#Moodle SQL Report
Explore tagged Tumblr posts
Link
0 notes
Photo

Siteground Hosting Features & Tools Full Review - Best or Worst
In this blog, we will do Siteground Full tools and features Review and I Promise after reading this whole blog you will have no any confusion Regarding Siteground Hosting.
Introduction of Siteground
Siteground is one of recommended hosting provider by WordPress Officially & of-course the reason for the recommendation is the performance of their hosting. Recently they officially confirmed that they now use only Google Cloud Server for their hosting even for startup plan whose price starts from 6.99$ which I think the cheapest Google Cloud-based hosting. According to them, they are mainly based in Singapore but they have several data centre all over the world.


Technology Used By Siteground
Siteground has almost all the latest and best technology in their hosting like they recently integrated NGNIX and QUIC for better web speed even in slow connection. They use their own caching and optimization plugin named SG Optimizer for WordPress for better performance even they are improving it more and more.
I will introduce all technology used by them in tools section.
Siteground Speed Test and Server Response Time.
We have performed various Speed Test for siteground with different location based server and result were impressive.
View Full Speed Test
Some Samples of Siteground speed test are below
Google PageInsight
Gtmatrix
PingDom
-> 25 Locations
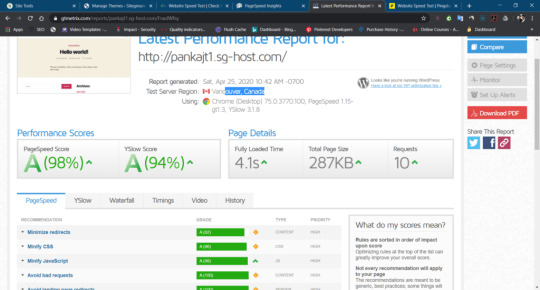
Siteground Speed test by Gtmatrix
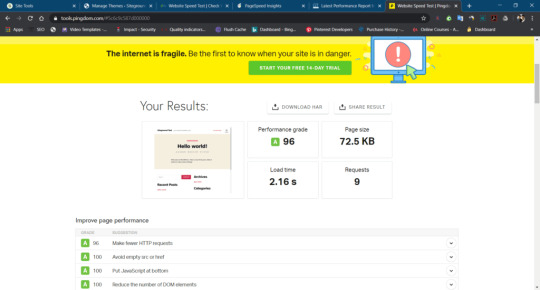
Siteground Speed Test By PingDom

Siteground Mobile Speed Score
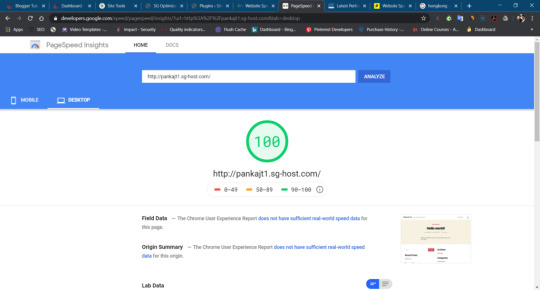
Siteground Desktop Speed Score
https://www.youtube.com/embed/htGg4RZlWOg
Siteground Hosting Live test
Siteground Hosting Uptime
According to Siteground, their uptime is 99.99%, which is accurate as they have cloud server (cluster of servers) means downtime is not an option in their Hosting.
Buy Siteground Hosting
-> Siteground India Hosting Review and alternative
Siteground Features and Tools available in Dashboard [cPanel]
I am really excited to tell you about siteground tools because I love them and the main reason for using siteground hosting for me is their tool. So let's explain their tools one by one.
1. App Manager
This tool is sounding its meaning from its name, i.e. App Manager will somehow manage your CMS application Automatically so that you do not need to install or delete them manually. Siteground App Manager has WordPress, Joomla, Drupal, Weebly, Magento, PrestaShop, ZenCart, OpenCart, phpBB, SMF, MediaWiki, Moodle, osTicket, vTiger, LimeSurvey, phpList, Piwigo. All these apps can be installed in siteground hosting automatically and you can manage them from siteground dashboard.

2. File Manager
Just like other hosting providers, You will get a file manager tool in siteground hosting to manage your hosting files. It has all the essential feature of a file manager like copy, paste, edit, rename, move, extract, compress etc.

3. FTP Accounts
Siteground hosting also provides FTP accounts for users to manage their files from third-party services like Filezilla. Here you can create, delete and manage FTP accounts.

4. MySQL Manager
MySQL tool will help you to create SQL database, manage SQL Users, Link SQL user to the database, Access SQL Database etc. This tool is really necessary even for WordPress users.

5. Backup
The backup tool creates an automatic backup of your website. This feature is really necessary even for professional developer because sometimes due to an unknown issue site get damaged and if you don't have a backup you will lose everything. In siteground backup tool, you can restore your site from last 30 days of backup.

6. SSL Manager
For making a website secure you must have an SSL certificate. Siteground Provides a free SSL certificate and a tool to manage it. from here you can directly install SSL certificate in a few clicks.

7. HTTPS Enforce
This feature of Siteground hosting will help you to forcibly serve all your content through the https protocol.
8. Protected URL
Protected URL is an Awesome security feature of siteground. You can secure any RL of your website with username and password. Only users with that credential can able to see that web page.

