#OffensiveSecurity
Explore tagged Tumblr posts
Text

Are organizations truly prepared to defend against the relentless surge of cyber threats? Recent reports from leading cybersecurity firms such as Gartner highlight that the demand for offensive security professionals has surged by over 30% in the past year alone.
0 notes
Text
AI and cybersecurity: Modernize your SecOps to tackle today's threats

The introduction of AI has triggered a profound transformation in the landscape of offensive security. https://jpmellojr.blogspot.com/2024/10/how-ai-is-becoming-powerful-tool-for.html
0 notes
Text
NoSQLMap: Automated NoSQL Database Enumeration | #Enumeration #NoSQL #NoSQLMap #OffensiveSecurity #Hacking
0 notes
Photo
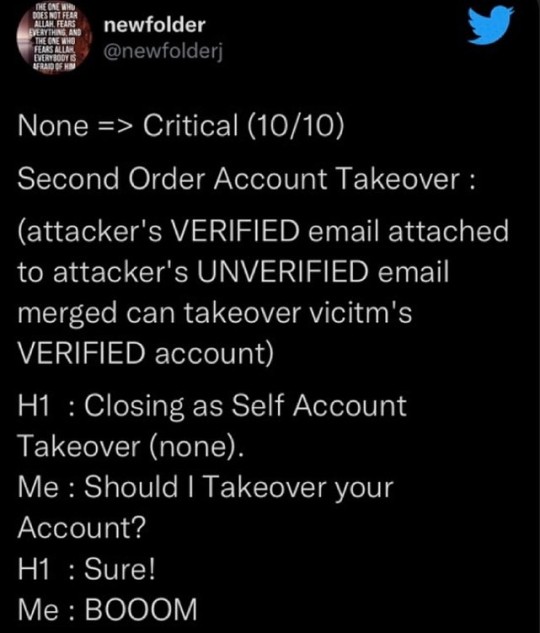
Daily Tweets. #tweets #tweetsfromtwitter #hackertweet #hackerinstagram #biohacking #applicationsecurity #lifehacks #mobilehacks #penetrationtesting #offensivesecurity https://www.instagram.com/p/ClRSbmVy0Mq/?igshid=NGJjMDIxMWI=
#tweets#tweetsfromtwitter#hackertweet#hackerinstagram#biohacking#applicationsecurity#lifehacks#mobilehacks#penetrationtesting#offensivesecurity
4 notes
·
View notes
Text
Okey, okay.
my best friend annoys me!!! I ignore him but he tries to restore our relationship.
first of all, I became being like that because he offended me. literally hurt my soul hardly and seriously.
I don't find the strength to forgive him.
he's an asshole:(
#black love#literature#i love you#likeforlikes#pop music#romeo and juliet#shakespeare#chandler bing#euro 2020#friends tv show#love story#frienship#friends#like4like#likeforfollow#instagram#chronic pain#offensivesecurity#sorry#fuck you#fuck
2 notes
·
View notes
Link

#threat detection#OffensiveSecurity#RedTeam#BlueTeam#OSINT#AttackSurface#Phishing#PostExploitation#Exploit#ThreatDetection
1 note
·
View note
Video
instagram
Why settle for Clint Bondad's hacking stories if we tell better hacking stories based on real-world scenarios than him? ✌️We'll teach you how to do it properly without any cryptic messages though 😏 Here are some of the feedback that we have during our Julu's VAPT Bootcamp 3 days to go before we start our August Bootcamp. We're still accepting enrollees! #GuideM2PWN #GuideM2Secure #GuideMOnline #VAPT #penetrationtesting #offensivesecurity #cybersecurity #ethicalhacking https://www.instagram.com/p/CDRvEZzAmXf/?igshid=2fldmie4zi7k
#guidem2pwn#guidem2secure#guidemonline#vapt#penetrationtesting#offensivesecurity#cybersecurity#ethicalhacking
1 note
·
View note
Photo

