#Load Balancing in vSphere
Explore tagged Tumblr posts
Text
vSphere cluster Shared Storage Configuration with StarWind SAN and NAS
vSphere cluster Shared Storage Configuration with StarWind SAN @vexpert #homelab #vmwarecommunities #vSphereClusterConfiguration #StarWindSAN&NAS #VMwarevSphereClient #SharedStorageSystem #HighAvailabilityvSphere #ESXiHostManagement #vSphereHA&DRS
A vSphere Cluster is a fundamental building block in a VMware environment allowing organizations to configure powerful virtualized environments for running virtual machines and containers. A properly configured vSphere cluster, incorporating multiple ESXi hosts, ensures service continuity and performance for users, providing them access to many features and resources. Shared storage is a vital…

View On WordPress
#Configuring Shared Storage#ESXi Host Management#High Availability vSphere#Load Balancing in vSphere#Shared Storage System#StarWind SAN & NAS#VMware Cluster Resources#VMware vSphere Client#vSphere Cluster Configuration#vSphere HA & DRS
0 notes
Text
VMware Training – The Right Choice to Harness Your IT Potential
Unless you stay updated with the latest trends and technologies, it is impossible to take your career ahead in the IT industry. Upskilling with certification courses is a smart way to stay ahead of your competitors and be better at what you do. Studies show that certified IT professionals are 60% more efficient than their non-certified counterparts.
If you are aiming to advance your career and make a mark in virtualization and cloud computing, VMware training could be your ticket to success.
What is VMware?
VMware is a leading virtualization technology, enabling businesses to optimize their IT infrastructure. With VMware, multiple virtual machines can operate on a single physical server, maximizing efficiency and resource utilization. Its comprehensive suite of tools supports everything from data center management to application modernization, making VMware skills indispensable in the modern IT environment.
Why VMware Training Matters
Career Advancement
Employers prioritize candidates with specialized skills, and VMware training can set you apart. Certified professionals often command higher salaries and enjoy better job opportunities.
Increased Productivity
Upskilling enhances not only individual performance but also overall team productivity. Trained professionals can deploy and manage VMware solutions more efficiently, reducing downtime and streamlining operations.
Certification Value
VMware training certifications, such as VMware Certified Professional (VCP) and VMware Certified Advanced Professional (VCAP), are globally recognized. They validate your expertise and demonstrate your commitment to staying current in a rapidly evolving field.
Types of VMware Training Courses
Leading training providers offer a variety of training formats and courses to cater to different learning needs and career paths.
Popular Courses
VMware vSphere: Master the basics of virtualization and server management.
VMware Cloud Director: Advanced Networking with NSX-T Data Center: The course covers the design, integration, configuration, and management of VMware Cloud Director™ 10.x with VMware NSX® Advanced Load Balancer.
VMware Cloud Director: Install Configure Manage: The course covers key features and functionality of VMware Cloud Director, including workload provisioning, organization, and network configuration for system and organization administrators.
VMware Aria Operations for Logs: Install, Configure, Manage: This course provides hands-on training in deploying, configuring, and managing VMware Aria Operations™, covering architecture, use cases, and benefits to effectively monitor your environment.
Training Details
Authorized VMware training providers deliver excellent learning experiences. Their accredited instructors use official courseware to ensure quality and relevance. With flexible scheduling options, including self-paced and live virtual training, you can easily integrate learning into your routine. Whether you’re a beginner or an experienced professional, these providers offer tailored training solutions to meet your needs.
Real-World Applications of VMware Skills
VMware training is highly relevant for roles like system administrators, cloud architects, and IT managers. Certified professionals are often seen as industry leaders equipped to handle complex virtualization challenges. Be it optimizing a data center or designing a hybrid cloud solution, VMware expertise can transform your career.
Conclusion
VMware training is more than just a course—it is a gateway to professional growth and innovation. Equip yourself with cutting-edge skills to thrive in the evolving tech industry. Ready to take the next step? Visit Ascendient Learning to explore VMware certification programs and accelerate your IT career today.
1 note
·
View note
Quote
もう手に入らないものは何ですか? リスト は 次のとおりです。 VMware vSphere エンタープライズ プラス VMware vSphere+ VMware vSphere Standard (サブスクリプションを除く) VMware vSphere ROBO VMware vSphere スケールアウト VMware vSphere デスクトップ VMware vSphere アクセラレーション キット VMware vSphere Essentials キット VMWare vSphere Essentials Plus Kit (新規サブスクリプション製品を除く) VMware vSphere スターター/ファウンデーション VMware vSphere と運用管理 VMware vSphere ベーシック VMware vSphere アドバンスト VMware vSphere ストレージ アプライアンス VMware vSphere ハイパーバイザー VMware Cloud Foundation (新しい VCF サブスクリプション サービスを除く) VDI 向け VMware Cloud Foundation VMware Cloud Foundation for ROBO VMware SDDC マネージャー VMware vCenter Standard VMware vCenter Foundation VMware vSAN VMware vSAN ROBO VMware vSAN デスクトップ VMware HCI キット VMware サイト リカバリ マネージャー VMware Cloud エディション/クラウド パック VMware vCloud スイート VMware Aria スイート (旧 vRealize Suite) VMware Aria Universal Suite (旧称 vRealize Cloud Universal) vMware Aria Suite の期間 VMware Aria Operations for Networks (旧称 vRealize Network Insight) VMWare Aria Operations for Networks Universal (旧称 vRealize Network Insight Universal) VMware vRealize Network Insight ROBO VMWare Aria Operations for Logs (旧称 vRealize Log Insight) VMware vRealize Operations 8 アプリケーション監視アドオン VMware Aria の操作 VMware Aria オートメーション VMware Aria Automation for Secure Hosts アドオン (旧称 SaltStack SecOps) VMware vRealize Automation SaltStack SecOps アドオン VMware Aria Operations for Integrations (旧称 vRealize True Visibility Suite) VMware クラウド ディレクター クラウドディレクターサービス VMware NSX VMware NSX デスクトップ用 VMware NSX ロボ VMware NSX 分散ファイアウォール VMware NSX ゲートウェイ ファイアウォール VMware NSX の脅威から分散ファイアウォールへ VMware NSX 脅威防御からゲートウェイ ファイアウォールまで VMware NSX Advanced Threat Prevention から分散ファイアウォールへ VMware NSX Advanced Threat Prevention からゲートウェイ ファイアウォールまで VMware NSX Advanced Load Balancer (サブスクリプション、SaaS を除く) Antrea を使用した VMware Container Networking Enterprise VMware HCX VMware HCX+
VMware、インフラストラクチャの「地殻変動」の中で 56 製品を廃止
1 note
·
View note
Text
Middle DevOps/SRE Engineer
Райффайзен Банк Аваль Required skills 3+ years of experience on DevOps role with production-grade systems; Proficient in Linux administration and configuration; Network understanding: TCP/IP, DNS, Load-balancers, PKI TLS, network security, etc.; Deep knowledge of public cloud platforms AWS is preferable; Good knowledge of private clouds vSphere is preferable; Good Linux system internals and…

