#docker privilege escalation
Explore tagged Tumblr posts
Text
DogCat - Exploiting LFI and Docker Privilege Escalation -TryHackMe Walkthrough
In this walkthrough, we’ll explore the Dogcat room on TryHackMe, a box that features a Local File Inclusion (LFI) vulnerability and Docker privilege escalation. LFI allows us to read sensitive files from the system and eventually gain access to the server.There are a total of 4 flags in this machine which we need to find. Let’s Dive in! Step 1: Scanning the Target Start by scanning the target…
#Backup Script Exploit#Bash Reverse Shell#Crontab Exploit#Cybersecurity in Docker#Docker Container Security#Docker Exploit Tutorial#docker privilege escalation#Docker Security#Docker Vulnerabilities#Linux Privilege Escalation#Netcat Listener Setup#Reverse Shell Exploit#Shell Injection Attack#Tar Archive Exploit#Volume Mount Vulnerability
1 note
·
View note
Text
Is cPanel on Its Deathbed? A Tale of Technology, Profits, and a Slow-Moving Train Wreck
Ah, cPanel. The go-to control panel for many web hosting services since the dawn of, well, web hosting. Once the epitome of innovation, it’s now akin to a grizzled war veteran, limping along with a cane and wearing an “I Survived Y2K” t-shirt. So what went wrong? Let’s dive into this slow-moving technological telenovela, rife with corporate greed, security loopholes, and a legacy that may be hanging by a thread.
Chapter 1: A Brief, Glorious History (Or How cPanel Shot to Stardom)
Once upon a time, cPanel was the bee’s knees. Launched in 1996, this software was, for a while, the pinnacle of web management systems. It promised simplicity, reliability, and functionality. Oh, the golden years!
Chapter 2: The Tech Stack Tortoise
In the fast-paced world of technology, being stagnant is synonymous with being extinct. While newer tech stacks are integrating AI, machine learning, and all sorts of jazzy things, cPanel seems to be stuck in a time warp. Why? Because the tech stack is more outdated than a pair of bell-bottom trousers. No Docker, no Kubernetes, and don’t even get me started on the lack of robust API support.
Chapter 3: “The Corpulent Corporate”
In 2018, Oakley Capital, a private equity firm, acquired cPanel. For many, this was the beginning of the end. Pricing structures were jumbled, turning into a monetisation extravaganza. It’s like turning your grandma’s humble pie shop into a mass production line for rubbery, soulless pies. They’ve squeezed every ounce of profit from it, often at the expense of the end-users and smaller hosting companies.
Chapter 4: Security—or the Lack Thereof
Ah, the elephant in the room. cPanel has had its fair share of vulnerabilities. Whether it’s SQL injection flaws, privilege escalation, or simple, plain-text passwords (yes, you heard right), cPanel often appears in the headlines for all the wrong reasons. It’s like that dodgy uncle at family reunions who always manages to spill wine on the carpet; you know he’s going to mess up, yet somehow he’s always invited.
Chapter 5: The (Dis)loyal Subjects—The Hosting Companies
Remember those hosting companies that once swore by cPanel? Well, let’s just say some of them have been seen flirting with competitors at the bar. Newer, shinier control panels are coming to market, offering modern tech stacks and, gasp, lower prices! It’s like watching cPanel’s loyal subjects slowly turn their backs, one by one.
Chapter 6: The Alternatives—Not Just a Rebellion, but a Revolution
Plesk, Webmin, DirectAdmin, oh my! New players are rising, offering updated tech stacks, more customizable APIs, and—wait for it—better security protocols. They’re the Han Solos to cPanel’s Jabba the Hutt: faster, sleeker, and without the constant drooling.
Conclusion: The Twilight Years or a Second Wind?
The debate rages on. Is cPanel merely an ageing actor waiting for its swan song, or can it adapt and evolve, perhaps surprising us all? Either way, the story of cPanel serves as a cautionary tale: adapt or die. And for heaven’s sake, update your tech stack before it becomes a relic in a technology museum, right between floppy disks and dial-up modems.
This outline only scratches the surface, but it’s a start. If cPanel wants to avoid becoming the Betamax of web management systems, it better start evolving—stat. Cheers!