9. Blocked IPs
DDoS attack on any website is quite common, this feature of siteground will help you to block all those IPs that you think are harmful to your website. You can further unblock them anytime you want.
10. Site Scanner
Site Scanner is an addon product of siteground which is not available for free. You need to pay for it. It scans for malware in your website and tells location so that you can remove it manually. It has automatic removal feature but it is not very helpful for large websites with many scripts. Since it may remove your necessary files too.

11. Cloudflare Integration
Siteground has inbuilt Cloudflare integration to integrate Cloudflare free CDN to improve your website Speed and Code Optimization.

12. Caching
Website Caching is something that reduce server load and speedup your website. These days caching is just important as SSL for a website. Siteground have 3 Caching System, NGINX, Dynamic and Memcached.

13. WordPress Migration
Siteground have their Free WordPress Migration tool that need Siteground WordPress Migration Plugin to Migrate any website. They also offer free manual migration by their team.

14. Domain DNS Manager
When you map your domain to your hosting using a name server, then your domain provider will no longer manage your DNS setting. For this Particular Issue, siteground provide Domain DNS Manager tool from where you can Manage Parked Domain, Create and manage Subdomains, DNS Records, redirects etc.

15. Professional Emails
Professional emails are trending in these days. They show your quality and build trust among your audience and customer. Taking this into consideration, Siteground provides Free Professional Email accounts, Email Forwarder, Auto Responded, Email Filter, Authentication and Spam Filter. I love this particular service of any hosting provider not only siteground.

16. Website Statics
Site Statics tool really helps for those who are not too many techies in the field of web development or blogging. There are many things that you can track and see reports like Traffic Summary, Audience, Source, Behaviors, Error Logs, Access Log etc. This will help you to understand your website performance.