View On WordPress
1 note
·
View note
Text
Virtualmachine sphere

#Virtualmachine sphere how to#
#Virtualmachine sphere password#
#Virtualmachine sphere windows#
You add a credential to the DPM server so you can pair it up with credential on the VMware server. See the following sections for detailed information on adding, updating, or deleting credentials. Using the Manage Credentials dialog, you can add, update, or delete credentials. In the tool ribbon, click Manage VMware Credentials. In the list of assets to manage, click Production Servers. In the DPM Administrator Console, click Management. Open the Manage VMware Credentials feature
A credential can be deleted only if it is not being used to authenticate a VMware server.
#Virtualmachine sphere password#
Once credential details such as: Description, User name, and Password are updated, DPM uses these credentials to communicate with all VMware servers.One credential can be used to authenticate multiple VMware servers.Note the following details about credentials: However, DPM has a Manage VMware Credentials feature to securely store and manage credentials. As it can be necessary to change credentials, and a data center can have multiple vCenter servers requiring unique credentials, tracking these credentials can be a problem. Each time DPM communicates with a VMware server, DPM must be authenticated. Instead, DPM uses a user name and password credential to authenticate its remote communication with the VMware server. Credential managementĭPM does not use an agent to communicate with a VMware server. To manage a VMware server, DPM needs valid credentials to access VMware servers. You don't need to add ESXi servers to DPM. If you use both vCenter Server and ESXi server, configure only the vCenter Server to work with DPM. To establish communication between DPM and the VMware server, configure the VMware credentials and establish a secure connection between DPM and the VMware vCenter Server or VMware vSphere Hypervisor (ESXi) server.
#Virtualmachine sphere how to#
The following information details how to configure VMware for DPM protection.
TCP 443 and TCP 902 between MABS and ESXi host.
Ensure the following network ports are open:.
DPM cannot protect VMware VMs with existing snapshots.
DPM cannot detect or protect VMware vApps.
DPM cannot protect VMware VMs with pass-through disks and physical raw device mappings (pRDM).
Once DPM completes the first backup, then you can back up user snapshots.
You cannot back up user snapshots before the first DPM backup.
DPM cannot protect VMware VMs to a secondary DPM server.
If you use vCenter to manage ESXi servers in your environment, add vCenter (and not ESXi) to the DPM protection group.
#Virtualmachine sphere windows#
If you are protecting vCenter Server (running on Windows) using FQDN as VMware Server, you cannot protect the vCenter Server as Windows Server.If you want to use FQDN, you should stop the protection as Windows Server, remove the protection agent, and then add as VMware Server using FQDN.You can use static IP address of vCenter Server as a workaround.If you have been using DPM to protect vCenter server (running on Windows) as Windows Server, you cannot protect that as VMware server using FQDN of the server.DPM can recover files/folders from a Windows VM without recovering the entire VM, which helps recover necessary files faster.īefore you start backing up a VMware virtual machine, review the following list of limitations and prerequisites.DPM protects VMs migrated for load balancing: As VMs are migrated for load balancing, DPM automatically detects and continues VM protection.DPM protects VMs stored on a local disk, network file system (NFS), or cluster storage.As you organize your VMs in recursive folders, DPM automatically detects and protects the new VMs deployed in the recursive folders. DPM detects new VMs on a daily basis and protects them automatically. When protecting folders, DPM not only protects the VMs in that folder, but also protects VMs added later. DPM detects these folders and lets you protect VMs at the folder level and includes all subfolders. Folder level auto protection: vCenter lets you organize your VMs in VM folders.DPM also detects VMs managed by vCenter, allowing you to protect large deployments. As your deployment size grows, use vCenter to manage your VMware environment. Detect and protect VMs managed by vCenter: DPM detects and protects VMs deployed on a VMware server (vCenter or ESXi server).DPM's backup and recovery workflow helps you manage long-term retention and offsite backup. Cloud Integrated Backup: DPM protects workloads to disk, tape and cloud.Instead, just provide the IP address or fully qualified domain name (FQDN), and login credentials used to authenticate the VMware server with DPM. Agentless backup: DPM does not require an agent to be installed on the vCenter or ESXi server, to back up the virtual machine.Backup to tape is supported from DPM 2019.

0 notes
Text
Subnet mask table 4 bits

#SUBNET MASK TABLE 4 BITS HOW TO#
#SUBNET MASK TABLE 4 BITS UPGRADE#
#SUBNET MASK TABLE 4 BITS SOFTWARE#
#SUBNET MASK TABLE 4 BITS PLUS#
IP addresses are either configured by a DHCP server or manually configured (static IP addresses). Get familar with related technical terms.Support Contact support to resolve issues.Professional Services Engage with professional services for migration and customization.Knowledge Base Get the best documentation on our product.LBTV Hits all major topics of modern load balancing.Virtual Summit Attend a quarterly summit to learn more.Webinars Join our subject matter experts to explore a use case.Content Library Find everything related to multi-cloud load balancing.How-To Videos Watch 3-5 min videos and learn new skills.
#SUBNET MASK TABLE 4 BITS HOW TO#
Operations Videos Learn how to deploy our prooduct.Workshops Attend free workshops to get hands-on.Start Here Get the catalog of all eduational offerings.Container Ingress Connect and secure container applications.
#SUBNET MASK TABLE 4 BITS SOFTWARE#
Software Load Balancer Modernize hardware load balancers.
Intelligent WAF Protect web applications with WAF.
Overview Bring simplicity and flexibilty to consume cloud services.
VMware Tanzu Bridge lab-to-production gap with Kubernetes Ingress Services.
Kubernetes Deliver enteprise-grade ingress services for any container platform.
OpenStack Build private cloud with advanced load balancing on OpenStack.
Google Cloud Platform Future-proof application delivery for Google Cloud.
Amazon Web Services Make multi-cloud load balancing easy for AWS.
Microsoft Azure Deliver enteprise-grade load balancing on Azure.
VMware vSphere Modernize data center and extend VMware load balancing anywhere.
VMware Horizon Enable remote working with the best integrated VDI solution.
VMware NSX Connect and secure your workloads with native NSX integration.
Web Application Firewall Secure web apps with scalable application security.
#SUBNET MASK TABLE 4 BITS UPGRADE#
Upgrade from F5 Replace legacy load balancers with modern load balancing.
Platform Architecture Take a new approach to application services.
Platform Overview Deep dive into software-defined architecture.
What We Do Understand multi-cloud load balancing.
It not only calculates the required fields but also pops out a window that draws the bit pattern and explains the results. With Windows 2000 and beyond Subnetting you do not have to do that anymore.īTW, if you need to calculate Subnet Masks and Network IDs and you can’t do it yourself (Duh, “Paper MCSE” or not?) you should try this fantastic Subnet Calculator right here: the result would have been 240 instead of 224. If you wanted 8 subnets, you had to calculate like you wanted 10, i.e.
#SUBNET MASK TABLE 4 BITS PLUS#
For example, if you wanted 2 subnets, you had to figure the number you wanted plus 2 – calculate like you wanted 4, i.e. Note: In Windows NT 4.0 you had to subtract 2 from the total number of available subnets. Only in Class C networks does the N value remain the same. In a Class B network instead of saying 5 (for example again, duh!) you must say 5+8. Therefore in a Class A network instead of saying 7 (for example) you must say 7+8+8. N=Number of Non-masked bits – Remember that in Class A and B networks you have other octets besides the one you’re subnetting. The table deals with Subnetting of only one octet. Use this table to help you calculate Subnet Masks, available hosts per subnet or number of subnets per class.