#hosting#wordpress#cpanel#webdesign#servers#websites#webdeveloper#technology#tech#website#developer#digitalagency#uk#ukdeals#ukbusiness#smallbussinessowner
14 notes
·
View notes
Text
Podman for Beginners: Understanding Rootless Containers
In the fast-evolving world of containerization, Podman has emerged as a powerful, user-friendly, and secure alternative to Docker. One of its standout features is the support for rootless containers, which allows users to run containers without requiring elevated privileges. If you're new to Podman and curious about rootless containers, this guide is for you.
What is Podman?
Podman (Pod Manager) is an open-source container engine that enables users to create, manage, and run containers and pods. Unlike Docker, Podman operates without a central daemon, which enhances its security and flexibility.
What Are Rootless Containers?
Rootless containers allow users to run containers as non-root users. This significantly reduces security risks, as it minimizes the impact of potential vulnerabilities within containers. With rootless containers, even if a container is compromised, the damage is limited to the privileges of the user running it.
Benefits of Rootless Containers
Enhanced Security Rootless containers reduce the risk of privilege escalation, making them an ideal choice for running containers in development and production environments.
User-Specific Containers Each user can manage their container ecosystem independently, avoiding conflicts and ensuring isolation.
No Root Privileges Required Rootless containers eliminate the need for administrative access, making them safer for shared environments and CI/CD pipelines.
How to Get Started with Podman Rootless Containers
Step 1: Install Podman
Ensure you have Podman installed on your system. For most Linux distributions, you can install Podman using the package manager:
sudo apt install podman # For Debian-based systems sudo dnf install podman # For Fedora-based systems
Step 2: Verify Installation
Run the following command to check if Podman is installed correctly:
podman --version
Step 3: Create and Run a Rootless Container
Switch to a non-root user and run the following commands:
Pull an image:podman pull alpine
Run a container:podman run --rm -it alpine sh
This runs an Alpine Linux container in a rootless mode.
Step 4: Manage Containers
You can list running containers using:
podman ps
And stop a container using:
podman stop <container_id>
Limitations of Rootless Containers
While rootless containers are highly secure, there are some limitations:
Networking: Networking features may be restricted due to the lack of root privileges.
Performance: Certain operations may have slight performance overheads.
Compatibility: Not all container images or workloads are fully compatible with rootless containers.
When to Use Rootless Containers
Rootless containers are ideal for:
Development environments where security and isolation are essential.
CI/CD pipelines that don’t require root access.
Scenarios where multi-user isolation is necessary.
Conclusion
Podman’s rootless containers offer a seamless and secure way to work with containers, especially for users who value security and flexibility. By enabling rootless operations, Podman empowers developers to build and manage containers without compromising system integrity.
Ready to embrace rootless containers? Install Podman today and experience the future of containerization!
For more details click www.hawkstack.com
#Podman #RootlessContainers #Containerization #DevOps #ContainerSecurity
0 notes
Text
"Container Security Market: Poised for Explosive Growth with Enhanced Protection Trends through 2025"
Container Security Market : Containerization has revolutionized the way organizations deploy and manage applications, offering agility, scalability, and efficiency. However, this rapid adoption has introduced new vulnerabilities, making container security a top priority in modern DevSecOps strategies. Protecting containers isn’t just about securing the application but the entire lifecycle — images, registries, orchestration platforms, and runtime environments. Cyberattacks targeting containers, such as malware injection or privilege escalation, can compromise critical data and services. Implementing robust solutions, like image scanning, runtime protection, and role-based access controls, is essential to safeguard your containerized workloads from emerging threats.
To Request Sample Report : https://www.globalinsightservices.com/request-sample/?id=GIS20462 &utm_source=SnehaPatil&utm_medium=Article
With the rise of Kubernetes, Docker, and hybrid cloud environments, organizations must adopt a proactive approach to container security. This involves integrating security into every stage of the CI/CD pipeline, automating vulnerability detection, and ensuring compliance with industry standards. Tools like Kubernetes-native security platforms and runtime threat analysis are becoming indispensable. As businesses scale their operations, prioritizing container security isn’t just a defensive measure — it’s a competitive advantage that builds trust, resilience, and innovation in the digital era.