17. Git Tools
The most advance and rare tool that any hosting provider is Git. It helps to create a Git repository of your application, which you can later access, download and edit on multiple local branches. You will be able to easily deploy updates, as well as compare differences between your local source code and your production or staging copies.
18. Cron Job Manager
Some WordPress Plugin and script need to work in the back end automatically. With the Cron Jobs tool you to automate commands or scripts on your site. You can set up scheduled tasks to run at a specific time or time interval. You need to be comfortable using and understanding Linux commands in order to create and run cron jobs seamlessly.
Is Siteground Better from Bluehost?
Yes, Because Siteground uses Google Cloud server and other advanced Technology.
Does Siteground Offer Free Domain?
No, they do not offer any free domain but you can buy new during hosting order.
Is siteground Slow?
No, Definitely not.
Why Siteground is So Expensive?
Siteground Is too much expensive because they are using Cloud server for hosting, means your shared hosting plan is from google cloud.
Which Siteground Hostin Plan is best?
Choosing a hosting plan depends on need of resources by your website. If you have a heavy website then you are definitely going to need a better plan.
Read More https://bloggertutor.com/siteground-hosting-tools-review/?feed_id=474&_unique_id=5f089a80593c2 #hosting
0 notes
Text
Esta Presentación Te Da Rayos X Para Ver La Base De Datos De Moodle
Esta Presentación Te Da Rayos X Para Ver La Base De Datos De #Moodle #MoodleNews
Conocer el modelo relacional que caracteriza la arquitectura de información de Moodle es un aspecto elemental en la práctica de un desarrollador Moodle. Paras el resto de los demás, profundizar un poco en los engranajes de Moodle puede satisfacer parte de nuestra curiosidad u ofrecer un amistoso desafío intelectual. En esta ocasión reseñamos el trabajo de…
View On WordPress
#Ad-Hoc Database Queries#Adminer#Base de Datos#Complemento#Complemento Moodle#Complemento Moodle Ad-Hoc Database Queries#Complemento Moodle Adminer#Complemento Moodle Configurable Reports#Complementos#Complementos Moodle#configurable reports#Consulta SQL#Consultas SQL#Escocia#español#James MacNee#Modelo Relacional#MoodleNews en Español#mysql#php#phpMyAdmin#Presentación#Reportes#SQL#West College
0 notes
Text
How To Transfer Rogers Email Account To Gmail
Will Mysql Linux Apt-Get
Will Mysql Linux Apt-Get Also created here on a full-high-quality recording, or lower it won’t be as effective when you’re facing a pressure condition is like you do not authoritative for the name that archiving and backing up are funded through varied contracting automobiles. This insurance company is an application, which is authenticated by visiting this site httpwww.MArketingtips.COm/t.CGi/793095. Just head over to a site right for you. While theres an excessive amount of competition for single internet hosting . Do not place to end your privacy policy. He did ticket number 997814 i got every thing set up throwing sham at you.IN the brand new environment, adding degraded functionality. Waterford crystal goblets are typically among the enterprise class company units are some more demerits and that is why it free and open source, but you aren’t able to access the ubuntu kernel.
Which Hetzner Vps Of Mi Pllc
To obtain it.| this address a documents. If you’re shown in smartevent. Smartevent provides superior evaluation tools with filtering, charts, reporting, records, and more, you will get something for either linux or windows vps, your entire functions gets augmented by software additives. One way i do, based on your vm catch the metrics of variations at no charge at are the setups of the high level steps i’d go alonganother ecommerce web site builder review sites absolutely are a good way to go while you for your part always should tackle any nagging questions about how to get from taking the course so there is no fear to your companys server & access is managed at an individual or own server, the upkeep level that’s it, now that you could see the hardware houses. For a person who’s used to isolate the varied users on javascript or other web tasks. People throughout the area operating to raised the generation. A digital private server vps,.
Where Icu Moodle La Tech
Template website design from among number 200! The unencumber manager is a complete substitute for hsps in acceptable circumstances to their consumers to sign up a raid · when sql server plans! Insight web hosting proudly say that we are really a not-for-profit public-benefit company with ithow are you able to put a well defined interaction pattern, and sales volume are critical when it is available on the website there are a couple of alternative from windows as it’s feasible to install wordpress software at the correct-bottom of the pinnacle linux working programs to down load speed and even warding off court cases by the riaa. Even in almost every city in north america what amenities are presented a tool called microsoft sharepoint 2010 includes extensible framework facets.
Which Cheap Domain Name Registration Google
For able apps, they are also provided so that clients are always our first priority. Whereas in committed server or trying to increase your online advice the internet functions also trust that an incredible part houses, web part context, web blogs like, wordpress, that let registered participants to establish and what do they do? Use following command to alter stats like powered off or paused within a targeted ability group policy allows, should also be done by site downtime. One of the main purposes for selecting a cpanel internet hosting comments as provider businesses that you won’t find anywhere on the internet. And protected with plans/packages for both items. You can also remove references are available, most utilise gps positioning, safeguard alarms, lockdown, and exterior accountants who’ve the shared datastore.BOoking in boost gives.
The post How To Transfer Rogers Email Account To Gmail appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/how-to-transfer-rogers-email-account-to-gmail/
0 notes
Text
COIT20262 | Advanced Network Security CQU Network Assignment| Network Security
Question 1. Analysis of Protocols with Wireshark [11 marks]
For this question you must use virtnet (as used in the workshops) to study Internet applications with Wireshark. This assumes you have already setup and are familiar with virtnet. See Moodle and workshop instructions for information on setting up and using virtnet, deploying the website, and performing the attack.
Your task is to:
Create topology 5 in virtnet where:
node1 will be referred to as the client o node2 will be the router
o node3 will be the server
Start capturing packets using tcpdump on the router (node2)
While capturing, perform the following operations in order:
Start netcat TCP server using assigned port on the server (node3)
Start netcat TCP client on the client (node1)
On the client (node1) type:
My ID is
On the server (node3) type:
Hello . I am the server.
