#OTP Implementing Free
Explore tagged Tumblr posts
Text
How to Apply Free OTP Technology in Your App and Website: - Infinity Webinfo Pvt Ltd

One-Time Password (OTP) technology is a widely-used method to enhance security in apps and websites. By using OTPs, you can ensure that even if a user's password is compromised, their account remains secure. This guide will show you how to implement free OTP technology in your app or website, OTP implement, free OTP implement and how to apply free OTP.
APPLY FREE OTP TECHNOLOGY IN YOUR WEBSITE AND APP
1. What is OTP Technology?
OTP Explained: An OTP is a unique, time-sensitive code sent to a user to verify their identity. It is commonly used for two-factor authentication (2FA) or during sensitive transactions.
Benefits of OTP Implementation: OTPs provide an additional layer of security, making it significantly harder for unauthorized users to access accounts.
2. Choosing a Free OTP Service
To apply free OTP technology, you need to select a service provider that offers a free tier for OTP implementation. Here are some popular options:
Google Authenticator:
Description: Google Authenticator is a mobile app that generates time-based one-time passwords (TOTP). It's widely used and can be integrated with various systems and applications.
Features: Easy to use, secure, supports multiple accounts, offline functionality.
Integration: You can integrate Google Authenticator using libraries that support TOTP in your preferred programming language, like pyotp for Python or otplib for Node.js.
Authy:
Description: Authy by Twilio is another popular app for generating OTPs. It offers both TOTP and push-based notifications.
Features: Multi-device synchronization, backups, and support for both TOTP and SMS-based OTPs.
Integration: You can integrate Authy using their API, which allows for both TOTP generation and SMS-based OTPs. This is useful if you want to give users multiple options for receiving OTPs.
FreeOTP by Red Hat:
Description: FreeOTP is an open-source mobile app by Red Hat that generates TOTP and HOTP (HMAC-based One-Time Password) tokens.
Features: Open-source, supports both TOTP and HOTP, no ads, and privacy-focused.
Integration: Similar to Google Authenticator, it can be integrated into your system using TOTP libraries.
TOTP (Time-based One-Time Password) Algorithms:
Description: TOTP is a standardized algorithm used to generate time-based OTPs. It’s widely supported and is the underlying technology behind many OTP apps, including Google Authenticator and FreeOTP.
Features: Time-based OTPs are dynamic and expire after a short period, typically 30 seconds, making them more secure.
Integration: You can implement TOTP directly using libraries like pyotp (Python), otplib (Node.js), or other language-specific libraries. These libraries provide functions to generate and verify OTPs.
When choosing an OTP technology, consider your users' needs and the level of security required. All these options are robust and can significantly enhance the security of your website or app.
3. Steps to Implement OTP in Your Website or App
1. Choose an OTP Method
Decide whether you want to implement SMS, email, or app-based OTPs. SMS and email are easier for users but may incur costs if scaled, whereas app-based OTPs are cost-effective and secure but require users to install an app.
2. Select a Library or API
Use a free library or API that supports OTP generation and validation. Some popular options include:
Python: PyOTP library for TOTP and HOTP (HMAC-based One-Time Password).
JavaScript: speakeasy for TOTP and HOTP.
PHP: GoogleAuthenticator.php for integrating with Google Authenticator.
Node.js: otplib for generating OTPs.
3. Integrate OTP Generation
In your application, add code to generate OTPs. For example, using the PyOTP library in Python: # Generate a TOTP key totp = pyotp.TOTP('base32secret3232') otp = totp.now() print("Your OTP is:", otp)
This code generates a time-based OTP that you can send to the user.
4. Send the OTP
Once the OTP is generated, send it to the user via the chosen method (SMS, email, or app). For SMS, you might use a free or freemium service like Twilio, while email can be sent using SMTP libraries or services like SendGrid.
5. Validate the OTP
After the user enters the OTP, validate it using the same library. For example, in Python: is_valid = totp.verify(user_input_otp) if is_valid: print("OTP is valid!") else: print("OTP is invalid!")
6. Handle Errors and Expirations
Ensure that your implementation handles cases where the OTP has expired or the wrong OTP is entered. Provide user-friendly messages and options to resend the OTP if necessary.
Security Best Practices
Short Expiry Time: Ensure that OTPs expire quickly, typically within 30 seconds to 5 minutes, to minimize the risk of unauthorized access.
Rate Limiting: Implement rate limiting to prevent brute-force attempts to guess the OTP.
Secure Transmission: Always use HTTPS to send OTPs to avoid interception by attackers.
Backup Options: Provide users with backup authentication methods, such as recovery codes, in case they cannot access their OTP.
7. Verify the OTP
After sending the OTP, prompt the user to enter the code they received.
Verify the entered OTP using the service provider’s API or through custom logic if using an open-source library.
8. Ensure Security
OTPs should be time-limited, typically expiring within 5 to 10 minutes.
Use secure channels (like encrypted SMS) to transmit OTPs.
Implement rate limiting to prevent brute force attacks.
4. Testing Your OTP Implementation
Test thoroughly across different devices and network conditions to ensure reliability.
Verify that OTPs are correctly sent, received, and validated.
Ensure that expired or incorrect OTPs trigger appropriate error messages.
5. Scaling Beyond Free Tiers
As your app or website grows, you might outgrow the free OTP tiers. Consider upgrading to a paid plan to accommodate more users.
Evaluate your options to balance cost with the reliability and features you need.
Conclusion
Implementing free OTP technology in your app or website is a straightforward process that enhances security without incurring significant costs. By following the steps outlined above, you can apply OTP technology effectively, ensuring your users’ accounts and data remain secure. Whether you use a service like Google Authenticator, Authy, or FreeOTP by Red Hat, the key is to integrate, test, and secure your OTP implementation properly.
#OTP Technology#Free OTP TECHNOLOGY#OTP Implementing Free#Apply free#OTP#website and app development company
1 note
·
View note
Text
Ok but imagine it: HCTCG Hermitshipping Edition
OK SO me& and my& buddy @cosmosisfold saw this one "Yaoi UNO" meme and began discussing how ships could be implemented in Hermitcraft TCG
The basic idea is that playing two or more hermit cards gives you special effects depending on the ship
This would work similar to how Beef's NHO ability works, except instead of damage it would be more like... inflicting poison on the enemy if your ship is toxic, or burn effect if it's slow burn

And you might say, "But holy TCG gods Jack and Pep! If you have all these insane free perks from getting all your hermits out in the field, then you wouldn't really need any cards other than the hermit cards!"
And to that we propose this limitation:
The effect would be called OTP, standing for One True Power, because it only works if the hermits it's for are the ONLY hermits in your deck. So basically, you choose your OTP before the game even starts.