0 notes
Text
The Differences Of KVM And VMware
Today’s environment is dynamic and changing at a moment’s notice. The need to manage multiple platforms, virtual desktops, Servers, Storage and Network all in a single system makes VMWare special. It enables containers as well as virtualized environments on specific machines to be accessed remotely via the internet or over the phone using any device with a web browser and appropriate software. Let’s take a look at the main differences between KVM and VMware.
What is KVM?
KVM is a virtualization technology that enables a managed, virtualized guest computer system on a Scale-Out Tower (SOT) or host-based server. In a nutshell, virtual machines work as if they were running on physical machines, but with the addition of a VMWare Player, the guests become virtual machines. These virtual machines can be teamed up with one or multiple virtual desktops, or “virtualized desktops.” KVM virtualization is sometimes also used to mention with VMware’s vSphere platform.
What is VMware?
Virtualization technology is the practice of putting computers, or virtual machines, in hosts or clouds that are also virtualized. Imagine a virtualized virtual server, cloud server, or VMs on a virtual machine. The virtual machine is a high-level, stateless software that runs on one or more hosts. On a virtual machine, the virtual server is the base system, and all its dependencies are virtual machines. If a virtual machine has dependencies other than the real host, then that host’s virtual machine is executed on the virtual server.
Differences between KVM and VMware
While the virtualization landscape is a lot more diverse than that, the main differences between KVM and VMware are the following:
- Virtual machines can be physical or virtual.
- Virtual machines have their own host computer. Virtual machines can host applications, Web applications, and services like load balancers, web hosts, and Mods.
- Virtual desktops are not network-attached devices (NAS). Network-attached devices are software appliances that can be connected to the internet, but are not part of the virtual machine.
- Virtual desktops can be distributed across multiple hosts. The host environment variable controls the virtualization strategy on the virtual machine. On most virtualization products, the host environment variable is set to “none.”
- Virtual machines can run within a single host. Virtual desktops can run on separate hosts or on a cluster of hosts, but they can never run on a single host.
- Virtual machines can have multiple remote users. Remote users are not responsible for managing the VMs or the guest OS. They can connect to the virtual machine through any web browser or other software, but each virtual machine should have a unique user.
Conclusion
KVM and virtualization technologies have been at the center of IT innovation for the last few years. With the advent of the cloud, virtualization became a rapidly growing area of IT, and with it came a need for technologies that could be used on remote, virtualized systems. One of the most popular and successful virtualization technologies is KVM, which can be used on a wide variety of platforms and devices. With this article, you’ll understand the main differences between KVM and VMware, and how they can be used to hybridize the virtualization process on remote systems with on-site usage.
0 notes
Text
VMware Networking: 5 Concepts to Master
VMware Networking: 5 Concepts to Master #homelab #selfhosted #vmware #VMwareNetworkingEssentials #vSphereStandardVsDistributedSwitch #ManagingMultipleUplinks #UnderstandingVMwareFailovers #MasteringLoadBalancingInVirtualEnvironments #VLANTaggingInVMware
One of the challenges when getting into virtualization using VMware ESXi and vSphere with vCenter Server is understanding the many different networking concepts. There are a few foundational concepts in the VMware networking layer that you need to understand and master that will provide a basis for building your environment connected to the virtual network in your VMware environment. Table of…