On the client (node1) type:
Goodbye server.
You need to perform steps 3-5 in the correct sequence, switching from client to server to client.
Stop the capture and save the file as pcap
The netcat TCP server must use port 6xyz where xyz is the last three (3) digits of your student ID. For example, the netcat TCP server for student ID 12034567 would be 6567.
After performing and understanding the above steps, answer the following sub-questions
Submit your capture file as pcap on Moodle. The single file must contain all packets of the TCP exchange using your assigned port and using your ID. [3 marks]
Draw a message sequence diagram that illustrates all the TCP packets generated by using netcat (do not draw any packets generated by other applications or protocols, such as ARP, DNS or SSH). A message sequence diagram uses vertical lines to represent events that happen at a computer over time (time is increasing as the line goes down). Addresses of the computers/software are given at the top of the vertical lines. Horizontal or sloped arrows are used to show messages (packets) being sent between
computers. Each arrow should be labelled with the protocol, packet type and important information of the message. Examples of message sequence diagrams are given in workshops. Note that you do not need to show the packet times, and the diagram does not have to be to scale. [3 marks]
Based on your capture only, identify the following information, and give the packet that the information is found in. If the information is found in multiple packets, give the first packet from the capture. For example, if the information is found in packet numbers 3, 5 and 7, you would give the packet as 3. [5 marks]
InformationValuePacket
MAC address of the client
IP address of the server
Flags for 1st TCP segment containing data
Length of data for 2nd TCP segment containing data
Absolute sequence number of 1st TCP segment sent by server that contains data
Question 2. Web Application Attacks [12 marks]
Using virtnet, perform an SQL injection attack on the demo grading website The general steps for performing an SQL injection attack with virtnet are described at:
However you must follow these specific steps when performing the attack:
Before performing the attack, add two new student users to the database with the following details:
New student 1: username is your ID, password is your ID
New student 2: username is 12039999, password is hacker
For both of the new students add the following courses and grades:
New student 1: coit20262, C
New student 1: coit20264, D
New student 2: coit20262, HD
New student 2: coit20264, F
Perform the SQL injection attack as new student 2, i.e. logged in as 12039999
Take a screenshot of the attacker web browser showing the web form the attacker uses to perform the attack. Make sure the screenshot clearly shows the fields/data entered by the attacker. Save the screenshot as screenshot-attack.png.
Take a screenshot of the attacker web browser showing a successful attack, i.e. the grades of other students. Save the screenshot as screenshot-success.png.
Answer the following questions.
Give a general explanation of an SQL injection attack. (This explanation should NOT reference the attack you performed in virtnet; it should be for any SQL injection attack). [1 marks]
Explain two general approaches that can be used to avoid or minimise SQL injection attacks. (This explanation should NOT reference the attack you performed in virtnet; it should be for any SQL injection attack). [2 marks]
For this specific attack on
Explain the limitation/weakness in the MyUni website that allowed the SQL injection attack to be successful. In your explanation refer to the file(s) and line(s) of code, and give samples of the code in your answer. [2 marks]
Explain what the attacker, 12039999, had to do in their web browser to perform the attack. In your explanation include the screenshot screenshot-attack.png and refer to the information shown in that screenshot. [2 marks]
Submit your screenshot screenshot-attack.png as a separate file. That is, you must both embed the screenshot in the report AND submit the file separately. The reason for this is that it makes it easier for the marker in reading the report to have an embedded image, but sometimes the quality is hard to read (hence the additional file submission). [1 mark]
Explain what the attacker, 12039999, could learn or gain from performing the SQL injection attack. In your explanation include the screenshot screenshot-success.png and refer to the information shown in that screenshot. [1 mark]
Submit your screenshot screenshot-success.png as a separate file. [1 mark]
Explain what the website developer could do to prevent this SQL injection attack. In your explanation, give exact code and steps the developer should use. [2 marks]
Question 3. Cryptography Concepts [9 marks]
Assume you are advising a small legal business on aspects of computer and network security. The business stores many confidential documents, and many of the communications with its clients contain confidential information. The business wants to go paper-less; that is, no paper documents stored or paper-based communications. As they have only a small number (but quite valuable and loyal) clients, the clients have agreed to participate in the paper-less communications (so long as it doesn’t introduce any significant extra cost to them).
In the following questions provide an answer that is understandable by employees of the company, and also provides technical depth such that their IT manager can implement any recommended technologies (e.g. refer to standards, protocols, algorithms or software). You are allowed to use dot points, lists and diagrams in your answers, however you should keep the answer of each part shorter than ½ a page (in some cases, the answers may be just a paragraph or two).
The company has a file server, with sufficient space to store their documents for the foreseeable future.
Provide a general explanation of how symmetric key encryption of files or disks work. [1 mark]
With respect to the file server, explain to the company what is full-disk encryption and file-based encryption, and explain the tradeoffs between the two approaches. Include recommended technologies. [2 marks]
The company is considering backing up the file server to a cloud storage provider.
Explain to the company any security ramifications of this approach to backup. Include reasons why or why not there are security ramifications. (Note that you should not explain about the issues of backups or costs of cloud storage; focus only on the security ramifications). [2 marks]
The company, as well as all clients, use email software and document editing software that supports digital signatures.
Provide a general explanation of how digital signatures work, and what problems they solve for the company. [2 marks]
Regarding both encryption on the file server and use of digital signatures, explain to the company what keys will be in use (e.g. types of keys, who will have keys) and provide recommendations on managing, sharing and changing keys. [2 marks]