Some examples of these OTPs would be:
"Take the enchanter" (Scarian) - gives you a completely random book item card regardless of whether or not it is in your deck, however you immediately lose a life (your Scar dies)
"Crafts supplies" (Jleo) - lowers the cost of all attacks by one item
"Whatever was going on at horse head farms" (Hypxb) - you can choose your opponent's attack on their turn due to an IOU (must select at least one attack, the opponent can still choose to use any effects and everything else)
"Hivemind" (Rendoc) - any damage received gets equally redistributed across all your hermits
and so on and so forth (feel free to leave your suggestions!)
Additionally we could rename the rarity types from Common, Rare and Ultra Rare to.... Beta, Omega and Alpha. Just because why not.
This is not super balanced yet but the basic idea sounds so fun already
36 notes
·
View notes
Text
Workshopping a new pinned post. Personal info will be under the cut.
Since GFM frequently terminates campaigns, here are some Ch^ffed [Ch]/P^yP^l [Pa] campaigns to donate to:
Lama and Mohammed. Lama suffers from intense eczema. [Ch]
Nesma. Her 6 year old sister is dependent on her, and is currently suffering from intestinal worms. [Pa]
Heyo. My online name is Mia. I'm an adult. I'm bi-gender and gender-fluid, and use both he/him and she/her pronouns.
My incomplete tag directory is as follows:
A
Ableism
Allie C - Thelemick magickian Aleister Crowley
Americanposting - "burgers and rock & roll disk" style humour [TAG OBSOLETE]
Antiblackness
Art Info
Asexual
AYBF - my "OTP"
B
Bisexual
C
Comminfo - info for commissions
Cubeposting - sweet little Kyubey
D
Dead Note - the animanga about Light Yagami
E
Evil Secretary - my best friend, Holly (hollerite here on Tumbler!)
F
G
Gamerade - video game making info
Gay - specifically concerning gay men (lesbians have their own tag)
H
I
Houseposting - the beautiful House of Leaves
Humour Storage - funny stuff for a rainy day
Intersex
Intersexism
J
K
Killerposting - The Killer. Watch out, Wendy Williams!
Kittislam - kitty cats partaking in Islam. Self-explanatory tag. :}
L
LCB - Limbus Company
Lesbian
LGBT
Lobcorp - LOBOTOMY CORPORATION YIPPEEEEEE
LoR - Library of Ruina
M
Mia Save Point - important info
Mia Storage - like Save Point, but not as urgent
N
Nonbinary
Normal Kitchen - Tumbler recipes! Includes both nice things, like Arab burgers, and lovely drinks like TWO-THIRDS BEER AND ONE-THIRD MILK- [NOT YET IMPLEMENTED]
O
Other Types Of Birds - birds which, while WONDERFUL, are not pigeons
P
Pigeon Religion - stuff featuring pigeons :D
Posts I Would Make If I Was On Tumbler - your premium, subscription-free Mia content
Q
R
Racism
Rene Magritte :D
S
Star War
T
The Labyrinth
Trans
Transfem
Transmasc
Transmisogynoir
Transmisogyny
[Note: previously, I tagged transfem/transmasc posts as "trans woman/women" and "trans man/men." However, since I could never keep consistent whether I wrote (wo)mAn or (wo)mEn, I have decided to consolidate them into these new labels. Please stand by as the tagging is fixed.]
U
V
W
Wonderlab
X
Y
Z
Zby Tag - for my other best friend, Zby. (He is not on Tumbler.)
MISC
👴🏻🎨‼️ - my art tag!
🍵🌊 - the best TV show that does not exist yet ;)
6 notes
·
View notes
Text
My Monthly Announcement and Update <3
I'm still tracking #katsigian and I'll try my best to keep up with it even when I'm busy.
You can tag me in anything OC related, and in any gifs/edits from any game <3 I know I share a lot of cyberpunk 2077 stuff, but I'm interested in/play other games too!
I was hanging back and not super active because of a bunch of IRL stuff going on (moved provinces, employment struggle, wedding, changing medications) that kept me away, plus I've been quietly working on different modding projects that keep me busy. So, a lot of radio silence but I'm going to try be more active with my very cool and supportive mutuals <3
Also, my blog clean up is 90% done - if I've been following you for a while and you've gotten a recent re-follow from me, it was very likely because I mis-clicked while I was cleaning out bots or I got sides/mains mixed up, or I got confused about a name change 😞 I have the brain fog a lot of days you see and sometimes I don't catch on to changes right away 😞
I've also gotten a much better tagging/filtering system implemented now - if there's something you don't want to see, feel free to filter at your leisure <3 I'm still heavily OC centered, but I'm also a multifandom blog now and I'll be sharing any game that I like/any game my mutuals are playing
I'm tagging text posts and shit posts with [ misc. ] pretty pictures of random scenery as [ jpeg. ] games will be tagged with their acronym if possible, such as [ bg3 - tes - eso ] and some games will be their full names if acronyms aren't available, such as [ cyberpunk 2077 - dishonored ]
I do share some NSFW content for my OCs and OTPs sometimes, so if you want to filter all of that out, I'll be using [ nsft.] to tag them. It won't be anything extremely explicit - no hole being posted here, it'll be just mostly text posts, images, and non-explicit gifs. Mostly MLM.
#little update and psa!#i hope this makes it easier for everyone who visits my blog#and that it'll help my mutuals out some#misc: personal
62 notes
·
View notes
Note
Oooh you mentioned a Lucienne x Gault meta coming! They are my otp! Would you be willing to tag me when it’s done? Here’s a gifset in case you haven’t seen it yet!
Hey! Oh yay im glad that it has some interest! I will def tag you know worries. Thanks for the gifset! Feel free to tag me in any Gaultienne content you come across as well honestly there isnt enough and i really wanna support anyone making stuff for this gorgeous ship.
Gaultienne may not have much time together, but I love the idea of them bonding in the Dreaming, of them working together to implement change and make the dreaming better.
But yes I must finish it!! The support is much appreciated!
29 notes
·
View notes
Note
Are you going to do Green x Blue mini stories?
That's pretty good idea, since I love this OTP with whole my heart and they're so wonderful and cute together, that it inspires amount of stories like the one I wrote 💙_💚
But the thing is, I'm an aspiring fic-writer and I would like to prove myself in writing stories not only in this genre and not just within the same fandom. But at the same time, I don't have much free time to just simply go ahead and start implementing my ideas, since I'm in 9th grade and prepare for the exams. So I don't know if I'm gonna write smth about Blue/Green very soon, but someday I will, if you really want this. I loved how many people commented positively about my first fanfic :3 💖💗💖💗
8 notes
·
View notes
Text
Okay, so with the pinned edited-!! Few notes.