View On WordPress
#configuring VMkernel ports#ensuring security with virtual switches#managing multiple uplinks#mastering load balancing in virtual environments#optimizing virtual and physical network communication#understanding VMware failovers#VLAN tagging in VMware#VMware network traffic management#VMware networking essentials#vSphere Standard vs Distributed Switch
1 note
·
View note
Text
New Post has been published on VMware Virtualization Blog
New Post has been published on https://www.tayfundeger.com/runecast-5-1-ile-gelen-yeni-ozellikler.html
Runecast 5.1 ile Gelen Yeni Özellikler
Merhaba,
Runecast 5.1 ile Gelen Yeni Özellikler isimli bu yazımda sizlere Runecast’ın yeni gelen versiyonu ile birlikte gelen yeniliklerden bahsediyor olacağım.
Daha önce Runecast’ı kullanmadıysanız veya ne işe yaradığını bilmiyorsanız aşağıdaki linki inceleyebilirsiniz.
Runecast Analyzer Nedir?
Runecast Analyzer
Runecast Kullanmanın Avantajları
Runecast 5.1 ile Gelen Yeni Özellikler
Runecast ile ilgili zaman zaman makaleler yazıyorum ancak bu süreçte Runecast kendini oldukça hızlı geliştirmeye devam ediyor. Geçtiğimiz zamanlarda makale yazdığımda Runecast’ın Nutanix support’unun olup olmadığı konusunda çok fazla soru geliyordu. Bu sorunuzu artık Evet! Olarak yanıtlayabilirim. Artık Nutanix AOS kullanıyorsanız Runecast ile ortamlarınızı analiz edebileceksiniz.
Runecast 5.1 ile birlikte gelen yenilikler hakkında kısaca bilgi vermek istiyorum.
Configuration Vault:
Configuration Vault özelliği aslında beni oldukça heyecanlandıran özelliklerden birtanesidir. Bu özellik sayesinde altyapımıza daha hakim olabiliriz.
Configuration Vault özelliği sayesinde VMware vSphere, VMware Horizon, AWS, Kubernetes, NSX, vCloud Director ve AWS gibi ortamlarda yer alan konfigurasyon verilerinin metaları Runecast’a kopyalanır. Bu veriler Runecast dashboard’ında karşınıza grafikler halinde sunulur. Configuration Vault’ın asıl amacı aslında altyapınızda yapılan değişiklikleri analiz etmenize yardımcı olmaktır.
Runecast 5.1 ile Gelen Yeni Özellikler
Bu özelliği biraz daha detaylandırmak istiyorum. 10 taneden az ESXi host’u bulunan firmalarda genellikle satın almalarda çok uğraşmazsınız. Ancak bir datacenter iseniz, altyapınıza yeni bir sunucu alımı yapmak istediğinizde büyüme raporlarına ihtiyacınız olacaktır. 2019 senesinde kaç virtual machine bulunuyordu, 2020’de kaç virtual machine’e ulaştık? 2019 senesinde datastore doluluk oranı neydi 2020’de ne kadar oldu gibi soruların cevaplarını bulabilirsiniz.
Aslında bu işlemleri VROPS üzerinden de gerçekleştirebilirsiniz ancak orada bu işlemleri gerçekleştirmek için kendiniz raporlar çıkarmanız gerekiyor. Bu raporları çıkarmak ve hazırlamak biraz sürenizi alıyor. Aynı şekilde Rvtools gibi raporlar ilede bunu yapabilirsiniz ancak Runecast size bu dataları günlük verirken Rvtools gibi ürünlerde sadece çalıştırdığınız günü baz alırsınız. Runecast bizlere tüm verileri tek bir ekranda günlük rapor şeklinde verebiliyor. Tüm bunlara ek olarak, ESXi hostlar arasındaki versiyon farklılığı, fiziksel sunucular arasındaki donanım ve firmware farklılığına kadar detayların hepsini tek bir ekranda görebilir ve bunları CSV formatında dışarı çıkarabilirsiniz.
Yukarıda örneği doğrudan VMware üzerinden verdim ancak, eğer bir AWS kullanıcısı iseniz, Eleastic IP, Load Balances, RDS Cluster, RDS Instance ve VPC’lerinde detaylarını görebilirsiniz. Yukarıda hangi ürünleri support ettiğini ayrıca belirttim zaten.
Configuration Vault özelliği sayesinde altyapınızda bulunan farklılıkları görebilir, böylece eğer bir sorun yaşıyorsanız bu sorunun konfigurasyon farkından mı kaynaklı sorusunun cevabını hızlı bir şekilde görebilirsiniz.
Remediation:
Runecast’ın üzerinde en çok uğraştığı aslında özelliklerden birtanesi Remediation özelliği diye belirtiliyor. Bende bunu anlattıktan sonra ne kadar güzel bir özellik olduğunuda kendiniz anlamış olacaksınız 🙂
Remediation, bir sorun tespit edildiğinde bu sorunun düzeltilmesine yardımcı olan harika bir özelliktir. Elbette şuanda tespit edilen sorunların hepsi otomatik olarak düzeltilemesede, ilerleyen sürümlerde bu kapsamın daha da ilerleyeceğini, yeteneklerinin artacağını düşünüyorum.
Remediation özelliği sayesinde altyapınızda oluşan bir hata veya bir konfigurasyon hatasını düzeltebilirsiniz. Örneğin ESXi Server üzerinde SSH’ı aktif duruma getirdiğinizde, Host üzerinde sarı bir ünlem çıkacaktır. Bunun sebebi aslında güvenlik açığından kaynaklanmaktadır. Zaten VMware Best Practices’lerini okuduğunuzda SSH’ı kullanmadığınızda disable etmeniz gerektiğini görürsünüz. 22 numaralı port SSH tarafından kullanıldığı için siz servisi başlattığınızda bu port üzerinden dışarıdan bağlantı sağlanabilecektir.
Bundan dolayı eğer kullanmıyor isek, SSH’ı stop durumda bırakmamız gerekmektedir. Ancak çok büyük ortamlarda maalesef bunun takibini yapmam mümkün olamayabiliyor. Eğer Runecast kullanıyorsanız Best Practices bölümünde karşınıza çıkan uyarılara müdahale edebilirsiniz. Yukarıda vermiş olduğum örnekte olduğu gibi SSH servisi start durumda ise karşınıza çıkan Remediation butonu ile bu servisi durdurabileceğiniz PowerCLI ve Ansible script’leri karşınıza çıkacaktır.
Runecast’ın Remediation özelliği gibi çalışan farklı bir ürün hakkında bilgi vermek istiyorum. vRealize Orchestrator aslında burada bahsedeceğim Remediation özelliği gibi işlemleri yapabiliyor. Orchestrator, VMware’in enfazla kullanılan ürünlerinden birtanesidir. Çünkü ayrı bir lisansa ihtiyaç duymaz ve vCenter Server lisansı ile birlikte gelir. Ancak ileri seviye scripting bilgisine sahip değilseniz Orchestrator ile çok fazla işlem yapamazsınız. Dolayısıyla hem kullanımı zor hemde ciddi bir know how gerektiren bir üründür. Ancak Runecast sayesinde basit bir şekilde sorunlarımızı çözebileceğiz.
Ben açıkcası Runecast 5.1 ile Gelen Yeni Özellikler Remediation özelliğini ileride daha kapsamlı olacağını düşünüyorum. İlerleyen versiyonlarda otomatik müdahale gibi işlemlerde olabilir. Biliyorsunuz VROPS’da actios diye bir tab ve buradan bazı müdahalelerde bulunulabiliyor. Ben bunun Runecast içinde geleceğini düşünüyorum. Yani bir süre sonra, eğer Runecast’a sahipseniz altyapınızı hiç izlemenize bile gerek kalmayabilir:)
Runecast Vmware Analyzer – Türkiye Distribütör firması “OTD Bilişim” satış ekibi [email protected] ile iletişime geçebilirsiniz.
Umarım faydalı olmuştur.
İyi çalışmalar.
0 notes
Text
Deep Dive Architecture Comparison of DaaS & VDI, Part 2
In part 1 of this blog series, I discussed the Horizon 7 architecture and a typical single-tenant deployment using Pods and Blocks. In this post I will discuss the Horizon DaaS platform architecture and how this offers massive scale for multiple tenants in a service provider environment.
Horizon DaaS Architecture
The fundamental difference with the Horizon DaaS platform is multi-tenancy architecture. There are no Connection or Security servers, but there are some commonalities. I mentioned Access Point previously, this was originally developed for Horizon Air, and is now a key component for both Horizon 7 and DaaS for remote access.
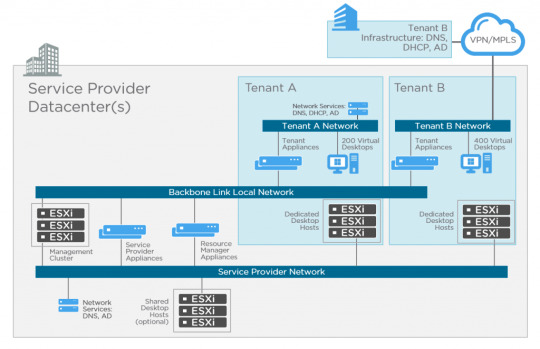
If you take a look at the diagram above you’ll see these key differences. Let’s start with the management appliances. There are five virtual appliances (OVA) used for Horizon DaaS; Service Provider, Tenant, Desktop Manager, Resource Manager and Access Point. When these appliances are deployed, they are always provisioned as an HA pair (master/slave), except for Access Point which is active/active across multiple appliances. No load-balancer is required, only for multiple Access Point appliances. The remaining virtual appliances use a virtual IP in the master/slave configuration. There is only a single OVA (template), and upon initial installation, the bootstrap process uses this template as a base for each of the virtual appliance types.
I’ve already introduced Access Point with the Horizon 7 architecture previously, but it’s worth mentioning that this is a recent addition. Previously with the original Desktone product and subsequent versions of Horizon DaaS platform, remote access was provided using dtRAM (Desktone Remote Access Manager). The dtRAM is also a virtual appliance (based on FreeBSD and pfSense) and still available, but I would now recommend using Access Point for the latest features.
Service Provider
The service provider has two different types of virtual appliance (HA pair); the Service Provider and Resource Manager.
The Service Provider appliance provides the Service Center portal where the provider can perform a number of activities including Desktop Model management, Tenant management, monitoring and discovery of infrastructure resources. This appliance also contains a Resource Manager service which targets and deploys other management virtual appliances. For example, when a Tenant Appliance pair is created, it’s name, networks, IP address, and so on, are stored in the FDB (Fabric Database). The Service Provider appliance then instructs the resource manager service to clone a tenant appliance.
Resource Manager
The Resource Manager virtual appliance communicates with the infrastructure (vCenter) to carry out desktop provisioning, and provides management of all desktops for tenants. Unlike Horizon 7 that can provision View Composer linked clones, Instant Clones or full clones, only full clones are currently supported with Horizon DaaS. Resources are assigned to tenants so they can consume compute, storage and network for virtual desktops.
It’s important to note that Resource Manager appliances are tied to the service provider, and not the tenant.
Tenant
The tenant also has two different types of virtual appliance (HA pair); Tenant and Desktop Manager virtual appliance.
The Tenant appliance provides a web-based UI (Enterprise Center) for both the tenant end-user and IT administrator. End-users can manage their own virtual desktops, and the administrator functions allow for creation and management of the tenant desktops.
Other tenant operations provided by Enterprise Center, include:
Domain registration
Gold pattern conversion
Desktop pool creation
AD user and group assignment to virtual desktops
The Tenant virtual appliance also contains a Desktop Manager component which brokers connections to tenant virtual desktops. Each Desktop Manager supports up to 5,000 virtual desktops. If more are required then a HA-pair of Desktop Manager virtual appliances can be deployed.
Desktop Manager
The Desktop Manager virtual appliance is the same as the Tenant appliance, but does not include the brokering or Enterprise Center portal. You can deploy Desktop Manager appliances to scale beyond the 5,000 virtual desktop limit.
Resources are assigned to the Desktop Manager for consumption by the tenant. In some cases you may have a vSphere cluster dedicated for 3D workloads with vDGA pass-through. These 3D specific resources would be dedicated to a Desktop Manager virtual appliance pair.
Each virtual desktop is installed with the DaaS Agent which sends heartbeats to the Desktop Manager in order to keep track of it’s state.
Networking
As shown in the above diagram, there are three networks associated with Horizon DaaS; Backbone Link Local network, Service Provider network, and tenant networks.
The Backbone Link Local network is a private network that is dedicated for all virtual appliances. Although the Tenant virtual appliances are connected to this network, there is no access from the tenant network.
The Service Provider management network provides access for service provider administration of the Service Provider appliances, and vSphere infrastructure.
The Tenant network (per tenant) is dedicated for virtual desktops. This also has IP connectivity to the tenants supporting infrastructure such as Active Directory, DNS, NTP, and file servers.
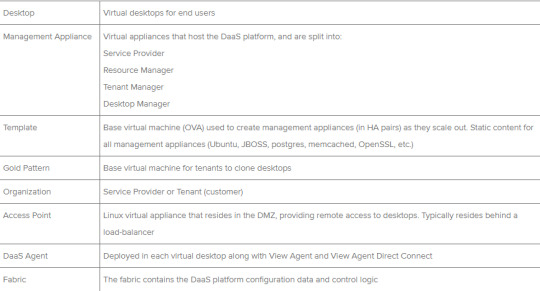
Horizon DaaS Terminology
Conclusion
VMware Horizon® is a family of desktop and application virtualization solutions that has matured significantly over the past few years. vCloud Air Network service providers can provide customers with either a managed Horizon 7 platform, or Desktop as a Service with Horizon DaaS.
Both Horizon 7 and Horizon DaaS offer virtual desktops and applications, and used in combination with App Volumes, applications can be delivered in near real-time to end-users.
Access Point provides remote access to both Horizon 7 and Horizon DaaS which provide many advantages to the service provider. With their active/active scalable deployment, and hardened Linux platform, service providers and customers can benefit from multiple authentication and access methods from any device and any location.
For both Horizon solutions, RDSH continues to be an attractive choice for delivering desktop or application sessions. These can either be presented to the user with the Horizon Client, or with integration with Workspace ONE and Identity Manager.
Finally, the vCloud Air Network is a global ecosystem of service providers that are uniquely positioned to supply modern enterprises with the ideal VMware-based solutions they need to grow their businesses. Built on the foundation of existing VMware technology, vCloud Air Network Service Providers deliver a seamless entry into the cloud. You can learn more about the vCloud Air Network, or search for a vCAN service provider here: http://vcloudproviders.vmware.com
0 notes
Text
Key Generator Vmware Esxi 6.7 Key Generator