#ContainerSecurity #CloudSecurity #DevSecOps #CybersecurityTrends #KubernetesSecurity #DockerSafety #CloudNative #AppSecurity #SecureContainers #TechInnovation #DevOpsSecurity #SecurityFirst #FutureOfCybersecurity #CloudProtection #ITSecurity
0 notes
Text
Catch
So over the last few weeks I've been working on Catch. With work and the festive period I haven't had a lot of time; I finally got the opportunity to finish it last night. :)
It has a medium rating but I wouldn't say it's due to the initial foothold and privilege escalation being difficult- it's more due to there being a couple of rabbit holes (all of which I fell into for a period!)

Enumeration
As always, a port scan kicks off the process. Unfortunately I can't show the output of the port scan as during the time I switched laptops and I'm too lazy to power my old one on. xD However, the results were roughly as follows:
Port 80: HTTP (Catch Global Systems main page)
Port 3000: Gitea(?)
Port 5000: Lets Chat(?)
Port 8000: Cachet status page system
Port 80 was the first location I checked. You're greeted with what appears to be Catch's main application:
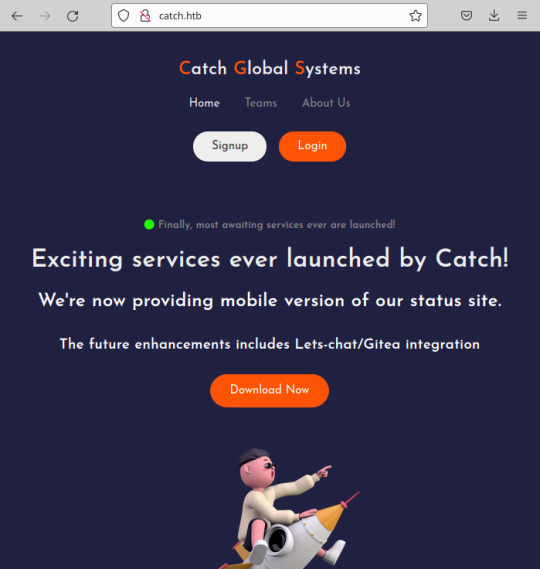
The signup/login functionality isn't present; I did notice the ability to download a file. The file that downloads is an apk.
For those that are unfamiliar with mobile applications, apk is one of the file formats for an Android mobile application which uses XML and Java. Having a little experience with mobile applications, my first thought was to decompile the apk and check for any hidden hardcoded secrets, usually stored in strings.xml.
To decompile the apk, I used apktool.
$ apktool d catchv1.0.apk
This decompiles the apk to near it's original form and places the resulting files in ./catchv1.0/. From here, I viewed ./res/values/strings.xml and found 3 potentially usable tokens for other applications:
$ grep token catchv1.0/res/values/strings.xml <string name="gitea_token">b87bfb6345ae72ed5ecdcee05bcb34c83806fbd0</string> <string name="lets_chat_token">NjFiODZhZWFkOTg0ZTI0NTEwMzZlYjE2OmQ1ODg0NjhmZjhiYWU0NDYzNzlhNTdmYTJiNGU2M2EyMzY4MjI0MzM2YjU5NDljNQ==</string> <string name="slack_token">xoxp-23984754863-2348975623103</string>
Foothold
With these in hand, I started with Lets Chat at random. Lets Chat is an open-source chat application utilizing a REST api. With it being open-source, it didn't take long at all to find how to use the discovered token:
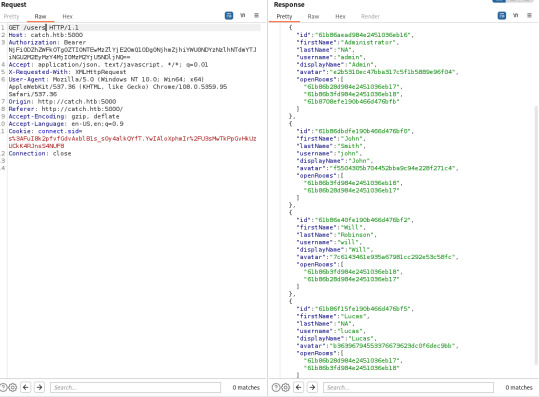

As you can see, a password for John is viewable in one of the chat rooms. This grants you access to another one of their applications called Cachet- open-source yet again.