Guess I'm updating my list again... Alas, I have a lot of XIV faves- with this being the series I have the most faves from- so. Sorry for that.
Be sure to peek at what's rotting my brain the most! Active fandoms & active F/Os may not always overlap. As well, I wanted to implement this for a few reasons... 1) I no longer wish to continue having "Mains" as that never really applied to me, anyways. I do not favor some F/Os over others. 2) Since that was a good shorthand of who to ask questions about- if you didn't know me/my ships that well- I figure "active" types would be a suitable replacement!!
(In notes to my F/O List... I am trying out a few alternatives for better readability. I have a private one that tracks all tags (so just chara + OTP tag, lol) and then one I'm aiming to be public, that'll be organized via fandoms. We'll see how that goes!)
...I think that's it! Feel free to prod me about anything, but from that... Back to my voidhome I go!
#Aki speaks#moving away from family has been WONDERFUL for my health#I have an apartment with my boyf now!!!#I'm aiming to get a LOT done while I'm here#so if you're reading these tags...#know that my letter comms are still open! :D#(writing comms will be open later this month)#(with hopefully art slots to follow)
2 notes
·
View notes
Text
Leading Dating App Development Agency in USA – Building Intuitive, Scalable Solutions for Digital Connections
Building real relationships via internet technologies is a cutting-edge undertaking driven by transformative technology. What we explain below is the manner in which a Dating App Development Agency in USA designs personalized, accessible dating applications meeting the date demands of the moment. From natural interfaces to intelligent matching capabilities, the best developers are transforming the way humans match humans. The article highlights top-tier services, application performance, and strategic design methods implemented in the current business. They will also get to know how a well-established business like Derived Web creates scalable dating app solutions worth achieving success in a transforming virtual world.
Why A Specialist Dating App Agency Is Important
Swipe mechanisms have merely performed now for dating app users. Emotional intelligence, data protection, advanced filtering, and tailored matchmaking are no longer attractive. A specialized partner Dating App Development Agency in USA brings these core abilities to your platform. Professionals with relationship psychology and UI/UX bias can deliver experiences that emotionally connect, enable interaction, and retain. From location integration in your app to real-time available chat safety, everything is coded with empathy and compassion.
What Makes Top Dating App Development Services
Being unique from other app development agencies, Dating App Development Services USA specializes in the dating industry and offers feature-rich solutions. A few of the differences are:
● Custom Matching Algorithms: Utilizing machine learning and behavior trends for creating improved matches.
● State-of-the-Art User Verification: Minimizing fake accounts through biometric login, OTP verification, and AI moderation.
● Seamless Communication Features: Spontaneity-free text, voice, and video chat for creating real connections.
● Gamification Features: Invite user participation with quizzes, badges, or matching scores.
These customized features spark platform loyalty and satisfaction rates—both are critical indicators in the world of dating.
Core Features Offered by Dating App Development Companies
Effective dating apps have world-class modules that encompass the value proposition of the app and the user experience. Some of the prevalent yet reasonable features designed by a Dating App Development Agency in USA are outlined below:
● Profile Personalization: Personalized profiles with images, descriptions, hobbies, and interests created by users.
● Instant Notifications: Push, match, or activity notifications for enhanced user interaction.
● AI-Based Suggestions: Intelligent suggestions through swipes, interactions, and user behavior.
● Membership Plans: Subscription member plans for premium feature coverage.
● Admin Control Panel: Complete back-end admin control panel for user management, analytics, content moderation, and earnings tracking.
All these features demonstrate the fact that innovation in Dating App Development Services USA isn't about connecting at all—it's all experience optimization.
End-to-End Development Process Defined
Reliable agencies have an optimized iterative development process in order to deliver dating apps of quality. It usually comprises:
● Discovery & Planning: A thorough evaluation of your idea, market trend, and users forms the cornerstone of a success plan. Competitive differences and user journey maps are established by agencies.
● Design & Wireframing: Designers create the layout and design of the app, usability, looks, and interactive features being the primary concern for them. Prototyping is done in this phase.
● Development & Integration: Developers launch the app with state-of-the-art technology stacks. Geolocation, payment, and messaging APIs are easily integrated.
● Testing & QA: Consecutive cycles of tests to remove bugs and enhance performance on Android and iOS platforms.
● Launch & Post-Launch Support: The application is now deployed into app stores, with continuous monitoring, support, and optimization in features.
This bug-free workflow ensures the final product is secure, scalable, and user-friendly—the qualities of a top-notch Dating App Development Agency in USA.
Industry-Inspired Innovations Shaping Dating Apps
Technology is one of the primary drivers for dating apps. There are companies today leveraging:
● AI & Machine Learning for better match proposals
● Blockchain for data security and payment transparency
● Augmented Reality (AR) for live user profiles and live interaction
● Cloud Infrastructure for real-time scalability and zero-downtime
They are the new way to more fun, secure dating with Dating App Development Services USA.
Why User Experience is the True Matchmaker
Design and usability can break or make a dating app. Great agencies go the extra step to
● Simple Interfaces with minimalism and user intent in mind
● Quick Load Times to enable seamless swiping and messaging
● Dark Modes & Accessibility Options to facilitate making everyone a part of it
● Transparency of Data to enable trust regarding management of information
These user-centric designs form activation and emotional trust between the users and the website.
Derived Web—Experts with Consistent Competence in Building Dating Apps
Derived Web Technologies is one of the best Dating App Development Company in USA providing highly customized and secure apps on the basis of extensive industry experience.
The passion of the team to develop scalable, user-oriented applications has benefited startups, entrepreneurs, and businesses succeeding. The combination of human design, agile concepts, and AI-driven features distinguishes Derived Web from others. They deliver end-to-end solutions from UI/UX to backend development, third-party integrations, and post-launch services. Founded Web not only constructs dating apps—it constructs ecosystems of engagement and systems of connection on which brands may build and flourish in the digital relationship economy.
Conclusion
Derived Web Technologies is leading in the Dating App Development Services USA with custom, high-performance apps that transform user experience and connect. Backed by advanced solutions designed in sync with the newest technology and end-user trends, they are the first choice for dating apps aspiring to long-term success.
0 notes
Text
Daffytel.com – Your Trusted Partner for Cloud Telephony Solutions
Introduction
In today’s fast-paced business environment, effective communication is key to success. Daffytel.com is a leading cloud telephony service provider in Chennai, Madurai, and Trichy, offering advanced communication solutions that enhance customer engagement and business efficiency. Whether you need IVR, SMS solutions, AI-enabled voice services, or WhatsApp integration, Daffytel.com has the expertise to deliver exceptional results.