Vmware Esx Server 2 5 5 serials generator: Sagetv Media Server 6 5 9 204 serial number maker: Vmware Esx Server 2.5.3 serial key gen: Vmware Ace Workstation 6 5 2 serials key: Vmware Workstation V 6.5 crack: Vmware-workstation 6 5 3 serial number maker: Vmware Workstation 6.5.1 crack: Vmware Workstation 6 5 3 key generator: Vmware. Mar 1, 2020; 2 min read. VSphere 6.5 torrent or any other torrent from the. You purchased a server with VMware ESXi embedded in the hardware and need to. Partner Activation Code (PAC): A printed code delivered from your OEM. Vmware Vsphere 6.7 Keygen 4,9/5 3834 votes. VMware vCenter Server 6 / 6.7. Esxi keygen Esxi keygen. Vmware Vsphere 6.7 Keygen Standalone; Vmware Vsphere 6.7 Platinum Keygen; Release Date: JUN 9, 2020. VMware vCenter Server and modules for Windows 6.7.0U3b. Installer for VMware vCenter Server, VMware Platform Services Controller, VMware vSphere.
Vmware Esxi 6.7 Download Iso
Vmware Esxi 6.7 Free
Vmware Esxi 6.7 License Key
Register to download your Free Product
This download center features technical documentation and installation guides to make your use of vSphere Hypervisor a success.
Vmware Esxi 6.7 Download Iso
Top vSphere Hypervisor Resources

VMware vSphere Hypervisor – Install & Configure
Thank you for downloading VMware vSphere Hypervisor
Introductory Resources
Vmware Esxi 6.7 Free
Installing, Deploying and Using VMware vSphere Hypervisor
Videos
Installing, Deploying and Using VMware vSphere Hypervisor
Technical Virtualization Topics
Read technical information on deploying virtualization to the entire IT infrastructure.
Troubleshooting & Support
Learn basic tips and tricks for troubleshooting various components of VMware vSphere Hypervisor.
Other Resources
How to Buy
Build a Dynamic Datacenter with VMware vSphere
VMware vSphere Hypervisor enables single-server partitioning and forms the foundation for a virtualized datacenter. By upgrading to more advanced editions of VMware vSphere, you can build upon this base virtualization layer to obtain centralized management, continuous application availability, and maximum operational efficiency. VMware vSphere is the most widely deployed enterprise virtualization suite that offers customers:
Centralized management of virtual machines and their physical hosts
Integrated back up and restore of virtual machines
Protection against physical server failures for high availability
Live migration of virtual machines between physical servers with no downtime
Dynamic load balancing of virtual machines to guarantee service levels
Customers can obtain VMware vSphere Hypervisor free of charge and later seamlessly upgrade to more advanced kits of vSphere designed for Small Businesses or Mid-Size & Enterprise Businesses