Cachet is the last stop before system access; admittedly this is where I fell rabbit hole 1 as I did spend some time trying to use the gitea_token, more out of curiosity than anything. After spending some time on this, however, I gave up and focused on Cachet.
As it turns out, the version of Cachet in use had two pubicly known vulnerabilities related to interaction with the application's dotenv file. One allowed you to leak values set in dotenv while the other allowed you to add new values to dotenv which could be used to achieve remote command execution. This is done by hosting a redis server, altering the dotenv file to make the application use your hosted redis server as a session driver and finally changing the value of the session key after the initial connection to a payload generated by phpggc. Better detail off this is given here.
I did spend some time playing around with the RCE vulnerability here, more out of interest as I haven't had any experience with Redis prior to this and it took me a while to get RCE working as the video doesn't explicitly show the process step-by-step.
Originally, I was getting the token from the source code in the application, adding this as a key with the phpggc payload as the value and then altering the dotenv file to connect to my Redis Server. As the RCE occurs when the client connects the second time and reads the value from the original session token, this didn't work.
I did eventually get this working, uploaded a PHP web shell and upgraded this to a reverse shell; this ultimately proved to be a waste of time as you end up in a Docker instance with no ability to break out of it!

With a heavy heart, I turned to the second vulnerability and leaked the database password from the dotenv file. This grants us access to the server through SSH as WIll.
Privilege Escalation
Privilege escalation was actually quite easy! Some simple enumeration reveals the presence of world-writeable directory /opt/mdm/apk_bin. In /opt/mdm, there is a Bash file verify.sh.
verify.sh is used to verify the legitimacy of apks uploaded to apk_bin and is executed as part of a cronjob which is executed as root. While references to verify.sh cannot be directly found, there is reference to 'check.sh' in the root directory in running processes (netstat -ano.)
The interesting lines of the script are here:
app_check() { APP_NAME=$(grep -oPm1 "(?<=string name=\"app_name\">)[^<]+" "$1/res/values/strings.xml") echo $APP_NAME ...
The function app_check is taking the app_name from strings.xml and echoing it back with no form of mitigation against command injection. For example, wrapping the variable name with ${} would have prevented this vulnerability being exploitable as this would have specified that only variable expansion was expected- the app name would have been echoed back as a string and not interpreted as a literal Bash command.
I tested this first by simply making the app name 'Catch; touch /opt/mdm/heuheu' and uploading it using python -m SimpleHTTPServer on my end and curl on Catch's end which achieved the expected outcome.
I did this with APK Editor Studio after encountering some errors trying do manually decompile and then recompile with apktool. Note that you also need to create a key for signing the APK as verify.sh uses jarsigner to verify this.
will@catch:/opt/mdm/apk_bin$ ls -al .. total 16 drwxr-x--x+ 3 root root 4096 Jan 6 21:55 . drwxr-xr-x 4 root root 4096 Dec 16 2021 .. drwxrwx--x+ 2 root root 4096 Jan 6 22:03 apk_bin -rw-r--r-- 1 root root 0 Jan 6 21:55 heuheu -rwxr-x--x+ 1 root root 1894 Mar 3 2022 verify.sh
From here, I went old school and just made /etc/passwd fully accessible by everyone before changing root's password to 'mwaha'
Generating the password:
$ openssl passwd mwaha KW56XEY7wxZuU
Where the password is added in /etc/passwd:
root:KW56XEY7wxZuU:...
There you go. ^-^
#hackthebox#hacking#android apk#apktool#command injection#redis server#dotenv#cachet#lets chat#gitea#cronjob#web shell#reverse shell#ssh#docker#open source
20 notes
·
View notes
Photo

Don’t run Docker containers with docker run --net=host Don’t run Kubernetes Pods with .spec.hostNetwork: true CVE-2020–15257: A compromise host network container running as UID 0 can escape the container, escalate privileges, and compromise the host. https://t.co/b5XGmqYFFj (via Twitter http://twitter.com/TheHackersNews/status/1334516790857265154)
1 note
·
View note
Text
[Media] deepce
deepce Docker Enumeration, Escalation of Privileges and Container Escapes (DEEPCE) https://github.com/stealthcopter/deepce #infosec #pentesting

0 notes
Text
What is Docker Compose: Example, Benefits and Basic Commands - ACEIT
What is Docker Compose?