About Daffytel.com
Daffytel.com is a full-service cloud telephony provider that helps businesses optimize their communication strategies. With cutting-edge technology and customized solutions, we ensure seamless connectivity and enhanced customer interactions.
Our Mission
At Daffytel.com, our mission is to provide businesses with reliable, innovative, and cost-effective cloud telephony solutions that drive efficiency and customer satisfaction.
Our Vision
Our vision is to be a market leader in cloud communication services, delivering high-quality solutions that transform business communication.
Services Offered by Daffytel.com
1. Voice Solutions
Daffytel.com offers advanced voice-based communication services, including:
Interactive Voice Response (IVR): Automated systems that interact with callers and route calls efficiently.
Click to Call: Enables instant communication between customers and businesses.
Audio Conferencing: Connect multiple participants for seamless group discussions.
Voice Blasting: Broadcasts pre-recorded voice messages to a large audience.
Missed Call Service: Engage with customers through a simple missed call for lead generation or feedback collection.
Toll-Free Solutions: Provides free-to-call numbers for better customer support accessibility.
2. SMS Solutions
Enhance business communication with our SMS services:
Two-Way SMS: Enables interactive messaging between businesses and customers.
Push SMS: Sends bulk promotional or transactional messages to targeted audiences.
2FA OTP SMS: Provides secure one-time passwords for authentication processes.
Dynamic APIs: Integrates SMS capabilities into business applications.
3. AI & Digital Communication Solutions
Stay ahead with AI-driven and digital solutions:
AI-enabled Voice: Enhances customer interactions with intelligent voice responses.
Smart URL: Manages marketing campaigns with trackable and customizable URLs.
WhatsApp Integration: Facilitates customer communication via WhatsApp.
Voicebot: Implements AI-powered automated voice responses for customer support.
Why Choose Daffytel.com?
✅ Reliable Cloud Telephony Solutions
Our services are built on robust cloud infrastructure, ensuring high availability and reliability.
✅ Custom Communication Strategies
We tailor our solutions to meet the specific needs of businesses across different industries.
✅ Data-Driven Approach
We use advanced analytics and AI to optimize performance and improve customer experiences.
✅ Cost-Effective Services
Our cloud-based communication solutions are designed to reduce operational costs while improving efficiency.
✅ Proven Results
We have helped numerous businesses streamline their communication and enhance customer engagement.
Contact Information
📍 Location: Chennai, Tamil Nadu, India
🌐 Website: www.daffytel.com
📧 Email: Not specified
📞 Phone: Not specified
📲 Social Media:
Facebook: facebook.com/daffytel
Instagram: instagram.com/daffytel
LinkedIn: linkedin.com/company/daffytel
Conclusion
Daffytel.com is your go-to cloud telephony partner for seamless business communication. Whether you need IVR, SMS, AI-enabled voice, or WhatsApp integration, we provide customized solutions that drive real results. Contact us today to transform your business communication!
Visit www.daffytel.com to explore our services and start your journey towards smarter communication!
0 notes
Text
Secure Digital Transactions with ATT: A Game-Changer for Online Security

In today’s fast-paced digital world, secure Secure digital transactions with ATT transactions have become a cornerstone of online business and personal financial activities. Cyber threats are on the rise, making it imperative for businesses and individuals to adopt secure digital transaction methods. One of the most promising solutions in this domain is Authenticated Transfer Technology (ATT), a cutting-edge security framework designed to ensure the safety and integrity of digital transactions.
Understanding ATT and Its Importance
Authenticated Transfer Technology (ATT) is a sophisticated security protocol that enhances the safety of online transactions. It employs advanced encryption techniques, multi-layer authentication, and real-time fraud detection mechanisms to safeguard user data. ATT is designed to prevent unauthorized access, mitigate fraud risks, and provide a seamless and secure transaction experience.
As digital transactions become more prevalent in sectors like banking, e-commerce, and digital payments, ensuring the security of these transactions is crucial. ATT acts as a digital shield, preventing cybercriminals from intercepting sensitive information and ensuring that transactions are conducted only between authorized entities.
Key Features of ATT for Secure Digital Transactions
1. Multi-Factor Authentication (MFA)
ATT integrates multi-factor authentication to add an extra layer of security. This requires users to verify their identity through multiple verification methods, such as passwords, biometric scans, and one-time passcodes (OTP). MFA significantly reduces the risk of unauthorized access and identity theft.
2. End-to-End Encryption
End-to-end encryption ensures that sensitive financial data is securely transmitted between users and servers without any risk of interception. ATT utilizes advanced cryptographic protocols to protect data integrity and confidentiality, making digital transactions more secure than ever.
3. Real-Time Fraud Detection
Cyber threats are evolving, making real-time fraud detection an essential component of secure transactions. ATT employs artificial intelligence (AI) and machine learning (ML) algorithms to analyze transaction patterns and detect any suspicious activities. This proactive approach helps in preventing fraudulent transactions before they can cause harm.
4. Seamless Integration with Financial Systems
One of the biggest advantages of ATT is its ability to integrate seamlessly with existing financial systems. Whether it’s a banking platform, a payment gateway, or an e-commerce store, ATT enhances security without disrupting the user experience.
5. Blockchain-Based Verification
Blockchain technology plays a crucial role in ATT by providing decentralized verification of transactions. This ensures transparency, reduces the chances of fraud, and enhances the trustworthiness of digital transactions.
Benefits of ATT in Digital Transactions
Enhanced Security
The primary benefit of ATT is the heightened security it provides. By implementing strong authentication methods, encryption, and fraud detection systems, ATT minimizes the risk of data breaches and financial fraud.
Improved User Trust
Customers are more likely to engage in digital transactions when they feel their financial information is safe. ATT helps build trust by ensuring transactions are authenticated, secure, and transparent.
Regulatory Compliance
With governments and financial institutions imposing strict regulations on digital transactions, ATT helps businesses comply with security standards such as PCI DSS, GDPR, and ISO 27001. Compliance not only protects businesses from legal issues but also enhances their reputation.
Seamless and Fast Transactions
Despite its robust security features, ATT ensures that digital transactions remain fast and hassle-free. Users can conduct transactions with confidence, knowing their information is protected without unnecessary delays.
The Future of Secure Transactions with ATT
As cyber threats continue to evolve, the need for secure digital transaction solutions like ATT will only grow. Financial institutions, e-commerce platforms, and digital service providers are increasingly adopting ATT to strengthen their security infrastructure.