Please login or create an account to access VMware vSphere Hypervisor license and downloads
Support
View the top articles related to troubleshooting and support for this product. Add keywords to narrow your search.
Relevant Keywords:
VMware vSphere 6.7 has been announced by VMware recently and there are many enhancement and new features are available with this release. Question is how we can obtain a free version of vSphere 6.7 for our non-production or testing environment.
As earlier how we used to get free license for older versions same method we have the options to generate vSphere 6.7 license. License key with no expiration date can created free at VMware’s website. You can use the “Free Hypervisor” as identical to the paid version but with some software limitations.
Avast 2015.10.0.2208 activation code. Also Free version has some technical Spec and limitations , find the below .
Vmware Esxi 6.7 License Key
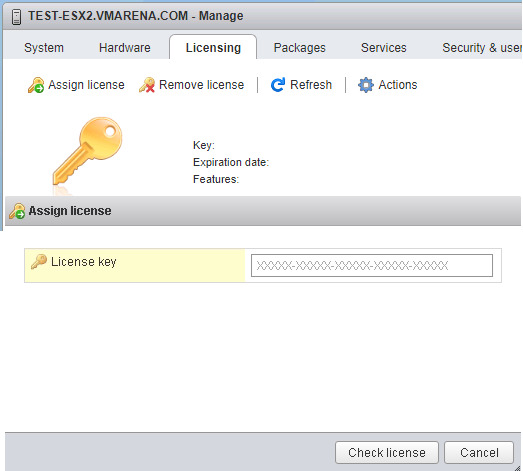
Free ESXi cannot be added to a vCenter Server
No commercial support
Some API functionality is missing
Number of logical CPUs per host: 480
No physical CPU limitation
Maximum vCPUs per virtual machine: 8
If you have already a free key for ESXi 6.0 or 6.5, you can use the old key for vSphere 6.7 also.
How to Obtain Free vSphere License
Browse to VMware vSphere Hypervisor (ESXi) 6.7 Download Page
You can Login with existing account or create an account
To Register for ESXi you have to enter your personal information .After registration, you will receive a unique license key and access to the vSphere 6.7 binaries.
Now Download VMware vSphere Hypervisor 6.7 – Binaries
You can install ESXi to your Hardware and ass the License to the ESXI host from web Client
Login as root with the Embedded Host Client (https://<ESX IP / FQDN>/ui/)
5.Navigate to Manage -> Licensing
6. Click Assign license and enter your license key and start using the free vSphere 6.7 Error reading shape file autocad.

0 notes
Link

UTILITY STORES CORPORATION OF PAKISTAN (PRIVATE) LIMITED
HEAD OFFICE, ISLAMABAD
CAREER OPPORTUNITY
Utility Stores Corporation is looking for individuals for following positions who are innovative, productive and
enthusiastic with ability to deliver results: -
ProvinciaV
S.No Name of Post
Requisite Qualification
Regional Quota
and Experience
University Degree in Computer Science, Business
Administration or related field equals to 16 years of education
with minimum 10 years practical experience preferably in
Digital Transformation Project Management/Data Science/Big
Data/IT Systems and Architecture in an Industrial /
Project Manager
Merit: 01
Commercial/ FMCG organization.PMP, Agile, and/or other
1 (Market Based Salary)
Project Management-related certification(s).Must have
(01 Post)
experience of managing implementation projects in any Retail
Chain organization. Experience in developing detailed project
schedules and building effective Work Breakdown Structures
(WBS).Proficiency with MS Project, Excel, Visio, PowerPoint
and SharePoint with experience presenting to stakeholders and /
or Senior Leadership.
University Degree in Computer Science or related field equals
to 16 years of education. 7 years of experience with utilizing,
configuring, and installing software for connecting distributed
software and services across heterogeneous platforms.
Experience in securing production workloads in public/private
clouds, Private Cloud Deployment using Open Source
Technologies, like Linux, MaaS - Bare Metal Management
software, Open Stack software bundle and with Linux operating
Manager Systems/
Sindh: 01
systems. Strong understanding across cloud and infrastructure
Information Security
2 (Market Based Salary)
components (server, storage, data, and applications) to deliver
end to end cloud infrastructure architectures and designs. Clear
(01 Post)
understanding of the challenges of information security.
Excellent analytical and problem-solving abilities to identify
and fix security risks.
University Degree in Computer Science or related field equals
to 16 years of education.5 years of relevant work experience
particularly in Software Requirements, Software Architecture,
Software Development Fundamentals, Object-Oriented Design
(OOD), Multimedia Content Development and Software
Software Developer
Punjab: 01
ICT: 01
(Market Based Salary)
Debugging. Work experience as a Python Developer and
expertise in at least one popular Python framework (like
Django, Flask or Pyramid). Knowledge of object-relational
(02 Posts)
mapping (ORM), Odoo framework and front-end technologies
(like JavaScript and HTMLS).
University Degree in Computer Science or related field equals
to 16 years of education with3 years of relevant experience.
Demonstrable portfolio of released applications on the App
store or the Android market. Extensive knowledge of at least
Mobile App Developer
one programming language like Swift, Java etc. Experience
(Market Based Salary) Punjab
(Including ICT)
with third-party libraries and APIs. Superior analytical skills
(01 Post)
: : 01
with a good problem-solving attitude, ability to perform in a
team environment and ability to interpret and follow technical
plan.
University Degree in Computer Science or related field equals
to 16 years of education with 5 years of relevant database
administration experience. Hands-on experience in the
Database Administrator
definition, design, creation, and security of a database
5 (Market Based Salary) Punjab: 01
environment and database technologies (MySQL, MS SQL
(01 Post)
PostgreSQL Oracle, MongoDB). Experience with any cloud
services (OpenStack, AWS, and Microsoft Azure. Ability to
work independently with minimal supervision.
University Degree in Computer Science or related field equals
to 16 years of education with 5 years of relevant network
administration experience. Advanced knowledge of system
vulnerabilities and security issues and knowledge of best
practices around management, control, and monitoring of server
Network Administrator
infrastructure. Experience with firewalls, Internet VPN's
(Market Based Salary)
Punjab: 01
remote implementation, VMs, troubleshooting, and problem
(01 Post)
resolution. Ability to set up and configure server hardware.
University Degree in Computer Science or related field equals to
16 years of education with 5 years relevant hands on experience
with automation/DevOps activities. Extensive experience with
automation using scripting languages, such as Python as well as
configuration of infrastructure with code automation, version
control software and job execution tools, preferably Git.
Experience with Application Logging, Monitoring and
7 DevOps Engineers Punjab: 01
performance Management. Strong understanding of continuous
(Market Based Salary)
Sindh: 01 integration/delivery practices and other DevOps concepts.
(02 Posts)
Experience with cloud platforms, virtualization platforms and
containers, such as AWS, Azure, OpenStack, Docker,
VMWare/VSphere, etc. Experience with web application
environments, such as TCP/IP, SSL/TLS, HTTP, DNS, routing,
load balancing, CDNs, etc.
University Degree in Interaction Design, Architecture, or related
field equals to 16 years of education.3 years of relevant
experience with multiple visual design programs such as
Photoshop or Illustrator. Knowledgeable in wire-framing tools,
storyboards, user flows, and site mapping. In-depth
understanding of UI, latest design and technology trends and
UI Graphic Designer
their role in a commercial environment. Measure Human
8
Punjab (Including
(Market Based Salary)
ICT): 01 Computer interaction element of a design. Mathematical aptitude
(01 Posts)
and problem-solving skills to analyze problems and strategize
for better solutions. Able to multitask, prioritize, and manage
time efficiently, work independently and as an active member of
a team. Create visual elements such as logos, original images,
and illustrations to help deliver a message. Design layouts,
including selection of colors, images, and typefaces.
University Degree in Computer Science or related field equals to
16 years of education with minimum one year of relevant work
experience. Experience in Software Requirements, Software
Junior Software Baluchistan: 01
Architecture, Software Development Fundamentals, Object-
Developer
Oriented Design (OOD), Multimedia Content Development,
(Market Based Salary)
KPK: 01
Software Debugging. Work experience as a Python Developer
(02 Posts)
with expertise in at least one popular Python framework (like
Django, Flask or Pyramid). Knowledge of object-relational
mapping (ORM), Odoo framework and Familiarity with front-
end technologies (like JavaScript and HTML5).
1.
2.
3.
4.
5.
6.
Maximum age limit for positions at serial 1 & 2 is 45 years, for positions at serial 3to 8 is 40 years and
for position at serial 9 is 30 years.
• The appointment would be purely on a contract basis for a period of 2 years, extendable subject to
satisfactory performance.
Organization is committed to the principles of equal employment opportunity and to make employment
decision based on merit. Female Candidates are encouraged to apply.
Applicants working in Government, Semi-Government Autonomous Bodies should route their
applications through proper channel duly accompanied with NOC.
Advance copy of the application shall not be entertained.
Applicants sending applications through post courier must indicate the name of position on the top left
corner of the envelope.
Only shortlisted candidates would be called for interview.
Internal candidate meeting the above criteria can also apply.
Applications on the prescribed format (available on USC website www.usc.org.pk) along with CV
should reach through post on the following address within 15 days of the publication of this
advertisement. Applications received after due date will not be entertained.
Office of the General Manager (HR&A)
Utility Stores Corporation of Pakistan (Private) Limited
Head Office, Plot No. 2039, Sector F-7/G-7, Blue Area, Islamabad
Contact No. 051-9245039
7.
8.
9
PID(1) 6155/20
0 notes
Photo