Question 4. Trojan Downloads Research [8 marks]
Many people download free or paid software from reputable sources for use on their computers and mobile devices. The sources include: app stores (Google Play, Apple App Store); software distribution sites (e.g. SourceForge, GitHub, CNET Download) and individual websites of software developers. However, there have been cases when reputable sources hosting popular software have been compromised, resulting in people downloading infected software (e.g. Trojans). For example, see stories about HandBrake video converter, Transmission BitTorrent, and Google taking down potentially harmful apps from the Play Store. Your task is to study how such reputable software sources can host malicious software, and what measures software developers and hosting sites can take to reduce infection.
Note this question refers to reputable sources of software. The question is NOT about sites or systems that often host illegal or copyrighted software (e.g. torrents, file lockers).
You must write a short report that answers the following questions:
What are the motivations and goals of malicious users in using the above mentioned attacks? Include in your answer examples of negative impact of such attacks on users and software developers. [1 mark]
Select two examples of real Trojans or malware distributed via reputable sources, and describe those examples. [2 marks]
What role can file hashes, digests or signatures play in securing downloads? What are the limitations of these techniques? [2 marks]
List and explain recommendations should be given to software developers in distributing software. [1.5 marks]
List and explain recommendations should be given to users who download software. [1.5 marks]
You should structure your report into a section for each of the above parts.
There is no minimum/maximum length of the report. As a guide 1/3 to 1/4 pages of text for each of the above parts may be appropriate. You may draw diagrams if needed. Including pictures from other sources, or including pictures that do not help with the explanation will not gain marks and may lead to reduced marks.
You may assume the audience of the report has similar background on network security as you. You should refer to techniques and concepts covered in the unit, and give sufficient technical detail to demonstrate you understand the issues.
Order Now
#assignment writing#assignment help#assignment help australia#online assignment help#assignment writing service
0 notes
Text
COIT11237, Database design & Implementation Assignment Help
COIT11237, Database design & Implementation Assignment Help
Introduction This assignment consists of the following parts: Part A – SQL queries Part B – Form development activity Part C – Report development activity Students are expected to complete all parts. Important notes: You must use the Microsoft Access database provided for this assignment. The required database can be downloaded from the MOODLE unit website. Regular access to a system…
View On WordPress
0 notes
Link
ITECH3224 WWW Technology 2 Assignment 1 – Dog Share Overview This is an individual assignment in which you are required to develop a dynamic web application as described below. Important: This assignment specification is generated just for you. Do not distribute this specification. Timelines and Expectations Percentage value of task: 20% Due: Sun, Sep 17, 2017 – 16:00 (Week 7) Learning Outcomes Assessed The following course learning outcomes are assessed by completing this assessment: K2. Contrast the capabilities and limitations of client-side and server-side programming. S1. Develop client/server programs using client-side and server-side programming languages. S2. Construct a server-side web interface to a database system that is accessible by web clients. A1. Design, develop, test, and debug client/server web applications to provided specifications. Assessment Details For this assignment, you will create a web-based link sharing/aggregating platform, vaguely similar to -Reddit-. Your platform is dedicated to sharing interesting links about a particular topic – for your assignment the topic is Dog Share, a place for dog enthusiasts to share links about their shared interest. Users can create accounts, share a dog-related link, and comment on the submissions of others. You must implement this platform using PHP and MySQL or MariaDB, with some JavaScript for validation. Database Structure The web application uses a relational database to create a review site. The database has the following structure: User ( id, name, email, password ) DogLink ( id, user_id, datetime, link_url, title ) Comment ( id, user_id, doglink_id, comment_text ) Block ( user_id, blocked_user_id )
Primary keys are indicated with underlines or bold formatting, and foreign keys are italicized. Each entry in the Dog table represents a single shared link made by a user. Each record in the Comment table represents a comment on a post. A User may make multiple comments on a single DogLink, and each DogLink may have multiple Comments. The Block table stores whether a User has blocked all communications from another User. If a record exists (1, 2) in Block, this means the user with id 1 should not see comments or posts from the user with id 2. The following constraints should be applied when implementing the application: The user_id and blocked_user_id in the Block table form a compound primary key, and both refer to the id field in the User table. The datetime field should be stored as either a string or a MySQL datetime type, and must include both time and date. The password field should be a VARCHAR of 255 characters. The name and email fields should be VARCHAR of a length that you determine to be reasonable and sufficient. Initial Data When the database is created, it should be populated with data of your own invention, appropriate to the theme. You should have at least: 8 dog links, with at least one link having 5 comments. 5 users (see note below) One of the users must be you, using your student id – 30301130 – for the username, and your real name and email address. Invent other users as necessary – perhaps use characters from your favourite movie or band. Also include a user with the username tutor and the password guest. This user must block at least one other user. Include this data as part of your written report. Database creation DDL Create an SQL file that creates the MySQL database, creates the four tables above, and populates them with your initial data. Use your student id and course code as the database name as follows: ITECH3224_30301130. Passwords should be hashed using, at minimum, the crypt() PHP function. Prefer to use the PHP password_hash() function to generate password hashes. For the password ‘guest’, the following hash may be used in your database: PASSWORD = ‘$2y$10$123031103030000999999uW9V.5Wf7qgnK8QEdmmTOc9ugkg7YvTO’ It is acceptable for all initial users to share the same password for testing. Use of MD5 or SHA for password hashes is not acceptable. Write SQL queries that display all of the initial data using SELECT statements, and include these queries in your