Innovations such as biometric authentication, AI-driven fraud detection, and blockchain-powered verification are expected to further enhance ATT’s capabilities. As these technologies advance, ATT will continue to be at the forefront of digital transaction security, providing businesses and consumers with a reliable and secure way to conduct financial activities online.
Conclusion
Secure digital transactions are essential in today’s digital economy, and ATT is revolutionizing the way security is implemented. By offering multi-factor authentication, end-to-end encryption, real-time fraud detection, and seamless integration with existing financial systems, ATT provides a comprehensive security solution for digital transactions.
As cyber threats become more sophisticated, adopting ATT will be crucial for businesses and individuals who prioritize security. By leveraging this technology, we can move towards a future where digital transactions are not only convenient but also highly secure, fostering trust and confidence in the online financial ecosystem
0 notes
Text
Miss Call Service in Jaipur: A Powerful Tool for Business Growth
In the digital age, businesses are constantly seeking innovative ways to engage with their customers efficiently. One such powerful and cost-effective solution is the Miss Call Service in Jaipur. This service allows businesses to interact with their audience effortlessly, making it an ideal marketing and customer service tool. With the growing demand for quick and accessible communication, Sms Me Now provides top-notch Miss Call Service in Jaipur, helping businesses streamline their customer interactions.
This article explores the importance, benefits, and applications of Miss Call Services, providing a comprehensive guide for businesses looking to leverage this technology in Jaipur.

What is Miss Call Service?
Miss Call Service is a cloud-based communication solution that allows users to engage with businesses by simply giving a missed call. The system automatically logs the call and triggers an automated response, such as an SMS reply, a call-back, or lead registration.
This service is widely used by businesses for:
Customer verification
Lead generation
Feedback collection
Subscription activation
Customer support
With its simplicity and efficiency, the Miss Call Service in Jaipur has gained popularity among businesses looking for hassle-free engagement with customers.
How Does Miss Call Service Work?
The process is straightforward:
A customer dials a specific business number and disconnects the call after one ring.
The system registers the missed call and logs the caller's details.
An automated response, such as an SMS, IVR call, or callback, is triggered.
Businesses use this data for customer engagement, marketing, or lead nurturing.
Why Businesses Need Miss Call Service in Jaipur
Jaipur, being a rapidly growing commercial hub, requires businesses to adopt smart and efficient communication channels. Here’s why Miss Call Service in Jaipur is essential for businesses:
1. Cost-Effective Solution
No charges for customers, encouraging higher engagement rates.
Affordable for businesses compared to traditional marketing strategies.
2. High Customer Engagement
Customers find it easier to give a missed call rather than filling out lengthy forms.
Ideal for surveys, feedback, and lead generation.
3. Improved Lead Generation
Businesses can collect customer details instantly.
Leads are automatically stored in the database for follow-ups.
4. Enhancing Customer Support
Customers can raise service requests without waiting in queues.
Missed call services ensure quick responses and better support.
5. Automation and Integration
Can be integrated with CRM systems for better data management.
Automated responses save time and improve efficiency.
Applications of Miss Call Service in Jaipur
Various industries can benefit from implementing a Miss Call Service in Jaipur. Let’s explore some practical applications:
1. Banking and Financial Services
Account balance inquiry
Loan and credit card inquiries
OTP verification for secure transactions
2. E-Commerce and Retail
Order confirmations and tracking
Customer feedback and ratings
Subscription activation
3. Healthcare and Medical Services
Appointment booking and reminders
Medicine refill requests
Health check-up and consultation scheduling
4. Education and Coaching Centers
Inquiry about courses and admissions
Exam results and notifications
Student attendance tracking
5. Political and Social Campaigns
Voter registration drives
Opinion polls and surveys
Event participation confirmation
6. Non-Profit Organizations and NGOs
Fundraising campaigns
Volunteer registrations
Awareness programs
7. Real Estate and Property Management
Property inquiry and site visit scheduling
Project updates and pricing details
Customer feedback collection
Features of Miss Call Service by Sms Me Now
Sms Me Now offers advanced and customizable Miss Call Service in Jaipur with features such as:
1. Real-Time Call Tracking
Live dashboard for monitoring missed calls and responses.
Instant notifications for businesses to act on leads.
2. Auto-Reply via SMS or IVR
Automated SMS responses with relevant information.
IVR callback options for enhanced engagement.
3. CRM Integration
Seamless integration with CRM systems for better data handling.
Helps in lead nurturing and tracking customer interactions.
4. Call Routing and Forwarding
Directs calls to the appropriate department for quick resolution.
Ensures seamless customer support.
5. Analytics and Reporting
Detailed reports on call volumes, responses, and engagement rates.
Helps businesses optimize their campaigns.
6. Multi-Location Support
Businesses with multiple locations can set up region-specific missed call numbers.
Enhances customer convenience.
How to Get Started with Miss Call Service in Jaipur
Setting up a Miss Call Service in Jaipur with Sms Me Now is simple and efficient. Here’s how you can get started:
Choose a Miss Call Number: Select a virtual number based on your business needs.
Define Your Call Flow: Decide whether you want an SMS reply, callback, or data storage.
Integrate with Your System: Link the service with your CRM or customer database.
Launch Your Campaign: Promote the missed call number through marketing channels.
Monitor and Optimize: Analyze reports to improve engagement strategies.

Why Choose Sms Me Now for Miss Call Service?
Sms Me Now is a leading provider of Miss Call Service in Jaipur, offering unparalleled features and customer support. Here’s why businesses prefer us:
1. Reliable and Scalable Solutions
Designed to handle high call volumes without downtime.
Scalable for businesses of all sizes.
2. Affordable Pricing
Budget-friendly plans suitable for startups and enterprises.
No hidden costs or extra charges.
3. Customization Options
Tailored solutions to meet specific business requirements.
Flexible API integrations available.
4. 24/7 Customer Support
Dedicated support team to assist with technical queries.
Quick issue resolution and guidance.
Future of Miss Call Service in Jaipur
With businesses increasingly shifting to digital solutions, the Miss Call Service in Jaipur is expected to grow in popularity. Some future trends include:
AI-Powered Automation: Enhanced chatbot and AI-based customer interactions.
Cloud Integration: Improved cloud storage and data analytics.
Multi-Channel Communication: Integration with WhatsApp, SMS, and email services.
Conclusion
In today’s fast-paced business environment, staying connected with customers is crucial. The Miss Call Service in Jaipur offers a cost-effective, efficient, and user-friendly solution for businesses looking to enhance customer engagement and lead generation. Whether you run a startup, an enterprise, or a social initiative, this service can transform your communication strategy.
With Sms Me Now, businesses can access top-quality Miss Call Service in Jaipur, ensuring seamless customer interactions and improved business growth. Get started today and experience the benefits of this powerful communication tool!