Dell PowerEdge R230 Vs Dell PowerEdge R330
Both Dell PowerEdge R230 and Dell PowerEdge R330 are 1-socket rack servers developed for dispersed programs in SMB, hosting, and OEM.
The PowerEdge R230 and Dell Power Edge R330 servers are somewhat scalable for information growth as they encourage up to four or eight inside 3.5-inch cabled or hot-plug hard-drives.
Moreover, users can enlarge the Wave memory capability via their 4 DIMM slots, which now supports as much as 64GB of memory for a 33% boost in memory efficiency on engineering and reliable application functionality and response times.
They are servers behind Microsoft Windows Server using Hyper-V, VMWare vSphere ESXi, and Citrix Xen Server. The R330 supports both the Red Hat Enterprise Virtualization HyperVisor adding a bunch of versatility when work-load conditions vary.
Dell Poweredge R230:
· The R230 is just a compact, 1U rackmount server.
· At the front of the device have the four 3.5" drive bays (users can even install 2.5" drives)
· This R230's Back shows us a port and also a VGA interface to the much Left-hand. The side would be your ability supply without redundancy.
· Near the Middle of this R230 is the 1Gb adapter that is Quad Port that is Broadcom.
· It would be the Broadcom DualPort 1Gb Base-T adapter, the two USB 3.0 interfaces, and a network interface. Quad-port will be the 2 PCIe expansion slots.
· The inside accessibility of the server is possible with sliding the panel off by pulling the latch top.
· Dell PowerEdge R230 is also a powerful and Efficient rack host great for applications in SMBshosting OEM customers and businesses.
· This server features two times that the I/O expansion is in contrast to the previous creation server, 3 x that the maximum inner storage ability and 100 percent greater memory potential.
Well Suited for:
SMB data productivity and collaboration applications, storage, mail/messaging, file/print
Dell PowerEdge R330
· The R330 can be a 1U server. The Dell Energy Edge R330's front has the same branding buttons And ports as the R230, just a different design.
· This arrangement, there are eight drive bays: 6 to precisely the right-hand side and two underneath the optical Disk around the left.
· The R330 offers an LCD With navigation buttons that exhibits platform details that is critical.
· The rear of R330 has a serial port, and a VGA port, both of them are located on the far left. The much right side is the power source.
· Dell PowerEdge R330 is a versatile rack machine ideal for small enterprises, remote offices and OEM clients require performance. Even the PowerEdge R330 provides up to 56 percent more storage capacity compared to the last generation server.
· Well Suited for Collaboration and Productivity applications file/print in SMB and office.
Whether in the home or even a small office, Dell Servers will be the ideal fit for your IT wants. One socket server Portfolio providing balanced overall performance and storage capacity of growth. Server rental provides Dell server sale in Bangalore, Chennai, Hyderabad, Pune, Kolkata, Mumbai, and Delhi.
0 notes
Text
Introduction to Cloud Computing
New Post has been published on https://computercoolingstore.com/introduction-to-cloud-computing/
Introduction to Cloud Computing