Docker
An easy-to-use Linux container technology
Docker image format
It helps in application packaging and delivery
Top Engineering Colleges in Jaipur Rajasthan says Docker is a tool that can package an application and its dependencies in a virtual container that can run on any Linux server. This helps enable flexibility and portability on where the application can run, whether on-premises, public cloud, private cloud, bare metal, etc also It composes works in all environments: production, staging, development, testing, as well as CI workflows and with Compose, you use a YAML file to configure your application’s services.
Docker Vs Virtualization
Positive expects of Docker,
Lighter than Virtual machines.
docker images are very small in size
Deploying and scaling is relatively easy
Containers have less startup time
Less secure
Technologies Behind Docker
Control groups:
There are some keys but control Groups are another key component of Linux Containers with Cgroup we can implement resource accounting and limit and also ensure that each container gets its fair share of memory, CPand U, and disk I/O, and thanks to Group up, we can make sure that at single container cannot bring the system down by exhausting resources.
Union file systems:
It is a read-only part and a written part and merges those Docker images made up of layers.
Technologies behind docker
Namespaces also help to create isolated workspace for each process and When you run a container, Docker creates a set of namespaces for that container
SELinux:- It provides secure separation of containers by applying SELinux policy and labels.
Technologies Behind Docker
Capabilities:
One of the most important capabilities is docker drops all capabilities except those needed also "root" within a container have fewer privileges than the real "root" and the best practice for users would be to remove all capabilities except those explicitly required for their processes, so even if an intruder manages to escalate to root within a container.
Components
Docker Images
Docker containers
Docker Hub
Docker Registry
Docker daemon
Docker client
Dcokerfile
It is a text document that contains all the commands a user could call on the command line to assemble an image also it builds can build images using Dockerfile.
Let's talk about real-life applications first!
One application consists of multiple containers, and One container is dependent on another also Mutual dependence startup order, so the Process involves building containers and then deploying them, also Long docker run commands and Complexity are proportional to the number of containers involved.
Docker Compose
Private Colleges of Engineering in Jaipur Rajasthan has a tool for defining and running multi-container Docker applications, It is a YML file and composes contains information about how to build the containers and deploy containers, also Integrated with Docker Swarm so Competes with Kubernetes
Conclusion:
Best Engineering Colleges in Jaipur Rajasthan says The big advantage of using Compose is you can define your application stack in a file, keep it at the root of your project repo (it’s now version controlled), and easily enable someone else to contribute to your project, also Someone would only need to clone your repo and start the compose app and In fact, you might see quite a few projects on GitHub/GitLab doing exactly this now, and Compose works in all environments: production, staging, development, testing, as well as CI workflows also it has commands for managing the whole life cycle of your application with security also according to client requirement they do the needful.
Start, stop and rebuild services
View the status of running services
Stream the log output of running services
Run a one-off command on a service
0 notes
Text
(Download PDF/Epub) Kali Linux Penetration Testing Bible - Gus Khawaja
Download Or Read PDF Kali Linux Penetration Testing Bible - Gus Khawaja Free Full Pages Online With Audiobook.