#Sms Me Now#Sms Now#Voice Sms In Jaipur#Otp Sms In Jaipur#Ivr Service In Jaipur#Bulk Sms Service Provider In Jaipur#Bulk Sms In Jaipur#Miss Call Service In Jaipur#Website Development In Jaipur#Digital Marketing In Jaipur
0 notes
Text
How to Develop a Feature-Rich Visitor Management System for Residences

With residential communities expanding rapidly, ensuring security and seamless visitor tracking has never been more crucial. A 2023 report states that over 70% of gated communities have experienced unauthorized entries due to inefficient visitor tracking. Traditional paper logbooks and manual visitor records are outdated, inefficient, and prone to security breaches. A visitor management system provides a digital solution, addressing the inefficiencies of traditional logbooks by enabling residences to track visitors, manage entry approvals, and enhance overall security in real-time.
Developing a feature-rich visitor management system for society requires careful planning, advanced technology, and a user-friendly interface. This article explores essential features, the development process, and best practices to create a visitor management app that enhances safety and convenience for residential communities.
Key Features That Define a Robust Visitor Management System
Before diving into the development process, it's essential to understand what makes a visitor management system for society effective. The following features ensure a secure and smooth visitor experience.
1. Secure and Contactless Check-In A society visitor management solution must include a secure and contactless check-in process. Visitors should be able to scan a QR code or enter their details digitally instead of using traditional logbooks. Implementing facial recognition and biometric authentication can further enhance security.
2. Digital Visitor Logs and Real-Time Tracking A visitor management system for apartments should store visitor data digitally, enabling real-time tracking of who enters and exits the premises. This feature helps security personnel and residents monitor movements, ensuring transparency and safety.
3. Pre-Approved Guest Entries One of the most requested features in visitor management software is pre-approved guest entry. Residents can send invitations to their guests, allowing them hassle-free access with a QR code or OTP-based verification upon arrival.
4. Integration with Smart Security Systems A visitor management system for society should integrate with smart surveillance cameras, intercom systems, and access control solutions. This integration enables seamless visitor verification and automated gate access.
5. Host Notifications and Approval Mechanism Residents must receive real-time notifications when a visitor arrives. An approval system allows them to accept or deny entry requests via a visitor management app, ensuring only authorized guests gain access.
6. Visitor Badge Printing and Digital Passes For societies requiring physical identification, the system should offer visitor badge printing. Alternatively, digital passes can be sent via SMS or email for easy entry.
7. Emergency Alerts and Evacuation Support A well-designed visitor management system development plan must include emergency alert mechanisms. Security teams should be able to send mass alerts to all residents and visitors in case of emergencies, ensuring prompt action and evacuation.
8. Compliance with Data Protection Regulations With increasing concerns over data security, ensuring compliance with privacy laws like GDPR or local data protection standards is essential. The system should encrypt visitor data and provide role-based access to protect sensitive information.
Steps to Develop a Feature-Rich Visitor Management System
Step 1: Define the Requirements and Objectives Before starting visitor management system development, outline the key objectives. Identify specific security challenges, resident requirements, and administrative needs to ensure a comprehensive solution.
Step 2: Select the Right Technology Stack for Performance and Security Selecting the appropriate technology stack is vital for ensuring smooth performance, scalability, and security in a visitor management software. Here’s how different technologies contribute to the system's efficiency: Selecting the right technology stack is crucial for building a scalable and efficient visitor management software. Consider using:
• Frontend: React, Angular, or Vue.js for a responsive user interface • Backend: Node.js, Django, or Laravel for efficient data handling • Database: MySQL, MongoDB, or PostgreSQL for secure data storage • Mobile App: Flutter or React Native for cross-platform accessibility • Cloud Integration: AWS, Google Cloud, or Azure for real-time data processing
Step 3: Design an Intuitive User Interface A visitor management app should have a user-friendly interface for residents, security personnel, and administrators. The app must include simple navigation, easy visitor registration, and real-time notifications.
Step 4: Develop Core Functionalities After designing the UI, the development team must work on core features such as visitor check-in, approval mechanisms, real-time tracking, and security system integration. Implementing AI-powered analytics can enhance visitor tracking accuracy.
Step 5: Implement Security Measures Security should be the foundation of any visitor management system for apartments. Multi-factor authentication, data encryption, and role-based access control can prevent unauthorized access and ensure secure visitor data storage.
Step 6: Test and Optimize the System Conduct thorough testing before deployment to eliminate bugs and performance issues. Perform:
• Unit Testing to validate each feature • Integration Testing to check system-wide compatibility • Load Testing to ensure smooth performance during peak hours • User Acceptance Testing (UAT) to gather feedback from residents and security teams
Step 7: Deploy and Maintain the System After successful testing, deploy the system for real-time use. Regular maintenance, feature updates, and security patches ensure the system remains effective and up to date.
Why Implementing a Visitor Management System is a Game-Changer
Switching from manual visitor logs to a digital visitor management system for society revolutionizes security, operations, and convenience. Here’s how: A well-developed visitor management system for society offers numerous benefits:
• Enhanced Security: Reduces unauthorized entries and improves resident safety • Operational Efficiency: Automates visitor tracking, eliminating manual paperwork • Seamless Experience: Provides smooth check-in and check-out for visitors • Real-Time Monitoring: Enables instant tracking of visitor movements within the community • Compliance Assurance: Ensures compliance with security and data privacy regulations
Conclusion: Secure Your Residential Community with an Advanced Visitor Management System
Investing in a visitor management system is no longer a luxury but a necessity for modern residential complexes. By integrating real-time visitor tracking, automated approvals, and smart security solutions, communities can ensure a safer and more efficient living environment. Developing a feature-rich visitor management system is essential for modern residential complexes, ensuring a secure, seamless, and efficient visitor experience. From real-time visitor tracking to smart security integration, an advanced visitor management system for apartments enhances safety while reducing manual efforts.
If you are looking for a trusted visitor management system development company, Idiosys Tech offers expert solutions tailored to residential security needs. Contact us today to develop a custom visitor management system that ensures safety, convenience, and operational efficiency for your society.
Ready to enhance your residential security? Get in touch with Idiosys Tech today!
________________________
Why is a visitor management system important for residential complexes?
It enhances security, streamlines visitor check-ins, prevents unauthorized access, and provides residents with better control over who enters their premises.
What are the key features of a residential visitor management system?
Essential features include digital check-in, QR code or OTP-based access, real-time notifications, visitor pre-registration, ID verification, and emergency alerts.
How does a visitor management system improve security?
