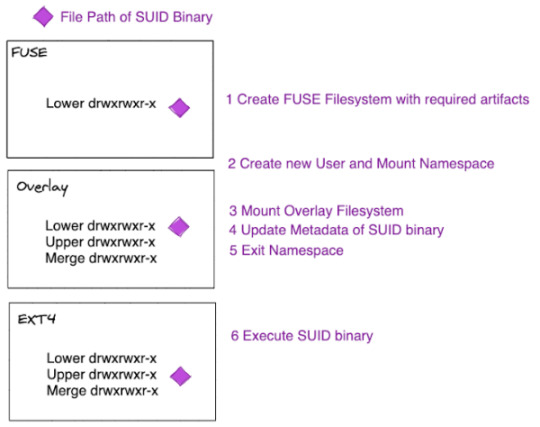
Source: https://thehackernews.com/2025/06/cisa-warns-of-active-exploitation-of.html
More info:
https://www.cisa.gov/news-events/alerts/2025/06/17/cisa-adds-one-known-exploited-vulnerability-catalog
https://securitylabs.datadoghq.com/articles/overlayfs-cve-2023-0386/
2 notes
·
View notes
Text
CVE-2025-6018 and CVE-2025-6019 Vulnerability Exploitation: Chaining Local Privilege Escalation Flaws Lets Attackers Gain Root Access on Most Linux Distributions
Unlock the Secrets of Ethical Hacking! Ready to dive into the world of offensive security? This course gives you the Black Hat hacker’s perspective, teaching you attack techniques to defend against malicious activity. Learn to hack Android and Windows systems, create undetectable malware and ransomware, and even master spoofing techniques. Start your first hack in just one hour! Enroll now and…
0 notes
Text
Fixes available for local privilege escalation vulnerability in libblockdev using udisks
Qualys discovered two vulnerabilities in various Linux distributions which allow local attackers to escalate privileges. The first vulnerability (CVE-2025-6018) was found in the PAM configuration. This CVE does not impact default Ubuntu installations because of how the pam_systemd.so and pam_env.so modules are invoked. The second vulnerability (CVE-2025-6019) affects both libblockdev and udisks2…
0 notes
Text
CISA Warns of Active Exploitation of Linux Kernel Privilege Escalation Vulnerability
http://i.securitythinkingcap.com/TLQKgX
0 notes
Text
0 notes
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
Top Red Hat Tools for Securing Linux Systems
Linux systems are known for their robustness and security. However, even the most secure systems require proper tools and practices to maintain their integrity. Red Hat offers a comprehensive suite of tools to secure Linux systems, making them ideal for enterprises. Below are some top Red Hat tools that help in fortifying Linux environments.
1. SELinux (Security-Enhanced Linux)
Overview:
SELinux is an integral security module in Red Hat Enterprise Linux (RHEL). It enforces mandatory access control policies that restrict users and applications from accessing specific resources unless explicitly permitted.
Key Features:
Fine-grained access controls.
Prevents privilege escalation.
Offers pre-configured and customizable policies.
Example:
To check the status of SELinux and enforce its policy:sestatussetenforce 1
2. Red Hat Identity Management (IdM)
Overview:
IdM centralizes authentication, authorization, and account management, offering secure identity solutions.
Key Features:
Kerberos-based authentication.
Centralized control for users and systems.
Integration with Active Directory.
Example:
To install and configure IdM:yum install ipa-serveripa-server-install
3. OpenSCAP (Security Content Automation Protocol)
Overview:
OpenSCAP helps automate compliance audits by scanning systems against security baselines such as CIS and STIG.
Key Features:
Compliance reporting.
Vulnerability detection.
Remediation guidance.
Example:
To scan the system with a profile:oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_cis /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
Conclusion:
Securing Linux systems is a continuous process that requires the right tools and practices. Red Hat’s suite of tools, including SELinux, IdM, and OpenSCAP, provide a robust foundation for maintaining system security. Implementing these tools effectively ensures compliance, minimizes risks, and enhances overall system reliability.