youtube
Follow the Insanity at: Downloadable Podcasts at: iTunes: Info
Level: Beginner Date Created: December 17, 2010 Length of Class: 75 Minutes Tracks
Cloud and Virtual Computing Prerequisites
None Purpose of Class
This class introduces students to the world of Cloud Computing and explains that Cloud Computing is more then Virtualization. Chapters
Introduction (00:00) Web Applications (06:51) Clustering (09:26) Terminal Services (16:26) Application Servers (25:13) Virtualization (30:00) Hosted Instances (44:05) Hosted Solutions (54:41) Public vs. Private Clouds (58:06) Final Thoughts (60:00) Class Notes
Introduction Cloud Computing is a design philosophy that breaks the Operating System and Applications from the Hardware Web Applications Are Created in Web Programming Languages Generally Use Databases to Store Data Clusters Are Generally Used for Database Servers (MySQL, Microsoft Active Directory) Load is balanced between servers in a cluster. If one server fails the cluster responds by not sending traffic to it. Servers maintain the same data by using replication Terminal Services Based off of old Mainframe and Dumb Terminal Architecture Now You Use Terminal Services Servers and Thin Clients Thin Clients can be Hardware Devices or Software installed on a computer All processing happens on Terminal Services Server and the Thin Client simply gets a “Window” into the server. Example: Application Servers Uses Terminal Services but instead of providing a full Environment it only delivers a specific Application. Virtualization Uses Desktop Clients Software or Hypervisors to allow you to install multiple Operating Systems on to one physical server. Hypervisors i. Hypervisor is installed on the physical hardware to support the Operating Systems, and Management Software is used to configure each Virtual Machine, or Instance. ii. VMWare uses ESXi as the Hypervisor and vSphere for the Management Software Hosted Instances Examples: Amazon EC2 , Microsft Azure You Pay for Use (Storage Amount, CPU Power, RAM, Bandwidth) Edge Locations are used by some providers to allow for faster access to servers over the Internet. You may be charged to send data from the main servers to the Edge Servers Hosted Solutions Are pieces of software that are hosted by vendors using the Cloud (Hosted Exchange, Google Docs, Adobe Acrobat.com, Mozy) Public vs. Private Clouds The Public Cloud is Cloud Computing used from Online Vendors Private Clouds are environments on business/organization property that use Cloud Technologies. Final Thoughts…. Security… Most Small Business Security is poor. Security for most small to medium sized business will be better when systems are hosted in the cloud Local and Internet Bandwidth becomes more important with Cloud Computing. Even on the LAN you may end using all of your bandwidth. Resources
VirtualBox VMWare ESXi Amazon Web Services Microsoft Azure MySQL Cluster
0 notes
Text
Introduction to Cloud Computing
New Post has been published on https://computercoolingstore.com/introduction-to-cloud-computing/
Introduction to Cloud Computing

youtube
Follow the Insanity at: Downloadable Podcasts at: iTunes: Info
Level: Beginner Date Created: December 17, 2010 Length of Class: 75 Minutes Tracks
Cloud and Virtual Computing Prerequisites
None Purpose of Class
This class introduces students to the world of Cloud Computing and explains that Cloud Computing is more then Virtualization. Chapters
Introduction (00:00) Web Applications (06:51) Clustering (09:26) Terminal Services (16:26) Application Servers (25:13) Virtualization (30:00) Hosted Instances (44:05) Hosted Solutions (54:41) Public vs. Private Clouds (58:06) Final Thoughts (60:00) Class Notes
Introduction Cloud Computing is a design philosophy that breaks the Operating System and Applications from the Hardware Web Applications Are Created in Web Programming Languages Generally Use Databases to Store Data Clusters Are Generally Used for Database Servers (MySQL, Microsoft Active Directory) Load is balanced between servers in a cluster. If one server fails the cluster responds by not sending traffic to it. Servers maintain the same data by using replication Terminal Services Based off of old Mainframe and Dumb Terminal Architecture Now You Use Terminal Services Servers and Thin Clients Thin Clients can be Hardware Devices or Software installed on a computer All processing happens on Terminal Services Server and the Thin Client simply gets a “Window” into the server. Example: Application Servers Uses Terminal Services but instead of providing a full Environment it only delivers a specific Application. Virtualization Uses Desktop Clients Software or Hypervisors to allow you to install multiple Operating Systems on to one physical server. Hypervisors i. Hypervisor is installed on the physical hardware to support the Operating Systems, and Management Software is used to configure each Virtual Machine, or Instance. ii. VMWare uses ESXi as the Hypervisor and vSphere for the Management Software Hosted Instances Examples: Amazon EC2 , Microsft Azure You Pay for Use (Storage Amount, CPU Power, RAM, Bandwidth) Edge Locations are used by some providers to allow for faster access to servers over the Internet. You may be charged to send data from the main servers to the Edge Servers Hosted Solutions Are pieces of software that are hosted by vendors using the Cloud (Hosted Exchange, Google Docs, Adobe Acrobat.com, Mozy) Public vs. Private Clouds The Public Cloud is Cloud Computing used from Online Vendors Private Clouds are environments on business/organization property that use Cloud Technologies. Final Thoughts…. Security… Most Small Business Security is poor. Security for most small to medium sized business will be better when systems are hosted in the cloud Local and Internet Bandwidth becomes more important with Cloud Computing. Even on the LAN you may end using all of your bandwidth. Resources
VirtualBox VMWare ESXi Amazon Web Services Microsoft Azure MySQL Cluster
0 notes
Text
Introduction to Cloud Computing
New Post has been published on https://computercoolingstore.com/introduction-to-cloud-computing/
Introduction to Cloud Computing

youtube
Follow the Insanity at: Downloadable Podcasts at: iTunes: Info
Level: Beginner Date Created: December 17, 2010 Length of Class: 75 Minutes Tracks
Cloud and Virtual Computing Prerequisites
None Purpose of Class
This class introduces students to the world of Cloud Computing and explains that Cloud Computing is more then Virtualization. Chapters
Introduction (00:00) Web Applications (06:51) Clustering (09:26) Terminal Services (16:26) Application Servers (25:13) Virtualization (30:00) Hosted Instances (44:05) Hosted Solutions (54:41) Public vs. Private Clouds (58:06) Final Thoughts (60:00) Class Notes
Introduction Cloud Computing is a design philosophy that breaks the Operating System and Applications from the Hardware Web Applications Are Created in Web Programming Languages Generally Use Databases to Store Data Clusters Are Generally Used for Database Servers (MySQL, Microsoft Active Directory) Load is balanced between servers in a cluster. If one server fails the cluster responds by not sending traffic to it. Servers maintain the same data by using replication Terminal Services Based off of old Mainframe and Dumb Terminal Architecture Now You Use Terminal Services Servers and Thin Clients Thin Clients can be Hardware Devices or Software installed on a computer All processing happens on Terminal Services Server and the Thin Client simply gets a “Window” into the server. Example: Application Servers Uses Terminal Services but instead of providing a full Environment it only delivers a specific Application. Virtualization Uses Desktop Clients Software or Hypervisors to allow you to install multiple Operating Systems on to one physical server. Hypervisors i. Hypervisor is installed on the physical hardware to support the Operating Systems, and Management Software is used to configure each Virtual Machine, or Instance. ii. VMWare uses ESXi as the Hypervisor and vSphere for the Management Software Hosted Instances Examples: Amazon EC2 , Microsft Azure You Pay for Use (Storage Amount, CPU Power, RAM, Bandwidth) Edge Locations are used by some providers to allow for faster access to servers over the Internet. You may be charged to send data from the main servers to the Edge Servers Hosted Solutions Are pieces of software that are hosted by vendors using the Cloud (Hosted Exchange, Google Docs, Adobe Acrobat.com, Mozy) Public vs. Private Clouds The Public Cloud is Cloud Computing used from Online Vendors Private Clouds are environments on business/organization property that use Cloud Technologies. Final Thoughts…. Security… Most Small Business Security is poor. Security for most small to medium sized business will be better when systems are hosted in the cloud Local and Internet Bandwidth becomes more important with Cloud Computing. Even on the LAN you may end using all of your bandwidth. Resources
VirtualBox VMWare ESXi Amazon Web Services Microsoft Azure MySQL Cluster
0 notes