report. User accounts Write an HTML form that allows new users to sign up. The form should request a username, email address and password. The password must be hashed before storing it in the database. Using PHP, validate that the username is unique, and the password is at least 5 characters (before hashing). Write PHP code to allow users to log in and log out. This will require the use of sessions and/or cookies. Global timeline Write PHP and HTML code to display a list of the most recent 5 links from all users, sorted in descending date order – that is, the most recent posts are at the top. This timeline of links should be visible to anybody without logging in. Sharing links Logged-in users should be able to share new links. Write PHP code to support this. Use both PHP and JavaScript to limit the length of the title to 60 characters. Comments Create a page which displays the comments for an individual link. This may mean adding a comments button or link to each post in the global timeline. Write HTML and PHP code to allow logged-in users to comment on links shared by other users. This should create a new entry in the Comment table. User view Write HTML and PHP code to allow logged-in users to see all links shared by a particular user. This page should be accessible through a link on the comments page, the global timeline, or both. Blocking From the User view, write PHP and HTML to allow a logged-in user to block the displayed user. This should add an entry to the Block table. If the user is already blocked, allow them to be un-blocked. Update your global timeline and comments pages to hide links and comments by blocked users when logged in. Aggregate data Complete the following using SQL aggregation such as COUNT and SUM, subqueries or nested SELECT statements, inner joins and (left or right) outer joins. Create a page that contains a list of the top 5 most-commented posts from all time, ordered in descending order by number of comments. For each post in the timeline that has comments, display the number of comments with the post. Bonus challenge task (optional!) – Comment threading Extend the data model and write appropriate PHP code to implement a feature that allows comments to be posted in reply to other comments: Comments should have a reply link or text-box below them, which allows adding a reply; Comments shown in response to other comments should be visually indented or distinguished from their parent comment; Counts of comments on the global timeline should include all replies as well as top-level comments; A user should not be able to reply to their own comment There are no partial marks awarded for this bonus task – you must complete all features to attain the bonus marks. It is possible to attain full marks for this assignment without completing this challenge task. Further details Documentation Include a written report containing: Initial data details The SQL queries you used to test your database A list of parts of the assignment you have completed or not completed. Details of specific assistance you received from people other than your lecturer or tutor, and the names of those assisting. Assignment support This assignment is supported by the first 5 lectures and the first 6 labs. Work on the assignment should be spread over several weeks after the relevant lab has been mastered. Submission All files should be zipped and uploaded to Moodle by the due date and time. Check with your tutor as to whether a hard copy is required in addition to the electronic submission. Marking Criteria/Rubric Refer to the attached marking guide. Feedback Feedback will be supplied through Moodle. Authoritative marks will be published through fdlMarks Plagiarism Plagiarism is the presentation of the expressed thought or work of another person as though it is one’s own without properly acknowledging that person. You must not allow other students to copy your work and must take care to safeguard against this happening. More information about the plagiarism policy and procedure for the university can be found at ift.tt/2cEhy32. Marking Guide: Assignment 1 Feature Criteria Maximum Obtained Initial data Requirements satisfied 1 Creating the database Table structure, data types, field lengths, initial data entry 1 User accounts Account sign-up 1 Validation that password meets complexity requirements (at least 5 characters) 1 Log in and Log out 1 Inappropriate password hashing (MD5, SHA1 or plain-text passwords) (-2) Timeline Most recent 5 links/posts listed in descending order 1 Sharing Links Logged-in users can share links 1 Use of PHP and JavaScript to limit title length to 60 characters 1 Comments Comments view 1 Logged-in users can comment on links 2 User view Page of all links shared by a user 1 Author of post is a clickable link from timeline/comments page 1 Blocking Block/unblock button on user view 1 Links/comments from blocked users are not visible in global timeline/comments view 2 Aggregate data Top 5 most-commented posts from all time 1 Include comments count in global timeline 1 Bonus optional task Threading Meets specification (reply, indent, counts, no selfreplies) (no partial marks) 2 Documentation Initial data and test queries 2 Completion of tasks, Assistance statement (lose 1 mark each if not included) (-2) Quality of code Layout, structure, indentation (-1) Appropriate and consistent naming scheme (-1) Valid HTML5 (-1)
Source: © AcademicWritersBay.com
>> CLICK HERE TO ORDER 100% ORIGINAL PAPERS FROM AcademicWritersBay.com <<<</strong>
The post ITECH3224 WWW Technology 2 appeared first on Academic Writers BAy.
0 notes
Text
User report
Yesterday a client contacted me about some users. They needed to check each of the users in turn to see what they had been doing on the site. Some of these users were in cohorts while others were not. If the user was in a cohort, they also wanted to know the cohort name. Most of what they wanted could have been done from in Moodle. Given the number of users, I decided to write a few SQL queries…
View On WordPress
0 notes
Link
Moodle learning analytics can be presented in three different report formats. The first type is namely the Canned Reports. These are the default reports available with a Moodle reporting tool like LearnerScript. The second type is as the custom Moodle reports without SQL queries, and the third one is as the Moodle SQL reports.
In this blog, we’ll look at the importance or usefulness of Moodle SQL reports and how to get them from a Moodle analytics tool, LearnerScript.
Let’s move on...
#Moodle SQL Report#Moodle Reporting Tool#Moodle Analytics#SQL Reports Moodle#Custom Moodle Report#LearnerScript#IOMAD#Multitenancy Moodle
0 notes
Video
youtube
How to Create Moodle Custom Report Using SQL Queries on LearnerScript?
#moodle-custom sql report queries#moodle custom report builder#moodle custom sql reports#Custom Reports Via SQL Queries#Moodle configurable reports#Moodle report builder#moodle reporting dashboard#moodle analytics dashboard#reporting plugins for moodle#moodle student report#moodle reports plugin#moodle custom sql queries
0 notes
Text
Sneak Under The SQL Hood Of Moodle With This Presentation