0 notes
Text
Podman for Beginners: Understanding Rootless Containers
In the fast-evolving world of containerization, Podman has emerged as a powerful, user-friendly, and secure alternative to Docker. One of its standout features is the support for rootless containers, which allows users to run containers without requiring elevated privileges. If you're new to Podman and curious about rootless containers, this guide is for you.
What is Podman?
Podman (Pod Manager) is an open-source container engine that enables users to create, manage, and run containers and pods. Unlike Docker, Podman operates without a central daemon, which enhances its security and flexibility.
What Are Rootless Containers?
Rootless containers allow users to run containers as non-root users. This significantly reduces security risks, as it minimizes the impact of potential vulnerabilities within containers. With rootless containers, even if a container is compromised, the damage is limited to the privileges of the user running it.
Benefits of Rootless Containers
Enhanced Security Rootless containers reduce the risk of privilege escalation, making them an ideal choice for running containers in development and production environments.
User-Specific Containers Each user can manage their container ecosystem independently, avoiding conflicts and ensuring isolation.
No Root Privileges Required Rootless containers eliminate the need for administrative access, making them safer for shared environments and CI/CD pipelines.
How to Get Started with Podman Rootless Containers
Step 1: Install Podman
Ensure you have Podman installed on your system. For most Linux distributions, you can install Podman using the package manager:
sudo apt install podman # For Debian-based systems sudo dnf install podman # For Fedora-based systems
Step 2: Verify Installation
Run the following command to check if Podman is installed correctly:
podman --version
Step 3: Create and Run a Rootless Container
Switch to a non-root user and run the following commands:
Pull an image:podman pull alpine
Run a container:podman run --rm -it alpine sh
This runs an Alpine Linux container in a rootless mode.
Step 4: Manage Containers
You can list running containers using:
podman ps
And stop a container using:
podman stop <container_id>
Limitations of Rootless Containers
While rootless containers are highly secure, there are some limitations:
Networking: Networking features may be restricted due to the lack of root privileges.
Performance: Certain operations may have slight performance overheads.
Compatibility: Not all container images or workloads are fully compatible with rootless containers.
When to Use Rootless Containers
Rootless containers are ideal for:
Development environments where security and isolation are essential.
CI/CD pipelines that don’t require root access.
Scenarios where multi-user isolation is necessary.
Conclusion
Podman’s rootless containers offer a seamless and secure way to work with containers, especially for users who value security and flexibility. By enabling rootless operations, Podman empowers developers to build and manage containers without compromising system integrity.
Ready to embrace rootless containers? Install Podman today and experience the future of containerization!
For more details click www.hawkstack.com
#Podman #RootlessContainers #Containerization #DevOps #ContainerSecurity
0 notes
Text
Using Linux's AppArmor to Segment and Secure Application Access
Introduction What is AppArmor and Why is it Important? AppArmor is a Mandatory Access Control (MAC) security framework for Linux that allows system administrators to restrict programs’ capabilities and enforce the principle of least privilege. It is an essential tool for securing Linux systems and preventing malicious activities such as privilege escalation, file and network access, and data…
0 notes
Text
Was It Really GPAC? (No!) Getting a CVE Removed from CISA KEV
On October 3, 2024, Aquasec published a report about newly discovered malware named “perfctl”, targeting Linux servers. In it they cite the malware taking advantage of misconfigurations, as well as attempting to “exploit the Polkit vulnerability (CVE-2021-4043) to escalate privileges.” Only problem is that CVE-2021-4043 isn’t “the Polkit vulnerability”, which in itself is problematic since…
0 notes
Text
Make-me-root 'Looney Tunables' security hole on Linux needs your attention

Source: https://www.theregister.com/2023/10/04/linux_looney_tunables_bug/
More info: https://blog.qualys.com/vulnerabilities-threat-research/2023/10/03/cve-2023-4911-looney-tunables-local-privilege-escalation-in-the-glibcs-ld-so#potential-impact-of-looney-tunables
2 notes
·
View notes
Link
0 notes
Text
The Role of Python and SQL in Ethical Hacking: A Solid Foundation for Success
Ethical hacking is a dynamic field that requires a diverse skill set and a constant thirst for knowledge. While Python and SQL are powerful tools in the arsenal of an ethical hacker, they are not the sole determinants of one’s proficiency.