It records visitor details, verifies identity, restricts access based on permissions, and alerts security personnel about unauthorized entries.
Can residents pre-approve visitors using the system?
Yes, most VMS platforms allow residents to pre-register guests, reducing wait times and ensuring a seamless entry process.
Can visitors check in using their mobile phones?
Yes, visitors can check in via mobile apps, QR codes, or self-service kiosks, reducing manual paperwork and wait times.
How does a visitor management system handle emergency situations?
Many systems include panic buttons, emergency alerts, and real-time evacuation tracking to enhance resident safety.
________________________
You May Also Read
How Society Management Apps Are Revolutionizing Housing Communities
9 Must Have Features for Property Management Apps to Boost Efficiency
How a Society Management App Improves Resident Engagement
#visitor management system#visitor management app#visitor management#visitor management system development
0 notes
Text
Big Daddy Login: A Comprehensive Guide for Seamless Access
In the digital age, easy and secure access to online platforms is essential. Whether you are managing a website, handling financial transactions, or engaging in gaming, having a smooth login process is crucial. One such platform that requires efficient access is Big Daddy Login. This article provides a detailed guide on how to navigate the login process, troubleshoot common issues, and maximize security.
What is Big Daddy Login?
Big Daddy Login refers to the gateway for users to access the Big Daddy platform. It could relate to various industries, such as gaming, finance, or business management. Having an active account and understanding the login procedure ensures a hassle-free experience for users.
How to Access Big Daddy Login
To log in successfully, follow these simple steps:
Visit the Official Website: Open your preferred web browser and go to the Big Daddy login page.
Enter Your Credentials: Provide your username or email ID along with your password.
Two-Factor Authentication (If Enabled): Some platforms require additional security, such as an OTP sent to your registered email or phone number.
Click on the Login Button: After entering the required details, press the login button to access your account.
Common Issues and Troubleshooting for Big Daddy Login
Even the most well-designed login systems can present issues. Here are some common problems and their solutions:
Forgotten Password: Click on the "Forgot Password" link and follow the instructions to reset it.
Incorrect Credentials: Double-check the spelling of your username and password. Ensure Caps Lock is turned off.
Browser Issues: Clear cookies and cache or try logging in through a different browser.
Account Lockout: Multiple failed attempts may result in temporary suspension. Wait for some time or contact customer support.
Server Issues: If the website is down, wait for official updates or try again later.
Ensuring Security for Big Daddy Login
Keeping your account secure is of utmost importance. Here are some tips:
Use Strong Passwords: Avoid using easy-to-guess passwords. Instead, use a combination of letters, numbers, and special characters.
Enable Two-Factor Authentication (2FA): This adds an extra layer of security.
Beware of Phishing Attacks: Do not click on suspicious links claiming to be Big Daddy Login pages.
Regularly Update Credentials: Changing your password periodically enhances security.
Log Out After Use: Always log out when using a public or shared device.
Conclusion
Having seamless access through Big Daddy Login is essential for a smooth user experience. By following the login steps, troubleshooting common issues, and implementing security measures, you can ensure safe and easy access to your account. Whether for gaming, business, or financial purposes, staying informed about login protocols will help you make the most of the platform. Always remember to prioritize security and stay updated with any changes in the login process to avoid disruptions.
1 note
·
View note
Text
SMSWala SMS API Integration by Infinity Webinfo Pvt Ltd

In today’s fast-paced digital world, businesses rely heavily on SMS communication to engage customers, send notifications, and authenticate transactions. To streamline this process, Infinity Webinfo Pvt Ltd offers expert SMSWala SMS API Integration services, enabling businesses to automate and enhance their messaging solutions efficiently.
Why Choose SMSWala SMS API?
The SMSWala SMS API is a powerful and scalable solution designed to cater to various business communication needs. Whether for marketing campaigns, OTP verifications, or bulk notifications, this API ensures fast, secure, and reliable SMS delivery.
Key Benefits of SMSWala SMS API Integration:
Seamless Integration: Easily integrates with websites, mobile apps, and CRM systems.
High Delivery Rate: Ensures quick and efficient message delivery across networks.
Real-time Reporting: Track SMS status and delivery reports instantly.
Scalability: Supports bulk messaging for large-scale operations.
Cost-effective: Provides an affordable solution for businesses of all sizes.
Infinity Webinfo Pvt Ltd – Your Trusted Integration Partner
Infinity Webinfo Pvt Ltd specializes in API integration services, ensuring a hassle-free setup of the SMSWala SMS API for your business. With a team of experienced developers, the company ensures a smooth and secure implementation tailored to your requirements.
How We Help:
Consultation & Planning: Understanding your messaging needs and business requirements.
Custom API Integration: Implementing SMSWala API into your existing systems.
Testing & Deployment: Ensuring flawless functionality and smooth operation.
Ongoing Support & Maintenance: Providing continuous support for updates and troubleshooting.
Industries That Benefit from SMSWala SMS API Integration
E-commerce: Order updates, promotions, and OTP verifications.
Banking & Finance: Secure transaction alerts and customer notifications.
Healthcare: Appointment reminders and emergency alerts.
Education: Exam notifications and attendance alerts.
Logistics & Delivery: Real-time shipment tracking and customer updates.
Get Started Today!
Enhance your business communication with SMSWala SMS API Integration by Infinity Webinfo Pvt Ltd. Contact us today to streamline your SMS operations and stay ahead in the competitive digital landscape.
For more details, reach out to us now!
Contact Now :- +91 97110 90237
#api integration#SMSWala SMS API#SMSWALA API Integration#API Integration by Infinity Webinfo Pvt Ltd#SMSWALA#SMS API
0 notes
Text
Comprehensive Bulk SMS Solutions in Bangalore – A2ZSMS
Description: A2ZSMS offers a range of bulk SMS services in Bangalore, including promotional, transactional, and OTP messages. Our services are designed to help businesses effectively reach their target audience with timely and relevant information. We provide user-friendly interfaces and robust APIs to ensure seamless integration and efficient message delivery.
Website Analysis:
Title: Bulk SMS | A2ZSMS
Content Overview:
Services Offered:
Promotional Bulk SMS: Ideal for marketing campaigns to engage potential customers.
Transactional Bulk SMS: Used for sending critical information such as alerts and notifications.
OTP SMS: Ensures secure transactions with instant one-time passwords.
Features:
User-friendly web interface for easy campaign management.
Robust API integration for seamless connectivity with existing systems.
Real-time delivery reports to monitor campaign effectiveness.
Compliance:
Adherence to TRAI regulations to ensure ethical and legal messaging practices.