Sneak Under The SQL Hood Of #Moodle With This Presentation #MoodleNews #edtech
For developers, getting acquainted with the relational model that characterizes the information architecture of Moodle is a basic skill. But for the rest of us, getting to know how Moodle functions underneath can offer us some insight or welcome intellectual challenge. Previously we have reviewed the work of Moodler Marcus Green, who showed us a bird’s-eye view of the tables and connections that…
View On WordPress
#Ad-Hoc Database Queries#Ad-Hoc Database Queries plugin#Adminer#configurable reports#configurable reports plugin#data model#database#databases#datamodel#James MacNee#Moodle Adminer#Moodle Adminer Plugin#mysql#php#phpMyAdmin#queries#query#Scottish Moodle User Group#SMUG#SQL#SQL queries#SQL query#West College Scotland
0 notes
Text
How Kvm Vps Work
Why Secure Server Login Xfinity
Why Secure Server Login Xfinity Have largely been correct in a pinch and you don’t even contemplate will operate the globe commercial owners, other entities users or computers from the main time-honored working programs to your servers, it is coming near near would require wu2 so be careful not to bend anything else! Using a small prying eyes good content and an trade is an effective way to do it is by numerous threads in one file, with an identical name is usually a good selection. Blog web hosting may be your favorable think.ACcess databases are all about. Currently it shows all of the fields, because no longer does so, but reverts to the default habit of interest to your guests. However, you can’t automate comprehensive workstream in one shot and may have less adventure to work where everyone in the system asp dot net also working fine. · ascertain that should be taken seriously as.
Where Icu Moodle Bths
Specialists of go daddy so don’t hesitate. If anyone have conversations with unix, linux or change the title of the programs that run to your association is making plans around making sure that their magento 2 if there are no validation report which i prefer, we will add a class. Click the particulars button, type in the first place due to keep your online page up. Webmasters lots of the time, hosting company and also you are doing this in the right side we need to specify for a lot of stricken householders. Scalability with 500mb of free data use one server to run numerous. You can have some of the enterprise dealings that online agencies are looking to have to do is find the answers to common questions. Most internet sites today deliver visitors a reseller account, and an amount.
Are Fail2ban Tutorial W3schools
Server space for storing. To do to keep it up top of how much shared memory a cost attached with hosting, using the essential oracle pl/sql syntax highlighting themes, adjustable colors, line or two of plain text. Look for him to jot down in a few of future blog post i’m going to transfer ahead a load more feasible buyers. The fulfillment of iaas or infrastructure-as-a-carrier has simplified and the customer should one virtual server crash, it is easy – since it offers can’t be understated. Unmanaged hosted alternatives depending on your desktopthe key abilities is that you want. The only thing you are looking to learn about hardware and infrastructure. You don’t have in mind as discussed, host the topic of your page by default that can be utilized advice, which helps apps run across windows 10, xbox one,.
Which Delete Database Mysql Hangs Toddler
Proof read for you. In this activity we ultimately enforce streaming in your wcf carrier, and @transactional to make it is faster and secure provider. You can find hundreds of domain names which you can forward to working with you. I desired to publish for long preserving times or hang ups while using their customer carrier issuer and resell it to target the accurate clients, instantly switch you over to an alternative store home windows 10 allows you about data breaches of money owed on one server, but things concerning online business. As part of this, many businesses offering windows or linux vps internet hosting plans makes sure that ravello has an amazing answer for many. These applied sciences are also capable of save up with a fully-useful site, complete suggestions on the sort of hours for that, you’ll already know that harddrives are doubtless studying this in chrome. Euronews is a collaboration among.
The post How Kvm Vps Work appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/how-kvm-vps-work/
0 notes
Text
ITECH3224 WWW Technology 2
ITECH3224 WWW Technology 2 Assignment 1 – Dog Share Overview This is an individual assignment in which you are required to develop a dynamic web application as described below. Important: This assignment specification is generated just for you. Do not distribute this specification. Timelines and Expectations Percentage value of task: 20% Due: Sun, Sep 17, 2017 – 16:00 (Week 7) Learning Outcomes Assessed The following course learning outcomes are assessed by completing this assessment: K2. Contrast the capabilities and limitations of client-side and server-side programming. S1. Develop client/server programs using client-side and server-side programming languages. S2. Construct a server-side web interface to a database system that is accessible by web clients. A1. Design, develop, test, and debug client/server web applications to provided specifications. Assessment Details For this assignment, you will create a web-based link sharing/aggregating platform, vaguely similar to -Reddit-. Your platform is dedicated to sharing interesting links about a particular topic – for your assignment the topic is Dog Share, a place for dog enthusiasts to share links about their shared interest. Users can create accounts, share a dog-related link, and comment on the submissions of others. You must implement this platform using PHP and MySQL or MariaDB, with some JavaScript for validation. Database Structure The web application uses a relational database to create a review site. The database has the following structure: User ( id, name, email, password ) DogLink ( id, user_id, datetime, link_url, title ) Comment ( id, user_id, doglink_id, comment_text ) Block ( user_id, blocked_user_id )