We will explore the role of Python and SQL in ethical hacking and discuss the additional skills and knowledge needed to excel in this field.
Mastering ethical hacking is an exciting journey. Dedicate yourself to continuous learning, stay curious, and enjoy the adventure! If you’re ready to delve deeper, consider enrolling in an Ethical Hacking course in Chennai for certifications and job placement opportunities.
Python: A Versatile Ally Python, a versatile programming language, plays a significant role in ethical hacking. Its simplicity, readability, and extensive libraries make it a popular choice for scripting, automation, and developing security tools. With Python, ethical hackers can quickly create custom scripts to automate repetitive tasks, manipulate data, and interact with various network protocols.

SQL: Unveiling Database Vulnerabilities SQL (Structured Query Language) is the standard language for managing and querying databases. In ethical hacking, understanding SQL is crucial for assessing and exploiting database vulnerabilities. By leveraging SQL, ethical hackers can identify flaws in database configurations, execute unauthorized queries, and extract sensitive data.
SQL injection attacks, one of the most common web application vulnerabilities, involve exploiting improper SQL query handling to manipulate or extract data from databases. Ethical hackers proficient in SQL can effectively identify and exploit such vulnerabilities, thereby helping organizations strengthen their database security.
Beyond Python and SQL: Expanding Your Toolbox While Python and SQL are valuable assets, becoming a good ethical hacker requires a broader skill set.
Here are additional skills and knowledge areas that complement Python and SQL:
Networking: Understanding computer networks, protocols, and network security is crucial for conducting network-based attacks, identifying vulnerabilities, and analyzing network traffic.
Operating Systems: Familiarity with different operating systems (e.g., Windows, Linux, macOS) is essential for understanding system-level weaknesses, security configurations, and privilege escalation techniques.
Web Technologies: Knowledge of web technologies (e.g., HTML, CSS, JavaScript, web servers) is vital for assessing web application vulnerabilities, understanding client-server interactions, and conducting web-based attacks.

4. Security Tools: Proficiency in using a wide range of security tools and frameworks (e.g., Metasploit, Wireshark, Burp Suite) enhances the effectiveness of ethical hacking assessments and enables comprehensive vulnerability analysis.
ACTE has been implementing several technology motivated training programs that provide ethical hacking Certifications and Courses at Chennai.
5. Cryptography: Understanding cryptographic principles and techniques helps in analyzing cryptographic protocols, identifying weaknesses, and assessing the security of encrypted systems.
6. Reverse Engineering: Basic knowledge of reverse engineering techniques enables ethical hackers to analyze malware, understand exploit mechanisms, and assess software vulnerabilities.
7. Social Engineering: Familiarity with social engineering techniques and psychology allows ethical hackers to assess the human element of security and identify potential vulnerabilities in organizational processes.
While Python and SQL provide a solid foundation for ethical hacking, they are just the beginning. A good ethical hacker must continuously expand their knowledge and skills in various domains, such as networking, operating systems, web technologies, security tools, cryptography, reverse engineering, and social engineering.
By embracing a continuous learning mindset, participating in cybersecurity communities, and pursuing relevant certifications, aspiring ethical hackers can equip themselves with the comprehensive skill set necessary to excel in this ever-evolving field. Python and SQL serve as valuable tools in their arsenal, but the journey to becoming a proficient ethical hacker goes beyond these two languages.
0 notes