The 15th Edition of cOcOn. International Security & Hacking Conference. #connect #collaborate #contribute www.cOcOn.org . . . #cOcOn #keralapolice #cyberdome #mammootty #cybersecurity #ethicalhackingandcybersecurity #hackers #conference #hacking #internationalconference #cyberworld #meta #metauniverse #metaverse #cyberdefense #offensivesecurity #antidrone #defense #keralapolicecyberdome #cocon2022 #grandhyatt #mammookka #kochi #kerala #canon #canon6dphotography #arjunrkrishnaphotography (at Grand Hyatt Kochi Bolgatty) https://www.instagram.com/p/Ci92ui7PWIF/?igshid=NGJjMDIxMWI=
#connect#collaborate#contribute#cocon#keralapolice#cyberdome#mammootty#cybersecurity#ethicalhackingandcybersecurity#hackers#conference#hacking#internationalconference#cyberworld#meta#metauniverse#metaverse#cyberdefense#offensivesecurity#antidrone#defense#keralapolicecyberdome#cocon2022#grandhyatt#mammookka#kochi#kerala#canon#canon6dphotography#arjunrkrishnaphotography
0 notes
Photo

You are not your thoughts, you are what you do #kalilinux #linux #debian #pentesting #hack #fwh #fewwillhunt #talkless #domore #talklessdomore #whitehat #offensivesecurity #training #work #future #love #beyourself https://www.instagram.com/p/B8ad13vHX3e/?igshid=vc1ujqe69558
#kalilinux#linux#debian#pentesting#hack#fwh#fewwillhunt#talkless#domore#talklessdomore#whitehat#offensivesecurity#training#work#future#love#beyourself
0 notes
Text
0 notes
Text
Powerglot - Encodes Offensive Powershell Scripts Using Polyglots
Powerglot - Encodes Offensive Powershell Scripts Using Polyglots #Encodes #Netcat #Offensive #OffensiveSecurity
[sc name=”ad_1″]
Powerglot encodes several kind of scripts using polyglots, for example, offensive powershell scripts. It is not needed a loader to run the payload.
In red-team exercises or offensive tasks, masking of payloads is usually done by using steganography, especially to avoid network level protections, being one of the most common payloads scripts developed in powershell. Recent…
View On WordPress
#Encodes#Netcat#Offensive#Offensive Security#Payload#Polyglot#Polyglots#Powerglot#PowerShell#Privilege Escalation#python3#Red Team#scripts
1 note
·
View note
Photo

Raccoon: Offensive Security Tool for Reconnaissance | #Cybersecurity #OffensiveSecurity #Reconnaissance #Scanning #Vulnerabilities #Security
0 notes
Photo

She Came, She Found Vulnerability, She Injected, She Stole, She Made a Backdoor, She Defaced, She Left Her Impression, She Went Anonymous, She Infected, No Traces were found the ip was Anonymous, Reverse IP Tracking Failed with Fatal Error, Reverse Proxy Tracking the Server was Confused, If it is a Computer, it would be nothing for me but it was my Heart which got infected, No Hacker or Doctor in this world can patch this, I don't know her face, I don't know her voice, I don't know where she lives, I don't know from where she was, I don't know whether she will come again, I don't know when she will come again, But She is somewhere in this planet. I may be a hacker but am also a human with heart. It's not a poetry it is a real incident which happened few months ago in my hacking history. I realised hacking and psychology had a great connection in human life. For security I cannot say on which protocol she came. " SHE WAS A HACKER ONE WHO HACKED A HACKER'S HEART " <3 #offensivesecurity (en Querétaro Arteaga, Mexico)
0 notes
Link
#vulnerability#OffensiveSecurity#payloads#VAPT#RedTeam#Blueteam#ProcessInjection#Enumeration#Bugbounty#Infosec#Appsec#Hacking#Cyber#ap#expl
0 notes
Text
[Media] RedTeam-OffensiveSecurity
RedTeam-OffensiveSecurity Tools & Interesting Things for RedTeam Ops https://github.com/bigb0sss/RedTeam-OffensiveSecurity

0 notes
Video
youtube
Socat - Socket CAT | Fundamentals of Cybersecurity
SOCAT (Socket CAT)
It is a networking tool that is used for transferring data between two location. Location could be socket or port such as TCP, UDP, Ipv4 and so on. Utility for data transfer between two address.
Syntax -
#socat [option] <address ><address>
In one machine, command prompt,
# socat - TCP4-LISTEN:4444 -- you will get "hello" message here
In another machine, command prompt,
# socat - TCP4:192.168.117.130:4444 -- you can send the message "hello"
#sockets #port #socat #SOCAT #portforwarding #portredirection #ethicalhacking #cybersecurity #offensivesecurity
0 notes