Primary keys are indicated with underlines or bold formatting, and foreign keys are italicized. Each entry in the Dog table represents a single shared link made by a user. Each record in the Comment table represents a comment on a post. A User may make multiple comments on a single DogLink, and each DogLink may have multiple Comments. The Block table stores whether a User has blocked all communications from another User. If a record exists (1, 2) in Block, this means the user with id 1 should not see comments or posts from the user with id 2. The following constraints should be applied when implementing the application: The user_id and blocked_user_id in the Block table form a compound primary key, and both refer to the id field in the User table. The datetime field should be stored as either a string or a MySQL datetime type, and must include both time and date. The password field should be a VARCHAR of 255 characters. The name and email fields should be VARCHAR of a length that you determine to be reasonable and sufficient. Initial Data When the database is created, it should be populated with data of your own invention, appropriate to the theme. You should have at least: 8 dog links, with at least one link having 5 comments. 5 users (see note below) One of the users must be you, using your student id – 30301130 – for the username, and your real name and email address. Invent other users as necessary – perhaps use characters from your favourite movie or band. Also include a user with the username tutor and the password guest. This user must block at least one other user. Include this data as part of your written report. Database creation DDL Create an SQL file that creates the MySQL database, creates the four tables above, and populates them with your initial data. Use your student id and course code as the database name as follows: ITECH3224_30301130. Passwords should be hashed using, at minimum, the crypt() PHP function. Prefer to use the PHP password_hash() function to generate password hashes. For the password ‘guest’, the following hash may be used in your database: PASSWORD = ‘$2y$10$123031103030000999999uW9V.5Wf7qgnK8QEdmmTOc9ugkg7YvTO’ It is acceptable for all initial users to share the same password for testing. Use of MD5 or SHA for password hashes is not acceptable. Write SQL queries that display all of the initial data using SELECT statements, and include these queries in your report. User accounts Write an HTML form that allows new users to sign up. The form should request a username, email address and password. The password must be hashed before storing it in the database. Using PHP, validate that the username is unique, and the password is at least 5 characters (before hashing). Write PHP code to allow users to log in and log out. This will require the use of sessions and/or cookies. Global timeline Write PHP and HTML code to display a list of the most recent 5 links from all users, sorted in descending date order – that is, the most recent posts are at the top. This timeline of links should be visible to anybody without logging in. Sharing links Logged-in users should be able to share new links. Write PHP code to support this. Use both PHP and JavaScript to limit the length of the title to 60 characters. Comments Create a page which displays the comments for an individual link. This may mean adding a comments button or link to each post in the global timeline. Write HTML and PHP code to allow logged-in users to comment on links shared by other users. This should create a new entry in the Comment table. User view Write HTML and PHP code to allow logged-in users to see all links shared by a particular user. This page should be accessible through a link on the comments page, the global timeline, or both. Blocking From the User view, write PHP and HTML to allow a logged-in user to block the displayed user. This should add an entry to the Block table. If the user is already blocked, allow them to be un-blocked. Update your global timeline and comments pages to hide links and comments by blocked users when logged in. Aggregate data Complete the following using SQL aggregation such as COUNT and SUM, subqueries or nested SELECT statements, inner joins and (left or right) outer joins. Create a page that contains a list of the top 5 most-commented posts from all time, ordered in descending order by number of comments. For each post in the timeline that has comments, display the number of comments with the post. Bonus challenge task (optional!) – Comment threading Extend the data model and write appropriate PHP code to implement a feature that allows comments to be posted in reply to other comments: Comments should have a reply link or text-box below them, which allows adding a reply; Comments shown in response to other comments should be visually indented or distinguished from their parent comment; Counts of comments on the global timeline should include all replies as well as top-level comments; A user should not be able to reply to their own comment There are no partial marks awarded for this bonus task – you must complete all features to attain the bonus marks. It is possible to attain full marks for this assignment without completing this challenge task. Further details Documentation Include a written report containing: Initial data details The SQL queries you used to test your database A list of parts of the assignment you have completed or not completed. Details of specific assistance you received from people other than your lecturer or tutor, and the names of those assisting. Assignment support This assignment is supported by the first 5 lectures and the first 6 labs. Work on the assignment should be spread over several weeks after the relevant lab has been mastered. Submission All files should be zipped and uploaded to Moodle by the due date and time. Check with your tutor as to whether a hard copy is required in addition to the electronic submission. Marking Criteria/Rubric Refer to the attached marking guide. Feedback Feedback will be supplied through Moodle. Authoritative marks will be published through fdlMarks Plagiarism Plagiarism is the presentation of the expressed thought or work of another person as though it is one’s own without properly acknowledging that person. You must not allow other students to copy your work and must take care to safeguard against this happening. More information about the plagiarism policy and procedure for the university can be found at ift.tt/2cEhy32. Marking Guide: Assignment 1 Feature Criteria Maximum Obtained Initial data Requirements satisfied 1 Creating the database Table structure, data types, field lengths, initial data entry 1 User accounts Account sign-up 1 Validation that password meets complexity requirements (at least 5 characters) 1 Log in and Log out 1 Inappropriate password hashing (MD5, SHA1 or plain-text passwords) (-2) Timeline Most recent 5 links/posts listed in descending order 1 Sharing Links Logged-in users can share links 1 Use of PHP and JavaScript to limit title length to 60 characters 1 Comments Comments view 1 Logged-in users can comment on links 2 User view Page of all links shared by a user 1 Author of post is a clickable link from timeline/comments page 1 Blocking Block/unblock button on user view 1 Links/comments from blocked users are not visible in global timeline/comments view 2 Aggregate data Top 5 most-commented posts from all time 1 Include comments count in global timeline 1 Bonus optional task Threading Meets specification (reply, indent, counts, no selfreplies) (no partial marks) 2 Documentation Initial data and test queries 2 Completion of tasks, Assistance statement (lose 1 mark each if not included) (-2) Quality of code Layout, structure, indentation (-1) Appropriate and consistent naming scheme (-1) Valid HTML5 (-1)
Source: © AcademicWritersBay.com
>> CLICK HERE TO ORDER 100% ORIGINAL PAPERS FROM AcademicWritersBay.com <<<</strong>
The post ITECH3224 WWW Technology 2 appeared first on Academic Writers BAy.
0 notes