[*] Download PDF Here => Kali Linux Penetration Testing Bible
[*] Read PDF Here => Kali Linux Penetration Testing Bible
Your ultimate guide to pentesting with Kali LinuxKali is a popular and powerful Linux distribution used by cybersecurity professionals around the world. Penetration testers must master Kali's varied library of tools to be effective at their work. The Kali Linux Penetration Testing Bible is the hands-on and methodology guide for pentesting with Kali.You'll discover everything you need to know about the tools and techniques hackers use to gain access to systems like yours so you can erect reliable defenses for your virtual assets. Whether you're new to the field or an established pentester, you'll find what you need in this comprehensive guide.Build a modern dockerized environment Discover the fundamentals of the bash language in Linux Use a variety of effective techniques to find vulnerabilities (OSINT, Network Scan, and more) Analyze your findings and identify false positives and uncover advanced subjects, like buffer overflow, lateral movement, and privilege escalation Apply
0 notes
Text
Pwned Vulnhub Walkthrough
Pwned vulnhub challenge is an easy boot2root machine. One of the key take away from this machine is how you can escalate your privileges using Dockers. This blog post is about how I exploited this machine and what are the different tools I used to make that happen. Below are the requirements: You can get the virtual machine from here : https://www.vulnhub.com/entry/pwned-1,507/ I used Kali as a…

View On WordPress
0 notes
Text
Security researchers find Azure Functions vulnerability
Security researchers find Azure Functions vulnerability
Source: Security Magazine Security researchers find Azure Functions vulnerability Intezer researchers discovered a new vulnerability in Azure Functions, which would allow an attacker to escalate privileges and escape the Azure Functions Docker container to the Docker host.
View On WordPress
0 notes
Link
via Twitter https://twitter.com/PatrickCMiller
0 notes
Photo

Docker Privilege Escalation #privilegeescalation #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Text
Tesla Bug Bounty & Windows Bugs
Researcher Finds Tesla XSS Vulnerability (article)
This is actually pretty relevant to some of the stuff we’ve been covering recently... basically some guy named Sam decided to test the infotainment system in the Tesla Model 3 for XSS vulnerabilities - he used a piece of software called XSS hunter which discovered a problem in the “Name Your Vehicle” field. He didn’t notice the vulnerability until he had to submit an appointment to get his vehicle fixed a couple months later through the Tesla mobile app.
When he checked the XSS Hunter web software he noticed it had been triggered and sent information about his vehicle including ‘the vehicle’s VIN, speed, temperature, version number, whether it was locked or not, tire pressure, and alerts’. It also included ‘firmware details, geodefense locations, CAN viewers, and configurations’.
It was actually quite possible that if the link had been modified (in terms of the ID), he would have been able to grab details about other cars. All you would need to do is submit multiple support requests using the XSS injections to obtain the data; after a while you might be able to work out a way to access more data or do it more directly even. In fact, the researcher was payed $10,000 for the vulnerability - bug bounties are cool guise!
Windows Privilege Escalation Vulnerabilities (article)
Just thought I would mention this article as it goes to show how many bugs are constantly being found in operating systems, especially Windows. There were a number of vulnerabilities including:
Splwow64.exe (CVE-2019-0880) - component in window designed to allow 32-bit applications to use a 64-bit printer spooler service
Vulnerability could be exploited for privilege escalation from ‘low-integrity to medium integrity’; i.e. it could be chained with another to escalate even further
Win32k component (CVE-2019-1132) - related to how this part handles objects in memory
Attacker would need to log onto the system then ‘run a specially crafted application’ which would allow them to execute arbitrary code in kernel mode
Windows privilege escalation
SQL server remote code execution
Azure automation privilege escalation
Remote Desktop Services (RDS) remote code execution
SymCrypt DoS
Docker privilege escalation
The first two were zero-day vulnerabilities however the rest have been publicly known for a while. The fact that Microsoft has taken all the way till July to patch these is ridiculous - for example, the SymCrypt flaw they had known for 90 days to June 11 when Google Project Zero notified them. I understand in a way that they need to obviously make sure they aren’t introducing even bigger security vulnerabilities than they already have, but this is still too long.
0 notes
Text
Docker for Pentest - Image With Tools To Create A Pentest Environment
Docker for Pentest - Image With The More Used Tools To Create A Pentest Environment Easily And Quickly #create #Docker
[sc name=”ad_1″]
Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly.
Features
OS, networking, developing and pentesting tools installed.
Connection to HTB (Hack the Box) vpn to access HTB machines.
Popular wordlists installed: SecLists, dirb, dirbuster, fuzzdb, wfuzz and rockyou.
Proxy service to send traffic from any browsers and burp suite
View On WordPress
#create#Docker#Docker for Pentest#Easily#environment#image#John the Ripper#linux#pentest#Privilege Escalation#Quickly#Tools#Wfuzz#Wordlists
0 notes