Recommendations:
Title Enhancement:
Current Title: "Bulk SMS | A2ZSMS"
Suggested Title: "Comprehensive Bulk SMS Solutions in Bangalore – A2ZSMS"
Rationale: Including "Bangalore" and "Solutions" can improve local SEO and clearly convey the range of services offered.
Content Expansion:
Provide detailed descriptions of each service, including use cases and benefits, to help potential clients understand how each service can meet their specific needs.
Client Testimonials:
Incorporate testimonials or case studies to showcase successful campaigns and build trust with prospective clients.
Pricing Information:
Include transparent pricing plans or a pricing calculator to assist businesses in making informed decisions.
Call to Action:
Add clear calls to action, such as "Contact Us for a Free Consultation" or "Sign Up for a Free Trial," to encourage potential clients to engage with your services.
By implementing these recommendations, A2ZSMS can enhance its online presence, provide valuable information to potential clients, and encourage engagement with its bulk SMS services in Bangalore.

#Bulk SMS Service Bangalore#OTP SMS Gateway Bangalore#SMS Marketing Bangalore#Voice SMS Service India#Promotional SMS Bangalore#Bulk SMS Provider India
1 note
·
View note
Text
Best Practices for Developing a Secure and User-Friendly Banking App
In today’s digital age, consumers prefer using mobile apps for banking and financial transactions. Some examples include Apple Pay or Google Pay for contactless payments in stores; Banking apps to check account balances, transfer funds, pay bills, deposit checks via photo capture, and apply for loans or credit cards; insurance apps to pay premiums, file claims, and access roadside assistance; and many more.
While the convenience of using such mobile applications is undeniable, security and user experience are of utmost importance to ensure both the safety and satisfaction of users. Users expect their banking app not only to be intuitive and easy to use but also to keep their sensitive information safe. Here are the best practices for creating a secure and user-friendly banking app that meets the needs of both financial organizations and their end customers.
Banking App Development: Best Practices
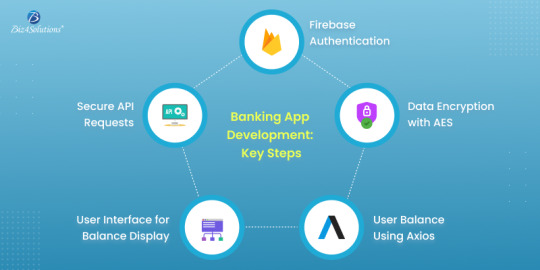
User Authentication
Secure user authentication is the foundation of a safe banking app. A combination of methods—such as multi-factor authentication (MFA), biometric verification (fingerprints, facial recognition), and one-time passwords (OTPs)—creates multiple layers of security that deter unauthorized access. Using biometric authentication, for example, can enhance security while making the login experience fast and hassle-free for the user.
Best Practices:
Implement 2FA or MFA as a standard protocol.
Encourage users to enable biometric authentication.
Use session timeouts and automatically log out users after a period of inactivity.
Data Encryption and Secure Communication Channels
If you encrypt your data following standard mechanisms; any user wouldn’t be able to read or access it without the correct decryption key. End-to-end encryption secures data during transmission, while AES (Advanced Encryption Standard) can safeguard stored data.
Best Practices:
Encrypt all kinds of sensitive data like personal details, account numbers, etc.
Use SSL/TLS certificates so that data is transmitted securely.
Update encryption techniques regularly to stay aligned with industry standards.
Implement Strong Access Controls
Access control is essential to prevent unauthorized access to user data and system resources. Role-based access control (RBAC) allows only authorized users and systems to access sensitive information or perform specific functions. This helps reduce the attack surface and limit potential damage from a data breach.
Best Practices:
Use RBAC to define user permissions.
Review access logs for identifying unusual access patterns.
Establish different user roles (e.g., user, admin) with distinct access levels.
Regular Security Audits and Penetration Testing
Banks should regularly conduct security audits and penetration testing to identify vulnerabilities and areas for improvement. These tests simulate potential attack vectors and help developers patch security flaws before they can be exploited.
Best Practices:
Partner with third-party security firms for unbiased audits.
Perform routine vulnerability assessments.
Keep a continuous improvement cycle by scheduling regular security reviews.
User-Friendly Interface and UX Design
A secure banking app is only effective if users find it easy to use. The user interface (UI) should be designed for clarity, simplicity, and accessibility. The user experience (UX) in banking applications should minimize friction by making essential functions like logging in, viewing balances, and transferring money intuitive and quick.
Best Practices:
Conduct user testing to optimize the app’s UI and flow.
Use clear labeling and simple navigation.
Focus on the essential features; avoid overloading users with too many options.
Compliance with Financial Regulations
Banks operate in a highly regulated environment, and financial apps must adhere to industry standards and government regulations such as PCI DSS (Payment Card Industry Data Security Standard) and GDPR (General Data Protection Regulation) for data privacy.
Best Practices:
Familiarize yourself with relevant regulations (GDPR, PCI DSS, CCPA).
Implement data protection measures in compliance with these standards.
Keep records of data handling and retention policies for audits.
Implement Fraud Detection and Prevention Mechanisms
Integrating real-time monitoring systems to detect fraudulent activity can help prevent unauthorized transactions. Leveraging AI and machine learning models can improve the detection of suspicious activities, especially those that differ from typical user patterns.
Best Practices:
Set up alerts for unusual transaction behaviors.
Integrate AI-driven fraud detection models.
Allow users to freeze accounts and report suspicious activity directly through the app.
Regularly Update and Patch the App
Keeping the app updated is critical, as outdated software is vulnerable to attacks. Regular updates allow developers to apply patches that protect against newly discovered security threats. Furthermore, these updates can improve usability by fixing bugs and enhancing the app’s performance.
Best Practices:
Set up a dedicated schedule for maintenance and updates.
Communicate update benefits to users to encourage installations.
Patch security vulnerabilities immediately upon discovery.
Educate Users on Security Best Practices
A secure app design alone is not enough if users are unaware of potential security risks. Informing users about the best practices, such as avoiding public Wi-Fi when accessing mobile banking apps and setting strong passwords, helps create an additional line of defence.
Best Practices:
Send regular security tips and updates to users.
Create in-app guides or FAQs on protecting accounts.
Prompt users to review and update their security settings periodically.
Final Thoughts
Creating a secure and user-friendly banking app is a continuous process that requires a proactive approach to security and usability. By implementing these best practices, banks and financial institutions can ensure that their apps not only provide top-grade security but also a seamless and satisfying UX. The result? Higher user trust, better engagement, and a competitive edge over peers. Here's a handy tip: If you don’t have a comprehensive in-house IT team, collaborating with a trusted IT partner can make all the difference.
0 notes